COIT 20246 Assignment Submission
VerifiedAdded on 2023/06/05
|13
|3929
|457
AI Summary
This article discusses the impacts of legacy systems on organisations and how they can negatively impact organisational agility and prove to be problematic. The main point covered in the resource is that legacy systems are inflexible, costly to maintain, and pose a security risk.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
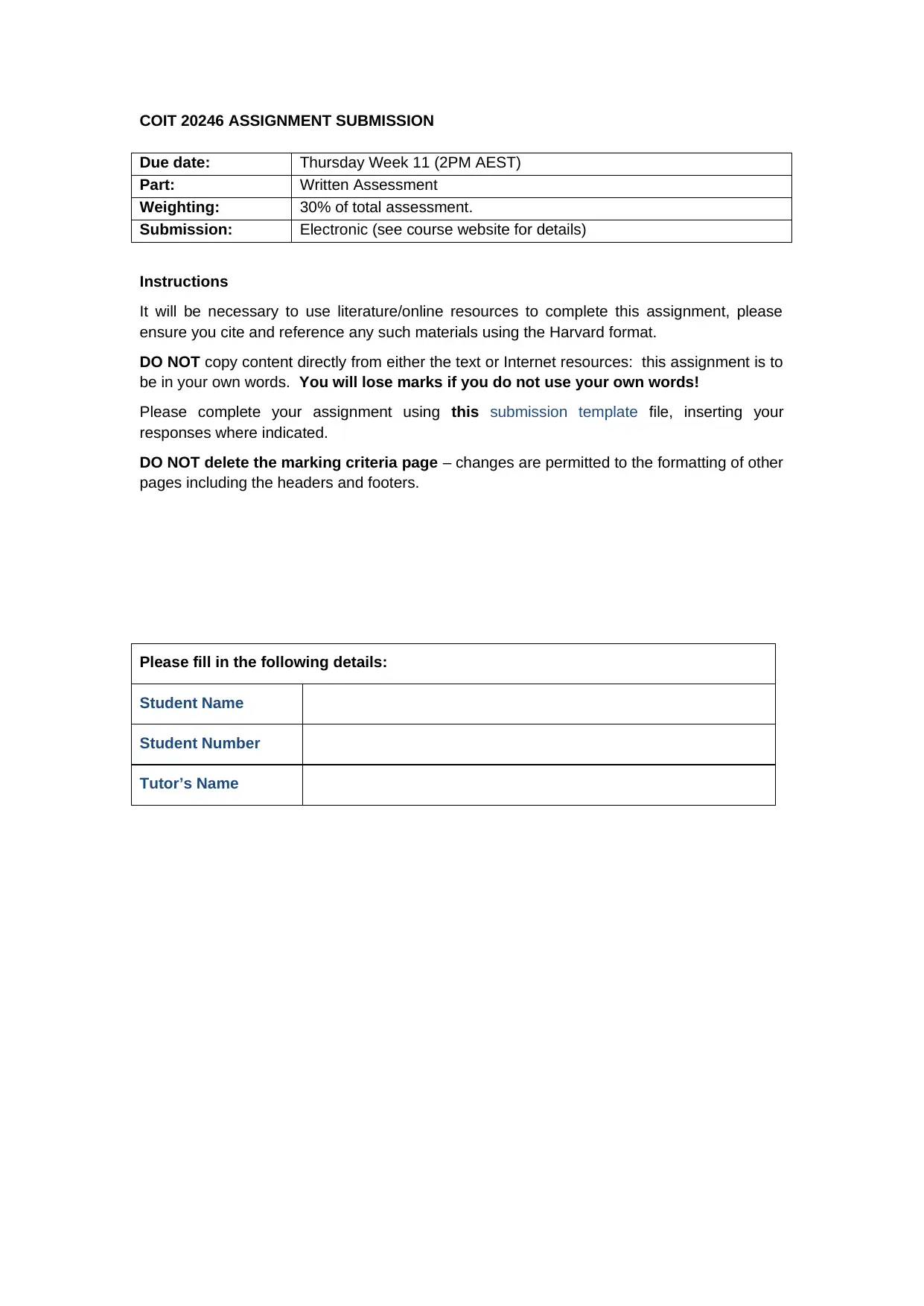
COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this assignment, please
ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this assignment is to
be in your own words. You will lose marks if you do not use your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the formatting of other
pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this assignment, please
ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this assignment is to
be in your own words. You will lose marks if you do not use your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the formatting of other
pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is a table to
complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Week 1
The text discusses how Central Processing Units (CPUs) function but is silent on another
processing component of modern computers, the Graphics Processing Unit (GPU). Find and
summarise ONE resource that describes what a GPU is and how it differs from a CPU. The
resource (and your summary) should discuss at least one non-graphics related use for GPUs.
Title and Reference:
What's the difference between a CPU and a GPU?
Raphael, M. (2016). What's the difference between a CPU and a GPU?
[Online]. Available from:
https://www.electronicproducts.com/Hardware/Computers/What_s_the_difference_between_
a_CPU_and_a_GPU.aspx [Accessed 17 September 2018].
Summary:
CPU and a GPU differ with their role played in a computing system. CPU is the vital logic
circuitry passing data into a hardware system and is an electronic system’s heart determining
input-out activities. Contrastingly GPU is a specially designed electronic circuit made for
displaying image and video further enhancing the usage of frame buffers for displaying
purposes in computers, mobile phones and gaming consoles. It can either be installed as a
slot card component or reside on the motherboard of a device. Simple central works are
performed by CPU while complex calculations for rendering animations, images, and videos
are performed by GPU. CPU process works sequentially whereas parallel tasks are
processes by GPU.
