Cloud-Based Enterprise Systems: Architecture, Security, and Case Study
VerifiedAdded on 2019/09/25
|24
|3754
|200
Report
AI Summary
This report delves into the adoption of cloud computing technology within business enterprises. It explores the advantages of cloud solutions, such as scalability and cost-effectiveness, while also addressing critical security concerns. The report examines cloud architecture, including provider, enterprise, and user requirements, and discusses various deployment techniques like public, private, community, and hybrid clouds. It highlights security threats, risks, and vulnerabilities, emphasizing the importance of data governance and security. Furthermore, the report provides an overview of cloud-based business processes and the security concerns for enterprises. It concludes with a case study on migrating enterprise IT services to the cloud, offering practical insights and real-world applications. The report emphasizes the need for purposeful planning and resource management in the design and implementation of cloud-based enterprise systems to ensure data security and operational efficiency.

Running head: CLOUD-ENTERPRISE
SYSTEMS
1
Cloud Based Enterprise Systems
Author Name
Your University
Name
SYSTEMS
1
Cloud Based Enterprise Systems
Author Name
Your University
Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD-ENTERPRISE 2
Cloud Based Enterprise Systems
Abstract
This Paper focuses on the adopting Cloud Computing technology in
Business Enter- prises.While advances in technological field and
discovery of new technologies. Cloud storage is a service model where
data are maintained, manager, backed up remotely over internet. Thus
when we just imagine of business enterprise to include cloud computing
it has a great opportunities coming its way when business converts
online. It delivers all types of services with a easy suitable approach
while it turns online. The most ad- vantageous point when cloud usage is
done then the whole enterprise system becomes scalable and the
resources are available at a different priorities, virtualized resources are
available when needed. The new stream is now strikes which opens new
opportunities and business models.The customers also gets benefit for
the resources as they have to pay for the resources what they use.
Computing and internet is the new era of the 21st century and adding
cloud computing to the enterprise infrastructure. These deployment may
cause major issue of this century that is Security. Security of data is most
of the important thing to be taken care.If in a system, there is lack of
security then it is not reliable and not worth. For the successful
implementation there must be purposeful planning and managment of
resources with keeping major key points in mind while design. Here
security is the key point where threats. vulnerbilities and other internet
risks may affect the system if lack of security. Thus every
organization/company must take preventive measures and build or implement
a secured system.
In this paper, we will discuss about the cloud architecture for enterprise
Cloud Based Enterprise Systems
Abstract
This Paper focuses on the adopting Cloud Computing technology in
Business Enter- prises.While advances in technological field and
discovery of new technologies. Cloud storage is a service model where
data are maintained, manager, backed up remotely over internet. Thus
when we just imagine of business enterprise to include cloud computing
it has a great opportunities coming its way when business converts
online. It delivers all types of services with a easy suitable approach
while it turns online. The most ad- vantageous point when cloud usage is
done then the whole enterprise system becomes scalable and the
resources are available at a different priorities, virtualized resources are
available when needed. The new stream is now strikes which opens new
opportunities and business models.The customers also gets benefit for
the resources as they have to pay for the resources what they use.
Computing and internet is the new era of the 21st century and adding
cloud computing to the enterprise infrastructure. These deployment may
cause major issue of this century that is Security. Security of data is most
of the important thing to be taken care.If in a system, there is lack of
security then it is not reliable and not worth. For the successful
implementation there must be purposeful planning and managment of
resources with keeping major key points in mind while design. Here
security is the key point where threats. vulnerbilities and other internet
risks may affect the system if lack of security. Thus every
organization/company must take preventive measures and build or implement
a secured system.
In this paper, we will discuss about the cloud architecture for enterprise
CLOUD-ENTERPRISE 3
systems, its basic requirements, the security challenges for enterprise
with its applications in risk managment areas and a case study that will
brief in detail about the migrating enterprise IT system services to cloud
for the better experience and making it more portable.
systems, its basic requirements, the security challenges for enterprise
with its applications in risk managment areas and a case study that will
brief in detail about the migrating enterprise IT system services to cloud
for the better experience and making it more portable.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CLOUD-ENTERPRISE 4
Introduction
In the era of 21st century, Cloud computing is the huge bubble with lots
of opportunities in different application areas. Since world is advancing
technically using IT systems thus IT demand is also widely increasing.
