Cloud Privacy and Security Report: Employee Data Risk Assessment
VerifiedAdded on 2023/06/10
|26
|7380
|354
Report
AI Summary
This report comprehensively examines cloud privacy and security, particularly concerning employee data. It begins with an introduction to cloud computing, highlighting its benefits and various service models such as SaaS, PaaS, and IaaS. The report then delves into existing and new threats to the security and privacy of employee data, including issues of confidentiality, integrity, and availability, along with the severity of these risks. It also explores the implications of digital identity issues, provider-related concerns, and data sensitivity, offering a detailed analysis of potential vulnerabilities and challenges. The report discusses the existing threats like confidentiality, integrity, and availability, along with the new threats like hacking of sensitive employee data and illegal local network access from cloud services. By addressing these aspects, the report aims to provide a thorough understanding of the critical elements involved in securing employee data within a cloud environment and discusses the potential risks and issues involved.

Running head: CLOUD PRIVACY AND SECURITY
Cloud Privacy and Security
Name of the Student
Name of the University
Author’s Note
Cloud Privacy and Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CLOUD PRIVACY AND SECURITY
Table of Contents
Introduction......................................................................................................................................2
Cloud Computing.............................................................................................................................2
1.1 Existing threats to security of employee data............................................................................5
1.2 New threats to security of employee data..................................................................................7
1.3 Severity of risk to security employee data.................................................................................8
2.1 Existing threats to privacy of employee data.............................................................................9
2.2 New Threats to privacy of employee data...............................................................................11
2.3 Severity of risk to privacy employee data...............................................................................12
3. Digital Identity issues................................................................................................................13
4. Provider Issues...........................................................................................................................15
5. Data Sensitivity Issues...............................................................................................................17
Conclusion.....................................................................................................................................19
References......................................................................................................................................21
CLOUD PRIVACY AND SECURITY
Table of Contents
Introduction......................................................................................................................................2
Cloud Computing.............................................................................................................................2
1.1 Existing threats to security of employee data............................................................................5
1.2 New threats to security of employee data..................................................................................7
1.3 Severity of risk to security employee data.................................................................................8
2.1 Existing threats to privacy of employee data.............................................................................9
2.2 New Threats to privacy of employee data...............................................................................11
2.3 Severity of risk to privacy employee data...............................................................................12
3. Digital Identity issues................................................................................................................13
4. Provider Issues...........................................................................................................................15
5. Data Sensitivity Issues...............................................................................................................17
Conclusion.....................................................................................................................................19
References......................................................................................................................................21

2
CLOUD PRIVACY AND SECURITY
Introduction
Cloud computing has been emerging in large context in the IT field. The services
provided by the cloud computing have been beneficial for every organization in the market. The
cloud has been providing platform for various advance technologies in the market. The cloud
computing has been creating opportunities for various organizations in their growth in the
market. Various cloud computing service models including SaaS, PaaS and IaaS have been
implementing in the organization for developing business in the market (Almorsy, Grundy &
Muller 2016). The use of cloud computing services have beneficial for the organization. The
services are flexible and easily accessible for any part of the world. Cloud computing has been
providing services to both online and offline services in the companies. This technology has
enabled on-demand services to the customers and users of the cloud. Therefore this has gained
more attention in market. Cloud computing is mainly used for the data storage purposes. Large
amount of data and information of cloud users are stored over the cloud storage through internet.
Therefore, security of data and information is an important aspect for the cloud computing
services and providers. There have been many cases of cyber breaches in various companies.
This report deals with cyber issues in the Charity that helps in improving
accommodation, mental health and training to society. The security and privacy of employee
data, digital identity issues, and provider solution issues and data sensitivity have been discussed
in the report. A proper risks management process has been followed with the cloud deployment
models.
