Cloud Computing Strategy for Regional Gardens Limited
VerifiedAdded on 2023/06/11
|18
|5931
|187
AI Summary
This paper determines the cloud computing strategy for the Regional Gardens limited, a gardening enterprise. This report addresses the integration of hybrid cloud computing into the current information technology and computing infrastructure. Cloud computing architectures such as software as a service and platform as a service are suggested in the report as the ideal architectures to enable the company meet their objectives. The report assesses the risks involved with the implementation and deployment of the hybrid cloud computing. Lastly, in the report, a strategic plan is laid to explain the migration of email services from the on premise facility to the cloud based server.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

CLOUD COMPUTING
NAME
COURSE
UNIVERSITY/AFFILIATION
NAME
COURSE
UNIVERSITY/AFFILIATION
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Abstract.
This paper determines the cloud computing strategy for the Regional Gardens limited,
a gardening enterprise. This report addresses the integration of hybrid cloud computing into
the current information technology and computing infrastructure. Cloud computing
architectures such as software as a service and platform as a service are suggested in the
report as the ideal architectures to enable the company meet their objectives, Armbrust et al
(2010). This report assesses the risks involved with the implementation and deployment of
the hybrid cloud computing. Using a risk assessment matrix, the risks are described and a
solution presented for each. Additionally, the report recommends the security and other issues
that must be included in the company’s BCP such as back-up and recovery and resilience.
Lastly, in the report, a strategic plan is laid to explain the migration of email services from
the on premise facility to the cloud based server.
Introduction.
The agricultural sector has really developed fats and largely over the past years. At
the centre of the development has been the ability to use technology in the agricultural
processes. Apart from use of farm machinery as the technology, communication technology
has been a pillar in the development. With the need to cut the cost of acquiring information
technology, staff, infrastructure and software, cloud computing has become an emerging and
very reliable technology, Armbrust et al (2010). Cloud computing is an online-based
environment that provides computational services to the clients such as servers, computing
and big data analytics, storage, applications and a platform for development. Through the
internet, the computer services provided cut the cost of ownership of acquiring on premise
technology and equipment.
The application of hybrid computing means that each provision, that is the Amazon
and the Bathurst data centre remain separate entities that are connected through proprietary
software and technology that allows portability and exchange of data and software interfaces.
The cloud computing provides different models or architectures of computing that provide
different services to the clients through their measured subscriptions. The models are
software as a service, platform as a service and infrastructure as a service. Through the SaaS
model, the client accesses and uses the software directly over the internet without installing
on to their computers. In the PaaS model, the cloud offers a computing platform that enables
This paper determines the cloud computing strategy for the Regional Gardens limited,
a gardening enterprise. This report addresses the integration of hybrid cloud computing into
the current information technology and computing infrastructure. Cloud computing
architectures such as software as a service and platform as a service are suggested in the
report as the ideal architectures to enable the company meet their objectives, Armbrust et al
(2010). This report assesses the risks involved with the implementation and deployment of
the hybrid cloud computing. Using a risk assessment matrix, the risks are described and a
solution presented for each. Additionally, the report recommends the security and other issues
that must be included in the company’s BCP such as back-up and recovery and resilience.
Lastly, in the report, a strategic plan is laid to explain the migration of email services from
the on premise facility to the cloud based server.
Introduction.
The agricultural sector has really developed fats and largely over the past years. At
the centre of the development has been the ability to use technology in the agricultural
processes. Apart from use of farm machinery as the technology, communication technology
has been a pillar in the development. With the need to cut the cost of acquiring information
technology, staff, infrastructure and software, cloud computing has become an emerging and
very reliable technology, Armbrust et al (2010). Cloud computing is an online-based
environment that provides computational services to the clients such as servers, computing
and big data analytics, storage, applications and a platform for development. Through the
internet, the computer services provided cut the cost of ownership of acquiring on premise
technology and equipment.
The application of hybrid computing means that each provision, that is the Amazon
and the Bathurst data centre remain separate entities that are connected through proprietary
software and technology that allows portability and exchange of data and software interfaces.
The cloud computing provides different models or architectures of computing that provide
different services to the clients through their measured subscriptions. The models are
software as a service, platform as a service and infrastructure as a service. Through the SaaS
model, the client accesses and uses the software directly over the internet without installing
on to their computers. In the PaaS model, the cloud offers a computing platform that enables

the development of applications with the different programming languages available such as
java and python. In the IaaS model and architecture, the cloud allows the client to access the
cloud resources and scale them up depending on the needs of the client and payment is made
in the pay-per-use design, Jamil & Zaki (2011).
Project development.
Cloud architectures.
The cloud architecture is the structural system composting of the components,
services and functions provided by the cloud service provider. The components are formed by
the front end of the cloud including interfaces for software functionality, the back end such as
storage, the network used to access the cloud and the delivery system.
In the strategy employed by the Regional Gardens Board, the following architectures are
suitable for the implementation of the project.
1. Software as a service.
In this cloud based service model, the Regional Gardens employees do not use installed
computer or mobile applications to perform functions of the company. Rather, the employees
access the services installed and running on the cloud via the internet and use the online
applications to perform the functions. The SaaS architecture is highly flexible and scalable,
Armbrust et al (2009). Unlike the past, where Regional Gardens would need to load their
applications on the cloud, currently the cloud provider allows the client to use the software
and applications without the need for any local installations. The cloud based software
allows the users to use the same application with the same code, same customization and
configuration and therefore the work output is enhanced in terms of quality and quantity. The
software service on the cloud allows the company to pay an annual fee for the use of the
cloud services. The software as a service architecture is set up in that the cloud-based service
provider deals with all the other issues such as maintenance and security of the software
platform.
A good structure of the proposed structure as a service model is the multitenant
architecture. In this design, the same application or software is accessed by the different
employees of the company from anywhere at any time on demand. This model supports
scalability since the same program can be installed or virtually run from different servers and
therefore allow different employees to run the same application at the same time, Armbrust et
java and python. In the IaaS model and architecture, the cloud allows the client to access the
cloud resources and scale them up depending on the needs of the client and payment is made
in the pay-per-use design, Jamil & Zaki (2011).
Project development.
Cloud architectures.
The cloud architecture is the structural system composting of the components,
services and functions provided by the cloud service provider. The components are formed by
the front end of the cloud including interfaces for software functionality, the back end such as
storage, the network used to access the cloud and the delivery system.
In the strategy employed by the Regional Gardens Board, the following architectures are
suitable for the implementation of the project.
1. Software as a service.
In this cloud based service model, the Regional Gardens employees do not use installed
computer or mobile applications to perform functions of the company. Rather, the employees
access the services installed and running on the cloud via the internet and use the online
applications to perform the functions. The SaaS architecture is highly flexible and scalable,
Armbrust et al (2009). Unlike the past, where Regional Gardens would need to load their
applications on the cloud, currently the cloud provider allows the client to use the software
and applications without the need for any local installations. The cloud based software
allows the users to use the same application with the same code, same customization and
configuration and therefore the work output is enhanced in terms of quality and quantity. The
software service on the cloud allows the company to pay an annual fee for the use of the
cloud services. The software as a service architecture is set up in that the cloud-based service
provider deals with all the other issues such as maintenance and security of the software
platform.
A good structure of the proposed structure as a service model is the multitenant
architecture. In this design, the same application or software is accessed by the different
employees of the company from anywhere at any time on demand. This model supports
scalability since the same program can be installed or virtually run from different servers and
therefore allow different employees to run the same application at the same time, Armbrust et

al (2009). Additionally, in this model, the company’s IT administrator can be allowed access
to the beta version of the application for testing before official upgrades.
The advantages therefor to the Regional Gardens company are:
Software as a service reduces the cost of ownership of the purchased and installed
software since the software is now accessed online through the internet without the need to
locally install the program. Instead of spending money on the purchase of the program, the
cloud based service provider provides the software to be accessed from the web browser
installed on the company’s computers. Additionally, the software as a service allows for the
payment of only the software the company is going to use. This eliminates the need for the
payment of un-used licenced third party programs, Wu, Garg, & Buyya, (2011, May).
Software as a service can be accessed anywhere at any time, very accessible. This feature
allows for the company to focus more on production from remote areas.
