ITC568 Cloud Privacy: Risk Assessment for Charity's SaaS Migration
VerifiedAdded on 2023/06/08
|14
|2709
|69
Report
AI Summary
This report provides a risk assessment plan for a community-based charity in California considering a migration to a SaaS cloud service. It identifies potential security, privacy, and ethical issues related to employee data, digital identity, and data sensitivity. The report analyzes threats such as unauthorized CSP use, API vulnerabilities, and data breaches, evaluating their severity and likelihood. It also addresses privacy concerns like vendor lock-in and loss of control over data governance. The assessment includes a review of digital identity issues, provider solution risks, and data sensitivity, with recommendations for mitigating these risks and ensuring compliance with data protection regulations during the migration process. This document is available on Desklib, a platform offering study tools and solved assignments for students.

Running head: CLOUD PRIVACY AND SECURITY
Cloud Privacy and Security
Name of the Student
Name of the University
Author note
Cloud Privacy and Security
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CLOUD PRIVACY AND SECURITY
Executive summery
The security and privacy of the cloud networking holds the authenticity and the efficiency of
the cloud network. In this presented a risk assessment plan for a community based charity
regarding their changes in cloud based operation and service utility for a charity organisation
situated in California, USA. There will be potential issues before as well as after the
migration to SaaS application. The security, privacy and ethical considerations have been
found to be the major components of the risk and treats assessment.
Executive summery
The security and privacy of the cloud networking holds the authenticity and the efficiency of
the cloud network. In this presented a risk assessment plan for a community based charity
regarding their changes in cloud based operation and service utility for a charity organisation
situated in California, USA. There will be potential issues before as well as after the
migration to SaaS application. The security, privacy and ethical considerations have been
found to be the major components of the risk and treats assessment.

2CLOUD PRIVACY AND SECURITY
Table of Content
Introduction................................................................................................................................4
Body:..........................................................................................................................................4
Security of Employee Data....................................................................................................5
Privacy of Employee Data.....................................................................................................7
Digital Identity Issues..........................................................................................................10
Provider Solution Issues.......................................................................................................10
Data Sensitivity....................................................................................................................11
Conclusion................................................................................................................................12
References:...............................................................................................................................13
Table of Content
Introduction................................................................................................................................4
Body:..........................................................................................................................................4
Security of Employee Data....................................................................................................5
Privacy of Employee Data.....................................................................................................7
Digital Identity Issues..........................................................................................................10
Provider Solution Issues.......................................................................................................10
Data Sensitivity....................................................................................................................11
Conclusion................................................................................................................................12
References:...............................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CLOUD PRIVACY AND SECURITY
Introduction
The Cloud computing system is the most dynamic and advanced networking system
in this era of digitalisation that allows the users to operate the data and information in a
virtual storage based system with customised accessibility and encryptions. However the
security and privacy of the cloud networking holds the authenticity and the efficiency of the
cloud network (awsstatic.com., 2018). This report presents a risk assessment plan for a
community based charity regarding their changes in cloud based operation and service utility.
The aim of this paper is to guide the HR area of the organisation in order to develop a
sustainable privacy and security policy list while collaborating with a third party vendor for
SaaS cloud service.
At the initial stage, the paper has found some essential treats and security factors
regarding information transaction of HR Database. There the potential issues after the
migration to SaaS application have been analysed. The privacy consideration of the 500
employees has been also taken into consideration where the result of any hazard has been
also discussed. The security compliance of digital identity system and the operation and
location SaaS service provider have been also examined. Moreover, the risk analysis report
has been delivered a data sensitivity analysis by considering the HR operation of the charity
has been presented with ethical and legal compliances it order to migrate the system to SaaS
third party operator safely.
Body:
Because of the huge geographical distance between the vendor operation of SaaS cloud and
the charity organisation, there will be potential issues before as well as after the migration to
Introduction
The Cloud computing system is the most dynamic and advanced networking system
in this era of digitalisation that allows the users to operate the data and information in a
virtual storage based system with customised accessibility and encryptions. However the
security and privacy of the cloud networking holds the authenticity and the efficiency of the
cloud network (awsstatic.com., 2018). This report presents a risk assessment plan for a
community based charity regarding their changes in cloud based operation and service utility.
The aim of this paper is to guide the HR area of the organisation in order to develop a
sustainable privacy and security policy list while collaborating with a third party vendor for
SaaS cloud service.
