Cloud Computing Solution for DTGOV
VerifiedAdded on 2023/03/17
|29
|8675
|51
AI Summary
This report aims to provide the appropriate cloud computing solution for the DTGOV organisation for allowing the fast computing capabilities in the organisation. The recommended cloud architectures for the organisation that could be deployed by the organisation. The benefits and the issues of the recommended cloud architecture are provided in this report. The major risks of the hybrid cloud strategy has been briefly described in this report along with the critical analysis of these issues on the organisation. The information security controls and the steps that are required to be taken for securing the computing of the organisation are clearly stated in this report. The recommends that are required to be included in the policies and the protocols of the organisation are clearly stated along with the clear discussion of the information security. The operations checklist has been provided for the cloud deployment. Lastly this report concludes with an appropriate conclusion for the report that provides the summary of the report.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CLOUD COMPUTING SOLUTION FOR DTGOV
CLOUD COMPUTING SOLUTION FOR DTGOV
Name of student
Name of university
Author’s note:
CLOUD COMPUTING SOLUTION FOR DTGOV
Name of student
Name of university
Author’s note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
CLOUD COMPUTING SOLUTION FOR DTGOV
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Recommended architectures......................................................................................2
Issues and benefits of recommended cloud architecture..........................................10
Issues of Service load balancing architecture:.....................................................10
Benefits of Service load balancing architecture:..................................................10
Issues of dynamic scaling architecture:................................................................11
Benefits of the dynamic scaling architecture:......................................................11
Issues of resource pooling architecture:...............................................................12
Benefits of the resource pooling architecture:.....................................................13
Risks of hybrid cloud strategy..................................................................................13
Information security steps and the controls.............................................................15
Recommends that are to be included.......................................................................18
Backup and disaster recovery...............................................................................18
Application resilience...........................................................................................19
Operations checklist.................................................................................................20
Conclusion....................................................................................................................21
References....................................................................................................................23
CLOUD COMPUTING SOLUTION FOR DTGOV
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Recommended architectures......................................................................................2
Issues and benefits of recommended cloud architecture..........................................10
Issues of Service load balancing architecture:.....................................................10
Benefits of Service load balancing architecture:..................................................10
Issues of dynamic scaling architecture:................................................................11
Benefits of the dynamic scaling architecture:......................................................11
Issues of resource pooling architecture:...............................................................12
Benefits of the resource pooling architecture:.....................................................13
Risks of hybrid cloud strategy..................................................................................13
Information security steps and the controls.............................................................15
Recommends that are to be included.......................................................................18
Backup and disaster recovery...............................................................................18
Application resilience...........................................................................................19
Operations checklist.................................................................................................20
Conclusion....................................................................................................................21
References....................................................................................................................23

2
CLOUD COMPUTING SOLUTION FOR DTGOV
Introduction
This report aims to provide the appropriate cloud computing solution for the DTGOV
organisation for allowing the fast computing capabilities in the organisation. The
recommended cloud architectures for the organisation that could be deployed by the
organisation. The benefits and the issues of the recommended cloud architecture are provided
in this report. The major risks of the hybrid cloud strategy has been briefly described in this
report along with the critical analysis of these issues on the organisation. The information
security controls and the steps that are required to be taken for securing the computing of the
organisation are clearly stated in this report. The recommends that are required to be included
in the policies and the protocols of the organisation are clearly stated along with the clear
discussion of the information security. The operations checklist has been provided for the
cloud deployment. Lastly this report concludes with an appropriate conclusion for the report
that provides the summary of the report.
Discussion
In the present times, the companies are increasingly becoming global organisations.
These organisations commonly do not restrict themselves in the conducting of business in
any single location. This is the similar situation with the DTGOV organisation who wants to
expand their business and increase the availability of the data for the employees and the
customers of the organisation.
Recommended architectures
Some of the architecture that would help the organisation to fulfil the business
strategies are:
CLOUD COMPUTING SOLUTION FOR DTGOV
Introduction
This report aims to provide the appropriate cloud computing solution for the DTGOV
organisation for allowing the fast computing capabilities in the organisation. The
recommended cloud architectures for the organisation that could be deployed by the
organisation. The benefits and the issues of the recommended cloud architecture are provided
in this report. The major risks of the hybrid cloud strategy has been briefly described in this
report along with the critical analysis of these issues on the organisation. The information
security controls and the steps that are required to be taken for securing the computing of the
organisation are clearly stated in this report. The recommends that are required to be included
in the policies and the protocols of the organisation are clearly stated along with the clear
discussion of the information security. The operations checklist has been provided for the
cloud deployment. Lastly this report concludes with an appropriate conclusion for the report
that provides the summary of the report.
Discussion
In the present times, the companies are increasingly becoming global organisations.
These organisations commonly do not restrict themselves in the conducting of business in
any single location. This is the similar situation with the DTGOV organisation who wants to
expand their business and increase the availability of the data for the employees and the
customers of the organisation.
Recommended architectures
Some of the architecture that would help the organisation to fulfil the business
strategies are:

