Comprehensive Cloud Risk Assessment for AWS Edge Deployment
VerifiedAdded on 2023/06/08
|12
|3545
|301
Report
AI Summary
This report provides a comprehensive risk assessment of deploying AWS edge services, focusing on potential risks such as data sprawl, edge device proliferation, and security vulnerabilities. It details mitigation strategies, including the use of AWS IoT Greengrass V2, access control, and enhanced network security. The report also explores available AWS support services like AWS Outposts, AWS Wavelength, and AWS Storage Gateway, highlighting their roles in securing edge deployments. Furthermore, it discusses the cloud deployment risk management process, emphasizing the importance of creating services that cooperate with edge deployments, utilizing near-edge data centers, and ensuring robust security measures. The report concludes by underscoring the need for continuous monitoring and adaptation to address evolving security challenges in AWS edge environments, offering insights valuable for organizations like DR Alarm considering AWS cloud infrastructure investment. Desklib provides access to this and other solved assignments for students.

CLOUD RISK
ASSESSMENT
1
ASSESSMENT
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................3
MAIN BODY...................................................................................................................................3
Risks of using AWS edge............................................................................................................3
AWS support services available..................................................................................................5
Cloud Deployment risk management process map......................................................................7
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................11
INTRODUCTION...........................................................................................................................3
MAIN BODY...................................................................................................................................3
Risks of using AWS edge............................................................................................................3
AWS support services available..................................................................................................5
Cloud Deployment risk management process map......................................................................7
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................11

INTRODUCTION
Cloud security refer to collection of security measures which is particularly designed for
securing the cloud based infrastructure (Paul, & Aithal, 2019). Such measures make sure end
user and device authentication. AWS (Amazon web service) is the subsidiary of Amazon which
enables the on demand cloud platform and API to users, organisation on pay as you go basis.
This service generally gives the distributed computing process and software tools through AWS
server. DR Alarm a company sells the alarm and monitoring product, recently they have been
trying to expand their business after massive success of their product, they are thinking to invest
in AWS cloud infrastructure. Following report will cover the Risks associated with AWS and its
mitigation strategies, it will also cover the resources that are availed by AWS security hub.
Moving further report also discuss the process map for cloud deployment risk management.
MAIN BODY
Risks of using AWS edge
AWS edge is the service deliver data analysis and provides the storage that is near to
endpoints and also enables the user to deploy the API and tools outside the AWS data centres.
Develop high performance application which can analyse and keeps the data where it is occurred
and enables ultra-low latency and real time responsiveness. AWS edge networking helps in
forwarding the user faced data firmly and with improvised latency in whole world. Thus with
this platform business can easily manage their team work, where it provides the better secure
enterprise document safe and sharing (Rizvi & et.al 2018). By deploying AWS edge it will
benefit the business by limiting the malicious attacks by simply encrypting the data and
eliminates the network hops while controlling the application access. Edge AWS is benefit which
increases the speed by reducing latency and improvised security and privacy measure. There are
some potential risks which are associated with AWS edge that are as follows:
Proliferation of the edge device assist in keeping and analysing data which enhances the
risks like virtual security. Where remote accessing of these devices enables the attackers
to attack the device and steal useful or critical information, it also gives the opportunity to
hackers to gain access for corporate system and use data for their purpose.
3
Cloud security refer to collection of security measures which is particularly designed for
securing the cloud based infrastructure (Paul, & Aithal, 2019). Such measures make sure end
user and device authentication. AWS (Amazon web service) is the subsidiary of Amazon which
enables the on demand cloud platform and API to users, organisation on pay as you go basis.
This service generally gives the distributed computing process and software tools through AWS
server. DR Alarm a company sells the alarm and monitoring product, recently they have been
trying to expand their business after massive success of their product, they are thinking to invest
in AWS cloud infrastructure. Following report will cover the Risks associated with AWS and its
mitigation strategies, it will also cover the resources that are availed by AWS security hub.
Moving further report also discuss the process map for cloud deployment risk management.
MAIN BODY
Risks of using AWS edge
AWS edge is the service deliver data analysis and provides the storage that is near to
endpoints and also enables the user to deploy the API and tools outside the AWS data centres.
