COIT 20246 Assignment Submission
VerifiedAdded on 2023/06/11
|9
|3329
|56
AI Summary
This document provides instructions and tasks for COIT 20246 Assignment Submission. It includes details such as due date, part, weighting, and submission. The tasks include finding and summarizing resources on various topics such as modern CPUs, GUI operating systems, LPWANs, VoIP protocols, blockchains, net neutrality, and job automation due to ICT based automation. Each task has a specific title, reference, and summary.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
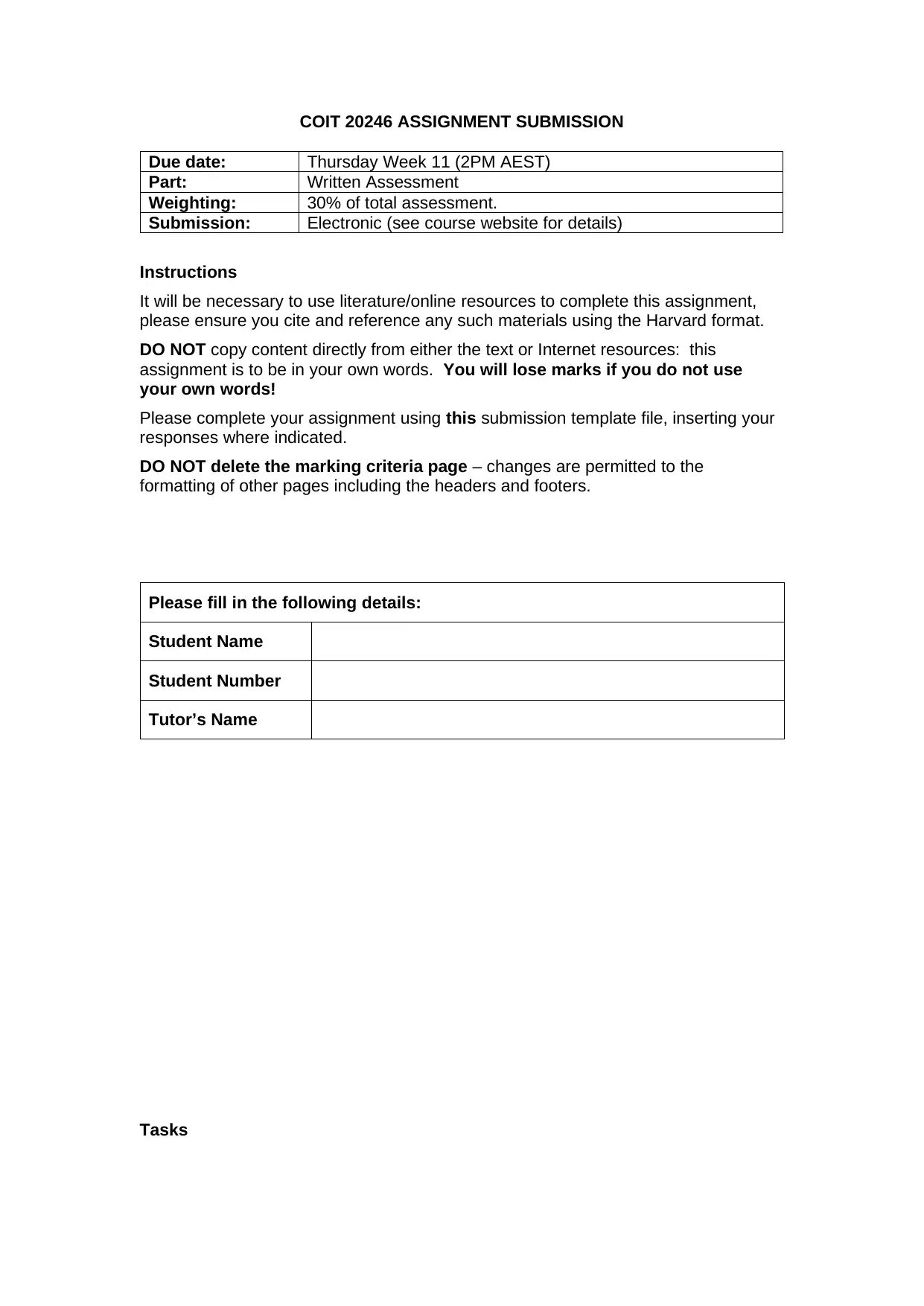
COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this assignment,
please ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Tasks
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
It will be necessary to use literature/online resources to complete this assignment,
please ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Tasks
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

There are ten (10) tasks, one for each week: the tasks are detailed below. There is
a table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Week 1
The text discusses how modern CPUs function. Recently a critical flaw in
microprocessor design has been discovered that allows two extremely serious
security exploits: Spectre and Meltdown. Find and summarise ONE resource that
describes how either of these exploits work. The resource (and your summary)
should focus on what is occurring in the CPU that allows these exploits to occur.