At the initial stage, the paper has found some essential treats and security factors
regarding information transaction of HR Database. There the potential issues after the
migration to SaaS application have been analysed. The privacy consideration of the 500
employees has been also taken into consideration where the result of any hazard has been
also discussed. The security compliance of digital identity system and the operation and
location SaaS service provider have been also examined. Moreover, the risk analysis report
has been delivered a data sensitivity analysis by considering the HR operation of the charity
has been presented with ethical and legal compliances it order to migrate the system to SaaS
third party operator safely.
Body:
Because of the huge geographical distance between the vendor operation of SaaS cloud and
the charity organisation, there will be potential issues before as well as after the migration to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CLOUD PRIVACY AND SECURITY
SaaS application. Within these vulnerable issues, the security, privacy and ethical
considerations are the major components of the risk and treats assessment.
Security of Employee Data
In existing cloud server of the community based charity organisation contains 50 x86
and 64 bit server based on the Windows Server 2008 R2 to handle the file processing,
database handling storing service. The type of physical networking based intranet system
comprise of many physical risks, such as data loss due to physical damage, broken server
efficiency due to operational glitch, distorted indexing system due to lack of updated
synchronisations (Owasp.org., 2018). In the existing networking system of the charity
company, the Personal Identity Information or PII data of clients is connected under the
supervision of the “on-premises” intranet system. The existing Identification handling is
mostly depended on the 10 Red Hat Enterprise Linux 5 servers. Apart from that, the existing
system is not compatible for advanced DBMS operation and SQL server inscription that can
create significant boundaries in networking capability.
After the migration to the SaaS service provider the data control and security
operation will highly vulnerable due to the amount of dependency on encryption policy and
strategy of the service provider. In other words if a attacker can have access on the cloud
operation of the vendor company, the HR and other Database of the charity organisation will
be also exposed to the hacker. In this case, the data will be transferred in multi-duplex
connection between California and India. Therefore, the transmitted data package could be
incomplete, deleted or redundant due to the server issues in the data transition traffic
(nsw.gov.au., 2018). The following table will explain the severity of the risks and threat to
Security of employee data due to the migration:
Threat Risk Severity
SaaS application. Within these vulnerable issues, the security, privacy and ethical
considerations are the major components of the risk and treats assessment.
Security of Employee Data
In existing cloud server of the community based charity organisation contains 50 x86
and 64 bit server based on the Windows Server 2008 R2 to handle the file processing,
database handling storing service. The type of physical networking based intranet system
comprise of many physical risks, such as data loss due to physical damage, broken server
efficiency due to operational glitch, distorted indexing system due to lack of updated
synchronisations (Owasp.org., 2018). In the existing networking system of the charity
company, the Personal Identity Information or PII data of clients is connected under the
supervision of the “on-premises” intranet system. The existing Identification handling is
mostly depended on the 10 Red Hat Enterprise Linux 5 servers. Apart from that, the existing
system is not compatible for advanced DBMS operation and SQL server inscription that can
create significant boundaries in networking capability.
After the migration to the SaaS service provider the data control and security
operation will highly vulnerable due to the amount of dependency on encryption policy and
strategy of the service provider. In other words if a attacker can have access on the cloud
