Cloud Security and Privacy for Land Titles Agency: Threat and Risk Assessment
VerifiedAdded on 2023/05/30
|13
|3073
|431
AI Summary
This article discusses the development of threat and risk assessment for PII data for people registered with Land Titles Agency. It also reviews the stability of using PaaS and SaaS database and provides recommendations for the chosen model. Additionally, it suggests control approaches for protecting data and mitigating risks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CLOUD SECURITY AND PRIVACY
Land Titles Agency: Case Scenario
Name of the student:
Name of the university:
Land Titles Agency: Case Scenario
Name of the student:
Name of the university:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2CLOUD SECURITY AND PRIVACY
1. Development of Threat and Risk Assessment for PII data for people
registered
The responsibility of Land Titles Agency is to maintain the land registry details of block
of lands that are either sold or transferred from one owner to any new owner. The role of the
agency is to keep the records of all the block of lands that are newly bought and sold. They
create new registered certificates for the new land owners. These certificates ensure the proof for
land ownership. In order to verify the identification of every person the agency needs to deal
with large number of lawyers and conveyancers as well (Ibrahim et al., 2018). With the changing
time the number of information regarding the legal certificates and ownership are also
increasing. In order to deal properly with the information it has become important for the agency
to change their operational environment from the general to cloud based. The agency is willing
to upgrade their system from the current one to a public cloud based one. It is found that, the
upgraded system will help the agency to increase its operational, functional and business
efficiency. The threats and risks that may occur due to these changes are developed (Serhani,
Atif & Benharref, 2014). In addition to this, the risk and threats identified in this case include
both privacy and data protection and elaborated in the below section:
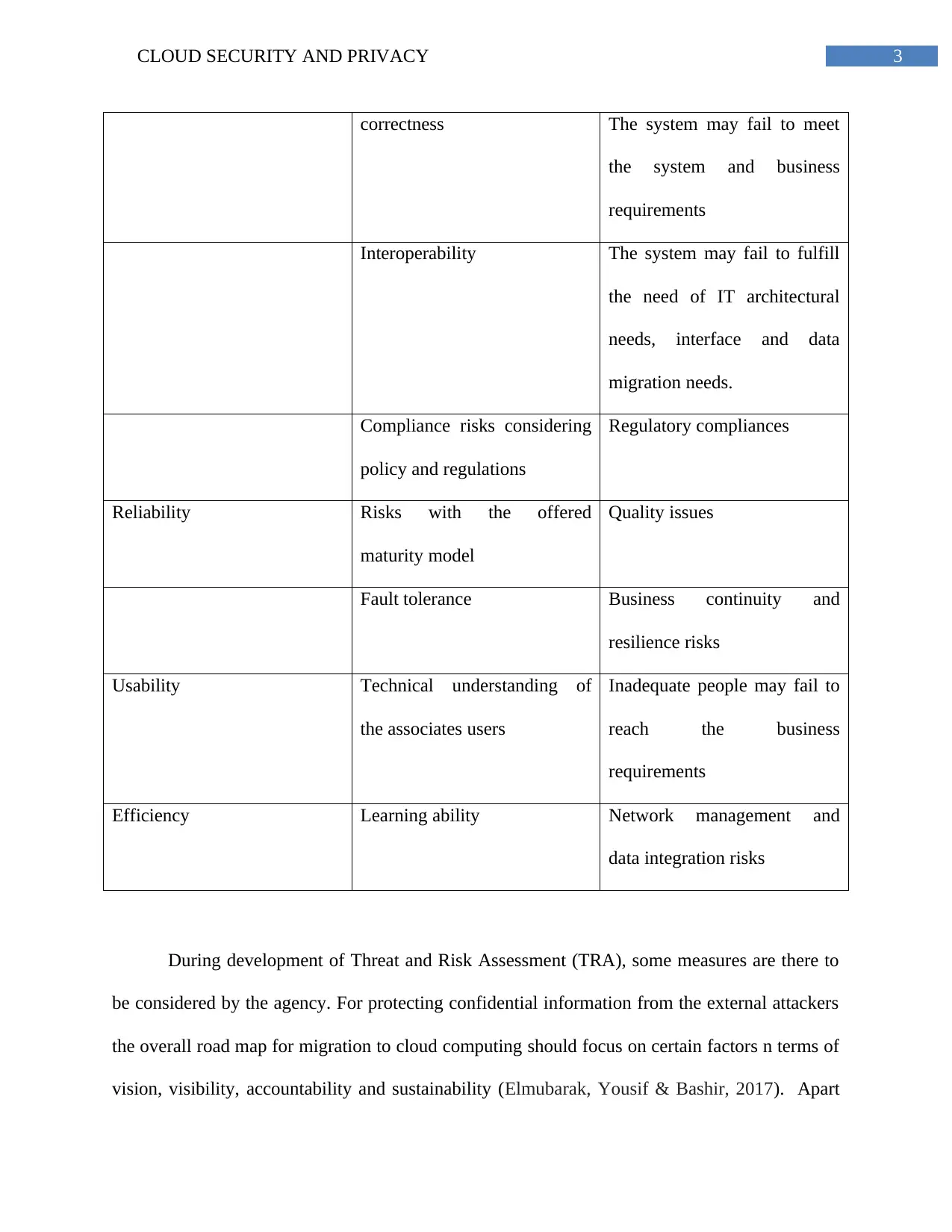
Risk assessment
Features Subcharacteristics Cloud risks
Functionality Business requirement
suitability
The developed functional
solution may not meet the
business requirements.
1. Development of Threat and Risk Assessment for PII data for people
registered
The responsibility of Land Titles Agency is to maintain the land registry details of block
