COIT 20246 Assignment: Analyzing Computer Systems and IoT Applications
VerifiedAdded on 2022/10/11
|14
|4610
|12
Homework Assignment
AI Summary
This assignment, submitted for COIT 20246, presents summaries of various computer science topics. Week 1 explores the differences between SIMD and MIMD architectures, highlighting their significance in parallel processing, with SIMD using synchronous processing and MIMD incorporating asynchronous mechanisms. Week 2 focuses on deadlock prevention algorithms, specifically the wait-die algorithm, explaining how it prevents deadlocks by prioritizing older processes. Week 3 discusses IoT applications in smart farming, detailing how IoT technologies enhance agricultural practices through sensors, drones, and automated systems. Week 4 examines technologies for running IPv4 and IPv6 simultaneously, specifically the dual-stack approach. Week 5 covers using mobile device IDs for authentication. Week 6 discusses the Facebook security breach and its impact. Week 7 differentiates between e-business and e-commerce, explaining their distinct characteristics. Week 8 addresses SAP HANA migration. Week 9 explores rapid application development with Node.js, and Week 10 analyzes reasons for IT system implementation failures. Each summary provides the context, key points, and usefulness of the selected resources, adhering to the CQU Harvard referencing style and the specified word count.

COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Instructions
It will be necessary to use online resources to complete this assignment, please
ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is
a table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Each summary should briefly explain:
- What the resource is about
- Why you selected it
- What are the main points or key information covered in the resource
- Why the resource was useful.
For more advice about how to complete the assignment, as well as examples and
information about selecting good resources, please see the assessment page on the
Moodle unit web site:
https://moodle.cqu.edu.au/mod/assign/view.php?id=965540
1
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Instructions
It will be necessary to use online resources to complete this assignment, please
ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is
a table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Each summary should briefly explain:
- What the resource is about
- Why you selected it
- What are the main points or key information covered in the resource
- Why the resource was useful.
For more advice about how to complete the assignment, as well as examples and
information about selecting good resources, please see the assessment page on the
Moodle unit web site:
https://moodle.cqu.edu.au/mod/assign/view.php?id=965540
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
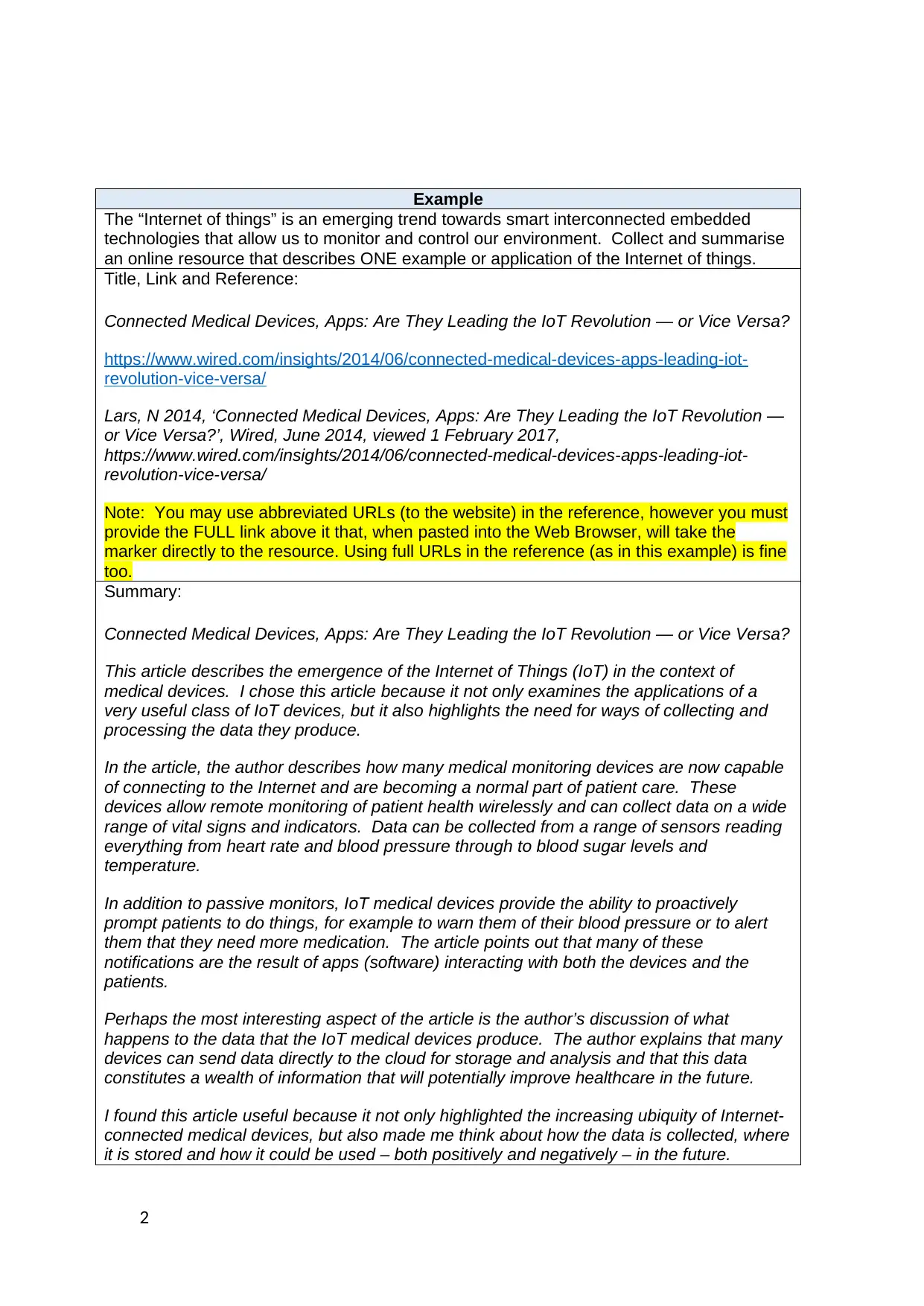
Example
The “Internet of things” is an emerging trend towards smart interconnected embedded
technologies that allow us to monitor and control our environment. Collect and summarise
an online resource that describes ONE example or application of the Internet of things.
Title, Link and Reference:
Connected Medical Devices, Apps: Are They Leading the IoT Revolution — or Vice Versa?
https://www.wired.com/insights/2014/06/connected-medical-devices-apps-leading-iot-
revolution-vice-versa/
Lars, N 2014, ‘Connected Medical Devices, Apps: Are They Leading the IoT Revolution —
or Vice Versa?’, Wired, June 2014, viewed 1 February 2017,
https://www.wired.com/insights/2014/06/connected-medical-devices-apps-leading-iot-
revolution-vice-versa/
Note: You may use abbreviated URLs (to the website) in the reference, however you must
provide the FULL link above it that, when pasted into the Web Browser, will take the
marker directly to the resource. Using full URLs in the reference (as in this example) is fine
too.
Summary:
Connected Medical Devices, Apps: Are They Leading the IoT Revolution — or Vice Versa?
