Analysis of Cloud Computing Architecture, Privacy, and Security
VerifiedAdded on 2022/12/30
|9
|2174
|97
Report
AI Summary
This report provides a comprehensive overview of cloud computing privacy and security. It begins by defining cloud computing and then delves into its architecture, including front-end and back-end components. The report highlights the importance of cloud computing, emphasizing its efficiency, flexibility, and strategic advantages. It then explores the implementation process, including analyzing business workflows and developing implementation strategies. A significant portion of the report addresses ethical and technical issues, such as privacy, compliance, security vulnerabilities, and sustainability concerns. It offers practical solutions, including managing user access, monitoring user activities, data backup strategies, and employee training on anti-phishing techniques. The findings summarize the architecture, importance, implementation, ethical issues, and proposed solutions. The report concludes by emphasizing the importance of understanding cloud computing privacy and security for both personal and professional applications, and the need to learn about the technical aspects for data protection. The report uses references to support the concepts discussed.

Cloud Privacy and
Security
Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
Concepts of cloud privacy and security is discussed in this report where architecture of
cloud computing is analysed, observation of the important of cloud computing, interpretation of
implementation of cloud computing, examining ethical or technical issues or challenges in cloud
computing, determining the solutions of such challenges related to cloud computing and deep
study of findings with a proper conclusion in context of cloud privacy and security.
Concepts of cloud privacy and security is discussed in this report where architecture of
cloud computing is analysed, observation of the important of cloud computing, interpretation of
implementation of cloud computing, examining ethical or technical issues or challenges in cloud
computing, determining the solutions of such challenges related to cloud computing and deep
study of findings with a proper conclusion in context of cloud privacy and security.

Table of Contents
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................1
Cloud computing architecture................................................................................................1
Importance of cloud computing..............................................................................................2
Implementation of cloud computing......................................................................................3
Ethical or technical issues or challenges................................................................................4
Solutions.................................................................................................................................4
FINDINGS.......................................................................................................................................5
CONCLUSION................................................................................................................................5
References:.......................................................................................................................................6
INTRODUCTION...........................................................................................................................1
MAIN BODY...................................................................................................................................1
Cloud computing architecture................................................................................................1
Importance of cloud computing..............................................................................................2
Implementation of cloud computing......................................................................................3
Ethical or technical issues or challenges................................................................................4
Solutions.................................................................................................................................4
FINDINGS.......................................................................................................................................5
CONCLUSION................................................................................................................................5
References:.......................................................................................................................................6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INTRODUCTION
Cloud computing is defined as the availability of computer resources on demand by the
user for various purposes like storing the data and the computing power. In other words, it is
considered as the data centres over the internet which is accessible to the respective users (Cook,
Robinson, Ferrag and Janicke, 2018). The following discussions are made on the architecture,
importance, implementation, ethical or technical issues and solutions in context of cloud
computing privacy and security.
