COIT11238 Written Assignment Submission (T3 2017) Analysis
VerifiedAdded on 2020/05/16
|14
|3589
|42
Homework Assignment
AI Summary
This document presents a comprehensive solution to the COIT11238 written assignment for Term 3 2017. The assignment covers a wide range of networking topics, starting with common ICT terminology errors and their correct usage. It delves into the concept of a kernel within an operating system an...

COIT11238 WRITTEN ASSIGNMENT SUBMISSION
(T3 2017)
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
While it should not be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using the
Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
WRitten ASSESSMENT TEMPLATE - PAGE 1
(T3 2017)
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Instructions
While it should not be necessary to use literature/online resources to complete this
assignment, please ensure you cite and reference any such materials using the
Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Please fill in the following details:
Student Name
Student Number
WRitten ASSESSMENT TEMPLATE - PAGE 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week One
Assignment Question:
People often misuse ICT terminology. Imagine you receive the following email:
Dear Helpdesk
My hard drive took ages to boot-up this morning and now my Internet has stopped
working and I can’t print anything. Help!
Frustrated User.
What terminology mistakes has the user made? What terminology should they have
used?
Your answer:
The user have made terminology mistake while posting complain because the
internet connection is not dependent on the printing jobs. The user have stated that
his printing is not working due to his internet connection and that is totally wrong. The
boot up time depends on the services and programs enabled at the start up and the
unnecessary programs must be disabled for reducing the start-up time.
The terminology that should be used by the users is quoted below:
“Dear helpdesk,
I wish to lodge a complaint about the PC that I am using because it took more time
than the usual to boot-up. While connecting to the internet I found that it had stopped
working. I cannot connect my printer for printing anything.
I am looking forward for any solution to resolve the problem
Sincerely,
Username
Date”
Your question:
What is a kernel?
Your sample answer:
It is the central heart of the operating system and use for providing essential service
required for running small applications and other components of the operating
system. The kernel of the OS is kept small because it is loaded into the main memory
at the time of booting up the operating system. The kernel is used for management of
the memory and the tasks and acts as a mediator between the hardware and the
WRitten ASSESSMENT TEMPLATE - PAGE 2
Assignment Question:
People often misuse ICT terminology. Imagine you receive the following email:
Dear Helpdesk
My hard drive took ages to boot-up this morning and now my Internet has stopped
working and I can’t print anything. Help!
Frustrated User.
What terminology mistakes has the user made? What terminology should they have
used?
Your answer:
The user have made terminology mistake while posting complain because the
internet connection is not dependent on the printing jobs. The user have stated that
his printing is not working due to his internet connection and that is totally wrong. The
boot up time depends on the services and programs enabled at the start up and the
unnecessary programs must be disabled for reducing the start-up time.
The terminology that should be used by the users is quoted below:
“Dear helpdesk,
I wish to lodge a complaint about the PC that I am using because it took more time
than the usual to boot-up. While connecting to the internet I found that it had stopped
working. I cannot connect my printer for printing anything.
I am looking forward for any solution to resolve the problem
Sincerely,
Username
Date”
Your question:
What is a kernel?
Your sample answer:
It is the central heart of the operating system and use for providing essential service
required for running small applications and other components of the operating
system. The kernel of the OS is kept small because it is loaded into the main memory
at the time of booting up the operating system. The kernel is used for management of
the memory and the tasks and acts as a mediator between the hardware and the
WRitten ASSESSMENT TEMPLATE - PAGE 2

applications installed in the operating system (Borzovs et al. 2014). The protected
area of the main memory is used for loading the kernel such that it cannot be
overwritten by another process.
Week Two
Assignment Question:
An office LAN has twenty workstations. The office manager has asked you to replace
their 100Mbps (wired) hub with a 100Mbps wireless AP. Will this increase or
decrease the bandwidth available to each workstation? Explain your reasoning.
Your answer:
The LAN connection would be the best choice because it uses full duplex connection
and the wireless access point uses the half duplex connection for transferring the
data packets. In the wireless transmission if two of the nodes connected in the
network sends data packets it can cause collision and the packet may be lost (Stuber
et al. 2017). In the wireless transmission 50 mbps speed can be obtained. The rate of
collision increases with the increase in the nodes but in case of Ethernet connection
the data packets are stored in the switch until the transmission is over. Thus and
effective 80 mbps transfer speed can be maintained.
Your question:
What are the difference between a wireless access point and adhoc networks?
