Advanced Network Security Assignment 2022
VerifiedAdded on 2022/09/15
|9
|2776
|42
Assignment
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
COIT20262 Assignment 1 Submission Term 2, 2019
COIT20262 - Advanced Network Security, Term 2, 2019
Assignment 1 Submission
Due date: 10am Monday 26 August 2019
(Week 6)
ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: 12085235
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 9
COIT20262 - Advanced Network Security, Term 2, 2019
Assignment 1 Submission
Due date: 10am Monday 26 August 2019
(Week 6)
ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: 12085235
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

COIT20262 Assignment 1 Submission Term 2, 2019
Question 1. Packet Capture and Analysis
Part (d) Message Sequence Chart
Advanced Network Security Page 2 of 9
Question 1. Packet Capture and Analysis
Part (d) Message Sequence Chart
Advanced Network Security Page 2 of 9
COIT20262 Assignment 1 Submission Term 2, 2019
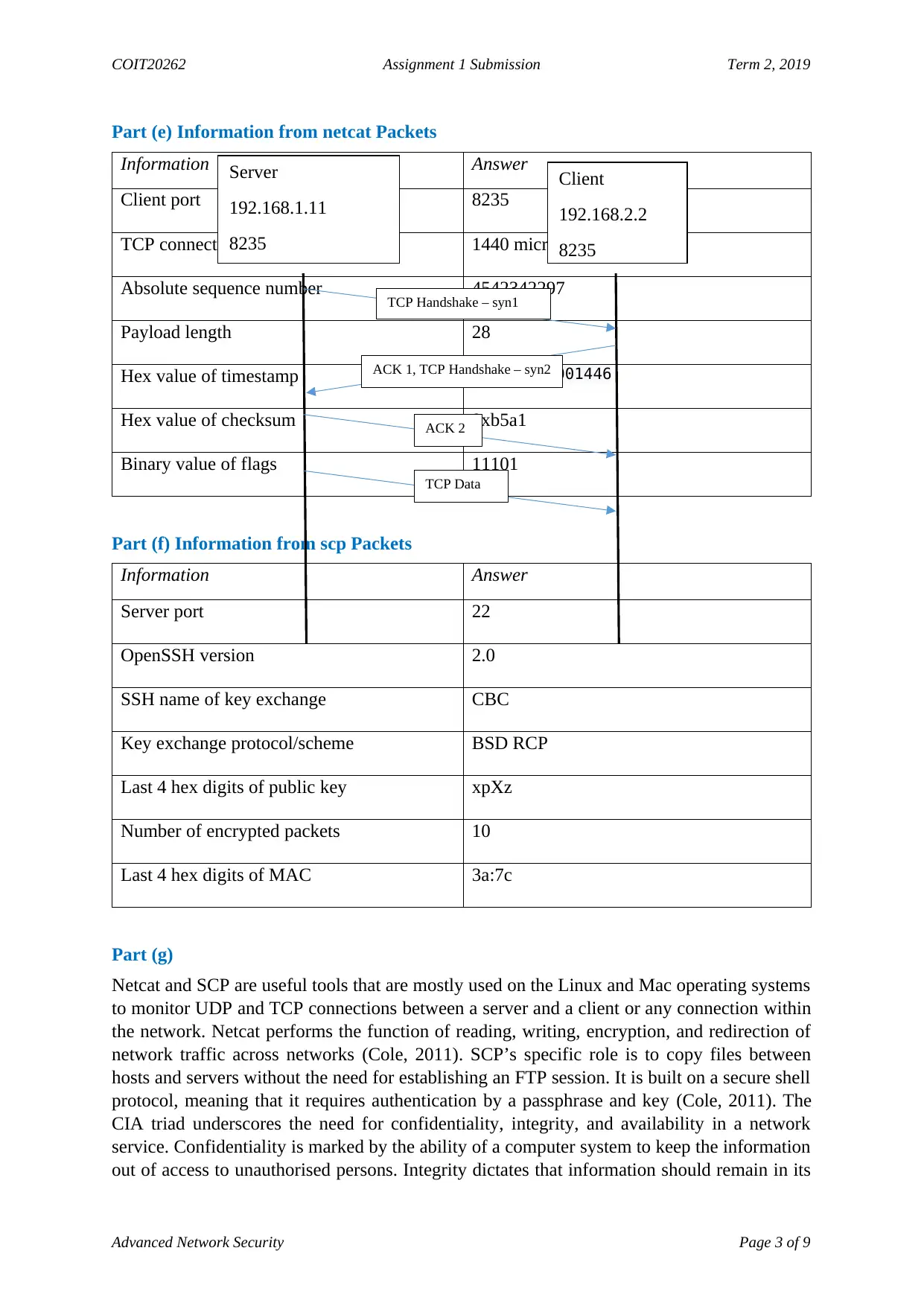
Part (e) Information from netcat Packets
Information Answer
Client port 8235
TCP connection duration 1440 microseconds
Absolute sequence number 4542342297
Payload length 28
Hex value of timestamp 00:00:00.001446
Hex value of checksum 0xb5a1
Binary value of flags 11101
Part (f) Information from scp Packets
Information Answer
Server port 22
OpenSSH version 2.0
SSH name of key exchange CBC
Key exchange protocol/scheme BSD RCP
Last 4 hex digits of public key xpXz
Number of encrypted packets 10
Last 4 hex digits of MAC 3a:7c
Part (g)
Netcat and SCP are useful tools that are mostly used on the Linux and Mac operating systems
to monitor UDP and TCP connections between a server and a client or any connection within
the network. Netcat performs the function of reading, writing, encryption, and redirection of
network traffic across networks (Cole, 2011). SCP’s specific role is to copy files between
hosts and servers without the need for establishing an FTP session. It is built on a secure shell
protocol, meaning that it requires authentication by a passphrase and key (Cole, 2011). The
CIA triad underscores the need for confidentiality, integrity, and availability in a network
service. Confidentiality is marked by the ability of a computer system to keep the information
