Distributed System Security in Fitness Industry
VerifiedAdded on 2022/08/21
|13
|2723
|11
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CLOUD COMPUTING
DISTRIBUTED SYSTEM SECURITY IN FITNESS INDUSTRY
Name of the Student:
Name of the University:
Author Note:
DISTRIBUTED SYSTEM SECURITY IN FITNESS INDUSTRY
Name of the Student:
Name of the University:
Author Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1CLOUD COMPUTING
Introduction
The fitness industry deals with numerous computing process and methods which is
benefited by the distributed computing systems which allow multiple heterogeneous or
homogenous workstations and computer to perform as a unified computing environment. The
fitness managers in this environment are allowed to access the remote and local business
resources for operating various business processes. In this computing environment, the fitness
officials deal with numerous sensitive data and thus require a tight security (Abadi et al. 2016).
This research proposal will be aiming at some security concerns of distributed systems in a
technology and fitness industry. In this research study various security system will be involved
for which various literatures will be reviewed. Finally, the research provides recommendation
and future scope of the research study dealing with various key areas in distributed system
security.
This research study will be aiming at securing different distributed systems in the fitness
industry from external threats and risks. The computing environment is surrounded with multiple
threats and risks as many attackers try to phish the sensitive information for their sole benefit
(Ghosh 2014). This research study will be helpful for multiple fitness firms to strengthen the
security of their distributed system.
The objectives of this research study will be as follows:
To know the importance of distributed systems in the fitness industry.
To analyze various models of distributed computing system.
To determine various security measures to protect the distributed computing
environment.
Introduction
The fitness industry deals with numerous computing process and methods which is
benefited by the distributed computing systems which allow multiple heterogeneous or
homogenous workstations and computer to perform as a unified computing environment. The
fitness managers in this environment are allowed to access the remote and local business
resources for operating various business processes. In this computing environment, the fitness
officials deal with numerous sensitive data and thus require a tight security (Abadi et al. 2016).
This research proposal will be aiming at some security concerns of distributed systems in a
technology and fitness industry. In this research study various security system will be involved
for which various literatures will be reviewed. Finally, the research provides recommendation
and future scope of the research study dealing with various key areas in distributed system
security.
This research study will be aiming at securing different distributed systems in the fitness
industry from external threats and risks. The computing environment is surrounded with multiple
threats and risks as many attackers try to phish the sensitive information for their sole benefit
(Ghosh 2014). This research study will be helpful for multiple fitness firms to strengthen the
security of their distributed system.
The objectives of this research study will be as follows:
To know the importance of distributed systems in the fitness industry.
To analyze various models of distributed computing system.
To determine various security measures to protect the distributed computing
environment.

2CLOUD COMPUTING
The research questions that will be used to achieve the research aim and objectives are stated
below:
What is the importance of Distributed Computing system in a fitness firm?
What are the different models of distributed computing system?
What are the security measures used to protect the system from external environment?
Literature Review
Distributed Computing System
In computer science, distributed system is described as a single unified system of
distributed processes, processors and computers altogether by common communication network
or medium for transmitting messages (Orgerie, Assuncao and Lefevre 2014). These messages
can be transmitted by logically or physically.
The advantages of distributed computing are as follows:
Development in Business Performance: The multiple nodes of the distributed system
allow the fitness industry to process their operations in a parallel manner. This increases
the performance level of the business applications. Sharing of the Resources: Distributed system allow sufficient access to the resources
and this helps the business to easily share and distribute its key resources among various
departments. Developed Extendibility: The distributed systems are developed to be adaptive and
modular. The file storage capacity and the computing operations can be increased by the
fitness firms by increasing the number of nodes in the system (Zhao et al. 2014).
The research questions that will be used to achieve the research aim and objectives are stated
below:
What is the importance of Distributed Computing system in a fitness firm?
What are the different models of distributed computing system?
What are the security measures used to protect the system from external environment?
Literature Review
Distributed Computing System
In computer science, distributed system is described as a single unified system of
distributed processes, processors and computers altogether by common communication network
or medium for transmitting messages (Orgerie, Assuncao and Lefevre 2014). These messages
can be transmitted by logically or physically.