SaaS is highly flexible and scalable. Since the program is cloud hosted, it allows the
company to easily increase the usage of the software resources without being afraid of
exhausting or overrunning the limited on premise resource.
SaaS model reduces the responsibilities of the IT department to provide security and
maintenance of the system and therefore reduces the company’s expenditure on acquiring a
large IT human expertise since the cloud based service provider shoulders the responsibilities
of security, software upgrade and maintenance.
SaaS model offers a cross device compatibility since its accessed from the net. This
feature also confers additional advantages in that all the employees use the same code base to
perform the company’s functions and therefore the errors, bugs and system crashes of using
older versions of programs is eliminated.
2. Platform as a service.
This is a cloud based service that will allow Regional Gardens to develop and manage
their own applications and programs that suit the demands of the company, Armbrust et al
(2010). The services are provided from an online platform and server. Just like the software
as a service, the PaaS allows the employees access and use the online software however,
permission is granted to the company IT experts to manage and control the software aspects
of the service provided.
to the beta version of the application for testing before official upgrades.
The advantages therefor to the Regional Gardens company are:
Software as a service reduces the cost of ownership of the purchased and installed
software since the software is now accessed online through the internet without the need to
locally install the program. Instead of spending money on the purchase of the program, the
cloud based service provider provides the software to be accessed from the web browser
installed on the company’s computers. Additionally, the software as a service allows for the
payment of only the software the company is going to use. This eliminates the need for the
payment of un-used licenced third party programs, Wu, Garg, & Buyya, (2011, May).
Software as a service can be accessed anywhere at any time, very accessible. This feature
allows for the company to focus more on production from remote areas.
SaaS is highly flexible and scalable. Since the program is cloud hosted, it allows the
company to easily increase the usage of the software resources without being afraid of
exhausting or overrunning the limited on premise resource.
SaaS model reduces the responsibilities of the IT department to provide security and
maintenance of the system and therefore reduces the company’s expenditure on acquiring a
large IT human expertise since the cloud based service provider shoulders the responsibilities
of security, software upgrade and maintenance.
SaaS model offers a cross device compatibility since its accessed from the net. This
feature also confers additional advantages in that all the employees use the same code base to
perform the company’s functions and therefore the errors, bugs and system crashes of using
older versions of programs is eliminated.
2. Platform as a service.
This is a cloud based service that will allow Regional Gardens to develop and manage
their own applications and programs that suit the demands of the company, Armbrust et al
(2010). The services are provided from an online platform and server. Just like the software
as a service, the PaaS allows the employees access and use the online software however,
permission is granted to the company IT experts to manage and control the software aspects
of the service provided.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

The service provider provides the server with analytic capabilities, storage, operating
framework and system and programming languages such as java and python, Buyya et al
(2009). The server allows the developers owned by Regional Gardens to develop, run and test
their application online.
In the environment provided by the PaaS, the Regional Gardens IT department and
developers focus on the development, deployment of the applications and software while the
provider addresses the needs concerning runtime environment, OS, virtualization, servers and
database management including storage. The PaaS architecture offers service management
and control such as workflow, monitoring and discovery.
The hybrid PaaS, allowed the public service that is derived from the SaaS and the private
service running on the data centres at Bathurst to be merged and deployed as a single hosting
platform.
The platform as a service architecture offers the additional features that allow the
developers of the company to design other services that run on the PaaS such as
communications using video, voice and messages, mobile platforms service and open
platform for running and deployment of open source software such as android operating
system, Armbrust et al (2009).
The benefits that the PaaS architecture will offer to Regional Gardens company include:
The platform as a service will cut the cost of acquiring the necessary technology to
develop, run and deploy applications that would help drive the objectives of Regional
Gardens.
In the PaaS model, the speed at which the development and deployment of the
applications and software occurs is extremely fast, Krutz, & Vines (2010). This is so because
the cloud based service provider allows the company’s IT stuff and developers to focus solely
on the development.
In the hybrid environment, the PaaS supports both the cloud based services and the data
centre services at Bathurst. Through the homogenous work environment, the workflow is
highly enhanced through the clouds and thus allows for efficient and easy scaling. The hybrid
model also offers the Regional Gardens to have more control over their services such as
security, applications usage plans, advertisements, development and management, Cerullo,
& Cerullo (2014).
framework and system and programming languages such as java and python, Buyya et al
(2009). The server allows the developers owned by Regional Gardens to develop, run and test
their application online.
In the environment provided by the PaaS, the Regional Gardens IT department and
developers focus on the development, deployment of the applications and software while the
provider addresses the needs concerning runtime environment, OS, virtualization, servers and
database management including storage. The PaaS architecture offers service management
and control such as workflow, monitoring and discovery.
The hybrid PaaS, allowed the public service that is derived from the SaaS and the private
service running on the data centres at Bathurst to be merged and deployed as a single hosting
platform.
The platform as a service architecture offers the additional features that allow the
developers of the company to design other services that run on the PaaS such as
communications using video, voice and messages, mobile platforms service and open
platform for running and deployment of open source software such as android operating
system, Armbrust et al (2009).
The benefits that the PaaS architecture will offer to Regional Gardens company include:
The platform as a service will cut the cost of acquiring the necessary technology to
develop, run and deploy applications that would help drive the objectives of Regional
Gardens.
In the PaaS model, the speed at which the development and deployment of the
applications and software occurs is extremely fast, Krutz, & Vines (2010). This is so because
the cloud based service provider allows the company’s IT stuff and developers to focus solely
on the development.
In the hybrid environment, the PaaS supports both the cloud based services and the data
centre services at Bathurst. Through the homogenous work environment, the workflow is
highly enhanced through the clouds and thus allows for efficient and easy scaling. The hybrid
model also offers the Regional Gardens to have more control over their services such as
security, applications usage plans, advertisements, development and management, Cerullo,
& Cerullo (2014).

3. Infrastructure as a service.
In the IaaS model, the cloud based computing provider allows the Regional Gardens to
pay only for the services that would be utilized. Amazon web services provides the servers,
hardware, networking features, security, technical experts and storage services to the
company, Jamil & Zaki (2011). Regional Gardens won’t need to manage the cloud
infrastructure but rather use the services provided for data outsourcing. In this model, the
SaaS delivers the services that can be accessed from the internet while the PaaS grants the
company the tools and services to develop and deploy applications and allow communication
protocols, Jamil & Zaki (2011).
Benefits:
IaaS will only allow Regional Gardens limited to pay for the services and resources
required. The model also has an integrated function that allows all the other model be
integrated into the hybrid model of the architecture.
4. Resource pooling
This is an architecture which is based on the make and use of at least one resource
pools where two information technology resources are always organised and maintained
using the system which can automatically ensure that they endure synchronized. The pools
can be complex containing more than one pools which are made for a particular application.
Some of the common example of the resource pooling includes the following;
i. The Virtual server pool
ii. Physical server pool
iii. Storage pools
iv. Network pools
v. CPU pools
5. Bursting architecture
Cloud bursting is an application arrangement demonstrate in which an application
keeps running in a private cloud or server farm and blasts into an open cloud when the
interest for registering limit spikes. The benefit of such a crossover cloud arrangement is that
an association pays for additional register assets when they are required.
In the IaaS model, the cloud based computing provider allows the Regional Gardens to
pay only for the services that would be utilized. Amazon web services provides the servers,
hardware, networking features, security, technical experts and storage services to the
company, Jamil & Zaki (2011). Regional Gardens won’t need to manage the cloud
infrastructure but rather use the services provided for data outsourcing. In this model, the
SaaS delivers the services that can be accessed from the internet while the PaaS grants the
company the tools and services to develop and deploy applications and allow communication
protocols, Jamil & Zaki (2011).
Benefits:
IaaS will only allow Regional Gardens limited to pay for the services and resources
required. The model also has an integrated function that allows all the other model be
integrated into the hybrid model of the architecture.
4. Resource pooling
This is an architecture which is based on the make and use of at least one resource
pools where two information technology resources are always organised and maintained
using the system which can automatically ensure that they endure synchronized. The pools
can be complex containing more than one pools which are made for a particular application.