MAIN BODY
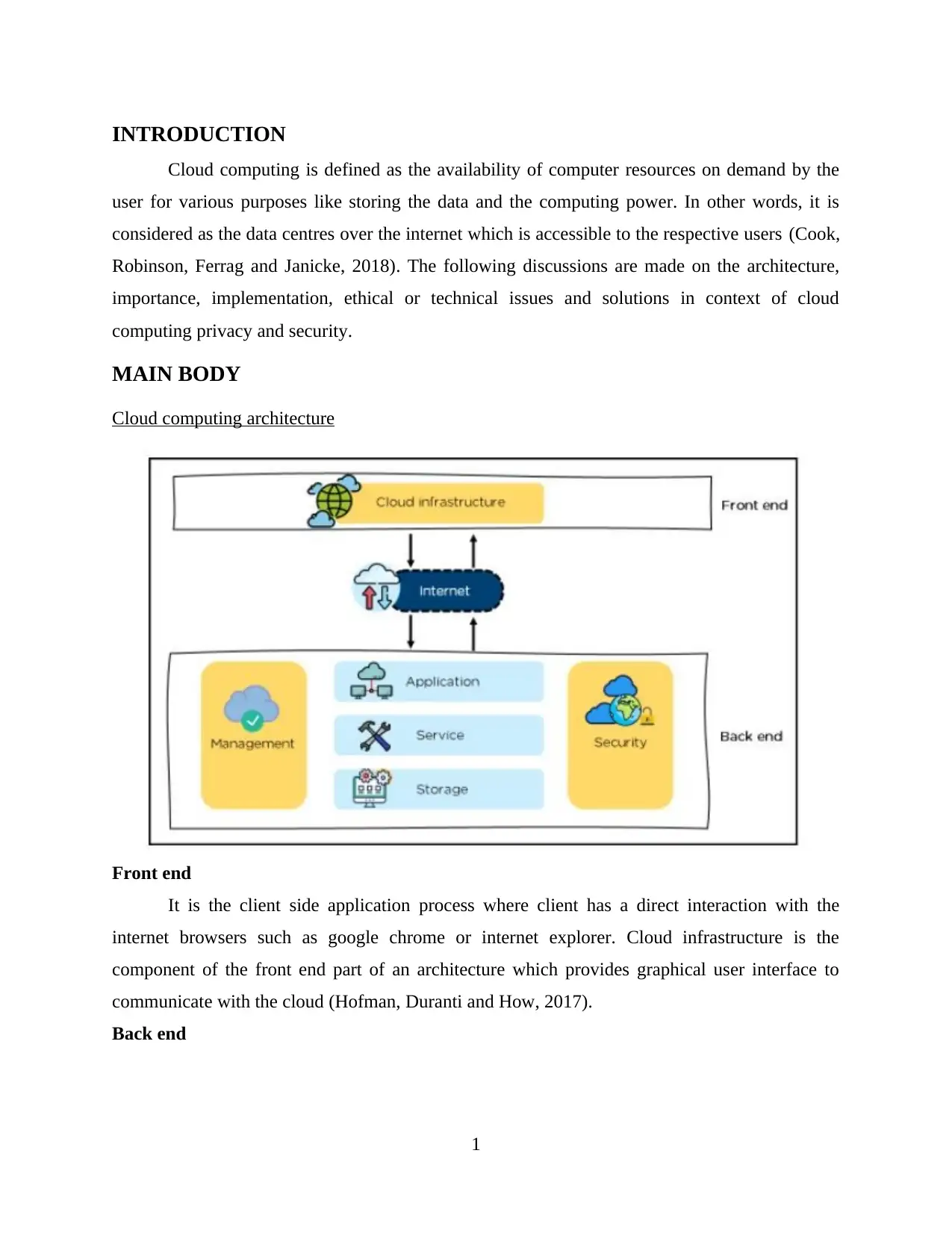
Cloud computing architecture
Front end
It is the client side application process where client has a direct interaction with the
internet browsers such as google chrome or internet explorer. Cloud infrastructure is the
component of the front end part of an architecture which provides graphical user interface to
communicate with the cloud (Hofman, Duranti and How, 2017).
Back end
1
Cloud computing is defined as the availability of computer resources on demand by the
user for various purposes like storing the data and the computing power. In other words, it is
considered as the data centres over the internet which is accessible to the respective users (Cook,
Robinson, Ferrag and Janicke, 2018). The following discussions are made on the architecture,
importance, implementation, ethical or technical issues and solutions in context of cloud
computing privacy and security.
MAIN BODY
Cloud computing architecture
Front end
It is the client side application process where client has a direct interaction with the
internet browsers such as google chrome or internet explorer. Cloud infrastructure is the
component of the front end part of an architecture which provides graphical user interface to
communicate with the cloud (Hofman, Duranti and How, 2017).
Back end
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

It is the server side applications process where all the internal processes are performed
like data storage. It follows the request from the user and process it back to them with a result. It
has several components, discusses are as follows:
Application
It is considered as any application or a software that a client wants to access for it's
personal or any professional purpose.
