University Report: Cloud Systems and Applications Literature Review
VerifiedAdded on 2023/06/05
|14
|3230
|363
Report
AI Summary
This report provides a comprehensive literature review of cloud systems and applications, exploring major service models such as IaaS, PaaS, and SaaS, along with cloud computing security best practices. It compares and contrasts the characteristics of various cloud deployment models, including public, private, community, and hybrid clouds, and their adoption in business organizations. The report delves into the considerations for adopting a hybrid cloud model. It identifies the main security and privacy threats associated with cloud computing and discusses the risks and threats specific to different cloud deployment models. Furthermore, it examines security solutions and standards in cloud environments, along with the various security tools available. The report emphasizes the importance of encryption, security solutions, and the challenges related to interoperability, data migration, and security issues in cloud environments. This report also touches on the benefits of cloud computing in terms of cost reduction, scalability, and business process improvement.

Running head: CLOUD SYSTEMS AND APPLICATIONS
Cloud Systems and Applications: Literature Review
Name of the Student
Name of the University
Author’s Note
Cloud Systems and Applications: Literature Review
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CLOUD SYSTEMS AND APPLICATIONS
Table of Contents
Major service model of cloud computing and cloud computing security best practices...........2
Comparing characteristics of four main cloud deployment models and their adoption in
business organization.................................................................................................................5
Hybrid cloud considered for an organization.............................................................................7
Main security and privacy threats related to cloud computing..................................................8
Risks and threats for the cloud deployment models -............................................................8
Security solution and standards in cloud environment -........................................................9
Security tools for cloud computing......................................................................................10
References................................................................................................................................11
CLOUD SYSTEMS AND APPLICATIONS
Table of Contents
Major service model of cloud computing and cloud computing security best practices...........2
Comparing characteristics of four main cloud deployment models and their adoption in
business organization.................................................................................................................5
Hybrid cloud considered for an organization.............................................................................7
Main security and privacy threats related to cloud computing..................................................8
Risks and threats for the cloud deployment models -............................................................8
Security solution and standards in cloud environment -........................................................9
Security tools for cloud computing......................................................................................10
References................................................................................................................................11

2
CLOUD SYSTEMS AND APPLICATIONS
Major service model of cloud computing and cloud computing security best
practices
There are different service models and they are divided into IaaS, PaaS and SaaS and
they are defined below:
Infrastructure as a Service (IaaS) – Infrastructure as a Service is used as a self-
service model and helps in remote management of large IT infrastructure such as data
centres. It can provide virtualisation of the computer resources using the internet and hosted
by third party service providers such as Azure, Google and Amazon web service. The
organization can use the service instead of purchasing hardware and payment is made for the
resource used (Almorsy, Grundy and Müller 2016). With the model the company can add or
modify the It infrastructure based on their needs and it is also preferred by many of the
organization since it is more familiar than the other two model. The model is capable of
delivering strict security requirement and regulations for the business models.
Figure 1: IaaS Architecture
(Source: Cloudoye Blog. 2019)
CLOUD SYSTEMS AND APPLICATIONS
Major service model of cloud computing and cloud computing security best
practices
There are different service models and they are divided into IaaS, PaaS and SaaS and
they are defined below:
Infrastructure as a Service (IaaS) – Infrastructure as a Service is used as a self-
service model and helps in remote management of large IT infrastructure such as data
centres. It can provide virtualisation of the computer resources using the internet and hosted
by third party service providers such as Azure, Google and Amazon web service. The
organization can use the service instead of purchasing hardware and payment is made for the
resource used (Almorsy, Grundy and Müller 2016). With the model the company can add or
modify the It infrastructure based on their needs and it is also preferred by many of the
organization since it is more familiar than the other two model. The model is capable of
delivering strict security requirement and regulations for the business models.
Figure 1: IaaS Architecture
(Source: Cloudoye Blog. 2019)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CLOUD SYSTEMS AND APPLICATIONS
Platform as a service (PaaS) – It allows the organization to run, build and managing
applications without the need to manage applications without the need of IT infrastructure. It
can be used for faster and easier deployment and deploying and testing different types of
applications (Manuel 2015). The development team can reduce the time of development as
they do not need to worry about the IT infrastructure activities for example backup and
storage, provisioning servers and thus they can concentrate on developing the codes and
creating applications. The management overhead cost can be reduced and reduces the cost.