Title and Reference:
Kocher, P., Genkin, D., Gruss, D., Haas, W., Hamburg, M., Lipp, M., Mangard, S.,
Prescher, T., Schwarz, M. and Yarom, Y., 2018. Spectre Attacks: Exploiting
Speculative Execution. arXiv preprint arXiv:1801.01203.
https://arxiv.org/pdf/1801.01203.pdf
Summary:
This paper focuses on the critical flaw in the microprocessor design in CPU. This
paper discusses about the spectre and meltdown attacks in the CPU. These attacks
create serious threat for the CPU function. At a high level, Spectre attacks trick
processor into speculatively executing instructions sequences that should not have
executed during correct program execution. Meltdown attacks exploits out-of-order
execution in order to leak the target primary memory. However, meltdown attack
does not uses branch prediction for achieving speculative execution. A fundamental
security assumption underpinning all of these in which the CPU will faithfully execute
software, including its safety checks (Kocher et al. 2018). Speculative execution
unfortunately violates this assumption in ways that allow adversaries to violate the
secrecy of memory and register contents. This paper has been focusing in the
mitigating technique form these risks and threats to the CPU operation functions. The
feasibility of exploitation helps on depending on a number of factors including the
software and hardware systems of the PC. Various mitigating strategies have been
provided in the paper. Fuzzing tools are used for mitigating these threats and issues
in the CPU operations. The microprocessor design needs to be revised according to
the need of the users.
Week 2
Prior to 1985, there were very few Operating Systems (OSes) that used Graphical
User Interfaces (GUIs). Find and summarise ONE resource that describes ONE of
these GUI operating systems. The OS must have been release prior to 1985 so
cannot be Microsoft Windows.
Title and Reference:
Johnson, J., Roberts, T.L., Verplank, W., Smith, D.C., Irby, C.H., Beard, M. and
Mackey, K., 1989. The xerox star: A retrospective. Computer, 22(9), pp.11-26.
https://wiki.cs.umd.edu/cmsc434_f09/images/c/cb/Xerox.pdf
Summary:
This paper describes about the Xerox Star operating system that uses graphical user
interface that was released in 1981. The Xerox Star has been a significant for
increasing the demand of IT industry in the market. Star was introduced in 1981 with
a table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Week 1
The text discusses how modern CPUs function. Recently a critical flaw in
microprocessor design has been discovered that allows two extremely serious
security exploits: Spectre and Meltdown. Find and summarise ONE resource that
describes how either of these exploits work. The resource (and your summary)
should focus on what is occurring in the CPU that allows these exploits to occur.
Title and Reference:
Kocher, P., Genkin, D., Gruss, D., Haas, W., Hamburg, M., Lipp, M., Mangard, S.,
Prescher, T., Schwarz, M. and Yarom, Y., 2018. Spectre Attacks: Exploiting
Speculative Execution. arXiv preprint arXiv:1801.01203.
https://arxiv.org/pdf/1801.01203.pdf
Summary:
This paper focuses on the critical flaw in the microprocessor design in CPU. This
paper discusses about the spectre and meltdown attacks in the CPU. These attacks
create serious threat for the CPU function. At a high level, Spectre attacks trick
processor into speculatively executing instructions sequences that should not have
executed during correct program execution. Meltdown attacks exploits out-of-order
execution in order to leak the target primary memory. However, meltdown attack
does not uses branch prediction for achieving speculative execution. A fundamental
security assumption underpinning all of these in which the CPU will faithfully execute
software, including its safety checks (Kocher et al. 2018). Speculative execution
unfortunately violates this assumption in ways that allow adversaries to violate the
secrecy of memory and register contents. This paper has been focusing in the
mitigating technique form these risks and threats to the CPU operation functions. The
feasibility of exploitation helps on depending on a number of factors including the
software and hardware systems of the PC. Various mitigating strategies have been
provided in the paper. Fuzzing tools are used for mitigating these threats and issues
in the CPU operations. The microprocessor design needs to be revised according to
the need of the users.
Week 2
Prior to 1985, there were very few Operating Systems (OSes) that used Graphical
User Interfaces (GUIs). Find and summarise ONE resource that describes ONE of
these GUI operating systems. The OS must have been release prior to 1985 so
cannot be Microsoft Windows.
Title and Reference:
Johnson, J., Roberts, T.L., Verplank, W., Smith, D.C., Irby, C.H., Beard, M. and
Mackey, K., 1989. The xerox star: A retrospective. Computer, 22(9), pp.11-26.
https://wiki.cs.umd.edu/cmsc434_f09/images/c/cb/Xerox.pdf
Summary:
This paper describes about the Xerox Star operating system that uses graphical user
interface that was released in 1981. The Xerox Star has been a significant for
increasing the demand of IT industry in the market. Star was introduced in 1981 with

its bitmapped screen, mouse driven interface and clearly distinguished from other
computers. The GUI has helped in maintaining a proper look to the computer screen.