Service
It is considered as the analysing and providing of a types of a service that a client wants
to access for it's operations (Kalaiprasath, Elankavi and Udayakumar, 2017).
Storage
It stores and manages the large amount of data like files, folders, videos, software, images
and many more over the internet so as to process the user's request of any service they are
demanding for.
Management
It is responsible for the management of the coordination between various components of
front end and back end services that is to be provided to the user.
Security
It is responsible to build up the security services of the data to the client in the back end
part of the architecture.
Internet
It is considered as the medium or communication channel through which all the request
and results are being processed for the user (Kong, Lei and Ma, 2018).
Importance of cloud computing
Efficiency
Cloud computing creates efficiency in business operations because it provides smooth
accessibility and facilities to access the data and information as requested for the business needs
and requirements, it assist in savings of the cost because storing every important data on the
internet saves the external cost and it makes more cost effective. Moreover, it supports in the
proper security of any confidential data and if in case it lost or corrupted the it has a solution of
recovery options as well to maintain the efficiency in an organization.
Flexibility
2
like data storage. It follows the request from the user and process it back to them with a result. It
has several components, discusses are as follows:
Application
It is considered as any application or a software that a client wants to access for it's
personal or any professional purpose.
Service
It is considered as the analysing and providing of a types of a service that a client wants
to access for it's operations (Kalaiprasath, Elankavi and Udayakumar, 2017).
Storage
It stores and manages the large amount of data like files, folders, videos, software, images
and many more over the internet so as to process the user's request of any service they are
demanding for.
Management
It is responsible for the management of the coordination between various components of
front end and back end services that is to be provided to the user.
Security
It is responsible to build up the security services of the data to the client in the back end
part of the architecture.
Internet
It is considered as the medium or communication channel through which all the request
and results are being processed for the user (Kong, Lei and Ma, 2018).
Importance of cloud computing
Efficiency
Cloud computing creates efficiency in business operations because it provides smooth
accessibility and facilities to access the data and information as requested for the business needs
and requirements, it assist in savings of the cost because storing every important data on the
internet saves the external cost and it makes more cost effective. Moreover, it supports in the
proper security of any confidential data and if in case it lost or corrupted the it has a solution of
recovery options as well to maintain the efficiency in an organization.
Flexibility
2

Cloud computing creates flexibility in business operations because it provides scalability
as due to the workload on the business, it supports them by having the scalable nature to the
business, it also provides the facility in selecting the required tool as per the needs of the
business so that request can be processed in an appropriate manner. Moreover, it also provides
the various cloud options thereby giving the flexibility to the user and more controlling choices
to user and can use their power of control in accessing of the data (Mollah, Azad and Vasilakos,
2017).
Strategic edge
Cloud computing creates the strategic edge in business operations because it helps in
increment of the productivity, assist in software updates automatically, gives more competitive
advantages and supports in increment in collaboration with an organization for proper
management of data and computer resources.
Implementation of cloud computing
Analyse the business workflow and applications
This is the first step of implementation of the cloud computing which states that it is
necessary to analyse the proper work flow of the business operations and applications and
services provided by the company or even for the self use so that requirement can be identified
easily.
Strategy to implement
This is the second step of implementation of the cloud computing which states that it is
necessary to develop or build up the strategies for execution of the cloud computing because it
not not as easy job, it requires appropriate tactic to be successful in implementation. It has two
major parts, they are as follows:
Interpret cost and benefits
It is one of the part to develop the strategy that is the analysing or interpreting the cost to
implement of the cloud computing according to the needs and requirements of the business and
how it can benefit the firm in several ways. It is essential to determine that the cost which is
planned must be effective and not be more than the benefit it is giving to the company (Rana,
Kubbo and Jayabalan, 2017).
Building up IT roadmap
3
as due to the workload on the business, it supports them by having the scalable nature to the
business, it also provides the facility in selecting the required tool as per the needs of the
business so that request can be processed in an appropriate manner. Moreover, it also provides
the various cloud options thereby giving the flexibility to the user and more controlling choices
to user and can use their power of control in accessing of the data (Mollah, Azad and Vasilakos,
2017).