CLOUD PRIVACY AND SECURITY
Introduction
Cloud computing has been emerging in large context in the IT field. The services
provided by the cloud computing have been beneficial for every organization in the market. The
cloud has been providing platform for various advance technologies in the market. The cloud
computing has been creating opportunities for various organizations in their growth in the
market. Various cloud computing service models including SaaS, PaaS and IaaS have been
implementing in the organization for developing business in the market (Almorsy, Grundy &
Muller 2016). The use of cloud computing services have beneficial for the organization. The
services are flexible and easily accessible for any part of the world. Cloud computing has been
providing services to both online and offline services in the companies. This technology has
enabled on-demand services to the customers and users of the cloud. Therefore this has gained
more attention in market. Cloud computing is mainly used for the data storage purposes. Large
amount of data and information of cloud users are stored over the cloud storage through internet.
Therefore, security of data and information is an important aspect for the cloud computing
services and providers. There have been many cases of cyber breaches in various companies.
This report deals with cyber issues in the Charity that helps in improving
accommodation, mental health and training to society. The security and privacy of employee
data, digital identity issues, and provider solution issues and data sensitivity have been discussed
in the report. A proper risks management process has been followed with the cloud deployment
models.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CLOUD PRIVACY AND SECURITY
Cloud Computing
Cloud Computing is a concept that has helped in storing data and information of
organizations and users over the internet. This services have helped in providing a variety of
benefits to the organizations related to the storage of the data and information (Saa, Moscoso-
Zea, Costales, & Luján-Mora, 2017). Cloud computing have helped in maintaining a flexible and
accessible approach to the cloud users. There are various deployment models of the cloud
computing that have been discussed below:
Public Cloud: Public clouds refers to providing services to an organization and users
publically. The access privacy of the cloud services has been public in this case. Therefore, data
and information stored in this model will be publically accessed to other memory in the
organizations. Therefore, the security level of the model has been very low (Puthal, Sahoo &
Swain, 2015). The physical infrastructure of this model is designed by the cloud service
provider in the market. However, it helps in providing a large space for storing data and
information over the cloud.
Private Cloud: Private clouds that are designated to private organizations are providing a
single tenant service to users. Therefore, any assigned users will be able to access stored data
and information in cloud. The use of the private cloud has been used for storing legal and
private documents of the companies over the cloud. Therefore, the security level of the cloud
model is higher than other models of cloud (Singh & Chatterjee, 2017). The limited access to
people have helped in providing a security articles in the cloud ensuring the security in data ad
information stored in it. However, this model provides a standardized protection to data with
respect to scalability and size. This model provide complete control over the data and
information stored in the cloud.
CLOUD PRIVACY AND SECURITY
Cloud Computing
Cloud Computing is a concept that has helped in storing data and information of
organizations and users over the internet. This services have helped in providing a variety of
benefits to the organizations related to the storage of the data and information (Saa, Moscoso-
Zea, Costales, & Luján-Mora, 2017). Cloud computing have helped in maintaining a flexible and
accessible approach to the cloud users. There are various deployment models of the cloud
computing that have been discussed below:
Public Cloud: Public clouds refers to providing services to an organization and users
publically. The access privacy of the cloud services has been public in this case. Therefore, data
and information stored in this model will be publically accessed to other memory in the
organizations. Therefore, the security level of the model has been very low (Puthal, Sahoo &
Swain, 2015). The physical infrastructure of this model is designed by the cloud service
provider in the market. However, it helps in providing a large space for storing data and
information over the cloud.
Private Cloud: Private clouds that are designated to private organizations are providing a
single tenant service to users. Therefore, any assigned users will be able to access stored data
and information in cloud. The use of the private cloud has been used for storing legal and
private documents of the companies over the cloud. Therefore, the security level of the cloud
model is higher than other models of cloud (Singh & Chatterjee, 2017). The limited access to
people have helped in providing a security articles in the cloud ensuring the security in data ad
information stored in it. However, this model provides a standardized protection to data with
respect to scalability and size. This model provide complete control over the data and
information stored in the cloud.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CLOUD PRIVACY AND SECURITY
Hybrid cloud: Hybrid cloud include both public and private cloud in the market.
Therefore, it has both attributes of private and public cloud models. It allows transitive
information exchange with portability. However, with the use of hybrid cloud, service provider’s
helps in using third party interdependence in the cloud services (Rittinghouse & Ransome,
2016). The maintenance of the hybrid cloud have been easy than there two cloud models.