3
CLOUD COMPUTING SOLUTION FOR DTGOV
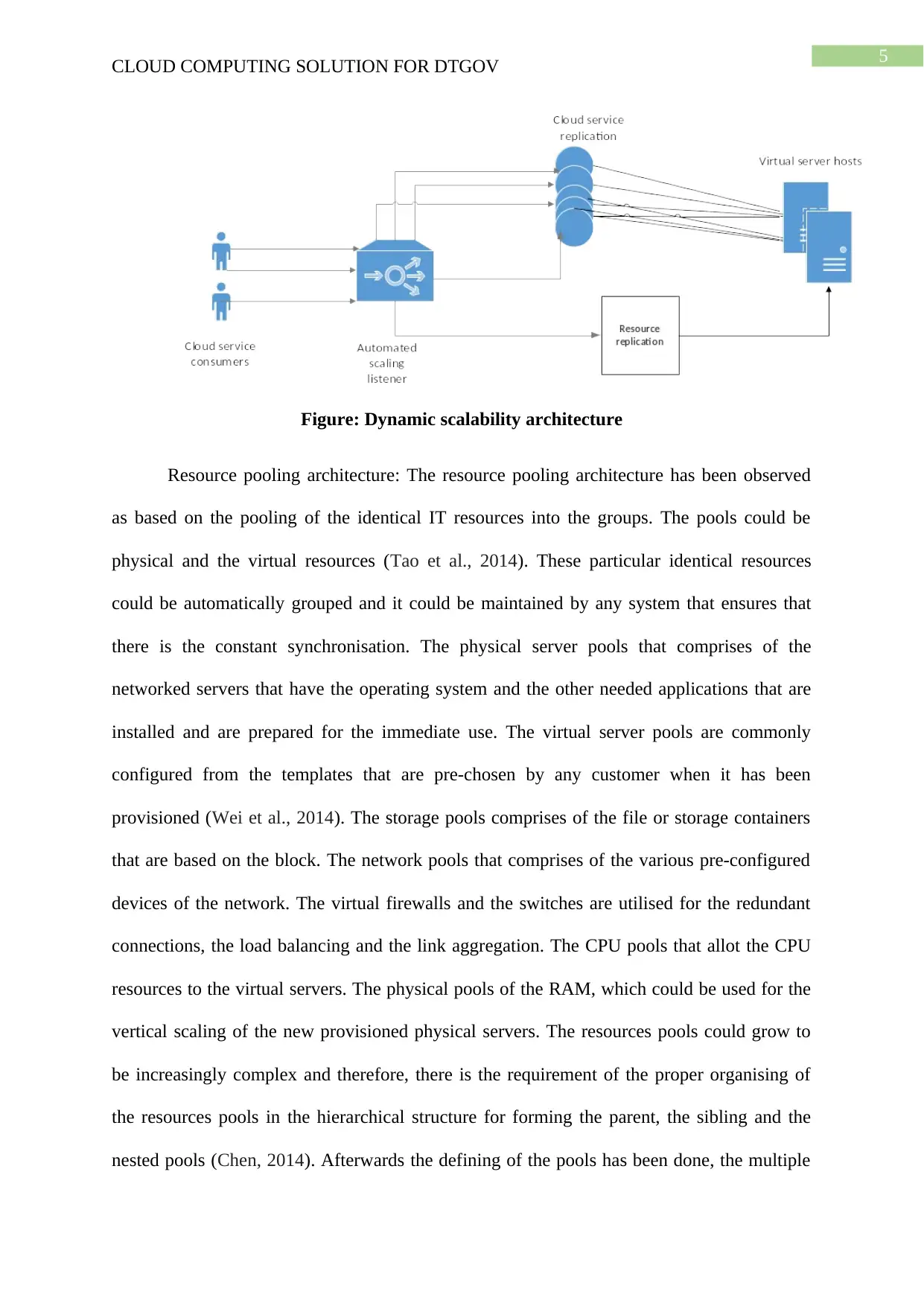
Dynamic scalability architecture: This architecture is the architectural model that is
based on the system of any predefined scaling conditions that triggers the dynamic allocation
of all the IT resources from the resource pools (Rittinghouse & Ransome, 2016). The
dynamic allocation allows the variable utilisation as it has been dictated by the demand
fluctuations of the usage as the unnecessary IT resources could be effectively reclaimed
deprived of any requiring manual interaction. The listener of the automated scaling has been
configured with the workload thresholds that perform the dictation when the new IT
resources are required to be added to all the workload processing (Hashem et al., 2015). The
mechanism could be offered with the logic that determines the number of the extra IT
resources could be dynamically provided on the basis of the terms of any provided
provisioning contract of any cloud consumer. Some of the dynamic scaling that could be
utilised by the organisation are the dynamic horizontal scaling, the dynamic vertical scaling,
and the dynamic relocation. In the dynamic horizontal scaling, the instances of the IT
resources are scaled in and out in for handling the workloads that are significantly
fluctuating. The automatic scaling listener performs the effective monitoring of the requests
and the replication of the signals resources for the initiation of the IT resource duplication
according the permissions and the requirements. In the dynamic vertical scaling, the instances
of the IT resources could be scaled down and up when any major requirement of the adjusting
has been faced for the processing capacity of any single IT resource (Botta et al., 2016). As
an example, the virtual server that has been overloaded could have the memory dynamically
extended or it might have the addition of the processing core. In the dynamic relocation, the
relocation of the IT resources is done to any host with the increased capacity. This dynamic
scalability architecture could be applied to the significant range of the IT resources that
includes the virtual servers as well as the cloud storage devices. Besides this core automated
scaling listener as well as the mechanisms of the resource replication, some of the
CLOUD COMPUTING SOLUTION FOR DTGOV
Dynamic scalability architecture: This architecture is the architectural model that is
based on the system of any predefined scaling conditions that triggers the dynamic allocation
of all the IT resources from the resource pools (Rittinghouse & Ransome, 2016). The
dynamic allocation allows the variable utilisation as it has been dictated by the demand
fluctuations of the usage as the unnecessary IT resources could be effectively reclaimed
deprived of any requiring manual interaction. The listener of the automated scaling has been
configured with the workload thresholds that perform the dictation when the new IT
resources are required to be added to all the workload processing (Hashem et al., 2015). The
mechanism could be offered with the logic that determines the number of the extra IT
resources could be dynamically provided on the basis of the terms of any provided
provisioning contract of any cloud consumer. Some of the dynamic scaling that could be
utilised by the organisation are the dynamic horizontal scaling, the dynamic vertical scaling,
and the dynamic relocation. In the dynamic horizontal scaling, the instances of the IT
resources are scaled in and out in for handling the workloads that are significantly
fluctuating. The automatic scaling listener performs the effective monitoring of the requests
and the replication of the signals resources for the initiation of the IT resource duplication
according the permissions and the requirements. In the dynamic vertical scaling, the instances
of the IT resources could be scaled down and up when any major requirement of the adjusting
has been faced for the processing capacity of any single IT resource (Botta et al., 2016). As
an example, the virtual server that has been overloaded could have the memory dynamically
extended or it might have the addition of the processing core. In the dynamic relocation, the
relocation of the IT resources is done to any host with the increased capacity. This dynamic
scalability architecture could be applied to the significant range of the IT resources that
includes the virtual servers as well as the cloud storage devices. Besides this core automated
scaling listener as well as the mechanisms of the resource replication, some of the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
CLOUD COMPUTING SOLUTION FOR DTGOV
mechanisms that could also be utilised in the form of the cloud architecture are the cloud
usage monitor, the hypervisor and the pay-per-use monitor (Whaiduzzaman et al., 2014).
With the help of this architecture, the database in the cloud storage could be elastically and
dynamically scalable. This allows the firm to provide the complete data availability for the
customers and the employees of the organisation. The database architecture that could be
significantly used by the organisation are the share nothing database architecture and the
shared disk database architecture. Within the shared nothing database architecture, the
partitioning of the data could be done and then maintained into the partitioned servers. It
could be observed that the performance could be significantly decreased with addition of any
extra servers (Chen et al., 2015). These particular aspects are the present problems that are
being faced by organisations while the shared nothing database is being deployed in the
cloud. In the architecture of the shared disk database, there is no requirement of the
partitioning of the data. It utilises the group of the low cost servers with the sole collection of
the data. Deprived of the partitioning, the complete data could be placed in total servers and it
has been defined as the master-master configuration. If any of the node fails, the other nodes
could provide the required service to the organisation. Therefore, it majorly supports the
dynamic and the elastic scalability, the high availability and the reduced maintenance (Ali,
Khan & Vasilakos, 2015). This architectural model is significantly based on the system of the
predefined conditions of the scaling that performs the triggering of the dynamic allocation of
all the IT resources from the resource pools. This dynamic allocation allows the variable
utilisation as it has been dictated by the usage demand fluctuations as the unnecessary IT
resources could be efficiently reclaimed deprived of any requirement of the manual
interaction.
CLOUD COMPUTING SOLUTION FOR DTGOV
mechanisms that could also be utilised in the form of the cloud architecture are the cloud
usage monitor, the hypervisor and the pay-per-use monitor (Whaiduzzaman et al., 2014).
With the help of this architecture, the database in the cloud storage could be elastically and
dynamically scalable. This allows the firm to provide the complete data availability for the
customers and the employees of the organisation. The database architecture that could be
significantly used by the organisation are the share nothing database architecture and the
shared disk database architecture. Within the shared nothing database architecture, the
partitioning of the data could be done and then maintained into the partitioned servers. It
could be observed that the performance could be significantly decreased with addition of any
extra servers (Chen et al., 2015). These particular aspects are the present problems that are
being faced by organisations while the shared nothing database is being deployed in the
cloud. In the architecture of the shared disk database, there is no requirement of the
partitioning of the data. It utilises the group of the low cost servers with the sole collection of
the data. Deprived of the partitioning, the complete data could be placed in total servers and it
has been defined as the master-master configuration. If any of the node fails, the other nodes
could provide the required service to the organisation. Therefore, it majorly supports the
dynamic and the elastic scalability, the high availability and the reduced maintenance (Ali,
Khan & Vasilakos, 2015). This architectural model is significantly based on the system of the
predefined conditions of the scaling that performs the triggering of the dynamic allocation of
all the IT resources from the resource pools. This dynamic allocation allows the variable
utilisation as it has been dictated by the usage demand fluctuations as the unnecessary IT
resources could be efficiently reclaimed deprived of any requirement of the manual
interaction.
5
CLOUD COMPUTING SOLUTION FOR DTGOV
Figure: Dynamic scalability architecture
Resource pooling architecture: The resource pooling architecture has been observed
as based on the pooling of the identical IT resources into the groups. The pools could be
physical and the virtual resources (Tao et al., 2014). These particular identical resources
could be automatically grouped and it could be maintained by any system that ensures that
there is the constant synchronisation. The physical server pools that comprises of the
networked servers that have the operating system and the other needed applications that are
installed and are prepared for the immediate use. The virtual server pools are commonly
configured from the templates that are pre-chosen by any customer when it has been
provisioned (Wei et al., 2014). The storage pools comprises of the file or storage containers
that are based on the block. The network pools that comprises of the various pre-configured
devices of the network. The virtual firewalls and the switches are utilised for the redundant
connections, the load balancing and the link aggregation. The CPU pools that allot the CPU
resources to the virtual servers. The physical pools of the RAM, which could be used for the
vertical scaling of the new provisioned physical servers. The resources pools could grow to
be increasingly complex and therefore, there is the requirement of the proper organising of
the resources pools in the hierarchical structure for forming the parent, the sibling and the
nested pools (Chen, 2014). Afterwards the defining of the pools has been done, the multiple
CLOUD COMPUTING SOLUTION FOR DTGOV
Figure: Dynamic scalability architecture
Resource pooling architecture: The resource pooling architecture has been observed
as based on the pooling of the identical IT resources into the groups. The pools could be
physical and the virtual resources (Tao et al., 2014). These particular identical resources
could be automatically grouped and it could be maintained by any system that ensures that
there is the constant synchronisation. The physical server pools that comprises of the
networked servers that have the operating system and the other needed applications that are
installed and are prepared for the immediate use. The virtual server pools are commonly
configured from the templates that are pre-chosen by any customer when it has been
provisioned (Wei et al., 2014). The storage pools comprises of the file or storage containers
that are based on the block. The network pools that comprises of the various pre-configured
devices of the network. The virtual firewalls and the switches are utilised for the redundant
connections, the load balancing and the link aggregation. The CPU pools that allot the CPU
resources to the virtual servers. The physical pools of the RAM, which could be used for the
vertical scaling of the new provisioned physical servers. The resources pools could grow to
be increasingly complex and therefore, there is the requirement of the proper organising of
the resources pools in the hierarchical structure for forming the parent, the sibling and the
nested pools (Chen, 2014). Afterwards the defining of the pools has been done, the multiple