Users can focus on their work and use various software on their PC. The applications
installed in the Xerox operating system is visible to the users that helped in gaining
the interest of users for using their PC (Johnson et al. 1989). The Star features were
focusing in the low level architectural view of users in the market. The OS has been
able to fulfil the demands of the customers at that time in the market. The operation
system include the distributed personal computing technique. This paper has
described about the distributed personal computing. This operating system depends
on the direct manipulation of the data objects in the discrete functions of operating
system.
Week 3
Low-Powered Wide-Area Networks (LPWANs) are wireless communication networks
that are characterised by linking devices over large distances. Devices (including
simple sensors) typically can only communicate at very low bit rates, however, the
communication and associated electronics consume very little power. As such,
LPWAN devices can be battery powered and operate independently for many
months or even years. Find and summarise ONE resource that describes ONE
platform or technology that implements a LPWAN.
Title and Reference:
Kartakis, S., Choudhary, B.D., Gluhak, A.D., Lambrinos, L. and McCann, J.A., 2016,
October. Demystifying low-power wide-area communications for city IoT applications.
In Proceedings of the Tenth ACM International Workshop on Wireless Network
Testbeds, Experimental Evaluation, and Characterization (pp. 2-8). ACM.
https://spiral.imperial.ac.uk/bitstream/10044/1/37548/2/Demystifying%20Low-Power
%20Wide Area%20Communications%20for%20City%20IoT%20Applications.pdf
Summary:
This paper descries about the application of Low power wide area communication in
the IoT connectivity technology. This technology has been helping in minimizing the
issues of the mesh network of wires and cables for connecting various computers
and devices. In recent days, low power wide area technologies have been available
for the kilometre wide communication. However, there is a lack of understanding
about the behaviour of such technologies under real conditions. The LPWA
technologies have been an emerging technologies that has been included in new
physical layer communications capable of leveraging trade-off between range and
data-types. City sensing communication require low-cost materials and low-powered
sensing nodes. LPWA technologies helps in providing guidelines for the urban IoT
developer (Kartakis et al. 2016). The use of the IoT applications have been
maintaining the services provided to the customers in the market. The use of this
technology has helped in maintaining a clear and concise communication in the
computer devices. This paper describes about the implementation of the LPWA in
the communication sector for interconnecting into a network. This paper has been
based in initial experiments performed during designing a real world sensing solution
with several LPWA modules. The real development of the technology has been
depicted in the paper.
Week 4
Voice over IP (VoIP) is a group of hardware and software technologies that allow
computers. The GUI has helped in maintaining a proper look to the computer screen.
Users can focus on their work and use various software on their PC. The applications
installed in the Xerox operating system is visible to the users that helped in gaining
the interest of users for using their PC (Johnson et al. 1989). The Star features were
focusing in the low level architectural view of users in the market. The OS has been
able to fulfil the demands of the customers at that time in the market. The operation
system include the distributed personal computing technique. This paper has
described about the distributed personal computing. This operating system depends
on the direct manipulation of the data objects in the discrete functions of operating
system.
Week 3
Low-Powered Wide-Area Networks (LPWANs) are wireless communication networks
that are characterised by linking devices over large distances. Devices (including
simple sensors) typically can only communicate at very low bit rates, however, the
communication and associated electronics consume very little power. As such,
LPWAN devices can be battery powered and operate independently for many
months or even years. Find and summarise ONE resource that describes ONE
platform or technology that implements a LPWAN.
Title and Reference:
Kartakis, S., Choudhary, B.D., Gluhak, A.D., Lambrinos, L. and McCann, J.A., 2016,
October. Demystifying low-power wide-area communications for city IoT applications.
In Proceedings of the Tenth ACM International Workshop on Wireless Network
Testbeds, Experimental Evaluation, and Characterization (pp. 2-8). ACM.
https://spiral.imperial.ac.uk/bitstream/10044/1/37548/2/Demystifying%20Low-Power
%20Wide Area%20Communications%20for%20City%20IoT%20Applications.pdf
Summary:
This paper descries about the application of Low power wide area communication in
the IoT connectivity technology. This technology has been helping in minimizing the
issues of the mesh network of wires and cables for connecting various computers
and devices. In recent days, low power wide area technologies have been available
for the kilometre wide communication. However, there is a lack of understanding
about the behaviour of such technologies under real conditions. The LPWA
technologies have been an emerging technologies that has been included in new
physical layer communications capable of leveraging trade-off between range and
data-types. City sensing communication require low-cost materials and low-powered
sensing nodes. LPWA technologies helps in providing guidelines for the urban IoT
developer (Kartakis et al. 2016). The use of the IoT applications have been
maintaining the services provided to the customers in the market. The use of this
technology has helped in maintaining a clear and concise communication in the
computer devices. This paper describes about the implementation of the LPWA in
the communication sector for interconnecting into a network. This paper has been
based in initial experiments performed during designing a real world sensing solution
with several LPWA modules. The real development of the technology has been
depicted in the paper.
Week 4
Voice over IP (VoIP) is a group of hardware and software technologies that allow

users to communicate via voice and video over the Internet. VoIP uses a number of
different software protocols, depending on the application. Find and summarise ONE
resource that describes ONE of these VoIP protocols.