This article describes the emergence of the Internet of Things (IoT) in the context of
medical devices. I chose this article because it not only examines the applications of a
very useful class of IoT devices, but it also highlights the need for ways of collecting and
processing the data they produce.
In the article, the author describes how many medical monitoring devices are now capable
of connecting to the Internet and are becoming a normal part of patient care. These
devices allow remote monitoring of patient health wirelessly and can collect data on a wide
range of vital signs and indicators. Data can be collected from a range of sensors reading
everything from heart rate and blood pressure through to blood sugar levels and
temperature.
In addition to passive monitors, IoT medical devices provide the ability to proactively
prompt patients to do things, for example to warn them of their blood pressure or to alert
them that they need more medication. The article points out that many of these
notifications are the result of apps (software) interacting with both the devices and the
patients.
Perhaps the most interesting aspect of the article is the author’s discussion of what
happens to the data that the IoT medical devices produce. The author explains that many
devices can send data directly to the cloud for storage and analysis and that this data
constitutes a wealth of information that will potentially improve healthcare in the future.
I found this article useful because it not only highlighted the increasing ubiquity of Internet-
connected medical devices, but also made me think about how the data is collected, where
it is stored and how it could be used – both positively and negatively – in the future.
2
The “Internet of things” is an emerging trend towards smart interconnected embedded
technologies that allow us to monitor and control our environment. Collect and summarise
an online resource that describes ONE example or application of the Internet of things.
Title, Link and Reference:
Connected Medical Devices, Apps: Are They Leading the IoT Revolution — or Vice Versa?
https://www.wired.com/insights/2014/06/connected-medical-devices-apps-leading-iot-
revolution-vice-versa/
Lars, N 2014, ‘Connected Medical Devices, Apps: Are They Leading the IoT Revolution —
or Vice Versa?’, Wired, June 2014, viewed 1 February 2017,
https://www.wired.com/insights/2014/06/connected-medical-devices-apps-leading-iot-
revolution-vice-versa/
Note: You may use abbreviated URLs (to the website) in the reference, however you must
provide the FULL link above it that, when pasted into the Web Browser, will take the
marker directly to the resource. Using full URLs in the reference (as in this example) is fine
too.
Summary:
Connected Medical Devices, Apps: Are They Leading the IoT Revolution — or Vice Versa?
This article describes the emergence of the Internet of Things (IoT) in the context of
medical devices. I chose this article because it not only examines the applications of a
very useful class of IoT devices, but it also highlights the need for ways of collecting and
processing the data they produce.
In the article, the author describes how many medical monitoring devices are now capable
of connecting to the Internet and are becoming a normal part of patient care. These
devices allow remote monitoring of patient health wirelessly and can collect data on a wide
range of vital signs and indicators. Data can be collected from a range of sensors reading
everything from heart rate and blood pressure through to blood sugar levels and
temperature.
In addition to passive monitors, IoT medical devices provide the ability to proactively
prompt patients to do things, for example to warn them of their blood pressure or to alert
them that they need more medication. The article points out that many of these
notifications are the result of apps (software) interacting with both the devices and the
patients.
Perhaps the most interesting aspect of the article is the author’s discussion of what
happens to the data that the IoT medical devices produce. The author explains that many
devices can send data directly to the cloud for storage and analysis and that this data
constitutes a wealth of information that will potentially improve healthcare in the future.
I found this article useful because it not only highlighted the increasing ubiquity of Internet-
connected medical devices, but also made me think about how the data is collected, where
it is stored and how it could be used – both positively and negatively – in the future.
2

Week 1
The text discusses about different architectures for parallel processing used for
Multiprocessor Machines such as multiple-instruction stream - multiple-data stream
(MIMD), single-instruction stream - multiple-data stream (SIMD) etc. Find and
summarise ONE resource that compares between MIMD and SIMD architectures.
The resource and your summary must focus only on MIMD and SIMD architectures.
Title, Link and Reference:
A comparative analysis of SIMD and MIMD architectures
Kaur, M. & Kaur, R 2013, ‘A comparative analysis of SIMD and MIMD architectures’, International
Journal of Advanced Research in Computer Science and Software Engineering, vol. 3, no. 9, pp.1151-
1156. (http://ijarcsse.com/Before_August_2017/docs/papers/Volume_3/9_September2013/V3I9-
0332.pdf)
Summary:
This article describes significance distribution between SIMD and MIMD
architectures in categorization with various areas. I selected this article as it not only
elaborates both in details with parallel computers but also clearly states what is data
stream and instruction streams.
In this article, Single Instruction stream, Multiple Data stream (SIMD) stated as a
form of parallel architecture where a single instruction is implemented to a group of
the data stream or unique data at the same time. On the other hand, MIMD stands for
Multiple Instruction Multiple Data Stream includes workstations having multiple
processing units, instruction stream and data streams. It is known to be one of the
most complex configurations but it also ensures efficiency.
The key differences between SIMD and MIMD are that SIMD follows synchronous
processing whereas MIMD incorporated an asynchronous mechanism over various
communication program. As only one print of the program is stored by SIMD, it
requires less memory where memory requirements increases in MIMD as its
individual copy of program is stored by processing elements. MIMD is more costly
than SIMD as it needs one decoder for each processing element. As last, there is
greater performance in SIMD in case of uniform control unit overlap while in the
non-uniform CU overlap MIMD is higher effective.
I found this article beneficial as it not only defined both the terms but also gives a
competitive explorations of both the articles and thus made me think, which
architecture is better in which area.
Week 2
3
The text discusses about different architectures for parallel processing used for
Multiprocessor Machines such as multiple-instruction stream - multiple-data stream
(MIMD), single-instruction stream - multiple-data stream (SIMD) etc. Find and
summarise ONE resource that compares between MIMD and SIMD architectures.
The resource and your summary must focus only on MIMD and SIMD architectures.
Title, Link and Reference:
A comparative analysis of SIMD and MIMD architectures
Kaur, M. & Kaur, R 2013, ‘A comparative analysis of SIMD and MIMD architectures’, International
Journal of Advanced Research in Computer Science and Software Engineering, vol. 3, no. 9, pp.1151-
1156. (http://ijarcsse.com/Before_August_2017/docs/papers/Volume_3/9_September2013/V3I9-
0332.pdf)
Summary:
This article describes significance distribution between SIMD and MIMD
architectures in categorization with various areas. I selected this article as it not only
elaborates both in details with parallel computers but also clearly states what is data
stream and instruction streams.
In this article, Single Instruction stream, Multiple Data stream (SIMD) stated as a
form of parallel architecture where a single instruction is implemented to a group of
the data stream or unique data at the same time. On the other hand, MIMD stands for
Multiple Instruction Multiple Data Stream includes workstations having multiple
processing units, instruction stream and data streams. It is known to be one of the
most complex configurations but it also ensures efficiency.