6
CLOUD COMPUTING SOLUTION FOR DTGOV
instances of the resources from each of the pool could be utilised for the creation of the in-
memory pool of all the live IT resources that could be pulled and then utilised on the demand
by any system as it is required. The resources pool architecture utilises the several kinds of
the similar kind of the mechanisms as the architecture of the workload distribution functions
and these are the auditing of the pools for the effective monitoring of the usage of the
resources pools, the utilisation of the cloud usage monitor at the run time for the effective
tracking and the synchronising of the IT resources and the underlying management systems,
the hypervisor that manages the access of the virtual server pools and the virtual server for
any other resources pools, the use of the logical network perimeter that could logically
organise and then isolate the resources pools, the utilisation of the Pay-per-use monitor is
done that collects the information of the usage and the billing on the basis of how the IT
resources are being used by the customers of the organisation and the remote administration
is also used that has the major function of the creation of the interface with the back-end
servers for the effective administration of the resource pools, the resource management
system is used that offers the customers with all the required tools and the options of the
permission management that is used for the administration of the resource pools and the
resource replication that helps in the generating of several new instances of the resource for
the resources pools as it has been dictated by the demand (Almorsy, Grundy & Müller, 2016).
The sharing of the identical IT resources for the scalability purposes could be significantly
error prone and it is the problem for maintaining the completely synchronised on any on-
going basis. The provided solution for this kind of issue is the maintenance of the automated
synchronisation system for the effective grouping of the identical IT resources into the pools
and for maintaining the effective synchronicity. The resource pooling architecture could be
utilised for both the horizontally or the vertically scale the systems on the basis of the proper
organising of the pools. The resource pools of the RAM and the CPU could be utilised for the
CLOUD COMPUTING SOLUTION FOR DTGOV
instances of the resources from each of the pool could be utilised for the creation of the in-
memory pool of all the live IT resources that could be pulled and then utilised on the demand
by any system as it is required. The resources pool architecture utilises the several kinds of
the similar kind of the mechanisms as the architecture of the workload distribution functions
and these are the auditing of the pools for the effective monitoring of the usage of the
resources pools, the utilisation of the cloud usage monitor at the run time for the effective
tracking and the synchronising of the IT resources and the underlying management systems,
the hypervisor that manages the access of the virtual server pools and the virtual server for
any other resources pools, the use of the logical network perimeter that could logically
organise and then isolate the resources pools, the utilisation of the Pay-per-use monitor is
done that collects the information of the usage and the billing on the basis of how the IT
resources are being used by the customers of the organisation and the remote administration
is also used that has the major function of the creation of the interface with the back-end
servers for the effective administration of the resource pools, the resource management
system is used that offers the customers with all the required tools and the options of the
permission management that is used for the administration of the resource pools and the
resource replication that helps in the generating of several new instances of the resource for
the resources pools as it has been dictated by the demand (Almorsy, Grundy & Müller, 2016).
The sharing of the identical IT resources for the scalability purposes could be significantly
error prone and it is the problem for maintaining the completely synchronised on any on-
going basis. The provided solution for this kind of issue is the maintenance of the automated
synchronisation system for the effective grouping of the identical IT resources into the pools
and for maintaining the effective synchronicity. The resource pooling architecture could be
utilised for both the horizontally or the vertically scale the systems on the basis of the proper
organising of the pools. The resource pools of the RAM and the CPU could be utilised for the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CLOUD COMPUTING SOLUTION FOR DTGOV
vertically scaling of any IT resource like the virtual server if there is any increase in the
workload and there is a major requirement of the CPU as well as the RAM (Sadiku, Musa &
Momoh, 2014). The virtual servers could pull these specific resources from the resource
pools of the CPU and the RAM. In any live environment of the business who are using the
application servers might face significant issue when the workload increases and there is the
requirement of the increase in the hosting by the virtual server along with the increased CPU
cycles and the RAM for effective computation. The request is sent by the virtual server for
the resources from Resource Management System that allocates the increase RAM and the
CPU resources from resource pool of the RAM and CPU for the vertical scaling of the server
(Gai et al., 2016). When there is a drop in the load, the resources could be released and it is
made available to resources pool once more. The resources pools like the virtual or the
physical servers could be extensively utilised for the horizontal scaling of the system by
implementing the extra virtual or the physical servers from any virtual server pool online as
soon as the demand is increased, then the shutdown could be done again when workloads
scales down (Botta et al., 2014). Some of the kinds of the resources pools are the physical
server pools that are composed of the networked servers which has been installed along with
the operating systems as well as the other necessary applications and the programs that are
ready to use immediately. The virtual server pools are commonly configured by the
utilisation of the sole of the various available templates that are chosen by any cloud
consumer while the provisioning is done (Marinescu, 2017). The storage or pools of the cloud
storage device comprises of the file based or even block based structures of storage that
comprises of the empty or the filled devices of the cloud storage. The network pools
commonly comprises of the distinct preconfigured connectivity devices of the network. As an
instance, the pool of the devices on the virtual firewall or the switches on the physical
network could be created for the redundant connectivity, the load balancing or the link
CLOUD COMPUTING SOLUTION FOR DTGOV
vertically scaling of any IT resource like the virtual server if there is any increase in the
workload and there is a major requirement of the CPU as well as the RAM (Sadiku, Musa &
Momoh, 2014). The virtual servers could pull these specific resources from the resource
pools of the CPU and the RAM. In any live environment of the business who are using the
application servers might face significant issue when the workload increases and there is the
requirement of the increase in the hosting by the virtual server along with the increased CPU
cycles and the RAM for effective computation. The request is sent by the virtual server for
the resources from Resource Management System that allocates the increase RAM and the
CPU resources from resource pool of the RAM and CPU for the vertical scaling of the server
(Gai et al., 2016). When there is a drop in the load, the resources could be released and it is
made available to resources pool once more. The resources pools like the virtual or the
physical servers could be extensively utilised for the horizontal scaling of the system by
implementing the extra virtual or the physical servers from any virtual server pool online as
soon as the demand is increased, then the shutdown could be done again when workloads
scales down (Botta et al., 2014). Some of the kinds of the resources pools are the physical
server pools that are composed of the networked servers which has been installed along with
the operating systems as well as the other necessary applications and the programs that are
ready to use immediately. The virtual server pools are commonly configured by the
utilisation of the sole of the various available templates that are chosen by any cloud
consumer while the provisioning is done (Marinescu, 2017). The storage or pools of the cloud
storage device comprises of the file based or even block based structures of storage that
comprises of the empty or the filled devices of the cloud storage. The network pools
commonly comprises of the distinct preconfigured connectivity devices of the network. As an
instance, the pool of the devices on the virtual firewall or the switches on the physical
network could be created for the redundant connectivity, the load balancing or the link

8
CLOUD COMPUTING SOLUTION FOR DTGOV
aggregation (Jula, Sundararajan & Othman, 2014). Along with the virtual servers and the
devices of the cloud storage that are commonly mechanisms of the pooling, there are some of
the mechanisms that could be the part of the cloud architecture, that includes the audit
monitor, the cloud usage monitor, the hypervisor, the perimeter of the logical network, the
monitor of the pay-per-use, the system of the remote administration, the system for the
resource management and the resources replication.
Figure: Resource pooling architecture
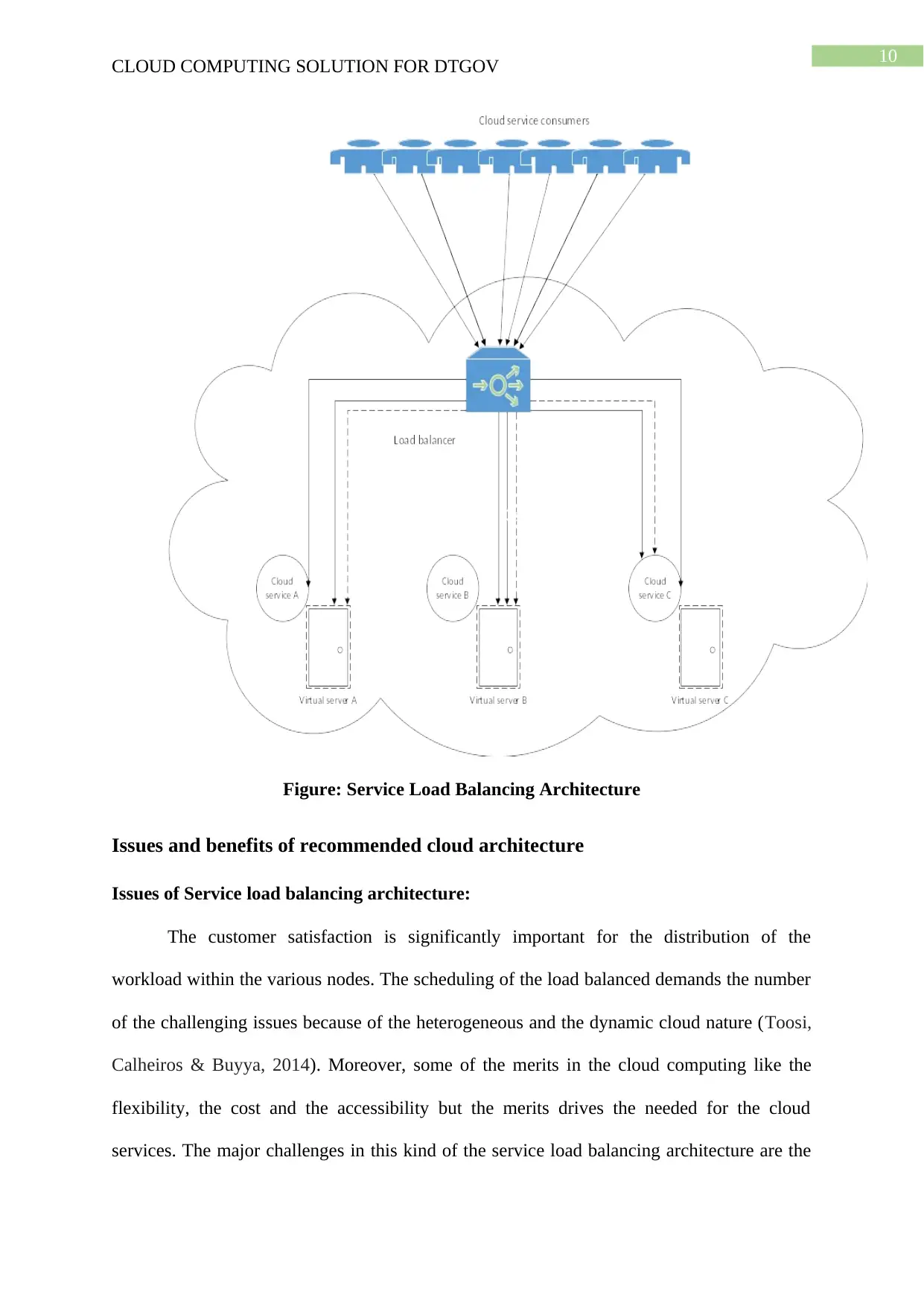
Service Load Balancing Architecture: This particular architecture could be defined as
the specialised version of architecture of the workload distribution, which is specifically
designed for the scaling of the implementation of the cloud services (Aazam & Huh, 2014).
The redundant deployments of the cloud services could be created with the system of load
balancing that is added for the dynamic distribution of the workloads. This duplicate
implementation of the cloud service could be organisation into the resource pool while the
positioning of the load balancer is done as the either any external or the built in component
for allowing the host servers to effectively balance all the workloads on their own. On the
CLOUD COMPUTING SOLUTION FOR DTGOV
aggregation (Jula, Sundararajan & Othman, 2014). Along with the virtual servers and the
devices of the cloud storage that are commonly mechanisms of the pooling, there are some of
the mechanisms that could be the part of the cloud architecture, that includes the audit
monitor, the cloud usage monitor, the hypervisor, the perimeter of the logical network, the
monitor of the pay-per-use, the system of the remote administration, the system for the
resource management and the resources replication.
Figure: Resource pooling architecture
Service Load Balancing Architecture: This particular architecture could be defined as
the specialised version of architecture of the workload distribution, which is specifically
designed for the scaling of the implementation of the cloud services (Aazam & Huh, 2014).
The redundant deployments of the cloud services could be created with the system of load
balancing that is added for the dynamic distribution of the workloads. This duplicate
implementation of the cloud service could be organisation into the resource pool while the
positioning of the load balancer is done as the either any external or the built in component
for allowing the host servers to effectively balance all the workloads on their own. On the