Title and Reference:
Lange, M.R. and Saric, A., 2016. Substitution between fixed, mobile, and voice over
IP telephony–Evidence from the European Union. Telecommunications
Policy, 40(10-11), pp.1007-1019.
Summary:
This paper deals with the development of the telecommunication in the European
market. This paper explores about the access substitution of mobile calls and
communication. The use of the voice over IP has been helping in providing a clear
voice Call over the internet. This technology also support the video conferencing
along with voice calls over large distances. There has been recent developments in
the EU communication market due to the implementation of the voice over IP. The
challenges in the mobile telecommunication have been described in the paper. This
paper discusses about the vulnerability issues in the mobile communication methods.
This paper focuses on the implementation of the voice over the IP in the European
commission system. An empirical strategy has been used in order to complete the
research in this paper (Lange, M.R. and Saric 2016). The use of the voice over IP
has been heeling in imagining the conversation and communication of the users with
the systems in the European commission. The use of this technology in the system
might he in enhancing the voice and video calls over the internet. It also helps in
increasing the privacy of the chat and video calls among users.
Week 5
different software protocols, depending on the application. Find and summarise ONE
resource that describes ONE of these VoIP protocols.
Title and Reference:
Lange, M.R. and Saric, A., 2016. Substitution between fixed, mobile, and voice over
IP telephony–Evidence from the European Union. Telecommunications
Policy, 40(10-11), pp.1007-1019.
Summary:
This paper deals with the development of the telecommunication in the European
market. This paper explores about the access substitution of mobile calls and
communication. The use of the voice over IP has been helping in providing a clear
voice Call over the internet. This technology also support the video conferencing
along with voice calls over large distances. There has been recent developments in
the EU communication market due to the implementation of the voice over IP. The
challenges in the mobile telecommunication have been described in the paper. This
paper discusses about the vulnerability issues in the mobile communication methods.
This paper focuses on the implementation of the voice over the IP in the European
commission system. An empirical strategy has been used in order to complete the
research in this paper (Lange, M.R. and Saric 2016). The use of the voice over IP
has been heeling in imagining the conversation and communication of the users with
the systems in the European commission. The use of this technology in the system
might he in enhancing the voice and video calls over the internet. It also helps in
increasing the privacy of the chat and video calls among users.
Week 5
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

One of the many uses of cryptography has been the development of the blockchain. Blockchains are commonly used as the basis for maintaining the data
integrity of crypto currencies, though have many, many more applications. Find and summarise ONE resource that describes how blockchains work. Note
that the resource should focus on the blockchain mechanism, NOT crypto currencies.
Title and Reference:
Zheng, Z., Xie, S., Dai, H.N. and Wang, H., 2016. Blockchain challenges and opportunities: A survey. Work Pap.–2016.
https://www.researchgate.net/profile/Hong-Ning_Dai/publication/319058582_Blockchain_Challenges_and_Opportunities_A_Survey/links/
59d86d50a6fdcc2aad0a2f2a/Blockchain-Challenges-and-Opportunities-A-Survey.pdf
Summary:
This report discusses about the benefits and challenges of the blockchain technology in the market. The use of the blockchain technology have been helping
in maintaining the transfer of digital mete and transaction all over the world. The use of the block chain technology have been minimizing the challenges in
transferring digital accounts and documents between parties. The cryptography technology has been used in the block chain. The digital documents are
properly encrypted to end=sure the security of the data and information of company. This paper has discussed about the architecture of the blockchain in order
to understand the phenomenon if the blockchain in the market. Different components of the blockchain has been providing in the paper (Zheng et al. 2016).
The challenges to the blockchain technology in the market has been discusses in the report. This technology has been creating various security issues in the
marmite related to the financial transfer pf documents in the market. There are no third party between the transactions. Therefore, there in track of the
transaction dine between parties. The zero involvement of the third party helps in reducing the extra cost of the transferring the money. Various security
algorithms have been discuss3d in this report including the RSA algorithm that might help in mitigating the security issues in the block chain technology.
integrity of crypto currencies, though have many, many more applications. Find and summarise ONE resource that describes how blockchains work. Note
that the resource should focus on the blockchain mechanism, NOT crypto currencies.
Title and Reference:
Zheng, Z., Xie, S., Dai, H.N. and Wang, H., 2016. Blockchain challenges and opportunities: A survey. Work Pap.–2016.
https://www.researchgate.net/profile/Hong-Ning_Dai/publication/319058582_Blockchain_Challenges_and_Opportunities_A_Survey/links/
59d86d50a6fdcc2aad0a2f2a/Blockchain-Challenges-and-Opportunities-A-Survey.pdf
Summary:
This report discusses about the benefits and challenges of the blockchain technology in the market. The use of the blockchain technology have been helping
in maintaining the transfer of digital mete and transaction all over the world. The use of the block chain technology have been minimizing the challenges in
transferring digital accounts and documents between parties. The cryptography technology has been used in the block chain. The digital documents are
properly encrypted to end=sure the security of the data and information of company. This paper has discussed about the architecture of the blockchain in order
to understand the phenomenon if the blockchain in the market. Different components of the blockchain has been providing in the paper (Zheng et al. 2016).
