Cloud Computing Risks and Benefits in Finance
VerifiedAdded on 2020/04/07
|15
|4194
|137
AI Summary
This assignment examines the advantages and disadvantages of implementing cloud computing in the financial services sector. It delves into key aspects like security threats, data privacy concerns, regulatory compliance, operational efficiency gains, and cost savings. Students are expected to evaluate the potential impact of cloud adoption on risk management within financial institutions.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 1
RISK ASSESSMENT REPORT FOR MIGRATING BUSINESS PROCEDURES TO THE
CLOUD SPACE FOR BUSINESS PRODUCTIVITY
CASE STUDY (AZTEC LIMITED)
BY
RISK ASSESSMENT REPORT FOR MIGRATING BUSINESS PROCEDURES TO THE
CLOUD SPACE FOR BUSINESS PRODUCTIVITY
CASE STUDY (AZTEC LIMITED)
BY
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 2
Executive Summary
Technological developments have disrupted business operations in terms of service
manufacturing, provision and marketing procedures. Today’s modern business have therefore
seen a lot of changes in the way they operate. Emerging advances have shifted business
operations from traditional operations towards adopting digital revolution. Cloud computing
technology is an emerging technology that has changed the way businesses perform their
operations in order to achieve their objectives.
As a result, the financial services sector is under a lot of pressure to adopt digital
transformation in order to improve efficiency and increase business agility which are
essential in helping the industry continue thriving and expanding in terms of reaching clients,
increasing client base and effectively competing in the financial market. However, not all
financial services sector organizations have embraced the digital shift. This report introduces
cloud computing emerging technology by outlining its key features and types of services
models including SaaS, IaaS and PaaS. It also expounds on how these services can be
deployed, either by using a private, public, community or hybrid cloud space and pros and
cons for each type of deployment expounded, followed by organizational benefits of
implementing cloud services. The paper also discusses the financial service industry with
regard to adopting cloud services and the impacts felt as well as impacts of adopting cloud
technology for Aztec limited including benefits and risks.
Further, the report outlines the threats and susceptibilities that come along with cloud services
implementation including loss of information control, network dependency, BYOD risks,
data insecurity and more. To deal with the above mentioned effects, a risk management
evaluation has been done. Specifically data insecurity being one of the key risks for cloud
computing deployment has been further discussed in terms of data insecurity concerns and
procedures to minimize and avoid them including mobile data management, data encryption
techniques, backup procedures, data access authentication and authorization and installing
backbone networks and finally the conclusion of the report.
The following are the recommendations to Aztec Management with regard to migrating its
key business applications to an external cloud service provider.
i) Cloud computing deployment will enable Aztec to boost its financial agility by
widening its market audience to other newer regions through the world wide web
ii) Aztec will be able to add efficiency in all its business operations
iii) Aztec will be able to reduce operational costs associated with new software
hardware and storage acquisition by ensuring the essential infrastructure resources
are available as they can now be accessed on the Internet
iv) Cloud computing will provide regular services and systems monitoring
v) Cloud services will also help in business continuity by providing growth and
sustainability of Aztec
vi) Cloud adoption will improved mobility as business processes flexibility as they can
now be accessed from any place at any time
vii) Data and information centralization will be enhanced allowing quick retrieval and
updates
viii) Aztec will experience improved collaboration with prospective and existing clients
and stakeholders
Executive Summary
Technological developments have disrupted business operations in terms of service
manufacturing, provision and marketing procedures. Today’s modern business have therefore
seen a lot of changes in the way they operate. Emerging advances have shifted business
operations from traditional operations towards adopting digital revolution. Cloud computing
technology is an emerging technology that has changed the way businesses perform their
operations in order to achieve their objectives.
As a result, the financial services sector is under a lot of pressure to adopt digital
transformation in order to improve efficiency and increase business agility which are
essential in helping the industry continue thriving and expanding in terms of reaching clients,
increasing client base and effectively competing in the financial market. However, not all
financial services sector organizations have embraced the digital shift. This report introduces
cloud computing emerging technology by outlining its key features and types of services
models including SaaS, IaaS and PaaS. It also expounds on how these services can be
deployed, either by using a private, public, community or hybrid cloud space and pros and
cons for each type of deployment expounded, followed by organizational benefits of
implementing cloud services. The paper also discusses the financial service industry with
regard to adopting cloud services and the impacts felt as well as impacts of adopting cloud
technology for Aztec limited including benefits and risks.
Further, the report outlines the threats and susceptibilities that come along with cloud services
implementation including loss of information control, network dependency, BYOD risks,
data insecurity and more. To deal with the above mentioned effects, a risk management
evaluation has been done. Specifically data insecurity being one of the key risks for cloud
computing deployment has been further discussed in terms of data insecurity concerns and
procedures to minimize and avoid them including mobile data management, data encryption
techniques, backup procedures, data access authentication and authorization and installing
backbone networks and finally the conclusion of the report.
The following are the recommendations to Aztec Management with regard to migrating its
key business applications to an external cloud service provider.
i) Cloud computing deployment will enable Aztec to boost its financial agility by
widening its market audience to other newer regions through the world wide web
ii) Aztec will be able to add efficiency in all its business operations
iii) Aztec will be able to reduce operational costs associated with new software
hardware and storage acquisition by ensuring the essential infrastructure resources
are available as they can now be accessed on the Internet
iv) Cloud computing will provide regular services and systems monitoring
v) Cloud services will also help in business continuity by providing growth and
sustainability of Aztec
vi) Cloud adoption will improved mobility as business processes flexibility as they can
now be accessed from any place at any time
vii) Data and information centralization will be enhanced allowing quick retrieval and
updates
viii) Aztec will experience improved collaboration with prospective and existing clients
and stakeholders

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 3
Table of Contents
Introduction................................................................................................................................4
Cloud computing technology.................................................................................................4
Essential Features...................................................................................................................4
Cloud technology service approaches....................................................................................4
Cloud technology deployment approaches............................................................................5
Strengths of adopting cloud computing technology...............................................................6
Financial services sector review.................................................................................................6
Australian financial service sector.........................................................................................6
Cloud computing adoption in the financial services sector...................................................6
Cloud technology compliance procedures in financial services and cyber security
guidelines...............................................................................................................................7
Cloud computing deployment for Aztec Limited......................................................................8
Benefits of cloud adoption for Aztec.....................................................................................8
Benefits of cloud adoption to customers................................................................................8
Cloud adoption Threats and vulnerabilities...........................................................................8
Risk Management.......................................................................................................................9
Data security risks for cloud services.......................................................................................10
Data security procedures for cloud services.............................................................................10
Conclusion................................................................................................................................11
References................................................................................................................................12
Table of Contents
Introduction................................................................................................................................4
Cloud computing technology.................................................................................................4
Essential Features...................................................................................................................4
Cloud technology service approaches....................................................................................4
Cloud technology deployment approaches............................................................................5
Strengths of adopting cloud computing technology...............................................................6
Financial services sector review.................................................................................................6
Australian financial service sector.........................................................................................6
Cloud computing adoption in the financial services sector...................................................6
Cloud technology compliance procedures in financial services and cyber security
guidelines...............................................................................................................................7
Cloud computing deployment for Aztec Limited......................................................................8
Benefits of cloud adoption for Aztec.....................................................................................8
Benefits of cloud adoption to customers................................................................................8
Cloud adoption Threats and vulnerabilities...........................................................................8
Risk Management.......................................................................................................................9
Data security risks for cloud services.......................................................................................10
Data security procedures for cloud services.............................................................................10
Conclusion................................................................................................................................11
References................................................................................................................................12

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 4
Introduction
Cloud computing provides the capability to transform business operations, opportunities and
demands by offering agility, elasticity and speed for organizational resources (Oracle,
2015). For company leaders, cloud services provide business lines to offer computing
applications for rolling out main business procedures. One of the most popular benefit of
cloud computing is that it facilitates IT resources utilization as integrated services by an
organization, which drives efficiency and costs reductions combined computing assets and
processes as well as quick functionality updates. The following evaluation report expounds
on the risks involved with migrating key business applications together with their associated
data on the cloud space for Aztec Limited, a financial service provider.