There are various cloud service delivery models that are discussed below:
Software as a Service (SaaS): Cloud users and there companies have been running
applications and software over the cloud in the SaaS. This service helped in providing access to
several applications and programs that are high in cost. This service helps in providing it in rent
on monthly basis. Cloud users abs organization can use software and applications as per their
need and there is no need to buy an expensive application (Saa, Moscoso-Zea, Costales, &
Luján-Mora, 2017). Therefore, it has helped in minimizing the initial cost of users and
organizations in the market. The use if the SaaS has been used by most if the companies
including the Charity. Cloud users do not have to maintain and control software and programs in
the SaaS. This model helps in minimizing the cost of the software including operating system,
network, servers and storage.
Platform as a Service (PaaS): This model describes about a layer of software and
environment that helps in maintaining a deployed area for the users over the cloud. This model
is responsible for providing platforms for deployment of various applications in the organization
(Modi et al. 2013). Various applications including Java, Python and .net. PaaS providers helps in
offering predefined operating systems and application servers, including LAMP (Linux, Apache,
MySql and PHP) platform, restricted J2EE, and Ruby.
CLOUD PRIVACY AND SECURITY
Hybrid cloud: Hybrid cloud include both public and private cloud in the market.
Therefore, it has both attributes of private and public cloud models. It allows transitive
information exchange with portability. However, with the use of hybrid cloud, service provider’s
helps in using third party interdependence in the cloud services (Rittinghouse & Ransome,
2016). The maintenance of the hybrid cloud have been easy than there two cloud models.
There are various cloud service delivery models that are discussed below:
Software as a Service (SaaS): Cloud users and there companies have been running
applications and software over the cloud in the SaaS. This service helped in providing access to
several applications and programs that are high in cost. This service helps in providing it in rent
on monthly basis. Cloud users abs organization can use software and applications as per their
need and there is no need to buy an expensive application (Saa, Moscoso-Zea, Costales, &
Luján-Mora, 2017). Therefore, it has helped in minimizing the initial cost of users and
organizations in the market. The use if the SaaS has been used by most if the companies
including the Charity. Cloud users do not have to maintain and control software and programs in
the SaaS. This model helps in minimizing the cost of the software including operating system,
network, servers and storage.
Platform as a Service (PaaS): This model describes about a layer of software and
environment that helps in maintaining a deployed area for the users over the cloud. This model
is responsible for providing platforms for deployment of various applications in the organization
(Modi et al. 2013). Various applications including Java, Python and .net. PaaS providers helps in
offering predefined operating systems and application servers, including LAMP (Linux, Apache,
MySql and PHP) platform, restricted J2EE, and Ruby.

5
CLOUD PRIVACY AND SECURITY
Infrastructure as a Service (IaaS): This model helps in providing basic storage and
computing capabilities over the network (Albaroodi, Manickam & Singh, 2014). Different
networks, systems, servers and other computing equipment are provided by the cloud model on
rent. Therefore, the buying cost of the infrastructure becomes low.
1.1 Existing threats to security of employee data
Various organizations including The Charity used to upload their documents and data
over the internet. The use of cloud computing has been helping in storing professional and
private of the organization. The employee data and information of the Charity has been
uploaded over the cloud. The company is also using the SaaS for getting benefit of the services.
However, there have been various security issues in the employee data of the Charity. There are
various protocols that ensure data security over the cloud including FTP, HTTPS and SCP
(Ramachandra, Iftikhar & Khan, 2017). However, these protocols are not able to maintain
security of the employee data. The cloud security threats have been already faced by the Charity
in order to secure employee data over the cloud. There are several existing issues related to the
employee data in the Charity. These security issues have been discussed below:
Confidentiality: This is one of existing cloud security issues related to the employee data.