Develop high performance application which can analyse and keeps the data where it is occurred
and enables ultra-low latency and real time responsiveness. AWS edge networking helps in
forwarding the user faced data firmly and with improvised latency in whole world. Thus with
this platform business can easily manage their team work, where it provides the better secure
enterprise document safe and sharing (Rizvi & et.al 2018). By deploying AWS edge it will
benefit the business by limiting the malicious attacks by simply encrypting the data and
eliminates the network hops while controlling the application access. Edge AWS is benefit which
increases the speed by reducing latency and improvised security and privacy measure. There are
some potential risks which are associated with AWS edge that are as follows:
Proliferation of the edge device assist in keeping and analysing data which enhances the
risks like virtual security. Where remote accessing of these devices enables the attackers
to attack the device and steal useful or critical information, it also gives the opportunity to
hackers to gain access for corporate system and use data for their purpose.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Data storage and protection where data is being collected and analysed at edge lacks the
better stiff physical security for the centralised assets. As by simply eliminating the disk
drive from edge resource can compromise the vital information. And due to limited
availability of the local resources it can be more complex to back up the reliable data.
Password and authentication, edge services might not have cooperated by the security
operations and some also have lax password discipline. In fact, attackers also have
different ways to decode the password and to break the password protocol (Verma & et.al
2019)Data sprawl, where businesses uses more and more edge devices to manage various
array of operations and it creates a complexity for monitoring and tracking. On particular
duration these devices outgrow the edge boundaries, developing bandwidth overcrowding
endangered the security and privacy for various devices.
There is a rapid growing requirement for data processing that is available for the users at
edge of network for reducing the accelerated analysis, thus due to this data is being stored
on IOT devices that is growing concern for malicious attacks. As computing is moving
towards the edge which is imposing risk for data to be theft or steal.
Mitigation strategies for risk
AWS services along with the points of presence (PoP) present at edge location is
associated from AWS network backbone. It provides the better and secure experience to user.
Where it also enables the services that is easily run on the edge platform that allows for
delivering the content or information (Susukailo & et.al 2021). Security for the edge is similar to
the cloud security, as company have extended the cloud services to edge so that AWS will
operate securely with better and secured infrastructure. Where to mitigate any risk there is an
AWS owned infrastructure which is tracked 24/7 to secure the data confidentiality and integrity
that is available for the user.
AWS IOT green grass V2 is the open source internet of things edge and cloud services it
enables to develop and deploy and control the IOT application on devices. Thus DR alarm can
also proceed with AWS IOT greengrass to design software so that it will enables their devices to
act locally on data in order to develops and run the prediction that is based on Machine learning
models. As it also helps in addressing the security perspective of AWS edge by protecting data,
enabling device authentication and compliance validation. This device also helps in collecting
better stiff physical security for the centralised assets. As by simply eliminating the disk
drive from edge resource can compromise the vital information. And due to limited
availability of the local resources it can be more complex to back up the reliable data.
Password and authentication, edge services might not have cooperated by the security
operations and some also have lax password discipline. In fact, attackers also have
different ways to decode the password and to break the password protocol (Verma & et.al
2019)Data sprawl, where businesses uses more and more edge devices to manage various
array of operations and it creates a complexity for monitoring and tracking. On particular
duration these devices outgrow the edge boundaries, developing bandwidth overcrowding
endangered the security and privacy for various devices.
There is a rapid growing requirement for data processing that is available for the users at
edge of network for reducing the accelerated analysis, thus due to this data is being stored
on IOT devices that is growing concern for malicious attacks. As computing is moving
towards the edge which is imposing risk for data to be theft or steal.
Mitigation strategies for risk
AWS services along with the points of presence (PoP) present at edge location is
associated from AWS network backbone. It provides the better and secure experience to user.
Where it also enables the services that is easily run on the edge platform that allows for
delivering the content or information (Susukailo & et.al 2021). Security for the edge is similar to
the cloud security, as company have extended the cloud services to edge so that AWS will
operate securely with better and secured infrastructure. Where to mitigate any risk there is an
AWS owned infrastructure which is tracked 24/7 to secure the data confidentiality and integrity
that is available for the user.
AWS IOT green grass V2 is the open source internet of things edge and cloud services it
enables to develop and deploy and control the IOT application on devices. Thus DR alarm can
also proceed with AWS IOT greengrass to design software so that it will enables their devices to
act locally on data in order to develops and run the prediction that is based on Machine learning
models. As it also helps in addressing the security perspective of AWS edge by protecting data,
enabling device authentication and compliance validation. This device also helps in collecting
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and analysing data that is related to information and it simply communicate securely over local
network. IOT devices can also communicate easily or securely with the AWS IoT core.