Your sample answer:
The wireless network is created using a wireless access point and it is different from
the ad hoc network because there no requirement of an wireless access point for the
establishment of connection between the nodes. The ad hoc network can be
developed easily and is used for different purpose such as gaming, exchanging data,
etc. A peer to peer connection is used for the communication in the ad hoc network
and it is similar with the Bluetooth technology (Stuber et al. 2017). The ad hoc
network have different issues such as there is more congestion in the ad hoc network
and it cannot be extended.
But in case of wireless access point a permanent wireless network is created and
can be extended with the installation of repeaters or bridges for connecting more
number of wireless
devices. The
wireless access point is connected to the LAN for establishment of connection
between the nodes.
WRitten ASSESSMENT TEMPLATE - PAGE 3
area of the main memory is used for loading the kernel such that it cannot be
overwritten by another process.
Week Two
Assignment Question:
An office LAN has twenty workstations. The office manager has asked you to replace
their 100Mbps (wired) hub with a 100Mbps wireless AP. Will this increase or
decrease the bandwidth available to each workstation? Explain your reasoning.
Your answer:
The LAN connection would be the best choice because it uses full duplex connection
and the wireless access point uses the half duplex connection for transferring the
data packets. In the wireless transmission if two of the nodes connected in the
network sends data packets it can cause collision and the packet may be lost (Stuber
et al. 2017). In the wireless transmission 50 mbps speed can be obtained. The rate of
collision increases with the increase in the nodes but in case of Ethernet connection
the data packets are stored in the switch until the transmission is over. Thus and
effective 80 mbps transfer speed can be maintained.
Your question:
What are the difference between a wireless access point and adhoc networks?
Your sample answer:
The wireless network is created using a wireless access point and it is different from
the ad hoc network because there no requirement of an wireless access point for the
establishment of connection between the nodes. The ad hoc network can be
developed easily and is used for different purpose such as gaming, exchanging data,
etc. A peer to peer connection is used for the communication in the ad hoc network
and it is similar with the Bluetooth technology (Stuber et al. 2017). The ad hoc
network have different issues such as there is more congestion in the ad hoc network
and it cannot be extended.
But in case of wireless access point a permanent wireless network is created and
can be extended with the installation of repeaters or bridges for connecting more
number of wireless
devices. The
wireless access point is connected to the LAN for establishment of connection
between the nodes.
WRitten ASSESSMENT TEMPLATE - PAGE 3
You're viewing a preview
Unlock full access by subscribing today!

Week Three
Assignment Question:
There are two other LANs at GAMPS office, one for the main office (called ADMIN)
and one for the admissions gate (called GATE). There are 5 workstations on each
LAN. On ADMIN, the workstations connect to a 100Mbps hub. On GATE, the
workstations connect to a 100Mbs switch with all ports operating in half-duplex mode.
If you connected your laptop to GATE, would it be subject to more, the same or less
collisions than if it was connected to ADMIN? You can assume data rates and traffic
patterns are the same on each LAN. Justify your answer by explaining the origin of
the collisions.
Your answer:
The hubs are used as a multiport repeater and it is used for connecting multiple
nodes installed in the network. The hubs have limited capability and it cannot find the
best path for transferring the data packets for reducing wastage. The switch are used
for acting as a buffer and manage the network traffic without impacting on the
performance of the network. It have error checking and thus reduces errors in the
transmission of the data packets. It can be used for dividing the collision domain and
increase the efficiency of the network (Pluta, Stewart and Korson 2017). If a laptop is
connected with the GATE network then it would be subject to less collision because it
gets connected with the switch and the switch is efficient for management of the
traffic in the network and reduces collision to a large extend than the hubs which
broadcast the network packets causing wastage of the resources.
Your question:
Compare and contrast the physical and the logical network topology.
Your sample answer:
The physical topology is used for the demonstration of the communication channels
used for communication such as the workstations and the network cables. It consists
of the physical network structure while in case of logical network topology, the logics
used such as the protocol, IP addressing scheme, VLANs are used for demonstration
(Pluta, Stewart and Korson 2017). E.g. For a Local area network the star topology is
used and it is called the physical topology and but if the same communication
channels is used for the connection of the nodes in the star topology the logical
topology is defined as bus.
WRitten ASSESSMENT TEMPLATE - PAGE 4
Assignment Question:
There are two other LANs at GAMPS office, one for the main office (called ADMIN)
and one for the admissions gate (called GATE). There are 5 workstations on each
LAN. On ADMIN, the workstations connect to a 100Mbps hub. On GATE, the
workstations connect to a 100Mbs switch with all ports operating in half-duplex mode.
If you connected your laptop to GATE, would it be subject to more, the same or less
collisions than if it was connected to ADMIN? You can assume data rates and traffic
patterns are the same on each LAN. Justify your answer by explaining the origin of
the collisions.