Strategic edge
Cloud computing creates the strategic edge in business operations because it helps in
increment of the productivity, assist in software updates automatically, gives more competitive
advantages and supports in increment in collaboration with an organization for proper
management of data and computer resources.
Implementation of cloud computing
Analyse the business workflow and applications
This is the first step of implementation of the cloud computing which states that it is
necessary to analyse the proper work flow of the business operations and applications and
services provided by the company or even for the self use so that requirement can be identified
easily.
Strategy to implement
This is the second step of implementation of the cloud computing which states that it is
necessary to develop or build up the strategies for execution of the cloud computing because it
not not as easy job, it requires appropriate tactic to be successful in implementation. It has two
major parts, they are as follows:
Interpret cost and benefits
It is one of the part to develop the strategy that is the analysing or interpreting the cost to
implement of the cloud computing according to the needs and requirements of the business and
how it can benefit the firm in several ways. It is essential to determine that the cost which is
planned must be effective and not be more than the benefit it is giving to the company (Rana,
Kubbo and Jayabalan, 2017).
Building up IT roadmap
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

It is necessary to create the roadmap of the implementation of the cloud computing
because it clears the picture of cost, time and scalability of the resources so that that company
can implement it in a very potential manner.
Ethical or technical issues or challenges
Privacy
There is a issue in a privacy of the data stored on the internet because any one can access
the data or information stored with or without permission. That is why it can be said that there is
always an issue of privacy of data in an organization (Sahmim and Gharsellaoui, 2017).
Compliance
There are various acts, rules, regulations and norms to use the cloud computing but to
adopt such acts are very expensive and not at all cost effective. Therefore, it is considered as
difficult to use cloud computing with or without adopting such acts.
Security
Services which are offered by cloud are always with the help of third party and it is
difficult to trust another person outside the business with regarding to the data and information
stored because business don't know that what type of a person can access it's data.
Sustainability
Cloud computing has a negative affect on the sustainability of an environment due to the
large amount of heat generation and huge amount of electricity used by it. Therefore it directly
affects the environment sustainability (Sridhar and Sriram, 2017).
Solutions
Managing access of the user
It can be one of the solution that the business can provide access to only those employees
who are trustable and whom they believe that those people will not at all leak their private
information and not interrupt their information security at any cost. Therefore, company has to
provide the access to some users so that it can be safe to use the cloud computing.
Monitoring user activities
Company has given the access to their employees so it is important for the business to
monitor all the activities that the employee is performing on the internet with the data because
there are the chances that the most trustable person also can leak the information for the personal
4
because it clears the picture of cost, time and scalability of the resources so that that company
can implement it in a very potential manner.
Ethical or technical issues or challenges
Privacy
There is a issue in a privacy of the data stored on the internet because any one can access
the data or information stored with or without permission. That is why it can be said that there is
always an issue of privacy of data in an organization (Sahmim and Gharsellaoui, 2017).
Compliance
There are various acts, rules, regulations and norms to use the cloud computing but to
adopt such acts are very expensive and not at all cost effective. Therefore, it is considered as
difficult to use cloud computing with or without adopting such acts.
Security
Services which are offered by cloud are always with the help of third party and it is
difficult to trust another person outside the business with regarding to the data and information
stored because business don't know that what type of a person can access it's data.
Sustainability
Cloud computing has a negative affect on the sustainability of an environment due to the
large amount of heat generation and huge amount of electricity used by it. Therefore it directly
affects the environment sustainability (Sridhar and Sriram, 2017).
Solutions
Managing access of the user
It can be one of the solution that the business can provide access to only those employees
who are trustable and whom they believe that those people will not at all leak their private
information and not interrupt their information security at any cost. Therefore, company has to
provide the access to some users so that it can be safe to use the cloud computing.