The use of PaaS makes it easy to scale and innovate the service on demand.
Figure 2: PaaS Architecture
(Source: Milesweb.com. 2019)
Software as a Service (SaaS) – It can be deployed for replacing the traditional on
device software which are licensed on the basis of subscription. It can be hosted in the cloud
centrally and thus can be accessed directly using the web browser eliminating the need of
CLOUD SYSTEMS AND APPLICATIONS
Platform as a service (PaaS) – It allows the organization to run, build and managing
applications without the need to manage applications without the need of IT infrastructure. It
can be used for faster and easier deployment and deploying and testing different types of
applications (Manuel 2015). The development team can reduce the time of development as
they do not need to worry about the IT infrastructure activities for example backup and
storage, provisioning servers and thus they can concentrate on developing the codes and
creating applications. The management overhead cost can be reduced and reduces the cost.
The use of PaaS makes it easy to scale and innovate the service on demand.
Figure 2: PaaS Architecture
(Source: Milesweb.com. 2019)
Software as a Service (SaaS) – It can be deployed for replacing the traditional on
device software which are licensed on the basis of subscription. It can be hosted in the cloud
centrally and thus can be accessed directly using the web browser eliminating the need of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CLOUD SYSTEMS AND APPLICATIONS
installation or downloading (Shaikh and Sasikumar 2015). There are some SaaS application
that needs plugin for running.
Figure 3 – SaaS Platform
(Source: Milesweb.com. 2019)
The security of the cloud servers are an important and it can be achieved with
implementing broad set of policies and encryption mechanism such that the unauthorised
access to the resources is restricted. The data is available in a readable pain text format and
when it is transmitted over the network the plain text becomes vulnerable to malicious access
by any third party agents. The implementation of encryption mechanism helps in maintaining
confidentiality of the data and it can be applied for encoding the plain text into cipher text
such that the data is unavailable to the third party agents and the security is maintained
(Gangwar, Date and Ramaswamy 2015). The encryption is done with the help of
standardized algorithm for transforming the plain text into cipher text. With the application of
CLOUD SYSTEMS AND APPLICATIONS
installation or downloading (Shaikh and Sasikumar 2015). There are some SaaS application
that needs plugin for running.
Figure 3 – SaaS Platform
(Source: Milesweb.com. 2019)
The security of the cloud servers are an important and it can be achieved with
implementing broad set of policies and encryption mechanism such that the unauthorised
access to the resources is restricted. The data is available in a readable pain text format and
when it is transmitted over the network the plain text becomes vulnerable to malicious access
by any third party agents. The implementation of encryption mechanism helps in maintaining
confidentiality of the data and it can be applied for encoding the plain text into cipher text
such that the data is unavailable to the third party agents and the security is maintained
(Gangwar, Date and Ramaswamy 2015). The encryption is done with the help of
standardized algorithm for transforming the plain text into cipher text. With the application of
5
CLOUD SYSTEMS AND APPLICATIONS
the encryption in the plain text it is paired with an encryption key. The key is a secret
message that is used for sharing data with the authorized parties. The encryption may of two
forms such as symmetric and asymmetric in case of symmetric encryption the same key is
utilized for encrypting and decrypting the data (Gai et al. 2016). In case of asymmetric
encryption two different keys are used known as public and private key. The private key is
available with the owner of the message and the public key is common to all the users. A
message or document encrypted with a private key can be decrypted with its corresponding
public key. It offers integrity, protection with the non-repudiation and authenticity. The
communication channel is encrypted and different safeguard mechanism is applied for
maintaining confidentiality.