Your answer:
The hubs are used as a multiport repeater and it is used for connecting multiple
nodes installed in the network. The hubs have limited capability and it cannot find the
best path for transferring the data packets for reducing wastage. The switch are used
for acting as a buffer and manage the network traffic without impacting on the
performance of the network. It have error checking and thus reduces errors in the
transmission of the data packets. It can be used for dividing the collision domain and
increase the efficiency of the network (Pluta, Stewart and Korson 2017). If a laptop is
connected with the GATE network then it would be subject to less collision because it
gets connected with the switch and the switch is efficient for management of the
traffic in the network and reduces collision to a large extend than the hubs which
broadcast the network packets causing wastage of the resources.
Your question:
Compare and contrast the physical and the logical network topology.
Your sample answer:
The physical topology is used for the demonstration of the communication channels
used for communication such as the workstations and the network cables. It consists
of the physical network structure while in case of logical network topology, the logics
used such as the protocol, IP addressing scheme, VLANs are used for demonstration
(Pluta, Stewart and Korson 2017). E.g. For a Local area network the star topology is
used and it is called the physical topology and but if the same communication
channels is used for the connection of the nodes in the star topology the logical
topology is defined as bus.
WRitten ASSESSMENT TEMPLATE - PAGE 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week Four
Assignment Question:
What are two benefits of fibre-optic cabling over wireless networks?
Your answer:
The two benefits identified over the wireless networks are listed below:
It is faster than the wireless radio signals because the data are transmitted in
the fibre optics cable in the speed of the light but in the wireless network the
data is transferred in the speed of the radio signals (Kizza 2017).
The fibre optics cable are not affected by the interference and it not possible
for the wireless network because when there are many devices emitting
wireless signals and it can operate in the same frequency causes distortion.
Your question:
What are the benefits and disadvantage of co-axial cables?
Your sample answer:
The advantages and disadvantage of the co axial cables are given below:
Advantages
The co axial cables can be applied for high frequency transmission because of
its tensile strength and less weight of the cable.
The shields of the co axial cable can reduce the attenuation and thus it is less
susceptible to noise when compared with the twisted pair cables.
Disadvantages
The installation of the co axial cables are difficult for its stiffness and thickness
for the long distance transmission
For the co axial cable a single cable is used for transmission of the data
packets and if it breaks it can cause failure for the whole network (Kizza
2017).
WRitten ASSESSMENT TEMPLATE - PAGE 5
Assignment Question:
What are two benefits of fibre-optic cabling over wireless networks?
Your answer:
The two benefits identified over the wireless networks are listed below:
It is faster than the wireless radio signals because the data are transmitted in
the fibre optics cable in the speed of the light but in the wireless network the
data is transferred in the speed of the radio signals (Kizza 2017).
The fibre optics cable are not affected by the interference and it not possible
for the wireless network because when there are many devices emitting
wireless signals and it can operate in the same frequency causes distortion.
Your question:
What are the benefits and disadvantage of co-axial cables?
Your sample answer:
The advantages and disadvantage of the co axial cables are given below:
Advantages
The co axial cables can be applied for high frequency transmission because of
its tensile strength and less weight of the cable.
The shields of the co axial cable can reduce the attenuation and thus it is less
susceptible to noise when compared with the twisted pair cables.
Disadvantages
The installation of the co axial cables are difficult for its stiffness and thickness
for the long distance transmission
For the co axial cable a single cable is used for transmission of the data
packets and if it breaks it can cause failure for the whole network (Kizza
2017).
WRitten ASSESSMENT TEMPLATE - PAGE 5

Week Five
Assignment Question:
When you turn on a computer, it “knows” its MAC address. What type of address
does it need to receive messages from the Internet and how does it get this address?
Your answer:
For connecting with the internet an IP address is required which is used for sending
and receiving messages. The IP address can be static or dynamic provided by the
ISP (internet service provider) or allocated using a DHCP server. The dynamic IP
address is used in private networks and suitable protocols are used for mapping the
MAC address with the IP address or vice versa (Levin and Schmidt 2014). The MAC
address are used for identification of the nodes connected in the network.
Your question:
“A MAC address have multiple IP address”. Explain
Your sample answer:
There may be more than one IP address associated with a MAC address and this
may occurs for the servers or if the computer is connected with more than one
network. For both of the network the IP address would be different but since they are
connected to a computer node the MAC address would not change. In case of the
server it can be used for providing more than one service and thus for each of the
service different IP address are used but the Mac address remain the same (Levin
and Schmidt 2014). The server roles can be transferred from one IP address to
another and can improve the scalability of the network.