The advantages of distributed computing are as follows:
Development in Business Performance: The multiple nodes of the distributed system
allow the fitness industry to process their operations in a parallel manner. This increases
the performance level of the business applications. Sharing of the Resources: Distributed system allow sufficient access to the resources
and this helps the business to easily share and distribute its key resources among various
departments. Developed Extendibility: The distributed systems are developed to be adaptive and
modular. The file storage capacity and the computing operations can be increased by the
fitness firms by increasing the number of nodes in the system (Zhao et al. 2014).

3CLOUD COMPUTING
Developed Availability, Fault tolerance and Reliability: The collection of multiple
storage and computing resources can help the fitness firms to reduce the possibility of
data redundancy and can also help them to increase the fault tolerability level.
Using Distributed computing environment in the fitness firms can also have some
disadvantages too like:
Heterogeneity: Distributed Systems allow a user to access data from various business
resources. This can allow multiple attackers to easily access the sensitive information and
misuse them in various means. Openness: Openness feature of the distributed system can also increase security concern
for the fitness industry (Maksimov 2014). Scalability: The increased scalability also increases the number of resources and users
which increases the security threats for the fitness firms. Trust and Security: Operating as an industry, the fitness firms have to deal with huge
data. These data can be highly sensitive to multiple individuals and the distributed
computing environment requires huge security measures to protect the environment from
attackers.
Various models of Distributed Computing System
The distributed computing can be divided in four models:
Cluster Computing: In this model, set of computer are connected together for
communicating with high speed. This group of computers are presented as a single system to the
users. This model can help the fitness firms to increase the computing power and performance.
Developed Availability, Fault tolerance and Reliability: The collection of multiple
storage and computing resources can help the fitness firms to reduce the possibility of
data redundancy and can also help them to increase the fault tolerability level.
Using Distributed computing environment in the fitness firms can also have some
disadvantages too like:
Heterogeneity: Distributed Systems allow a user to access data from various business
resources. This can allow multiple attackers to easily access the sensitive information and
misuse them in various means. Openness: Openness feature of the distributed system can also increase security concern
for the fitness industry (Maksimov 2014). Scalability: The increased scalability also increases the number of resources and users