The resource is about highlighting the differences between CPU and a GPU and it has been
selected because the differences are elaborated in a lucid language. The key information that
is covered in the resource is that both CPU and GPU can be differentiated by the role they
play within any computing system and although data is handled by both, only one is required
in all computers. The chosen resource was useful because it contributed in identifying how
GPU is different from CPU without many efforts.
There are ten (10) tasks, one for each week: the tasks are detailed below. There is a table to
complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Week 1
The text discusses how Central Processing Units (CPUs) function but is silent on another
processing component of modern computers, the Graphics Processing Unit (GPU). Find and
summarise ONE resource that describes what a GPU is and how it differs from a CPU. The
resource (and your summary) should discuss at least one non-graphics related use for GPUs.
Title and Reference:
What's the difference between a CPU and a GPU?
Raphael, M. (2016). What's the difference between a CPU and a GPU?
[Online]. Available from:
https://www.electronicproducts.com/Hardware/Computers/What_s_the_difference_between_
a_CPU_and_a_GPU.aspx [Accessed 17 September 2018].
Summary:
CPU and a GPU differ with their role played in a computing system. CPU is the vital logic
circuitry passing data into a hardware system and is an electronic system’s heart determining
input-out activities. Contrastingly GPU is a specially designed electronic circuit made for
displaying image and video further enhancing the usage of frame buffers for displaying
purposes in computers, mobile phones and gaming consoles. It can either be installed as a
slot card component or reside on the motherboard of a device. Simple central works are
performed by CPU while complex calculations for rendering animations, images, and videos
are performed by GPU. CPU process works sequentially whereas parallel tasks are
processes by GPU.
The resource is about highlighting the differences between CPU and a GPU and it has been
selected because the differences are elaborated in a lucid language. The key information that
is covered in the resource is that both CPU and GPU can be differentiated by the role they
play within any computing system and although data is handled by both, only one is required
in all computers. The chosen resource was useful because it contributed in identifying how
GPU is different from CPU without many efforts.

Week 2
One of the potential next advances in Operating Systems (OSes) will be Artificial Intelligence
(AI) capabilities. Find and summarise ONE resource that discusses how AI could change the
way OSes function and/or interact with users.
Title and Reference:
How conversation (with context) will usher in the AI future.
IBM. (no date). How conversation (with context) will usher in the AI future. (Online) Available
from: https://www.ibm.com/watson/advantage-reports/future-of-artificial-intelligence/ai-
conversation.html [Accessed 17 sep 2018]
Summary:
AI can change the way OSes can function and interact with users because of advances that
have been achieved in AI and AI-integrated assistants. The ability of computers has
advanced and they have begun to interact with users and researchers are being conducted to
make this ability of AI-human relationship more natural to reach to its full capability. Many
OSes functions have been built that work on human computer interaction (HCI) depending on
AI and its applications. But advances in HCI has still not reached to full conversational
capabilities but they have truly paved way for vast change with more sophisticated AI-infused
interactions. In order to make these machines master effective conversation still one vital
element needs to be developed which is context. AI enabled OSes have made vital shift from
command base on screen interaction that was present in earlier. AI –infused OSes functions
like assistants are now available in phones, smart homes that permit users to interact with
them through voice conversations. But due to high expectation with AI-conversational
assistants, users have reached at level of frustration as these machines have still not reached
to advance level of machine learning. At present these AI assistants can allow better
interaction systems to identify speech and transform text into speech with components of
natural language processing. So they are able to respond like humans but they cannot
respond to unbound back and fro exchanges with emotions. These gaps are pertinent as they
are not yet made with full natural language understanding and dialogues which is possible
with sense of context in conversational systems.
This resource elaborates the manner AI has transformed operating systems and interaction
and has been useful.
One of the potential next advances in Operating Systems (OSes) will be Artificial Intelligence
(AI) capabilities. Find and summarise ONE resource that discusses how AI could change the
way OSes function and/or interact with users.
Title and Reference:
How conversation (with context) will usher in the AI future.
IBM. (no date). How conversation (with context) will usher in the AI future. (Online) Available
from: https://www.ibm.com/watson/advantage-reports/future-of-artificial-intelligence/ai-
conversation.html [Accessed 17 sep 2018]
Summary:
AI can change the way OSes can function and interact with users because of advances that
have been achieved in AI and AI-integrated assistants. The ability of computers has
advanced and they have begun to interact with users and researchers are being conducted to
make this ability of AI-human relationship more natural to reach to its full capability. Many
OSes functions have been built that work on human computer interaction (HCI) depending on
AI and its applications. But advances in HCI has still not reached to full conversational
capabilities but they have truly paved way for vast change with more sophisticated AI-infused
interactions. In order to make these machines master effective conversation still one vital
element needs to be developed which is context. AI enabled OSes have made vital shift from
command base on screen interaction that was present in earlier. AI –infused OSes functions
like assistants are now available in phones, smart homes that permit users to interact with
them through voice conversations. But due to high expectation with AI-conversational
assistants, users have reached at level of frustration as these machines have still not reached
to advance level of machine learning. At present these AI assistants can allow better
interaction systems to identify speech and transform text into speech with components of
natural language processing. So they are able to respond like humans but they cannot
respond to unbound back and fro exchanges with emotions. These gaps are pertinent as they
are not yet made with full natural language understanding and dialogues which is possible
with sense of context in conversational systems.