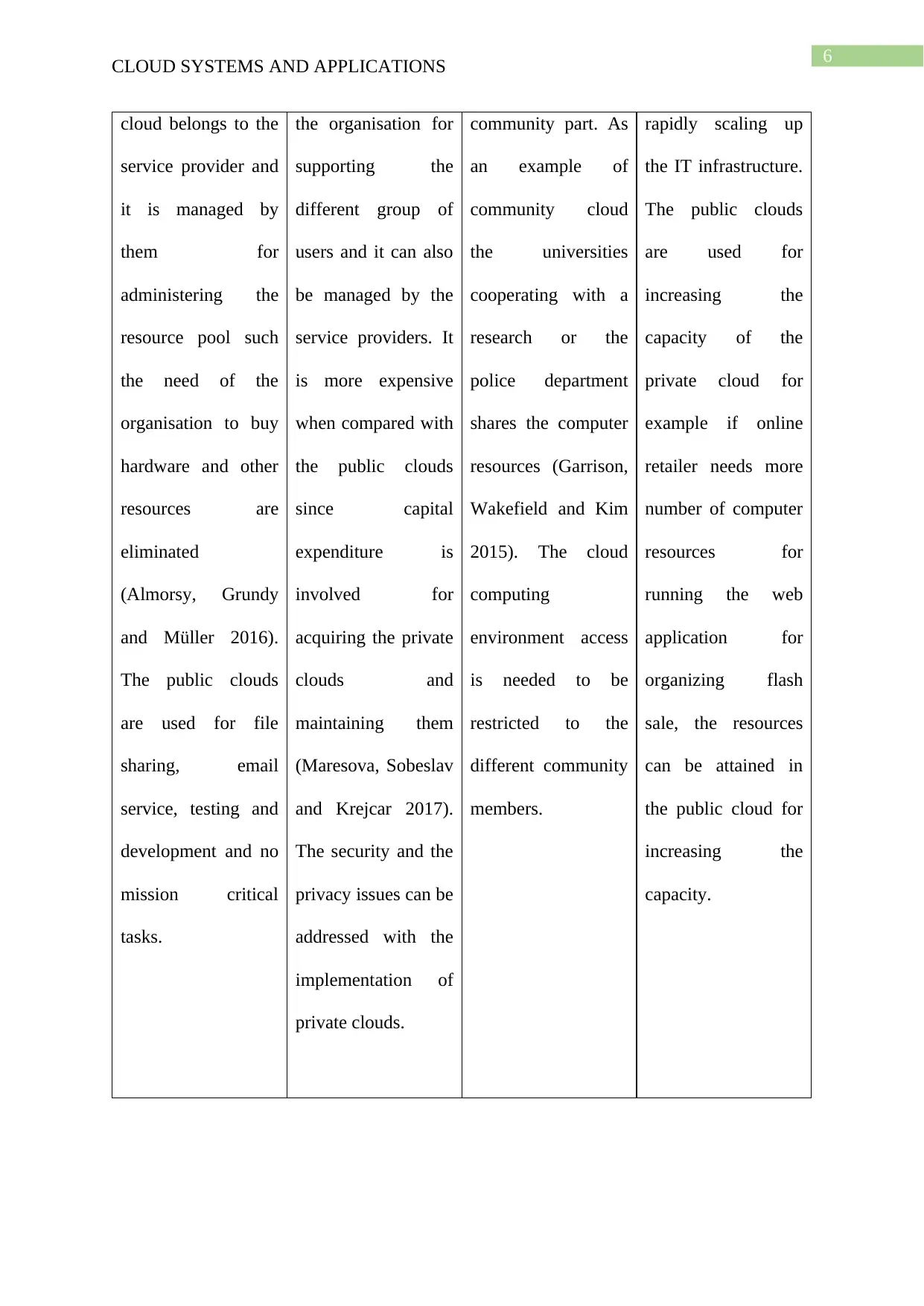
Comparing characteristics of four main cloud deployment models and their
adoption in business organization
There are four main cloud deployment models such as public cloud, private cloud,
community cloud and Hybrid cloud. Each of the cloud deployment model is developed for
different organizational needs and the success of the deployment depends on the selection of
the model aligning the requirement of the organisation.
Public cloud Private Cloud Community Cloud Hybrid Cloud
The public
cloud model is
available to all the
users and third party
servers are used for
storing the data. The
infrastructure of the
Private cloud
is used by single
organization and is
based on IaaS
service architecture.