Other strategies can be follows is to utilise the access control and surveillance for
increasing physical security at edge. Control edge configuration can also have been done and
also by developing the audit procedures for managing the data can also be better measure to
reduce risk in AWS edge (Mulder, 2020). Additionally, it can also be done to enable the better
level of network for security in between the devices and edge facilities. By treating the edge as
component of the public cloud in IT operation can also be beneficial. For overcoming the data
sprawl risk in AWS edge organisation can proceed to monitor their compliance data and system,
as once the data is being exported to other system then track all destination where it is delivered.
To deal with data security problem AWS shield DDoS mitigation system is available which is
used with the AWS edge services that helps in overcoming the data security problem.
AWS support services available
AWS security hub gives the comprehensive picture about the security states in AWS and
enables to monitor system environment against the security industry policies. Suitable support
services are available for the AWS edge is as follows:
AWS outposts: It is completely managed service which extends the AWS infrastructure, API and
other tools to virtual datacentre and to facility for better hybrid experience. AWS outposts is
better for the workloads which only needed a low latency for accessing the system (Guptha,
Murali & Subbulakshmi, 2021).
AWS wavelength: It allows the developers to create the applications which provides the single
digit millisecond latencies to phone and consumer. Where AWS developers easily implement
their applications to the wavelength zone which embed the AWS compute in the
telecommunications providers.
AWS storage gateway: It is a hybrid cloud that provides the storage services which enable the
user to easily connects and extend them on premises process to this storage gateway, where
caching for the information can easily held locally for the little latency for access.
At Edge AWs provides the services which accounts the different components of the edge
security, it involves the preventive measures mechanism like access control, Encryption, audit
for configuration and other physical security. Security for the edge is quite similar to the security
5
network. IOT devices can also communicate easily or securely with the AWS IoT core.
Other strategies can be follows is to utilise the access control and surveillance for
increasing physical security at edge. Control edge configuration can also have been done and
also by developing the audit procedures for managing the data can also be better measure to
reduce risk in AWS edge (Mulder, 2020). Additionally, it can also be done to enable the better
level of network for security in between the devices and edge facilities. By treating the edge as
component of the public cloud in IT operation can also be beneficial. For overcoming the data
sprawl risk in AWS edge organisation can proceed to monitor their compliance data and system,
as once the data is being exported to other system then track all destination where it is delivered.
To deal with data security problem AWS shield DDoS mitigation system is available which is
used with the AWS edge services that helps in overcoming the data security problem.
AWS support services available
AWS security hub gives the comprehensive picture about the security states in AWS and
enables to monitor system environment against the security industry policies. Suitable support
services are available for the AWS edge is as follows:
AWS outposts: It is completely managed service which extends the AWS infrastructure, API and
other tools to virtual datacentre and to facility for better hybrid experience. AWS outposts is
better for the workloads which only needed a low latency for accessing the system (Guptha,
Murali & Subbulakshmi, 2021).
AWS wavelength: It allows the developers to create the applications which provides the single
digit millisecond latencies to phone and consumer. Where AWS developers easily implement
their applications to the wavelength zone which embed the AWS compute in the
telecommunications providers.
AWS storage gateway: It is a hybrid cloud that provides the storage services which enable the
user to easily connects and extend them on premises process to this storage gateway, where
caching for the information can easily held locally for the little latency for access.
At Edge AWs provides the services which accounts the different components of the edge
security, it involves the preventive measures mechanism like access control, Encryption, audit
for configuration and other physical security. Security for the edge is quite similar to the security
5

at cloud, by expanding cloud services to edge, AWS enables the better approach for operating
securely with the strong infrastructure and other secure measure. It is also found that AWS
owned infrastructure is continuously tracked and manage for providing better safeguarding
processes to maintain confidentiality, integrity for the data. Shifting cloud’s storage work to edge
endpoints helps in providing better transparent control to mitigate any risk (Chen, Takabi & Le-
Khac, 2019). Defence within depth framework like different layers of the security controls that
enables the strong protection layers. There are three edge protection which works in securing the
connectivity between the initial infrastructure and edge services. Some of the consumer edge
applications are as follows:
Safe content delivery: At edge AWS provides the security measure for protecting the architecture
to enable security from edge to cloud. Safeguarding at AWS initiates with the core infrastructure
that is developed and designed for cloud to fulfil the security requirements. At edge AWS
enables the services which encompasses the distinct features of edge security like encryption.
Secure content delivery gives the data, API and other video or application to consumers, it is
provided over safest platform.
Protection in network and application layer: Edge computing allows manufacturers for
gathering and processing the collected data to make useful predictions for better decision making
process. Edge applications also enhances the efficiencies by reducing the costs and helps in
protecting against the attacks.
