Packet Capture and Analysis
VerifiedAdded on 2022/11/29
|7
|1576
|364
AI Summary
This document provides information about packet capture and analysis for COIT20262 Assignment 1 Submission in the Advanced Network Security course. It includes details about message sequence chart, information from packets, encryption implementation, modification attack, replay attack, and more.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
COIT20262 Assignment 1 Submission Term 1, 2019
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 1 Submission
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 1 Submission
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
COIT20262 Assignment 1 Submission Term 1, 2019
Question 1. Packet Capture and Analysis
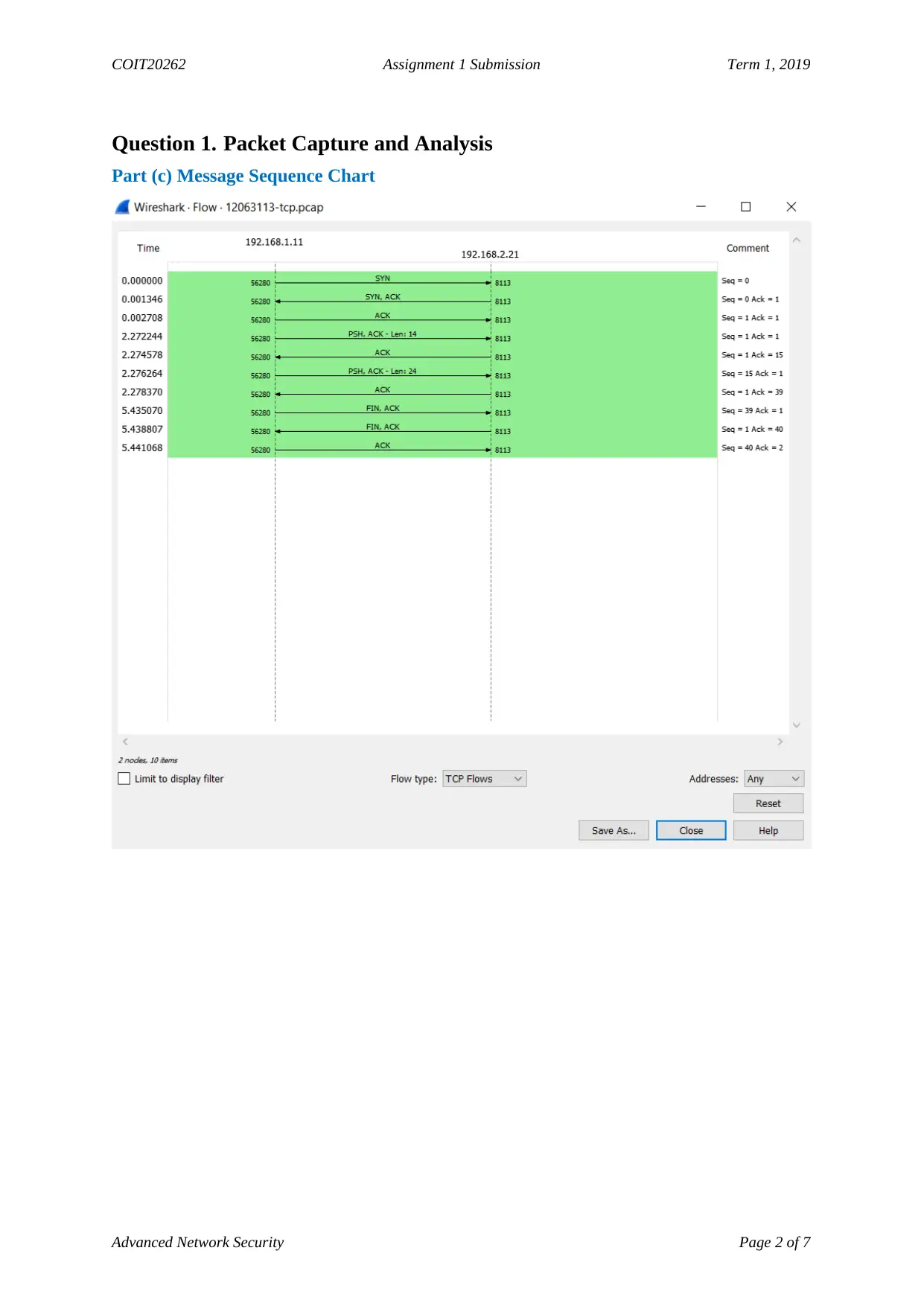
Part (c) Message Sequence Chart
Advanced Network Security Page 2 of 7
Question 1. Packet Capture and Analysis