This threat mainly occur inside the organization. The services are flexible and easily accessible
for any part of the world. This threat has been already existing in the Charity. The delivery of
cloud services are hampered by this threat. There are various middles that can be affected by this
security issue including the SaaS. Software and programs provided by the SaaS has been leaked
out if the company that have been creating loss to the business (Kshetri, 2013). The employee
data has been leaked by the insider attack causing loss of privacy of employee. There are various
security breaches due to the confidential breach. The use of cloud computing services have
CLOUD PRIVACY AND SECURITY
Infrastructure as a Service (IaaS): This model helps in providing basic storage and
computing capabilities over the network (Albaroodi, Manickam & Singh, 2014). Different
networks, systems, servers and other computing equipment are provided by the cloud model on
rent. Therefore, the buying cost of the infrastructure becomes low.
1.1 Existing threats to security of employee data
Various organizations including The Charity used to upload their documents and data
over the internet. The use of cloud computing has been helping in storing professional and
private of the organization. The employee data and information of the Charity has been
uploaded over the cloud. The company is also using the SaaS for getting benefit of the services.
However, there have been various security issues in the employee data of the Charity. There are
various protocols that ensure data security over the cloud including FTP, HTTPS and SCP
(Ramachandra, Iftikhar & Khan, 2017). However, these protocols are not able to maintain
security of the employee data. The cloud security threats have been already faced by the Charity
in order to secure employee data over the cloud. There are several existing issues related to the
employee data in the Charity. These security issues have been discussed below:
Confidentiality: This is one of existing cloud security issues related to the employee data.
This threat mainly occur inside the organization. The services are flexible and easily accessible
for any part of the world. This threat has been already existing in the Charity. The delivery of
cloud services are hampered by this threat. There are various middles that can be affected by this
security issue including the SaaS. Software and programs provided by the SaaS has been leaked
out if the company that have been creating loss to the business (Kshetri, 2013). The employee
data has been leaked by the insider attack causing loss of privacy of employee. There are various
security breaches due to the confidential breach. The use of cloud computing services have
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CLOUD PRIVACY AND SECURITY
beneficial for the organization. Cloud computing has been providing services to both online and
offline services in the companies. Various confidential data is uploaded over the cloud storage
that has been accessed by unauthorized users and breached out in the market. Therefore, this has
been causing financial loss to the organization. Data leakage has been major issue in the cloud
computing environment as data and information in the public cloud is accessed by anyone in the
organization.
Figure 1: Security traits
(Source: Aljawarneh, Alawneh, & Jaradat, 2017, pp.387)
Integrity: The integrity of information and data has been another issues that has been
faced by the organization in recent years. The use of the data segregation in organization has
been craving problems for the organization. Various cloud hosting environments including SaaS
has been configured for sharing computing resource among all other employee included in the
cloud server. Therefore, there can be breaching of data from Cloud database system (Lin &
Liao, 2017). This has been a great threat to data integrity of the cloud storage. The remote of data
and information has been provided to all of the employees including the public cloud services.
The use to the Cloud can be done by any of the employees. This create high chances of breaches
CLOUD PRIVACY AND SECURITY
beneficial for the organization. Cloud computing has been providing services to both online and
offline services in the companies. Various confidential data is uploaded over the cloud storage
that has been accessed by unauthorized users and breached out in the market. Therefore, this has
been causing financial loss to the organization. Data leakage has been major issue in the cloud
computing environment as data and information in the public cloud is accessed by anyone in the
organization.
Figure 1: Security traits
(Source: Aljawarneh, Alawneh, & Jaradat, 2017, pp.387)
Integrity: The integrity of information and data has been another issues that has been
faced by the organization in recent years. The use of the data segregation in organization has
been craving problems for the organization. Various cloud hosting environments including SaaS
has been configured for sharing computing resource among all other employee included in the
cloud server. Therefore, there can be breaching of data from Cloud database system (Lin &
Liao, 2017). This has been a great threat to data integrity of the cloud storage. The remote of data
and information has been provided to all of the employees including the public cloud services.
The use to the Cloud can be done by any of the employees. This create high chances of breaches
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CLOUD PRIVACY AND SECURITY
out the integrity of data in the database (Alassafi et al., 2017). The modification of data is
another problem in the data integrity issue. The administrator of the cloud server has the super
control of the data and information accessed and controlled by the employee. Therefore, the use
of data administrator is look after the security breaches in the cloud computing. However, there
has been lack in the security protocols of the Charity. However, implementation of access
controls has been accessed by cloud enterprises. The access to the database has been creating a
major problems in the integrity if the data and information in the organization.