The key differences between SIMD and MIMD are that SIMD follows synchronous
processing whereas MIMD incorporated an asynchronous mechanism over various
communication program. As only one print of the program is stored by SIMD, it
requires less memory where memory requirements increases in MIMD as its
individual copy of program is stored by processing elements. MIMD is more costly
than SIMD as it needs one decoder for each processing element. As last, there is
greater performance in SIMD in case of uniform control unit overlap while in the
non-uniform CU overlap MIMD is higher effective.
I found this article beneficial as it not only defined both the terms but also gives a
competitive explorations of both the articles and thus made me think, which
architecture is better in which area.
Week 2
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The text discusses about one of the common problems that can arise during
resource allocation in operating systems, which is known as deadlock. Find and
summarise ONE resource that describes an algorithm of either deadlock avoidance
or deadlock prevention. The resource, and your summary, must focus on a single
algorithm of either deadlock avoidance or deadlock prevention, NOT both.
Title, Link and Reference:
Deadlock Prevention Algorithms
Krzyzanowski, P 2017, Distributed Deadlock, viewed 31 August 2010,
https://www.cs.rutgers.edu/~pxk/417/notes/deadlock.html
Summary:
This article describes deadlock prevention algorithms and I chose this article as it
clearly elaborates prevention algorithms with diagrams and simple conditions.
In a system, a deadlock is known to be as condition where various processes do
request for resources that can never be satisfied. It is necessary to design a system
considering an alternative to detect deadlocks. Deadlock prevention is known to be as
a mechanism to ensure that at least one significant condition for deadlock can never
arise. For the current resources, resource request and resource availability, there is no
requirement of data by the system in case of deadlock prevention. Some of the
deadlock prevention includes serializing tokens and non-blocking synchronization
algorithms. With regards to this, all the resources are requested at once in deadlock
prevention.
The four conditions include mutual exclusion, hold and wait, non-preemption and
circular wait. When one process is trying to block waiting for a resource that is
already use by another process, it need to assess which of the two processes relates to
a younger timestamp and offer priority to the older process.
If the resource is being used by a younger process, then the older process (that seeks
for the resource) waits. On the other hand, if an older process is holding the resource,
the younger process (that needs the resource) waits. If an older process is holding the
resource, the younger process (that seeks for the resource) aborts itself. This power
the graph of resource utilization to be directed from older to younger processes,
making cycle unmanageable. It is also called as the wait-die algorithm.
This article is useful for me as it made me understand deadlock prevention algorithms
with an effective example in relation with series of queues.
4
resource allocation in operating systems, which is known as deadlock. Find and
summarise ONE resource that describes an algorithm of either deadlock avoidance
or deadlock prevention. The resource, and your summary, must focus on a single
algorithm of either deadlock avoidance or deadlock prevention, NOT both.
Title, Link and Reference:
Deadlock Prevention Algorithms
Krzyzanowski, P 2017, Distributed Deadlock, viewed 31 August 2010,
https://www.cs.rutgers.edu/~pxk/417/notes/deadlock.html
Summary:
This article describes deadlock prevention algorithms and I chose this article as it
clearly elaborates prevention algorithms with diagrams and simple conditions.
In a system, a deadlock is known to be as condition where various processes do
request for resources that can never be satisfied. It is necessary to design a system
considering an alternative to detect deadlocks. Deadlock prevention is known to be as
a mechanism to ensure that at least one significant condition for deadlock can never
arise. For the current resources, resource request and resource availability, there is no
requirement of data by the system in case of deadlock prevention. Some of the
deadlock prevention includes serializing tokens and non-blocking synchronization
algorithms. With regards to this, all the resources are requested at once in deadlock
prevention.
The four conditions include mutual exclusion, hold and wait, non-preemption and
circular wait. When one process is trying to block waiting for a resource that is
already use by another process, it need to assess which of the two processes relates to
a younger timestamp and offer priority to the older process.
If the resource is being used by a younger process, then the older process (that seeks
for the resource) waits. On the other hand, if an older process is holding the resource,
the younger process (that needs the resource) waits. If an older process is holding the
resource, the younger process (that seeks for the resource) aborts itself. This power
the graph of resource utilization to be directed from older to younger processes,
making cycle unmanageable. It is also called as the wait-die algorithm.
This article is useful for me as it made me understand deadlock prevention algorithms
with an effective example in relation with series of queues.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 3
Internet of things (IoT) is an emerging trend towards smart interconnected
embedded technologies that allow us to monitor and control our environment. Find
and summarise ONE resource that describes applications of the Internet of things
in the field of Smart Farming. The resource and your summary must focus on
application of IoT ONLY in the field of smart farming.
Title, Link and Reference:
Internet of Things Platform for Smart Farming
Jayaraman, P., Yavari, A., Georgakopoulos, D., Morshed, A. & Zaslavsky, A 2016,
‘Internet of things platform for smart farming: Experiences and lessons
learnt’. Sensors, vol. 16, no. 11, p. 1884.
(https://www.researchgate.net/publication/309894257_Internet_of_Things_Platform_for_Smart_
Farming_Experiences_and_Lessons_Learnt)
Summary:
This resource provides definition of IoT and its application in the arena of
agriculture.
I chose this article as it precisely states various applications of IoT based farming
and its impact in future.
The article states that IoT has the ability to impact the world where we live, sectors
with progression; smart cities all are from IoT norms. In the upcoming time, there
will be significant increase in the farming practices to feed the earth population, as
there will be nearly 9.6 billion people by 2050. The production is also getting
hampered due to various environmental problems and IoT based farming can help
in this situation as with Smart farming concept evolved from IoT, it will help in
raising productivity while decreasing waste. Deployment of IT technology in the
agriculture is known as smart farming where the crops in the area are observed
through the help of sensors that include humidity, light, temperature moisture of
soil with automated irrigation machines. In IoT based farming, some of necessary
application include agriculture drones, precise farming, livestock monitoring and
smart greenhouse. For instance, agriculture drones can help in spreading of various
fertilizers in the field, and also for other security purposes. In livestock monitoring,
farmer can observe health situation of the cattle and the location. Deployment of
5
Internet of things (IoT) is an emerging trend towards smart interconnected
embedded technologies that allow us to monitor and control our environment. Find
and summarise ONE resource that describes applications of the Internet of things
in the field of Smart Farming. The resource and your summary must focus on
application of IoT ONLY in the field of smart farming.
Title, Link and Reference:
Internet of Things Platform for Smart Farming
Jayaraman, P., Yavari, A., Georgakopoulos, D., Morshed, A. & Zaslavsky, A 2016,
‘Internet of things platform for smart farming: Experiences and lessons
learnt’. Sensors, vol. 16, no. 11, p. 1884.
(https://www.researchgate.net/publication/309894257_Internet_of_Things_Platform_for_Smart_
Farming_Experiences_and_Lessons_Learnt)
Summary:
This resource provides definition of IoT and its application in the arena of
agriculture.
I chose this article as it precisely states various applications of IoT based farming
and its impact in future.