While using cloud computing in IT enterprises is an ease in IT industry,
with the combination of cloud computing and IT industry may help
enterprises in delivering on-demand services. Systems become more
distributed, scalable, reliable, cost effective, etc,. are key advantages of
the Cloud based IT enterprises.
Cloud computing(Carr & Yu, 2008) has been expressed in many ways by
different organ- izations based on the application areas. Since there are
no standard definitions has been adopted until now. The commonly used
definition for the cloud(Chan, Mei, & Zhang, 2009) stands for computing
with: “Common, Location-independent, Online Utility that is available on
Demand”. Clouds provide various service models they are IaaS (Infra-
structure as a service), PaaS (Platform as a service) and SaaS (Software
as a Service). Using IaaS customers can develop their own applications
based on processing, storage and network connectivity as provided by
IaaS. Using PaaS customers can increase their focus towards application
feature expansions based on the databases, queues, work flow engines,
etc which is provided by service provider. Using SaaS customer could get
the 3rd party applications with some customizing options as per customer
for their own corporate logo, colors, etc as it provides complete end user
applications.
In business Enterprises and Infrastructure, cloud provides a vast shift
where many out- sourced resources can be used and can be made
available as per requirements. In this paper we will discuss the cloud
based architecture as per the enterprises point of view. Further we will
discuss about the challenges in cloud based IT infrastructures.There are
many threats and risks while cloud is connected to enterprise for easy or
Introduction
In the era of 21st century, Cloud computing is the huge bubble with lots
of opportunities in different application areas. Since world is advancing
technically using IT systems thus IT demand is also widely increasing.
While using cloud computing in IT enterprises is an ease in IT industry,
with the combination of cloud computing and IT industry may help
enterprises in delivering on-demand services. Systems become more
distributed, scalable, reliable, cost effective, etc,. are key advantages of
the Cloud based IT enterprises.
Cloud computing(Carr & Yu, 2008) has been expressed in many ways by
different organ- izations based on the application areas. Since there are
no standard definitions has been adopted until now. The commonly used
definition for the cloud(Chan, Mei, & Zhang, 2009) stands for computing
with: “Common, Location-independent, Online Utility that is available on