Cloud computing technology
According to (IBM, 2017), cloud computing paradigm is the provision of on-demand
computing services including storage, data centers, computer networks to applications that
paid for as its utilized through the Internet. Cloud computing therefore allows enterprises and
users access to computing capabilities that allow them process and store and process data,
either through a third party provider or in a private cloud which makes access to data
processes more reliable and efficient (Mell & Grance, 2011). Additionally, cloud computing
depend on resource sharing to achieve economy of scale and consistency (Haghighat,
Zonouz, & Abdel-Mottaleb, 2015).
Essential Features
Quick elasticity - IT asset resources can rapidly scale out as needed for businesses
On-demand self-service – end-users are able to access, evaluate and control required
computing resources without administrative assistance
Expansive access to the network –services are distributed over varied devices and
average networks
Resource pooling – IT resources are accessed and shared across various multiple
applications
Measured service – IT resources usage can be tracked for each end-user application
for effective billing
Cloud technology service approaches
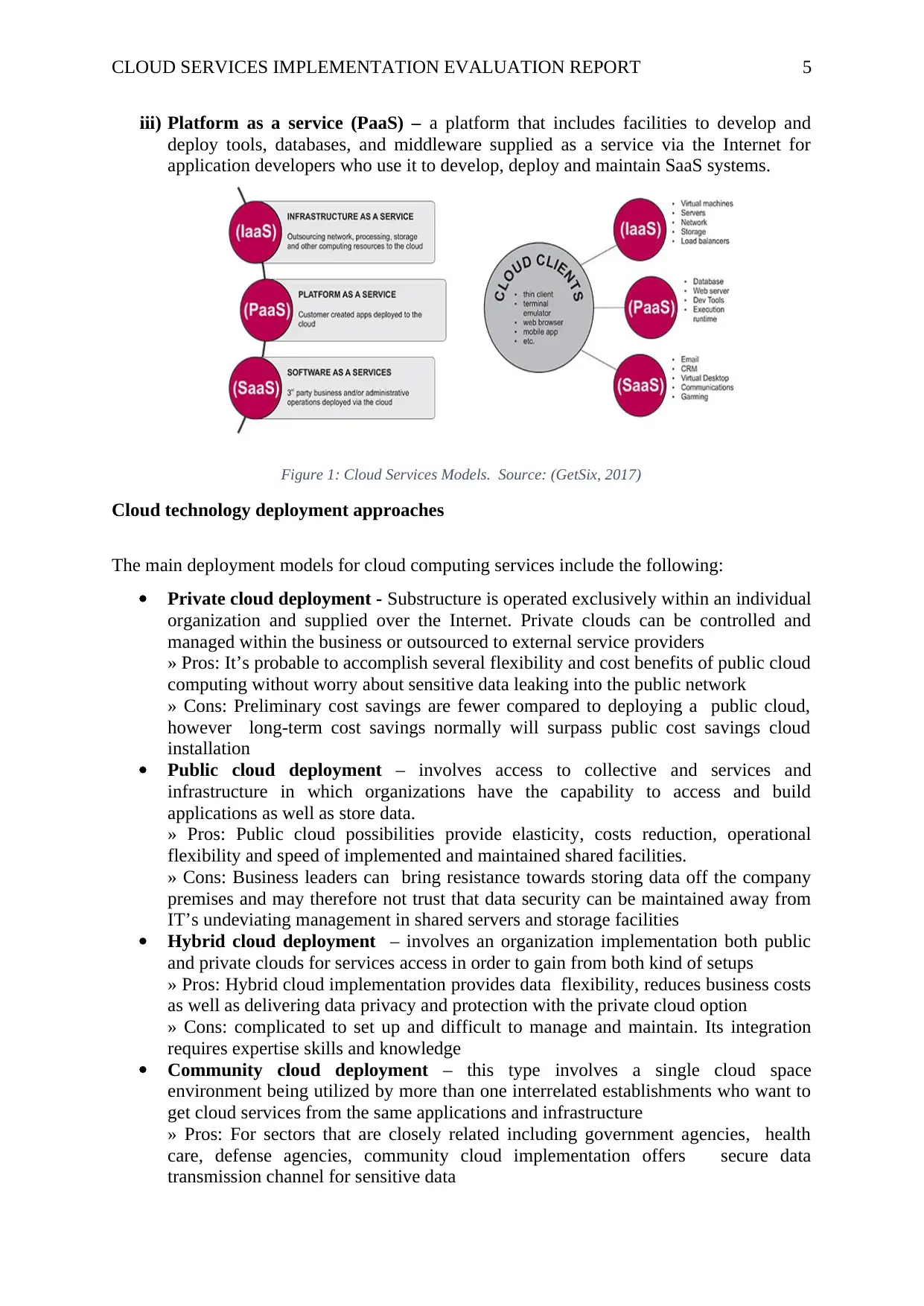
Cloud computing services can be implemented as the following services (Oracle, 2015), and
are shown in the figure 1 below.
i) Software as a service (SaaS) – involves software applications delivered as a service
to users through the web.
ii) Infrastructure as a service (IaaS) – involves hardware based services such as
servers, networking hardware and storage devices via the Internet.
Introduction
Cloud computing provides the capability to transform business operations, opportunities and
demands by offering agility, elasticity and speed for organizational resources (Oracle,
2015). For company leaders, cloud services provide business lines to offer computing
applications for rolling out main business procedures. One of the most popular benefit of
cloud computing is that it facilitates IT resources utilization as integrated services by an
organization, which drives efficiency and costs reductions combined computing assets and
processes as well as quick functionality updates. The following evaluation report expounds
on the risks involved with migrating key business applications together with their associated
data on the cloud space for Aztec Limited, a financial service provider.
Cloud computing technology
According to (IBM, 2017), cloud computing paradigm is the provision of on-demand
computing services including storage, data centers, computer networks to applications that
paid for as its utilized through the Internet. Cloud computing therefore allows enterprises and
users access to computing capabilities that allow them process and store and process data,
either through a third party provider or in a private cloud which makes access to data
processes more reliable and efficient (Mell & Grance, 2011). Additionally, cloud computing
depend on resource sharing to achieve economy of scale and consistency (Haghighat,
Zonouz, & Abdel-Mottaleb, 2015).