WRitten ASSESSMENT TEMPLATE - PAGE 6
Assignment Question:
When you turn on a computer, it “knows” its MAC address. What type of address
does it need to receive messages from the Internet and how does it get this address?
Your answer:
For connecting with the internet an IP address is required which is used for sending
and receiving messages. The IP address can be static or dynamic provided by the
ISP (internet service provider) or allocated using a DHCP server. The dynamic IP
address is used in private networks and suitable protocols are used for mapping the
MAC address with the IP address or vice versa (Levin and Schmidt 2014). The MAC
address are used for identification of the nodes connected in the network.
Your question:
“A MAC address have multiple IP address”. Explain
Your sample answer:
There may be more than one IP address associated with a MAC address and this
may occurs for the servers or if the computer is connected with more than one
network. For both of the network the IP address would be different but since they are
connected to a computer node the MAC address would not change. In case of the
server it can be used for providing more than one service and thus for each of the
service different IP address are used but the Mac address remain the same (Levin
and Schmidt 2014). The server roles can be transferred from one IP address to
another and can improve the scalability of the network.
WRitten ASSESSMENT TEMPLATE - PAGE 6
You're viewing a preview
Unlock full access by subscribing today!

Week Six
Assignment Question:
Explain how it is that IPv4 and IPv6 can co-exist on the same networks and describe
two technologies that enable this.
Your answer:
The two technologies that can be applied for co-existing the IPv4 and the IPv6
address at the same network are given below:
NAT64 and
Dual Stacking
NAT64 – It is used for the translation of the IPv6 network into Ipv4 without changing
the current network infrastructure
Dual Stacking – It is a device used for translating the Ipv4 address into Ipv6 such
that the Ipv4 network can understand the Ipv6 packets and enable communication
between the Ipv4 and the Ipv6 network (Dao et al. 2015).
Your question:
Explain the working of the Ipv6 firewalls
Your sample answer:
The firewall configured with Ipv6 address works similar to the firewall configured with
the Ipv4 addressing scheme. There are many firewall devices that are compatible
with Ipv6 and it should be tested for meeting the gold standards and working of the
firewall depends on the rules set on the firewall for blocking the unknown sources
and secure the network from unauthorised access (Dao et al. 2015).
WRitten ASSESSMENT TEMPLATE - PAGE 7
Assignment Question:
Explain how it is that IPv4 and IPv6 can co-exist on the same networks and describe
two technologies that enable this.
Your answer:
The two technologies that can be applied for co-existing the IPv4 and the IPv6
address at the same network are given below:
NAT64 and
Dual Stacking
NAT64 – It is used for the translation of the IPv6 network into Ipv4 without changing
the current network infrastructure
Dual Stacking – It is a device used for translating the Ipv4 address into Ipv6 such
that the Ipv4 network can understand the Ipv6 packets and enable communication
between the Ipv4 and the Ipv6 network (Dao et al. 2015).
Your question:
Explain the working of the Ipv6 firewalls
Your sample answer:
The firewall configured with Ipv6 address works similar to the firewall configured with
the Ipv4 addressing scheme. There are many firewall devices that are compatible
with Ipv6 and it should be tested for meeting the gold standards and working of the
firewall depends on the rules set on the firewall for blocking the unknown sources
and secure the network from unauthorised access (Dao et al. 2015).
WRitten ASSESSMENT TEMPLATE - PAGE 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week Seven
Assignment Question:
A switching table has the following entries:
MAC Address Port #
00-25-2A-00-00-0F 4
00-25-2A-00-10-FC 1
00-25-2A-00-00-
DD
2
00-25-2A-00-11-21 3
Port 3 is connected to a hub.
During your testing, the following events occur:
1. The entry for 00-25-2A-00-10-FC expires.
2. An addition device (00-25-2A-00-10-00) is connected to the hub on port 3.
3. A new virtualised machine (00-25-2A-AA-10-0C) is started on the server
connected to port 2
4. Device (00-25-2A-00-10-00) is disconnected from the hub on port 3 and
connected to port 5.
Draw the switching table that you’d expect to see at the end of these events. The
order of entries is unimportant:
Your answer:
MAC Address Port #
00-25-2A-00-00-0F 4
00-25-2A-00-00-DD 2
00-25-2A-AA-10-
0C
2
00-25-2A-00-10-00 5
Your question:
The MAC address can be used for identification of the IP address of a computer.
Explain how?