of lands that are either sold or transferred from one owner to any new owner. The role of the
agency is to keep the records of all the block of lands that are newly bought and sold. They
create new registered certificates for the new land owners. These certificates ensure the proof for
land ownership. In order to verify the identification of every person the agency needs to deal
with large number of lawyers and conveyancers as well (Ibrahim et al., 2018). With the changing
time the number of information regarding the legal certificates and ownership are also
increasing. In order to deal properly with the information it has become important for the agency
to change their operational environment from the general to cloud based. The agency is willing
to upgrade their system from the current one to a public cloud based one. It is found that, the
upgraded system will help the agency to increase its operational, functional and business
efficiency. The threats and risks that may occur due to these changes are developed (Serhani,
Atif & Benharref, 2014). In addition to this, the risk and threats identified in this case include
both privacy and data protection and elaborated in the below section:
Risk assessment
Features Subcharacteristics Cloud risks
Functionality Business requirement
suitability
The developed functional
solution may not meet the
business requirements.
3CLOUD SECURITY AND PRIVACY
correctness The system may fail to meet
the system and business
requirements
Interoperability The system may fail to fulfill
the need of IT architectural
needs, interface and data
migration needs.
Compliance risks considering
policy and regulations
Regulatory compliances
Reliability Risks with the offered
maturity model
Quality issues
Fault tolerance Business continuity and
resilience risks
Usability Technical understanding of
the associates users
Inadequate people may fail to
reach the business
requirements
Efficiency Learning ability Network management and
data integration risks
During development of Threat and Risk Assessment (TRA), some measures are there to
be considered by the agency. For protecting confidential information from the external attackers
the overall road map for migration to cloud computing should focus on certain factors n terms of
vision, visibility, accountability and sustainability (Elmubarak, Yousif & Bashir, 2017). Apart
correctness The system may fail to meet
the system and business
requirements
Interoperability The system may fail to fulfill
the need of IT architectural
needs, interface and data
migration needs.