This resource elaborates the manner AI has transformed operating systems and interaction
and has been useful.

Week 3
The text discusses how Netflix uses Amazon Web Services (AWS) as a Cloud Service
Provider (CSP) for Infrastructure as a Service (IaaS). Find and summarise ONE resource
that describes ONEother commercial IaaS provider that is NOT Google. The resource and
your summary should describe how the IaaS differs from AWS.
Title and Reference:
How Oracle differentiates its IaaS against AWS
Saran, C. (2017). How Oracle differentiates its IaaS against AWS [Online]. Available from:
https://www.computerweekly.com/news/450417449/How-Oracle-differentiates-its-IaaS-
against-AWS [Accessed 17 September 2018].
Summary:
Oracle Cloud is a commercial IaaS provider. Iaas comparing to AWS is both faster and lower-
cost besides allowing users in running their largest and most demanding database workloads
in the cloud, which is impossible in Amazon Cloud. The IaaS platform is 70% low in price
compared to AWS. Users of AWS often have to worry about the network however; in IaaS the
networking remains same whether virtual machines or bare metal servers are run. Making
configuration choices is necessary with AWS and the AWS are specified in certain
combinations further implicating networking capacity, which is not the case with IaaS. On
AWS workload having higher compute requirements needs high bandwidth but codes are
used in IaaS in such a way that with growing workload more virtual machines are added.
The resource is about bringing into light how IaaS differs from AWS and it has been selected
because Oracle Cloud as prominent IaaS provider has precisely presented the differences of
using an IaaS platform over that of AWS. The main point covered in the resource is that IaaS
is faster and cheaper than AWS. The chosen resource was useful because it gave ease in
figuring out the how IaaS differs from AWS.
The text discusses how Netflix uses Amazon Web Services (AWS) as a Cloud Service
Provider (CSP) for Infrastructure as a Service (IaaS). Find and summarise ONE resource
that describes ONEother commercial IaaS provider that is NOT Google. The resource and
your summary should describe how the IaaS differs from AWS.
Title and Reference:
How Oracle differentiates its IaaS against AWS
Saran, C. (2017). How Oracle differentiates its IaaS against AWS [Online]. Available from:
https://www.computerweekly.com/news/450417449/How-Oracle-differentiates-its-IaaS-
against-AWS [Accessed 17 September 2018].
Summary:
Oracle Cloud is a commercial IaaS provider. Iaas comparing to AWS is both faster and lower-
cost besides allowing users in running their largest and most demanding database workloads
in the cloud, which is impossible in Amazon Cloud. The IaaS platform is 70% low in price
compared to AWS. Users of AWS often have to worry about the network however; in IaaS the
networking remains same whether virtual machines or bare metal servers are run. Making
configuration choices is necessary with AWS and the AWS are specified in certain
combinations further implicating networking capacity, which is not the case with IaaS. On
AWS workload having higher compute requirements needs high bandwidth but codes are
used in IaaS in such a way that with growing workload more virtual machines are added.
The resource is about bringing into light how IaaS differs from AWS and it has been selected
because Oracle Cloud as prominent IaaS provider has precisely presented the differences of
using an IaaS platform over that of AWS. The main point covered in the resource is that IaaS
is faster and cheaper than AWS. The chosen resource was useful because it gave ease in
figuring out the how IaaS differs from AWS.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Week 4
IPv4 is discussed in the text, yet the emerging IPv6 protocol is only mentioned briefly. Find
and summarise ONE resource that describes the IPv6 protocol. The resource and your
summary should describe how IPv6 differs from IPv4.
Title and Reference:
IPv4 vs IPv6: What is the difference between IPv4 and IPv6
Sabarinath. (2018). IPv4 vs IPv6: What is the difference between IPv4 and IPv6 [Online].
Available from: https://techlog360.com/ipv4-vs-ipv6/ [Accessed 17 September 2018].
Summary:
IPv6 is an advanced generation of Internet Protocol with capability of providing unlimited
number of addresses and has replaced IPv4 for accommodating the increasing number of
networks globally besides resolving the exhaustion problem of IP address exhaustion.
Address space is the key difference between IPv6 and IPv4. Address fields in IPv6 are 128-
bits while in IPv4 it is 32-bits. IPv5 has in-built strong security in terms of encryption and
authentication whereas IPv4 lacks security. IPv6 header has 40bytes compared to IPv4
header has 20 bytes. Moreover, IPv6 header has 8 fields compared to 13 fields of IPv4
header. Packet size of IPv6 is 1280 bytes requisite without fragmentation while IPv4 packet
size is 576 bytes and fragmentation is optional. Many Internet Service Providers do not have
IPv6 connectivity however, in case of IPv4, ISP have either both connectivity or IPv4.
The resource is about describing the IPv6 protocol and how it differs from IPv4 and it has
been selected because of easy description and presentation of the basic differences between
IPv6 and IPv4. Key information covered in the resource is that IPv6 is more advanced with
better features comparing to IPv4. The chosen resource was useful in outlining the key
differences.
IPv4 is discussed in the text, yet the emerging IPv6 protocol is only mentioned briefly. Find
and summarise ONE resource that describes the IPv6 protocol. The resource and your
summary should describe how IPv6 differs from IPv4.