DDoS (Distributed denial of services): DDoS mitigation is the defense layer that operates at
edge, it ensures availability of services and operations. DDoS attacks are purposeful attempts to
attack system and make the resources unavailable for the users. Some DDoS attacks are SYN
floods which affects the TCP protocol (Indrani & et.al 2021). Hence AWS involves the
protective measures for the DDoS attacks, where user who uses application load balancers and
elastic IP’s are provided with basic protection against transport layer and DDoS attacks.
Other security measure is provided by AWS to edge is it enables the shield Standard
defensive traffic that is forwarded by the Aws edge location through DDoS. Thus it also
allows the user to integrate the AWS web application firewall (WAF) to leverage the process
for WAF.
securely with the strong infrastructure and other secure measure. It is also found that AWS
owned infrastructure is continuously tracked and manage for providing better safeguarding
processes to maintain confidentiality, integrity for the data. Shifting cloud’s storage work to edge
endpoints helps in providing better transparent control to mitigate any risk (Chen, Takabi & Le-
Khac, 2019). Defence within depth framework like different layers of the security controls that
enables the strong protection layers. There are three edge protection which works in securing the
connectivity between the initial infrastructure and edge services. Some of the consumer edge
applications are as follows:
Safe content delivery: At edge AWS provides the security measure for protecting the architecture
to enable security from edge to cloud. Safeguarding at AWS initiates with the core infrastructure
that is developed and designed for cloud to fulfil the security requirements. At edge AWS
enables the services which encompasses the distinct features of edge security like encryption.
Secure content delivery gives the data, API and other video or application to consumers, it is
provided over safest platform.
Protection in network and application layer: Edge computing allows manufacturers for
gathering and processing the collected data to make useful predictions for better decision making
process. Edge applications also enhances the efficiencies by reducing the costs and helps in
protecting against the attacks.
DDoS (Distributed denial of services): DDoS mitigation is the defense layer that operates at
edge, it ensures availability of services and operations. DDoS attacks are purposeful attempts to
attack system and make the resources unavailable for the users. Some DDoS attacks are SYN
floods which affects the TCP protocol (Indrani & et.al 2021). Hence AWS involves the
protective measures for the DDoS attacks, where user who uses application load balancers and
elastic IP’s are provided with basic protection against transport layer and DDoS attacks.
Other security measure is provided by AWS to edge is it enables the shield Standard
defensive traffic that is forwarded by the Aws edge location through DDoS. Thus it also
allows the user to integrate the AWS web application firewall (WAF) to leverage the process
for WAF.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Customisable content delivery network: With this service that is provided for the AWS edge user
can easily manage their web content delivery by utilising the amazon cloud front for enhancing
the latency to secure the applications. As cloud front is quickest content delivery network which
cooperates the video, API and other file caching. Serving the traffic internationally by distributed
AWS edge location services, where cloud fronts easily encrypts the request and sent back to the
origin of application. Cloud front edge computing efficiencies simply work with the security
services of AWS shield and allows for enabling the AWS web firewall to develop protective
measure to fights against the DDoS.
Better network routing and traffic management: End user latency and other complications in
connectivity is derived by ineffectiveness within traffic which routes in between the devices. It
can be easily address by utilising the Amazon routing 53 to control the network traffic. Router 53
is better scalable cloud domain name system which converts the website name in IP address for
enabling better connection for internet communication (Park, Lee & Park, 2021). Another
benefit of route 53 is that it enables to operate the network traffic on the basis of geographical
proximity, through which user can easily initiates their application for managing performant
connectivity.
Identity and access management: AWS services allows for safe management of identities and
other resources. by using AWS end user have identity services for their workforce and to manage
the consumer application for initiating the work quickly as well as to control the access to
workloads.
Compliance and data privacy: AWS provides the better aspects for compliance status that
regularly monitors system environment by utilising the automated compliance checks on the
basis of industry policies which the businesses follow.
Application protection: Protection at network and application enables to implement the fine
grained policies over network points across the firm. AWS services allows for inspecting and
filtering the network traffic to protect the information from third party authorisation.