Compliance risks considering
policy and regulations
Regulatory compliances
Reliability Risks with the offered
maturity model
Quality issues
Fault tolerance Business continuity and
resilience risks
Usability Technical understanding of
the associates users
Inadequate people may fail to
reach the business
requirements
Efficiency Learning ability Network management and
data integration risks
During development of Threat and Risk Assessment (TRA), some measures are there to
be considered by the agency. For protecting confidential information from the external attackers
the overall road map for migration to cloud computing should focus on certain factors n terms of
vision, visibility, accountability and sustainability (Elmubarak, Yousif & Bashir, 2017). Apart

4CLOUD SECURITY AND PRIVACY
from this, other features that are to be considered for managing data include confidentiality,
integrity and availability. Significant remediation and approve can provide effective control over
the activities of the agencies. The technical review should be served over the agency security
model. Matured IT processing should be followed accordingly by the agency to gain measurable
resultants.
Privacy for the data: Cloud computing technology has been identified as a boon for the
millennial and technical world for very obvious reason. Only data storage and data management
are not the privacy actions but also it gives the users high time data access capabilities. The users
can access needful data from the server regardless of time and location (Pham et al., 2017). The
security related issues are categorized in security concerns faced by consumers and the
consumers. the providers should make sure that the infrastructure they have developed is
completely secured and the data of the users are absolutely protected.
Data protection: In order to protect server data two different technologies should be followed
by the agency are encryption and application firewall. With the help of encryption technology
none of the unauthenticated and unauthorized user will be able to access data from the server
without permission. The data transmission channel will also be secured and the unwanted users
can not access the transmission channel (Hussain, Hussain & Hussain, 2014). It will give high
time as well as sustainable protection to the agency. The agency can avoid loss of sensitive data,
malware infection, hacked interface, violation of existing regulatory controls etc.
2. Discussion on stability of using PaaS and SaaS database
from this, other features that are to be considered for managing data include confidentiality,
integrity and availability. Significant remediation and approve can provide effective control over
the activities of the agencies. The technical review should be served over the agency security
model. Matured IT processing should be followed accordingly by the agency to gain measurable
resultants.
Privacy for the data: Cloud computing technology has been identified as a boon for the
millennial and technical world for very obvious reason. Only data storage and data management
are not the privacy actions but also it gives the users high time data access capabilities. The users
can access needful data from the server regardless of time and location (Pham et al., 2017). The
security related issues are categorized in security concerns faced by consumers and the
consumers. the providers should make sure that the infrastructure they have developed is
completely secured and the data of the users are absolutely protected.
Data protection: In order to protect server data two different technologies should be followed
by the agency are encryption and application firewall. With the help of encryption technology
none of the unauthenticated and unauthorized user will be able to access data from the server
without permission. The data transmission channel will also be secured and the unwanted users
can not access the transmission channel (Hussain, Hussain & Hussain, 2014). It will give high
time as well as sustainable protection to the agency. The agency can avoid loss of sensitive data,
malware infection, hacked interface, violation of existing regulatory controls etc.
2. Discussion on stability of using PaaS and SaaS database
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

5CLOUD SECURITY AND PRIVACY
2.a Review of both the PaaS and SaaS model
Two different architecture models exist such as one SP and Many SP’s, which are
followed by the business organizations. Security challenges are referred to as the most
highlighted obstacles that are required to be resolved from the core operational system. Cloud
computing technology is a prevalent IT outsourcing paradigm that entails high security level
risks. The operational and functional capabilities of these two models are given in the below
section:
SaaS (software as a service): Software as a Service (SaaS) is an on demand software
which is used for licensing and delivery model where a completely functional software product
can be successfully delivered. Through the help of the web Browsers the users can access the
SaaS offerings. This platform is secured for storing confidential information. The SaaS providers
are allowed to host application and also make the host available for the users with the internet,
frequently browser based interface (Skourletopoulos et al., 2015). The common example of the
SaaS platform users are Google apps, Drop box, Cisco WebEx concur etc. SaaS platform is
managed from the centralized location and hosted professionally on remote server. This platform
is accessible over the internet service. However the users are not responsible for updating
software and hardware updates.