which increases the security threats for the fitness firms. Trust and Security: Operating as an industry, the fitness firms have to deal with huge
data. These data can be highly sensitive to multiple individuals and the distributed
computing environment requires huge security measures to protect the environment from
attackers.
Various models of Distributed Computing System
The distributed computing can be divided in four models:
Cluster Computing: In this model, set of computer are connected together for
communicating with high speed. This group of computers are presented as a single system to the
users. This model can help the fitness firms to increase the computing power and performance.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
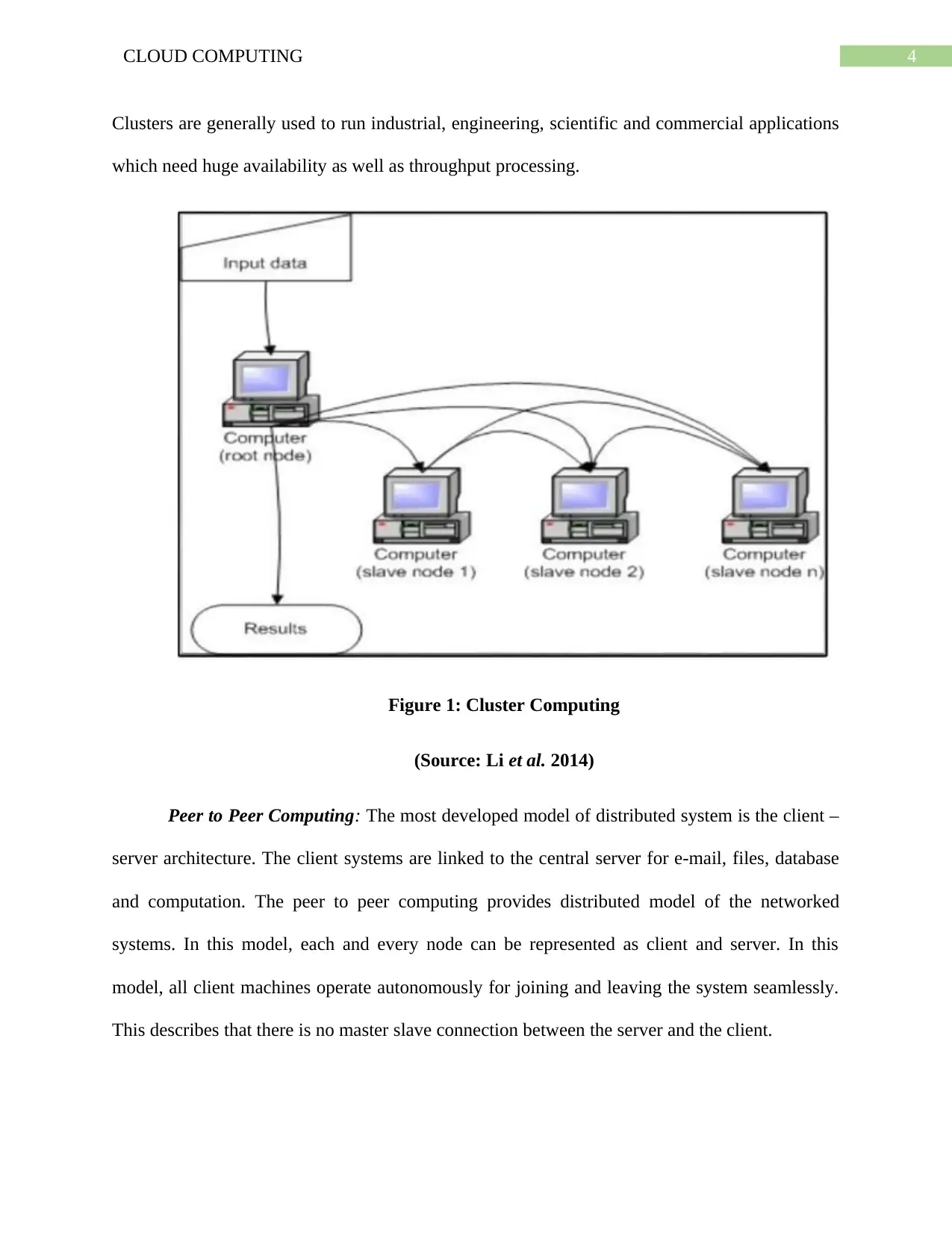
4CLOUD COMPUTING
Clusters are generally used to run industrial, engineering, scientific and commercial applications
which need huge availability as well as throughput processing.
Figure 1: Cluster Computing
(Source: Li et al. 2014)
Peer to Peer Computing: The most developed model of distributed system is the client –
server architecture. The client systems are linked to the central server for e-mail, files, database
and computation. The peer to peer computing provides distributed model of the networked
systems. In this model, each and every node can be represented as client and server. In this
model, all client machines operate autonomously for joining and leaving the system seamlessly.
This describes that there is no master slave connection between the server and the client.
Clusters are generally used to run industrial, engineering, scientific and commercial applications
which need huge availability as well as throughput processing.
Figure 1: Cluster Computing
(Source: Li et al. 2014)
Peer to Peer Computing: The most developed model of distributed system is the client –
server architecture. The client systems are linked to the central server for e-mail, files, database
and computation. The peer to peer computing provides distributed model of the networked
systems. In this model, each and every node can be represented as client and server. In this
model, all client machines operate autonomously for joining and leaving the system seamlessly.
This describes that there is no master slave connection between the server and the client.

5CLOUD COMPUTING
Figure 2: Peer to Peer Computing
(Source: Bandara and Jayasumana 2013)
Grid Computing: In this model of distributed computing, a group of heterogeneous
systems are spread among numerous domains to provide access to the business resources. Grid
computing can also be used in the fitness firms to select, share, and aggregate the distributed
resources. Grids are generally considered as heterogeneous clusters interconnected with high
speed networks. They offer centralized controls which can allow the officials of the fitness firm
to operate each and every computing operations from one define location.