9
CLOUD COMPUTING SOLUTION FOR DTGOV
basis of the anticipated workload and the processing capacity of the environment of the host
server, the multiple instances of every implementation of the cloud service could be
effectively generated as the part of the resource pool that could efficiently respond to the
fluctuating request volumes with the increased efficiency (Oliveira, Thomas & Espadanal,
2014). The positioning of the load balancer could be done as either independent of all the
cloud services as well as the host servers or it could be built-in section of the environment of
the server or the application. In former case, the primary server along with the logic of the
load balancing could effectively communicate with the adjacent servers for the effective
balancing of the workload.
CLOUD COMPUTING SOLUTION FOR DTGOV
basis of the anticipated workload and the processing capacity of the environment of the host
server, the multiple instances of every implementation of the cloud service could be
effectively generated as the part of the resource pool that could efficiently respond to the
fluctuating request volumes with the increased efficiency (Oliveira, Thomas & Espadanal,
2014). The positioning of the load balancer could be done as either independent of all the
cloud services as well as the host servers or it could be built-in section of the environment of
the server or the application. In former case, the primary server along with the logic of the
load balancing could effectively communicate with the adjacent servers for the effective
balancing of the workload.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10
CLOUD COMPUTING SOLUTION FOR DTGOV
Figure: Service Load Balancing Architecture
Issues and benefits of recommended cloud architecture
Issues of Service load balancing architecture:
The customer satisfaction is significantly important for the distribution of the
workload within the various nodes. The scheduling of the load balanced demands the number
of the challenging issues because of the heterogeneous and the dynamic cloud nature (Toosi,
Calheiros & Buyya, 2014). Moreover, some of the merits in the cloud computing like the
flexibility, the cost and the accessibility but the merits drives the needed for the cloud
services. The major challenges in this kind of the service load balancing architecture are the
CLOUD COMPUTING SOLUTION FOR DTGOV
Figure: Service Load Balancing Architecture
Issues and benefits of recommended cloud architecture
Issues of Service load balancing architecture:
The customer satisfaction is significantly important for the distribution of the
workload within the various nodes. The scheduling of the load balanced demands the number
of the challenging issues because of the heterogeneous and the dynamic cloud nature (Toosi,
Calheiros & Buyya, 2014). Moreover, some of the merits in the cloud computing like the
flexibility, the cost and the accessibility but the merits drives the needed for the cloud
services. The major challenges in this kind of the service load balancing architecture are the

11
CLOUD COMPUTING SOLUTION FOR DTGOV
security issues, the legal and the compliant issues, the QoS, interoperability issues and the
performance, the load balancing and the issues of the data management. The performance
could be of significant issues for the computing environment for the complete efficiency of
system. In the service load balancing architecture, all the parameters could be improved that
would lead to the complete improvement of the system performance (Li et al., 2015). The
response time has been described in the distributed systems about the amount of time that is
required for the responding to any specific load balancing. In service load balancing
architecture, the dynamic scaling takes increased response time as opposed to the other
architecture (Avram, 2014).
Benefits of Service load balancing architecture:
The highly performing applications of the service load balancing architecture are the
major benefit of the conventional on-premise substitutes and are significantly less expensive
and the implementation process is significantly simple. The company could gain the
increased scalability and with the effective utilisation of the load balancers, the company
could easily match up with the increased traffic from the users and then distribute among the
various servers or the network devices (Fehling et al., 2014). With the implementation of the
service load balancing architecture, the company could gain the ability of effective handling
of the unseen spikes in the traffic in the network. The business continuity could be executed
with the increased flexibility. It is gained because when the workload has been distributed
among the various servers or the network units, with the failure of even one node could
burden the complete network but this burden could be effectively handled by shifting it to
any other active node (Rahimi et al., 2014).
Issues of dynamic scaling architecture:
Some of the issues that are faced by the implementation of the dynamic scaling
architecture could be categorised as the issues of migration from one cloud to another, the
CLOUD COMPUTING SOLUTION FOR DTGOV
security issues, the legal and the compliant issues, the QoS, interoperability issues and the
performance, the load balancing and the issues of the data management. The performance
could be of significant issues for the computing environment for the complete efficiency of
system. In the service load balancing architecture, all the parameters could be improved that
would lead to the complete improvement of the system performance (Li et al., 2015). The
response time has been described in the distributed systems about the amount of time that is
required for the responding to any specific load balancing. In service load balancing
architecture, the dynamic scaling takes increased response time as opposed to the other
architecture (Avram, 2014).
Benefits of Service load balancing architecture:
The highly performing applications of the service load balancing architecture are the
major benefit of the conventional on-premise substitutes and are significantly less expensive
and the implementation process is significantly simple. The company could gain the
increased scalability and with the effective utilisation of the load balancers, the company
could easily match up with the increased traffic from the users and then distribute among the
various servers or the network devices (Fehling et al., 2014). With the implementation of the
service load balancing architecture, the company could gain the ability of effective handling
of the unseen spikes in the traffic in the network. The business continuity could be executed
with the increased flexibility. It is gained because when the workload has been distributed
among the various servers or the network units, with the failure of even one node could
burden the complete network but this burden could be effectively handled by shifting it to
any other active node (Rahimi et al., 2014).
Issues of dynamic scaling architecture:
Some of the issues that are faced by the implementation of the dynamic scaling
architecture could be categorised as the issues of migration from one cloud to another, the

12
CLOUD COMPUTING SOLUTION FOR DTGOV
issues of the optimisation of the cost and the configuration in the dynamic resources
allocation, the issues related to the auto scaling, the monitoring tools and the configurations
of the cloud and another issue that is being faced by the auto scaling failures (Xia et al.,
2016). Majority of the prevailing dynamic scaling methods solely considers the utilisation of
the resources at the system level. There is the lack of the consideration of the SLAs, the
requirements of the user performance and the concerns of cost. The SLA introduces their own
respective challenges that includes the over provisioning could costly whereas the under-
provisioning could impair the performance. The auto scaling is required for improving the
resources in the response to the fluctuating changes in the load swiftly and on the demand
(Barbarossa, Sardellitti & Di Lorenzo, 2014). Moreover, the mechanisms consists of the
delays of commonly several minutes when there is the allocation of the resources. Such
delays could lead to the violation of the SLA for the real time services.
Benefits of the dynamic scaling architecture:
As the means of the encapsulation of the physical resources, the virtualisation helps in
solving the several core challenges of the datacentre managers and it also delivers the
particular advantages like the higher rates of utilisation, the increased resource consolidation,
the lower usage of the power that leads to the decrease in the costs and the extensive saving
of the spaces (Manvi & Shyam, 2014). With the utilisation of the dynamic scaling
architecture, the workloads could be encapsulated and then transferred to the idle or the
underused systems. It denotes that the prevailing systems could be significantly consolidated,
so the purchasing of the additional server capacity could be significantly delayed or it could
be avoided. The dynamic scaling that is available with this architecture allows the
consolidation of the several IT resources. Beyond the server and the storage consolidation,
the scaling offers the opportunity of consolidation of the systems architecture, the application
infrastructure, databases and the data, the interfaces, the networks, and even the business
CLOUD COMPUTING SOLUTION FOR DTGOV
issues of the optimisation of the cost and the configuration in the dynamic resources
allocation, the issues related to the auto scaling, the monitoring tools and the configurations
of the cloud and another issue that is being faced by the auto scaling failures (Xia et al.,
2016). Majority of the prevailing dynamic scaling methods solely considers the utilisation of
the resources at the system level. There is the lack of the consideration of the SLAs, the
requirements of the user performance and the concerns of cost. The SLA introduces their own
respective challenges that includes the over provisioning could costly whereas the under-
provisioning could impair the performance. The auto scaling is required for improving the
resources in the response to the fluctuating changes in the load swiftly and on the demand
(Barbarossa, Sardellitti & Di Lorenzo, 2014). Moreover, the mechanisms consists of the
delays of commonly several minutes when there is the allocation of the resources. Such
delays could lead to the violation of the SLA for the real time services.
Benefits of the dynamic scaling architecture:
As the means of the encapsulation of the physical resources, the virtualisation helps in
solving the several core challenges of the datacentre managers and it also delivers the
particular advantages like the higher rates of utilisation, the increased resource consolidation,
the lower usage of the power that leads to the decrease in the costs and the extensive saving
of the spaces (Manvi & Shyam, 2014). With the utilisation of the dynamic scaling
architecture, the workloads could be encapsulated and then transferred to the idle or the
underused systems. It denotes that the prevailing systems could be significantly consolidated,
so the purchasing of the additional server capacity could be significantly delayed or it could
be avoided. The dynamic scaling that is available with this architecture allows the
consolidation of the several IT resources. Beyond the server and the storage consolidation,
the scaling offers the opportunity of consolidation of the systems architecture, the application
infrastructure, databases and the data, the interfaces, the networks, and even the business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
CLOUD COMPUTING SOLUTION FOR DTGOV
processes that leads to the significant cost saving and the increased efficiency (Sen, 2015).
With the utilisation of this architecture for the consolidation makes it significantly possible in
cutting the complete power consumption and then save the extensive costs. The major benefit
for which this architecture is extensively utilised is that the server sprawl still exists to be the
major problem in the datacenters of the company but the datacentre expansion could not be
the sole option, with the costly building investment and the cooling costs. The dynamic
scaling could alleviate this strain by the consolidation of the several virtual systems onto the
fewer physical systems (Stergiou et al., 2018).
Issues of resource pooling architecture:
The resource pooling could be described as the service that is provided to any user by
the providers for using the various resources and then share the similar according to the
demand of the application (Etro, 2015). The security issues are the major concern that are
connected with the resource pooling that could damage the working of the organisation
significantly. As the company is intending to deploy the IaaS service model in the
organisation, the issues that could be faced by the organisation are the mobility of the data
and the data residuals, the elastic perimeter could lead to the significant challenges in the
organisation and the shared multi-talent environment could be of significant issue (Yannuzzi
et al., 2014).
Benefits of the resource pooling architecture:
The resource pooling is executed when the storage and the resources of the cloud are
pooled for serving the multiple clients at the similar time. Relying on the resource
consumption of the clients, the usage could be set for providing significant resources to all
the clients (Gangwar, Date & Ramaswamy, 2015). Some of the benefits of the resource
pooling architecture that could be gained by the organisation are the increased availability,
the load balancing, the increased performance computing, the situation when any client is
CLOUD COMPUTING SOLUTION FOR DTGOV
processes that leads to the significant cost saving and the increased efficiency (Sen, 2015).
With the utilisation of this architecture for the consolidation makes it significantly possible in
cutting the complete power consumption and then save the extensive costs. The major benefit
for which this architecture is extensively utilised is that the server sprawl still exists to be the
major problem in the datacenters of the company but the datacentre expansion could not be
the sole option, with the costly building investment and the cooling costs. The dynamic
scaling could alleviate this strain by the consolidation of the several virtual systems onto the
fewer physical systems (Stergiou et al., 2018).
Issues of resource pooling architecture:
The resource pooling could be described as the service that is provided to any user by
the providers for using the various resources and then share the similar according to the
demand of the application (Etro, 2015). The security issues are the major concern that are
connected with the resource pooling that could damage the working of the organisation
significantly. As the company is intending to deploy the IaaS service model in the
organisation, the issues that could be faced by the organisation are the mobility of the data
and the data residuals, the elastic perimeter could lead to the significant challenges in the
organisation and the shared multi-talent environment could be of significant issue (Yannuzzi
et al., 2014).
Benefits of the resource pooling architecture:
The resource pooling is executed when the storage and the resources of the cloud are
pooled for serving the multiple clients at the similar time. Relying on the resource
consumption of the clients, the usage could be set for providing significant resources to all
the clients (Gangwar, Date & Ramaswamy, 2015). Some of the benefits of the resource
pooling architecture that could be gained by the organisation are the increased availability,
the load balancing, the increased performance computing, the situation when any client is