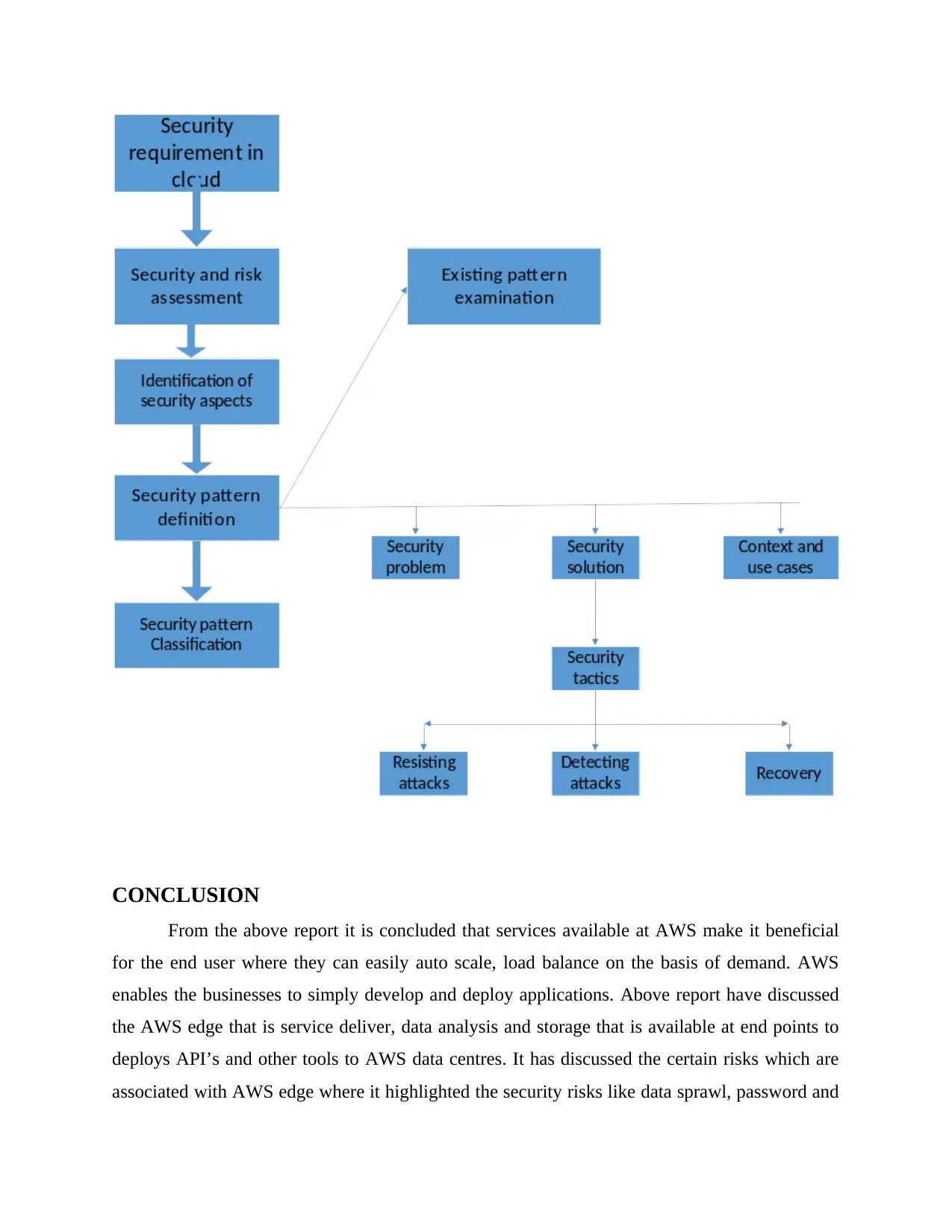
Cloud Deployment risk management process map
Deployment of edge strategy involves the following criteria which are as follows:
7
can easily manage their web content delivery by utilising the amazon cloud front for enhancing
the latency to secure the applications. As cloud front is quickest content delivery network which
cooperates the video, API and other file caching. Serving the traffic internationally by distributed
AWS edge location services, where cloud fronts easily encrypts the request and sent back to the
origin of application. Cloud front edge computing efficiencies simply work with the security
services of AWS shield and allows for enabling the AWS web firewall to develop protective
measure to fights against the DDoS.
Better network routing and traffic management: End user latency and other complications in
connectivity is derived by ineffectiveness within traffic which routes in between the devices. It
can be easily address by utilising the Amazon routing 53 to control the network traffic. Router 53
is better scalable cloud domain name system which converts the website name in IP address for
enabling better connection for internet communication (Park, Lee & Park, 2021). Another
benefit of route 53 is that it enables to operate the network traffic on the basis of geographical
proximity, through which user can easily initiates their application for managing performant
connectivity.
Identity and access management: AWS services allows for safe management of identities and
other resources. by using AWS end user have identity services for their workforce and to manage
the consumer application for initiating the work quickly as well as to control the access to
workloads.