Your sample answer:
With the application of the address resolution protocol the MAC address of a node
connected in the network can be found. The IP address is converted into the MAC
address using the ARP protocol and it works in the layer 2 Open Systems
Interconnection model (Silberschatz, Galvin and Gagne 2014). An ARP cache table
WRitten ASSESSMENT TEMPLATE - PAGE 8
Assignment Question:
A switching table has the following entries:
MAC Address Port #
00-25-2A-00-00-0F 4
00-25-2A-00-10-FC 1
00-25-2A-00-00-
DD
2
00-25-2A-00-11-21 3
Port 3 is connected to a hub.
During your testing, the following events occur:
1. The entry for 00-25-2A-00-10-FC expires.
2. An addition device (00-25-2A-00-10-00) is connected to the hub on port 3.
3. A new virtualised machine (00-25-2A-AA-10-0C) is started on the server
connected to port 2
4. Device (00-25-2A-00-10-00) is disconnected from the hub on port 3 and
connected to port 5.
Draw the switching table that you’d expect to see at the end of these events. The
order of entries is unimportant:
Your answer:
MAC Address Port #
00-25-2A-00-00-0F 4
00-25-2A-00-00-DD 2
00-25-2A-AA-10-
0C
2
00-25-2A-00-10-00 5
Your question:
The MAC address can be used for identification of the IP address of a computer.
Explain how?
Your sample answer:
With the application of the address resolution protocol the MAC address of a node
connected in the network can be found. The IP address is converted into the MAC
address using the ARP protocol and it works in the layer 2 Open Systems
Interconnection model (Silberschatz, Galvin and Gagne 2014). An ARP cache table
WRitten ASSESSMENT TEMPLATE - PAGE 8

is used for correlating the physical address and the IP address of the device and thus
it can be used for getting the MAC address of the device from the corresponding IP
address.
WRitten ASSESSMENT TEMPLATE - PAGE 9
it can be used for getting the MAC address of the device from the corresponding IP
address.
WRitten ASSESSMENT TEMPLATE - PAGE 9
You're viewing a preview
Unlock full access by subscribing today!

Week Eight
Assignment Question:
Describe how multiple processes can appear to be run simultaneously on a
computer.
Your answer:
The multiple process can run in the computer at the same time utilizing the
multitasking option in the operating system. Different methodology is applied for
handling multiple tasks at a time such as time slicing and context stitching. In time
slicing the CPU time cycles are divided among the process running. The context
stitching is utilized for transferring the control to the other process. In the multi-
tasking environment an operational overhead is used and the CPU cycles are utilized
efficiently. Pre-emptive and co-operative techniques are used. In the pre-emptive
technique each of the process are controlled for allocating a time slot for the
availability of the CPU (Coronel and Morris 2016). The co-operative technique works
by allocating the cpu to a process until it has finished its job.
Your question:
What is the difference between multiprogramming and multiprocessing?
Your sample answer:
Multiprocessing and multiprogramming differs from each other and given below:
Multiprocessing –
It is used for processing more than one number of request at a time.
Multiple CPUs are used for processing the request in parallel such that each
of the request are completed in less time.
It is expensive when compared with the multiprogramming environment.
Multiprogramming-
Single CPU is used and the programs are stored in the main memory for
executing concurrently(Silberschatz, Galvin and Gagne 2014).
Context switching applied for switching between the programs stored in the
memory
It is less expensive compared to the multi-processing environment.
WRitten ASSESSMENT TEMPLATE - PAGE 10
Assignment Question:
Describe how multiple processes can appear to be run simultaneously on a
computer.
Your answer:
The multiple process can run in the computer at the same time utilizing the
multitasking option in the operating system. Different methodology is applied for
handling multiple tasks at a time such as time slicing and context stitching. In time
slicing the CPU time cycles are divided among the process running. The context
stitching is utilized for transferring the control to the other process. In the multi-
tasking environment an operational overhead is used and the CPU cycles are utilized
efficiently. Pre-emptive and co-operative techniques are used. In the pre-emptive
technique each of the process are controlled for allocating a time slot for the
availability of the CPU (Coronel and Morris 2016). The co-operative technique works
by allocating the cpu to a process until it has finished its job.
Your question:
What is the difference between multiprogramming and multiprocessing?
Your sample answer:
Multiprocessing and multiprogramming differs from each other and given below:
Multiprocessing –
It is used for processing more than one number of request at a time.
Multiple CPUs are used for processing the request in parallel such that each
of the request are completed in less time.
It is expensive when compared with the multiprogramming environment.
Multiprogramming-
Single CPU is used and the programs are stored in the main memory for
executing concurrently(Silberschatz, Galvin and Gagne 2014).
Context switching applied for switching between the programs stored in the
memory
It is less expensive compared to the multi-processing environment.
WRitten ASSESSMENT TEMPLATE - PAGE 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week Nine
Assignment Question:
You have a 32GB USB stick. You are going to store an 8GB database file on the
drive. The database file contains sensitive information. What file system should you
format the drive with? Why?