Some of the common example of the resource pooling includes the following;
i. The Virtual server pool
ii. Physical server pool
iii. Storage pools
iv. Network pools
v. CPU pools
5. Bursting architecture
Cloud bursting is an application arrangement demonstrate in which an application
keeps running in a private cloud or server farm and blasts into an open cloud when the
interest for registering limit spikes. The benefit of such a crossover cloud arrangement is that
an association pays for additional register assets when they are required.

Specialists suggest cloud bursting for elite, non-basic applications that handle non-
touchy data. An application can be sent locally and afterward burst to the cloud to meet crest
requests, or the application can be moved to general society cloud to free up neighbourhood
assets for business-basic applications. Cloud blasting works best for applications that don't
rely upon a perplexing application conveyance foundation or reconciliation with different
applications, segments and frameworks inner to the server farm.
While considering cloud bursting, an association must think about security and
administrative consistence necessities. For instance, cloud bursting is frequently referred to as
a feasible choice for retailers that experience tops popular amid the Christmas shopping
season. Nonetheless, distributed computing specialist co-ops don't really offer a PCI DSS-
agreeable condition and retailers could be putting delicate information in danger by bursting
it to the general population cloud.
Shortcomings from the deployment of the architectures would include:
The Bathurst data centre is a fixed location, so the deployment of the hybrid cloud
technology will require the use of URLs and directories in the integration that makes the
whole process a little difficult and thus to create a solution, Regional Gardens will require to
source for dynamic resources.
Internet performance while running the cloud based software via a computer’s web
browser or mobile applications and accessing resources is likely to hinder the smooth
working and deployment of the cloud based computing services. From a business point of
view, instances of low work throughput and flow would reduce the revenue generated, Buyya
et al (2009).
Cloud services downtime and outages. Although this would be solved through a
service level agreement where the provider guarantees maximum uptime, such unfortunate
events can lead to very low revenue collections.
Increased cloud service costs due to cloud sprawl. Cloud sprawl is the over usage of
server resources due to failure to control, manage and monitoring of the cloud service usage,
Moreno-Vozmedian, Montero& Llorente (2012).
touchy data. An application can be sent locally and afterward burst to the cloud to meet crest
requests, or the application can be moved to general society cloud to free up neighbourhood
assets for business-basic applications. Cloud blasting works best for applications that don't
rely upon a perplexing application conveyance foundation or reconciliation with different
applications, segments and frameworks inner to the server farm.
While considering cloud bursting, an association must think about security and
administrative consistence necessities. For instance, cloud bursting is frequently referred to as
a feasible choice for retailers that experience tops popular amid the Christmas shopping
season. Nonetheless, distributed computing specialist co-ops don't really offer a PCI DSS-
agreeable condition and retailers could be putting delicate information in danger by bursting
it to the general population cloud.
Shortcomings from the deployment of the architectures would include:
The Bathurst data centre is a fixed location, so the deployment of the hybrid cloud
technology will require the use of URLs and directories in the integration that makes the
whole process a little difficult and thus to create a solution, Regional Gardens will require to
source for dynamic resources.
Internet performance while running the cloud based software via a computer’s web
browser or mobile applications and accessing resources is likely to hinder the smooth
working and deployment of the cloud based computing services. From a business point of
view, instances of low work throughput and flow would reduce the revenue generated, Buyya
et al (2009).
Cloud services downtime and outages. Although this would be solved through a
service level agreement where the provider guarantees maximum uptime, such unfortunate
events can lead to very low revenue collections.
Increased cloud service costs due to cloud sprawl. Cloud sprawl is the over usage of
server resources due to failure to control, manage and monitoring of the cloud service usage,
Moreno-Vozmedian, Montero& Llorente (2012).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
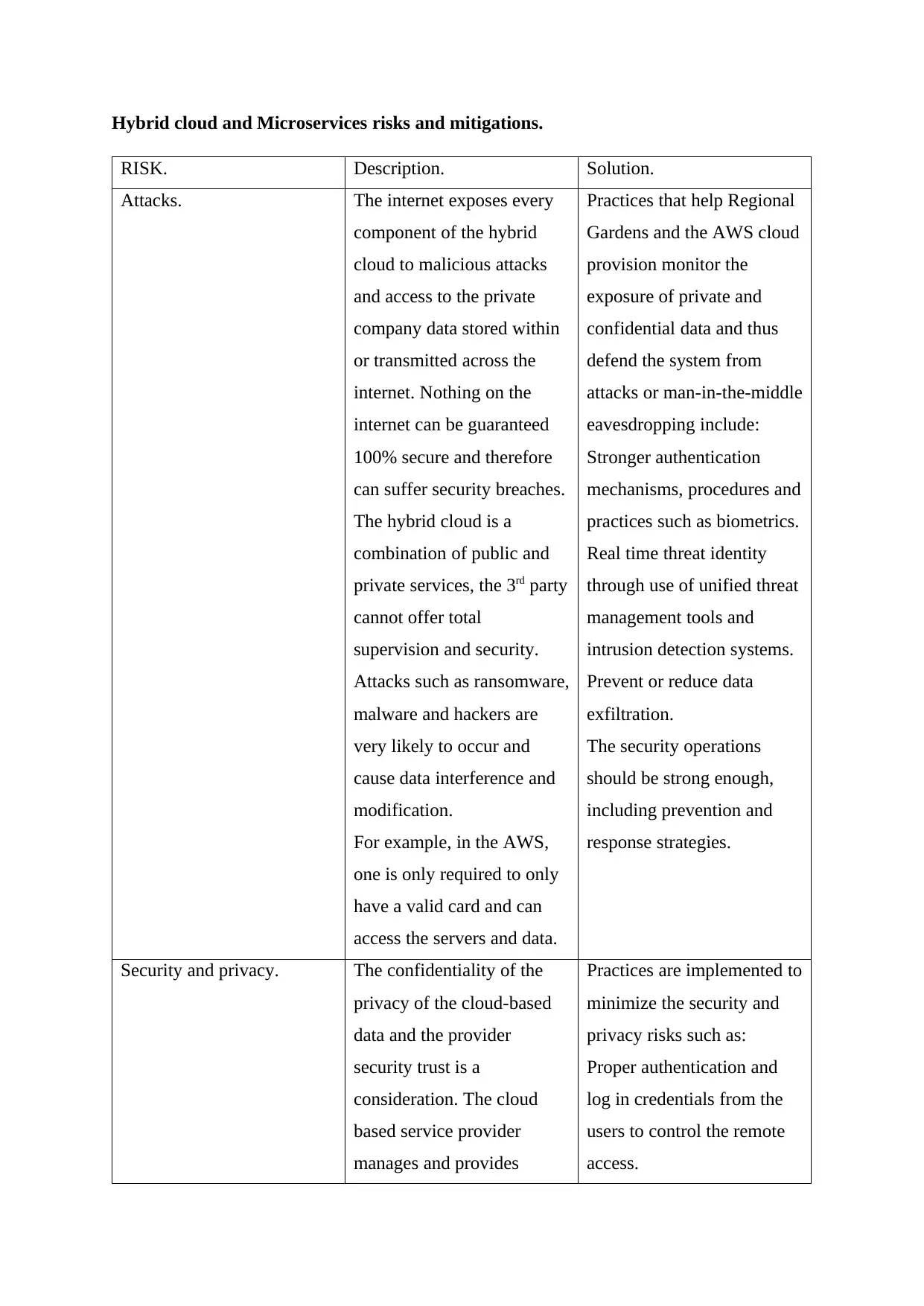
Hybrid cloud and Microservices risks and mitigations.
RISK. Description. Solution.
Attacks. The internet exposes every
component of the hybrid
cloud to malicious attacks
and access to the private
company data stored within
or transmitted across the
internet. Nothing on the
internet can be guaranteed
100% secure and therefore
can suffer security breaches.
The hybrid cloud is a
combination of public and
private services, the 3rd party
cannot offer total
supervision and security.
Attacks such as ransomware,
malware and hackers are
very likely to occur and
cause data interference and
modification.
For example, in the AWS,
one is only required to only
have a valid card and can
access the servers and data.
Practices that help Regional
Gardens and the AWS cloud
provision monitor the
exposure of private and
confidential data and thus
defend the system from
attacks or man-in-the-middle
eavesdropping include:
Stronger authentication
mechanisms, procedures and
practices such as biometrics.