out of access to unauthorised persons. Integrity dictates that information should remain in its
Advanced Network Security Page 3 of 9
Server
192.168.1.11
8235
Client
192.168.2.2
8235
TCP Handshake – syn1
ACK 1, TCP Handshake – syn2
ACK 2
TCP Data
Part (e) Information from netcat Packets
Information Answer
Client port 8235
TCP connection duration 1440 microseconds
Absolute sequence number 4542342297
Payload length 28
Hex value of timestamp 00:00:00.001446
Hex value of checksum 0xb5a1
Binary value of flags 11101
Part (f) Information from scp Packets
Information Answer
Server port 22
OpenSSH version 2.0
SSH name of key exchange CBC
Key exchange protocol/scheme BSD RCP
Last 4 hex digits of public key xpXz
Number of encrypted packets 10
Last 4 hex digits of MAC 3a:7c
Part (g)
Netcat and SCP are useful tools that are mostly used on the Linux and Mac operating systems
to monitor UDP and TCP connections between a server and a client or any connection within
the network. Netcat performs the function of reading, writing, encryption, and redirection of
network traffic across networks (Cole, 2011). SCP’s specific role is to copy files between
hosts and servers without the need for establishing an FTP session. It is built on a secure shell
protocol, meaning that it requires authentication by a passphrase and key (Cole, 2011). The
CIA triad underscores the need for confidentiality, integrity, and availability in a network
service. Confidentiality is marked by the ability of a computer system to keep the information
out of access to unauthorised persons. Integrity dictates that information should remain in its
Advanced Network Security Page 3 of 9
Server
192.168.1.11
8235
Client
192.168.2.2
8235
TCP Handshake – syn1
ACK 1, TCP Handshake – syn2
ACK 2
TCP Data

COIT20262 Assignment 1 Submission Term 2, 2019
original form throughout the transmission channel and in storage. A network that is
characterised by high availability is one that restricts access to unauthorized users but allows
maximum rights to access at high speeds to intended personnel. The read and write rules may
vary from one user to another. Netcat allows users to access, modify, and redirect not only
the packets flowing within the network, but also files hosted on the remote servers or hosts.