Monitoring user activities
Company has given the access to their employees so it is important for the business to
monitor all the activities that the employee is performing on the internet with the data because
there are the chances that the most trustable person also can leak the information for the personal
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

use that is why it is essential to monitor the activities of the users (Stergiou, Psannis, Gupta and
Ishibashi, 2018).
Backing up
This solution is for the safety for the company because if any data loss is faced by the
firm than the backed up data can help the firm to restore all the lost data that is why backing up
of all the data and information on a regular basis supports the company in safety of it's resources.
Employee training on anti phishing
It is important to train the employees about hacking and phishing methods so that they
can take preventive measures accordingly and can save their data from hacking and major loss.
Therefore employee training is necessary in an organization (Yang, Chen, Chen and Du, 2018).
FINDINGS
It is analysed that the architecture of cloud computing has majorly three parts that is front
end, back end and the internet. It has importance of efficiency, flexibility and strategic edge.
Implementation process includes analysing the business workflow and applications and strategy
to implement. Ethical and technical issue includes privacy, compliance, security and
sustainability. Solution involves managing access of the user, monitoring user activities, backing
up and employee training on anti phishing (Zhou, Cao, Dong and Vasilakos, 2017).
CONCLUSION
It is concluded that the cloud computing privacy and security is important to study so that
basic or deep knowledge can be gained of such a trend based topic. It is essential to learn about
the technical things over internet so that it can be applied either in any organization or personally
as well for proper privacy and security of large and confidential data. That is why this report
significantly covers the basic and deep concepts of cloud computing which includes the learnings
of it's architecture that how it actually works, it's importance in real life personally or
professionally, it's implementation process that how it can be implemented, it's ethical and
technical issues with appropriate solutions associated with it.
5
Ishibashi, 2018).
Backing up
This solution is for the safety for the company because if any data loss is faced by the
firm than the backed up data can help the firm to restore all the lost data that is why backing up
of all the data and information on a regular basis supports the company in safety of it's resources.
Employee training on anti phishing
It is important to train the employees about hacking and phishing methods so that they
can take preventive measures accordingly and can save their data from hacking and major loss.
Therefore employee training is necessary in an organization (Yang, Chen, Chen and Du, 2018).
FINDINGS
It is analysed that the architecture of cloud computing has majorly three parts that is front
end, back end and the internet. It has importance of efficiency, flexibility and strategic edge.
Implementation process includes analysing the business workflow and applications and strategy
to implement. Ethical and technical issue includes privacy, compliance, security and
sustainability. Solution involves managing access of the user, monitoring user activities, backing
up and employee training on anti phishing (Zhou, Cao, Dong and Vasilakos, 2017).
CONCLUSION
It is concluded that the cloud computing privacy and security is important to study so that
basic or deep knowledge can be gained of such a trend based topic. It is essential to learn about
the technical things over internet so that it can be applied either in any organization or personally
as well for proper privacy and security of large and confidential data. That is why this report
significantly covers the basic and deep concepts of cloud computing which includes the learnings
of it's architecture that how it actually works, it's importance in real life personally or
professionally, it's implementation process that how it can be implemented, it's ethical and
technical issues with appropriate solutions associated with it.
5

References:
Books and Journals
Cook, A., Robinson, M., Ferrag, M.A. and Janicke, H., 2018. Internet of cloud: Security and
privacy issues. In Cloud Computing for Optimization: Foundations, Applications, and
Challenges (pp. 271-301). Springer, Cham.
Hofman, D., Duranti, L. and How, E., 2017. Trust in the balance: Data protection laws as tools
for privacy and security in the cloud. Algorithms. 10(2). p.47.
Kalaiprasath, R., Elankavi, R. and Udayakumar, D.R., 2017. Cloud. security and compliance-A
semantic approach in end to end security. International Journal Of Mechanical
Engineering And Technology (Ijmet). 8(5). pp.987-994.
Kong, W., Lei, Y. and Ma, J., 2018. Data security and privacy information challenges in cloud
computing. International Journal of Computational Science and Engineering. 16(3).
pp.215-218.