Real time threat identity
through use of unified threat
management tools and
intrusion detection systems.
Prevent or reduce data
exfiltration.
The security operations
should be strong enough,
including prevention and
response strategies.
Security and privacy. The confidentiality of the
privacy of the cloud-based
data and the provider
security trust is a
consideration. The cloud
based service provider
manages and provides
Practices are implemented to
minimize the security and
privacy risks such as:
Proper authentication and
log in credentials from the
users to control the remote
access.
RISK. Description. Solution.
Attacks. The internet exposes every
component of the hybrid
cloud to malicious attacks
and access to the private
company data stored within
or transmitted across the
internet. Nothing on the
internet can be guaranteed
100% secure and therefore
can suffer security breaches.
The hybrid cloud is a
combination of public and
private services, the 3rd party
cannot offer total
supervision and security.
Attacks such as ransomware,
malware and hackers are
very likely to occur and
cause data interference and
modification.
For example, in the AWS,
one is only required to only
have a valid card and can
access the servers and data.
Practices that help Regional
Gardens and the AWS cloud
provision monitor the
exposure of private and
confidential data and thus
defend the system from
attacks or man-in-the-middle
eavesdropping include:
Stronger authentication
mechanisms, procedures and
practices such as biometrics.
Real time threat identity
through use of unified threat
management tools and
intrusion detection systems.
Prevent or reduce data
exfiltration.
The security operations
should be strong enough,
including prevention and
response strategies.
Security and privacy. The confidentiality of the
privacy of the cloud-based
data and the provider
security trust is a
consideration. The cloud
based service provider
manages and provides
Practices are implemented to
minimize the security and
privacy risks such as:
Proper authentication and
log in credentials from the
users to control the remote
access.
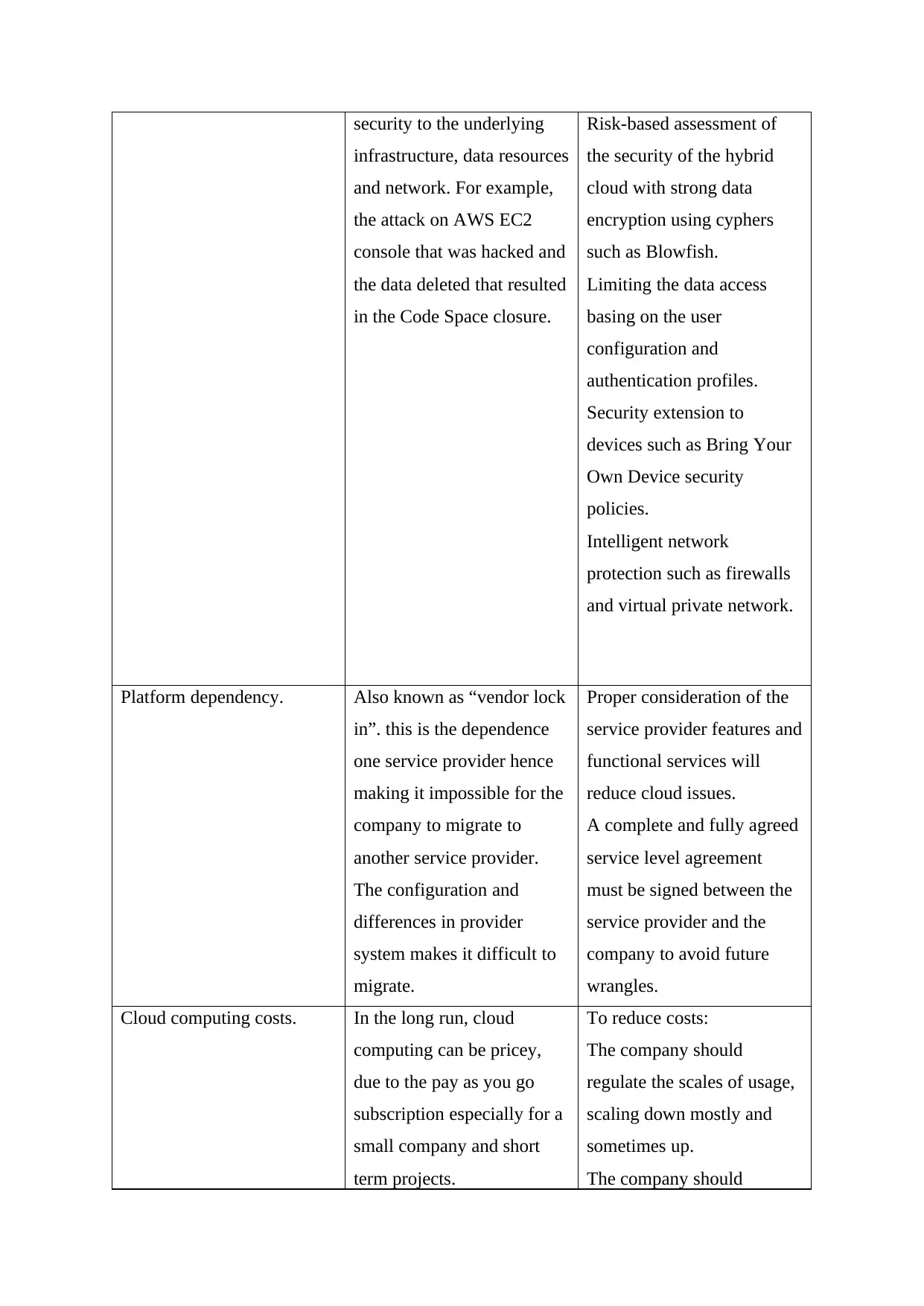
security to the underlying
infrastructure, data resources
and network. For example,
the attack on AWS EC2
console that was hacked and
the data deleted that resulted
in the Code Space closure.
Risk-based assessment of
the security of the hybrid
cloud with strong data
encryption using cyphers
such as Blowfish.
Limiting the data access
basing on the user
configuration and
authentication profiles.
Security extension to
devices such as Bring Your
Own Device security
policies.
Intelligent network
protection such as firewalls
and virtual private network.
Platform dependency. Also known as “vendor lock
in”. this is the dependence
one service provider hence
making it impossible for the
company to migrate to
another service provider.
The configuration and
differences in provider
system makes it difficult to
migrate.
Proper consideration of the
service provider features and
functional services will
reduce cloud issues.
A complete and fully agreed
service level agreement
must be signed between the
service provider and the
company to avoid future
wrangles.
Cloud computing costs. In the long run, cloud
computing can be pricey,
due to the pay as you go
subscription especially for a
small company and short
term projects.
To reduce costs:
The company should
regulate the scales of usage,
scaling down mostly and
sometimes up.
The company should
infrastructure, data resources
and network. For example,
the attack on AWS EC2
console that was hacked and
the data deleted that resulted
in the Code Space closure.
Risk-based assessment of
the security of the hybrid
cloud with strong data
encryption using cyphers
such as Blowfish.
Limiting the data access
basing on the user
configuration and
authentication profiles.
Security extension to
devices such as Bring Your
Own Device security
policies.
Intelligent network
protection such as firewalls
and virtual private network.
Platform dependency. Also known as “vendor lock
in”. this is the dependence
one service provider hence
making it impossible for the
company to migrate to
another service provider.
The configuration and
differences in provider
system makes it difficult to
migrate.
Proper consideration of the
service provider features and
functional services will
reduce cloud issues.
A complete and fully agreed
service level agreement
must be signed between the
service provider and the
company to avoid future
wrangles.
Cloud computing costs. In the long run, cloud
computing can be pricey,
due to the pay as you go
subscription especially for a
small company and short
term projects.
To reduce costs:
The company should
regulate the scales of usage,
scaling down mostly and
sometimes up.