Your answer:
For storing the 8 GB database file on a 32 GB USB stick the drive must be formatted
to NTFS format for the following reasons:
It does not limits the data and supports for transferring large files.
The files are tracked using the b-tree directory scheme and it does not uses
governing table as the FAT for storing the file information, instead it uses a
cluster.
The files are secured because an access control list is used for the files and
directories.
It also supports active directory for establishment of permission for accessing
the database file containing sensitive information (Coronel and Morris 2016).
It have integrated file compression for saving the space on the disk.
Your question:
Define ReFS
Your sample answer:
ReFs (Resilient File Systems) – It is developed by Microsoft and was introduced with
the Windows Server 2012 for resolving the issues that are associated with the NTFS
file system. There has been a change in the requirement of storage and is used for
data integrity checking, protecting the data from degradation and hard drive failure.
The ReFs was introduced for automatically handling the problems associated with
the hard drives and it have self-repairing property such as check disk, disk
defragmentation, etc. Some of the features present in NTFS are removed such as
compression, encryption, etc. and increases the reliability of the physical and the
logical disks (Coronel and Morris 2016).
WRitten ASSESSMENT TEMPLATE - PAGE 11
Assignment Question:
You have a 32GB USB stick. You are going to store an 8GB database file on the
drive. The database file contains sensitive information. What file system should you
format the drive with? Why?
Your answer:
For storing the 8 GB database file on a 32 GB USB stick the drive must be formatted
to NTFS format for the following reasons:
It does not limits the data and supports for transferring large files.
The files are tracked using the b-tree directory scheme and it does not uses
governing table as the FAT for storing the file information, instead it uses a
cluster.
The files are secured because an access control list is used for the files and
directories.
It also supports active directory for establishment of permission for accessing
the database file containing sensitive information (Coronel and Morris 2016).
It have integrated file compression for saving the space on the disk.
Your question:
Define ReFS
Your sample answer:
ReFs (Resilient File Systems) – It is developed by Microsoft and was introduced with
the Windows Server 2012 for resolving the issues that are associated with the NTFS
file system. There has been a change in the requirement of storage and is used for
data integrity checking, protecting the data from degradation and hard drive failure.
The ReFs was introduced for automatically handling the problems associated with
the hard drives and it have self-repairing property such as check disk, disk
defragmentation, etc. Some of the features present in NTFS are removed such as
compression, encryption, etc. and increases the reliability of the physical and the
logical disks (Coronel and Morris 2016).
WRitten ASSESSMENT TEMPLATE - PAGE 11

Week Ten
Assignment Question:
Firewalls can be effective against worms, but are generally of no use for viruses.
Why is this? You may need to do some additional research to answer this.
.
Your answer:
The firewalls are installed in the network as a physical hardware device used for
analysing the data packets in the network and take effective decision such as
allowing or dropping the data packets depending on the rules set on the firewall. The
firewall rules can be set depending on the IP address of the source and destination
the protocols used for communication. The firewall cannot be used for checking
malicious codes because it is designed for filtering the network traffic (Mahapatra et
al. 2017). By filtering the network traffic the firewall can prevent worms coming from
unknown networks but the virus can enter into the system from different sources
such as portable storage devices, attachment files, etc. Thus firewall are not effective
against viruses.
Your question:
What is the difference between the intrusion detection system and firewall?
Your sample answer:
The firewall is installed in a network for prevention of the unauthorised access by
filtering the data traffic in the network. The intrusion detection system is software and
hardware that is used for the detection of the intrusion and report against the attempt.
The firewall can be used for blocking an unauthorised connection but the IDS cannot
block any connection. The packets are sent and received in the network are checked
against the rules set in the firewall and if it not matches the packets are dropped
while in case of IDS the data flow pattern are analysed and an alert is sent to the
network administrator for detection of the unusual pattern(Mahapatra et al. 2017).
WRitten ASSESSMENT TEMPLATE - PAGE 12
Assignment Question:
Firewalls can be effective against worms, but are generally of no use for viruses.
Why is this? You may need to do some additional research to answer this.
.
Your answer:
The firewalls are installed in the network as a physical hardware device used for
analysing the data packets in the network and take effective decision such as
allowing or dropping the data packets depending on the rules set on the firewall. The
firewall rules can be set depending on the IP address of the source and destination
the protocols used for communication. The firewall cannot be used for checking
malicious codes because it is designed for filtering the network traffic (Mahapatra et
al. 2017). By filtering the network traffic the firewall can prevent worms coming from
unknown networks but the virus can enter into the system from different sources
such as portable storage devices, attachment files, etc. Thus firewall are not effective
against viruses.