Platform as a service (PaaS): PaaS provides the users different cloud components for
limited numbers of software when those are used for different operation and applications. In
order to create customized application PaaS gives the software developers an accurate
framework also. Confidential information can be stored with high security in SaaS. The
developers can manage the applications and on the other hand the enterprise can manage the
networking, storage and servers (Wu, Garg & Buyya, 2015). The PaaS platform is highly
2.a Review of both the PaaS and SaaS model
Two different architecture models exist such as one SP and Many SP’s, which are
followed by the business organizations. Security challenges are referred to as the most
highlighted obstacles that are required to be resolved from the core operational system. Cloud
computing technology is a prevalent IT outsourcing paradigm that entails high security level
risks. The operational and functional capabilities of these two models are given in the below
section:
SaaS (software as a service): Software as a Service (SaaS) is an on demand software
which is used for licensing and delivery model where a completely functional software product
can be successfully delivered. Through the help of the web Browsers the users can access the
SaaS offerings. This platform is secured for storing confidential information. The SaaS providers
are allowed to host application and also make the host available for the users with the internet,
frequently browser based interface (Skourletopoulos et al., 2015). The common example of the
SaaS platform users are Google apps, Drop box, Cisco WebEx concur etc. SaaS platform is
managed from the centralized location and hosted professionally on remote server. This platform
is accessible over the internet service. However the users are not responsible for updating
software and hardware updates.
Platform as a service (PaaS): PaaS provides the users different cloud components for
limited numbers of software when those are used for different operation and applications. In
order to create customized application PaaS gives the software developers an accurate
framework also. Confidential information can be stored with high security in SaaS. The
developers can manage the applications and on the other hand the enterprise can manage the
networking, storage and servers (Wu, Garg & Buyya, 2015). The PaaS platform is highly

6CLOUD SECURITY AND PRIVACY
available, scalable and it allows easy migration to the model. The amounts of coding get
minimized with the application of this model and develop and deploy complexity gets simpler
while storing information.
2. b Recommendations for chosen model: SaaS
Between SaaS and PaaS, the SaaS cloud computing model can increase the benefits of IT
related businesses up to 100 percent than the general. In order to update system mostly the
companies denies investing much capital every time. Among the Amazon Web Services (AWS)
or Google Cloud Platform (GCP), the company is required to use the Amazon Web Service SaaS
based platform. SaaS offers monthly rental charges instead of one time buying investment. There
are different situations where SaaS application stands very helpful (Sharma & Sood, 2014).
Though, Land Titles Agency is not a startup company or small company which requires
launching Ecommerce quickly but with SaaS platform it will be able to save time for
accomplishing the application. Both mobile and web access are required for fulfilling the
applications. SaaS provides three different data protection and privacy related opportunities such
as:
Data backup: This platform gives the owners an opportunity of keep data as a backup. If
any information is found to be destroyed or lost from the server then with the help of data backup
the information can be re retrieved again from the server (Lakra & Yadav, 2015). The SaaS
operators can duplicate the information and those data can be retrieved by the users whenever
required. It also makes sure that all the data are secured from the external attackers and no
critical data are lost from the server.
available, scalable and it allows easy migration to the model. The amounts of coding get
minimized with the application of this model and develop and deploy complexity gets simpler
while storing information.
2. b Recommendations for chosen model: SaaS
Between SaaS and PaaS, the SaaS cloud computing model can increase the benefits of IT
related businesses up to 100 percent than the general. In order to update system mostly the
companies denies investing much capital every time. Among the Amazon Web Services (AWS)
or Google Cloud Platform (GCP), the company is required to use the Amazon Web Service SaaS
based platform. SaaS offers monthly rental charges instead of one time buying investment. There
are different situations where SaaS application stands very helpful (Sharma & Sood, 2014).
Though, Land Titles Agency is not a startup company or small company which requires
launching Ecommerce quickly but with SaaS platform it will be able to save time for
accomplishing the application. Both mobile and web access are required for fulfilling the
applications. SaaS provides three different data protection and privacy related opportunities such
as:
Data backup: This platform gives the owners an opportunity of keep data as a backup. If
any information is found to be destroyed or lost from the server then with the help of data backup
the information can be re retrieved again from the server (Lakra & Yadav, 2015). The SaaS
operators can duplicate the information and those data can be retrieved by the users whenever
required. It also makes sure that all the data are secured from the external attackers and no
critical data are lost from the server.