Part (c) Message Sequence Chart
Advanced Network Security Page 2 of 7
COIT20262 Assignment 1 Submission Term 1, 2019
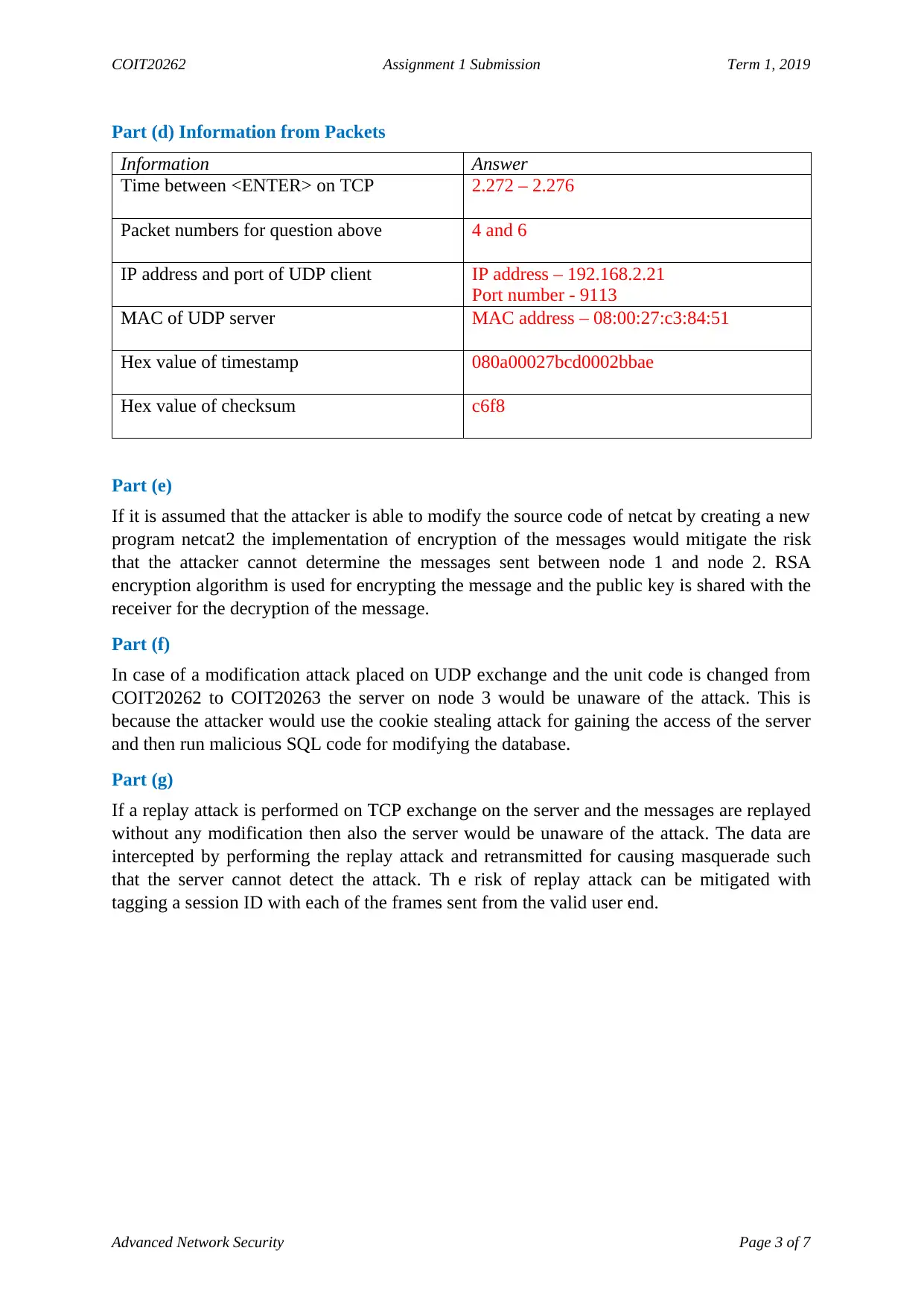
Part (d) Information from Packets
Information Answer
Time between <ENTER> on TCP 2.272 – 2.276
Packet numbers for question above 4 and 6
IP address and port of UDP client IP address – 192.168.2.21
Port number - 9113
MAC of UDP server MAC address – 08:00:27:c3:84:51
Hex value of timestamp 080a00027bcd0002bbae
Hex value of checksum c6f8
Part (e)
If it is assumed that the attacker is able to modify the source code of netcat by creating a new
program netcat2 the implementation of encryption of the messages would mitigate the risk
that the attacker cannot determine the messages sent between node 1 and node 2. RSA
encryption algorithm is used for encrypting the message and the public key is shared with the
receiver for the decryption of the message.