Availability: The cloud provider has been increasing responsibility for implementing
change management in the cloud computing of the company. This might help in providing
proper approaching the delivery of services if the cloud in the company (Saxena, 2013).
Therefore, the use if the change management in the cloud computing have been uncres8ng the
availability of the data in company. The access of the data has been increased to the employees
that has been causing problems in the cloud computing services.
1.2 New threats to security of employee data
Existing threats in the Charity has been discussed in above section. However, there are
various problems that can be arise in the Charity reject to the employee data. The cloud
company has been creating several opportunity for the employee to store their data over the
internet. However, there has been various cyber-attacks in the computing resources in the office
connected with the internet including mobile storage (Goyal, 2014). However, according to the
Cloud Security Alliance (CSA), there has been several cyber threats might be emerging in the
Charity related ti the data security in the cloud computing.
CLOUD PRIVACY AND SECURITY
out the integrity of data in the database (Alassafi et al., 2017). The modification of data is
another problem in the data integrity issue. The administrator of the cloud server has the super
control of the data and information accessed and controlled by the employee. Therefore, the use
of data administrator is look after the security breaches in the cloud computing. However, there
has been lack in the security protocols of the Charity. However, implementation of access
controls has been accessed by cloud enterprises. The access to the database has been creating a
major problems in the integrity if the data and information in the organization.
Availability: The cloud provider has been increasing responsibility for implementing
change management in the cloud computing of the company. This might help in providing
proper approaching the delivery of services if the cloud in the company (Saxena, 2013).
Therefore, the use if the change management in the cloud computing have been uncres8ng the
availability of the data in company. The access of the data has been increased to the employees
that has been causing problems in the cloud computing services.
1.2 New threats to security of employee data
Existing threats in the Charity has been discussed in above section. However, there are
various problems that can be arise in the Charity reject to the employee data. The cloud
company has been creating several opportunity for the employee to store their data over the
internet. However, there has been various cyber-attacks in the computing resources in the office
connected with the internet including mobile storage (Goyal, 2014). However, according to the
Cloud Security Alliance (CSA), there has been several cyber threats might be emerging in the
Charity related ti the data security in the cloud computing.

8
CLOUD PRIVACY AND SECURITY
Hacking of sensitive employee data: Cloud computing has been helping in providing a
great platform for storing data and information of employee and the user. Therefore, there is
huge possibility of cyber-attacks over the cloud server. Hacking of cloud network has been
common in recent times. Therefore, there is a huge risk of data loss of employee form the cloud
storage (Shei, Mouratidis & Delaney, 2017).
Illegal local network access from cloud services: Most CSP's luckily do furnish antiviruses
and firewalls' however with developing idea of online risks; a bargained cloud can be a close for end
clients and suppliers both. The public cloud has been accessed by all the members in the cloud.
Therefore, security of data and information in the cloud has been hampered by the accessibility
factor. Therefore, the security of data is not good in the public cloud. The Charity has been using
Public cloud in SaaS solution. Therefore, all data and information over the cloud is not safe for the
organization. The employee data stored over the public cloud can be accessed by ether members in
the cloud. This might create a serious issue in the organization related to data loss. The use of the
public cloud has helped in reducing complexity in the cloud services adopted by the Charity.
Stolen information from cloud computing employees: Various cases have been reported
regarding the stolen of data form the cloud server. Hackers are targeting the cloud server as there
are a lot of employee data stored in it. This has been creating an issue in the CSP and observed
at cloud.
Adherence and compliance of providers to security standards: The Cloud Security
Alliance (CSA) helps Cloud suppliers by giving key suggestions for keeping identified risks that
all CSP's face, a considerable lot of which are specified as every risk (Garg & Babbar, 2017).
CLOUD PRIVACY AND SECURITY
Hacking of sensitive employee data: Cloud computing has been helping in providing a
great platform for storing data and information of employee and the user. Therefore, there is
huge possibility of cyber-attacks over the cloud server. Hacking of cloud network has been
common in recent times. Therefore, there is a huge risk of data loss of employee form the cloud
storage (Shei, Mouratidis & Delaney, 2017).