The company should
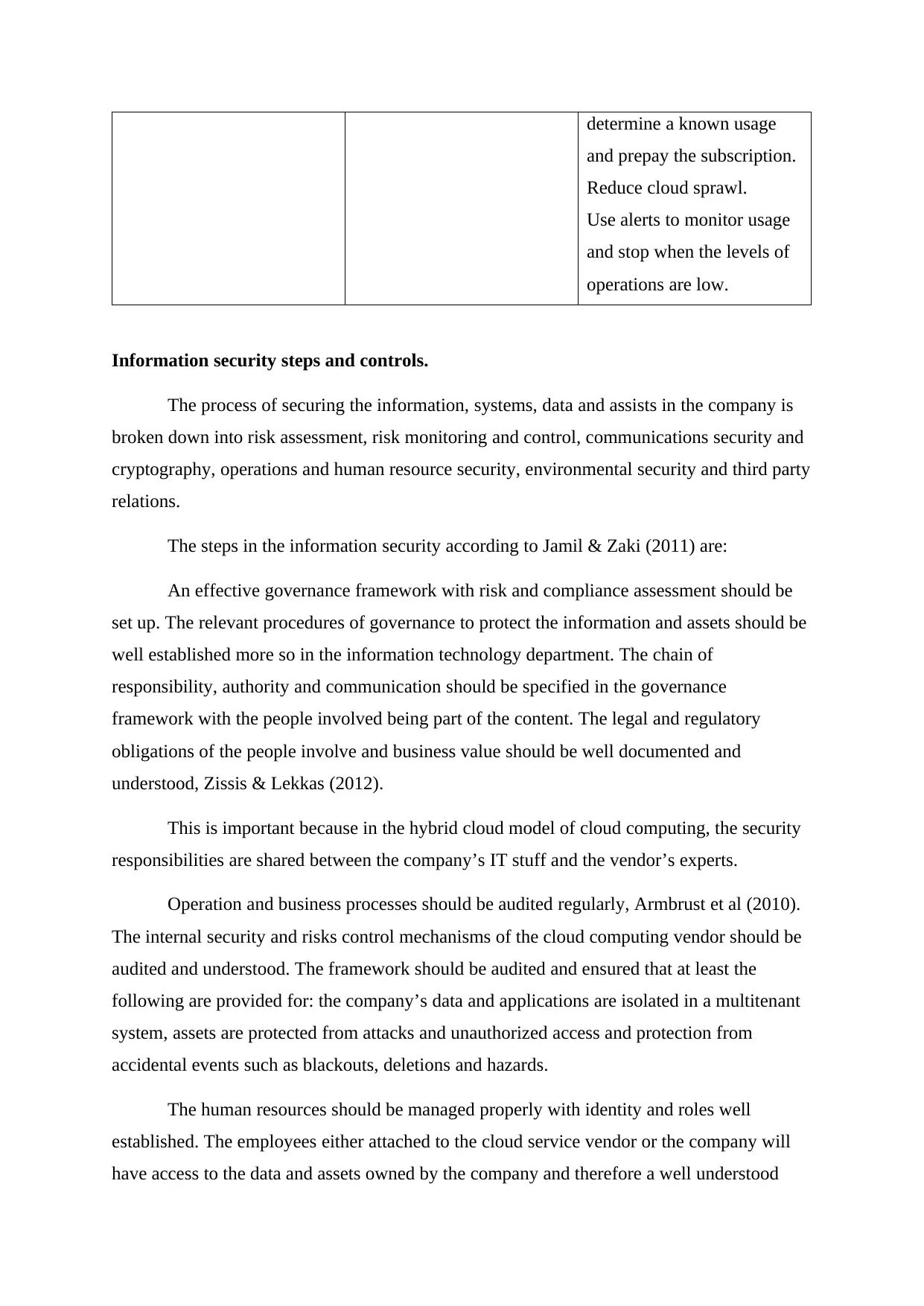
determine a known usage
and prepay the subscription.
Reduce cloud sprawl.
Use alerts to monitor usage
and stop when the levels of
operations are low.
Information security steps and controls.
The process of securing the information, systems, data and assists in the company is
broken down into risk assessment, risk monitoring and control, communications security and
cryptography, operations and human resource security, environmental security and third party
relations.
The steps in the information security according to Jamil & Zaki (2011) are:
An effective governance framework with risk and compliance assessment should be
set up. The relevant procedures of governance to protect the information and assets should be
well established more so in the information technology department. The chain of
responsibility, authority and communication should be specified in the governance
framework with the people involved being part of the content. The legal and regulatory
obligations of the people involve and business value should be well documented and
understood, Zissis & Lekkas (2012).
This is important because in the hybrid cloud model of cloud computing, the security
responsibilities are shared between the company’s IT stuff and the vendor’s experts.
Operation and business processes should be audited regularly, Armbrust et al (2010).
The internal security and risks control mechanisms of the cloud computing vendor should be
audited and understood. The framework should be audited and ensured that at least the
following are provided for: the company’s data and applications are isolated in a multitenant
system, assets are protected from attacks and unauthorized access and protection from
accidental events such as blackouts, deletions and hazards.
The human resources should be managed properly with identity and roles well
established. The employees either attached to the cloud service vendor or the company will
have access to the data and assets owned by the company and therefore a well understood
and prepay the subscription.
Reduce cloud sprawl.
Use alerts to monitor usage
and stop when the levels of
operations are low.
Information security steps and controls.
The process of securing the information, systems, data and assists in the company is
broken down into risk assessment, risk monitoring and control, communications security and
cryptography, operations and human resource security, environmental security and third party
relations.
The steps in the information security according to Jamil & Zaki (2011) are:
An effective governance framework with risk and compliance assessment should be
set up. The relevant procedures of governance to protect the information and assets should be
well established more so in the information technology department. The chain of
responsibility, authority and communication should be specified in the governance
framework with the people involved being part of the content. The legal and regulatory
obligations of the people involve and business value should be well documented and
understood, Zissis & Lekkas (2012).
This is important because in the hybrid cloud model of cloud computing, the security
responsibilities are shared between the company’s IT stuff and the vendor’s experts.
Operation and business processes should be audited regularly, Armbrust et al (2010).
The internal security and risks control mechanisms of the cloud computing vendor should be
audited and understood. The framework should be audited and ensured that at least the
following are provided for: the company’s data and applications are isolated in a multitenant
system, assets are protected from attacks and unauthorized access and protection from
accidental events such as blackouts, deletions and hazards.
The human resources should be managed properly with identity and roles well
established. The employees either attached to the cloud service vendor or the company will
have access to the data and assets owned by the company and therefore a well understood
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

framework should be established to control the human factors in the hybrid cloud service
model.
This is important to control the internal malicious access to data and assets that are
out of bounds for a particular or specific group of employees to confer additional security
from internal threats.
A proper data enforcement framework should be established. Data is the most
important and critical asset for the Regional Gardens company and is at the centre of the
information technology security priorities in the hybrid cloud computing model, Masud, &
Huang (2012). The control mechanisms to the data threats such as risk of data theft, data loss,
disclosure, tampering, modification, unauthorized access and data unavailability are
addressed in this step. The responsibility of the data protection is with both the company and
the vendor in the hybrid cloud computing model and therefore should be well taken care of.
A service level agreement should be documented with well-presented privacy policy.
The policies controlling the behaviours, activities and practices of the employees should be
well documented. Such activities might expose the data to unauthorized third parties. The
policies include the Bring Your Own Device policies and employee contract agreements.
The security framework of the cloud applications should be assed and tested. The
cloud based applications should be protected from any malicious attacks just like the network
and physical layers are protected.
This is so because, insecure application provisions can be used by attackers to gain
access to the whole network and cloud storage. The proper use of the applications will also
reduce the costs of cloud computing through reduction of cloud sprawls.
Proper security provision of the network and connections. Just like the other layers of
the hybrid cloud model are protected, the internet through which the cloud is accessed from
be protected again man in the middle attacks, eavesdropping and malicious network traffic.
This can be done through use of unified threat management tools and appliances in the
market or provided by the cloud service vendor, Li et al (2013).
Physical environment security evaluation. The physical infrastructure of the facilities
housing the computers and servers should be well secured. The audit reports of the area
should provide assurance to the company. The facility should be in a secure area, be
model.
This is important to control the internal malicious access to data and assets that are
out of bounds for a particular or specific group of employees to confer additional security
from internal threats.