Mollah, M.B., Azad, M.A.K. and Vasilakos, A., 2017. Security and privacy challenges in mobile
cloud computing: Survey and way ahead. Journal of Network and Computer
Applications, 84, pp.38-54.
Rana, M.E., Kubbo, M. and Jayabalan, M., 2017. Privacy and Security Challenge Towards
Cloud-Based Access Control. Asian. Journal of Information Technology. 16(2-5).
pp.274-281.
Sahmim, S. and Gharsellaoui, H., 2017. Privacy and security in internet-based computing: cloud
computing, internet of things, cloud of things: a review. Procedia computer
science, 112, pp.1516-1522.
Sridhar, J. and Sriram, M., 2017. Cloud privacy preserving for dynamic groups. International
Journal of Pure and Applied Mathematics. 116(8). pp.117-121.
Stergiou, C., Psannis, K.E., Gupta, B.B. and Ishibashi, Y., 2018. Security, privacy & efficiency
of sustainable cloud computing for big data & IoT. Sustainable Computing: Informatics
and Systems, 19, pp.174-184.
Yang, Y., Chen, X., Chen, H. and Du, X., 2018. Improving privacy and security in decentralizing
multi-authority attribute-based encryption in cloud computing. IEEE Access, 6,
pp.18009-18021.
Zhou, J., Cao, Z., Dong, X. and Vasilakos, A.V., 2017. Security and privacy for cloud-based IoT:
Challenges. IEEE Communications Magazine. 55(1). pp.26-33.
6
Books and Journals
Cook, A., Robinson, M., Ferrag, M.A. and Janicke, H., 2018. Internet of cloud: Security and
privacy issues. In Cloud Computing for Optimization: Foundations, Applications, and
Challenges (pp. 271-301). Springer, Cham.
Hofman, D., Duranti, L. and How, E., 2017. Trust in the balance: Data protection laws as tools
for privacy and security in the cloud. Algorithms. 10(2). p.47.
Kalaiprasath, R., Elankavi, R. and Udayakumar, D.R., 2017. Cloud. security and compliance-A
semantic approach in end to end security. International Journal Of Mechanical
Engineering And Technology (Ijmet). 8(5). pp.987-994.
Kong, W., Lei, Y. and Ma, J., 2018. Data security and privacy information challenges in cloud
computing. International Journal of Computational Science and Engineering. 16(3).
pp.215-218.
Mollah, M.B., Azad, M.A.K. and Vasilakos, A., 2017. Security and privacy challenges in mobile
cloud computing: Survey and way ahead. Journal of Network and Computer
Applications, 84, pp.38-54.
Rana, M.E., Kubbo, M. and Jayabalan, M., 2017. Privacy and Security Challenge Towards
Cloud-Based Access Control. Asian. Journal of Information Technology. 16(2-5).
pp.274-281.
Sahmim, S. and Gharsellaoui, H., 2017. Privacy and security in internet-based computing: cloud
computing, internet of things, cloud of things: a review. Procedia computer
science, 112, pp.1516-1522.
Sridhar, J. and Sriram, M., 2017. Cloud privacy preserving for dynamic groups. International
Journal of Pure and Applied Mathematics. 116(8). pp.117-121.
Stergiou, C., Psannis, K.E., Gupta, B.B. and Ishibashi, Y., 2018. Security, privacy & efficiency
of sustainable cloud computing for big data & IoT. Sustainable Computing: Informatics
and Systems, 19, pp.174-184.
Yang, Y., Chen, X., Chen, H. and Du, X., 2018. Improving privacy and security in decentralizing
multi-authority attribute-based encryption in cloud computing. IEEE Access, 6,
pp.18009-18021.
Zhou, J., Cao, Z., Dong, X. and Vasilakos, A.V., 2017. Security and privacy for cloud-based IoT:
Challenges. IEEE Communications Magazine. 55(1). pp.26-33.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