operation of the vendor company, the HR and other Database of the charity organisation will
be also exposed to the hacker. In this case, the data will be transferred in multi-duplex
connection between California and India. Therefore, the transmitted data package could be
incomplete, deleted or redundant due to the server issues in the data transition traffic
(nsw.gov.au., 2018). The following table will explain the severity of the risks and threat to
Security of employee data due to the migration:
Threat Risk Severity
5CLOUD PRIVACY AND SECURITY
Unauthorised Use of CSP On-demand self service provisioning can
enable the cloud service provider to use
CSP without consent of client IT
(Shadow IT) which also is a subject
under the ethical considerations of cloud
network
Low
API vulnerability Exposure of CSP to the service provider
can cause the loss of Internet-Accessible
Management APIs
Medium
Unauthorised surveillance of
Hackers
Since the data will be stored and operated
in another location, the hackers can break
the peer to peer transaction system and
scan the entire data packages and
encryptions
High
Table 1: Security assessment table
Source: (Created by author)
The following matrix represents the severity of the security factor due to the migration from
in-house network system to SaaS cloud based system. The attached numerical representations
represents the weight of the Impact and security factors respectively:
Overall Security Risk Severity
Impact
HIGH(2) Unauthorised
Use of CSP
Unauthorised
surveillance of
Hackers
LOW (1) API
vulnerability
LOW (1) HIGH(2)
Likelihood
From the Risk Severity assessment matrix it is clear that Unauthorised surveillance of
Hackers can cause the severity index of 4. Therefore, for security issues it would be the cheif
Unauthorised Use of CSP On-demand self service provisioning can
enable the cloud service provider to use
CSP without consent of client IT
(Shadow IT) which also is a subject
under the ethical considerations of cloud
network
Low
API vulnerability Exposure of CSP to the service provider
can cause the loss of Internet-Accessible
Management APIs
Medium
Unauthorised surveillance of
Hackers
Since the data will be stored and operated
in another location, the hackers can break
the peer to peer transaction system and
scan the entire data packages and
encryptions
High
Table 1: Security assessment table
Source: (Created by author)
The following matrix represents the severity of the security factor due to the migration from
in-house network system to SaaS cloud based system. The attached numerical representations
represents the weight of the Impact and security factors respectively:
Overall Security Risk Severity
Impact
HIGH(2) Unauthorised
Use of CSP
Unauthorised
surveillance of
Hackers
LOW (1) API
vulnerability
LOW (1) HIGH(2)
Likelihood
From the Risk Severity assessment matrix it is clear that Unauthorised surveillance of
Hackers can cause the severity index of 4. Therefore, for security issues it would be the cheif
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CLOUD PRIVACY AND SECURITY
concern of the charity organisation. Unauthorised Use of CSP scored 2 in the severity level
where the API vulnerability has only 1 level of severity.
Privacy of Employee Data
The existing intranet operation of the organisation could have minimum privacy issue
due to the self dependent network model which is also called “on-premises” networking
system. In this system the breach of data security system through external hacker can only
effect the privacy of the organisational HR database and Auditing system. The organisation is
using 10 Red Hat Enterprise Linux 5 servers to service public facing Web pages, which is a
high secure and advanced server system for outwards server operations, such as official
website auditing, social page developing, virtual forum management and others.
After the migration, there are some additional issues that can occur due to the change in data
operational environment and third party file handling methods. The compatibility of the
existing database structure and indexing system and the new SaaS based cloud operator or
service provider should be taken into account to avoid such risks (nist.gov., 2018).