A proper data enforcement framework should be established. Data is the most
important and critical asset for the Regional Gardens company and is at the centre of the
information technology security priorities in the hybrid cloud computing model, Masud, &
Huang (2012). The control mechanisms to the data threats such as risk of data theft, data loss,
disclosure, tampering, modification, unauthorized access and data unavailability are
addressed in this step. The responsibility of the data protection is with both the company and
the vendor in the hybrid cloud computing model and therefore should be well taken care of.
A service level agreement should be documented with well-presented privacy policy.
The policies controlling the behaviours, activities and practices of the employees should be
well documented. Such activities might expose the data to unauthorized third parties. The
policies include the Bring Your Own Device policies and employee contract agreements.
The security framework of the cloud applications should be assed and tested. The
cloud based applications should be protected from any malicious attacks just like the network
and physical layers are protected.
This is so because, insecure application provisions can be used by attackers to gain
access to the whole network and cloud storage. The proper use of the applications will also
reduce the costs of cloud computing through reduction of cloud sprawls.
Proper security provision of the network and connections. Just like the other layers of
the hybrid cloud model are protected, the internet through which the cloud is accessed from
be protected again man in the middle attacks, eavesdropping and malicious network traffic.
This can be done through use of unified threat management tools and appliances in the
market or provided by the cloud service vendor, Li et al (2013).
Physical environment security evaluation. The physical infrastructure of the facilities
housing the computers and servers should be well secured. The audit reports of the area
should provide assurance to the company. The facility should be in a secure area, be

protected against physical threats such as floods, security personnel within the area, security
equipment such as cctv camera properly installed and a quick response mechanism present.
A cloud service agreement inclusive of all security provisions. Since the hybrid
computing service provision involves two parties the vendor and the Regional Garden,
therefore an agreement should be made between the two parties, Sonwalkar (2013,
September). The agreement must include specific information concerning the security
provision such as practices directed towards protection of the data assists of the company.
This is important because the agreement should include the relevant information data
breaches, what ought to be done in case of such unfortunate events, the responsible party
when data attacks occur and the data back-up and recovery services.
The exit process should be set, with the security requirements well understood. This
should outline the termination of contract between the vendor and company in relation to the
data stored in the servers or cloud computers, Rahimi et al (2012 November). The exit
process should include the time requirement to provide the data after termination of contract
and the form of data to be provided from the cloud computers. The exit process should also
outline the time it would take for the vendor to delete the company data from the servers.
Additionally, the exit process should allow the company to audit the servers and ensure that
ball the data owned by the company has been deleted.
This important because sometimes the vendor after contract termination can provide
the data in a format that is not accessible.
Security control. Rationale.
Regular monitoring of the employee
accounts such as log ins.
This monitoring allows the employees
regular re-authentication while logging into
the system.
It also provides a base for intrusion
detection or prevention.
Limited administrative privileges to a few
employees.
This will assist the company and the vendor
to control the access of unauthorized data by
the employees.
Minimizes the use of privileges thus
reducing the risk of malicious activity and
equipment such as cctv camera properly installed and a quick response mechanism present.
A cloud service agreement inclusive of all security provisions. Since the hybrid
computing service provision involves two parties the vendor and the Regional Garden,
therefore an agreement should be made between the two parties, Sonwalkar (2013,
September). The agreement must include specific information concerning the security
provision such as practices directed towards protection of the data assists of the company.
This is important because the agreement should include the relevant information data
breaches, what ought to be done in case of such unfortunate events, the responsible party
when data attacks occur and the data back-up and recovery services.
The exit process should be set, with the security requirements well understood. This
should outline the termination of contract between the vendor and company in relation to the
data stored in the servers or cloud computers, Rahimi et al (2012 November). The exit
process should include the time requirement to provide the data after termination of contract
and the form of data to be provided from the cloud computers. The exit process should also
outline the time it would take for the vendor to delete the company data from the servers.
Additionally, the exit process should allow the company to audit the servers and ensure that
ball the data owned by the company has been deleted.
This important because sometimes the vendor after contract termination can provide
the data in a format that is not accessible.
Security control. Rationale.
Regular monitoring of the employee
accounts such as log ins.
This monitoring allows the employees
regular re-authentication while logging into
the system.
It also provides a base for intrusion
detection or prevention.
Limited administrative privileges to a few
employees.
This will assist the company and the vendor
to control the access of unauthorized data by
the employees.
Minimizes the use of privileges thus
reducing the risk of malicious activity and
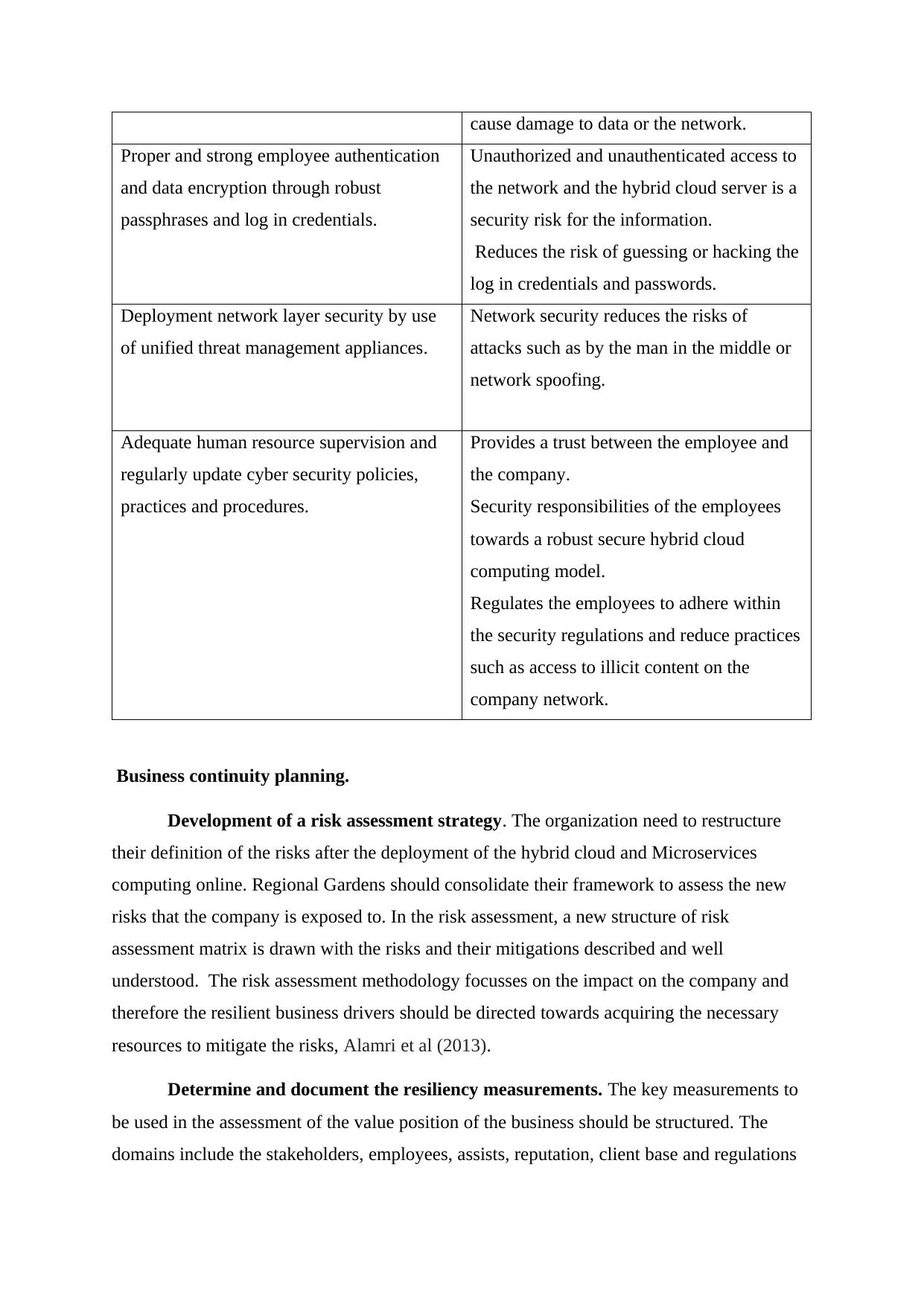
cause damage to data or the network.
Proper and strong employee authentication
and data encryption through robust
passphrases and log in credentials.