Your question:
What is the difference between the intrusion detection system and firewall?
Your sample answer:
The firewall is installed in a network for prevention of the unauthorised access by
filtering the data traffic in the network. The intrusion detection system is software and
hardware that is used for the detection of the intrusion and report against the attempt.
The firewall can be used for blocking an unauthorised connection but the IDS cannot
block any connection. The packets are sent and received in the network are checked
against the rules set in the firewall and if it not matches the packets are dropped
while in case of IDS the data flow pattern are analysed and an alert is sent to the
network administrator for detection of the unusual pattern(Mahapatra et al. 2017).
WRitten ASSESSMENT TEMPLATE - PAGE 12
You're viewing a preview
Unlock full access by subscribing today!

References
Borzovs, J., Ilziņa, I., Keiša, I., Pinnis, M. and Vasiļjevs, A., 2014. Terminology
localization guidelines for the national scenario.
Coronel, C. and Morris, S., 2016. Database systems: design, implementation, &
management. Cengage Learning.
Dao, N.N., Park, J., Park, M. and Cho, S., 2015, January. A feasible method to
combat against DDoS attack in SDN network. In Information Networking (ICOIN),
2015 International Conference on (pp. 309-311). IEEE.
Kizza, J.M., 2017. Guide to computer network security. Springer.
Levin, S.L. and Schmidt, S., 2014. IPv4 to IPv6: Challenges, solutions, and lessons.
Telecommunications Policy, 38(11), pp.1059-1068.
Mahapatra, N., Nanda, S., Kaur, G. and Pradhan, B., 2017. Unit-7 Data Security and
Management.
Pluta, S., Stewart, R.J. and Korson, J.L., 2017. Radio over fibre technology for
shipboard antenna links. Journal of Marine Engineering & Technology, pp.1-12.
Silberschatz, A., Galvin, P.B. and Gagne, G., 2014. Operating system concepts
essentials. John Wiley & Sons, Inc..
Stüber, G.L., 2017. Principles of mobile communication (Vol. 3). Springer.
Zhang, H., Chu, X., Guo, W. and Wang, S., 2015. Coexistence of Wi-Fi and
heterogeneous small cell networks sharing unlicensed spectrum. IEEE
Communications Magazine, 53(3), pp.158-164.
WRitten ASSESSMENT TEMPLATE - PAGE 13
Borzovs, J., Ilziņa, I., Keiša, I., Pinnis, M. and Vasiļjevs, A., 2014. Terminology
localization guidelines for the national scenario.
Coronel, C. and Morris, S., 2016. Database systems: design, implementation, &
management. Cengage Learning.
Dao, N.N., Park, J., Park, M. and Cho, S., 2015, January. A feasible method to
combat against DDoS attack in SDN network. In Information Networking (ICOIN),
2015 International Conference on (pp. 309-311). IEEE.
Kizza, J.M., 2017. Guide to computer network security. Springer.
Levin, S.L. and Schmidt, S., 2014. IPv4 to IPv6: Challenges, solutions, and lessons.
Telecommunications Policy, 38(11), pp.1059-1068.
Mahapatra, N., Nanda, S., Kaur, G. and Pradhan, B., 2017. Unit-7 Data Security and
Management.
Pluta, S., Stewart, R.J. and Korson, J.L., 2017. Radio over fibre technology for
shipboard antenna links. Journal of Marine Engineering & Technology, pp.1-12.
Silberschatz, A., Galvin, P.B. and Gagne, G., 2014. Operating system concepts
essentials. John Wiley & Sons, Inc..
Stüber, G.L., 2017. Principles of mobile communication (Vol. 3). Springer.
Zhang, H., Chu, X., Guo, W. and Wang, S., 2015. Coexistence of Wi-Fi and
heterogeneous small cell networks sharing unlicensed spectrum. IEEE
Communications Magazine, 53(3), pp.158-164.