Demand”. Clouds provide various service models they are IaaS (Infra-
structure as a service), PaaS (Platform as a service) and SaaS (Software
as a Service). Using IaaS customers can develop their own applications
based on processing, storage and network connectivity as provided by
IaaS. Using PaaS customers can increase their focus towards application
feature expansions based on the databases, queues, work flow engines,
etc which is provided by service provider. Using SaaS customer could get
the 3rd party applications with some customizing options as per customer
for their own corporate logo, colors, etc as it provides complete end user
applications.
In business Enterprises and Infrastructure, cloud provides a vast shift
where many out- sourced resources can be used and can be made
available as per requirements. In this paper we will discuss the cloud
based architecture as per the enterprises point of view. Further we will
discuss about the challenges in cloud based IT infrastructures.There are
many threats and risks while cloud is connected to enterprise for easy or
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD-ENTERPRISE 5
remote infra- structure. In reality, many enterprises faced malicious
attacks in this era thus we will discuss its causes, strengths and
weakness. Since cloud computing is the technology in boom and our
researchers are continuously researching and collaboratively work with the
organizations like amazon, Google, Microsoft and others who provide
solutions from any of the XaaS(as a service) here X can be Service,
Platform or Infrastructure.Security re-
remote infra- structure. In reality, many enterprises faced malicious
attacks in this era thus we will discuss its causes, strengths and
weakness. Since cloud computing is the technology in boom and our
researchers are continuously researching and collaboratively work with the
organizations like amazon, Google, Microsoft and others who provide
solutions from any of the XaaS(as a service) here X can be Service,
Platform or Infrastructure.Security re-
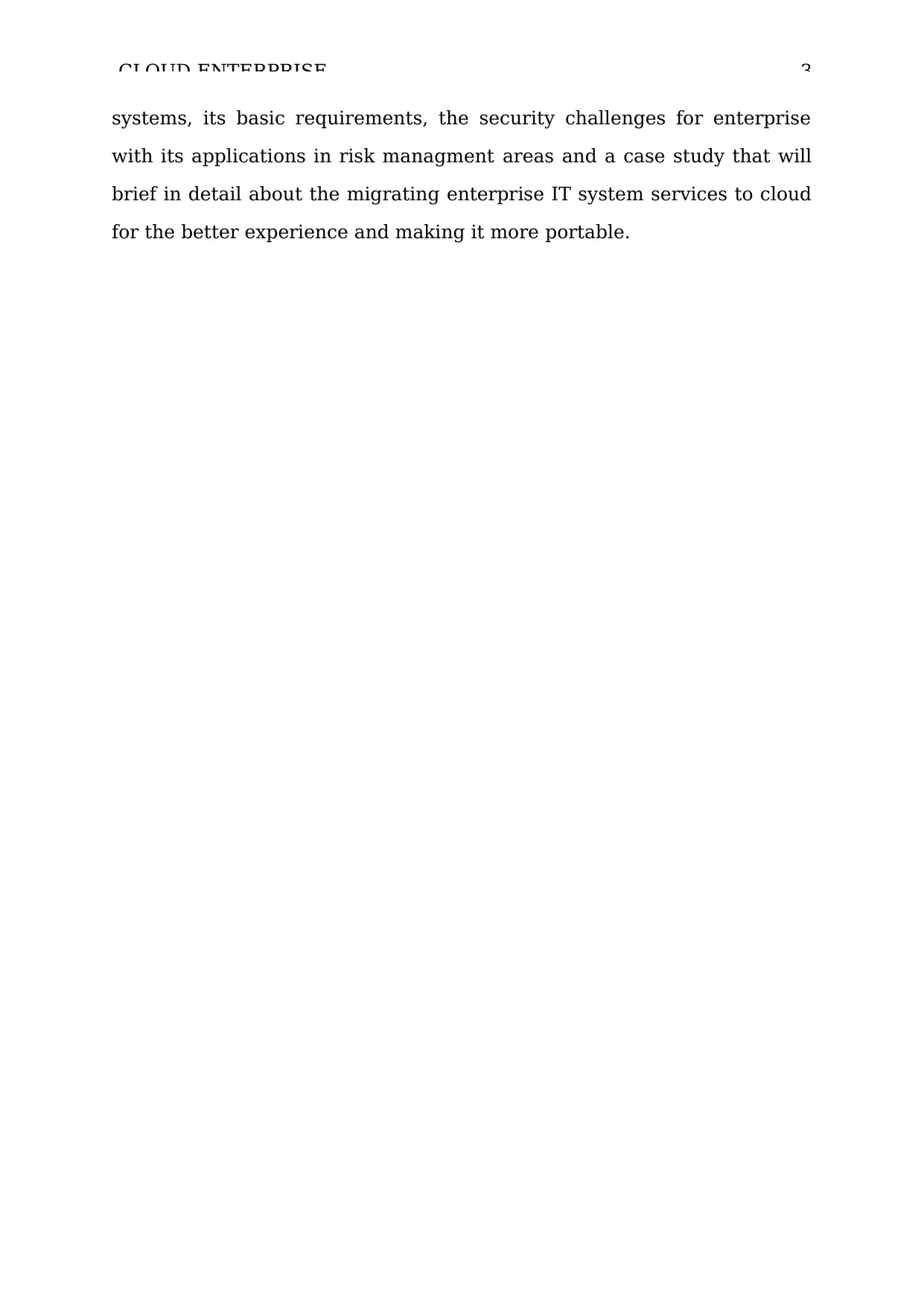
CLOUD-ENTERPRISE 6
searchers and professionals are working on security risks, potential threats,
vulnerabilities, and possible countermeasure in enterprise cloud
computing constantly.
Figure 1 . Service Model: XaaS
Later in the study we will discuss about how an enterprises are transiting
their IT infra- structure to cloud using case study and here a simple
background with its work will be discussed followed by its working
methods and outcomes.
searchers and professionals are working on security risks, potential threats,
vulnerabilities, and possible countermeasure in enterprise cloud
computing constantly.