7CLOUD SECURITY AND PRIVACY
Application resilience: Application resilience is a ability offers to the users to protect the
entire business process from external problems. This approach has become very much important
to the organizations where continuously multi tier software is implementing. Not only this but
also the hidden system vulnerabilities that are affecting the application resiliency are also
resolved with the help of SaaS platform.
Disaster recovery: SaaS disaster recovery is a restore or backup planning strategy which
includes maintenance and storing of data those are in electronic forms. The aim of the cloud
computing technology is to measures all security components so that the lost data either during
the platform migration or something else can be recovered easily (Balbudhe et al., 2015).
Moreover, the aim of this approach is to provide Land Titles Agency an electronic data recovery
opportunity. In other words, SaaS provides charge for the storage on pay per use models
depending upon capacity seta and bandwidth as well.
3. Control approaches can be used for protecting data
3.a Threats and Risk mitigation approaches
Name of the risks Mitigation strategies
Application resilience: Application resilience is a ability offers to the users to protect the
entire business process from external problems. This approach has become very much important
to the organizations where continuously multi tier software is implementing. Not only this but
also the hidden system vulnerabilities that are affecting the application resiliency are also
resolved with the help of SaaS platform.
Disaster recovery: SaaS disaster recovery is a restore or backup planning strategy which
includes maintenance and storing of data those are in electronic forms. The aim of the cloud
computing technology is to measures all security components so that the lost data either during
the platform migration or something else can be recovered easily (Balbudhe et al., 2015).
Moreover, the aim of this approach is to provide Land Titles Agency an electronic data recovery
opportunity. In other words, SaaS provides charge for the storage on pay per use models
depending upon capacity seta and bandwidth as well.
3. Control approaches can be used for protecting data
3.a Threats and Risk mitigation approaches
Name of the risks Mitigation strategies
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8CLOUD SECURITY AND PRIVACY
Cost risks: Land Titles Agency may fail to
estimate the actual cost that is needed to
accomplish the
Migration to SaaS cloud based platform.
Mainly due to poor accuracy in cost estimation
and scope creep cost level risk may occur.
In order to avoid the cost risks, the finance
manager of Land Titles Agency is required to
develop proper feasibility measurements and
resources as well. It will help the business
owners to gain measurable commercial
revenue and competitive advantages as well.
Scheduling risk: Scheduling risk is referred to
as that activity which occurs due to improper
time management. Inaccurate time
management may lead to overrunning cost and
over allocation budget. Schedule risks will also
affect the competitive advantage of Land Titles
Agency.
In order to avoid scheduling risk the head
executives of Land Titles Agency are required
to measure the complexity of each of the
activities taken for the new project. Based on
the complexity the time should be allotted for
the activities. With accurate measurement only
the issues of scheduling risks can be
completely resolved.
Performance risks: If the project manager and
the organizations head fail to assign
professional experts to the activities then the
project may not meet the objectives and goals.
It is the role of the HR executives to assign
accurate resources to specific activities.
In order to accomplish the project needs of
Land Titles Agency the HR should hire
professional experts. Only professional experts
will be able to meet the project objectives of
clod based data server. Apart from this, the
owners are also required to arrange technical
training and development program so that they
can develop their technical skills and
knowledge simultaneously.
Cost risks: Land Titles Agency may fail to
estimate the actual cost that is needed to
accomplish the
Migration to SaaS cloud based platform.
Mainly due to poor accuracy in cost estimation
and scope creep cost level risk may occur.
In order to avoid the cost risks, the finance
manager of Land Titles Agency is required to
develop proper feasibility measurements and
resources as well. It will help the business
owners to gain measurable commercial
revenue and competitive advantages as well.
Scheduling risk: Scheduling risk is referred to
as that activity which occurs due to improper
time management. Inaccurate time
management may lead to overrunning cost and
over allocation budget. Schedule risks will also
affect the competitive advantage of Land Titles
Agency.