concern of the charity organisation. Unauthorised Use of CSP scored 2 in the severity level
where the API vulnerability has only 1 level of severity.
Privacy of Employee Data
The existing intranet operation of the organisation could have minimum privacy issue
due to the self dependent network model which is also called “on-premises” networking
system. In this system the breach of data security system through external hacker can only
effect the privacy of the organisational HR database and Auditing system. The organisation is
using 10 Red Hat Enterprise Linux 5 servers to service public facing Web pages, which is a
high secure and advanced server system for outwards server operations, such as official
website auditing, social page developing, virtual forum management and others.
After the migration, there are some additional issues that can occur due to the change in data
operational environment and third party file handling methods. The compatibility of the
existing database structure and indexing system and the new SaaS based cloud operator or
service provider should be taken into account to avoid such risks (nist.gov., 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CLOUD PRIVACY AND SECURITY
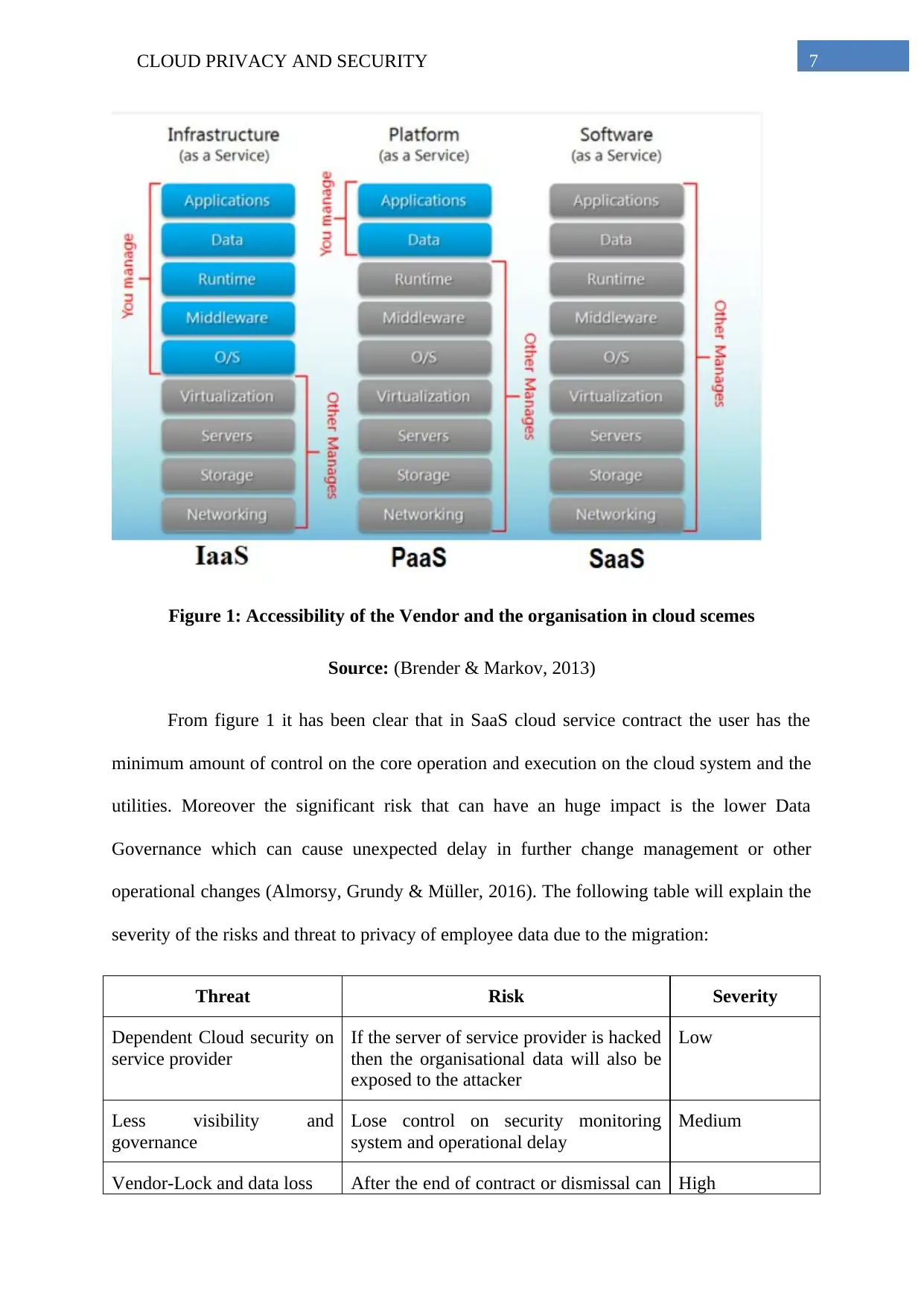
Figure 1: Accessibility of the Vendor and the organisation in cloud scemes
Source: (Brender & Markov, 2013)
From figure 1 it has been clear that in SaaS cloud service contract the user has the
minimum amount of control on the core operation and execution on the cloud system and the
utilities. Moreover the significant risk that can have an huge impact is the lower Data
Governance which can cause unexpected delay in further change management or other
operational changes (Almorsy, Grundy & Müller, 2016). The following table will explain the
severity of the risks and threat to privacy of employee data due to the migration:
Threat Risk Severity
Dependent Cloud security on
service provider
If the server of service provider is hacked
then the organisational data will also be
exposed to the attacker
Low
Less visibility and
governance
Lose control on security monitoring
system and operational delay
Medium
Vendor-Lock and data loss After the end of contract or dismissal can High
Figure 1: Accessibility of the Vendor and the organisation in cloud scemes
Source: (Brender & Markov, 2013)
From figure 1 it has been clear that in SaaS cloud service contract the user has the
minimum amount of control on the core operation and execution on the cloud system and the
utilities. Moreover the significant risk that can have an huge impact is the lower Data
Governance which can cause unexpected delay in further change management or other
operational changes (Almorsy, Grundy & Müller, 2016). The following table will explain the
severity of the risks and threat to privacy of employee data due to the migration:
Threat Risk Severity
Dependent Cloud security on
service provider
If the server of service provider is hacked
then the organisational data will also be
exposed to the attacker
Low
Less visibility and
governance
Lose control on security monitoring
system and operational delay
Medium
Vendor-Lock and data loss After the end of contract or dismissal can High
8CLOUD PRIVACY AND SECURITY
cause temporary or permanent data lock
on organisation’s cloud storage
Table 3: Privacy assessment table
Source: (Created by author)
The following matrix represents the severity of the privacy factors due to the migration rom
in house network system to SaaS cloud based system. The attached numerical representations
represents the weight of the Impact and security factors respectively :
Overall Privacy Risk Severity
Impact
HIGH (2) Vendor-Lock
and data loss
LOW (1)
Dependent
Cloud security
on service
provider
Less visibility and
governance
LOW (1) HIGH (2)
Likelihood
From the Risk Severity assessment matrix it is clear that there is no serious issues that
can cause the severity index of 4. Vendor-Lock and data loss and Less visibility and
governance scored 2 in the severity level where the Dependent Cloud security on service
provider has only 1 level of severity. Therefore, for the privacy of the HR data base the
charity organisation has to be highly concerned about the Vendor-Lock and data loss issues
and Less visibility and governance issues.