The article states that IoT has the ability to impact the world where we live, sectors
with progression; smart cities all are from IoT norms. In the upcoming time, there
will be significant increase in the farming practices to feed the earth population, as
there will be nearly 9.6 billion people by 2050. The production is also getting
hampered due to various environmental problems and IoT based farming can help
in this situation as with Smart farming concept evolved from IoT, it will help in
raising productivity while decreasing waste. Deployment of IT technology in the
agriculture is known as smart farming where the crops in the area are observed
through the help of sensors that include humidity, light, temperature moisture of
soil with automated irrigation machines. In IoT based farming, some of necessary
application include agriculture drones, precise farming, livestock monitoring and
smart greenhouse. For instance, agriculture drones can help in spreading of various
fertilizers in the field, and also for other security purposes. In livestock monitoring,
farmer can observe health situation of the cattle and the location. Deployment of
5

applications of IoT in greenhouse can be more effective than traditional way at it
routinely assess the situation of all the parameters needs for production of crops.
This resource is beneficial as it clearly states about various applications of IoT that
can be used in future to save farming and environment.
Week 4
The text discusses about IPv4, however, IPv6 is the emerging protocol which is in
the process of superseding IPv4. Find and summarise ONE resource that describes
about the technologies that are used to run both protocols simultaneously over the
same internet infrastructure.
Title, Link and Reference:
IPv6 and the transition from IPv4
Sclafani, P 2019, IPv6 and the transition from IPv4 explained, viewed 31 August 2010,
https://www.6connect.com/resources/ipv6-and-the-transition-from-ipv4-explained/
Summary:
This article describes dual stack technology that is used to run both protocols
simultaneously and I chose this articles as it starts with basic definition and
elaboration and includes various diagrams for easier understanding of the technology
and concept.
Considering background, IPv6 deployments increase over time, the natural next step
will be decreasing the role of IPv4 and back ends networks of management and front
end applications.
Dual stack is a transition technology in which IPv4 and IPv6 function in tandem over
dedicated and shared links. Both of protocol are completely deployed across the
infrastructure and everything online must transition to include both Ipv4 and Ipv6. In
addition, the switches, routers, computers and other devices operate both protocols in
Dual-IP stacks while getting easy support from all major OS and network vendors.
Dual Stack can be seen as an ideal solution but there are also two deployment
challenges faced by organizations and ISPs. It needs an existing infrastructure grid
that is capable of executing IPv6 but in many circumstances, there can be issue
relating to hardware and software updates. There is also needs activation of IPv6 on
major networks elements and to fulfil the requirement, the present network is required
to be redesigned. I found this resource beneficial as it made me understand about dual
6
routinely assess the situation of all the parameters needs for production of crops.
This resource is beneficial as it clearly states about various applications of IoT that
can be used in future to save farming and environment.
Week 4
The text discusses about IPv4, however, IPv6 is the emerging protocol which is in
the process of superseding IPv4. Find and summarise ONE resource that describes
about the technologies that are used to run both protocols simultaneously over the
same internet infrastructure.
Title, Link and Reference:
IPv6 and the transition from IPv4
Sclafani, P 2019, IPv6 and the transition from IPv4 explained, viewed 31 August 2010,
https://www.6connect.com/resources/ipv6-and-the-transition-from-ipv4-explained/
Summary:
This article describes dual stack technology that is used to run both protocols
simultaneously and I chose this articles as it starts with basic definition and
elaboration and includes various diagrams for easier understanding of the technology
and concept.
Considering background, IPv6 deployments increase over time, the natural next step
will be decreasing the role of IPv4 and back ends networks of management and front
end applications.
Dual stack is a transition technology in which IPv4 and IPv6 function in tandem over
dedicated and shared links. Both of protocol are completely deployed across the
infrastructure and everything online must transition to include both Ipv4 and Ipv6. In
addition, the switches, routers, computers and other devices operate both protocols in
Dual-IP stacks while getting easy support from all major OS and network vendors.
Dual Stack can be seen as an ideal solution but there are also two deployment
challenges faced by organizations and ISPs. It needs an existing infrastructure grid
that is capable of executing IPv6 but in many circumstances, there can be issue
relating to hardware and software updates. There is also needs activation of IPv6 on
major networks elements and to fulfil the requirement, the present network is required
to be redesigned. I found this resource beneficial as it made me understand about dual
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

stack technology in depth and its relation with the respective protocols IPv4 and IPv6.
Week 5
Network security has become a major concern of the ICT world, and user
authentication is one of the popular tools to assure network security. Find and
summarise ONE resource that describes any ONE authentication mechanism except
password. The resource, and your summary should focus purely on ONLY ONE type
of authentication mechanism.
Title, Link and Reference:
Hardware Token
sciencedirect.com 2014, Identification and Authentication, viewed 31 August 2019,
https://www.sciencedirect.com/topics/computer-science/hardware-token
Summary:
This article describes one of the secure authentication mechanism i.e. hardware
typically seen in the form factor of keychain fob or a credit card. I select this resource
as it explicitly states about hardware token and its uses. It also clears the advantage of
two factor authentication from a security outlook.
Hardware token is carried by the owner to authorize access to a network service.
There is an algorithm embedded in the device which needs to be matched with the
numbers that are being entered by the user. More complex hardware tokens are also
come up with LCD display and this approach towards authentication is also known as
multifactor authentication and it is considered to be stronger as it needs two factors.
The first factor is something only the individual remember (i.e. password) and
somewhat only the individual has (i.e. mobile phone). From a security viewpoint, the
hardware device in a Two-Factor authentication solution should be retained with the
user at all periods to have it safe.
I found this resource beneficial as it helps me aware about new authentication
mechanism techniques that give two factor protection to the user with the help of
serial number in the hardware token.
7
Week 5
Network security has become a major concern of the ICT world, and user
authentication is one of the popular tools to assure network security. Find and
summarise ONE resource that describes any ONE authentication mechanism except
password. The resource, and your summary should focus purely on ONLY ONE type
of authentication mechanism.
Title, Link and Reference:
Hardware Token
sciencedirect.com 2014, Identification and Authentication, viewed 31 August 2019,
https://www.sciencedirect.com/topics/computer-science/hardware-token
Summary:
This article describes one of the secure authentication mechanism i.e. hardware
typically seen in the form factor of keychain fob or a credit card. I select this resource
as it explicitly states about hardware token and its uses. It also clears the advantage of
two factor authentication from a security outlook.
Hardware token is carried by the owner to authorize access to a network service.
There is an algorithm embedded in the device which needs to be matched with the
numbers that are being entered by the user. More complex hardware tokens are also
come up with LCD display and this approach towards authentication is also known as
multifactor authentication and it is considered to be stronger as it needs two factors.
The first factor is something only the individual remember (i.e. password) and
somewhat only the individual has (i.e. mobile phone). From a security viewpoint, the
hardware device in a Two-Factor authentication solution should be retained with the
user at all periods to have it safe.