Essential Features
Quick elasticity - IT asset resources can rapidly scale out as needed for businesses
On-demand self-service – end-users are able to access, evaluate and control required
computing resources without administrative assistance
Expansive access to the network –services are distributed over varied devices and
average networks
Resource pooling – IT resources are accessed and shared across various multiple
applications
Measured service – IT resources usage can be tracked for each end-user application
for effective billing
Cloud technology service approaches
Cloud computing services can be implemented as the following services (Oracle, 2015), and
are shown in the figure 1 below.
i) Software as a service (SaaS) – involves software applications delivered as a service
to users through the web.
ii) Infrastructure as a service (IaaS) – involves hardware based services such as
servers, networking hardware and storage devices via the Internet.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 5
iii) Platform as a service (PaaS) – a platform that includes facilities to develop and
deploy tools, databases, and middleware supplied as a service via the Internet for
application developers who use it to develop, deploy and maintain SaaS systems.
Figure 1: Cloud Services Models. Source: (GetSix, 2017)
Cloud technology deployment approaches
The main deployment models for cloud computing services include the following:
Private cloud deployment - Substructure is operated exclusively within an individual
organization and supplied over the Internet. Private clouds can be controlled and
managed within the business or outsourced to external service providers
» Pros: It’s probable to accomplish several flexibility and cost benefits of public cloud
computing without worry about sensitive data leaking into the public network
» Cons: Preliminary cost savings are fewer compared to deploying a public cloud,
however long-term cost savings normally will surpass public cost savings cloud
installation
Public cloud deployment – involves access to collective and services and
infrastructure in which organizations have the capability to access and build
applications as well as store data.
» Pros: Public cloud possibilities provide elasticity, costs reduction, operational
flexibility and speed of implemented and maintained shared facilities.
» Cons: Business leaders can bring resistance towards storing data off the company
premises and may therefore not trust that data security can be maintained away from
IT’s undeviating management in shared servers and storage facilities
Hybrid cloud deployment – involves an organization implementation both public
and private clouds for services access in order to gain from both kind of setups
» Pros: Hybrid cloud implementation provides data flexibility, reduces business costs
as well as delivering data privacy and protection with the private cloud option
» Cons: complicated to set up and difficult to manage and maintain. Its integration
requires expertise skills and knowledge
Community cloud deployment – this type involves a single cloud space
environment being utilized by more than one interrelated establishments who want to
get cloud services from the same applications and infrastructure
» Pros: For sectors that are closely related including government agencies, health
care, defense agencies, community cloud implementation offers secure data
transmission channel for sensitive data
iii) Platform as a service (PaaS) – a platform that includes facilities to develop and
deploy tools, databases, and middleware supplied as a service via the Internet for
application developers who use it to develop, deploy and maintain SaaS systems.
Figure 1: Cloud Services Models. Source: (GetSix, 2017)
Cloud technology deployment approaches
The main deployment models for cloud computing services include the following:
Private cloud deployment - Substructure is operated exclusively within an individual
organization and supplied over the Internet. Private clouds can be controlled and
managed within the business or outsourced to external service providers
» Pros: It’s probable to accomplish several flexibility and cost benefits of public cloud
computing without worry about sensitive data leaking into the public network
» Cons: Preliminary cost savings are fewer compared to deploying a public cloud,
however long-term cost savings normally will surpass public cost savings cloud
installation
Public cloud deployment – involves access to collective and services and
infrastructure in which organizations have the capability to access and build
applications as well as store data.
» Pros: Public cloud possibilities provide elasticity, costs reduction, operational
flexibility and speed of implemented and maintained shared facilities.
» Cons: Business leaders can bring resistance towards storing data off the company
premises and may therefore not trust that data security can be maintained away from
IT’s undeviating management in shared servers and storage facilities
Hybrid cloud deployment – involves an organization implementation both public
and private clouds for services access in order to gain from both kind of setups
» Pros: Hybrid cloud implementation provides data flexibility, reduces business costs
as well as delivering data privacy and protection with the private cloud option
» Cons: complicated to set up and difficult to manage and maintain. Its integration
requires expertise skills and knowledge
Community cloud deployment – this type involves a single cloud space
environment being utilized by more than one interrelated establishments who want to
get cloud services from the same applications and infrastructure
» Pros: For sectors that are closely related including government agencies, health
care, defense agencies, community cloud implementation offers secure data
transmission channel for sensitive data

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 6
» Cons: harmonization is necessary for all member organizations in a community
cloud setting such as cloud services provider and centralized storage locations, failure
to which will not work effectively among the members of the cloud community
Strengths of adopting cloud computing technology
Cloud computing advancement has significant potential to improve security and robustness in
a business (ENISA, 2012).
i) Mobility: cloud providers and cloud services users can both replicate cloud content
and access services in many localities respectively. Such a setting enhances data
independence and redundancy preventing failure and providing a level of back up
service
ii) Edge networks provision: cloud space offers processing, storage and delivery close to
the network control which increases overall quality and reliability hence reducing
network challenges
iii) Enhanced incident responsiveness and resolve: cloud offers aptness in terms of
responses to actions, requests and instances, it is possible to provide faster responses
to clients as well as detect service problems including intrusion and tapping which
assists in creating more efficient and effective instance responses
iv) Risk management: many cloud services providers can provide expert skills to deal
with cloud services security risks and vulnerabilities hence securing the services for
organizations. They also work with compliance regulations that ensure data privacy
and confidentiality for organizations.
Financial services sector review
Globally, the financial services sector plays the role of fund transfer from one entity to
another (Kolakowski, 2017). It includes enterprises involved in undertakings that include
money lending, insurance, investing and security trading with customers being individuals,
organizations and government agencies.
Australian financial service sector
Australia’s services sector has seen been experiencing progressive growth and the financial
services sector has not been left behind (Coyne, 2017). The financial sector growth has been
estimated to be expanding at 3.5 percent per year, outperforming other sectors that have a
growth rate of 3.3 percent per year (Narayan, 2015). Part of what has driven this growth is
ICT adoption including cloud computing.
Cloud computing adoption in the financial services sector
The financial services industry is already embracing various cloud services and deployment
models for ICT needs. This means that many business operations within financial sector are
» Cons: harmonization is necessary for all member organizations in a community
cloud setting such as cloud services provider and centralized storage locations, failure
to which will not work effectively among the members of the cloud community
Strengths of adopting cloud computing technology
Cloud computing advancement has significant potential to improve security and robustness in
a business (ENISA, 2012).
i) Mobility: cloud providers and cloud services users can both replicate cloud content
and access services in many localities respectively. Such a setting enhances data
independence and redundancy preventing failure and providing a level of back up
service
ii) Edge networks provision: cloud space offers processing, storage and delivery close to
the network control which increases overall quality and reliability hence reducing
network challenges
iii) Enhanced incident responsiveness and resolve: cloud offers aptness in terms of
responses to actions, requests and instances, it is possible to provide faster responses
to clients as well as detect service problems including intrusion and tapping which
assists in creating more efficient and effective instance responses
iv) Risk management: many cloud services providers can provide expert skills to deal
with cloud services security risks and vulnerabilities hence securing the services for
organizations. They also work with compliance regulations that ensure data privacy
and confidentiality for organizations.