In order to avoid scheduling risk the head
executives of Land Titles Agency are required
to measure the complexity of each of the
activities taken for the new project. Based on
the complexity the time should be allotted for
the activities. With accurate measurement only
the issues of scheduling risks can be
completely resolved.
Performance risks: If the project manager and
the organizations head fail to assign
professional experts to the activities then the
project may not meet the objectives and goals.
It is the role of the HR executives to assign
accurate resources to specific activities.
In order to accomplish the project needs of
Land Titles Agency the HR should hire
professional experts. Only professional experts
will be able to meet the project objectives of
clod based data server. Apart from this, the
owners are also required to arrange technical
training and development program so that they
can develop their technical skills and
knowledge simultaneously.

9CLOUD SECURITY AND PRIVACY
Governance threat: If ethical standards and
community stewardship is not properly
followed then governing risks may occur in
Land Titles Agency.
Before developing the business goals and
objectives it is mandatory for the project heads
to develop business strategies considering
norms and business regulations. The business
governance level threats will be completely
resolved with the regulatory obligations.
Operational threats: The operational risks
include poor strategy implementation,
production, and distribution and procurement
problems.
Land Titles Agency should appoint operation
manager who will operate the operational
activities accurately
Legal risks: this issue may rise from
regulatory obligations, contract risks and
litigation that are brought against the
organization.
Proper legal actions and other approaches
should be introduced by the project manager
and other project heads before the
implementation of the project. It is the role of
the research and development team to conduct
legal regulations before successful
implementation of the projects.
3.b Recommendations
Besides operational, legal, regulatory, cost and performance level risk another major risk
that impacts the data management system of Land Titles Agency is security risks. The company
deals with maintenance of centralized registry for the newly titled lands. As the numbers of such
Governance threat: If ethical standards and
community stewardship is not properly
followed then governing risks may occur in
Land Titles Agency.
Before developing the business goals and
objectives it is mandatory for the project heads
to develop business strategies considering
norms and business regulations. The business
governance level threats will be completely
resolved with the regulatory obligations.
Operational threats: The operational risks
include poor strategy implementation,
production, and distribution and procurement
problems.
Land Titles Agency should appoint operation
manager who will operate the operational
activities accurately
Legal risks: this issue may rise from
regulatory obligations, contract risks and
litigation that are brought against the
organization.
Proper legal actions and other approaches
should be introduced by the project manager
and other project heads before the
implementation of the project. It is the role of
the research and development team to conduct
legal regulations before successful
implementation of the projects.
3.b Recommendations
Besides operational, legal, regulatory, cost and performance level risk another major risk
that impacts the data management system of Land Titles Agency is security risks. The company
deals with maintenance of centralized registry for the newly titled lands. As the numbers of such

10CLOUD SECURITY AND PRIVACY
plots are increasing day by day therefore, managing those data are becoming a challenge to the
company. Not only this but also the lawyers and conveyance’s details are also stored in the
company store. The recommendations given to Land Titles Agency are as follows:
Encryption technology and application firewall are the two different approaches that
helps to improve the business efficiency with high security.
Encryption technology: Data encryption is referred to as one of the most appreciable
data protection approach. The encrypted data cannot be decrypted by any external user who does
not have the key. Both symmetric and asymmetric keys are used to encrypt the information.
Even during transaction of data within the channel no data can be retrieved by the users. In
addition to this, no unauthenticated and unauthorized users will be able to hijack information
from the cloud server without permission.
Firewall: Application firewall and DMZ will also give high security to the confidential
information stored in the server.
plots are increasing day by day therefore, managing those data are becoming a challenge to the
company. Not only this but also the lawyers and conveyance’s details are also stored in the
company store. The recommendations given to Land Titles Agency are as follows:
Encryption technology and application firewall are the two different approaches that
helps to improve the business efficiency with high security.
Encryption technology: Data encryption is referred to as one of the most appreciable
data protection approach. The encrypted data cannot be decrypted by any external user who does
not have the key. Both symmetric and asymmetric keys are used to encrypt the information.