The challenges to the blockchain technology in the market has been discusses in the report. This technology has been creating various security issues in the
marmite related to the financial transfer pf documents in the market. There are no third party between the transactions. Therefore, there in track of the
transaction dine between parties. The zero involvement of the third party helps in reducing the extra cost of the transferring the money. Various security
algorithms have been discuss3d in this report including the RSA algorithm that might help in mitigating the security issues in the block chain technology.

Week 6
One controversial practical application of network traffic management is in the
contravention of the principle of “net neutrality”. Find and summarise ONE resource
that describes what net neutrality is and how its contravention could impact on
individual and business users of the Internet.
Title and Reference:
Choi, J.P., Jeon, D.S. and Kim, B.C., 2018. Net neutrality, network capacity, and
innovation at the edges. The Journal of Industrial Economics, 66(1), pp.172-204.
https://pdfs.semanticscholar.org/7a37/4bc8d1f38f21db9972b14b2863c6f3253ea0.pdf
Summary:
This paper discusses about net neutrality principle on the internet that needs to be
treated equally in their delivery process without any discrimination and charges in the
content source. The internet traffic management is n topic fir the research as the
traffic over the websites has been increased. This have been causing server
jamming problem in the organization (Choi,, Jeon. and Kim 2018). This paper have
developed a theoretical model that might help in analysing the effect of net neutrality
regulation on innovation incentives of major content providers. The ISP investment in
the internet traffic management has been maintained by the system. The use of the
net neutrality helps in maintaining the network congestion and QoS improvement.
One controversial practical application of network traffic management is in the
contravention of the principle of “net neutrality”. Find and summarise ONE resource
that describes what net neutrality is and how its contravention could impact on
individual and business users of the Internet.
Title and Reference:
Choi, J.P., Jeon, D.S. and Kim, B.C., 2018. Net neutrality, network capacity, and
innovation at the edges. The Journal of Industrial Economics, 66(1), pp.172-204.
https://pdfs.semanticscholar.org/7a37/4bc8d1f38f21db9972b14b2863c6f3253ea0.pdf
Summary:
This paper discusses about net neutrality principle on the internet that needs to be
treated equally in their delivery process without any discrimination and charges in the
content source. The internet traffic management is n topic fir the research as the
traffic over the websites has been increased. This have been causing server
jamming problem in the organization (Choi,, Jeon. and Kim 2018). This paper have
developed a theoretical model that might help in analysing the effect of net neutrality
regulation on innovation incentives of major content providers. The ISP investment in
the internet traffic management has been maintained by the system. The use of the
net neutrality helps in maintaining the network congestion and QoS improvement.
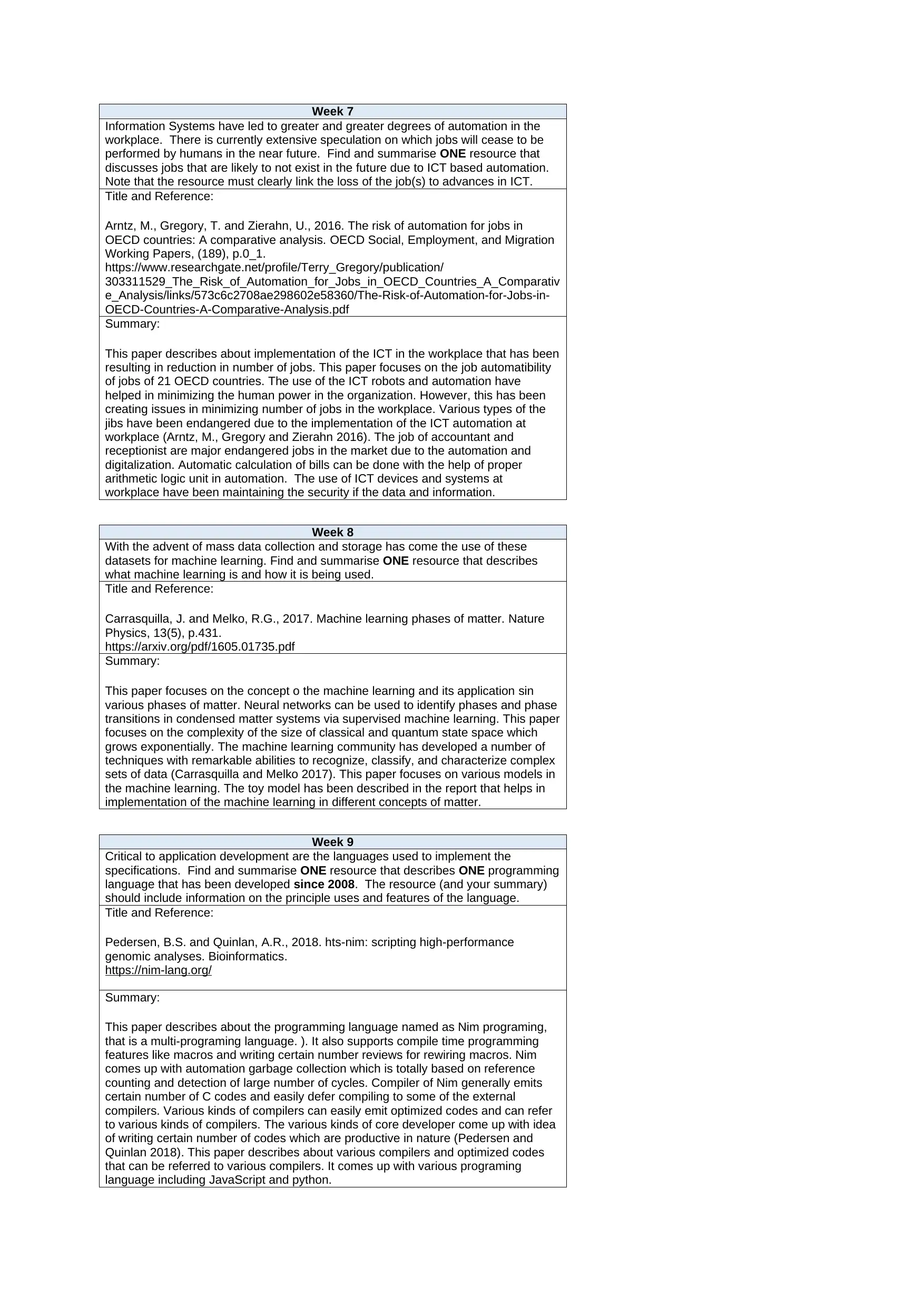
Week 7
Information Systems have led to greater and greater degrees of automation in the
workplace. There is currently extensive speculation on which jobs will cease to be
performed by humans in the near future. Find and summarise ONE resource that
discusses jobs that are likely to not exist in the future due to ICT based automation.
Note that the resource must clearly link the loss of the job(s) to advances in ICT.
Title and Reference:
Arntz, M., Gregory, T. and Zierahn, U., 2016. The risk of automation for jobs in