Compliance and data privacy: AWS provides the better aspects for compliance status that
regularly monitors system environment by utilising the automated compliance checks on the
basis of industry policies which the businesses follow.
Application protection: Protection at network and application enables to implement the fine
grained policies over network points across the firm. AWS services allows for inspecting and
filtering the network traffic to protect the information from third party authorisation.
Cloud Deployment risk management process map
Deployment of edge strategy involves the following criteria which are as follows:
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Create services for cooperating with edge deployments: New edge landscape is widespread
with suitable availability for new revenue streams and also enhances the competitiveness. Edge
computing is associate with the IOT to develop the reason for designing premium level services.
Use near edge data centre deployment for managing data and traffic in region: Passing the
roundtrip to cloud that decreases latency which allows quick response time to minimise the
possibilities for hazardous incidents (Cain, Raymond & Ransbottom, 2020). Thus in such it is up
to the user to make decision as what services are required for sending it to cloud and what
services are needed to run locally, overall it decreases the IT costs.
Improvise the connectivity capacity from edge to core: Tether the far edge process that consist
of local edge data centres which is present at cell towers base. Robust connectivity point is the
key for hybrid IT and edge strategy.
Deploy other services at edge: Processing at edge in a 10 milliseconds of device can
immediately responses that is required for IOT, from virtual reality, automation all requires low
latency for growth.
Identify what things are required to be manage at edge: Making better decisions as what are
need to be manage at edge and what to deliver at data centre. Closer to processing and data, the
more agile the firm can become.
Drop and dump non critical data at edge: Decision making for data which need to be dumped
and transfer for other analysis need to be done in frequent manner at edge.
Take action for useful data: Only useful data is delivers that concerns with depth analysis and
high security. Such process is expensive for distribution therefore core data centre remain useful.
For risk optimised plan for AWS edge deployment below are the key points to consider-
Develop consistent hybrid cloud: AWS hybrid cloud provides the better AWs experience which
the end user can easily avail irrespective of their physical location. It requires a selection for the
broadest set of storage and security and other operational services for constructing hybrid
architecture in order to meet the requirements. It accelerates digital transformation as well as
enhanced IT and developer efficiency, it also ensures the better delivery of distinct services and
experiences.
Improvise edge networking: Delivers user faced data efficiently with better latency worldwide
by using AWS edge services. It limits the attack exposure by encrypting data and to eliminate the
with suitable availability for new revenue streams and also enhances the competitiveness. Edge
computing is associate with the IOT to develop the reason for designing premium level services.
Use near edge data centre deployment for managing data and traffic in region: Passing the
roundtrip to cloud that decreases latency which allows quick response time to minimise the
possibilities for hazardous incidents (Cain, Raymond & Ransbottom, 2020). Thus in such it is up
to the user to make decision as what services are required for sending it to cloud and what
services are needed to run locally, overall it decreases the IT costs.
Improvise the connectivity capacity from edge to core: Tether the far edge process that consist
of local edge data centres which is present at cell towers base. Robust connectivity point is the
key for hybrid IT and edge strategy.
Deploy other services at edge: Processing at edge in a 10 milliseconds of device can
immediately responses that is required for IOT, from virtual reality, automation all requires low
latency for growth.
Identify what things are required to be manage at edge: Making better decisions as what are
need to be manage at edge and what to deliver at data centre. Closer to processing and data, the
more agile the firm can become.
Drop and dump non critical data at edge: Decision making for data which need to be dumped
and transfer for other analysis need to be done in frequent manner at edge.
Take action for useful data: Only useful data is delivers that concerns with depth analysis and
high security. Such process is expensive for distribution therefore core data centre remain useful.
For risk optimised plan for AWS edge deployment below are the key points to consider-
Develop consistent hybrid cloud: AWS hybrid cloud provides the better AWs experience which
the end user can easily avail irrespective of their physical location. It requires a selection for the
broadest set of storage and security and other operational services for constructing hybrid
architecture in order to meet the requirements. It accelerates digital transformation as well as
enhanced IT and developer efficiency, it also ensures the better delivery of distinct services and
experiences.
Improvise edge networking: Delivers user faced data efficiently with better latency worldwide
by using AWS edge services. It limits the attack exposure by encrypting data and to eliminate the

network hops. AWS global infrastructure gives the 100 Gbps fibres and allows for delivering the
data to application through edge location which reduces the cost.
Fuel industrial transformation: It Accelerates design and reinvent the supply chain. It also
assists in overcoming the challenges like intermittent connectivity. AWS make services available
for the user which involves edge to cloud service that encompasses Artificial intelligence,
robotics, analytics which assists in accomplishing the business outcomes.