The private cloud
are maintained by
Community
cloud model can be
used for supporting
sharing of the
computer resources
with multiple
organisation that is a
This are the
private and public
clouds
interconnected with
each other and it can
be used by the
organization for
CLOUD SYSTEMS AND APPLICATIONS
the encryption in the plain text it is paired with an encryption key. The key is a secret
message that is used for sharing data with the authorized parties. The encryption may of two
forms such as symmetric and asymmetric in case of symmetric encryption the same key is
utilized for encrypting and decrypting the data (Gai et al. 2016). In case of asymmetric
encryption two different keys are used known as public and private key. The private key is
available with the owner of the message and the public key is common to all the users. A
message or document encrypted with a private key can be decrypted with its corresponding
public key. It offers integrity, protection with the non-repudiation and authenticity. The
communication channel is encrypted and different safeguard mechanism is applied for
maintaining confidentiality.
Comparing characteristics of four main cloud deployment models and their
adoption in business organization
There are four main cloud deployment models such as public cloud, private cloud,
community cloud and Hybrid cloud. Each of the cloud deployment model is developed for
different organizational needs and the success of the deployment depends on the selection of
the model aligning the requirement of the organisation.
Public cloud Private Cloud Community Cloud Hybrid Cloud
The public
cloud model is
available to all the
users and third party
servers are used for
storing the data. The
infrastructure of the
Private cloud
is used by single
organization and is
based on IaaS
service architecture.
The private cloud
are maintained by
Community
cloud model can be
used for supporting
sharing of the
computer resources
with multiple
organisation that is a
This are the
private and public
clouds
interconnected with
each other and it can
be used by the
organization for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
CLOUD SYSTEMS AND APPLICATIONS
cloud belongs to the
service provider and
it is managed by
them for
administering the
resource pool such
the need of the
organisation to buy
hardware and other
resources are
eliminated
(Almorsy, Grundy
and Müller 2016).
The public clouds
are used for file
sharing, email
service, testing and
development and no
mission critical
tasks.
the organisation for
supporting the
different group of
users and it can also
be managed by the
service providers. It
is more expensive
when compared with
the public clouds
since capital
expenditure is
involved for
acquiring the private
clouds and
maintaining them
(Maresova, Sobeslav
and Krejcar 2017).
The security and the
privacy issues can be
addressed with the
implementation of
private clouds.
community part. As
an example of
community cloud
the universities
cooperating with a
research or the
police department
shares the computer
resources (Garrison,
Wakefield and Kim
2015). The cloud
computing
environment access
is needed to be
restricted to the
different community
members.
rapidly scaling up
the IT infrastructure.
The public clouds
are used for
increasing the
capacity of the
private cloud for
example if online
retailer needs more
number of computer
resources for
running the web
application for
organizing flash
sale, the resources
can be attained in
the public cloud for
increasing the
capacity.
CLOUD SYSTEMS AND APPLICATIONS
cloud belongs to the
service provider and
it is managed by
them for
administering the
resource pool such
the need of the
organisation to buy
hardware and other
resources are
eliminated
(Almorsy, Grundy
and Müller 2016).
The public clouds
are used for file
sharing, email
service, testing and
development and no
mission critical
tasks.
the organisation for
supporting the
different group of
users and it can also
be managed by the
service providers. It
is more expensive
when compared with
the public clouds
since capital
expenditure is
involved for
acquiring the private
clouds and
maintaining them
(Maresova, Sobeslav
and Krejcar 2017).
The security and the
privacy issues can be
addressed with the
implementation of
private clouds.
community part. As
an example of
community cloud
the universities
cooperating with a
research or the
police department
shares the computer
resources (Garrison,
Wakefield and Kim
2015). The cloud
computing
environment access
is needed to be
restricted to the
different community
members.
rapidly scaling up
the IT infrastructure.
The public clouds
are used for
increasing the
capacity of the
private cloud for
example if online
retailer needs more
number of computer
resources for
running the web
application for
organizing flash
sale, the resources
can be attained in
the public cloud for
increasing the
capacity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CLOUD SYSTEMS AND APPLICATIONS
With the implementation of the public cloud the cost can be lowered since it has no
capital expenditure involved and the private clouds has higher capital expenditure cost but the
cost is less than the owning private infrastructure and allows pooling of resources. Due to the
elastic nature of cloud computing the critical application deploys in cloud for supporting and
deployment of different application. For the deployment the application packages are
transmitted to the clouds from the service providers (Thota et al. 2018).