OECD countries: A comparative analysis. OECD Social, Employment, and Migration
Working Papers, (189), p.0_1.
https://www.researchgate.net/profile/Terry_Gregory/publication/
303311529_The_Risk_of_Automation_for_Jobs_in_OECD_Countries_A_Comparativ
e_Analysis/links/573c6c2708ae298602e58360/The-Risk-of-Automation-for-Jobs-in-
OECD-Countries-A-Comparative-Analysis.pdf
Summary:
This paper describes about implementation of the ICT in the workplace that has been
resulting in reduction in number of jobs. This paper focuses on the job automatibility
of jobs of 21 OECD countries. The use of the ICT robots and automation have
helped in minimizing the human power in the organization. However, this has been
creating issues in minimizing number of jobs in the workplace. Various types of the
jibs have been endangered due to the implementation of the ICT automation at
workplace (Arntz, M., Gregory and Zierahn 2016). The job of accountant and
receptionist are major endangered jobs in the market due to the automation and
digitalization. Automatic calculation of bills can be done with the help of proper
arithmetic logic unit in automation. The use of ICT devices and systems at
workplace have been maintaining the security if the data and information.
Week 8
With the advent of mass data collection and storage has come the use of these
datasets for machine learning. Find and summarise ONE resource that describes
what machine learning is and how it is being used.
Title and Reference:
Carrasquilla, J. and Melko, R.G., 2017. Machine learning phases of matter. Nature
Physics, 13(5), p.431.
https://arxiv.org/pdf/1605.01735.pdf
Summary:
This paper focuses on the concept o the machine learning and its application sin
various phases of matter. Neural networks can be used to identify phases and phase
transitions in condensed matter systems via supervised machine learning. This paper
focuses on the complexity of the size of classical and quantum state space which
grows exponentially. The machine learning community has developed a number of
techniques with remarkable abilities to recognize, classify, and characterize complex
sets of data (Carrasquilla and Melko 2017). This paper focuses on various models in
the machine learning. The toy model has been described in the report that helps in
implementation of the machine learning in different concepts of matter.
Week 9
Critical to application development are the languages used to implement the
specifications. Find and summarise ONE resource that describes ONE programming
language that has been developed since 2008. The resource (and your summary)
should include information on the principle uses and features of the language.
Title and Reference:
Pedersen, B.S. and Quinlan, A.R., 2018. hts-nim: scripting high-performance
genomic analyses. Bioinformatics.
https://nim-lang.org/
Summary:
This paper describes about the programming language named as Nim programing,
that is a multi-programing language. ). It also supports compile time programming
features like macros and writing certain number reviews for rewiring macros. Nim
comes up with automation garbage collection which is totally based on reference
counting and detection of large number of cycles. Compiler of Nim generally emits
certain number of C codes and easily defer compiling to some of the external
compilers. Various kinds of compilers can easily emit optimized codes and can refer
to various kinds of compilers. The various kinds of core developer come up with idea
of writing certain number of codes which are productive in nature (Pedersen and
Quinlan 2018). This paper describes about various compilers and optimized codes
that can be referred to various compilers. It comes up with various programing
language including JavaScript and python.