14
CLOUD COMPUTING SOLUTION FOR DTGOV
over utilising the space that has been allocated by the host, then the virtual client could be
moved to the another physical host and if any single host goes down, any other physical host
would start the machines of the virtual goes that was being executed by the original host
(Hsu, Ray & Li-Hsieh, 2014).
Risks of hybrid cloud strategy
By the simplistic definition, the hybrid cloud could be defined as the combination of
the both private and the public cloud. The hybrid cloud is majorly the effective combination
of the private and the public cloud that is bound together by the either standardised or the
proprietary technology that helps in enabling the portability of the application and the data
(Bera, Misra & Rodrigues, 2014). It could be the combination of the private cloud within the
organisation with more than one providers of the public cloud or the private cloud that is
hosted on any premises of the third party with more than one providers of the public cloud. It
has been observed that the services of the public cloud fails to meet the IT and the
requirements of the business of some business organisations (Mastelic et al., 2015). Any
environment of the hybrid cloud could help in meeting the requirements. In several methods,
the hybrid cloud could be considered as the intermediate stage as the enterprises prepares to
shift majority of the workloads to the public clouds. The public clouds is growing to be
increasingly popular in recent years. Deprived of the maintaining of any data centre, public
cloud majorly allows the almost instant provision of the resource and the quick scaling. The
Amazon EC2 that is the product of the Amazon has increasingly contributed to development
of the public cloud and it has been considered among the first solution of the public cloud
(Lian, Yen & Wang, 2014). Moreover, not solely the growth of the cloud community is
happening but number of the critiques is significantly increasing. Specifically, not solely in
the terms of the data privacy and the security but it is considered in the other topics like the
vendor lock-in, the availability, and the interoperability and the public cloud carries the
CLOUD COMPUTING SOLUTION FOR DTGOV
over utilising the space that has been allocated by the host, then the virtual client could be
moved to the another physical host and if any single host goes down, any other physical host
would start the machines of the virtual goes that was being executed by the original host
(Hsu, Ray & Li-Hsieh, 2014).
Risks of hybrid cloud strategy
By the simplistic definition, the hybrid cloud could be defined as the combination of
the both private and the public cloud. The hybrid cloud is majorly the effective combination
of the private and the public cloud that is bound together by the either standardised or the
proprietary technology that helps in enabling the portability of the application and the data
(Bera, Misra & Rodrigues, 2014). It could be the combination of the private cloud within the
organisation with more than one providers of the public cloud or the private cloud that is
hosted on any premises of the third party with more than one providers of the public cloud. It
has been observed that the services of the public cloud fails to meet the IT and the
requirements of the business of some business organisations (Mastelic et al., 2015). Any
environment of the hybrid cloud could help in meeting the requirements. In several methods,
the hybrid cloud could be considered as the intermediate stage as the enterprises prepares to
shift majority of the workloads to the public clouds. The public clouds is growing to be
increasingly popular in recent years. Deprived of the maintaining of any data centre, public
cloud majorly allows the almost instant provision of the resource and the quick scaling. The
Amazon EC2 that is the product of the Amazon has increasingly contributed to development
of the public cloud and it has been considered among the first solution of the public cloud
(Lian, Yen & Wang, 2014). Moreover, not solely the growth of the cloud community is
happening but number of the critiques is significantly increasing. Specifically, not solely in
the terms of the data privacy and the security but it is considered in the other topics like the
vendor lock-in, the availability, and the interoperability and the public cloud carries the

15
CLOUD COMPUTING SOLUTION FOR DTGOV
inherent risks. Although the hybrid clouds covers the significant value proposition and it also
enables the several opportunities, it comprises of the significant challenges and the issues that
are required to be considered and the proper mitigation plans are required to be implemented
(Boru et al., 2015). Especially because of the prevailing evolving nature, there are challenges
of the hybrid cloud strategy, which are:
Cost: This challenge is the major risks that has to be considered for the proper
implementation of the cloud strategy in the organisation as the infrastructure of the hybrid
cloud needs both the local data centre as well as the extra remote resources from the service
provider of the cloud (Khalil, Khreishah & Azeem, 2014). This is often the most mentioned
benefit of the cloud computing which the independence of the data center do not hold
significantly true for the hybrid environments (Chang, Kuo & Ramachandran, 2016).
Factually, the infrastructure of the hybrid cloud are required to factor for the setup as well as
the cost of operation for any data center as the costs that are based on the usage and these are
implemented by cloud provider. Relying on the utilisation, the cost of the data centre and
major cost of cloud service provider, the businesses are required to make the important
decision of moving or not moving to cloud could profitable (Zhan et al., 2015).
Costs of cooling, power and the physical plant: This cost is significantly based on the
nature of the cloud and the data centre that has been implemented in the private location and
it factors majorly in costs for the power, the expenses of the plant and the cooling (Jiang et
al., 2014).
Operation costs: The cloud environments comprises of the lower costs of the
hardware operations due to the fact that the virtualisation has been done for the data centres
and there are significant risks of the outage that could be moved to the external providers (Li
et al., 2018). The major operations costs associated with the software management, moreover,
CLOUD COMPUTING SOLUTION FOR DTGOV
inherent risks. Although the hybrid clouds covers the significant value proposition and it also
enables the several opportunities, it comprises of the significant challenges and the issues that
are required to be considered and the proper mitigation plans are required to be implemented
(Boru et al., 2015). Especially because of the prevailing evolving nature, there are challenges
of the hybrid cloud strategy, which are:
Cost: This challenge is the major risks that has to be considered for the proper
implementation of the cloud strategy in the organisation as the infrastructure of the hybrid
cloud needs both the local data centre as well as the extra remote resources from the service
provider of the cloud (Khalil, Khreishah & Azeem, 2014). This is often the most mentioned
benefit of the cloud computing which the independence of the data center do not hold
significantly true for the hybrid environments (Chang, Kuo & Ramachandran, 2016).
Factually, the infrastructure of the hybrid cloud are required to factor for the setup as well as
the cost of operation for any data center as the costs that are based on the usage and these are
implemented by cloud provider. Relying on the utilisation, the cost of the data centre and
major cost of cloud service provider, the businesses are required to make the important
decision of moving or not moving to cloud could profitable (Zhan et al., 2015).
Costs of cooling, power and the physical plant: This cost is significantly based on the
nature of the cloud and the data centre that has been implemented in the private location and
it factors majorly in costs for the power, the expenses of the plant and the cooling (Jiang et
al., 2014).
Operation costs: The cloud environments comprises of the lower costs of the
hardware operations due to the fact that the virtualisation has been done for the data centres
and there are significant risks of the outage that could be moved to the external providers (Li
et al., 2018). The major operations costs associated with the software management, moreover,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16
CLOUD COMPUTING SOLUTION FOR DTGOV
prevails similar in the IaaS environments and it decreases with the increase within abstraction
level.
Some of the other challenges includes the lack of the encryption, inadequate security
risk assessment, the poor compliance, the weak management of the security, the depleted data
redundancy, the failure of the identification and the authentication, the unprotected APIs and
the insufficient protection provided to the IP. Without the proper implementation of the
encryption, the significant transmission of the data from the network are easily susceptible to
the data theft or the compromising the integrity of the data. Without the proper
implementation of the risks assessment in the organisation, the detection and the
determination of any type of intrusion could not be accomplished deprived of the proper risk
management. If the organisation has not implemented the proper compliance, it denotes that
there might be some kind of parameters of the compliance among the provider of the public
cloud and the private cloud. The hybrid cloud and the enterprise could be significantly at risk
if in any situation, there has been the lack of the redundancy. These issues in the security of
the organisation arises in the situation when there might be no duplicate copies of the data in
any other data centres.
Information security steps and the controls
As the company is intending to deploy the IaaS instance of the AWS, it is vital to
execute the extensive analysis of the security issues in AWS workspace. It could be observed
that the major issue of the AWS workspace is the data breaches and this issue is the growing
concern for organisation who could implemented the cloud in the companies. The
recommended steps and the controls that are required to be included in the business are:
Encryption: As majority of the data could be transmitted to the users using the
internet, there is the major requirement of encrypting all the data that has to be sent over the
CLOUD COMPUTING SOLUTION FOR DTGOV
prevails similar in the IaaS environments and it decreases with the increase within abstraction
level.
Some of the other challenges includes the lack of the encryption, inadequate security
risk assessment, the poor compliance, the weak management of the security, the depleted data
redundancy, the failure of the identification and the authentication, the unprotected APIs and
the insufficient protection provided to the IP. Without the proper implementation of the
encryption, the significant transmission of the data from the network are easily susceptible to
the data theft or the compromising the integrity of the data. Without the proper
implementation of the risks assessment in the organisation, the detection and the
determination of any type of intrusion could not be accomplished deprived of the proper risk
management. If the organisation has not implemented the proper compliance, it denotes that
there might be some kind of parameters of the compliance among the provider of the public
cloud and the private cloud. The hybrid cloud and the enterprise could be significantly at risk
if in any situation, there has been the lack of the redundancy. These issues in the security of
the organisation arises in the situation when there might be no duplicate copies of the data in
any other data centres.
Information security steps and the controls
As the company is intending to deploy the IaaS instance of the AWS, it is vital to
execute the extensive analysis of the security issues in AWS workspace. It could be observed
that the major issue of the AWS workspace is the data breaches and this issue is the growing
concern for organisation who could implemented the cloud in the companies. The
recommended steps and the controls that are required to be included in the business are:
Encryption: As majority of the data could be transmitted to the users using the
internet, there is the major requirement of encrypting all the data that has to be sent over the