A step by step procedure is needed to be followed for the deployment of the cloud
service and it helps in adaptive application that is used for seamlessly migrating and scaling
from failures. Bandwidth aware scheduled algorithm is used for minimizing the deployment
numbers and utilizing the maximum bandwidth of the network. The cloud computing is
becoming a platform for its deployment in business and for the execution of application in the
cloud it is important for making required software. For the application that needs
infrastructure level optimization the software as a service and platform as a service is not
sufficient (Dahlberg, Kivijärvi and Saarinen 2017). The enterprises have heightened the
interest for adopting cloud computing in the past decades since it promises to reshape the way
according to the needs of the enterprise and management of their needs to compute resources
cost effectively and efficiently.
The cloud computing can be considered as an innovative model for generation of
values for the enterprise. The core business activity can be focused for improvement of the
productivity and with the increase in adoption the scalability, maintainability and the growth
of the organization can be improved (Lian 2017). The cloud computing is used for providing
the users an internet based computing service and it is built on existing computer technology
such as virtualization, grid computing and other forms of distributed computing.
CLOUD SYSTEMS AND APPLICATIONS
With the implementation of the public cloud the cost can be lowered since it has no
capital expenditure involved and the private clouds has higher capital expenditure cost but the
cost is less than the owning private infrastructure and allows pooling of resources. Due to the
elastic nature of cloud computing the critical application deploys in cloud for supporting and
deployment of different application. For the deployment the application packages are
transmitted to the clouds from the service providers (Thota et al. 2018).
A step by step procedure is needed to be followed for the deployment of the cloud
service and it helps in adaptive application that is used for seamlessly migrating and scaling
from failures. Bandwidth aware scheduled algorithm is used for minimizing the deployment
numbers and utilizing the maximum bandwidth of the network. The cloud computing is
becoming a platform for its deployment in business and for the execution of application in the
cloud it is important for making required software. For the application that needs
infrastructure level optimization the software as a service and platform as a service is not
sufficient (Dahlberg, Kivijärvi and Saarinen 2017). The enterprises have heightened the
interest for adopting cloud computing in the past decades since it promises to reshape the way
according to the needs of the enterprise and management of their needs to compute resources
cost effectively and efficiently.
The cloud computing can be considered as an innovative model for generation of
values for the enterprise. The core business activity can be focused for improvement of the
productivity and with the increase in adoption the scalability, maintainability and the growth
of the organization can be improved (Lian 2017). The cloud computing is used for providing
the users an internet based computing service and it is built on existing computer technology
such as virtualization, grid computing and other forms of distributed computing.

8
CLOUD SYSTEMS AND APPLICATIONS
Hybrid cloud considered for an organization
The hybrid cloud is considered for an organization for increasing the flexibility in the
deployment and with the implementation the IT department does not face locked in to the
particular solution. The quality is not needed to be compromised with the adoption of hybrid
cloud and it also offers best software, hardware and services that are needed for the business
needs (Taleb et al. 2015). It is best suitable for the business environment that have the
requirement of rapid scalability because some of them may need customization at the high
level for meeting the compliance and thus the private cloud is a better choice. The operation
cost can also be decreased with the implementation of hybrid cloud and adequate security is
needed to be maintained and it also helps in improving the compliance. It may not be
permitted by the business to move all the data in the public cloud and necessary steps are
needed to be taken for securing the data (Alam, Pandey and Rautaray 2015). The public cloud
vendors may not meet the security requirement and thus the selection of the hybrid cloud is
an ideal choice for offering less restriction in the business process and increase the reliability
of the public cloud offerings.
Main security and privacy threats related to cloud computing
Risks and threats for the cloud deployment models -
The main weakness of the cloud platform is its interoperability i.e. the communication
between the clouds is a different task and it also has global compliance problem for the
transmitting data between different regions. The cloud are of open standards and a bulk load
is limited with the bandwidth and since cloud service are multi-vendor solution.
There are very few hybrid cloud offering that are offered and no modification can be
made on the maintenance model.