I found this resource beneficial as it helps me aware about new authentication
mechanism techniques that give two factor protection to the user with the help of
serial number in the hardware token.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
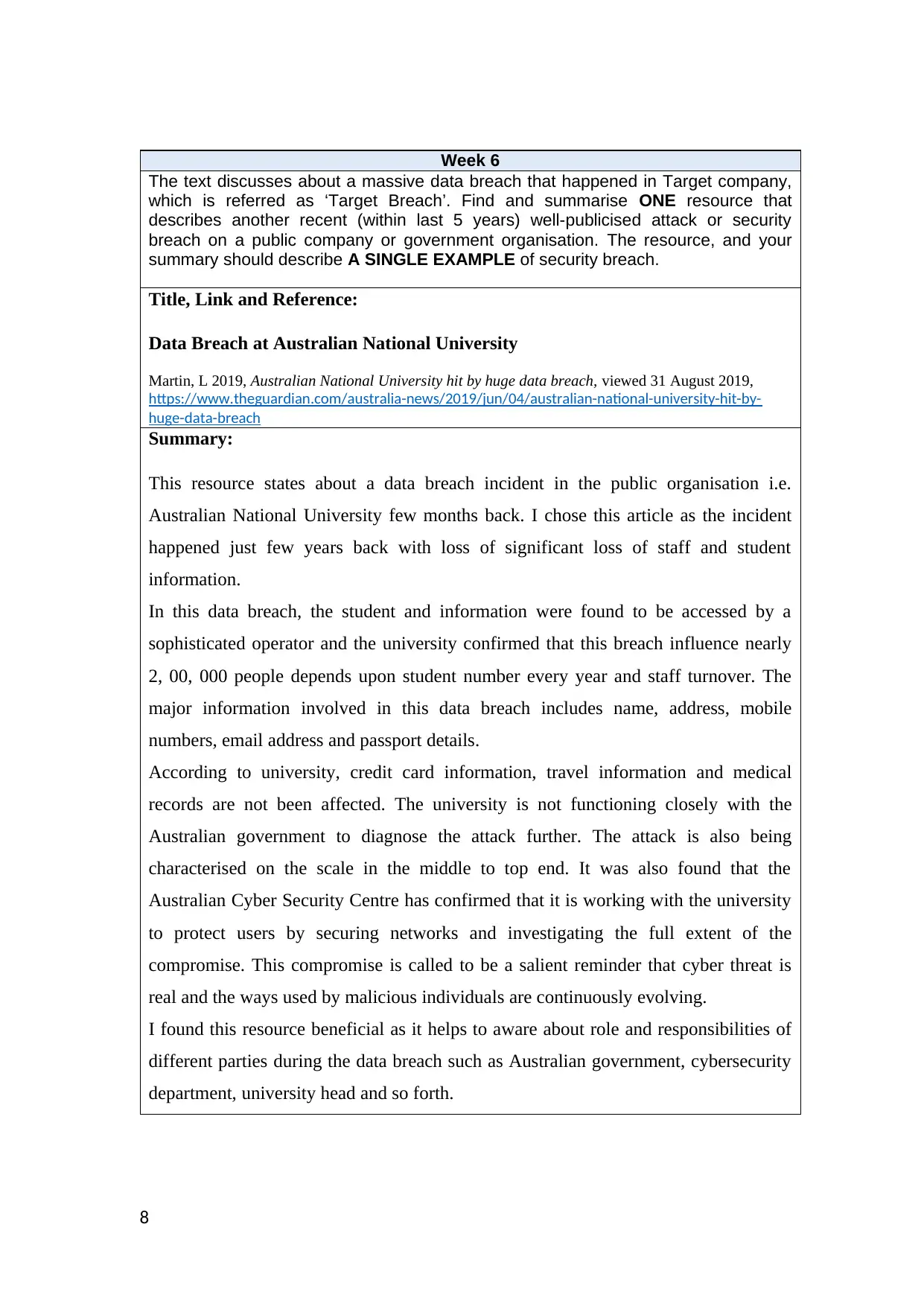
Week 6
The text discusses about a massive data breach that happened in Target company,
which is referred as ‘Target Breach’. Find and summarise ONE resource that
describes another recent (within last 5 years) well-publicised attack or security
breach on a public company or government organisation. The resource, and your
summary should describe A SINGLE EXAMPLE of security breach.
Title, Link and Reference:
Data Breach at Australian National University
Martin, L 2019, Australian National University hit by huge data breach, viewed 31 August 2019,
https://www.theguardian.com/australia-news/2019/jun/04/australian-national-university-hit-by-
huge-data-breach
Summary:
This resource states about a data breach incident in the public organisation i.e.
Australian National University few months back. I chose this article as the incident
happened just few years back with loss of significant loss of staff and student
information.
In this data breach, the student and information were found to be accessed by a
sophisticated operator and the university confirmed that this breach influence nearly
2, 00, 000 people depends upon student number every year and staff turnover. The
major information involved in this data breach includes name, address, mobile
numbers, email address and passport details.
According to university, credit card information, travel information and medical
records are not been affected. The university is not functioning closely with the
Australian government to diagnose the attack further. The attack is also being
characterised on the scale in the middle to top end. It was also found that the
Australian Cyber Security Centre has confirmed that it is working with the university
to protect users by securing networks and investigating the full extent of the
compromise. This compromise is called to be a salient reminder that cyber threat is
real and the ways used by malicious individuals are continuously evolving.
I found this resource beneficial as it helps to aware about role and responsibilities of
different parties during the data breach such as Australian government, cybersecurity
department, university head and so forth.
8
The text discusses about a massive data breach that happened in Target company,
which is referred as ‘Target Breach’. Find and summarise ONE resource that
describes another recent (within last 5 years) well-publicised attack or security
breach on a public company or government organisation. The resource, and your
summary should describe A SINGLE EXAMPLE of security breach.
Title, Link and Reference:
Data Breach at Australian National University
Martin, L 2019, Australian National University hit by huge data breach, viewed 31 August 2019,
https://www.theguardian.com/australia-news/2019/jun/04/australian-national-university-hit-by-
huge-data-breach
Summary:
This resource states about a data breach incident in the public organisation i.e.
Australian National University few months back. I chose this article as the incident
happened just few years back with loss of significant loss of staff and student
information.
In this data breach, the student and information were found to be accessed by a
sophisticated operator and the university confirmed that this breach influence nearly
2, 00, 000 people depends upon student number every year and staff turnover. The
major information involved in this data breach includes name, address, mobile
numbers, email address and passport details.
According to university, credit card information, travel information and medical
records are not been affected. The university is not functioning closely with the
Australian government to diagnose the attack further. The attack is also being
characterised on the scale in the middle to top end. It was also found that the
Australian Cyber Security Centre has confirmed that it is working with the university
to protect users by securing networks and investigating the full extent of the
compromise. This compromise is called to be a salient reminder that cyber threat is
real and the ways used by malicious individuals are continuously evolving.
I found this resource beneficial as it helps to aware about role and responsibilities of
different parties during the data breach such as Australian government, cybersecurity
department, university head and so forth.