Title and Reference:
IPv4 vs IPv6: What is the difference between IPv4 and IPv6
Sabarinath. (2018). IPv4 vs IPv6: What is the difference between IPv4 and IPv6 [Online].
Available from: https://techlog360.com/ipv4-vs-ipv6/ [Accessed 17 September 2018].
Summary:
IPv6 is an advanced generation of Internet Protocol with capability of providing unlimited
number of addresses and has replaced IPv4 for accommodating the increasing number of
networks globally besides resolving the exhaustion problem of IP address exhaustion.
Address space is the key difference between IPv6 and IPv4. Address fields in IPv6 are 128-
bits while in IPv4 it is 32-bits. IPv5 has in-built strong security in terms of encryption and
authentication whereas IPv4 lacks security. IPv6 header has 40bytes compared to IPv4
header has 20 bytes. Moreover, IPv6 header has 8 fields compared to 13 fields of IPv4
header. Packet size of IPv6 is 1280 bytes requisite without fragmentation while IPv4 packet
size is 576 bytes and fragmentation is optional. Many Internet Service Providers do not have
IPv6 connectivity however, in case of IPv4, ISP have either both connectivity or IPv4.
The resource is about describing the IPv6 protocol and how it differs from IPv4 and it has
been selected because of easy description and presentation of the basic differences between
IPv6 and IPv4. Key information covered in the resource is that IPv6 is more advanced with
better features comparing to IPv4. The chosen resource was useful in outlining the key
differences.

Week 5
WannaCry and NotPetya were two of the most significant malware attacks of 2017. Find and
summarise ONE resource that describes how ONE of these pieces of malware work. Note
that the resource should focus on ONE of these, NOT both.
Title and Reference:
What is WannaCry ransomware, how does it infect, and who was responsible?
Fruhlinger, J. (2018). What is WannaCry ransomware, how does it infect, and who was
responsible? [Online]. Available from:
https://www.csoonline.com/article/3227906/ransomware/what-is-wannacry-ransomware-how-
does-it-infect-and-who-was-responsible.html [Accessed 17 September 2018].
Summary:
In 2017 WannaCry, ransomware worm rapidly spread across multiple computer networks.
Once it infects a Windows device, files on the hard drive are encrypted forming it futile for
users to gain entry followed by demanding ransom cash in bitcoin for decrypting them.
Multiple components are present in this ransomware, arriving on the device corrupted as a
dropper, an independent program extracting other application components such as Tor, files
with encryption keys and application encrypting and decrypting data, embedded within it.
WannaCry once launched tries accessing a hard-coded URL; in case of failure encrypt files in
bulk so that users cannot access them unless a ransom is paid. WannaCry makes full use of
Windows vulnerability lying in the application of the Server Message Block protocol, which
helps to communicate numerous nodes on a network and the ransomware tricks Microsoft's
implementation by specifically designed packets to execute arbitrary code. The resource is
about detailed explanation of WannaCry malware attack of 2017. This particular resource has
been selected because the author has clearly described the process how this malware infects
computers and encrypts important files for demanding ransom from the users. The main point
that is covered in the resource is WannaCry encrypts a computer’s hard drive, forming it
hopeless for users to gain ingression to any file. The chosen resource was useful to
understand about this significant malware attack and how it worked.
WannaCry and NotPetya were two of the most significant malware attacks of 2017. Find and
summarise ONE resource that describes how ONE of these pieces of malware work. Note
that the resource should focus on ONE of these, NOT both.
Title and Reference:
What is WannaCry ransomware, how does it infect, and who was responsible?
Fruhlinger, J. (2018). What is WannaCry ransomware, how does it infect, and who was
responsible? [Online]. Available from:
https://www.csoonline.com/article/3227906/ransomware/what-is-wannacry-ransomware-how-
does-it-infect-and-who-was-responsible.html [Accessed 17 September 2018].
Summary:
In 2017 WannaCry, ransomware worm rapidly spread across multiple computer networks.
Once it infects a Windows device, files on the hard drive are encrypted forming it futile for
users to gain entry followed by demanding ransom cash in bitcoin for decrypting them.
Multiple components are present in this ransomware, arriving on the device corrupted as a
dropper, an independent program extracting other application components such as Tor, files
with encryption keys and application encrypting and decrypting data, embedded within it.
WannaCry once launched tries accessing a hard-coded URL; in case of failure encrypt files in
bulk so that users cannot access them unless a ransom is paid. WannaCry makes full use of
Windows vulnerability lying in the application of the Server Message Block protocol, which
helps to communicate numerous nodes on a network and the ransomware tricks Microsoft's
implementation by specifically designed packets to execute arbitrary code. The resource is
about detailed explanation of WannaCry malware attack of 2017. This particular resource has
been selected because the author has clearly described the process how this malware infects
computers and encrypts important files for demanding ransom from the users. The main point
that is covered in the resource is WannaCry encrypts a computer’s hard drive, forming it
hopeless for users to gain ingression to any file. The chosen resource was useful to
understand about this significant malware attack and how it worked.

Week 6
OpenFlow is a protocol that enables Software-Defined Networking (SDN). Find and
summarise ONE resource that describes how OpenFlow works and/or how it enables SDN.
Title and Reference:
What is OpenFlow? Definition and How it Relates to SDN
SDXcentral. (no date). What is OpenFlow? Definition and How it Relates to SDN [Online].