17
CLOUD COMPUTING SOLUTION FOR DTGOV
internet. The security policy for practising the implementation of the encryption is
significantly important for the organisation.
Identification of the reliable services: moreover, it has been discovered that the
authentication protocol could be considered as the approach for the identity, it is majorly
required by the organisation to implement the proper security steps and the controls for the
proper ensuring that the services that are taken from the service providers are maintaining the
data privacy.
Secure login functions: There is the major requirement of the utilisation of the strong
password and the credentials for gaining the effective prevention from any type of the
unauthorised access of all the desktops by any user where the valuable and sensitive
information of the organisation has been stored.
Besides these threats, there are some security threats that could impact significantly
on the business functions of the organisation like the issues that the S3 bucket provides the
permission that could be considered as significantly overly permissive. The configuration of
the cloudtrail has not been done properly and this raises the issues of loss of the knowledge
regarding the places from where the cloud data has been accessed. The unintentionally public
AMIs comprises of all the information that is required for the effective launching of the
instance of Amazon Ec2. When the AMIs are created by the user, these users are provided
with the option of making the EMI completely public, share this with the particular AWS
accounts or for making this instance public. The public AMIs could be launched by all the
AWS accounts and it also could be shared within the AMI catalog.
The strong credentials in the cloud storage could help in securing the access inside the
cloud storage of the organisation. The proper implementation of the firewall in the server of
the cloud storage could also help in the effective monitoring of the users who are presently
CLOUD COMPUTING SOLUTION FOR DTGOV
internet. The security policy for practising the implementation of the encryption is
significantly important for the organisation.
Identification of the reliable services: moreover, it has been discovered that the
authentication protocol could be considered as the approach for the identity, it is majorly
required by the organisation to implement the proper security steps and the controls for the
proper ensuring that the services that are taken from the service providers are maintaining the
data privacy.
Secure login functions: There is the major requirement of the utilisation of the strong
password and the credentials for gaining the effective prevention from any type of the
unauthorised access of all the desktops by any user where the valuable and sensitive
information of the organisation has been stored.
Besides these threats, there are some security threats that could impact significantly
on the business functions of the organisation like the issues that the S3 bucket provides the
permission that could be considered as significantly overly permissive. The configuration of
the cloudtrail has not been done properly and this raises the issues of loss of the knowledge
regarding the places from where the cloud data has been accessed. The unintentionally public
AMIs comprises of all the information that is required for the effective launching of the
instance of Amazon Ec2. When the AMIs are created by the user, these users are provided
with the option of making the EMI completely public, share this with the particular AWS
accounts or for making this instance public. The public AMIs could be launched by all the
AWS accounts and it also could be shared within the AMI catalog.
The strong credentials in the cloud storage could help in securing the access inside the
cloud storage of the organisation. The proper implementation of the firewall in the server of
the cloud storage could also help in the effective monitoring of the users who are presently

18
CLOUD COMPUTING SOLUTION FOR DTGOV
accessing the cloud or the users who are requesting the access inside the cloud. The board of
the company could be recommended to deploy the security policies for the effective
prevention of the unauthorised access within the cloud environment. The policies that are
defined earlier could be significantly distinct credentials that is provided to all the users of the
cloud and the users who require the access in the cloud storage. The main reason why this
controls are being recommended to be implemented in the cloud storage by the providers is
because these particular controls could help in the controlling of the access by the users in the
cloud who are constantly obtaining the data as well as making the effective addition in the
cloud storage. The data that is being received and then transmitted are required to be analysed
for any kind of malware and the security threats that might lead to the compromising of the
data. The majority of the access that is done by any user could be significantly restricted on
any of the resources as well as on the application from workspaces of users. The
implementation of the particular policies are required to be considered for the proper
allowing of the particular users with the major permission of the creation and the
management of the resources for the EC2 as well as the workspaces. The IAM or the Identity
and the Access Management allows the users of the AWS to execute the controlling of the
access to the account by the creation, the management of the permissions of the various users
of AWS.
Recommends that are to be included
Backup and disaster recovery
The applications of the organisation that have been hosted into the cloud of the
service provider comprises of the distinct necessity of the capability of the recovery of the
data during the situation of any disaster and it is required to be extensively connected with
majority of the purposes of the requirement linked with the location of the cloud storage
geographically, the recovery points along with the time for the effective recovery, which
CLOUD COMPUTING SOLUTION FOR DTGOV
accessing the cloud or the users who are requesting the access inside the cloud. The board of
the company could be recommended to deploy the security policies for the effective
prevention of the unauthorised access within the cloud environment. The policies that are
defined earlier could be significantly distinct credentials that is provided to all the users of the
cloud and the users who require the access in the cloud storage. The main reason why this
controls are being recommended to be implemented in the cloud storage by the providers is
because these particular controls could help in the controlling of the access by the users in the
cloud who are constantly obtaining the data as well as making the effective addition in the
cloud storage. The data that is being received and then transmitted are required to be analysed
for any kind of malware and the security threats that might lead to the compromising of the
data. The majority of the access that is done by any user could be significantly restricted on
any of the resources as well as on the application from workspaces of users. The
implementation of the particular policies are required to be considered for the proper
allowing of the particular users with the major permission of the creation and the
management of the resources for the EC2 as well as the workspaces. The IAM or the Identity
and the Access Management allows the users of the AWS to execute the controlling of the
access to the account by the creation, the management of the permissions of the various users
of AWS.
Recommends that are to be included
Backup and disaster recovery
The applications of the organisation that have been hosted into the cloud of the
service provider comprises of the distinct necessity of the capability of the recovery of the
data during the situation of any disaster and it is required to be extensively connected with
majority of the purposes of the requirement linked with the location of the cloud storage
geographically, the recovery points along with the time for the effective recovery, which
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19
CLOUD COMPUTING SOLUTION FOR DTGOV
performs the effective checking of the physical proximity of the sites of the disaster recovery.
Any effective strategy of disaster recovery mainly includes the type of the DR, which is
required to be included for the confirming of the application restoring during the situation of
any disaster. Any effective strategy is required to comprise of the DR that would comprise
the capability of the recovery region wise, the regional duplication, proper management of
the incoming traffic or the load balancing along with the proper maintenance of the
applications that are hosted in the cloud. The methods along with the properties of the AWS
that are required to be included within the BCP for the effective implementation of the
efficient DR strategy includes:
o Proper utilisation of the Amazon Route R3 for handling the situation of the regional
failover that might be based on the DNS.
o Reserved instances of the Amazon EC2 could help in the reserving the major capacity of
the DR in any remote location.
o Proper utilisation of the Amazon glacier for effective data archiving.
o Exploitation of the database of the shipping log for the influencing of the technologies of
the asynchronous data redundancy.
o Proper utilisation of the AMI or the Amazon Machine Image and the EBS snapshot copy
all through the various regions.
o Execute the additional instances, the AMI or the Amazon Machine Images or archive the
data in areas of the multiple AWS.
o Undertaking of effective third party tools as well as the periodic snapshots of the Amazon
EBS could be used for the restoring quickly from any data loss.
CLOUD COMPUTING SOLUTION FOR DTGOV
performs the effective checking of the physical proximity of the sites of the disaster recovery.
Any effective strategy of disaster recovery mainly includes the type of the DR, which is
required to be included for the confirming of the application restoring during the situation of
any disaster. Any effective strategy is required to comprise of the DR that would comprise
the capability of the recovery region wise, the regional duplication, proper management of
the incoming traffic or the load balancing along with the proper maintenance of the
applications that are hosted in the cloud. The methods along with the properties of the AWS
that are required to be included within the BCP for the effective implementation of the
efficient DR strategy includes:
o Proper utilisation of the Amazon Route R3 for handling the situation of the regional
failover that might be based on the DNS.
o Reserved instances of the Amazon EC2 could help in the reserving the major capacity of
the DR in any remote location.
o Proper utilisation of the Amazon glacier for effective data archiving.
o Exploitation of the database of the shipping log for the influencing of the technologies of
the asynchronous data redundancy.
o Proper utilisation of the AMI or the Amazon Machine Image and the EBS snapshot copy
all through the various regions.
o Execute the additional instances, the AMI or the Amazon Machine Images or archive the
data in areas of the multiple AWS.
o Undertaking of effective third party tools as well as the periodic snapshots of the Amazon
EBS could be used for the restoring quickly from any data loss.

20
CLOUD COMPUTING SOLUTION FOR DTGOV
Application resilience
The implementation of the hybrid cloud is significantly important for the company for
the various reasons. The major advantages that could be gained by the business are the
business reinforcement, the resilience and the disaster recovery. The main reason for the
offering the benefits is the agreement of the spanning all through the remote storage as well
as locally. This enabling of the alternatives have been offered by the practice of the storing all
data in the cloud. The main reason for this is the unprotected cloud could be utilised
extensively for major intention of the backup. Each of the application preserves the
distinctive features and the necessities of the High Availability or the HA. The AWS offers
the various building blocks infrastructural for assisting that organisation for the requirement
fulfilling in the techniques, which are significantly cost efficient. Analysis for the increased
availability, which could executed for the confirming of the applications recovery as there is
the increase in the needs and not solely the recovery of the component that could be included
within the effective HA strategy. As per the checklist of the Morad and Dalbhanjan, some of
the recommends that are to be included in the BCP of the organisation are:
o Instinctive scaling for executing the scaling recovery or the spontaneous instances
o AWS elastic beanstalk could be exploited to execute the scaling of the various situations
of management
o Flexible IP addresses for the IP addresses that could be significantly statics and it could
be remapped within the various occurences
o The use of the Amazon DynamoDB could be done for the effective loading of the couples
of the key/value
CLOUD COMPUTING SOLUTION FOR DTGOV
Application resilience
The implementation of the hybrid cloud is significantly important for the company for
the various reasons. The major advantages that could be gained by the business are the
business reinforcement, the resilience and the disaster recovery. The main reason for the
offering the benefits is the agreement of the spanning all through the remote storage as well
as locally. This enabling of the alternatives have been offered by the practice of the storing all
data in the cloud. The main reason for this is the unprotected cloud could be utilised
extensively for major intention of the backup. Each of the application preserves the
distinctive features and the necessities of the High Availability or the HA. The AWS offers
the various building blocks infrastructural for assisting that organisation for the requirement
fulfilling in the techniques, which are significantly cost efficient. Analysis for the increased
availability, which could executed for the confirming of the applications recovery as there is
the increase in the needs and not solely the recovery of the component that could be included
within the effective HA strategy. As per the checklist of the Morad and Dalbhanjan, some of
the recommends that are to be included in the BCP of the organisation are:
o Instinctive scaling for executing the scaling recovery or the spontaneous instances
o AWS elastic beanstalk could be exploited to execute the scaling of the various situations
of management
o Flexible IP addresses for the IP addresses that could be significantly statics and it could
be remapped within the various occurences
o The use of the Amazon DynamoDB could be done for the effective loading of the couples
of the key/value