Financial services sector review
Globally, the financial services sector plays the role of fund transfer from one entity to
another (Kolakowski, 2017). It includes enterprises involved in undertakings that include
money lending, insurance, investing and security trading with customers being individuals,
organizations and government agencies.
Australian financial service sector
Australia’s services sector has seen been experiencing progressive growth and the financial
services sector has not been left behind (Coyne, 2017). The financial sector growth has been
estimated to be expanding at 3.5 percent per year, outperforming other sectors that have a
growth rate of 3.3 percent per year (Narayan, 2015). Part of what has driven this growth is
ICT adoption including cloud computing.
Cloud computing adoption in the financial services sector
The financial services industry is already embracing various cloud services and deployment
models for ICT needs. This means that many business operations within financial sector are
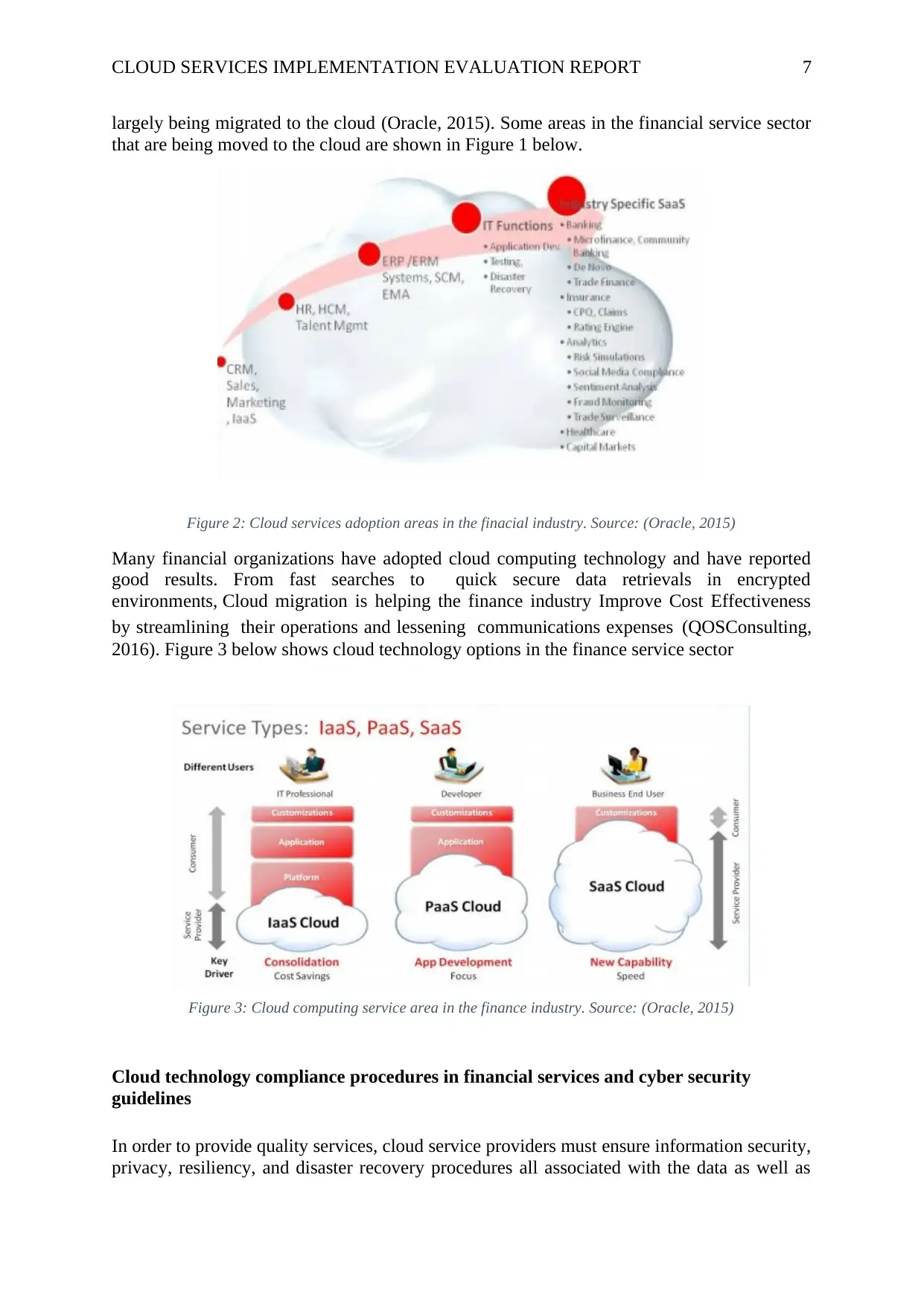
CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 7
largely being migrated to the cloud (Oracle, 2015). Some areas in the financial service sector
that are being moved to the cloud are shown in Figure 1 below.
Figure 2: Cloud services adoption areas in the finacial industry. Source: (Oracle, 2015)
Many financial organizations have adopted cloud computing technology and have reported
good results. From fast searches to quick secure data retrievals in encrypted
environments, Cloud migration is helping the finance industry Improve Cost Effectiveness
by streamlining their operations and lessening communications expenses (QOSConsulting,
2016). Figure 3 below shows cloud technology options in the finance service sector
Figure 3: Cloud computing service area in the finance industry. Source: (Oracle, 2015)
Cloud technology compliance procedures in financial services and cyber security
guidelines
In order to provide quality services, cloud service providers must ensure information security,
privacy, resiliency, and disaster recovery procedures all associated with the data as well as
largely being migrated to the cloud (Oracle, 2015). Some areas in the financial service sector
that are being moved to the cloud are shown in Figure 1 below.
Figure 2: Cloud services adoption areas in the finacial industry. Source: (Oracle, 2015)
Many financial organizations have adopted cloud computing technology and have reported
good results. From fast searches to quick secure data retrievals in encrypted
environments, Cloud migration is helping the finance industry Improve Cost Effectiveness
by streamlining their operations and lessening communications expenses (QOSConsulting,
2016). Figure 3 below shows cloud technology options in the finance service sector
Figure 3: Cloud computing service area in the finance industry. Source: (Oracle, 2015)
Cloud technology compliance procedures in financial services and cyber security
guidelines
In order to provide quality services, cloud service providers must ensure information security,
privacy, resiliency, and disaster recovery procedures all associated with the data as well as
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 8
creditworthiness of the providers themselves. These elements are essential towards
developing successful cloud strategy for organizations. As such, financial services sectors
need to comply within several procedures to ensure data integrity both for themselves and
their customers. Service agreement compliance procedures allows clients to comprehend the
strong control processes for cloud services and helps them to conserve data protection and
security (Scrofani, 2017).
Cloud computing deployment for Aztec Limited
Cloud technology can greatly improve business productivity for Aztec Limited. To ensure
sustainability of business functions in the cloud Aztec can make use of tools that provide
security and enables cloud services legal or governmental compliance standards. By adopting
cloud services, Aztec will benefit from the following according to (Nomani, 2016).