Part (f)
In case of a modification attack placed on UDP exchange and the unit code is changed from
COIT20262 to COIT20263 the server on node 3 would be unaware of the attack. This is
because the attacker would use the cookie stealing attack for gaining the access of the server
and then run malicious SQL code for modifying the database.
Part (g)
If a replay attack is performed on TCP exchange on the server and the messages are replayed
without any modification then also the server would be unaware of the attack. The data are
intercepted by performing the replay attack and retransmitted for causing masquerade such
that the server cannot detect the attack. Th e risk of replay attack can be mitigated with
tagging a session ID with each of the frames sent from the valid user end.
Advanced Network Security Page 3 of 7
Part (d) Information from Packets
Information Answer
Time between <ENTER> on TCP 2.272 – 2.276
Packet numbers for question above 4 and 6
IP address and port of UDP client IP address – 192.168.2.21
Port number - 9113
MAC of UDP server MAC address – 08:00:27:c3:84:51
Hex value of timestamp 080a00027bcd0002bbae
Hex value of checksum c6f8
Part (e)
If it is assumed that the attacker is able to modify the source code of netcat by creating a new
program netcat2 the implementation of encryption of the messages would mitigate the risk
that the attacker cannot determine the messages sent between node 1 and node 2. RSA
encryption algorithm is used for encrypting the message and the public key is shared with the
receiver for the decryption of the message.
Part (f)
In case of a modification attack placed on UDP exchange and the unit code is changed from
COIT20262 to COIT20263 the server on node 3 would be unaware of the attack. This is
because the attacker would use the cookie stealing attack for gaining the access of the server
and then run malicious SQL code for modifying the database.
Part (g)
If a replay attack is performed on TCP exchange on the server and the messages are replayed
without any modification then also the server would be unaware of the attack. The data are
intercepted by performing the replay attack and retransmitted for causing masquerade such
that the server cannot detect the attack. Th e risk of replay attack can be mitigated with
tagging a session ID with each of the frames sent from the valid user end.
Advanced Network Security Page 3 of 7

COIT20262 Assignment 1 Submission Term 1, 2019
Question 2. Cryptography
Part (c)
In this case the identified methods for the distribution of the public keys are the Moodle
forum and the email attachment. Public keys can be distributed among peoples through the
email by sending the key as an attachment. In the case of the Moodle forum it will be posted
right there and the peoples with the proper credentials can download the key. Here email uses
the authentication process for the secure communication and for protecting the private key.
Authentication is beneficial for securing the messages between two parties from external
threats but it does not provide security among sender and receiver about their message related
security which can lead to forgery and denial. The Moodle also uses the simple authentication
process which does not provide enough security for exchanging the public keys. The possible
attacks which can be done in this case is known message attack and the key conformation
attack.
Part (d)
In this case the digital signature can be leveraged for successfully distributing the public keys
through the Moodle website. The digital signature is secured more compared with the normal
authentication process as it provides both the authentication and the encryption. Here for
posting the private key to the Moodle forum the private key must be encrypted properly so
that the private key does not become accessible to all the users who have access to the
Moodle forum. Also, when the receiver is getting the private key it must be verified that
he/she has received the key so that no forgery and denial can occur and it can be achieved
through the digital signature. For a proper encryption the signature must follow a bit pattern
that depends on the signed message.
Part (e)
The security mechanism of the digital signature is very much advanced compared with the
authentication process. The digital signature is more reliable as it uses both the method of
encryption and authentication and for decrypting a file decryption key is required. Also the
digital signature can preserve the authenticity of the files. Due to this properties the digital
signature can resist various of intercepting attack which includes Man in the Middle Attack.
The digital signature does not have any type of self-protection as this keys can be stolen
easily and can be used without any permission of original author.
Advanced Network Security Page 4 of 7
Question 2. Cryptography
Part (c)
In this case the identified methods for the distribution of the public keys are the Moodle
forum and the email attachment. Public keys can be distributed among peoples through the
email by sending the key as an attachment. In the case of the Moodle forum it will be posted
right there and the peoples with the proper credentials can download the key. Here email uses
the authentication process for the secure communication and for protecting the private key.