21
CLOUD COMPUTING SOLUTION FOR DTGOV
Operations checklist
The effective deployment of all acute components of applications within the zones
of the various availability, among those who are appropriately duplicating the data
across the zones, as well as it is tested for determining how any failure across the
components might affect major availability of the application.
Dynamic IP addressing of the AWS has been understood and it is significantly
ensured for allowing the effective operation of the application when any
component of application have been restarted
The significant comprehension of how any failover would occur using the
components that are deployed of the application in several zones of the
availability and these are utilising the Elastic Load Balancing or the third party as
well as elastic IP addresses wherever it is appropriate
The significant gaining of knowledge regarding the instances of the Amazon EBS
that could be supported versus all the instances that could be store backed has
been done and most appropriate storage kind has been chosen with the proper
analysis and gain the major understanding of results of the data determination,
backup and the recovery.
Prior the effective sharing of all the images of the Amazon Machine with any
other instances, removal of the confidential and the sensitive information which
includes all the embedded public/private key of the instances has been done and
then reviewing of all files has been done for the SSH authorised keys has been
done
Utilisation of CNAME records could be executed for the effective mapping of the
DNS name of Elastic load balancing or buckets of the Amazon S3.
CLOUD COMPUTING SOLUTION FOR DTGOV
Operations checklist
The effective deployment of all acute components of applications within the zones
of the various availability, among those who are appropriately duplicating the data
across the zones, as well as it is tested for determining how any failure across the
components might affect major availability of the application.
Dynamic IP addressing of the AWS has been understood and it is significantly
ensured for allowing the effective operation of the application when any
component of application have been restarted
The significant comprehension of how any failover would occur using the
components that are deployed of the application in several zones of the
availability and these are utilising the Elastic Load Balancing or the third party as
well as elastic IP addresses wherever it is appropriate
The significant gaining of knowledge regarding the instances of the Amazon EBS
that could be supported versus all the instances that could be store backed has
been done and most appropriate storage kind has been chosen with the proper
analysis and gain the major understanding of results of the data determination,
backup and the recovery.
Prior the effective sharing of all the images of the Amazon Machine with any
other instances, removal of the confidential and the sensitive information which
includes all the embedded public/private key of the instances has been done and
then reviewing of all files has been done for the SSH authorised keys has been
done
Utilisation of CNAME records could be executed for the effective mapping of the
DNS name of Elastic load balancing or buckets of the Amazon S3.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22
CLOUD COMPUTING SOLUTION FOR DTGOV
Conclusion
Therefore, it could be concluded that the DTGOV could gain significantly from the
implementation of the cloud computing in the organisation. The dynamic allocation allows
the variable utilisation as it has been dictated by the demand fluctuations of the usage as the
unnecessary IT resources could be effectively reclaimed deprived of any requiring manual
interaction. The listener of the automated scaling has been configured with the workload
thresholds that perform the dictation when the new IT resources are required to be added to
all the workload processing. The resource pooling architecture has been observed as based on
the pooling of the identical IT resources into the groups. The pools could be physical and the
virtual resources. These particular identical resources could be automatically grouped and it
could be maintained by any system that ensures that there is the constant synchronisation.
The physical server pools that comprises of the networked servers that have the operating
system and the other needed applications that are installed and are prepared for the immediate
use. The virtual server pools are commonly configured from the templates that are pre-chosen
by any customer when it has been provisioned. The customer satisfaction is significantly
important for the distribution of the workload within the various nodes. The scheduling of the
load balanced demands the number of the challenging issues because of the heterogeneous
and the dynamic cloud nature. Moreover, some of the merits in the cloud computing like the
flexibility, the cost and the accessibility but the merits drives the needed for the cloud
services. The major challenges in this kind of the service load balancing architecture are the
security issues, the legal and the compliant issues, the QoS, interoperability issues and the
performance, the load balancing and the issues of the data management. The Amazon EC2
that is the product of the Amazon has increasingly contributed to development of the public
cloud and it has been considered among the first solution of the public cloud.
CLOUD COMPUTING SOLUTION FOR DTGOV
Conclusion
Therefore, it could be concluded that the DTGOV could gain significantly from the
implementation of the cloud computing in the organisation. The dynamic allocation allows
the variable utilisation as it has been dictated by the demand fluctuations of the usage as the
unnecessary IT resources could be effectively reclaimed deprived of any requiring manual
interaction. The listener of the automated scaling has been configured with the workload
thresholds that perform the dictation when the new IT resources are required to be added to
all the workload processing. The resource pooling architecture has been observed as based on
the pooling of the identical IT resources into the groups. The pools could be physical and the
virtual resources. These particular identical resources could be automatically grouped and it
could be maintained by any system that ensures that there is the constant synchronisation.
The physical server pools that comprises of the networked servers that have the operating
system and the other needed applications that are installed and are prepared for the immediate
use. The virtual server pools are commonly configured from the templates that are pre-chosen
by any customer when it has been provisioned. The customer satisfaction is significantly
important for the distribution of the workload within the various nodes. The scheduling of the
load balanced demands the number of the challenging issues because of the heterogeneous
and the dynamic cloud nature. Moreover, some of the merits in the cloud computing like the
flexibility, the cost and the accessibility but the merits drives the needed for the cloud
services. The major challenges in this kind of the service load balancing architecture are the
security issues, the legal and the compliant issues, the QoS, interoperability issues and the
performance, the load balancing and the issues of the data management. The Amazon EC2
that is the product of the Amazon has increasingly contributed to development of the public
cloud and it has been considered among the first solution of the public cloud.

23
CLOUD COMPUTING SOLUTION FOR DTGOV
CLOUD COMPUTING SOLUTION FOR DTGOV

24
CLOUD COMPUTING SOLUTION FOR DTGOV
References
Aazam, M., & Huh, E. N. (2014, August). Fog computing and smart gateway based
communication for cloud of things. In 2014 International Conference on Future
Internet of Things and Cloud (pp. 464-470). IEEE.
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Avram, M. G. (2014). Advantages and challenges of adopting cloud computing from an
enterprise perspective. Procedia Technology, 12, 529-534.
Barbarossa, S., Sardellitti, S., & Di Lorenzo, P. (2014). Communicating while computing:
Distributed mobile cloud computing over 5G heterogeneous networks. IEEE Signal
Processing Magazine, 31(6), 45-55.
Bera, S., Misra, S., & Rodrigues, J. J. (2014). Cloud computing applications for smart grid: A
survey. IEEE Transactions on Parallel and Distributed Systems, 26(5), 1477-1494.
Boru, D., Kliazovich, D., Granelli, F., Bouvry, P., & Zomaya, A. Y. (2015). Energy-efficient
data replication in cloud computing datacenters. Cluster computing, 18(1), 385-402.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2014, August). On the integration of
cloud computing and internet of things. In 2014 International Conference on Future
Internet of Things and Cloud (pp. 23-30). IEEE.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing
and internet of things: a survey. Future generation computer systems, 56, 684-700.
CLOUD COMPUTING SOLUTION FOR DTGOV
References
Aazam, M., & Huh, E. N. (2014, August). Fog computing and smart gateway based
communication for cloud of things. In 2014 International Conference on Future
Internet of Things and Cloud (pp. 464-470). IEEE.
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Avram, M. G. (2014). Advantages and challenges of adopting cloud computing from an
enterprise perspective. Procedia Technology, 12, 529-534.
Barbarossa, S., Sardellitti, S., & Di Lorenzo, P. (2014). Communicating while computing:
Distributed mobile cloud computing over 5G heterogeneous networks. IEEE Signal
Processing Magazine, 31(6), 45-55.
Bera, S., Misra, S., & Rodrigues, J. J. (2014). Cloud computing applications for smart grid: A
survey. IEEE Transactions on Parallel and Distributed Systems, 26(5), 1477-1494.
Boru, D., Kliazovich, D., Granelli, F., Bouvry, P., & Zomaya, A. Y. (2015). Energy-efficient
data replication in cloud computing datacenters. Cluster computing, 18(1), 385-402.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2014, August). On the integration of
cloud computing and internet of things. In 2014 International Conference on Future
Internet of Things and Cloud (pp. 23-30). IEEE.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing
and internet of things: a survey. Future generation computer systems, 56, 684-700.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25
CLOUD COMPUTING SOLUTION FOR DTGOV
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41.
Chen, X. (2014). Decentralized computation offloading game for mobile cloud
computing. IEEE Transactions on Parallel and Distributed Systems, 26(4), 974-983.
Chen, X., Jiao, L., Li, W., & Fu, X. (2015). Efficient multi-user computation offloading for
mobile-edge cloud computing. IEEE/ACM Transactions on Networking, 24(5), 2795-
2808.
Etro, F. (2015). The economics of cloud computing. In Cloud Technology: Concepts,
Methodologies, Tools, and Applications (pp. 2135-2148). IGI Global.
Fehling, C., Leymann, F., Retter, R., Schupeck, W., & Arbitter, P. (2014). Cloud computing
patterns: fundamentals to design, build, and manage cloud applications. Springer
Science & Business Media.
Gai, K., Qiu, M., Zhao, H., Tao, L., & Zong, Z. (2016). Dynamic energy-aware cloudlet-
based mobile cloud computing model for green computing. Journal of Network and
Computer Applications, 59, 46-54.
Gangwar, H., Date, H., & Ramaswamy, R. (2015). Understanding determinants of cloud
computing adoption using an integrated TAM-TOE model. Journal of Enterprise
Information Management, 28(1), 107-130.
Hashem, I. A. T., Yaqoob, I., Anuar, N. B., Mokhtar, S., Gani, A., & Khan, S. U. (2015). The
rise of “big data” on cloud computing: Review and open research issues. Information
systems, 47, 98-115.
CLOUD COMPUTING SOLUTION FOR DTGOV
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41.
Chen, X. (2014). Decentralized computation offloading game for mobile cloud
computing. IEEE Transactions on Parallel and Distributed Systems, 26(4), 974-983.
Chen, X., Jiao, L., Li, W., & Fu, X. (2015). Efficient multi-user computation offloading for
mobile-edge cloud computing. IEEE/ACM Transactions on Networking, 24(5), 2795-
2808.
Etro, F. (2015). The economics of cloud computing. In Cloud Technology: Concepts,
Methodologies, Tools, and Applications (pp. 2135-2148). IGI Global.
Fehling, C., Leymann, F., Retter, R., Schupeck, W., & Arbitter, P. (2014). Cloud computing
patterns: fundamentals to design, build, and manage cloud applications. Springer
Science & Business Media.
Gai, K., Qiu, M., Zhao, H., Tao, L., & Zong, Z. (2016). Dynamic energy-aware cloudlet-
based mobile cloud computing model for green computing. Journal of Network and
Computer Applications, 59, 46-54.
Gangwar, H., Date, H., & Ramaswamy, R. (2015). Understanding determinants of cloud
computing adoption using an integrated TAM-TOE model. Journal of Enterprise
Information Management, 28(1), 107-130.
Hashem, I. A. T., Yaqoob, I., Anuar, N. B., Mokhtar, S., Gani, A., & Khan, S. U. (2015). The
rise of “big data” on cloud computing: Review and open research issues. Information
systems, 47, 98-115.