Available from: https://www.sdxcentral.com/sdn/definitions/what-is-openflow/
[Accessed 17 September 2018].
Summary:
OpenFlow, a programmable network protocol for SDN environment, is used to communicate
between OpenFlow switches and controllers by separating the network device programming
from a hidden hardware offering a standard way to deliver a consolidated, programmable
network adapting changing network requirements quickly. Devices wanting to interact to an
SDN Controller must support the OF protocol for working in an OpenFlow environment.
Changes to the switch/router flow-table is pushed down by the SDN Controller through this
interface to allow network administrators divide traffic, control flows for excellent achievement
and test new configurations and applications. OpenFlow enables SDN to relay information to
switches/routers ‘below’ over southbound application programming interface and applications
and business logic ‘above’ by northbound API. The resource is about describing OpenFlow
and how it relates to SDN. This resource has been selected because it clearly illustrates the
working process of OpenFlow enabling SDN. The main point that is covered in the resource is
OpenFlow is a communication protocol in the environment of SDN enabling to make direct
interaction with the advanced devices of networking like routers and switches for adapting the
changing business needs. The chosen resource was useful to gaining an in-depth
understanding about what is OpenFlow and SDN besides knowing its working process and
how it enables SDN.
OpenFlow is a protocol that enables Software-Defined Networking (SDN). Find and
summarise ONE resource that describes how OpenFlow works and/or how it enables SDN.
Title and Reference:
What is OpenFlow? Definition and How it Relates to SDN
SDXcentral. (no date). What is OpenFlow? Definition and How it Relates to SDN [Online].
Available from: https://www.sdxcentral.com/sdn/definitions/what-is-openflow/
[Accessed 17 September 2018].
Summary:
OpenFlow, a programmable network protocol for SDN environment, is used to communicate
between OpenFlow switches and controllers by separating the network device programming
from a hidden hardware offering a standard way to deliver a consolidated, programmable
network adapting changing network requirements quickly. Devices wanting to interact to an
SDN Controller must support the OF protocol for working in an OpenFlow environment.
Changes to the switch/router flow-table is pushed down by the SDN Controller through this
interface to allow network administrators divide traffic, control flows for excellent achievement
and test new configurations and applications. OpenFlow enables SDN to relay information to
switches/routers ‘below’ over southbound application programming interface and applications
and business logic ‘above’ by northbound API. The resource is about describing OpenFlow
and how it relates to SDN. This resource has been selected because it clearly illustrates the
working process of OpenFlow enabling SDN. The main point that is covered in the resource is
OpenFlow is a communication protocol in the environment of SDN enabling to make direct
interaction with the advanced devices of networking like routers and switches for adapting the
changing business needs. The chosen resource was useful to gaining an in-depth
understanding about what is OpenFlow and SDN besides knowing its working process and
how it enables SDN.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 7
Historically, organisations have been able to improve business processes by implementing
Information Systems. However, as these systems age they can negatively impact on
organisational agility and can ultimately prove problematic. Such systems are broadly
referred to as Legacy Systems. Find and summarise ONE resource that discusses the
impacts of legacy systems on organisations. The resource and your summary should clearly
identify problems with maintaining legacy systems.
Title and Reference:
The risk of outdated technology: Why legacy systems cost you more than you realise
Alvarez technology group (2018) The risk of outdated technology: Why legacy systems cost
you more than you realise. (Online) Available from: https://www.alvareztg.com/the-risks-of-
outdated-technology-why-legacy-systems-cost-you-more-than-you-realize/ [Accessed on 24
September 2018]
Summary:
Legacy systems are those that are not flexible with business changes and this has impacted
organisations ERP systems with fact that due to legacy system the IS system are subjected
to more amount of customization. Also these have enhanced modifications to meet to
additional needs resulting into various problems of maintaining these systems. These are
absence of flexibility which does not allow organisations to conduct their regular activities with
change of elements. Also the system gets affected with frequent customization need as per
business change. The other problem is inadequate information where there is lack in
reporting capabilities and proper access to information held in system. This hampers quick
capability of response to business issues and solving them in timely way. Moreover there is
inadequacy of IT resources and dependency on individuals as customisation of these
systems needs specific understanding. So individuals who have handled this customisation
can interpret complexity with deep understanding. This enhances dependability on such
employees and organisations have to plan attritions and need to source new recruits who
have the supporting skills of legacy system applications which become troublesome.
The resource has been useful as it has given understanding on legacy system and their
problems and impact on companies.
Historically, organisations have been able to improve business processes by implementing
Information Systems. However, as these systems age they can negatively impact on
organisational agility and can ultimately prove problematic. Such systems are broadly
referred to as Legacy Systems. Find and summarise ONE resource that discusses the
impacts of legacy systems on organisations. The resource and your summary should clearly
identify problems with maintaining legacy systems.