Figure 2: Peer to Peer Computing
(Source: Bandara and Jayasumana 2013)
Grid Computing: In this model of distributed computing, a group of heterogeneous
systems are spread among numerous domains to provide access to the business resources. Grid
computing can also be used in the fitness firms to select, share, and aggregate the distributed
resources. Grids are generally considered as heterogeneous clusters interconnected with high
speed networks. They offer centralized controls which can allow the officials of the fitness firm
to operate each and every computing operations from one define location.

6CLOUD COMPUTING
Figure 3: Grid Computing
(Source: Bazinet, Zwickl and Cummings 2014)
Cloud Computing: Cloud Computing can be defined as the model used to enable the
convenient and on – demand access to the distributed network of the configurable resources.
Cloud computing can also be used in the fitness industry to store huge data securely. Cloud
computing is a platform where the servers provide various internet services to its users. The
services of cloud computing can be of three types: IaaS, PaaS and SaaS.
Figure 3: Grid Computing
(Source: Bazinet, Zwickl and Cummings 2014)
Cloud Computing: Cloud Computing can be defined as the model used to enable the
convenient and on – demand access to the distributed network of the configurable resources.
Cloud computing can also be used in the fitness industry to store huge data securely. Cloud
computing is a platform where the servers provide various internet services to its users. The
services of cloud computing can be of three types: IaaS, PaaS and SaaS.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CLOUD COMPUTING
Figure 4: Cloud Computing Model
(Source: Arora, Parashar and Transforming 2013)
Security Issues and Countermeasures in Distributed Computing System
Distributed Computing Environment is vulnerable to numerous threats. The attackers are
always trying to phish and extract the data from the distributed computing system. Thus,
distributed system should be protected from these attackers. The security services of the
distributed computing can be of six types namely: Authorization, Authentication,
Confidentiality, Non-repudiation, Accountability and Data Integrity (Carlin and Curran 2013).
Usually these distributed system face distributed denial of service and identity attacks where the
attackers always search for sensitive information to phish and misuse them in various means.
Confidentiality factor ensures that the data of the computing environment is not disclosed to the
unauthorized users. The data integrity factor can also be applied in the fitness firms to maintain
Figure 4: Cloud Computing Model
(Source: Arora, Parashar and Transforming 2013)
Security Issues and Countermeasures in Distributed Computing System
Distributed Computing Environment is vulnerable to numerous threats. The attackers are
always trying to phish and extract the data from the distributed computing system. Thus,
distributed system should be protected from these attackers. The security services of the
distributed computing can be of six types namely: Authorization, Authentication,
Confidentiality, Non-repudiation, Accountability and Data Integrity (Carlin and Curran 2013).
Usually these distributed system face distributed denial of service and identity attacks where the
attackers always search for sensitive information to phish and misuse them in various means.
Confidentiality factor ensures that the data of the computing environment is not disclosed to the
unauthorized users. The data integrity factor can also be applied in the fitness firms to maintain

8CLOUD COMPUTING
the consistency and accuracy of the data throughout its complete life cycle. Each and every
sensitive information will be encrypted from both the ends. The receiver side should have the
decryption key to decode the message that was sent by the sender. This encryption technique will
disallow any unauthorized user to enter and misuse the computing environment of the distributed
system (Khalil, Khreishah and Azeem 2014). This authentication technique can be applied to
every data and can be secured from outer world. The easy availability of the data can also
increase the threat for the firms and thus, they should be ensured that only authorized users can
only request for the data and information that are needed for their daily operations. Most of the
networks or the operating systems use IP addresses for determining the validity of the user. A
network solution will also be installed through which the network administrator can monitor the
network operations thoroughly.
Research methodology
The research will be conducted by utilizing the descriptive research design. Descriptive
research design can be helpful to analyze the effectiveness of securing the distributed computing
environment in the fitness industry. This research design will also allow the investigators to
study the result in a critical and logical manner. The research will be completed using mix
methodologies and thus descriptive research design will be an efficient choice for the
investigators. Security of the distributed system will mainly focus on securing the essential data
of the fitness firms. Thus, mix methodology will be helpful for the investigators determine the
significance and effectiveness of securing the distributed computing environment.