CLOUD SYSTEMS AND APPLICATIONS
Hybrid cloud considered for an organization
The hybrid cloud is considered for an organization for increasing the flexibility in the
deployment and with the implementation the IT department does not face locked in to the
particular solution. The quality is not needed to be compromised with the adoption of hybrid
cloud and it also offers best software, hardware and services that are needed for the business
needs (Taleb et al. 2015). It is best suitable for the business environment that have the
requirement of rapid scalability because some of them may need customization at the high
level for meeting the compliance and thus the private cloud is a better choice. The operation
cost can also be decreased with the implementation of hybrid cloud and adequate security is
needed to be maintained and it also helps in improving the compliance. It may not be
permitted by the business to move all the data in the public cloud and necessary steps are
needed to be taken for securing the data (Alam, Pandey and Rautaray 2015). The public cloud
vendors may not meet the security requirement and thus the selection of the hybrid cloud is
an ideal choice for offering less restriction in the business process and increase the reliability
of the public cloud offerings.
Main security and privacy threats related to cloud computing
Risks and threats for the cloud deployment models -
The main weakness of the cloud platform is its interoperability i.e. the communication
between the clouds is a different task and it also has global compliance problem for the
transmitting data between different regions. The cloud are of open standards and a bulk load
is limited with the bandwidth and since cloud service are multi-vendor solution.
There are very few hybrid cloud offering that are offered and no modification can be
made on the maintenance model.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CLOUD SYSTEMS AND APPLICATIONS
The data cannot be easily migrated to another service provider and the user
may face lock in. In depth knowledge is needed for implementing and
management of SLA contract. The organization needs to depend on third party
computing services for its operation and it also needs high speed internet
connection for connecting with cloud database (Chou 2015).
There are different security issues such as loss of data, malware,
confidentiality and authentication associated with cloud computing. The data
ownership and management is also an issue for the cloud platform.
The user may face difficulty while migrating from one cloud platform to
another and the connectivity, efficiency, safety and speed of the network has
also an impact on the cloud resources (Yan and Yu 2015).
The resource utilization measurement and activity of end users are managed
by the service providers.
Security solution and standards in cloud environment -
The problem associated with the management of cloud computing is preserving the
confidentiality of data and integrating it with different aided security solution such that the
security of the cloud framework is improved. The solution for the issue is to encrypt the data
that is needed to be stored in the cloud servers but with the encryption new problems may
come out. Another issue the trust between the client and the cloud service provider since
there are no possible path to make sure that the service management is trustworthy and is
there any risk for insider attack. For increasing the trust the companies uses service level
agreements contain the agreement between service provider and their customer (Shiau and
Chau 2016). It contains a detailed description about the working of service provider but there
are no clear format available currently that are used as SLA. The unavailability can cause
some of the services that may not be included and the customer may be unaware that they
CLOUD SYSTEMS AND APPLICATIONS
The data cannot be easily migrated to another service provider and the user
may face lock in. In depth knowledge is needed for implementing and
management of SLA contract. The organization needs to depend on third party
computing services for its operation and it also needs high speed internet
connection for connecting with cloud database (Chou 2015).
There are different security issues such as loss of data, malware,
confidentiality and authentication associated with cloud computing. The data
ownership and management is also an issue for the cloud platform.
The user may face difficulty while migrating from one cloud platform to
another and the connectivity, efficiency, safety and speed of the network has
also an impact on the cloud resources (Yan and Yu 2015).
The resource utilization measurement and activity of end users are managed
by the service providers.
Security solution and standards in cloud environment -
The problem associated with the management of cloud computing is preserving the
confidentiality of data and integrating it with different aided security solution such that the
security of the cloud framework is improved. The solution for the issue is to encrypt the data
that is needed to be stored in the cloud servers but with the encryption new problems may
come out. Another issue the trust between the client and the cloud service provider since
there are no possible path to make sure that the service management is trustworthy and is
there any risk for insider attack. For increasing the trust the companies uses service level
agreements contain the agreement between service provider and their customer (Shiau and
Chau 2016). It contains a detailed description about the working of service provider but there
are no clear format available currently that are used as SLA. The unavailability can cause
some of the services that may not be included and the customer may be unaware that they
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CLOUD SYSTEMS AND APPLICATIONS
might need the service later on. The cloud computing system needs to adhere different
regulatory requirement such as privacy and security laws. The major problem is that the laws
may vary from country to country and the users have no control for storing their data at
defined physical location. The confidentiality of data can cause prevention of improper
information disclosure (Dahlberg, Kivijärvi and Saarinen 2017). The cloud service providers
face issues for maintaining the confidentiality as the service providers have full access to the
information stored by the user at different remote location.