Authentication is beneficial for securing the messages between two parties from external
threats but it does not provide security among sender and receiver about their message related
security which can lead to forgery and denial. The Moodle also uses the simple authentication
process which does not provide enough security for exchanging the public keys. The possible
attacks which can be done in this case is known message attack and the key conformation
attack.
Part (d)
In this case the digital signature can be leveraged for successfully distributing the public keys
through the Moodle website. The digital signature is secured more compared with the normal
authentication process as it provides both the authentication and the encryption. Here for
posting the private key to the Moodle forum the private key must be encrypted properly so
that the private key does not become accessible to all the users who have access to the
Moodle forum. Also, when the receiver is getting the private key it must be verified that
he/she has received the key so that no forgery and denial can occur and it can be achieved
through the digital signature. For a proper encryption the signature must follow a bit pattern
that depends on the signed message.
Part (e)
The security mechanism of the digital signature is very much advanced compared with the
authentication process. The digital signature is more reliable as it uses both the method of
encryption and authentication and for decrypting a file decryption key is required. Also the
digital signature can preserve the authenticity of the files. Due to this properties the digital
signature can resist various of intercepting attack which includes Man in the Middle Attack.
The digital signature does not have any type of self-protection as this keys can be stolen
easily and can be used without any permission of original author.
Advanced Network Security Page 4 of 7
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

COIT20262 Assignment 1 Submission Term 1, 2019
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
DoS Attack: The Denial of Service attack (DoS) is a typical type of network attack which
can easily hamper normal system execution process of a particular system. The services of a
particular system becomes inaccessible whenever this attack is performed on that system. To
perform this attack numerous number of data packets are directly sent to the system which
reduces the performance of the system slowly and then it stops all the services completely.
DDoS Attack: The method of performing Distributed Denial of Service attack is very much
similar with the DoS attack but here Trojans are used instead of data packets.
Difference in Attack: The main difference between the attack done on the server resources
and the attack done on the network resources is that for the attack network resource attack
this done individually and for that the network security is compromised. Due to the attack
that is done on the server resource, it exhausts the processing power of the system create
chances for the DDoS attack.
Entities in DDoS Attacks
Ping Flooding Attack
Ping flooding attack or the ICMP attack is considered as a part of the DDoS attack. Here for
executing the attack numerous requests of ICMP echo is send directly to the computer which
lowers the performance of the system and the system becomes unstable.
For the ping flooding attack this is done overloading system using a ping which is
also considered as the ICMP echo. This is the reason that the system lost its stability and due
to that security mechanism of the systems also goes lower which creates potential
vulnerability. Here the IP address plays an important role as the attacker needs to know the IP
address of the attacker for performing this attack as without knowing the IP address the
attacker will not be able to send a high amount pings to the victim. Also, it is important to
Advanced Network Security Page 5 of 7
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
DoS Attack: The Denial of Service attack (DoS) is a typical type of network attack which
can easily hamper normal system execution process of a particular system. The services of a
particular system becomes inaccessible whenever this attack is performed on that system. To
perform this attack numerous number of data packets are directly sent to the system which
reduces the performance of the system slowly and then it stops all the services completely.
DDoS Attack: The method of performing Distributed Denial of Service attack is very much
similar with the DoS attack but here Trojans are used instead of data packets.
Difference in Attack: The main difference between the attack done on the server resources
and the attack done on the network resources is that for the attack network resource attack
this done individually and for that the network security is compromised. Due to the attack
that is done on the server resource, it exhausts the processing power of the system create
chances for the DDoS attack.
Entities in DDoS Attacks
Ping Flooding Attack
Ping flooding attack or the ICMP attack is considered as a part of the DDoS attack. Here for
executing the attack numerous requests of ICMP echo is send directly to the computer which
lowers the performance of the system and the system becomes unstable.
For the ping flooding attack this is done overloading system using a ping which is
also considered as the ICMP echo. This is the reason that the system lost its stability and due
to that security mechanism of the systems also goes lower which creates potential
vulnerability. Here the IP address plays an important role as the attacker needs to know the IP
address of the attacker for performing this attack as without knowing the IP address the
attacker will not be able to send a high amount pings to the victim. Also, it is important to
Advanced Network Security Page 5 of 7

COIT20262 Assignment 1 Submission Term 1, 2019
execute the attack in a proper sequence and for that appropriate ping command need to be
executed by the attacker. Also, the attacker have to make sure that he/she possessing more
bandwidth compared with bandwidth of victim.