Title and Reference:
The risk of outdated technology: Why legacy systems cost you more than you realise
Alvarez technology group (2018) The risk of outdated technology: Why legacy systems cost
you more than you realise. (Online) Available from: https://www.alvareztg.com/the-risks-of-
outdated-technology-why-legacy-systems-cost-you-more-than-you-realize/ [Accessed on 24
September 2018]
Summary:
Legacy systems are those that are not flexible with business changes and this has impacted
organisations ERP systems with fact that due to legacy system the IS system are subjected
to more amount of customization. Also these have enhanced modifications to meet to
additional needs resulting into various problems of maintaining these systems. These are
absence of flexibility which does not allow organisations to conduct their regular activities with
change of elements. Also the system gets affected with frequent customization need as per
business change. The other problem is inadequate information where there is lack in
reporting capabilities and proper access to information held in system. This hampers quick
capability of response to business issues and solving them in timely way. Moreover there is
inadequacy of IT resources and dependency on individuals as customisation of these
systems needs specific understanding. So individuals who have handled this customisation
can interpret complexity with deep understanding. This enhances dependability on such
employees and organisations have to plan attritions and need to source new recruits who
have the supporting skills of legacy system applications which become troublesome.
The resource has been useful as it has given understanding on legacy system and their
problems and impact on companies.

Week 8
With the advent of mass data collection and storage has come the use of these datasets for
data mining and analysis. Recently, Cambridge Analytica and Facebook have come under
intense scrutiny for their use of user data, allegedly in order to influence the US 2016 election.
Find and summarise ONE resource that describes what Cambridge Analytica did and why
their services were so controversial.
Title and Reference:
How Facebook Blew It
Pasternack, A & Winston, J. (2018). How Facebook Blew It. [Online]. Available from:
https://www.fastcompany.com/40550423/how-facebook-blew-it [Accessed 17 September
2018].
Summary:
Political consultation firm Cambridge Analytica that ran for the Trump crusade is accused of
harvesting raw data from around 87 million Facebook profiles. Psychological profiles of
consumers and voters were developed by the company for helping out political campaigns.
An application was designed Aleksandr Kogan, a British academic for harvesting data. Once
downloading the application and logging in with Facebook accounts, the application collected
users’ data including their friends, which as passed on to Cambridge Analytica against, which
paid for gathering Facebook data of Americans residing in key U.S. states. It used an arsenal
including a psychometric model for predicting the of every single adult in US for slicing up the
electorate into small-scale segments and microtargeting the right voters in the right states
with under-the-radar online ads that were emotionally tailored for gaining an advantage by
manipulating the electorates mind. Cambridge Analytica having close ties President Trump’s
election campaign used millions of users’ data without their consent violating the privacy rules
of Facebook. The resource is about describing how Cambridge Analytica helped in political
campaigning and has a large role in US 2016 Election. This resource has been selected
because it gives a detailed description about how the company since 2014 had gather
millions of users’ data without their knowledge and used it for benefiting elections. The
chosen resource was useful in comprehending what Cambridge Analytica did and why it
services are widely controversial.
With the advent of mass data collection and storage has come the use of these datasets for
data mining and analysis. Recently, Cambridge Analytica and Facebook have come under
intense scrutiny for their use of user data, allegedly in order to influence the US 2016 election.
Find and summarise ONE resource that describes what Cambridge Analytica did and why
their services were so controversial.
Title and Reference:
How Facebook Blew It
Pasternack, A & Winston, J. (2018). How Facebook Blew It. [Online]. Available from:
https://www.fastcompany.com/40550423/how-facebook-blew-it [Accessed 17 September
2018].
Summary:
Political consultation firm Cambridge Analytica that ran for the Trump crusade is accused of
harvesting raw data from around 87 million Facebook profiles. Psychological profiles of
consumers and voters were developed by the company for helping out political campaigns.
An application was designed Aleksandr Kogan, a British academic for harvesting data. Once
downloading the application and logging in with Facebook accounts, the application collected
users’ data including their friends, which as passed on to Cambridge Analytica against, which
paid for gathering Facebook data of Americans residing in key U.S. states. It used an arsenal
including a psychometric model for predicting the of every single adult in US for slicing up the
electorate into small-scale segments and microtargeting the right voters in the right states
with under-the-radar online ads that were emotionally tailored for gaining an advantage by
manipulating the electorates mind. Cambridge Analytica having close ties President Trump’s
election campaign used millions of users’ data without their consent violating the privacy rules
of Facebook. The resource is about describing how Cambridge Analytica helped in political
campaigning and has a large role in US 2016 Election. This resource has been selected
because it gives a detailed description about how the company since 2014 had gather
millions of users’ data without their knowledge and used it for benefiting elections. The
chosen resource was useful in comprehending what Cambridge Analytica did and why it
services are widely controversial.

Week 9
Load (or performance) testing is a critical step in the information systems development
process. The purpose of this testing is to simulate the peak expected load on a system to
ensure both hardware and software can operate effectively and meet key metrics. To do this,
specialised performance testing tools are used. Find and summarise ONE resource that
describes ONEsuch tool. The resource (and your summary) should include information on
the principle uses and features of the tool.
Title and Reference:
Load testing tools for websites and web apps
SMARTBEAR. (No date). Load testing tools for websites and web apps. (Online) Available:
https://smartbear.com/product/loadcomplete/overview/ [ Accessed on 17 September 2018]
Summary:
One of the tools for performance testing is LoadComplete which can be used for load, stress,
scalability testing and is developed from base level with sharp focus on in hand tasks.
LoadComplete tool does not need advance programming skills and is functional at both
traditional HTML and Rich Internet applications such as Java, ASP.NET etc. Moreover it has
record and playpack as well as visual programming feature in the tool that allows developing
powerful and adaptable first load testing. This tool permits users to create load from virtual
devices, on-premise devices and even cloud. Further personalised reports helps users get
more visibility and detect issues at both client and server level.