WRitten ASSESSMENT TEMPLATE - PAGE 13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
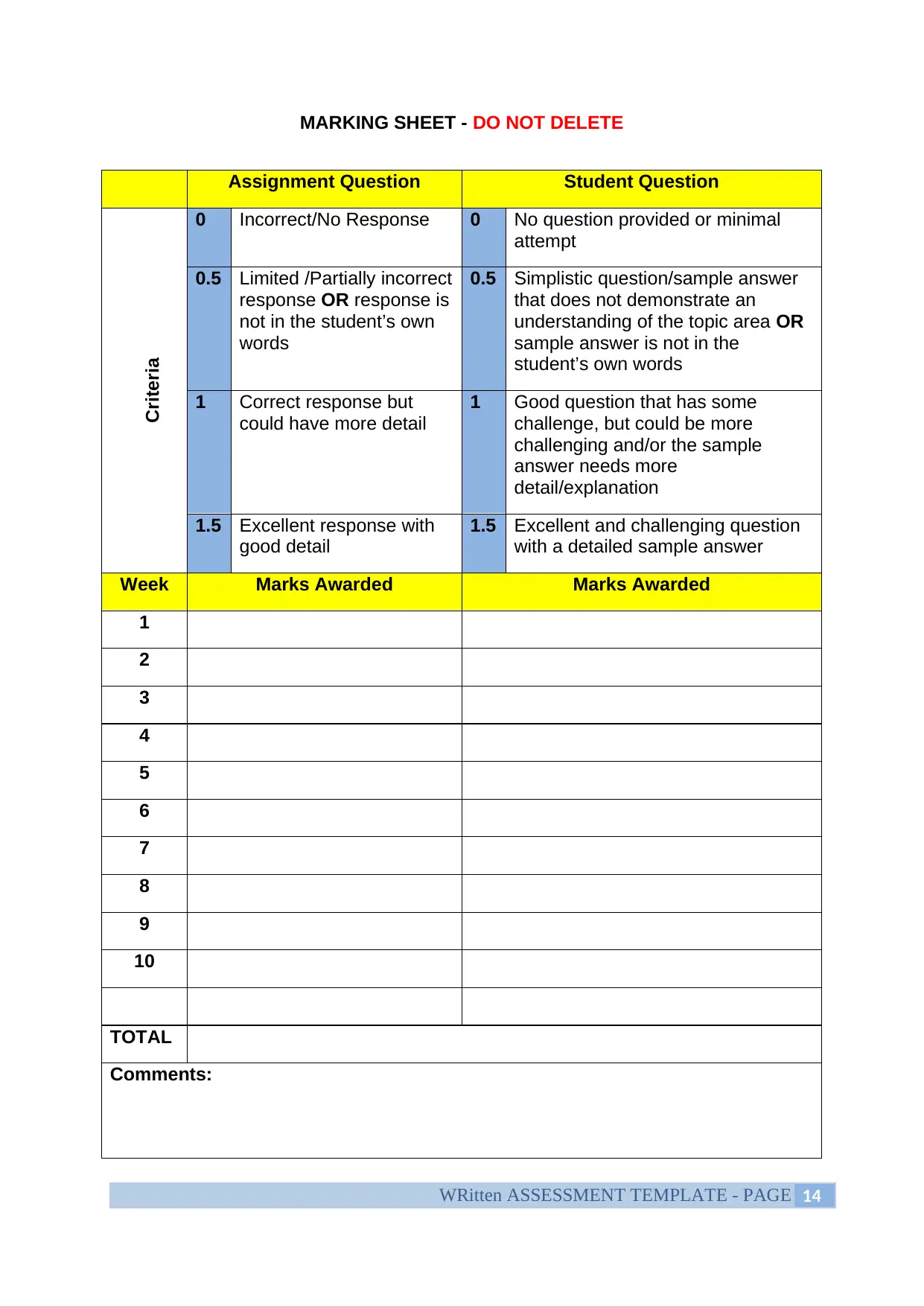
MARKING SHEET - DO NOT DELETE
Assignment Question Student Question
Criteria
0 Incorrect/No Response 0 No question provided or minimal
attempt
0.5 Limited /Partially incorrect
response OR response is
not in the student’s own
words
0.5 Simplistic question/sample answer
that does not demonstrate an
understanding of the topic area OR
sample answer is not in the
student’s own words
1 Correct response but
could have more detail
1 Good question that has some
challenge, but could be more
challenging and/or the sample
answer needs more
detail/explanation
1.5 Excellent response with
good detail
1.5 Excellent and challenging question
with a detailed sample answer
Week Marks Awarded Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
WRitten ASSESSMENT TEMPLATE - PAGE 14
Assignment Question Student Question
Criteria
0 Incorrect/No Response 0 No question provided or minimal
attempt
0.5 Limited /Partially incorrect
response OR response is
not in the student’s own
words
0.5 Simplistic question/sample answer
that does not demonstrate an
understanding of the topic area OR
sample answer is not in the
student’s own words
1 Correct response but
could have more detail
1 Good question that has some
challenge, but could be more
challenging and/or the sample
answer needs more
detail/explanation
1.5 Excellent response with
good detail
1.5 Excellent and challenging question
with a detailed sample answer
Week Marks Awarded Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
WRitten ASSESSMENT TEMPLATE - PAGE 14
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.