Benefits of cloud adoption for Aztec
ix) Cloud computing deployment will enable Aztec to boost their financial agility
through capability to enter newer regions (Coles, 2017).
x) Aztec will be able to add efficiency in all its business operations
xi) Aztec will be able to reduce operational costs associated with new software and
hardware and storage acquisition by ensuring the essential infrastructure resources
are available as they can now be accessed on the Internet
xii) Cloud computing will provide regular services and systems monitoring
xiii) Cloud services will also help in business continuity by providing growth and
sustainability of Aztec
xiv) Improved mobility as business processes flexibility as they can now be accessed
from any place at any time
xv) Data and information centralization allowing quick retrieval and updates
xvi) Improved collaboration with prospective and existing clients and stakeholders
Benefits of cloud adoption to customers
Cloud computing for Aztec Limited will not only benefit the business but will also benefit its
clients. According to (Khurana, 2017), some of the benefits that client customers will obtain
will include the following:
i) Data privacy
ii) Clients will overcome geographical limitations and can access Aztec services from
anywhere at any time
iii) Decrease in travel costs
iv) 24/7 services access
v) Active customer services engagement with Aztec
Cloud adoption Threats and vulnerabilities
creditworthiness of the providers themselves. These elements are essential towards
developing successful cloud strategy for organizations. As such, financial services sectors
need to comply within several procedures to ensure data integrity both for themselves and
their customers. Service agreement compliance procedures allows clients to comprehend the
strong control processes for cloud services and helps them to conserve data protection and
security (Scrofani, 2017).
Cloud computing deployment for Aztec Limited
Cloud technology can greatly improve business productivity for Aztec Limited. To ensure
sustainability of business functions in the cloud Aztec can make use of tools that provide
security and enables cloud services legal or governmental compliance standards. By adopting
cloud services, Aztec will benefit from the following according to (Nomani, 2016).
Benefits of cloud adoption for Aztec
ix) Cloud computing deployment will enable Aztec to boost their financial agility
through capability to enter newer regions (Coles, 2017).
x) Aztec will be able to add efficiency in all its business operations
xi) Aztec will be able to reduce operational costs associated with new software and
hardware and storage acquisition by ensuring the essential infrastructure resources
are available as they can now be accessed on the Internet
xii) Cloud computing will provide regular services and systems monitoring
xiii) Cloud services will also help in business continuity by providing growth and
sustainability of Aztec
xiv) Improved mobility as business processes flexibility as they can now be accessed
from any place at any time
xv) Data and information centralization allowing quick retrieval and updates
xvi) Improved collaboration with prospective and existing clients and stakeholders
Benefits of cloud adoption to customers
Cloud computing for Aztec Limited will not only benefit the business but will also benefit its
clients. According to (Khurana, 2017), some of the benefits that client customers will obtain
will include the following:
i) Data privacy
ii) Clients will overcome geographical limitations and can access Aztec services from
anywhere at any time
iii) Decrease in travel costs
iv) 24/7 services access
v) Active customer services engagement with Aztec
Cloud adoption Threats and vulnerabilities

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 9
Deploying cloud technology at Aztec comes with several risks (Shagin, 2012). Some of the
risks that may come with cloud computing adoption at Aztec include the following:
i) Network dependency – access cloud services means that Aztec requires a stable
computer network at all times
ii) Complexity in creating hybrid systems – Aztec limited is a financial organization
and may hold sensitive data which is not easy to store off the company premises
iii) Data centralization – keeping all the company information is risky as it can get lost
or be maliciously accessed
iv) Data insecurity - cloud computing services on the internet can easily be hacked
into by hackers and other intruders
v) Loss of governance – Aztec will lose control of their informational storage
facilities as they will be controlled by an external party (ENISA, 2012)
vi) Bring Your Own Device (BYOD) risks
vii) Service inaccessibility due to failure in the network or simply lack of services
from cloud providers
viii) Vendor lock-in which leads to dependence on services provided by a particular
provider which could limit the business only to that provider
(CloudStandardsCustomerCouncil, 2015)
Risk Management
A risk is a future uncertainty regarding a business procedure (TheEconomicTimes, 2017).
Thus a risk is the likelihood of an unsafe event that could negatively affect the achievement
of organizational objectives. It is essential to manage risks in a business to ensure business
productivity (Djemame, Armstrong, Guitart, & Macias, 2014). Risk management is measured
in terms of the impacts an event is likely to cause (Misra, 2008). For business continuity, it
would be crucial to manage all the threats and susceptibilities that can cause negative impacts
at Aztec through the use of several procedures
Mobile device management
Mobile device management refers to measures employed by a company to manage
and control the usage or mobile devices in the company network (Ferrill, 2017). The
digital shift together with ubiquitous technology including mobile computing devices
such as notebook computers, smart phones, tablet computers, kindles and more have
accelerated the rate at which employees carry these and use mobile devices which has
led to the concept of bring your own device(BYOD) . The work place has not been
spared as many staff members carry and use personal mobile devices at work. Some
companies allow BYOD at work while some do not. It is important to manage mobile
device management as they can be a way through which an attacker can access
company network.
Data backup procedures
Back up involves copying data in secondary physical or virtual spaces for retrieval in
case of a disaster (Kraanz, 2016). Performing data backup helps organization to
manage risks and any other uncertainties. Organizations that implement cloud
services should therefore employ data backup procedures for use in the event of
disasters and data security breaches
Backbone network
Backbone networks refer to many internet connections providing efficient data
exchanges (Dharmaweera, Rajendran, & Sekercioglu, 2011). For network efficiency
Deploying cloud technology at Aztec comes with several risks (Shagin, 2012). Some of the
risks that may come with cloud computing adoption at Aztec include the following:
i) Network dependency – access cloud services means that Aztec requires a stable
computer network at all times
ii) Complexity in creating hybrid systems – Aztec limited is a financial organization
and may hold sensitive data which is not easy to store off the company premises
iii) Data centralization – keeping all the company information is risky as it can get lost
or be maliciously accessed
iv) Data insecurity - cloud computing services on the internet can easily be hacked
into by hackers and other intruders
v) Loss of governance – Aztec will lose control of their informational storage
facilities as they will be controlled by an external party (ENISA, 2012)
vi) Bring Your Own Device (BYOD) risks
vii) Service inaccessibility due to failure in the network or simply lack of services
from cloud providers
viii) Vendor lock-in which leads to dependence on services provided by a particular
provider which could limit the business only to that provider
(CloudStandardsCustomerCouncil, 2015)
Risk Management
A risk is a future uncertainty regarding a business procedure (TheEconomicTimes, 2017).