Even during transaction of data within the channel no data can be retrieved by the users. In
addition to this, no unauthenticated and unauthorized users will be able to hijack information
from the cloud server without permission.
Firewall: Application firewall and DMZ will also give high security to the confidential
information stored in the server.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

11CLOUD SECURITY AND PRIVACY
References
Abdelmaboud, A., Jawawi, D. N., Ghani, I., Elsafi, A., & Kitchenham, B. (2015). Quality of
service approaches in cloud computing: A systematic mapping study. Journal of Systems
and Software, 101, 159-179.
Balbudhe, K. S., Bulbule, A., Dhanve, N., Raj, S., & Jadhav, N. (2015). Cloud based cultivation
management system. Advances in Computer Science: an International Journal, 4(3), 24-
28.
Bharadi, V. A., & D'Silva, G. M. (2015, February). Online signature recognition using software
as a service (SAAS) model on public cloud. In Computing Communication Control and
Automation (ICCUBEA), 2015 International Conference on (pp. 65-72). IEEE.
Bhardwaj, S., & Sahoo, B. (2015, May). A particle swarm optimization approach for cost
effective SaaS placement on cloud. In Computing, Communication & Automation
(ICCCA), 2015 International Conference on (pp. 686-690). IEEE.
Elmubarak, S. A., Yousif, A., & Bashir, M. B. (2017). Performance based Ranking Model for
Cloud SaaS Services. International Journal of Information Technology and Computer
Science (IJITCS), 9(1), 65-71.
Hussain, W., Hussain, F. K., & Hussain, O. K. (2014, November). Maintaining trust in cloud
computing through SLA monitoring. In International Conference on Neural Information
Processing (pp. 690-697). Springer, Cham.
References
Abdelmaboud, A., Jawawi, D. N., Ghani, I., Elsafi, A., & Kitchenham, B. (2015). Quality of
service approaches in cloud computing: A systematic mapping study. Journal of Systems
and Software, 101, 159-179.
Balbudhe, K. S., Bulbule, A., Dhanve, N., Raj, S., & Jadhav, N. (2015). Cloud based cultivation
management system. Advances in Computer Science: an International Journal, 4(3), 24-
28.
Bharadi, V. A., & D'Silva, G. M. (2015, February). Online signature recognition using software
as a service (SAAS) model on public cloud. In Computing Communication Control and
Automation (ICCUBEA), 2015 International Conference on (pp. 65-72). IEEE.
Bhardwaj, S., & Sahoo, B. (2015, May). A particle swarm optimization approach for cost
effective SaaS placement on cloud. In Computing, Communication & Automation
(ICCCA), 2015 International Conference on (pp. 686-690). IEEE.
Elmubarak, S. A., Yousif, A., & Bashir, M. B. (2017). Performance based Ranking Model for
Cloud SaaS Services. International Journal of Information Technology and Computer
Science (IJITCS), 9(1), 65-71.
Hussain, W., Hussain, F. K., & Hussain, O. K. (2014, November). Maintaining trust in cloud
computing through SLA monitoring. In International Conference on Neural Information
Processing (pp. 690-697). Springer, Cham.

12CLOUD SECURITY AND PRIVACY
Ibrahim, A. A., Wasim, M. U., Varrette, S., & Bouvry, P. (2018). PRESENCE: Monitoring and
Modelling the Performance Metrics of Mobile Cloud SaaS Web Services. Mobile
Information Systems, 2018.
Lakra, A. V., & Yadav, D. K. (2015). Multi-objective tasks scheduling algorithm for cloud
computing throughput optimization. Procedia Computer Science, 48, 107-113.
Morakos, P., & Meliones, A. (2014, July). Design and implementation of a cloud saas
framework for multi-tenant applications. In Information, Intelligence, Systems and
Applications, IISA 2014, The 5th International Conference on(pp. 273-278). IEEE.