As mentioned above, the research will be conducted by collecting both primary and
secondary data. A survey process will be conducted to collect the primary data. In this survey
process, a set of questionnaires will be provided and 50 participants can take part in this survey
the consistency and accuracy of the data throughout its complete life cycle. Each and every
sensitive information will be encrypted from both the ends. The receiver side should have the
decryption key to decode the message that was sent by the sender. This encryption technique will
disallow any unauthorized user to enter and misuse the computing environment of the distributed
system (Khalil, Khreishah and Azeem 2014). This authentication technique can be applied to
every data and can be secured from outer world. The easy availability of the data can also
increase the threat for the firms and thus, they should be ensured that only authorized users can
only request for the data and information that are needed for their daily operations. Most of the
networks or the operating systems use IP addresses for determining the validity of the user. A
network solution will also be installed through which the network administrator can monitor the
network operations thoroughly.
Research methodology
The research will be conducted by utilizing the descriptive research design. Descriptive
research design can be helpful to analyze the effectiveness of securing the distributed computing
environment in the fitness industry. This research design will also allow the investigators to
study the result in a critical and logical manner. The research will be completed using mix
methodologies and thus descriptive research design will be an efficient choice for the
investigators. Security of the distributed system will mainly focus on securing the essential data
of the fitness firms. Thus, mix methodology will be helpful for the investigators determine the
significance and effectiveness of securing the distributed computing environment.
As mentioned above, the research will be conducted by collecting both primary and
secondary data. A survey process will be conducted to collect the primary data. In this survey
process, a set of questionnaires will be provided and 50 participants can take part in this survey

9CLOUD COMPUTING
process. The questionnaire set will be consisting of 10 different questions that are associated to
the research topic (Brace 2018). The secondary data will be collected from online journals and
articles. The research study will also require non – probability sampling technique to sample the
data. 50 employees from global fitness firms will be allowed to take part in this survey.
The data will be presented in such a way that the readers can individually justify or
conclude the research study by their own. The data that will be collected from the survey method
will be converted in the percentage form. This percentage form will allow the investigators to
know the viewpoints of the participants easily. The percentage numeric will then be transformed
as charts, tables and graphs. The data will be plotted according to the number of responses. The
graphical representation of the data will assist the investigators to conclude the research. The
secondary data will be analyzed using the thematic method.
The research will be completed by considering few ethical guidelines. Moreover, the
research will not harm any individual in the whole process such as, in the survey method, none
of the participants will be forced to take part in the process. They can withdraw their
participation at any time of the process. Any sort of promoting pictures or logo will not be there
in the questionnaire set. The secondary sources will be selected in such a way that they are free
from plagiarism. The research must be completed with the expected budget and the within the
expected time range (Zhang et al. 2013). The research will consider all the risks of the fitness
industry and the research will be very helpful for various fitness firms such that they can
strengthen their security policies and measures to protect the systems from various attacks and
threats.
Therefore, the research study will be a huge benefit for the fitness industries. This
research proposal provided a brief idea of the research study. This proposal also led a layout of
process. The questionnaire set will be consisting of 10 different questions that are associated to
the research topic (Brace 2018). The secondary data will be collected from online journals and
articles. The research study will also require non – probability sampling technique to sample the
data. 50 employees from global fitness firms will be allowed to take part in this survey.
The data will be presented in such a way that the readers can individually justify or
conclude the research study by their own. The data that will be collected from the survey method
will be converted in the percentage form. This percentage form will allow the investigators to
know the viewpoints of the participants easily. The percentage numeric will then be transformed
as charts, tables and graphs. The data will be plotted according to the number of responses. The
graphical representation of the data will assist the investigators to conclude the research. The
secondary data will be analyzed using the thematic method.
The research will be completed by considering few ethical guidelines. Moreover, the
research will not harm any individual in the whole process such as, in the survey method, none
of the participants will be forced to take part in the process. They can withdraw their
participation at any time of the process. Any sort of promoting pictures or logo will not be there
in the questionnaire set. The secondary sources will be selected in such a way that they are free
from plagiarism. The research must be completed with the expected budget and the within the
expected time range (Zhang et al. 2013). The research will consider all the risks of the fitness
industry and the research will be very helpful for various fitness firms such that they can
strengthen their security policies and measures to protect the systems from various attacks and
threats.