cause temporary or permanent data lock
on organisation’s cloud storage
Table 3: Privacy assessment table
Source: (Created by author)
The following matrix represents the severity of the privacy factors due to the migration rom
in house network system to SaaS cloud based system. The attached numerical representations
represents the weight of the Impact and security factors respectively :
Overall Privacy Risk Severity
Impact
HIGH (2) Vendor-Lock
and data loss
LOW (1)
Dependent
Cloud security
on service
provider
Less visibility and
governance
LOW (1) HIGH (2)
Likelihood
From the Risk Severity assessment matrix it is clear that there is no serious issues that
can cause the severity index of 4. Vendor-Lock and data loss and Less visibility and
governance scored 2 in the severity level where the Dependent Cloud security on service
provider has only 1 level of severity. Therefore, for the privacy of the HR data base the
charity organisation has to be highly concerned about the Vendor-Lock and data loss issues
and Less visibility and governance issues.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9CLOUD PRIVACY AND SECURITY
Digital Identity Issues
As per the decision of the management, each employee will use individual charity
digital ID to authenticate in the cloud network for HR and Performance management system.
In case of any failure in index management and database crash the details of PII records can
be lost permanently (Rittinghouse & Ransome, 2016). Internally the digital ID will be
generated by the charity's Active Directory instance and will be available for log-in to
internal authentication and authorisation in vendor provided SaaS service. Therefore, after
generating the ID the authentication details will be sent to the SaaS service provider, which is
again can initiate third party surveillance on id. The following table describes the risks and
threats associated with the PII and Digital identity issue in for migrating SaaS cloud system:
Threat Risk Severity
Unauthorised surveillance on
end to end connectivity
During the PII database transfer to the vendor
company the details can be accessed by any
unauthorised entity
High
Vendor-Lock After the termination of contract the vender
company can temporary lock the PII access
High
Table 1: PII issues assessment table
Source: (Created by author)
Provider Solution Issues
Employee database and PII will be uploaded from the charity daily at 12:00 AEST.
The data will be transmitted from California, USA to the Bangalore, India. the During the
PII database and the HR database transition from the charity to the cloud service provider,
which is situated in India, the organisation must confirm the end to end encryption is secure
and out of reach for any external surveillance system (Hashizume et al., 2013). The
Digital Identity Issues
As per the decision of the management, each employee will use individual charity
digital ID to authenticate in the cloud network for HR and Performance management system.
In case of any failure in index management and database crash the details of PII records can
be lost permanently (Rittinghouse & Ransome, 2016). Internally the digital ID will be
generated by the charity's Active Directory instance and will be available for log-in to
internal authentication and authorisation in vendor provided SaaS service. Therefore, after
generating the ID the authentication details will be sent to the SaaS service provider, which is
again can initiate third party surveillance on id. The following table describes the risks and
threats associated with the PII and Digital identity issue in for migrating SaaS cloud system:
Threat Risk Severity
Unauthorised surveillance on
end to end connectivity
During the PII database transfer to the vendor
company the details can be accessed by any
unauthorised entity
High
Vendor-Lock After the termination of contract the vender
company can temporary lock the PII access
High
Table 1: PII issues assessment table
Source: (Created by author)
Provider Solution Issues
Employee database and PII will be uploaded from the charity daily at 12:00 AEST.
The data will be transmitted from California, USA to the Bangalore, India. the During the
PII database and the HR database transition from the charity to the cloud service provider,
which is situated in India, the organisation must confirm the end to end encryption is secure
and out of reach for any external surveillance system (Hashizume et al., 2013). The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CLOUD PRIVACY AND SECURITY
performance management information is another essential data packages that will be
transferred in this end to end connection where the data required to be verified by terminal
security server. Any failures of data transmission or incomplete transmission due to server
problem and security boundaries by national server security several dilemmas can be occur.