Illegal local network access from cloud services: Most CSP's luckily do furnish antiviruses
and firewalls' however with developing idea of online risks; a bargained cloud can be a close for end
clients and suppliers both. The public cloud has been accessed by all the members in the cloud.
Therefore, security of data and information in the cloud has been hampered by the accessibility
factor. Therefore, the security of data is not good in the public cloud. The Charity has been using
Public cloud in SaaS solution. Therefore, all data and information over the cloud is not safe for the
organization. The employee data stored over the public cloud can be accessed by ether members in
the cloud. This might create a serious issue in the organization related to data loss. The use of the
public cloud has helped in reducing complexity in the cloud services adopted by the Charity.
Stolen information from cloud computing employees: Various cases have been reported
regarding the stolen of data form the cloud server. Hackers are targeting the cloud server as there
are a lot of employee data stored in it. This has been creating an issue in the CSP and observed
at cloud.
Adherence and compliance of providers to security standards: The Cloud Security
Alliance (CSA) helps Cloud suppliers by giving key suggestions for keeping identified risks that
all CSP's face, a considerable lot of which are specified as every risk (Garg & Babbar, 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
CLOUD PRIVACY AND SECURITY
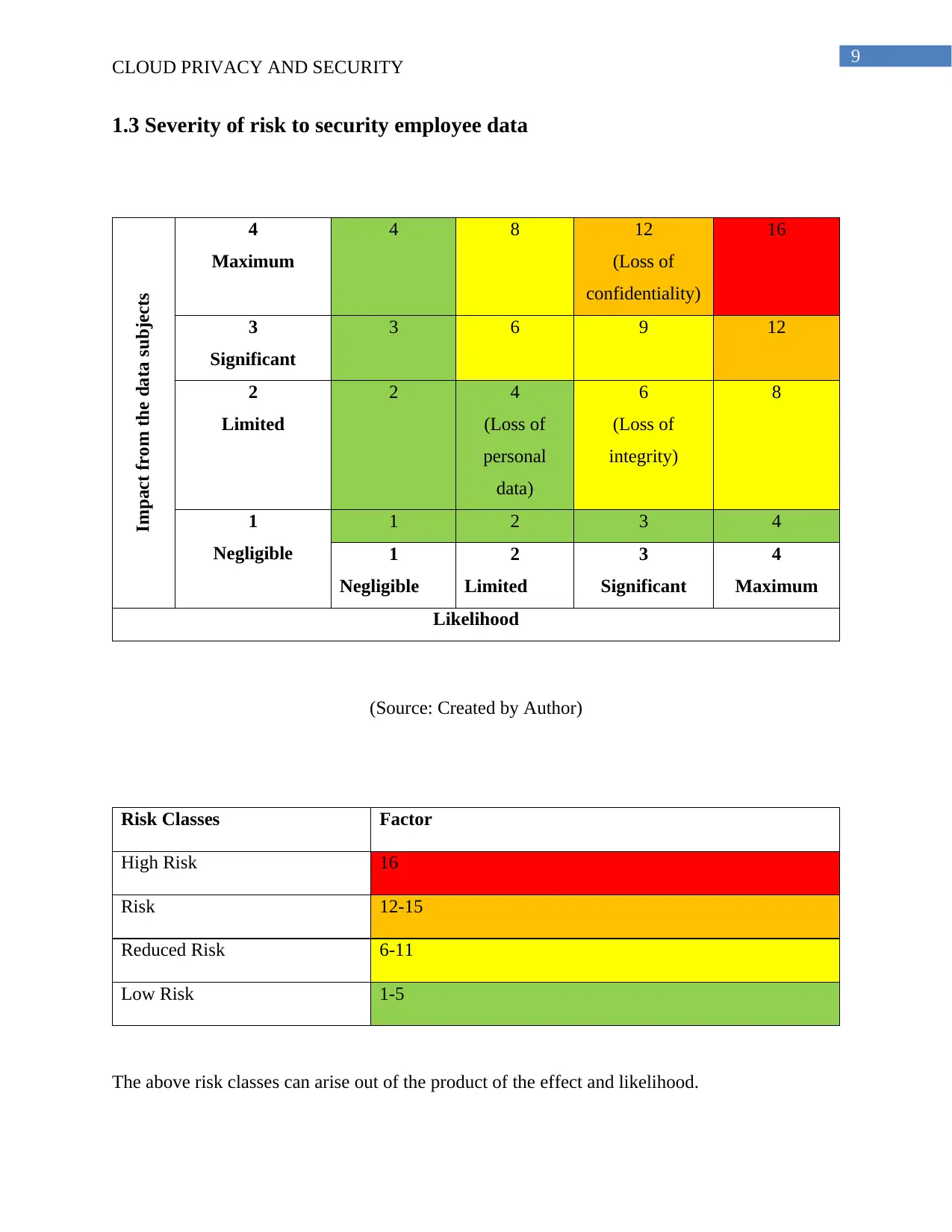
1.3 Severity of risk to security employee data
Impact from the data subjects
4
Maximum
4 8 12
(Loss of
confidentiality)
16
3
Significant
3 6 9 12
2
Limited
2 4
(Loss of
personal
data)
6
(Loss of
integrity)
8
1
Negligible
1 2 3 4
1
Negligible
2
Limited
3
Significant
4
Maximum
Likelihood
(Source: Created by Author)
Risk Classes Factor
High Risk 16
Risk 12-15
Reduced Risk 6-11
Low Risk 1-5
The above risk classes can arise out of the product of the effect and likelihood.
CLOUD PRIVACY AND SECURITY
1.3 Severity of risk to security employee data
Impact from the data subjects
4
Maximum
4 8 12
(Loss of
confidentiality)
16
3
Significant
3 6 9 12
2
Limited
2 4
(Loss of
personal
data)
6
(Loss of
integrity)
8
1
Negligible
1 2 3 4
1
Negligible
2
Limited
3
Significant
4
Maximum
Likelihood
(Source: Created by Author)
Risk Classes Factor
High Risk 16
Risk 12-15
Reduced Risk 6-11
Low Risk 1-5