Therefore, the research study will be a huge benefit for the fitness industries. This
research proposal provided a brief idea of the research study. This proposal also led a layout of
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10CLOUD COMPUTING
conducting the research. The methodologies that will be used are also mentioned and justified.
This research proposal also concluded that it will be a significant move for the fitness industry to
achieve its goals. The sensitive information of the industry should be protected from the outer
world as hackers are always trying to extract information for the computing environment.
Distributed Computing Environment is vulnerable to numerous threats. The security services of
the distributed computing can be of six types namely: Authorization, Authentication,
Confidentiality, Non-repudiation, Accountability and Data Integrity. It can be said that
authentication through encryption will be an effective security measure to protect the data from
the hackers or attackers. In the future researchers, it can be observed that the fitness industry gets
well developed by using the ideas of this research study. Future works may focus on
strengthening the computing power of every distributed models to improve the performance of
every fitness firms. It is recommended that the fitness industry should focus on employing
effective tools to monitor and analyze the computing environment on a regular phase. The
proposal also concluded that multifactor authentication can also be useful for securing the
distributed system from unauthorized access and controls. The employees of the fitness firms
also need efficient training such that they can easily operate the systems and manage the systems
efficiently.
conducting the research. The methodologies that will be used are also mentioned and justified.
This research proposal also concluded that it will be a significant move for the fitness industry to
achieve its goals. The sensitive information of the industry should be protected from the outer
world as hackers are always trying to extract information for the computing environment.
Distributed Computing Environment is vulnerable to numerous threats. The security services of
the distributed computing can be of six types namely: Authorization, Authentication,
Confidentiality, Non-repudiation, Accountability and Data Integrity. It can be said that
authentication through encryption will be an effective security measure to protect the data from
the hackers or attackers. In the future researchers, it can be observed that the fitness industry gets
well developed by using the ideas of this research study. Future works may focus on
strengthening the computing power of every distributed models to improve the performance of
every fitness firms. It is recommended that the fitness industry should focus on employing
effective tools to monitor and analyze the computing environment on a regular phase. The
proposal also concluded that multifactor authentication can also be useful for securing the
distributed system from unauthorized access and controls. The employees of the fitness firms
also need efficient training such that they can easily operate the systems and manage the systems
efficiently.

11CLOUD COMPUTING
Bibliography
Abadi, M., Agarwal, A., Barham, P., Brevdo, E., Chen, Z., Citro, C., Corrado, G.S., Davis, A.,
Dean, J., Devin, M. and Ghemawat, S., 2016. Tensorflow: Large-scale machine learning on
heterogeneous distributed systems. arXiv preprint arXiv:1603.04467.
Arora, R., Parashar, A. and Transforming, C.C.I., 2013. Secure user data in cloud computing
using encryption algorithms. International journal of engineering research and
applications, 3(4), pp.1922-1926.
Bandara, H.D. and Jayasumana, A.P., 2013. Collaborative applications over peer-to-peer
systems–challenges and solutions. Peer-to-Peer Networking and Applications, 6(3), pp.257-276.
Bazinet, A.L., Zwickl, D.J. and Cummings, M.P., 2014. A gateway for phylogenetic analysis
powered by grid computing featuring GARLI 2.0. Systematic biology, 63(5), pp.812-818.
Brace, I., 2018. Questionnaire design: How to plan, structure and write survey material for
effective market research. Kogan Page Publishers.
Carlin, S. and Curran, K., 2013. Cloud computing security. In Pervasive and Ubiquitous
Technology Innovations for Ambient Intelligence Environments (pp. 12-17). IGI Global.
Ghosh, S., 2014. Distributed systems: an algorithmic approach. Chapman and Hall/CRC.
Khalil, I.M., Khreishah, A. and Azeem, M., 2014. Cloud computing security: A
survey. Computers, 3(1), pp.1-35.