Figure 1 . Service Model: XaaS
Later in the study we will discuss about how an enterprises are transiting
their IT infra- structure to cloud using case study and here a simple
background with its work will be discussed followed by its working
methods and outcomes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CLOUD-ENTERPRISE 7
Architectural Requirements of Cloud Computing for
Enterprises
Since we have already discussed that cloud computing has a wide range
of scope in different areas such as enterprise level to academics too.
These days cloud computing is more used for study and research purpose
for the advancements For the purpose of making it generalized usage there
needs to be a requirement of standard API’s i.e., application program
interface and standard usage guide for the developers and architects but
the development of standard factors might take place of challenges in
making cloud computing reliable, scalable, interoperability.
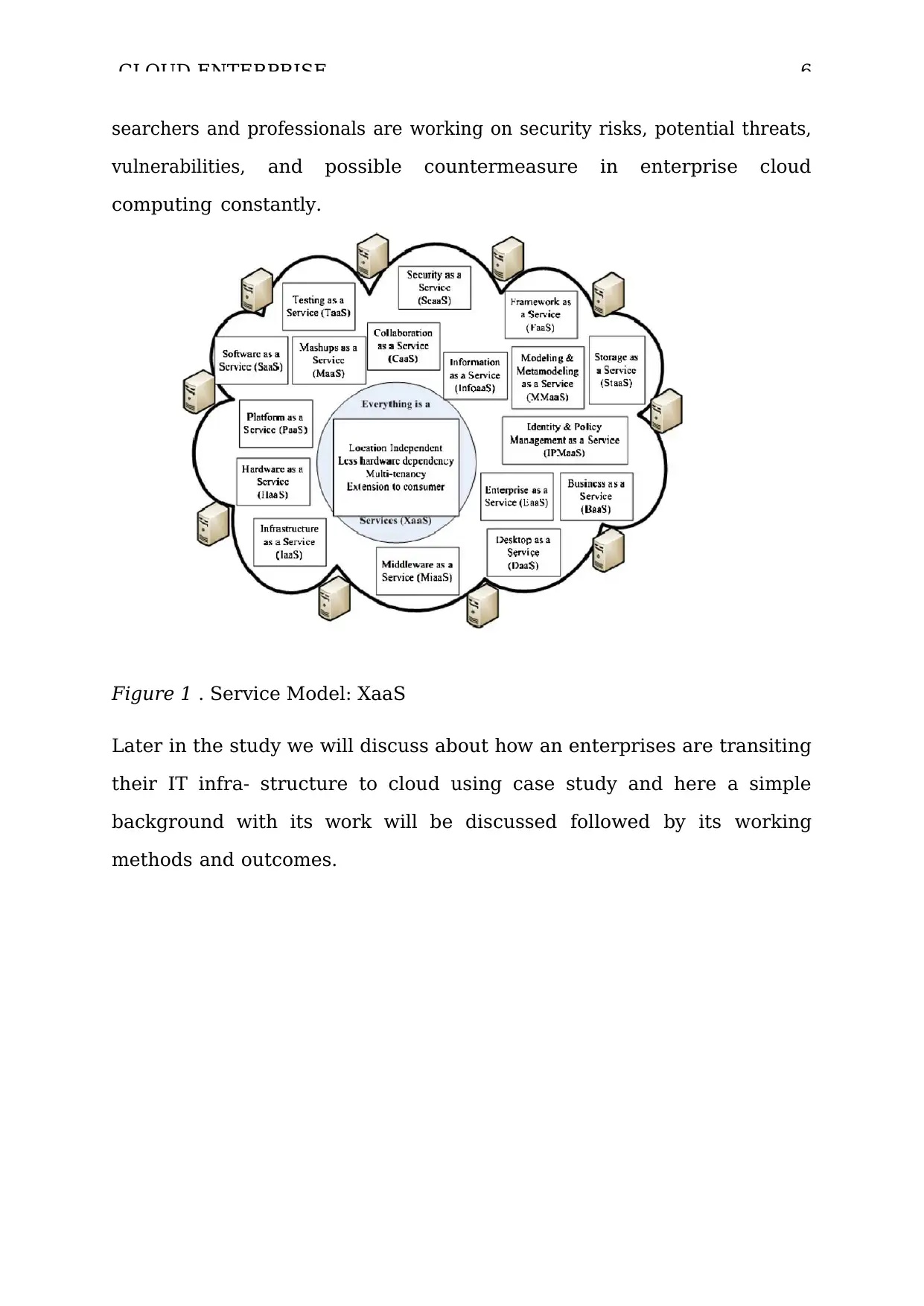
Figure 2 . Service Requirements: Provider, Enterprise, User
As shown in figure mentioned above, the cloud architectural
requirements are basically divided into 3 parts:
• Provider Requirements: Here visionary architecture must be
designed to sup- port infrastructure. To provide dynamic services
Architectural Requirements of Cloud Computing for
Enterprises
Since we have already discussed that cloud computing has a wide range
of scope in different areas such as enterprise level to academics too.