Threat Risk Severity
Data loss and incomplete
transition
PII data or information can be loosed or
incomplete due to server issues causing
repeated login failure of authorised user
Moderate
Cyber security Server
authentication failure
Due to the Cyber security authentication in
international data transaction, some encrypted
data can blocked
Low
Data Sensitivity
Data sensitivity refers the type of the data and to what extent the data is sensitive for
the company and the society as well. The initial ethical issues of the charity organisations
have been considered as the privacy section. Being a charity organisation, they operate large
amount of confidential data about the donor, receiver and the agencies (Beloglazov, Abawajy
& Buyya, 2012). All this information is strongly related to HR database and the resource
allocation system of HR management. Sometimes, the cloud service provider uses the client’s
information for partial business and promotional activity, which is also known as shadow IT
as discussed earlier. Therefore, in order to prevent these safety and security breaches the
charity and the SaaS vendor both should follow the WofG (Whole of Government) data
protection regulations and compliances (Fernando, Loke & Rahayu, 2013). The WofG uses a
Authorisation Kit known as ATO to protect the ethical issues and concerns of both client as
well as host side.
performance management information is another essential data packages that will be
transferred in this end to end connection where the data required to be verified by terminal
security server. Any failures of data transmission or incomplete transmission due to server
problem and security boundaries by national server security several dilemmas can be occur.
Threat Risk Severity
Data loss and incomplete
transition
PII data or information can be loosed or
incomplete due to server issues causing
repeated login failure of authorised user
Moderate
Cyber security Server
authentication failure
Due to the Cyber security authentication in
international data transaction, some encrypted
data can blocked
Low
Data Sensitivity
Data sensitivity refers the type of the data and to what extent the data is sensitive for
the company and the society as well. The initial ethical issues of the charity organisations
have been considered as the privacy section. Being a charity organisation, they operate large
amount of confidential data about the donor, receiver and the agencies (Beloglazov, Abawajy
& Buyya, 2012). All this information is strongly related to HR database and the resource
allocation system of HR management. Sometimes, the cloud service provider uses the client’s
information for partial business and promotional activity, which is also known as shadow IT
as discussed earlier. Therefore, in order to prevent these safety and security breaches the
charity and the SaaS vendor both should follow the WofG (Whole of Government) data
protection regulations and compliances (Fernando, Loke & Rahayu, 2013). The WofG uses a
Authorisation Kit known as ATO to protect the ethical issues and concerns of both client as
well as host side.

11CLOUD PRIVACY AND SECURITY
Conclusion
From the above discussion it is clear that the security and privacy of the cloud
networking holds the authenticity and the efficiency of the cloud network. The above report
presented a risk assessment plan for a community based charity regarding their changes in
cloud based operation and service utility for a charity organisation situated in California,
USA. Due to the huge geographical distance between the vendor operation of SaaS cloud and
the charity organisation, there will be potential issues before as well as after the migration to
SaaS application. The security, privacy and ethical considerations are the major components
of the risk and treats assessment.
From the above analysis and risk assessment, it has been found that the charity
organisation should ensure the end to end data encryption within the vendor and the
community server. The server protocol must be the major concern of this issue. As per the
Security Risk Severity assessment matrix Unauthorised surveillance of Hackers can cause the
severity index should be the chief concern of the charity organisation. On the other hand,
according to the Privacy Risk Severity assessment matrix, the charity organisation of
California should be careful about Vendor-Lock and data loss as well as the Less visibility
and governance before and after the agreement with the vendor company.
Conclusion
From the above discussion it is clear that the security and privacy of the cloud
networking holds the authenticity and the efficiency of the cloud network. The above report
presented a risk assessment plan for a community based charity regarding their changes in
cloud based operation and service utility for a charity organisation situated in California,
USA. Due to the huge geographical distance between the vendor operation of SaaS cloud and
the charity organisation, there will be potential issues before as well as after the migration to
SaaS application. The security, privacy and ethical considerations are the major components
of the risk and treats assessment.
From the above analysis and risk assessment, it has been found that the charity
organisation should ensure the end to end data encryption within the vendor and the
community server. The server protocol must be the major concern of this issue. As per the
Security Risk Severity assessment matrix Unauthorised surveillance of Hackers can cause the
severity index should be the chief concern of the charity organisation. On the other hand,
according to the Privacy Risk Severity assessment matrix, the charity organisation of
California should be careful about Vendor-Lock and data loss as well as the Less visibility
and governance before and after the agreement with the vendor company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