LoadComplete helps in making performance testing easier and simplified by simulating users
and developing load testing without line of code. It even permits users to create traffic utilising
cloud, VM or on-premise desktops. Some of the features of LoadComplete are it can
generate load testing in less time with record and playback feature, can quickly increase
traffic and develop custom load profiles for distinct locations. It even can create load testing
scenario without scripting language and can simulate traffic for various kind of visitors like
business, buyers, etc. Also it is enabled to describe performance threshold and generates
alert in case of quality service violation.
I have chosen this resource as it describes complete use and feature of a leading load testing
tool and has been useful.
Load (or performance) testing is a critical step in the information systems development
process. The purpose of this testing is to simulate the peak expected load on a system to
ensure both hardware and software can operate effectively and meet key metrics. To do this,
specialised performance testing tools are used. Find and summarise ONE resource that
describes ONEsuch tool. The resource (and your summary) should include information on
the principle uses and features of the tool.
Title and Reference:
Load testing tools for websites and web apps
SMARTBEAR. (No date). Load testing tools for websites and web apps. (Online) Available:
https://smartbear.com/product/loadcomplete/overview/ [ Accessed on 17 September 2018]
Summary:
One of the tools for performance testing is LoadComplete which can be used for load, stress,
scalability testing and is developed from base level with sharp focus on in hand tasks.
LoadComplete tool does not need advance programming skills and is functional at both
traditional HTML and Rich Internet applications such as Java, ASP.NET etc. Moreover it has
record and playpack as well as visual programming feature in the tool that allows developing
powerful and adaptable first load testing. This tool permits users to create load from virtual
devices, on-premise devices and even cloud. Further personalised reports helps users get
more visibility and detect issues at both client and server level.
LoadComplete helps in making performance testing easier and simplified by simulating users
and developing load testing without line of code. It even permits users to create traffic utilising
cloud, VM or on-premise desktops. Some of the features of LoadComplete are it can
generate load testing in less time with record and playback feature, can quickly increase
traffic and develop custom load profiles for distinct locations. It even can create load testing
scenario without scripting language and can simulate traffic for various kind of visitors like
business, buyers, etc. Also it is enabled to describe performance threshold and generates
alert in case of quality service violation.
I have chosen this resource as it describes complete use and feature of a leading load testing
tool and has been useful.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Week 10
While information systems and technology deliver many benefits to society, there is a high
incidence of failure in attempting to implement them. These IS/IT implementation project
failures frequently result in substantial financial losses. Find and summarise ONE resource
that describesONE example of an Australian IT/IS project that has failed. Note that the
resource should focus on ONE single example and it and your summary should clearly
explain the cause(s) of the failure.
Title and Reference:
Learning from the QLD health payroll fiasco
Sharma, K. (2013) Learning from the QLD health payroll fiasco (Online) Available from:
https://www.theaustralian.com.au/business/business-spectator/learning-from-the-qld-health-
payroll-fiasco-/news-story/174743f09e91d9550521b04d45d43ac3 [Accessed on 17
September 2018]
Summary:
One of the significant example of IT/IS project failure in history of Australia was Queensland
Health payroll system failure. The project was estimated at $6.19 million contract amid
Queensland State and IBM to change QLD health’s payroll system. But it resulted to
complexities when it was live and added $1.25 billion cost to taxpayers. The result was
project went under serious state level inquiry. The project failed because of user acceptance
testing (UAT) as instead of resolving issue the standard of testing was lowered. Moreover
poor guidelines to meet time line were another reason. There were signs of inappropriate
internal administration and negligence before QLD payroll project was given to IBM. The
Queensland Treasury underestimated cost of project to execute consistent SAP based HR
and finance system in their operations. The project has troubled start as budget was
insufficient and the delays in rollout was suffered as Health department systems was not
completely ready to integrate such standardized system. This was because of the fact that
government failed to provide details of specifications with high end of accuracy. Due to lack of
internal requisites there were various complexities in project that finally lead to blowout of
time and cost.
The resource selected was useful as it narrated details of projects and outlined cause of
failure.
While information systems and technology deliver many benefits to society, there is a high
incidence of failure in attempting to implement them. These IS/IT implementation project
failures frequently result in substantial financial losses. Find and summarise ONE resource
that describesONE example of an Australian IT/IS project that has failed. Note that the
resource should focus on ONE single example and it and your summary should clearly
explain the cause(s) of the failure.
Title and Reference:
Learning from the QLD health payroll fiasco
Sharma, K. (2013) Learning from the QLD health payroll fiasco (Online) Available from:
https://www.theaustralian.com.au/business/business-spectator/learning-from-the-qld-health-
payroll-fiasco-/news-story/174743f09e91d9550521b04d45d43ac3 [Accessed on 17
September 2018]
Summary:
One of the significant example of IT/IS project failure in history of Australia was Queensland
Health payroll system failure. The project was estimated at $6.19 million contract amid
Queensland State and IBM to change QLD health’s payroll system. But it resulted to
complexities when it was live and added $1.25 billion cost to taxpayers. The result was
project went under serious state level inquiry. The project failed because of user acceptance
testing (UAT) as instead of resolving issue the standard of testing was lowered. Moreover
poor guidelines to meet time line were another reason. There were signs of inappropriate
internal administration and negligence before QLD payroll project was given to IBM. The
Queensland Treasury underestimated cost of project to execute consistent SAP based HR
and finance system in their operations. The project has troubled start as budget was
insufficient and the delays in rollout was suffered as Health department systems was not
completely ready to integrate such standardized system. This was because of the fact that
government failed to provide details of specifications with high end of accuracy. Due to lack of
internal requisites there were various complexities in project that finally lead to blowout of
time and cost.