Information Systems have led to greater and greater degrees of automation in the
workplace. There is currently extensive speculation on which jobs will cease to be
performed by humans in the near future. Find and summarise ONE resource that
discusses jobs that are likely to not exist in the future due to ICT based automation.
Note that the resource must clearly link the loss of the job(s) to advances in ICT.
Title and Reference:
Arntz, M., Gregory, T. and Zierahn, U., 2016. The risk of automation for jobs in
OECD countries: A comparative analysis. OECD Social, Employment, and Migration
Working Papers, (189), p.0_1.
https://www.researchgate.net/profile/Terry_Gregory/publication/
303311529_The_Risk_of_Automation_for_Jobs_in_OECD_Countries_A_Comparativ
e_Analysis/links/573c6c2708ae298602e58360/The-Risk-of-Automation-for-Jobs-in-
OECD-Countries-A-Comparative-Analysis.pdf
Summary:
This paper describes about implementation of the ICT in the workplace that has been
resulting in reduction in number of jobs. This paper focuses on the job automatibility
of jobs of 21 OECD countries. The use of the ICT robots and automation have
helped in minimizing the human power in the organization. However, this has been
creating issues in minimizing number of jobs in the workplace. Various types of the
jibs have been endangered due to the implementation of the ICT automation at
workplace (Arntz, M., Gregory and Zierahn 2016). The job of accountant and
receptionist are major endangered jobs in the market due to the automation and
digitalization. Automatic calculation of bills can be done with the help of proper
arithmetic logic unit in automation. The use of ICT devices and systems at
workplace have been maintaining the security if the data and information.
Week 8
With the advent of mass data collection and storage has come the use of these
datasets for machine learning. Find and summarise ONE resource that describes
what machine learning is and how it is being used.
Title and Reference:
Carrasquilla, J. and Melko, R.G., 2017. Machine learning phases of matter. Nature
Physics, 13(5), p.431.
https://arxiv.org/pdf/1605.01735.pdf
Summary:
This paper focuses on the concept o the machine learning and its application sin
various phases of matter. Neural networks can be used to identify phases and phase
transitions in condensed matter systems via supervised machine learning. This paper
focuses on the complexity of the size of classical and quantum state space which
grows exponentially. The machine learning community has developed a number of
techniques with remarkable abilities to recognize, classify, and characterize complex
sets of data (Carrasquilla and Melko 2017). This paper focuses on various models in
the machine learning. The toy model has been described in the report that helps in
implementation of the machine learning in different concepts of matter.
Week 9
Critical to application development are the languages used to implement the
specifications. Find and summarise ONE resource that describes ONE programming
language that has been developed since 2008. The resource (and your summary)
should include information on the principle uses and features of the language.
Title and Reference:
Pedersen, B.S. and Quinlan, A.R., 2018. hts-nim: scripting high-performance
genomic analyses. Bioinformatics.
https://nim-lang.org/
Summary:
This paper describes about the programming language named as Nim programing,
that is a multi-programing language. ). It also supports compile time programming
features like macros and writing certain number reviews for rewiring macros. Nim
comes up with automation garbage collection which is totally based on reference
counting and detection of large number of cycles. Compiler of Nim generally emits
certain number of C codes and easily defer compiling to some of the external
compilers. Various kinds of compilers can easily emit optimized codes and can refer
to various kinds of compilers. The various kinds of core developer come up with idea
of writing certain number of codes which are productive in nature (Pedersen and
Quinlan 2018). This paper describes about various compilers and optimized codes
that can be referred to various compilers. It comes up with various programing
language including JavaScript and python.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 10
While information systems and technology deliver many benefits to society, they can
also result in negative effects and outcomes. One recent controversy, the
propagation of fake news and its influence on elections, has been linked to a type of
software called a “bot”. Find and summarise ONE resource that describes what bots
are and how they can be used for disseminating misinformation and affecting human
behaviour.
Title and Reference:
Varol, O., Ferrara, E., Davis, C.A., Menczer, F. and Flammini, A., 2017. Online
human-bot interactions: Detection, estimation, and characterization. arXiv preprint
arXiv:1703.03107.
https://arxiv.org/pdf/1703.03107.pdf?ftag=MSFd61514f
Summary:
This paper describes about the online human bots over the internet. This paper
focuses on the social media and its powerful tolls for detecting the human bits over
the internet. This paper has help in proposing a bot detection framework for
detecting the bits in the internet. The human bots can steal all the details from a user
by behaving like a human over the internet. The evaluation of model has been
provided in the paper (Varol et al. 2017). The network features of the framework has
been discussed in the paper. The use of the bit evaluation technique for detecting
bots over the internet has been provided in the paper.