8

Week 7
The text briefly discusses about e-commerce and e-business. Find and summarise
ONE resource that discusses the relationship between e-commerce and e-business.
The resource, and your summary should describe similarities and difference between
e-commerce and e-business.
Title, Link and Reference:
E-Business and E-Commerce
Magento 2017, E-Business vs E-Commerce, Know The Differences, viewed 31 August 2019,
https://medium.com/@Magento_expert/e-business-vs-e-commerce-know-the-differences-
151ec9baf0fe
Summary:
This article describes significance similarities and variances between e-commerce and
e-business as a two popular network. I chose this article due to its simplicity and
proper arrangement of explanation followed by definition, advantage, disadvantage,
similarities and differences.
E-business and E-commerce both are operated over network and e-commerce is
considered to be a subset of e-commerce. Both e-business and e-commerce owners
sustain service-oriented webpage while cultivating an online presence but the main
purpose of e-commerce website is to sell products whereas e-business website
generally helps in offering necessary information to the consumer about a product or
service to benefit them in taking out effective purchasing decision. E-business covers
broad range of other activities, unlike e-commerce that covers only online transaction.
In case of both e-commerce and e-business, the relationship is being maintained amid
service and vendor partners and this sort of interactions between businesses is very
necessary to enable organisations to offer their consumers with additions, add-ons and
accessories to the services and products that they sell and market.
When it comes to E-commerce and E-business, both the businesses owner and
consumers can gain all necessary benefits. I found this resource beneficial as it helps
me in clearing various doubts related to e-business and e-commerce.
9
The text briefly discusses about e-commerce and e-business. Find and summarise
ONE resource that discusses the relationship between e-commerce and e-business.
The resource, and your summary should describe similarities and difference between
e-commerce and e-business.
Title, Link and Reference:
E-Business and E-Commerce
Magento 2017, E-Business vs E-Commerce, Know The Differences, viewed 31 August 2019,
https://medium.com/@Magento_expert/e-business-vs-e-commerce-know-the-differences-
151ec9baf0fe
Summary:
This article describes significance similarities and variances between e-commerce and
e-business as a two popular network. I chose this article due to its simplicity and
proper arrangement of explanation followed by definition, advantage, disadvantage,
similarities and differences.
E-business and E-commerce both are operated over network and e-commerce is
considered to be a subset of e-commerce. Both e-business and e-commerce owners
sustain service-oriented webpage while cultivating an online presence but the main
purpose of e-commerce website is to sell products whereas e-business website
generally helps in offering necessary information to the consumer about a product or
service to benefit them in taking out effective purchasing decision. E-business covers
broad range of other activities, unlike e-commerce that covers only online transaction.
In case of both e-commerce and e-business, the relationship is being maintained amid
service and vendor partners and this sort of interactions between businesses is very
necessary to enable organisations to offer their consumers with additions, add-ons and
accessories to the services and products that they sell and market.
When it comes to E-commerce and E-business, both the businesses owner and
consumers can gain all necessary benefits. I found this resource beneficial as it helps
me in clearing various doubts related to e-business and e-commerce.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
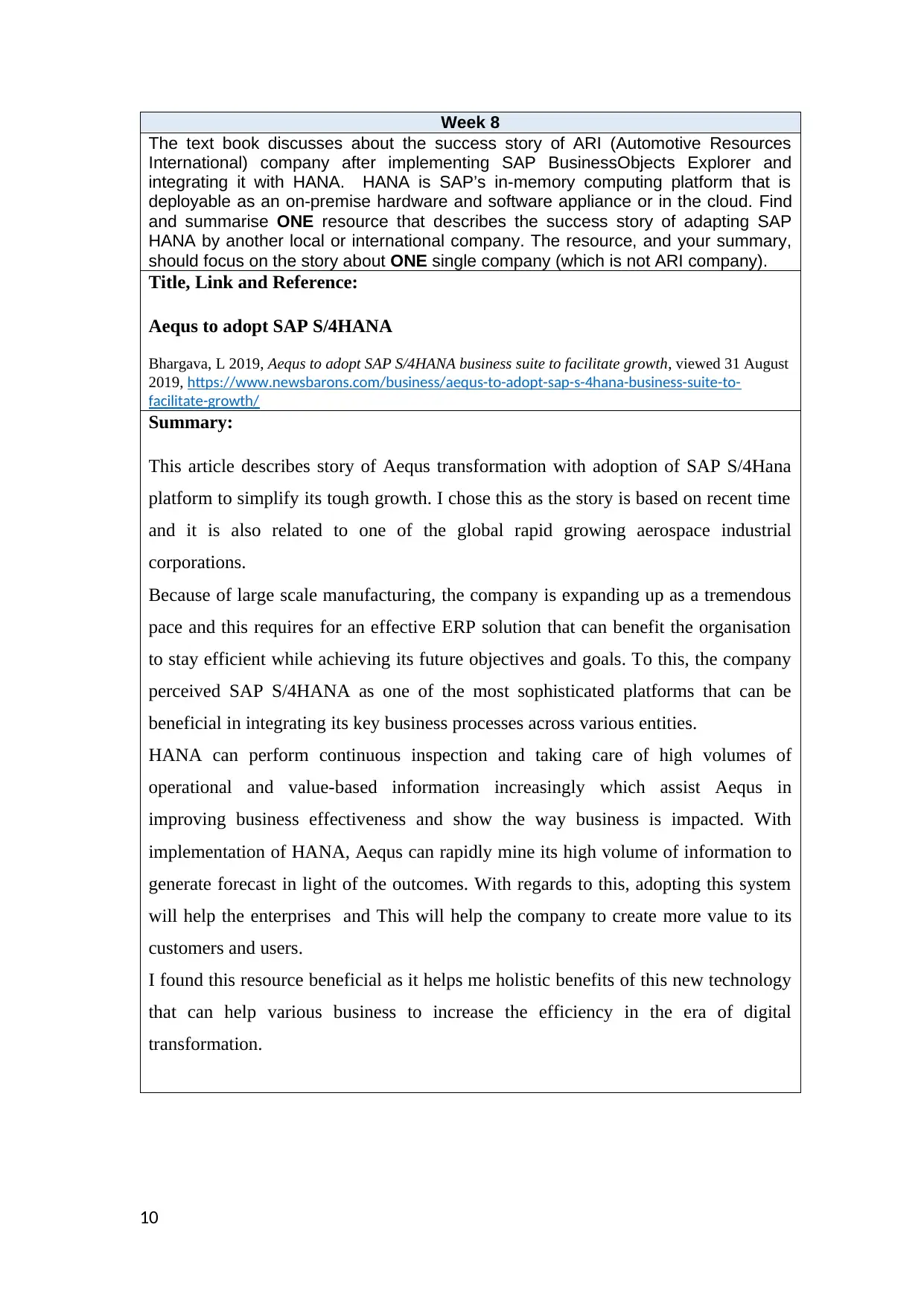
Week 8
The text book discusses about the success story of ARI (Automotive Resources
International) company after implementing SAP BusinessObjects Explorer and
integrating it with HANA. HANA is SAP’s in-memory computing platform that is
deployable as an on-premise hardware and software appliance or in the cloud. Find
and summarise ONE resource that describes the success story of adapting SAP
HANA by another local or international company. The resource, and your summary,
should focus on the story about ONE single company (which is not ARI company).