The above risk classes can arise out of the product of the effect and likelihood.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CLOUD PRIVACY AND SECURITY
2.1 Existing threats to privacy of employee data
Denial of service attacks: Data sensitivity has been an important threat to cloud clients
and all things considered to be same as to cloud professional for maintaining solutions to it
(Dang-Pham, Pittayachawan, & Bruno, 2017). This attack shuts down the main server if the
Charity and all the processes are broken. Therefore, in an instance all the operations in the
Charity might get lost. Therefore, this has been a great threat for the organization.
Increased authentication demands: The authentication factor of the users is an important
aspect for the security purposes in the Charity. There have been many unauthorized users trying
to breach into the systems of the Charity. This has led to the data loss in the organization. The
improvement of cloud computing in outrageous, permit utilization of customers on customer
side. As opposed to buying a permit and introducing a product on the customer side, clients will
validate so as to have the capacity to utilize a cloud application. There are a few favorable
circumstances in such a model, for example, making programming theft more troublesome and
making concentrated checking more helpful.
2.2 New Threats to privacy of employee data
Social networking attacks: There has been various social networking platforms including
Facebook, Twitter, Instagram and LinkedIn (Coppolino et al. 2017). Various users have been
using their social life over their account online. There have been increase in the cyber-attacks
over the internet. Huge amount of data loss has been reported over a year due to this social media
platforms. There have been increase in the fake profiles over the Facebook and it is continuously
increasing. The digital identity theft has been a common problem for users over the internet.
The use of social media platform has been for connecting with over people over the world. The
CLOUD PRIVACY AND SECURITY
2.1 Existing threats to privacy of employee data
Denial of service attacks: Data sensitivity has been an important threat to cloud clients
and all things considered to be same as to cloud professional for maintaining solutions to it
(Dang-Pham, Pittayachawan, & Bruno, 2017). This attack shuts down the main server if the
Charity and all the processes are broken. Therefore, in an instance all the operations in the
Charity might get lost. Therefore, this has been a great threat for the organization.