These days cloud computing is more used for study and research purpose
for the advancements For the purpose of making it generalized usage there
needs to be a requirement of standard API’s i.e., application program
interface and standard usage guide for the developers and architects but
the development of standard factors might take place of challenges in
making cloud computing reliable, scalable, interoperability.
Figure 2 . Service Requirements: Provider, Enterprise, User
As shown in figure mentioned above, the cloud architectural
requirements are basically divided into 3 parts:
• Provider Requirements: Here visionary architecture must be
designed to sup- port infrastructure. To provide dynamic services
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD-ENTERPRISE 8
and virtualized services is also one
and virtualized services is also one

CLOUD-ENTERPRISE 9
of the goal for provider requirements. In this architecture approach
storage, data security and cost model must be taken care of.
• Enterprise Requirements: With consideration to Enterprise point of
view, where an infrstructure on which many data and information are
dependent in a large or small scale enterprise. Thus the cloud
architecture design must be secure i.e., QoS- enabled, scalable and
inter-operable that provide efficient business management services.
• User Requirements: For user architectural design must be design
such that is easy for operations to users. Interface must be simple
and must adopt the user requirements easily, it must have
capabilities of learning that can answer the service level
agreements, pricing and metering. Security should be considered as
a highest priority so as to make system stable and usability of cloud
to users.
Enterprise Requirements
As per some survey in 2012 (Pring, Brown, Frank, Hayward, & Leong,
2009), 20% of enterprises email communication will be hosted on cloud.
Thus the potential of cloud based opportunities are increasing. Every
enterprises should checklist their requirements according to environment
and resources required keeping all points into consideration from
technology to resources requirements. To understand the new system, the
outsource resource must be used for survey and getting in touch with
specs discussed by experts or analysts. For an enterprise (Rimal, Jukan,
Katsaros, & Goeleven, 2011), every resources must be re-verified with
their requirements with care and attention from security of data to data
mobility and ownership. Here we will discuss about security, data
governing for business outcomes management and other skill
requirements.
of the goal for provider requirements. In this architecture approach
storage, data security and cost model must be taken care of.
• Enterprise Requirements: With consideration to Enterprise point of
view, where an infrstructure on which many data and information are
dependent in a large or small scale enterprise. Thus the cloud
architecture design must be secure i.e., QoS- enabled, scalable and
inter-operable that provide efficient business management services.
• User Requirements: For user architectural design must be design
such that is easy for operations to users. Interface must be simple
and must adopt the user requirements easily, it must have
capabilities of learning that can answer the service level
agreements, pricing and metering. Security should be considered as
a highest priority so as to make system stable and usability of cloud
to users.
Enterprise Requirements
As per some survey in 2012 (Pring, Brown, Frank, Hayward, & Leong,
2009), 20% of enterprises email communication will be hosted on cloud.