Title, Link and Reference:
Aequs to adopt SAP S/4HANA
Bhargava, L 2019, Aequs to adopt SAP S/4HANA business suite to facilitate growth, viewed 31 August
2019, https://www.newsbarons.com/business/aequs-to-adopt-sap-s-4hana-business-suite-to-
facilitate-growth/
Summary:
This article describes story of Aequs transformation with adoption of SAP S/4Hana
platform to simplify its tough growth. I chose this as the story is based on recent time
and it is also related to one of the global rapid growing aerospace industrial
corporations.
Because of large scale manufacturing, the company is expanding up as a tremendous
pace and this requires for an effective ERP solution that can benefit the organisation
to stay efficient while achieving its future objectives and goals. To this, the company
perceived SAP S/4HANA as one of the most sophisticated platforms that can be
beneficial in integrating its key business processes across various entities.
HANA can perform continuous inspection and taking care of high volumes of
operational and value-based information increasingly which assist Aequs in
improving business effectiveness and show the way business is impacted. With
implementation of HANA, Aequs can rapidly mine its high volume of information to
generate forecast in light of the outcomes. With regards to this, adopting this system
will help the enterprises and This will help the company to create more value to its
customers and users.
I found this resource beneficial as it helps me holistic benefits of this new technology
that can help various business to increase the efficiency in the era of digital
transformation.
10
The text book discusses about the success story of ARI (Automotive Resources
International) company after implementing SAP BusinessObjects Explorer and
integrating it with HANA. HANA is SAP’s in-memory computing platform that is
deployable as an on-premise hardware and software appliance or in the cloud. Find
and summarise ONE resource that describes the success story of adapting SAP
HANA by another local or international company. The resource, and your summary,
should focus on the story about ONE single company (which is not ARI company).
Title, Link and Reference:
Aequs to adopt SAP S/4HANA
Bhargava, L 2019, Aequs to adopt SAP S/4HANA business suite to facilitate growth, viewed 31 August
2019, https://www.newsbarons.com/business/aequs-to-adopt-sap-s-4hana-business-suite-to-
facilitate-growth/
Summary:
This article describes story of Aequs transformation with adoption of SAP S/4Hana
platform to simplify its tough growth. I chose this as the story is based on recent time
and it is also related to one of the global rapid growing aerospace industrial
corporations.
Because of large scale manufacturing, the company is expanding up as a tremendous
pace and this requires for an effective ERP solution that can benefit the organisation
to stay efficient while achieving its future objectives and goals. To this, the company
perceived SAP S/4HANA as one of the most sophisticated platforms that can be
beneficial in integrating its key business processes across various entities.
HANA can perform continuous inspection and taking care of high volumes of
operational and value-based information increasingly which assist Aequs in
improving business effectiveness and show the way business is impacted. With
implementation of HANA, Aequs can rapidly mine its high volume of information to
generate forecast in light of the outcomes. With regards to this, adopting this system
will help the enterprises and This will help the company to create more value to its
customers and users.
I found this resource beneficial as it helps me holistic benefits of this new technology
that can help various business to increase the efficiency in the era of digital
transformation.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 9
Rapid application development (RAD) is a process of creating a workable system in a
very short period of time. There are few recently developed frameworks available in
market to undertake RAD. Find and summarise ONE recent (within last two years)
resource that describes and recommends about ONE framework for RAD.
Title, Link and Reference:
Flutter framework for RAD
Jain, A 2018, 9 Points you must know about Flutter SDK, viewed 31 August
2019,https://medium.com/mindorks/9-points-you-must-know-about-flutter-sdk-3b7308c2b265
Summary:
This article describes Flutter framework for RAD and I chose this article because its
highlight details about Flutter Framework in just 9 steps which are useful for the readers
to gain out relevant information and especially for the developers.
Flutter is taking out headlines due to its growth in mobile development space. Its
popularity can be assessed with its adoption by some big companies like Google Ads,
Alibaba, Hamilton and many more. For instance, Google has already been come up with
Fuchsia OS where all the apps for Fuchsia OS will be developed using flutter. In addition,
it also has its own set of widgets rather than using the widgets offered by the host
operating system.
Flutter is not a language as it’s an SDK and its free and open source. Although it is used
by various companies, however, they are only using in some part of their apps. In
addition, due to its newness, it does not have very large community support and also
flutter app are also bigger in size than its native counterpart by 50-60%.
Flutter is a great cross-platform solution and increasing with time as various start-ups are
recruiting flutter developers for developing their mobile applications. However, it is
known to be as a very young language and therefore, it lags in plugins and various
Android/iOS libraries as these libraries account for a huge volume.
I found this resource beneficial as it helps provides me a holistic view of this new RAD
framework gaining popularity amid big companies.
11
Rapid application development (RAD) is a process of creating a workable system in a
very short period of time. There are few recently developed frameworks available in
market to undertake RAD. Find and summarise ONE recent (within last two years)
resource that describes and recommends about ONE framework for RAD.
Title, Link and Reference:
Flutter framework for RAD
Jain, A 2018, 9 Points you must know about Flutter SDK, viewed 31 August
2019,https://medium.com/mindorks/9-points-you-must-know-about-flutter-sdk-3b7308c2b265
Summary:
This article describes Flutter framework for RAD and I chose this article because its
highlight details about Flutter Framework in just 9 steps which are useful for the readers
to gain out relevant information and especially for the developers.
Flutter is taking out headlines due to its growth in mobile development space. Its
popularity can be assessed with its adoption by some big companies like Google Ads,
Alibaba, Hamilton and many more. For instance, Google has already been come up with
Fuchsia OS where all the apps for Fuchsia OS will be developed using flutter. In addition,
it also has its own set of widgets rather than using the widgets offered by the host
operating system.
Flutter is not a language as it’s an SDK and its free and open source. Although it is used
by various companies, however, they are only using in some part of their apps. In
addition, due to its newness, it does not have very large community support and also
flutter app are also bigger in size than its native counterpart by 50-60%.
Flutter is a great cross-platform solution and increasing with time as various start-ups are
recruiting flutter developers for developing their mobile applications. However, it is
known to be as a very young language and therefore, it lags in plugins and various
Android/iOS libraries as these libraries account for a huge volume.
I found this resource beneficial as it helps provides me a holistic view of this new RAD
framework gaining popularity amid big companies.
11

Week 10
The failure to successfully implement large scale IS has led to the downfall of many
previously successful companies. Find and summarise ONE resource that describes
few reasons of implementation failure for large scale IS. The resource, and your
summary, should analyse at least three reasons of the failure.