Increased authentication demands: The authentication factor of the users is an important
aspect for the security purposes in the Charity. There have been many unauthorized users trying
to breach into the systems of the Charity. This has led to the data loss in the organization. The
improvement of cloud computing in outrageous, permit utilization of customers on customer
side. As opposed to buying a permit and introducing a product on the customer side, clients will
validate so as to have the capacity to utilize a cloud application. There are a few favorable
circumstances in such a model, for example, making programming theft more troublesome and
making concentrated checking more helpful.
2.2 New Threats to privacy of employee data
Social networking attacks: There has been various social networking platforms including
Facebook, Twitter, Instagram and LinkedIn (Coppolino et al. 2017). Various users have been
using their social life over their account online. There have been increase in the cyber-attacks
over the internet. Huge amount of data loss has been reported over a year due to this social media
platforms. There have been increase in the fake profiles over the Facebook and it is continuously
increasing. The digital identity theft has been a common problem for users over the internet.
The use of social media platform has been for connecting with over people over the world. The

11
CLOUD PRIVACY AND SECURITY
use of social media has been helping in maintaining a keen approach to enhance the
communication with people in organization and society. Therefore, there is a huge data transfer
done over the social media websites. Therefore, there has been a great chance of cyber-breach
over these websites. The Charity might suffer with these problems in the future. Therefore, a
strong secured protocol is required for restricting cyber-attacks in the Charity.
Mobile device attacks: The utilization of advanced mobile phones has expanded and
cloud availability is presently not any more constrained to PC or work area figuring gadgets.
Assaults are currently rising that are focused for versatile gadgets and depend on highlights
generally connected with PCs and work areas, including rich application programming interfaces
(APIs) that encouraging group of people correspondences and foundation administrations,
dependably on remote Internet access, and substantial nearby information abilities (Rewadkar &
Ghatage , 2014). As versatile gadgets currently have these proportionate highlights, Internet-
based spyware, virus or even physical attacks may probably cause against cell phones, as they
are conceivably a less dangerous focus on attacker that wishes for staying undetected. This is for
the most part bolstered by the way that most cell phones do not have the comparable security
highlights empowered, or for some situation accessible. The HR management of the Charity has
been implanting SaaS cloud model in the Charity for using software and other computing
resources in the Charity. For instance, develop anti-malware, antivirus or full symmetric
encryption innovations are not across the board on current accessible advanced mobile phones.
2.3 Severity of risk to privacy employee data
Impact 4
Maximum
4 8 12
(Mobile Device
attack)
16
(Denial of
Service)
CLOUD PRIVACY AND SECURITY
use of social media has been helping in maintaining a keen approach to enhance the
communication with people in organization and society. Therefore, there is a huge data transfer
done over the social media websites. Therefore, there has been a great chance of cyber-breach
over these websites. The Charity might suffer with these problems in the future. Therefore, a
strong secured protocol is required for restricting cyber-attacks in the Charity.
Mobile device attacks: The utilization of advanced mobile phones has expanded and
cloud availability is presently not any more constrained to PC or work area figuring gadgets.
Assaults are currently rising that are focused for versatile gadgets and depend on highlights
generally connected with PCs and work areas, including rich application programming interfaces
(APIs) that encouraging group of people correspondences and foundation administrations,
dependably on remote Internet access, and substantial nearby information abilities (Rewadkar &
Ghatage , 2014). As versatile gadgets currently have these proportionate highlights, Internet-
based spyware, virus or even physical attacks may probably cause against cell phones, as they
are conceivably a less dangerous focus on attacker that wishes for staying undetected. This is for
the most part bolstered by the way that most cell phones do not have the comparable security
highlights empowered, or for some situation accessible. The HR management of the Charity has
been implanting SaaS cloud model in the Charity for using software and other computing
resources in the Charity. For instance, develop anti-malware, antivirus or full symmetric
encryption innovations are not across the board on current accessible advanced mobile phones.
2.3 Severity of risk to privacy employee data
Impact 4
Maximum
4 8 12
(Mobile Device
attack)
16
(Denial of
Service)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