Thus a risk is the likelihood of an unsafe event that could negatively affect the achievement
of organizational objectives. It is essential to manage risks in a business to ensure business
productivity (Djemame, Armstrong, Guitart, & Macias, 2014). Risk management is measured
in terms of the impacts an event is likely to cause (Misra, 2008). For business continuity, it
would be crucial to manage all the threats and susceptibilities that can cause negative impacts
at Aztec through the use of several procedures
Mobile device management
Mobile device management refers to measures employed by a company to manage
and control the usage or mobile devices in the company network (Ferrill, 2017). The
digital shift together with ubiquitous technology including mobile computing devices
such as notebook computers, smart phones, tablet computers, kindles and more have
accelerated the rate at which employees carry these and use mobile devices which has
led to the concept of bring your own device(BYOD) . The work place has not been
spared as many staff members carry and use personal mobile devices at work. Some
companies allow BYOD at work while some do not. It is important to manage mobile
device management as they can be a way through which an attacker can access
company network.
Data backup procedures
Back up involves copying data in secondary physical or virtual spaces for retrieval in
case of a disaster (Kraanz, 2016). Performing data backup helps organization to
manage risks and any other uncertainties. Organizations that implement cloud
services should therefore employ data backup procedures for use in the event of
disasters and data security breaches
Backbone network
Backbone networks refer to many internet connections providing efficient data
exchanges (Dharmaweera, Rajendran, & Sekercioglu, 2011). For network efficiency
CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 10
and proper access and usage of cloud services, a business has to have a robust
computer network. To ensure such effectiveness, it is vital to install backbone
networks to support cloud applications, services and infrastructure operations over the
Internet
Data authentication and authorization
Company that adopt cloud services should ensure that only the authorized and
authenticated systems and individuals can access their data and information for
security and privacy maintenance.
Data security risks for cloud services
Cloud computing offers amazing benefits for business organizations. However, there exists
multiple challenges for both individual users and enterprises. One of the most challenging
issue with cloud computing is data security, which goes hand in hand with factors including
privacy, trust, legal and compliance matters (Xiao & Xiao, 2013). Data security is a main
issue with regards to deploying cloud technology for business. Many data breaches including
the recent Wanna cry attack prove that data security is very important for cloud services
adoption success. However in the modern cloud computing environment, data insecurity is
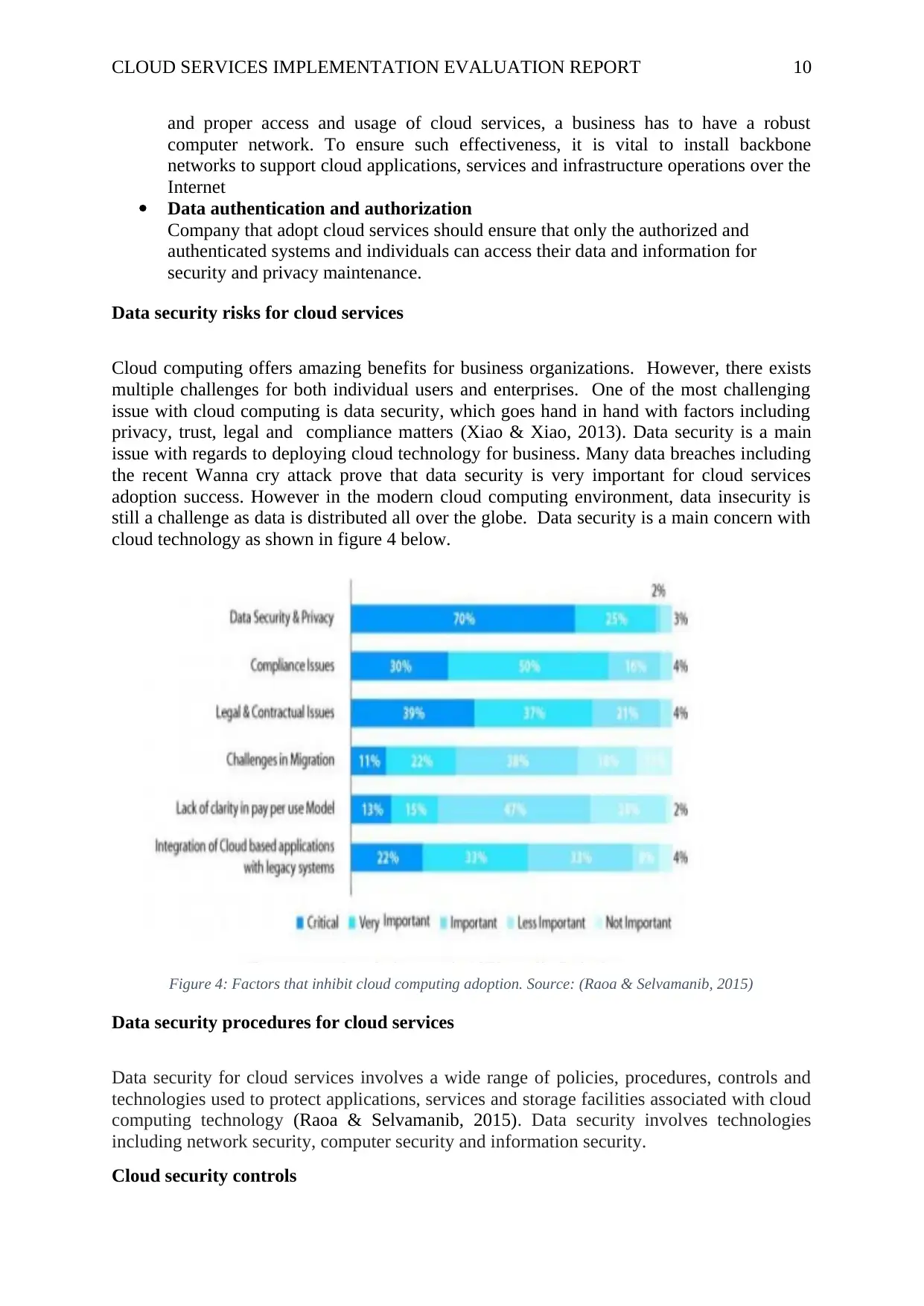
still a challenge as data is distributed all over the globe. Data security is a main concern with
cloud technology as shown in figure 4 below.
Figure 4: Factors that inhibit cloud computing adoption. Source: (Raoa & Selvamanib, 2015)
Data security procedures for cloud services
Data security for cloud services involves a wide range of policies, procedures, controls and
technologies used to protect applications, services and storage facilities associated with cloud
computing technology (Raoa & Selvamanib, 2015). Data security involves technologies
including network security, computer security and information security.
Cloud security controls
and proper access and usage of cloud services, a business has to have a robust
computer network. To ensure such effectiveness, it is vital to install backbone
networks to support cloud applications, services and infrastructure operations over the
Internet
Data authentication and authorization
Company that adopt cloud services should ensure that only the authorized and
authenticated systems and individuals can access their data and information for
security and privacy maintenance.
Data security risks for cloud services
Cloud computing offers amazing benefits for business organizations. However, there exists
multiple challenges for both individual users and enterprises. One of the most challenging
issue with cloud computing is data security, which goes hand in hand with factors including
privacy, trust, legal and compliance matters (Xiao & Xiao, 2013). Data security is a main
issue with regards to deploying cloud technology for business. Many data breaches including
the recent Wanna cry attack prove that data security is very important for cloud services
adoption success. However in the modern cloud computing environment, data insecurity is
still a challenge as data is distributed all over the globe. Data security is a main concern with
cloud technology as shown in figure 4 below.