Security tools for cloud computing
Improper modification can be prevented by integrity and for preserving integrity
encryption is applied. In the cloud computing environment there are multiple users with
different rights and there may be a requirement to provide access right to a user for accessing
subset of data and its delivery status is also needed to be verified and this can be achieved
with the application of digital signatures (Taleb et al. 2015). But the digital signature have the
problem that the users may not have access to the data superset and multiple subset of data
are needed to create the digital signature. The problem can be mitigated with providing the
user superset signature and metadata and result of query. The metadata can be utilized for
filling gaps in the data that cannot be accessed and validating the signature.
CLOUD SYSTEMS AND APPLICATIONS
might need the service later on. The cloud computing system needs to adhere different
regulatory requirement such as privacy and security laws. The major problem is that the laws
may vary from country to country and the users have no control for storing their data at
defined physical location. The confidentiality of data can cause prevention of improper
information disclosure (Dahlberg, Kivijärvi and Saarinen 2017). The cloud service providers
face issues for maintaining the confidentiality as the service providers have full access to the
information stored by the user at different remote location.
Security tools for cloud computing
Improper modification can be prevented by integrity and for preserving integrity
encryption is applied. In the cloud computing environment there are multiple users with
different rights and there may be a requirement to provide access right to a user for accessing
subset of data and its delivery status is also needed to be verified and this can be achieved
with the application of digital signatures (Taleb et al. 2015). But the digital signature have the
problem that the users may not have access to the data superset and multiple subset of data
are needed to create the digital signature. The problem can be mitigated with providing the
user superset signature and metadata and result of query. The metadata can be utilized for
filling gaps in the data that cannot be accessed and validating the signature.

11
CLOUD SYSTEMS AND APPLICATIONS
References
Alam, M.I., Pandey, M. and Rautaray, S.S., 2015. A comprehensive survey on cloud
computing. International Journal of Information Technology and Computer Science
(IJITCS), 7(2), p.68.
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Chou, D.C., 2015. Cloud computing: A value creation model. Computer Standards &
Interfaces, 38, pp.72-77.
Cloudoye Blog. (2019). Significant Features and Advantages of Infrastructure as a Service
(IaaS). [online] Available at: https://www.cloudoye.com/blog/cloud-computing/significant-
features-and-advantages-of-infrastructure-as-a-service-iaas [Accessed 5 Apr. 2019].
Dahlberg, T., Kivijärvi, H. and Saarinen, T., 2017, January. Longitudinal study on the
expectations of cloud computing benefits and an integrative multilevel model for
understanding cloud computing performance. In Proceedings of the 50th Hawaii
International Conference on System Sciences.
Gai, K., Qiu, M., Zhao, H., Tao, L. and Zong, Z., 2016. Dynamic energy-aware cloudlet-
based mobile cloud computing model for green computing. Journal of Network and
Computer Applications, 59, pp.46-54.
CLOUD SYSTEMS AND APPLICATIONS
References
Alam, M.I., Pandey, M. and Rautaray, S.S., 2015. A comprehensive survey on cloud
computing. International Journal of Information Technology and Computer Science
(IJITCS), 7(2), p.68.
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Chou, D.C., 2015. Cloud computing: A value creation model. Computer Standards &
Interfaces, 38, pp.72-77.
Cloudoye Blog. (2019). Significant Features and Advantages of Infrastructure as a Service
(IaaS). [online] Available at: https://www.cloudoye.com/blog/cloud-computing/significant-
features-and-advantages-of-infrastructure-as-a-service-iaas [Accessed 5 Apr. 2019].
Dahlberg, T., Kivijärvi, H. and Saarinen, T., 2017, January. Longitudinal study on the
expectations of cloud computing benefits and an integrative multilevel model for
understanding cloud computing performance. In Proceedings of the 50th Hawaii
International Conference on System Sciences.
Gai, K., Qiu, M., Zhao, H., Tao, L. and Zong, Z., 2016. Dynamic energy-aware cloudlet-
based mobile cloud computing model for green computing. Journal of Network and
Computer Applications, 59, pp.46-54.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