While information systems and technology deliver many benefits to society, they can
also result in negative effects and outcomes. One recent controversy, the
propagation of fake news and its influence on elections, has been linked to a type of
software called a “bot”. Find and summarise ONE resource that describes what bots
are and how they can be used for disseminating misinformation and affecting human
behaviour.
Title and Reference:
Varol, O., Ferrara, E., Davis, C.A., Menczer, F. and Flammini, A., 2017. Online
human-bot interactions: Detection, estimation, and characterization. arXiv preprint
arXiv:1703.03107.
https://arxiv.org/pdf/1703.03107.pdf?ftag=MSFd61514f
Summary:
This paper describes about the online human bots over the internet. This paper
focuses on the social media and its powerful tolls for detecting the human bits over
the internet. This paper has help in proposing a bot detection framework for
detecting the bits in the internet. The human bots can steal all the details from a user
by behaving like a human over the internet. The evaluation of model has been
provided in the paper (Varol et al. 2017). The network features of the framework has
been discussed in the paper. The use of the bit evaluation technique for detecting
bots over the internet has been provided in the paper.
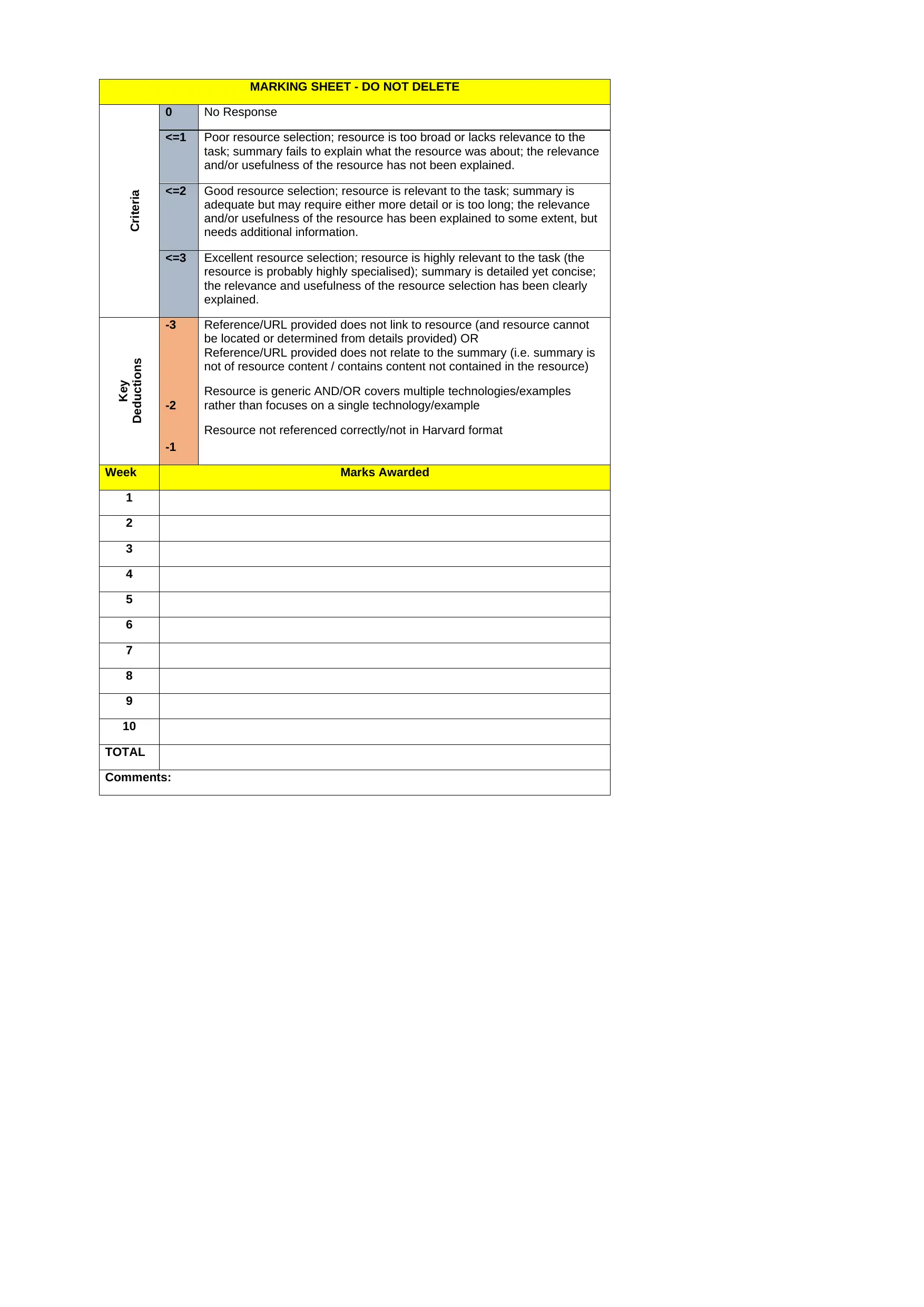
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content / contains content not contained in the resource)
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