While it us a powerful tool in the right hands that could allow for SSH level access to
information on a remote server, it could be fatal if accessed by black hat hackers as they
could use it to modify system files or write executable scripts on the bash shell, which initiate
an encryption or deletion sequence. SCP, having been built on top of SSH, isolates the
functions of different levels of users by their roles (Nestler, et al., 2014). It allows for the
copying of files but restricts deletion or modification. Therefore, the number of packets
flowing between the host and server or host to another host is higher in netcat than it is when
one uses SCP. Netcat offers a bare-bone approach to server management and is faster. On the
other hand, SCP, built on shell, is relatively slower. Both protocols are useful depending on
the nature of the task at hand.
Part (h)
ChaCha20 is a relatively new encryption algorithm that borrows the base architecture from
the AES model. It is significantly lighter and works optimally in devices with both restricted
and unrestricted access to powerful hardware resources. It utilizes the addition-rotation-xor
operation in its core functions. The AES encryption algorithm applies a binary scheme in its
computational operations, which require more processing compared to the ChaCha20’s
model. Therefore, the former is slower compared to the latter, especially when the hardware
resource is limited. Moreover, due to the amount of parallel computation that is required,
caching memory is required to store the preprocessed sections of code. The amount of work
required to perform cryptography using ChaCha20 is less compared to the AES standard, and
is thus, more preferable.
Advanced Network Security Page 4 of 9
original form throughout the transmission channel and in storage. A network that is
characterised by high availability is one that restricts access to unauthorized users but allows
maximum rights to access at high speeds to intended personnel. The read and write rules may
vary from one user to another. Netcat allows users to access, modify, and redirect not only
the packets flowing within the network, but also files hosted on the remote servers or hosts.
While it us a powerful tool in the right hands that could allow for SSH level access to
information on a remote server, it could be fatal if accessed by black hat hackers as they
could use it to modify system files or write executable scripts on the bash shell, which initiate
an encryption or deletion sequence. SCP, having been built on top of SSH, isolates the
functions of different levels of users by their roles (Nestler, et al., 2014). It allows for the
copying of files but restricts deletion or modification. Therefore, the number of packets
flowing between the host and server or host to another host is higher in netcat than it is when
one uses SCP. Netcat offers a bare-bone approach to server management and is faster. On the
other hand, SCP, built on shell, is relatively slower. Both protocols are useful depending on
the nature of the task at hand.
Part (h)
ChaCha20 is a relatively new encryption algorithm that borrows the base architecture from
the AES model. It is significantly lighter and works optimally in devices with both restricted
and unrestricted access to powerful hardware resources. It utilizes the addition-rotation-xor
operation in its core functions. The AES encryption algorithm applies a binary scheme in its
computational operations, which require more processing compared to the ChaCha20’s
model. Therefore, the former is slower compared to the latter, especially when the hardware
resource is limited. Moreover, due to the amount of parallel computation that is required,
caching memory is required to store the preprocessed sections of code. The amount of work
required to perform cryptography using ChaCha20 is less compared to the AES standard, and
is thus, more preferable.
Advanced Network Security Page 4 of 9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

COIT20262 Assignment 1 Submission Term 2, 2019
Question 1. Cryptography
Part (c)
The demands of information systems security dictate that the information stored by an
electronic system should maintain its confidentiality, availability, and integrity as stipulated
by principles behind the CIA triad. Communication requires that information be moved from
one point to another in a manner that is highly available to the authorized individuals. In
order to satisfy the requirements of both information security and communication principles,
it a system administrator has to enable the sharing of information in a manner that does not
compromise its confidentiality while allowing for maximum speeds and convenience, only to
people allowed to view them. Methods such as end-to-end encryption, which are schemes
provided under cryptographic approaches to concealing private information. Different
methods have been devised, which have their respective strengths and weaknesses. A
cryptographic method is supposed to use a message block to produce a hashed block that is
transmitted and deciphered using an agreed upon process that is known to the sender and
recipient. Some methods a re computationally expensive while others are simple but have
known flows. In order to leverage the advantages of each in different scenarios, a system
administrator should evaluate the tasks and apply the most suitable cryptographic method.