Unauthorized and unauthenticated access to
the network and the hybrid cloud server is a
security risk for the information.
Reduces the risk of guessing or hacking the
log in credentials and passwords.
Deployment network layer security by use
of unified threat management appliances.
Network security reduces the risks of
attacks such as by the man in the middle or
network spoofing.
Adequate human resource supervision and
regularly update cyber security policies,
practices and procedures.
Provides a trust between the employee and
the company.
Security responsibilities of the employees
towards a robust secure hybrid cloud
computing model.
Regulates the employees to adhere within
the security regulations and reduce practices
such as access to illicit content on the
company network.
Business continuity planning.
Development of a risk assessment strategy. The organization need to restructure
their definition of the risks after the deployment of the hybrid cloud and Microservices
computing online. Regional Gardens should consolidate their framework to assess the new
risks that the company is exposed to. In the risk assessment, a new structure of risk
assessment matrix is drawn with the risks and their mitigations described and well
understood. The risk assessment methodology focusses on the impact on the company and
therefore the resilient business drivers should be directed towards acquiring the necessary
resources to mitigate the risks, Alamri et al (2013).
Determine and document the resiliency measurements. The key measurements to
be used in the assessment of the value position of the business should be structured. The
domains include the stakeholders, employees, assists, reputation, client base and regulations
Proper and strong employee authentication
and data encryption through robust
passphrases and log in credentials.
Unauthorized and unauthenticated access to
the network and the hybrid cloud server is a
security risk for the information.
Reduces the risk of guessing or hacking the
log in credentials and passwords.
Deployment network layer security by use
of unified threat management appliances.
Network security reduces the risks of
attacks such as by the man in the middle or
network spoofing.
Adequate human resource supervision and
regularly update cyber security policies,
practices and procedures.
Provides a trust between the employee and
the company.
Security responsibilities of the employees
towards a robust secure hybrid cloud
computing model.
Regulates the employees to adhere within
the security regulations and reduce practices
such as access to illicit content on the
company network.
Business continuity planning.
Development of a risk assessment strategy. The organization need to restructure
their definition of the risks after the deployment of the hybrid cloud and Microservices
computing online. Regional Gardens should consolidate their framework to assess the new
risks that the company is exposed to. In the risk assessment, a new structure of risk
assessment matrix is drawn with the risks and their mitigations described and well
understood. The risk assessment methodology focusses on the impact on the company and
therefore the resilient business drivers should be directed towards acquiring the necessary
resources to mitigate the risks, Alamri et al (2013).
Determine and document the resiliency measurements. The key measurements to
be used in the assessment of the value position of the business should be structured. The
domains include the stakeholders, employees, assists, reputation, client base and regulations
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and compliance. The data point elements should be used to plan, monitor, track and recover
data information and use it to form a base of trusted enterprise corporation, Buyya et al
(2009).
Disaster recovery. This shouldn’t just include the natural disaster such as floods but
also the human errors and mistakes that might cause downtimes in the enterprise operations.
A team of dedicated employees is created to act as the quick response team incise of the
disasters. This team is designated before the disastrous event occurs and includes the
assignment of tasks and responsibilities to ensure the downtime or outage times do not hurt
significantly the revenue collection and mission or vision of the company, Buyya et al (2009).
Information backup. The data backup centre should be easily accessible in the
instance of downtime or disaster. However, the backup location should be safe from the rest
of the server of the hybrid cloud service to protect it from the disaster or downtime events.
The 3,2,1 rule of backup should be strictly adhered to meaning that the company data should
be transferred at least three times, on to two different mediums of data storage and one of the
media must be an offsite location.
OPERATIONAL CHECKLIST.
Regional Gardens is required to have a well-structured billing and account
governance framework that provides account management with the account to be used for the
billing process identified and the process of handling the bills for the AWS cloud service in
the SaaS and PaaS model outlined.
The company need to have developed a strategy for the management of the AWS
API, operating system, network and console program. In the strategy, the company is
required to have a proper data access mechanism for the access of the online cloud based
computing platform.
Regional Gardens is required to strategize on the identifying and tracking process for
the AWS provided resources such as SaaS infrastructure and architecture such as software,
analytics, data storage and data protection, Armbrust et al (2010).
The company is required to audit and report whether the AWS solution meets the
company’s expectations of the applications resilience and high availability requirements.
data information and use it to form a base of trusted enterprise corporation, Buyya et al
(2009).
Disaster recovery. This shouldn’t just include the natural disaster such as floods but
also the human errors and mistakes that might cause downtimes in the enterprise operations.
A team of dedicated employees is created to act as the quick response team incise of the
disasters. This team is designated before the disastrous event occurs and includes the
assignment of tasks and responsibilities to ensure the downtime or outage times do not hurt
significantly the revenue collection and mission or vision of the company, Buyya et al (2009).
Information backup. The data backup centre should be easily accessible in the
instance of downtime or disaster. However, the backup location should be safe from the rest
of the server of the hybrid cloud service to protect it from the disaster or downtime events.
The 3,2,1 rule of backup should be strictly adhered to meaning that the company data should
be transferred at least three times, on to two different mediums of data storage and one of the
media must be an offsite location.
OPERATIONAL CHECKLIST.
Regional Gardens is required to have a well-structured billing and account
governance framework that provides account management with the account to be used for the
billing process identified and the process of handling the bills for the AWS cloud service in
the SaaS and PaaS model outlined.
The company need to have developed a strategy for the management of the AWS
API, operating system, network and console program. In the strategy, the company is
required to have a proper data access mechanism for the access of the online cloud based
computing platform.
Regional Gardens is required to strategize on the identifying and tracking process for
the AWS provided resources such as SaaS infrastructure and architecture such as software,
analytics, data storage and data protection, Armbrust et al (2010).
The company is required to audit and report whether the AWS solution meets the
company’s expectations of the applications resilience and high availability requirements.

In the requirements, the company should report if the solution provided by the
Amazon Web Service hybrid computing service meets the disaster recovery and backup
expectations of the company.
Regional Gardens limited must consider the business criticality and plan a good
strategy for the monitoring and incident management program provided by the AWS solution
for the hybrid computing service.
Regional Gardens limited has planned how the cloud based vendor will be integrated
and configured into the existing IT stiff and operations. The strategy need to contain the set
up on how the upgrades and updates will be performed, launch or termination of operating
system and how the company shall manage and control server images.
E-mail integration into cloud service.
Email integration into cloud service is through the Amazon simple email service to
help Regional Gardens advertise, send, notify and transact through emails. Since its reliable
for such as small business, the cost effective method of integration is the amazon SDK
development tool into the existing software as a service application, Lin et al (2010).
The process:
1. Recruitment of expert developers on contract to design and code the email
applications on the cloud. The process of recruitment would be fair through
interviews and a tendering process.
The critical point in this step would be identification of the best of the best computer
programmers. This is critical because the email service should be integrated once and
therefore leaves no room for errors.
2. Identification of the most suitable programming language. From the many languages
and software platforms such as c++, java, python and go offered on the Amazon web
service, the best should be selected. Most suitable is the python programming
language.
3. Installation of the language.
4. Design of the email instance application. This is a critical step in the migration
process. The design should be simple enough to offer an easier to understand user
interface.
Amazon Web Service hybrid computing service meets the disaster recovery and backup
expectations of the company.
Regional Gardens limited must consider the business criticality and plan a good
strategy for the monitoring and incident management program provided by the AWS solution
for the hybrid computing service.
Regional Gardens limited has planned how the cloud based vendor will be integrated
and configured into the existing IT stiff and operations. The strategy need to contain the set
up on how the upgrades and updates will be performed, launch or termination of operating
system and how the company shall manage and control server images.
E-mail integration into cloud service.
Email integration into cloud service is through the Amazon simple email service to
help Regional Gardens advertise, send, notify and transact through emails. Since its reliable
for such as small business, the cost effective method of integration is the amazon SDK
development tool into the existing software as a service application, Lin et al (2010).
The process:
1. Recruitment of expert developers on contract to design and code the email
applications on the cloud. The process of recruitment would be fair through
interviews and a tendering process.
The critical point in this step would be identification of the best of the best computer
programmers. This is critical because the email service should be integrated once and
therefore leaves no room for errors.