The resource selected was useful as it narrated details of projects and outlined cause of
failure.
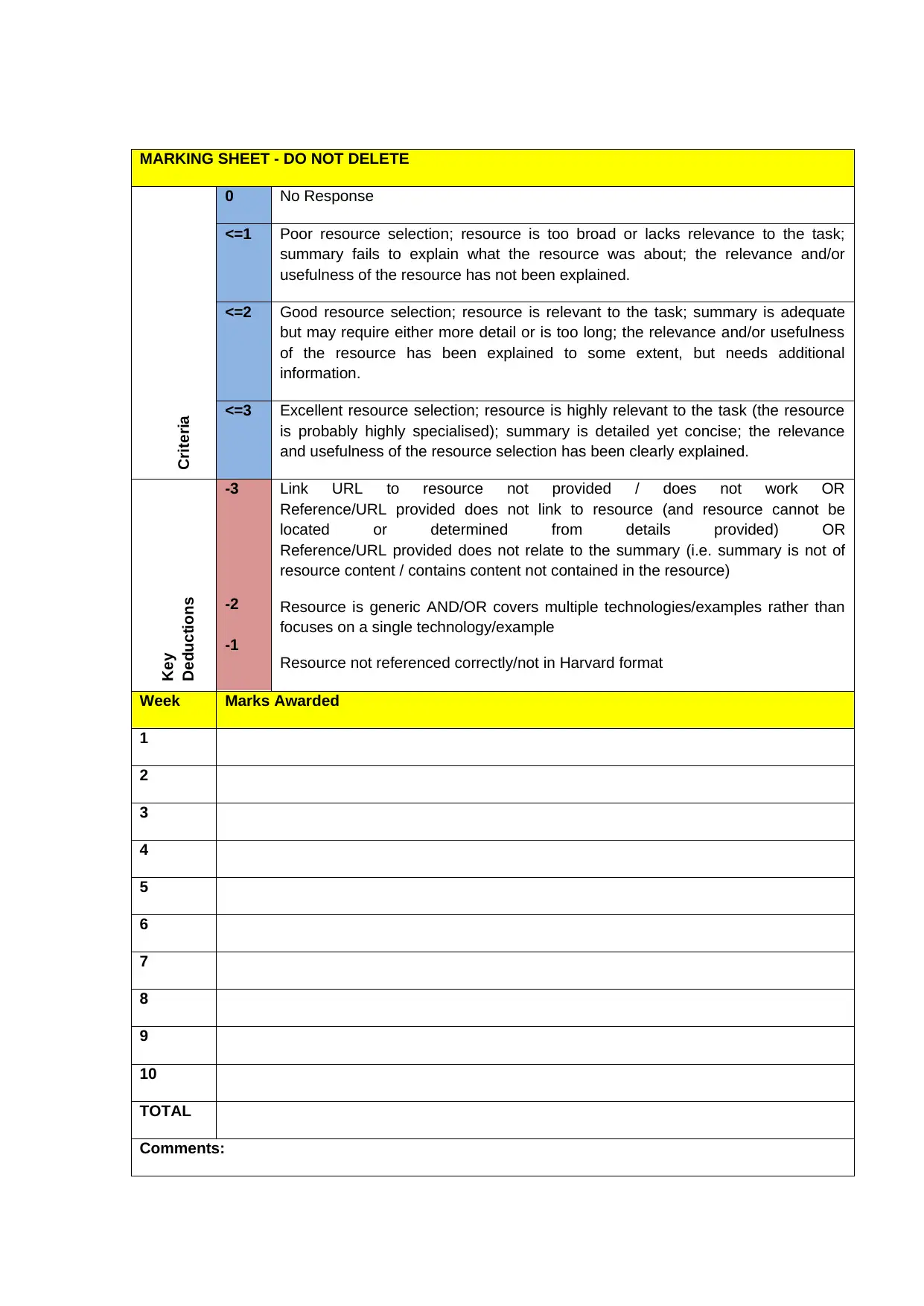
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the task;
summary fails to explain what the resource was about; the relevance and/or
usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is adequate
but may require either more detail or is too long; the relevance and/or usefulness
of the resource has been explained to some extent, but needs additional
information.
<=3 Excellent resource selection; resource is highly relevant to the task (the resource
is probably highly specialised); summary is detailed yet concise; the relevance
and usefulness of the resource selection has been clearly explained.
Key
Deductions
-3
-2
-1
Link URL to resource not provided / does not work OR
Reference/URL provided does not link to resource (and resource cannot be
located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is not of
resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples rather than
focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the task;
summary fails to explain what the resource was about; the relevance and/or
usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is adequate
but may require either more detail or is too long; the relevance and/or usefulness
of the resource has been explained to some extent, but needs additional
information.
<=3 Excellent resource selection; resource is highly relevant to the task (the resource
is probably highly specialised); summary is detailed yet concise; the relevance
and usefulness of the resource selection has been clearly explained.
Key
Deductions
-3
-2
-1
Link URL to resource not provided / does not work OR
Reference/URL provided does not link to resource (and resource cannot be
located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is not of
resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples rather than
focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:

1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.