Part (d)
The SHA256, AES, and RSA have been used in phase 2 of this section to encrypt the
messages sent between the sender and receiver. They are cryptographic technologies with
robust privacy provisions that have been deemed safe to use over the years. The MD5
algorithm, introduced in the early 1990s by Ronald Rivest, who also contributed to the
development of the RSA algorithm is a widely adopted mechanism of encrypting files shared
on the Internet (Vacca, 2009). Some of the widely known applications include the end-to-end
encryption of website traffic that is applied to most of the FTP websites around the world.
Widely used frameworks such as CodeIgniter, written in PHP and some of the security
hashing technologies in React and Angular platforms utilize the MD5 algorithm. While it
works for the most part, it has been proven to be insecure in certain cases where highly
sensitive information is involved. It has a vulnerability that enables a hacker to attack the
system during transfer of packets, intercept and modify the messages and obtain the same
digest as the original message, which means that no intrusion can be noticed on the receiver’s
end. This feature allows for serious security breaches such as session stealing and digital
certificate forgery which are ingredients of spoofing attempts. In application at phase 2, it is
not possible to know whether a particular implementation of MD5 will be compromised at
the time of encryption, and may allow third-party individuals to view the exchange of
information and modify it to suit his or her needs without being noticed for a long time.
Therefore, it is not a safe algorithm to replace those that are being used in the phase. MD6 is
available with better encryption standards and resolved conflict issues (Clarke, 2012).
Part (e)
A masquerade attack is a kind of attack launched by a hacker in which messages on transit to
the recipient are intercepted and re-sent in their modified or unmodified states to the receiver
later. Cryptographic algorithms that do not take into account the time stamps, duration of
sending messages are not sensitive to masquerade attacks (Aumasson, 2017). Therefore, a
Advanced Network Security Page 5 of 9
Question 1. Cryptography
Part (c)
The demands of information systems security dictate that the information stored by an
electronic system should maintain its confidentiality, availability, and integrity as stipulated
by principles behind the CIA triad. Communication requires that information be moved from
one point to another in a manner that is highly available to the authorized individuals. In
order to satisfy the requirements of both information security and communication principles,
it a system administrator has to enable the sharing of information in a manner that does not
compromise its confidentiality while allowing for maximum speeds and convenience, only to
people allowed to view them. Methods such as end-to-end encryption, which are schemes
provided under cryptographic approaches to concealing private information. Different
methods have been devised, which have their respective strengths and weaknesses. A
cryptographic method is supposed to use a message block to produce a hashed block that is
transmitted and deciphered using an agreed upon process that is known to the sender and
recipient. Some methods a re computationally expensive while others are simple but have
known flows. In order to leverage the advantages of each in different scenarios, a system
administrator should evaluate the tasks and apply the most suitable cryptographic method.
Part (d)
The SHA256, AES, and RSA have been used in phase 2 of this section to encrypt the
messages sent between the sender and receiver. They are cryptographic technologies with
robust privacy provisions that have been deemed safe to use over the years. The MD5
algorithm, introduced in the early 1990s by Ronald Rivest, who also contributed to the
development of the RSA algorithm is a widely adopted mechanism of encrypting files shared
on the Internet (Vacca, 2009). Some of the widely known applications include the end-to-end
encryption of website traffic that is applied to most of the FTP websites around the world.
Widely used frameworks such as CodeIgniter, written in PHP and some of the security
hashing technologies in React and Angular platforms utilize the MD5 algorithm. While it
works for the most part, it has been proven to be insecure in certain cases where highly
sensitive information is involved. It has a vulnerability that enables a hacker to attack the
system during transfer of packets, intercept and modify the messages and obtain the same
digest as the original message, which means that no intrusion can be noticed on the receiver’s
end. This feature allows for serious security breaches such as session stealing and digital
certificate forgery which are ingredients of spoofing attempts. In application at phase 2, it is
not possible to know whether a particular implementation of MD5 will be compromised at
the time of encryption, and may allow third-party individuals to view the exchange of
information and modify it to suit his or her needs without being noticed for a long time.
Therefore, it is not a safe algorithm to replace those that are being used in the phase. MD6 is
available with better encryption standards and resolved conflict issues (Clarke, 2012).