Mitigating Ping Flooding Attack
Cloudfare software can be used to stop the ping flooding attack and this software is very
much essential for stopping the ping flooding. Firewall also plays an important role for
stopping the attack. By using the firewall, unnecessary pings coming from the outside of the
network can be blocked efficiently thus the ping flooding attack can be minimised with great
effectiveness.
Advanced Network Security Page 6 of 7
execute the attack in a proper sequence and for that appropriate ping command need to be
executed by the attacker. Also, the attacker have to make sure that he/she possessing more
bandwidth compared with bandwidth of victim.
Mitigating Ping Flooding Attack
Cloudfare software can be used to stop the ping flooding attack and this software is very
much essential for stopping the ping flooding. Firewall also plays an important role for
stopping the attack. By using the firewall, unnecessary pings coming from the outside of the
network can be blocked efficiently thus the ping flooding attack can be minimised with great
effectiveness.
Advanced Network Security Page 6 of 7

COIT20262 Assignment 1 Submission Term 1, 2019
Bibliography:
Gupta, R. K. (2018). Mitigating Distributed-Denial of Service (DDoS) attacks in Software-
Defined Networking (SDN)(Doctoral dissertation).
Jaber, A. N., Zolkipli, M. F., Majid, M. A., & Anwar, S. (2017). Methods for Preventing
Distributed Denial of Service Attacks in Cloud Computing. Advanced Science Letters, 23(6),
5282-5285.
Kapur, R. K., Khatri, S. K., & Patnaik, L. M. (2018). Optimised elliptic curve digital
signature on NIST compliant curves for authentication of MANET nodes. International
Journal of Electronic Security and Digital Forensics, 10(4), 372-387.
Luo, S., Wu, J., Li, J., & Pei, B. (2015, August). A defense mechanism for distributed denial
of service attack in software-defined networks. In 2015 Ninth International Conference on
Frontier of Computer Science and Technology (pp. 325-329). IEEE.
Meti, N., Narayan, D. G., & Baligar, V. P. (2017, September). Detection of distributed denial
of service attacks using machine learning algorithms in software defined networks. In 2017
International Conference on Advances in Computing, Communications and Informatics
(ICACCI) (pp. 1366-1371). IEEE.
Shi, Y., Liang, J., Han, J., Gao, J., Xiong, G., & Fan, H. (2018, May). Intrusion-Resilient
Undetachable Digital Signature for Mobile-Agent-Based Collaborative Business Systems.
In 2018 IEEE 22nd International Conference on Computer Supported Cooperative Work in
Design ((CSCWD)) (pp. 401-406). IEEE.
Zhang, X., Yang, S., & Liu, Y. (2017). Integrated digital signature scheme research for the
hospital electronic medical record system. China Medical Equipment, 14(2), 97-99.
Advanced Network Security Page 7 of 7
Bibliography:
Gupta, R. K. (2018). Mitigating Distributed-Denial of Service (DDoS) attacks in Software-
Defined Networking (SDN)(Doctoral dissertation).
Jaber, A. N., Zolkipli, M. F., Majid, M. A., & Anwar, S. (2017). Methods for Preventing
Distributed Denial of Service Attacks in Cloud Computing. Advanced Science Letters, 23(6),
5282-5285.
Kapur, R. K., Khatri, S. K., & Patnaik, L. M. (2018). Optimised elliptic curve digital
signature on NIST compliant curves for authentication of MANET nodes. International
Journal of Electronic Security and Digital Forensics, 10(4), 372-387.
Luo, S., Wu, J., Li, J., & Pei, B. (2015, August). A defense mechanism for distributed denial
of service attack in software-defined networks. In 2015 Ninth International Conference on
Frontier of Computer Science and Technology (pp. 325-329). IEEE.
Meti, N., Narayan, D. G., & Baligar, V. P. (2017, September). Detection of distributed denial
of service attacks using machine learning algorithms in software defined networks. In 2017
International Conference on Advances in Computing, Communications and Informatics
(ICACCI) (pp. 1366-1371). IEEE.
Shi, Y., Liang, J., Han, J., Gao, J., Xiong, G., & Fan, H. (2018, May). Intrusion-Resilient
Undetachable Digital Signature for Mobile-Agent-Based Collaborative Business Systems.
In 2018 IEEE 22nd International Conference on Computer Supported Cooperative Work in
Design ((CSCWD)) (pp. 401-406). IEEE.
Zhang, X., Yang, S., & Liu, Y. (2017). Integrated digital signature scheme research for the
hospital electronic medical record system. China Medical Equipment, 14(2), 97-99.
Advanced Network Security Page 7 of 7
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