Title, Link and Reference:
Reasons of implementation failure for large scale IS
Faye, D 2016, The Top 10 Reasons Why Software Implementations Fail, viewed 31 August 2019,
https://fayebsg.com/2016/10/the-top-10-reasons-why-software-implementations-fail/
Summary:
This article states about various causes for the failure of large scale IS while
implementing in various companies. I chose this article as states more than three
reasons of the failure and thus improving the way to understand various approaches.
As per the article, the first reason is not to define clear goals for the project as if an
organisation does not conduct pre-implementation assessment of critical objectives, it
becomes impossible to highlight the cause for the failure of IS at operational level.
The other reasons are that believing IS will solve the problem when it is just a tool or
enabler. Insufficient training and support can also negatively influence a project or an
organisation implemented IS. If an organisation choose wrong provider, it can lead to
being too expensive for the organisation while lacking expertise. These are some of
the reasons why IS implementation fails for any company operating at any scale or
size. It can be said that a Bigger software is not always better but it can be improved if
proper planning made in advance to increase rate of success in the upcoming time
toward progression. Todays, IS becomes the lifeline of many business enterprise and
it is must to ensure that no barrier leads to negative impact as otherwise it will lead to
influence other business areas too.
The resource is helpful as along with the reasons, it also provides glimpse of various
other factor too having significant contribution in failure of IS and also impact long
term success of an enterprise.
12
The failure to successfully implement large scale IS has led to the downfall of many
previously successful companies. Find and summarise ONE resource that describes
few reasons of implementation failure for large scale IS. The resource, and your
summary, should analyse at least three reasons of the failure.
Title, Link and Reference:
Reasons of implementation failure for large scale IS
Faye, D 2016, The Top 10 Reasons Why Software Implementations Fail, viewed 31 August 2019,
https://fayebsg.com/2016/10/the-top-10-reasons-why-software-implementations-fail/
Summary:
This article states about various causes for the failure of large scale IS while
implementing in various companies. I chose this article as states more than three
reasons of the failure and thus improving the way to understand various approaches.
As per the article, the first reason is not to define clear goals for the project as if an
organisation does not conduct pre-implementation assessment of critical objectives, it
becomes impossible to highlight the cause for the failure of IS at operational level.
The other reasons are that believing IS will solve the problem when it is just a tool or
enabler. Insufficient training and support can also negatively influence a project or an
organisation implemented IS. If an organisation choose wrong provider, it can lead to
being too expensive for the organisation while lacking expertise. These are some of
the reasons why IS implementation fails for any company operating at any scale or
size. It can be said that a Bigger software is not always better but it can be improved if
proper planning made in advance to increase rate of success in the upcoming time
toward progression. Todays, IS becomes the lifeline of many business enterprise and
it is must to ensure that no barrier leads to negative impact as otherwise it will lead to
influence other business areas too.
The resource is helpful as along with the reasons, it also provides glimpse of various
other factor too having significant contribution in failure of IS and also impact long
term success of an enterprise.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
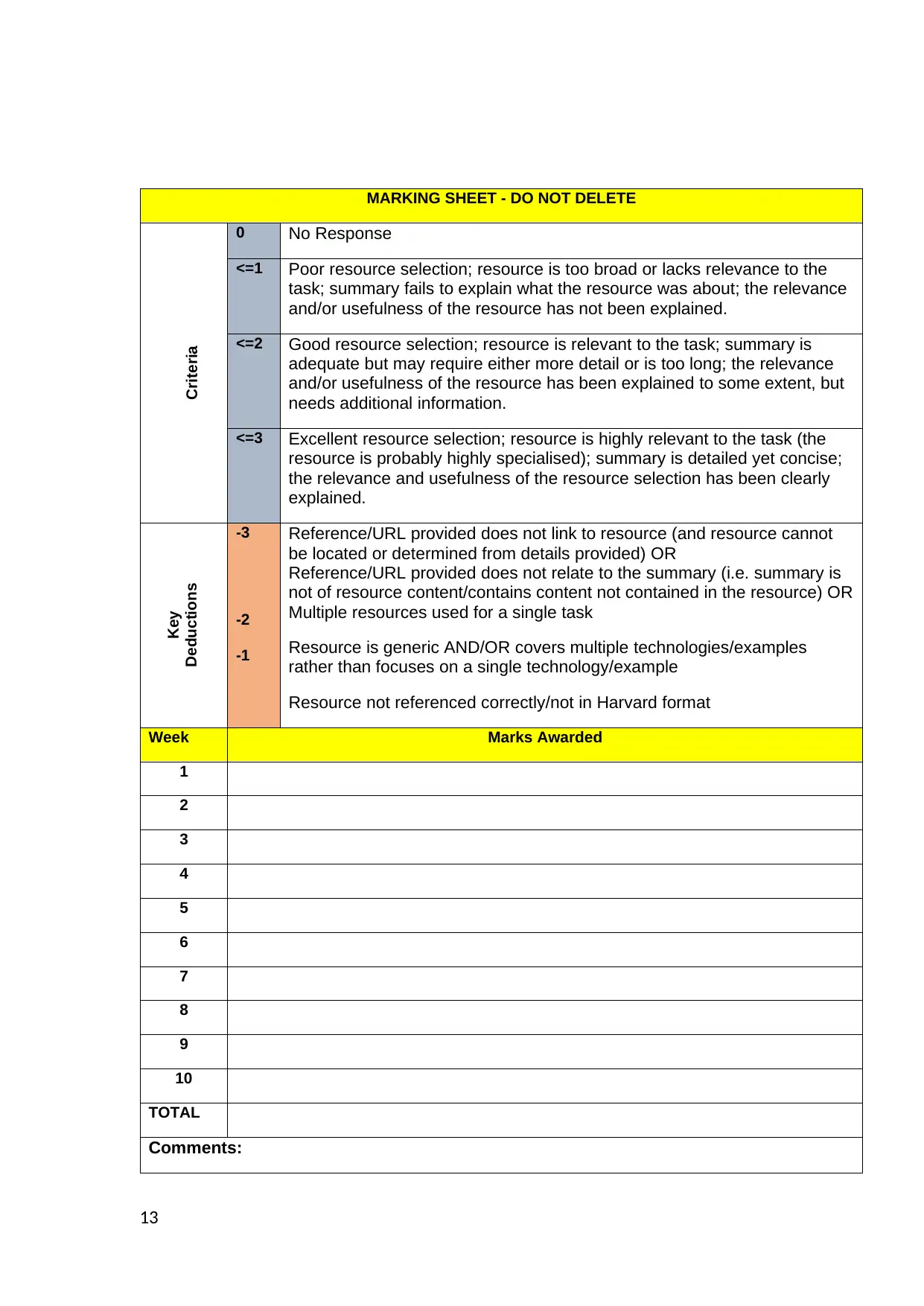
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content/contains content not contained in the resource) OR
Multiple resources used for a single task
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
13
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content/contains content not contained in the resource) OR
Multiple resources used for a single task
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

14
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