Part (e)
A masquerade attack is a kind of attack launched by a hacker in which messages on transit to
the recipient are intercepted and re-sent in their modified or unmodified states to the receiver
later. Cryptographic algorithms that do not take into account the time stamps, duration of
sending messages are not sensitive to masquerade attacks (Aumasson, 2017). Therefore, a
Advanced Network Security Page 5 of 9

COIT20262 Assignment 1 Submission Term 2, 2019
hacker may re-send a single message many times and the receiver systems may not notice the
difference. This kind of scenario may cause a DDoS attack leading to a further downgrade of
service. Also, the hacker may attach snippets of malicious code without causing the any
suspicion until a full attack is launched. It is also called a replay attack due to its nature of
operation.
Part (f)
The success of masquerade attacks results from the inability of a receiver system to recognize
and correlate the message content and the timestamp of reception. In other words, most
receiver systems in networks adopt a ‘dumb’ approach that only decrypts information without
having to inspect the content and correlate for timestamp approval. In order to prevent
masquerade attacks, intelligent network approaches have to be devised that not only decrypt
information but also inspect the payload for possible duplication that may cause a possible
DDoS attack. The implementation of firewalls with such capabilities is recommended
(Nestler, et al., 2014). The actions to be taken after the discovery of such illegal events may
be programmed for automatic deletion, automatic disconnection of the network, or temporary
blocking of associated IP addresses that are deemed to have been compromised. Moreover,
an escalation may be made to the concerned technical team who may decide to create a
honeypot to investigate the issue further or take legal action against potential attackers, if
their identities are unmasked (Vacca, 2009). The time stamp validation against the message
payload is the most effective method that allows for the prevention of such attacks.
Part (g)
The combination of an artificially intelligent firewall that learns trends in the reception of
payloads in correlation to the contents before and after decryption, coupled with the time
stamp approaches are ideal in the fight against masquerade attacks (Rankin, 2017). The
advantage of including artificial intelligence in the monitoring of network traffic is that the
system firewall learns about new patterns without human intervention in a progressive
manner and devises ways to either stop or escalate the issue. The utilization of the time stamp
information in the encryption and decryption of messages also enables the fixation of a
particular pattern block that is unique (Vacca, 2009). The repeated reception of the same
unique timestamp header block may be treated as being suspicious.
Advanced Network Security Page 6 of 9
hacker may re-send a single message many times and the receiver systems may not notice the
difference. This kind of scenario may cause a DDoS attack leading to a further downgrade of
service. Also, the hacker may attach snippets of malicious code without causing the any
suspicion until a full attack is launched. It is also called a replay attack due to its nature of
operation.
Part (f)
The success of masquerade attacks results from the inability of a receiver system to recognize
and correlate the message content and the timestamp of reception. In other words, most
receiver systems in networks adopt a ‘dumb’ approach that only decrypts information without
having to inspect the content and correlate for timestamp approval. In order to prevent
masquerade attacks, intelligent network approaches have to be devised that not only decrypt
information but also inspect the payload for possible duplication that may cause a possible
DDoS attack. The implementation of firewalls with such capabilities is recommended
(Nestler, et al., 2014). The actions to be taken after the discovery of such illegal events may
be programmed for automatic deletion, automatic disconnection of the network, or temporary
blocking of associated IP addresses that are deemed to have been compromised. Moreover,
an escalation may be made to the concerned technical team who may decide to create a
honeypot to investigate the issue further or take legal action against potential attackers, if
their identities are unmasked (Vacca, 2009). The time stamp validation against the message
payload is the most effective method that allows for the prevention of such attacks.
Part (g)
The combination of an artificially intelligent firewall that learns trends in the reception of
payloads in correlation to the contents before and after decryption, coupled with the time
stamp approaches are ideal in the fight against masquerade attacks (Rankin, 2017). The
advantage of including artificial intelligence in the monitoring of network traffic is that the
system firewall learns about new patterns without human intervention in a progressive
manner and devises ways to either stop or escalate the issue. The utilization of the time stamp
information in the encryption and decryption of messages also enables the fixation of a
particular pattern block that is unique (Vacca, 2009). The repeated reception of the same
unique timestamp header block may be treated as being suspicious.
Advanced Network Security Page 6 of 9

COIT20262 Assignment 1 Submission Term 2, 2019
Question 2. Malware Research
What is ransomware?