Construct better connected device experiences: Rapid and cost efficient feature helps in
developing differentiated and better consumer experience that is integrated with IoT and edge
computing services. AWS makes it simple and cost effective for using devices globally (Basig &
et.al 2021).
Run ruggedized edge computing: AWS enables the set of physical devices which are
specifically designed for smooth run on local computing applications and to transfers the data
into cloud.
Enhance 5G and multi access edge computing: User can easily utilise computing and other
services that offers similar developer experiences like in cloud, but the condition is to provide
services in communication service providers at edge of network. telecommunication and
enterprise consumers utilised the AWS services to analyse how 5G network is developed,
implement and manage.
AWS implements the security controls for managing the risks, where AWS control
environment is created that concern with certain standards and structures which provides the
implementation basis for setting the security requirements across AWS edge (Hsu, Wang, & See,
2022). AWS also utilises the specific aspects of Amazon’s control environment (CE) where the
leverage tools involve the equipment that are used for managing separation of job roles. AWS
CE consider as base for secure delivery of AWS services. Where risk management and
compliances process involves pre-launch and post launch process in which pre-launch activities
entails AWS application security to validate security risks that has been identified and mitigate.
Where post launch activities involve AWS security for ensuring maintenance of well security
posture, in this scanning is also done for analysing the vulnerability for management.
Process map
9
data to application through edge location which reduces the cost.
Fuel industrial transformation: It Accelerates design and reinvent the supply chain. It also
assists in overcoming the challenges like intermittent connectivity. AWS make services available
for the user which involves edge to cloud service that encompasses Artificial intelligence,
robotics, analytics which assists in accomplishing the business outcomes.
Construct better connected device experiences: Rapid and cost efficient feature helps in
developing differentiated and better consumer experience that is integrated with IoT and edge
computing services. AWS makes it simple and cost effective for using devices globally (Basig &
et.al 2021).
Run ruggedized edge computing: AWS enables the set of physical devices which are
specifically designed for smooth run on local computing applications and to transfers the data
into cloud.
Enhance 5G and multi access edge computing: User can easily utilise computing and other
services that offers similar developer experiences like in cloud, but the condition is to provide
services in communication service providers at edge of network. telecommunication and
enterprise consumers utilised the AWS services to analyse how 5G network is developed,
implement and manage.
AWS implements the security controls for managing the risks, where AWS control
environment is created that concern with certain standards and structures which provides the
implementation basis for setting the security requirements across AWS edge (Hsu, Wang, & See,
2022). AWS also utilises the specific aspects of Amazon’s control environment (CE) where the
leverage tools involve the equipment that are used for managing separation of job roles. AWS
CE consider as base for secure delivery of AWS services. Where risk management and
compliances process involves pre-launch and post launch process in which pre-launch activities
entails AWS application security to validate security risks that has been identified and mitigate.
Where post launch activities involve AWS security for ensuring maintenance of well security
posture, in this scanning is also done for analysing the vulnerability for management.
Process map
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CONCLUSION
From the above report it is concluded that services available at AWS make it beneficial
for the end user where they can easily auto scale, load balance on the basis of demand. AWS
enables the businesses to simply develop and deploy applications. Above report have discussed
the AWS edge that is service deliver, data analysis and storage that is available at end points to
deploys API’s and other tools to AWS data centres. It has discussed the certain risks which are
associated with AWS edge where it highlighted the security risks like data sprawl, password and
From the above report it is concluded that services available at AWS make it beneficial
for the end user where they can easily auto scale, load balance on the basis of demand. AWS
enables the businesses to simply develop and deploy applications. Above report have discussed
the AWS edge that is service deliver, data analysis and storage that is available at end points to
deploys API’s and other tools to AWS data centres. It has discussed the certain risks which are
associated with AWS edge where it highlighted the security risks like data sprawl, password and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

user authentication risk, it also discussed the mitigating strategies that would be deployed to
minimise risk. Moving further report have illustrated the AWS services that are available which
highlighted the network routing traffic management and other services. Report lastly concluded
with the discussion of cloud deployment risk management.
REFERENCES
Books and journals
Basig, L. & et.al (2021, September). Reliable Event Routing in the Cloud and on the Edge.
In European Conference on Software Architecture (pp. 243-259). Springer, Cham.
Cain, C., Raymond, D., & Ransbottom, J. S. (2020, March). The State of the Public Cloud:
Security Concerns with Cloud Computing. In 2020 SoutheastCon (pp. 1-5). IEEE.