Pham, V. V. H., Liu, X., Zheng, X., Fu, M., Deshpande, S. V., Xia, W., ... & Abdelrazek, M.
(2017, May). PaaS-black or white: an investigation into software development model for
building retail industry SaaS. In Software Engineering Companion (ICSE-C), 2017
IEEE/ACM 39th International Conference on (pp. 285-287). IEEE.
Pop, D. (2016). Machine learning and cloud computing: Survey of distributed and saas
solutions. arXiv preprint arXiv:1603.08767.
Serhani, M. A., Atif, Y., & Benharref, A. (2014). Towards an adaptive QoS-driven monitoring of
cloud SaaS. International Journal of Grid and Utility Computing, 5(4).
Sharma, A., & Sood, M. (2014). Incorporating MDA to design business intelligence services by
using SaaS model of cloud computing. International Journal of Computer
Applications, 106(16).
Skourletopoulos, G., Bahsoon, R., Mavromoustakis, C. X., & Mastorakis, G. (2015). The
technical debt in cloud software engineering: a prediction-based and quantification
Ibrahim, A. A., Wasim, M. U., Varrette, S., & Bouvry, P. (2018). PRESENCE: Monitoring and
Modelling the Performance Metrics of Mobile Cloud SaaS Web Services. Mobile
Information Systems, 2018.
Lakra, A. V., & Yadav, D. K. (2015). Multi-objective tasks scheduling algorithm for cloud
computing throughput optimization. Procedia Computer Science, 48, 107-113.
Morakos, P., & Meliones, A. (2014, July). Design and implementation of a cloud saas
framework for multi-tenant applications. In Information, Intelligence, Systems and
Applications, IISA 2014, The 5th International Conference on(pp. 273-278). IEEE.
Pham, V. V. H., Liu, X., Zheng, X., Fu, M., Deshpande, S. V., Xia, W., ... & Abdelrazek, M.
(2017, May). PaaS-black or white: an investigation into software development model for
building retail industry SaaS. In Software Engineering Companion (ICSE-C), 2017
IEEE/ACM 39th International Conference on (pp. 285-287). IEEE.
Pop, D. (2016). Machine learning and cloud computing: Survey of distributed and saas
solutions. arXiv preprint arXiv:1603.08767.
Serhani, M. A., Atif, Y., & Benharref, A. (2014). Towards an adaptive QoS-driven monitoring of
cloud SaaS. International Journal of Grid and Utility Computing, 5(4).
Sharma, A., & Sood, M. (2014). Incorporating MDA to design business intelligence services by
using SaaS model of cloud computing. International Journal of Computer
Applications, 106(16).
Skourletopoulos, G., Bahsoon, R., Mavromoustakis, C. X., & Mastorakis, G. (2015). The
technical debt in cloud software engineering: a prediction-based and quantification

13CLOUD SECURITY AND PRIVACY
approach. In Resource Management of Mobile Cloud Computing Networks and
Environments (pp. 24-42). IGI Global.
Stavrinides, G. L., & Karatza, H. D. (2016, June). Scheduling different types of applications in a
saas cloud. In Proceedings of the 6th International Symposium on Business Modeling and
Software Design (BMSD’16) (pp. 144-151).
Wu, L., Garg, S. K., & Buyya, R. (2015, December). Service level agreement (SLA) based SaaS
cloud management system. In Parallel and Distributed Systems (ICPADS), 2015 IEEE
21st International Conference on (pp. 440-447). IEEE.
approach. In Resource Management of Mobile Cloud Computing Networks and
Environments (pp. 24-42). IGI Global.
Stavrinides, G. L., & Karatza, H. D. (2016, June). Scheduling different types of applications in a
saas cloud. In Proceedings of the 6th International Symposium on Business Modeling and
Software Design (BMSD’16) (pp. 144-151).
Wu, L., Garg, S. K., & Buyya, R. (2015, December). Service level agreement (SLA) based SaaS
cloud management system. In Parallel and Distributed Systems (ICPADS), 2015 IEEE
21st International Conference on (pp. 440-447). IEEE.
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