2. Identification of the most suitable programming language. From the many languages
and software platforms such as c++, java, python and go offered on the Amazon web
service, the best should be selected. Most suitable is the python programming
language.
3. Installation of the language.
4. Design of the email instance application. This is a critical step in the migration
process. The design should be simple enough to offer an easier to understand user
interface.

The critical point and issue in the step is the design of a very complicated application.
This is because it would be hard to understand and therefore will become less usable.
5. Coding of the email instance application. A slow and steady process to ensure
accuracy to create a high quality application.
6. Testing on the online platform. Supervised by the project manager, the IT department
stuff the company will test the email application for all the services required by the
company executives.
7. Deployment. The final stable version of the email application will be deployed on the
software as a service platform to allow the clients of the company communicate.
8. Exit process. The exit process after the termination of the contract and deployment of
the email instance will include a plan and strategy on the maintenance of the email
instance of the PaaS.
This is a critical point and the issues would include setting the responsibility of the
security regulations, protection and policy of the email service.
This is because it would be hard to understand and therefore will become less usable.
5. Coding of the email instance application. A slow and steady process to ensure
accuracy to create a high quality application.
6. Testing on the online platform. Supervised by the project manager, the IT department
stuff the company will test the email application for all the services required by the
company executives.
7. Deployment. The final stable version of the email application will be deployed on the
software as a service platform to allow the clients of the company communicate.
8. Exit process. The exit process after the termination of the contract and deployment of
the email instance will include a plan and strategy on the maintenance of the email
instance of the PaaS.
This is a critical point and the issues would include setting the responsibility of the
security regulations, protection and policy of the email service.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References.
Armbrust, M., Fox, A., Griffith, R., Joseph, A. D., Katz, R., Konwinski, A., ... & Zaharia, M.
(2010). A view of cloud computing. Communications of the ACM, 53(4), 50-58.
Buyya, R., Yeo, C. S., Venugopal, S., Broberg, J., & Brandic, I. (2009). Cloud computing
and emerging IT platforms: Vision, hype, and reality for delivering computing as the 5th
utility. Future Generation computer systems, 25(6), 599-616.
Armbrust, M., Fox, A., Griffith, R., Joseph, A. D., Katz, R. H., Konwinski, A., ... & Zaharia,
M. (2009). Above the clouds: A berkeley view of cloud computing (Vol. 4, pp. 506-522).
Technical Report UCB/EECS-2009-28, EECS Department, University of California,
Berkeley.
Jamil, D., & Zaki, H. (2011). Cloud computing security. International Journal of Engineering
Science and Technology, 3(4).
Zissis, D., & Lekkas, D. (2012). Addressing cloud computing security issues. Future
Generation computer systems, 28(3), 583-592.
Wu, L., Garg, S. K., & Buyya, R. (2011, May). SLA-based resource allocation for software
as a service provider (SaaS) in cloud computing environments. In Proceedings of the 2011
11th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (pp. 195-
204). IEEE Computer Society.
Cerullo, V., & Cerullo, M. J. (2014). Business continuity planning: a comprehensive
approach. Information Systems Management, 21(3), 70-78.
Krutz, R. L., & Vines, R. D. (2010). Cloud security: A comprehensive guide to secure cloud
computing. Wiley Publishing.
Moreno-Vozmediano, R., Montero, R. S., & Llorente, I. M. (2012). Iaas cloud architecture:
From virtualized datacenters to federated cloud infrastructures. Computer, 45(12), 65-72.
Masud, M. A. H., & Huang, X. (2012). An e-learning system architecture based on cloud
computing. system, 10(11).
Armbrust, M., Fox, A., Griffith, R., Joseph, A. D., Katz, R., Konwinski, A., ... & Zaharia, M.
(2010). A view of cloud computing. Communications of the ACM, 53(4), 50-58.
Buyya, R., Yeo, C. S., Venugopal, S., Broberg, J., & Brandic, I. (2009). Cloud computing
and emerging IT platforms: Vision, hype, and reality for delivering computing as the 5th
utility. Future Generation computer systems, 25(6), 599-616.
Armbrust, M., Fox, A., Griffith, R., Joseph, A. D., Katz, R. H., Konwinski, A., ... & Zaharia,
M. (2009). Above the clouds: A berkeley view of cloud computing (Vol. 4, pp. 506-522).
Technical Report UCB/EECS-2009-28, EECS Department, University of California,
Berkeley.
Jamil, D., & Zaki, H. (2011). Cloud computing security. International Journal of Engineering
Science and Technology, 3(4).
Zissis, D., & Lekkas, D. (2012). Addressing cloud computing security issues. Future
Generation computer systems, 28(3), 583-592.
Wu, L., Garg, S. K., & Buyya, R. (2011, May). SLA-based resource allocation for software
as a service provider (SaaS) in cloud computing environments. In Proceedings of the 2011
11th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (pp. 195-
204). IEEE Computer Society.
Cerullo, V., & Cerullo, M. J. (2014). Business continuity planning: a comprehensive
approach. Information Systems Management, 21(3), 70-78.
Krutz, R. L., & Vines, R. D. (2010). Cloud security: A comprehensive guide to secure cloud
computing. Wiley Publishing.
Moreno-Vozmediano, R., Montero, R. S., & Llorente, I. M. (2012). Iaas cloud architecture:
From virtualized datacenters to federated cloud infrastructures. Computer, 45(12), 65-72.
Masud, M. A. H., & Huang, X. (2012). An e-learning system architecture based on cloud
computing. system, 10(11).

Alamri, A., Ansari, W. S., Hassan, M. M., Hossain, M. S., Alelaiwi, A., & Hossain, M. A.
(2013). A survey on sensor-cloud: architecture, applications, and approaches. International
Journal of Distributed Sensor Networks, 9(2), 917923.
Lin, Y., Shao, L., Zhu, Z., Wang, Q., & Sabhikhi, R. K. (2010). Wireless network cloud:
Architecture and system requirements. IBM Journal of Research and Development, 54(1), 4-
1.
Rahimi, M. R., Venkatasubramanian, N., Mehrotra, S., & Vasilakos, A. V. (2012,
November). MAPCloud: mobile applications on an elastic and scalable 2-tier cloud
architecture. In Utility and Cloud Computing (UCC), 2012 IEEE Fifth International
Conference on (pp. 83-90). IEEE.
Sonwalkar, N. (2013, September). The first adaptive MOOC: A case study on pedagogy
framework and scalable cloud Architecture—Part I. In MOOCs Forum (Vol. 1, No. P, pp. 22-
29). 140 Huguenot Street, 3rd Floor New Rochelle, NY 10801 USA: Mary Ann Liebert, Inc..
Li, X. Y., Zhou, L. T., Shi, Y., & Guo, Y. (2013). A trusted computing environment model in
cloud architecture. In Machine Learning and Cybernetics (ICMLC), 2010 International
Conference on (Vol. 6, pp. 2843-2848). IEEE.
(2013). A survey on sensor-cloud: architecture, applications, and approaches. International
Journal of Distributed Sensor Networks, 9(2), 917923.
Lin, Y., Shao, L., Zhu, Z., Wang, Q., & Sabhikhi, R. K. (2010). Wireless network cloud:
Architecture and system requirements. IBM Journal of Research and Development, 54(1), 4-
1.
Rahimi, M. R., Venkatasubramanian, N., Mehrotra, S., & Vasilakos, A. V. (2012,
November). MAPCloud: mobile applications on an elastic and scalable 2-tier cloud
architecture. In Utility and Cloud Computing (UCC), 2012 IEEE Fifth International
Conference on (pp. 83-90). IEEE.
Sonwalkar, N. (2013, September). The first adaptive MOOC: A case study on pedagogy
framework and scalable cloud Architecture—Part I. In MOOCs Forum (Vol. 1, No. P, pp. 22-
29). 140 Huguenot Street, 3rd Floor New Rochelle, NY 10801 USA: Mary Ann Liebert, Inc..
Li, X. Y., Zhou, L. T., Shi, Y., & Guo, Y. (2013). A trusted computing environment model in
cloud architecture. In Machine Learning and Cybernetics (ICMLC), 2010 International
Conference on (Vol. 6, pp. 2843-2848). IEEE.
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