Chen, L., Takabi, H., & Le-Khac, N. A. (Eds.). (2019). Security, privacy, and digital forensics in
the cloud. John Wiley & Sons.
11
minimise risk. Moving further report have illustrated the AWS services that are available which
highlighted the network routing traffic management and other services. Report lastly concluded
with the discussion of cloud deployment risk management.
REFERENCES
Books and journals
Basig, L. & et.al (2021, September). Reliable Event Routing in the Cloud and on the Edge.
In European Conference on Software Architecture (pp. 243-259). Springer, Cham.
Cain, C., Raymond, D., & Ransbottom, J. S. (2020, March). The State of the Public Cloud:
Security Concerns with Cloud Computing. In 2020 SoutheastCon (pp. 1-5). IEEE.
Chen, L., Takabi, H., & Le-Khac, N. A. (Eds.). (2019). Security, privacy, and digital forensics in
the cloud. John Wiley & Sons.
11

Guptha, A., Murali, H., & Subbulakshmi, T. (2021, May). A Comparative Analysis of Security
Services in Major Cloud Service Providers. In 2021 5th International Conference on
Intelligent Computing and Control Systems (ICICCS) (pp. 129-136). IEEE.
Hsu, T. H., Wang, Z. H., & See, A. R. (2022). A Cloud-Edge-Smart IoT Architecture for
Speeding Up the Deployment of Neural Network Models with Transfer Learning
Techniques. Electronics, 11(14), 2255.
Indrani, I. & et.al (2021). Internet of Cloud: Secure and Privacy Preserving Cloud Model with
IoT Enabled Service. Cloud Security: Techniques and Applications. 1. 83.
Mulder, J. (2020). Multi-Cloud Architecture and Governance: Leverage Azure, AWS, GCP, and
VMware vSphere to build effective multi-cloud solutions. Packt Publishing Ltd.
Park, S. J., Lee, Y. J., & Park, Y. C. (2021). Configuration Method of AWS Security
Architecture for Cloud Service. Journal of Convergence for Information
Technology. 11(7). 7-13.
Paul, P., & Aithal, P. S. (2019). Cloud Security: An Overview and Current Trend. International
Journal of Applied Engineering and Management Letters (IJAEML). 3(2). 53-58.
Rizvi, S. & et.al (2018). A security evaluation framework for cloud security auditing. The
Journal of Supercomputing. 74(11). 5774-5796.
Susukailo, V. & et.al (2021). Cybercrimes investigation via honeypots in cloud environments.
In CEUR Workshop Proceedingsthis link is disabled (Vol. 2923, pp. 91-96).
Verma, V. K. & et.al (2019). Next-generation Internet of things and cloud security
solutions. International Journal of Distributed Sensor Networks. 15(3).
1550147719835098.
Services in Major Cloud Service Providers. In 2021 5th International Conference on
Intelligent Computing and Control Systems (ICICCS) (pp. 129-136). IEEE.
Hsu, T. H., Wang, Z. H., & See, A. R. (2022). A Cloud-Edge-Smart IoT Architecture for
Speeding Up the Deployment of Neural Network Models with Transfer Learning
Techniques. Electronics, 11(14), 2255.
Indrani, I. & et.al (2021). Internet of Cloud: Secure and Privacy Preserving Cloud Model with
IoT Enabled Service. Cloud Security: Techniques and Applications. 1. 83.
Mulder, J. (2020). Multi-Cloud Architecture and Governance: Leverage Azure, AWS, GCP, and
VMware vSphere to build effective multi-cloud solutions. Packt Publishing Ltd.
Park, S. J., Lee, Y. J., & Park, Y. C. (2021). Configuration Method of AWS Security
Architecture for Cloud Service. Journal of Convergence for Information
Technology. 11(7). 7-13.
Paul, P., & Aithal, P. S. (2019). Cloud Security: An Overview and Current Trend. International
Journal of Applied Engineering and Management Letters (IJAEML). 3(2). 53-58.
Rizvi, S. & et.al (2018). A security evaluation framework for cloud security auditing. The
Journal of Supercomputing. 74(11). 5774-5796.
Susukailo, V. & et.al (2021). Cybercrimes investigation via honeypots in cloud environments.
In CEUR Workshop Proceedingsthis link is disabled (Vol. 2923, pp. 91-96).
Verma, V. K. & et.al (2019). Next-generation Internet of things and cloud security
solutions. International Journal of Distributed Sensor Networks. 15(3).
1550147719835098.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