Li, H., Ghodsi, A., Zaharia, M., Shenker, S. and Stoica, I., 2014, November. Tachyon: Reliable,
memory speed storage for cluster computing frameworks. In Proceedings of the ACM
Symposium on Cloud Computing (pp. 1-15).
Bibliography
Abadi, M., Agarwal, A., Barham, P., Brevdo, E., Chen, Z., Citro, C., Corrado, G.S., Davis, A.,
Dean, J., Devin, M. and Ghemawat, S., 2016. Tensorflow: Large-scale machine learning on
heterogeneous distributed systems. arXiv preprint arXiv:1603.04467.
Arora, R., Parashar, A. and Transforming, C.C.I., 2013. Secure user data in cloud computing
using encryption algorithms. International journal of engineering research and
applications, 3(4), pp.1922-1926.
Bandara, H.D. and Jayasumana, A.P., 2013. Collaborative applications over peer-to-peer
systems–challenges and solutions. Peer-to-Peer Networking and Applications, 6(3), pp.257-276.
Bazinet, A.L., Zwickl, D.J. and Cummings, M.P., 2014. A gateway for phylogenetic analysis
powered by grid computing featuring GARLI 2.0. Systematic biology, 63(5), pp.812-818.
Brace, I., 2018. Questionnaire design: How to plan, structure and write survey material for
effective market research. Kogan Page Publishers.
Carlin, S. and Curran, K., 2013. Cloud computing security. In Pervasive and Ubiquitous
Technology Innovations for Ambient Intelligence Environments (pp. 12-17). IGI Global.
Ghosh, S., 2014. Distributed systems: an algorithmic approach. Chapman and Hall/CRC.
Khalil, I.M., Khreishah, A. and Azeem, M., 2014. Cloud computing security: A
survey. Computers, 3(1), pp.1-35.
Li, H., Ghodsi, A., Zaharia, M., Shenker, S. and Stoica, I., 2014, November. Tachyon: Reliable,
memory speed storage for cluster computing frameworks. In Proceedings of the ACM
Symposium on Cloud Computing (pp. 1-15).

12CLOUD COMPUTING
Maksimov, V.I., 2014. Dynamical inverse problems of distributed systems (Vol. 37). Walter de
Gruyter GmbH & Co KG.
Orgerie, A.C., Assuncao, M.D.D. and Lefevre, L., 2014. A survey on techniques for improving
the energy efficiency of large-scale distributed systems. ACM Computing Surveys
(CSUR), 46(4), pp.1-31.
Zhang, Y., Li, B., Huang, C., Yang, X., Qian, H., Deng, Q., Zhao, Z., Li, A., Zhao, J., Zhang, X.
and Qu, F., 2013. Ten cities cross-sectional questionnaire survey of children asthma and other
allergies in China. Chinese Science Bulletin, 58(34), pp.4182-4189.
Zhao, X., Zhang, Y., Lion, D., Ullah, M.F., Luo, Y., Yuan, D. and Stumm, M., 2014. lprof: A
non-intrusive request flow profiler for distributed systems. In 11th {USENIX} Symposium on
Operating Systems Design and Implementation ({OSDI} 14) (pp. 629-644).
Maksimov, V.I., 2014. Dynamical inverse problems of distributed systems (Vol. 37). Walter de
Gruyter GmbH & Co KG.
Orgerie, A.C., Assuncao, M.D.D. and Lefevre, L., 2014. A survey on techniques for improving
the energy efficiency of large-scale distributed systems. ACM Computing Surveys
(CSUR), 46(4), pp.1-31.
Zhang, Y., Li, B., Huang, C., Yang, X., Qian, H., Deng, Q., Zhao, Z., Li, A., Zhao, J., Zhang, X.
and Qu, F., 2013. Ten cities cross-sectional questionnaire survey of children asthma and other
allergies in China. Chinese Science Bulletin, 58(34), pp.4182-4189.
Zhao, X., Zhang, Y., Lion, D., Ullah, M.F., Luo, Y., Yuan, D. and Stumm, M., 2014. lprof: A
non-intrusive request flow profiler for distributed systems. In 11th {USENIX} Symposium on
Operating Systems Design and Implementation ({OSDI} 14) (pp. 629-644).
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