26
CLOUD COMPUTING SOLUTION FOR DTGOV
Hsu, P. F., Ray, S., & Li-Hsieh, Y. Y. (2014). Examining cloud computing adoption
intention, pricing mechanism, and deployment model. International Journal of
Information Management, 34(4), 474-488.
Jiang, L., Da Xu, L., Cai, H., Jiang, Z., Bu, F., & Xu, B. (2014). An IoT-oriented data storage
framework in cloud computing platform. IEEE Transactions on Industrial
Informatics, 10(2), 1443-1451.
Jula, A., Sundararajan, E., & Othman, Z. (2014). Cloud computing service composition: A
systematic literature review. Expert systems with applications, 41(8), 3809-3824.
Khalil, I., Khreishah, A., & Azeem, M. (2014). Cloud computing security: A
survey. Computers, 3(1), 1-35.
Li, J., Li, J., Chen, X., Jia, C., & Lou, W. (2015). Identity-based encryption with outsourced
revocation in cloud computing. Ieee Transactions on computers, 64(2), 425-437.
Li, P., Li, J., Huang, Z., Gao, C. Z., Chen, W. B., & Chen, K. (2018). Privacy-preserving
outsourced classification in cloud computing. Cluster Computing, 21(1), 277-286.
Lian, J. W., Yen, D. C., & Wang, Y. T. (2014). An exploratory study to understand the
critical factors affecting the decision to adopt cloud computing in Taiwan
hospital. International Journal of Information Management, 34(1), 28-36.
Manvi, S. S., & Shyam, G. K. (2014). Resource management for Infrastructure as a Service
(IaaS) in cloud computing: A survey. Journal of network and computer
applications, 41, 424-440.
Marinescu, D. C. (2017). Cloud computing: theory and practice. Morgan Kaufmann.
CLOUD COMPUTING SOLUTION FOR DTGOV
Hsu, P. F., Ray, S., & Li-Hsieh, Y. Y. (2014). Examining cloud computing adoption
intention, pricing mechanism, and deployment model. International Journal of
Information Management, 34(4), 474-488.
Jiang, L., Da Xu, L., Cai, H., Jiang, Z., Bu, F., & Xu, B. (2014). An IoT-oriented data storage
framework in cloud computing platform. IEEE Transactions on Industrial
Informatics, 10(2), 1443-1451.
Jula, A., Sundararajan, E., & Othman, Z. (2014). Cloud computing service composition: A
systematic literature review. Expert systems with applications, 41(8), 3809-3824.
Khalil, I., Khreishah, A., & Azeem, M. (2014). Cloud computing security: A
survey. Computers, 3(1), 1-35.
Li, J., Li, J., Chen, X., Jia, C., & Lou, W. (2015). Identity-based encryption with outsourced
revocation in cloud computing. Ieee Transactions on computers, 64(2), 425-437.
Li, P., Li, J., Huang, Z., Gao, C. Z., Chen, W. B., & Chen, K. (2018). Privacy-preserving
outsourced classification in cloud computing. Cluster Computing, 21(1), 277-286.
Lian, J. W., Yen, D. C., & Wang, Y. T. (2014). An exploratory study to understand the
critical factors affecting the decision to adopt cloud computing in Taiwan
hospital. International Journal of Information Management, 34(1), 28-36.
Manvi, S. S., & Shyam, G. K. (2014). Resource management for Infrastructure as a Service
(IaaS) in cloud computing: A survey. Journal of network and computer
applications, 41, 424-440.
Marinescu, D. C. (2017). Cloud computing: theory and practice. Morgan Kaufmann.

27
CLOUD COMPUTING SOLUTION FOR DTGOV
Mastelic, T., Oleksiak, A., Claussen, H., Brandic, I., Pierson, J. M., & Vasilakos, A. V.
(2015). Cloud computing: Survey on energy efficiency. Acm computing surveys
(csur), 47(2), 33.
Oliveira, T., Thomas, M., & Espadanal, M. (2014). Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and services
sectors. Information & Management, 51(5), 497-510.
Rahimi, M. R., Ren, J., Liu, C. H., Vasilakos, A. V., & Venkatasubramanian, N. (2014).
Mobile cloud computing: A survey, state of art and future directions. Mobile
Networks and Applications, 19(2), 133-143.
Rittinghouse, J. W., & Ransome, J. F. (2016). Cloud computing: implementation,
management, and security. CRC press.
Sadiku, M. N., Musa, S. M., & Momoh, O. D. (2014). Cloud computing: opportunities and
challenges. IEEE potentials, 33(1), 34-36.
Sen, J. (2015). Security and privacy issues in cloud computing. In Cloud Technology:
Concepts, Methodologies, Tools, and Applications (pp. 1585-1630). IGI Global.
Stergiou, C., Psannis, K. E., Kim, B. G., & Gupta, B. (2018). Secure integration of IoT and
cloud computing. Future Generation Computer Systems, 78, 964-975.
Tao, F., Cheng, Y., Da Xu, L., Zhang, L., & Li, B. H. (2014). CCIoT-CMfg: cloud computing
and internet of things-based cloud manufacturing service system. IEEE Transactions
on Industrial Informatics, 10(2), 1435-1442.
Toosi, A. N., Calheiros, R. N., & Buyya, R. (2014). Interconnected cloud computing
environments: Challenges, taxonomy, and survey. ACM Computing Surveys
(CSUR), 47(1), 7.
CLOUD COMPUTING SOLUTION FOR DTGOV
Mastelic, T., Oleksiak, A., Claussen, H., Brandic, I., Pierson, J. M., & Vasilakos, A. V.
(2015). Cloud computing: Survey on energy efficiency. Acm computing surveys
(csur), 47(2), 33.
Oliveira, T., Thomas, M., & Espadanal, M. (2014). Assessing the determinants of cloud
computing adoption: An analysis of the manufacturing and services
sectors. Information & Management, 51(5), 497-510.
Rahimi, M. R., Ren, J., Liu, C. H., Vasilakos, A. V., & Venkatasubramanian, N. (2014).
Mobile cloud computing: A survey, state of art and future directions. Mobile
Networks and Applications, 19(2), 133-143.
Rittinghouse, J. W., & Ransome, J. F. (2016). Cloud computing: implementation,
management, and security. CRC press.
Sadiku, M. N., Musa, S. M., & Momoh, O. D. (2014). Cloud computing: opportunities and
challenges. IEEE potentials, 33(1), 34-36.
Sen, J. (2015). Security and privacy issues in cloud computing. In Cloud Technology:
Concepts, Methodologies, Tools, and Applications (pp. 1585-1630). IGI Global.
Stergiou, C., Psannis, K. E., Kim, B. G., & Gupta, B. (2018). Secure integration of IoT and
cloud computing. Future Generation Computer Systems, 78, 964-975.
Tao, F., Cheng, Y., Da Xu, L., Zhang, L., & Li, B. H. (2014). CCIoT-CMfg: cloud computing
and internet of things-based cloud manufacturing service system. IEEE Transactions
on Industrial Informatics, 10(2), 1435-1442.
Toosi, A. N., Calheiros, R. N., & Buyya, R. (2014). Interconnected cloud computing
environments: Challenges, taxonomy, and survey. ACM Computing Surveys
(CSUR), 47(1), 7.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

28
CLOUD COMPUTING SOLUTION FOR DTGOV
Wei, L., Zhu, H., Cao, Z., Dong, X., Jia, W., Chen, Y., & Vasilakos, A. V. (2014). Security
and privacy for storage and computation in cloud computing. Information
Sciences, 258, 371-386.
Whaiduzzaman, M., Sookhak, M., Gani, A., & Buyya, R. (2014). A survey on vehicular
cloud computing. Journal of Network and Computer applications, 40, 325-344.
Xia, Z., Wang, X., Zhang, L., Qin, Z., Sun, X., & Ren, K. (2016). A privacy-preserving and
copy-deterrence content-based image retrieval scheme in cloud computing. IEEE
Transactions on Information Forensics and Security, 11(11), 2594-2608.
Yannuzzi, M., Milito, R., Serral-Gracià, R., Montero, D., & Nemirovsky, M. (2014,
December). Key ingredients in an IoT recipe: Fog Computing, Cloud computing, and
more Fog Computing. In 2014 IEEE 19th International Workshop on Computer
Aided Modeling and Design of Communication Links and Networks (CAMAD) (pp.
325-329). IEEE.
Zhan, Z. H., Liu, X. F., Gong, Y. J., Zhang, J., Chung, H. S. H., & Li, Y. (2015). Cloud
computing resource scheduling and a survey of its evolutionary approaches. ACM
Computing Surveys (CSUR), 47(4), 63.
CLOUD COMPUTING SOLUTION FOR DTGOV
Wei, L., Zhu, H., Cao, Z., Dong, X., Jia, W., Chen, Y., & Vasilakos, A. V. (2014). Security
and privacy for storage and computation in cloud computing. Information
Sciences, 258, 371-386.
Whaiduzzaman, M., Sookhak, M., Gani, A., & Buyya, R. (2014). A survey on vehicular
cloud computing. Journal of Network and Computer applications, 40, 325-344.
Xia, Z., Wang, X., Zhang, L., Qin, Z., Sun, X., & Ren, K. (2016). A privacy-preserving and
copy-deterrence content-based image retrieval scheme in cloud computing. IEEE
Transactions on Information Forensics and Security, 11(11), 2594-2608.
Yannuzzi, M., Milito, R., Serral-Gracià, R., Montero, D., & Nemirovsky, M. (2014,
December). Key ingredients in an IoT recipe: Fog Computing, Cloud computing, and
more Fog Computing. In 2014 IEEE 19th International Workshop on Computer
Aided Modeling and Design of Communication Links and Networks (CAMAD) (pp.
325-329). IEEE.
Zhan, Z. H., Liu, X. F., Gong, Y. J., Zhang, J., Chung, H. S. H., & Li, Y. (2015). Cloud
computing resource scheduling and a survey of its evolutionary approaches. ACM
Computing Surveys (CSUR), 47(4), 63.
1 out of 29
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