Figure 4: Factors that inhibit cloud computing adoption. Source: (Raoa & Selvamanib, 2015)
Data security procedures for cloud services
Data security for cloud services involves a wide range of policies, procedures, controls and
technologies used to protect applications, services and storage facilities associated with cloud
computing technology (Raoa & Selvamanib, 2015). Data security involves technologies
including network security, computer security and information security.
Cloud security controls
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 11
Several controls can be used to reduce data insecurity in cloud systems according to (Ronald
& Dean, 2010)
Deterrent controls - intended to lessen cloud services attack by letting attackers
know of harsh consequences that will face them if they go on and intrude cloud
systems
Preventive controls – involve controls to strengthen cloud system services against
attack instances by decreasing and eliminating vulnerabilities such as authentication
and encryption
Detective controls - anticipated to discover and to appropriately respond to any
attack attempts
Corrective controls – used to lessen data security breach effects by reducing the
damage and restoring the cloud systems in order to rebuild compromised systems
Organizations can adopt several practices to provide data privacy and security (Ivery, 2016)
that include the following
Avoid storing sensitive data on the cloud space’
Manage and control the security options and usage of mobile devices that connect I
the company network
Reading and ensuring a proper understanding of service level agreements from cloud
service providers
Ensure strong passwords and implement 2 factor authentication 2FA practices
Make use of strong encryption standards
Implement virtual private networks(VPN) for data transfer
Use encrypted service providers
Conclusion
As stated in the introductory part, technology advances continue to transform business
organizations through the digital shift. As such, a business that does not digitize its processes
will fail to achieve a competitive advantage and may eventually fail. This is from the dawn of
the fact that for business to continue their operations successfully, they need to adopt ICT
technologies. The financial industry is not left behind in the effort to embrace ICT for
business productivity. It is therefore beneficial for Aztec Limited to adopt cloud services to
enhance all its operations and achieve continuity.
Several controls can be used to reduce data insecurity in cloud systems according to (Ronald
& Dean, 2010)
Deterrent controls - intended to lessen cloud services attack by letting attackers
know of harsh consequences that will face them if they go on and intrude cloud
systems
Preventive controls – involve controls to strengthen cloud system services against
attack instances by decreasing and eliminating vulnerabilities such as authentication
and encryption
Detective controls - anticipated to discover and to appropriately respond to any
attack attempts
Corrective controls – used to lessen data security breach effects by reducing the
damage and restoring the cloud systems in order to rebuild compromised systems
Organizations can adopt several practices to provide data privacy and security (Ivery, 2016)
that include the following
Avoid storing sensitive data on the cloud space’
Manage and control the security options and usage of mobile devices that connect I
the company network
Reading and ensuring a proper understanding of service level agreements from cloud
service providers
Ensure strong passwords and implement 2 factor authentication 2FA practices
Make use of strong encryption standards
Implement virtual private networks(VPN) for data transfer
Use encrypted service providers
Conclusion
As stated in the introductory part, technology advances continue to transform business
organizations through the digital shift. As such, a business that does not digitize its processes
will fail to achieve a competitive advantage and may eventually fail. This is from the dawn of
the fact that for business to continue their operations successfully, they need to adopt ICT
technologies. The financial industry is not left behind in the effort to embrace ICT for
business productivity. It is therefore beneficial for Aztec Limited to adopt cloud services to
enhance all its operations and achieve continuity.

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 12
References
CloudStandardsCustomerCouncil. (2015). Security for Cloud Computing. Retrieved from
http://www.cloud-council.org: http://www.cloud-council.org/deliverables/CSCC-
Security-for-Cloud-Computing-10-Steps-to-Ensure-Success.pdf
Coles, C. (2017, September). Advantages of Cloud Computing and How Your Business Can
Benefit From Them. Retrieved from Sky High Networks:
https://www.skyhighnetworks.com/cloud-security-blog/11-advantages-of-cloud-
computing-and-how-your-business-can-benefit-from-them/
Coyne, A. (2017, July 20). Cloud computing adoption in Australia is booming. Retrieved
from IT News : https://www.itnews.com.au/news/cloud-computing-adoption-in-
australia-is-booming-468833
Dharmaweera, N., Rajendran, R., & Sekercioglu, A. (2011). Toward a Power-Efficient
Backbone Network: The State of Research. Retrieved from
http://titania.ctie.monash.edu.au/: http://titania.ctie.monash.edu.au/papers/power-
efficient-bbone.pdf
Djemame, K., Armstrong, D., Guitart, J., & Macias, M. (2014). A Risk Assessment
Framework for Cloud Computing. IEEE White Rose Research , 2-3.
ENISA. (2012, December). Cloud Computing Benefits, risks and recommendations for
information security. Retrieved from resilience.enisa.europa.eu:
https://resilience.enisa.europa.eu/cloud-security-and-resilience/publications/cloud-
computing-benefits-risks-and-recommendations-for-information-security
Ferrill, P. (2017, June 20). The Best Mobile Device Management (MDM) Solutions of 2017.
Retrieved from PC Mag: https://www.pcmag.com/article/342695/the-best-mobile-
device-management-mdm-software
GetSix. (2017, September). The Types of Cloud Computing. Retrieved from getsix.eu:
http://getsix.eu/resources/glossary/the-types-of-cloud-computing/
Haghighat, M., Zonouz, S., & Abdel-Mottaleb, M. (2015). Cloud ID: Trustworthy cloud
based and cross- enterprise biometric identification. Expert Systems with Applications,
7905-7916.
IBM. (2017, September ). What is cloud computing? Retrieved from www.ibm.com:
https://www.ibm.com/cloud-computing/learn-more/what-is-cloud-computing/
Ivery, V. (2016, December 16). Tips to Keep Your Data Secure on the Cloud. Retrieved from
www.cio.com: https://www.cio.com/article/2380182/cloud-security/5-tips-to-keep-
your-data-secure-on-the-cloud.html
Khurana, A. (2017, April 18). Advantages of E-commerce Over Traditional Retail. Retrieved
from The Balance: https://www.thebalance.com/advantages-of-ecommerce-1141610
References
CloudStandardsCustomerCouncil. (2015). Security for Cloud Computing. Retrieved from
http://www.cloud-council.org: http://www.cloud-council.org/deliverables/CSCC-
Security-for-Cloud-Computing-10-Steps-to-Ensure-Success.pdf
Coles, C. (2017, September). Advantages of Cloud Computing and How Your Business Can
Benefit From Them. Retrieved from Sky High Networks:
https://www.skyhighnetworks.com/cloud-security-blog/11-advantages-of-cloud-
computing-and-how-your-business-can-benefit-from-them/
Coyne, A. (2017, July 20). Cloud computing adoption in Australia is booming. Retrieved
from IT News : https://www.itnews.com.au/news/cloud-computing-adoption-in-
australia-is-booming-468833
Dharmaweera, N., Rajendran, R., & Sekercioglu, A. (2011). Toward a Power-Efficient
Backbone Network: The State of Research. Retrieved from
http://titania.ctie.monash.edu.au/: http://titania.ctie.monash.edu.au/papers/power-
efficient-bbone.pdf
Djemame, K., Armstrong, D., Guitart, J., & Macias, M. (2014). A Risk Assessment
Framework for Cloud Computing. IEEE White Rose Research , 2-3.