Thus the potential of cloud based opportunities are increasing. Every
enterprises should checklist their requirements according to environment
and resources required keeping all points into consideration from
technology to resources requirements. To understand the new system, the
outsource resource must be used for survey and getting in touch with
specs discussed by experts or analysts. For an enterprise (Rimal, Jukan,
Katsaros, & Goeleven, 2011), every resources must be re-verified with
their requirements with care and attention from security of data to data
mobility and ownership. Here we will discuss about security, data
governing for business outcomes management and other skill
requirements.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CLOUD-ENTERPRISE 1
There are four types of cloud deployment techniques and all these
techniques have its own key responsibilities and pitfalls, they are as
follows:
• Public Cloud: This is expensive but less than private cloud for
procuring its deployment. It has pre developed Standard API’s to
make data seamlessly. For
There are four types of cloud deployment techniques and all these
techniques have its own key responsibilities and pitfalls, they are as
follows:
• Public Cloud: This is expensive but less than private cloud for
procuring its deployment. It has pre developed Standard API’s to
make data seamlessly. For
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD-ENTERPRISE 1
this type of cloud deployment target audience are large as well as
SMEs. The main pitfall is that the security is low and system may get
affected by malicious attacks like DDoS attacks. The legal issue of
this cloud is boundaries for data storage.
• Private Cloud: It has the highest priority at the security and control
of resources over internet. Thus it is basically targeted at Large
organizations and corporations. For migration, Standard API’s are
required between public, community and hybrid. It is the most
expensive deployment techniques.
• Community Cloud: This deployment technique is the cheapest
among all other technique and it requires Standard API’s for
migration to specific community. It has low priority to security thus
audience is small SME’s.
• Hybrid Cloud: This model is meant for cost savings and audience is
multiple internals and/or external providers. For the easy movement
of data standard API’s are needed to be developed.Issue here in this
deployment type is app compatibility. Highly limited resources and
boundary for data storage.
In Enterprises, not only technology is considered but the economical
factors are also considered in procuring any new system. The use of
cloud computing is benefitial eco- nomically too as enterprises will have
choice to usage and billing as per usage cycle which is also known as
pay-per-use model. The major disadvantage of cloud computing is lack of
cost based transparency.
For cloud data must be governed properly with security, since there are
many political as well as geographical issues. When data is traversed out
of any organization then the risk of threat or attack is increasing and the
question of data security for any organ- ization rises. The cloud users
must be protected against "data lock-in". Vendor must be able to lock the
this type of cloud deployment target audience are large as well as
SMEs. The main pitfall is that the security is low and system may get
affected by malicious attacks like DDoS attacks. The legal issue of
this cloud is boundaries for data storage.
• Private Cloud: It has the highest priority at the security and control
of resources over internet. Thus it is basically targeted at Large
organizations and corporations. For migration, Standard API’s are
required between public, community and hybrid. It is the most
expensive deployment techniques.
• Community Cloud: This deployment technique is the cheapest
among all other technique and it requires Standard API’s for
migration to specific community. It has low priority to security thus
audience is small SME’s.
• Hybrid Cloud: This model is meant for cost savings and audience is
multiple internals and/or external providers. For the easy movement
of data standard API’s are needed to be developed.Issue here in this
deployment type is app compatibility. Highly limited resources and
boundary for data storage.
In Enterprises, not only technology is considered but the economical
factors are also considered in procuring any new system. The use of
cloud computing is benefitial eco- nomically too as enterprises will have
choice to usage and billing as per usage cycle which is also known as
pay-per-use model. The major disadvantage of cloud computing is lack of
cost based transparency.
For cloud data must be governed properly with security, since there are
many political as well as geographical issues. When data is traversed out
of any organization then the risk of threat or attack is increasing and the
question of data security for any organ- ization rises. The cloud users
must be protected against "data lock-in". Vendor must be able to lock the

CLOUD-ENTERPRISE 1
data and control all information. Due to lack of interoperability and
standardization efforts, providers doesnot guarantee for security when user
wants to move data/information from one cloud to another
Data migration means distributing information to different users in most
efficient way.such as data streaming, VoIP,etc,. While data distribution
there are different goals to acheive
data and control all information. Due to lack of interoperability and
standardization efforts, providers doesnot guarantee for security when user
wants to move data/information from one cloud to another
Data migration means distributing information to different users in most
efficient way.such as data streaming, VoIP,etc,. While data distribution
there are different goals to acheive
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