ENISA. (2012, December). Cloud Computing Benefits, risks and recommendations for
information security. Retrieved from resilience.enisa.europa.eu:
https://resilience.enisa.europa.eu/cloud-security-and-resilience/publications/cloud-
computing-benefits-risks-and-recommendations-for-information-security
Ferrill, P. (2017, June 20). The Best Mobile Device Management (MDM) Solutions of 2017.
Retrieved from PC Mag: https://www.pcmag.com/article/342695/the-best-mobile-
device-management-mdm-software
GetSix. (2017, September). The Types of Cloud Computing. Retrieved from getsix.eu:
http://getsix.eu/resources/glossary/the-types-of-cloud-computing/
Haghighat, M., Zonouz, S., & Abdel-Mottaleb, M. (2015). Cloud ID: Trustworthy cloud
based and cross- enterprise biometric identification. Expert Systems with Applications,
7905-7916.
IBM. (2017, September ). What is cloud computing? Retrieved from www.ibm.com:
https://www.ibm.com/cloud-computing/learn-more/what-is-cloud-computing/
Ivery, V. (2016, December 16). Tips to Keep Your Data Secure on the Cloud. Retrieved from
www.cio.com: https://www.cio.com/article/2380182/cloud-security/5-tips-to-keep-
your-data-secure-on-the-cloud.html
Khurana, A. (2017, April 18). Advantages of E-commerce Over Traditional Retail. Retrieved
from The Balance: https://www.thebalance.com/advantages-of-ecommerce-1141610

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 13
Kolakowski, M. (2017, March 12). Financial Services Industry Basics. Retrieved from
www.thebalance.com: https://www.thebalance.com/the-financial-services-industry-
1287307
Kraanz, G. (2016, September). Back up. Retrieved from Tech Target :
http://searchdatabackup.techtarget.com/definition/backup
Mell, P., & Grance, T. (2011). National Institute of Standards and Technology: U.S.
Department of Commerce. NIST, 800-145.
Misra, K. (2008). Risk analysis and management: An introduction in Handbook of
Performability Engineering. Springer London, 667-681.
Narayan, P. (2015, July 29). An assessment of the Australian financial. Retrieved from
www.ilo.org: http://www.ilo.org/wcmsp5/groups/public/---asia/---ro-bangkok/---ilo-
jakarta/documents/meetingdocument/wcms_396163.pdf
Nomani, M. (2016, October 5). Cloud Computing Benefits Financial Sector. Retrieved from
Information Week:
https://www.informationweek.com/partner-perspectives/ibm/cloud-computing-
benefits-financial-sector/a/d-id/1325455
Oracle. (2015, November). Oracle Financial Services . Retrieved from www.oracle.com:
http://www.oracle.com/us/industries/financial-services/cloud-compute-financial-
services-wp-3124965.pdf
QOSConsulting. (2016, September 8). Cloud Technology: The new Key to Financial Services
Success. Retrieved from QOS Consulting : https://qos-consulting.com/cloud-
technology-new-key-financial-services-success/
Raoa, V., & Selvamanib, K. (2015). Data Security Challenges and Its Solutions in Cloud
Computing. International Conference on Intelligent Computing, Communication &
Convergence, 204-209.
Ronald, K., & Dean, R. (2010). Cloud Security: A Comprehensive Guide to Secure Cloud
Computing. Indianapolis, IN: Wiley, 80-179.
Scrofani, J. (2017, January 18). Compliance in the Cloud for New Financial Services
Cybersecurity Regulations. Retrieved from Amazon:
https://aws.amazon.com/blogs/security/compliance-in-the-cloud-for-new-financial-
services-cybersecurity-regulation
Shagin, A. (2012, October 5). The risks and benefits of cloud computing . Retrieved from
Digitalistmag.com:
https://www.digitalistmag.com/technologies/cloud-computing/2012/10/25/risks-and-
benefits-of-cloud-computing-020025
TheEconomicTimes. (2017, September ). Definition of 'Risk'. Retrieved from economic
times: http://economictimes.indiatimes.com/definition/risk
Xiao, Z., & Xiao, Y. (2013). Security and privacy in cloud computing. IEEE
Communications Surveys & Tutorials, 843-849.
Kolakowski, M. (2017, March 12). Financial Services Industry Basics. Retrieved from
www.thebalance.com: https://www.thebalance.com/the-financial-services-industry-
1287307
Kraanz, G. (2016, September). Back up. Retrieved from Tech Target :
http://searchdatabackup.techtarget.com/definition/backup
Mell, P., & Grance, T. (2011). National Institute of Standards and Technology: U.S.
Department of Commerce. NIST, 800-145.
Misra, K. (2008). Risk analysis and management: An introduction in Handbook of
Performability Engineering. Springer London, 667-681.
Narayan, P. (2015, July 29). An assessment of the Australian financial. Retrieved from
www.ilo.org: http://www.ilo.org/wcmsp5/groups/public/---asia/---ro-bangkok/---ilo-
jakarta/documents/meetingdocument/wcms_396163.pdf
Nomani, M. (2016, October 5). Cloud Computing Benefits Financial Sector. Retrieved from
Information Week:
https://www.informationweek.com/partner-perspectives/ibm/cloud-computing-
benefits-financial-sector/a/d-id/1325455
Oracle. (2015, November). Oracle Financial Services . Retrieved from www.oracle.com:
http://www.oracle.com/us/industries/financial-services/cloud-compute-financial-
services-wp-3124965.pdf
QOSConsulting. (2016, September 8). Cloud Technology: The new Key to Financial Services
Success. Retrieved from QOS Consulting : https://qos-consulting.com/cloud-
technology-new-key-financial-services-success/
Raoa, V., & Selvamanib, K. (2015). Data Security Challenges and Its Solutions in Cloud
Computing. International Conference on Intelligent Computing, Communication &
Convergence, 204-209.
Ronald, K., & Dean, R. (2010). Cloud Security: A Comprehensive Guide to Secure Cloud
Computing. Indianapolis, IN: Wiley, 80-179.
Scrofani, J. (2017, January 18). Compliance in the Cloud for New Financial Services
Cybersecurity Regulations. Retrieved from Amazon:
https://aws.amazon.com/blogs/security/compliance-in-the-cloud-for-new-financial-
services-cybersecurity-regulation
Shagin, A. (2012, October 5). The risks and benefits of cloud computing . Retrieved from
Digitalistmag.com:
https://www.digitalistmag.com/technologies/cloud-computing/2012/10/25/risks-and-
benefits-of-cloud-computing-020025
TheEconomicTimes. (2017, September ). Definition of 'Risk'. Retrieved from economic
times: http://economictimes.indiatimes.com/definition/risk
Xiao, Z., & Xiao, Y. (2013). Security and privacy in cloud computing. IEEE
Communications Surveys & Tutorials, 843-849.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 14

CLOUD SERVICES IMPLEMENTATION EVALUATION REPORT 15
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