A ransomware attack is a kind of attack in which a hacker takes control of computer
resources belonging to a target firm or entity and demands payment in exchange for a
decryption service (Vacca, 2009). During the period of the loss of control, a business owner
or the legally charged entity loses access to the resource and is not able to implement core
functions of the business. It is executed by malware that is designed to automate encryption
and send the keys to the hacker. If the captured computing resources are core to the business
functions of a company, the decision to pay the ransom may be made depending on a number
of factors and the recommendations of an information security team.
Infection Methods
Malicious programs designed to lock out the normal functioning of an entity’s computer are
written and published by hackers on websites that serve free software that may be preferred
by businesses intending to cut costs of operation (Cole, 2011). They may also be sent by
hackers to emails of unsuspecting employees of a company, who may open images that
install malware automatically. In other cases, stolen cookie sessions online and illegal access
to network nodes may allow attackers to install the malware onto the system. The malware,
once added to the network, may spread from one node to another while performing
encryption and storing or uploading the decryption keys to the hacker’s server (Liska &
Gallo, 2016). A message from the attacker may be displayed on the computers or
communicated in another way to demand for payment or the fulfilment of other conditions in
exchange of service restoration.
Role of Cryptography
Ransomware attacks are enabled by encryption methods that exist. Active research in the
design of robust encryption methods to secure network systems also contribute to more ways
in which the network availability may be compromised by hackers with sophisticated skills.
Some of the ways in which a network or computer may be taken is through the use of the
asymmetric encryption in which a hacker generates a public and private keys on a target
computer and stores the key in a specified location whose address is accessible in a manner
known only the attacker (Ballad, et al., 2010). Once the ransom is paid, the decrypting
method is shared in an agreed way. A similar attack may be launched in which the private
keys are uploaded to a server owned by an attacker and resent to the business owner or victim
entity upon the honouring of the terms of the ransom. A hybrid method of encryption
involving both the host and host-server methods may be deployed to give full control of the
system to a hacker. All the methods have their respective advantages for the hacker and the
victim depending on the complexity of the hack.
Not Pay Ransom
The university may reject the ransom demands if it has an updated copy of all records of
information stored at a safe location. Also, if the attacked system is not crucial to the core
operation of the university, the systems could be repaired by performing fresh installation of
software to eliminate the problem and restore normal operation.
Advanced Network Security Page 7 of 9
Question 2. Malware Research
What is ransomware?
A ransomware attack is a kind of attack in which a hacker takes control of computer
resources belonging to a target firm or entity and demands payment in exchange for a
decryption service (Vacca, 2009). During the period of the loss of control, a business owner
or the legally charged entity loses access to the resource and is not able to implement core
functions of the business. It is executed by malware that is designed to automate encryption
and send the keys to the hacker. If the captured computing resources are core to the business
functions of a company, the decision to pay the ransom may be made depending on a number
of factors and the recommendations of an information security team.
Infection Methods
Malicious programs designed to lock out the normal functioning of an entity’s computer are
written and published by hackers on websites that serve free software that may be preferred
by businesses intending to cut costs of operation (Cole, 2011). They may also be sent by
hackers to emails of unsuspecting employees of a company, who may open images that
install malware automatically. In other cases, stolen cookie sessions online and illegal access
to network nodes may allow attackers to install the malware onto the system. The malware,
once added to the network, may spread from one node to another while performing
encryption and storing or uploading the decryption keys to the hacker’s server (Liska &
Gallo, 2016). A message from the attacker may be displayed on the computers or
communicated in another way to demand for payment or the fulfilment of other conditions in
exchange of service restoration.
Role of Cryptography
Ransomware attacks are enabled by encryption methods that exist. Active research in the
design of robust encryption methods to secure network systems also contribute to more ways
in which the network availability may be compromised by hackers with sophisticated skills.
Some of the ways in which a network or computer may be taken is through the use of the
asymmetric encryption in which a hacker generates a public and private keys on a target
computer and stores the key in a specified location whose address is accessible in a manner
known only the attacker (Ballad, et al., 2010). Once the ransom is paid, the decrypting
method is shared in an agreed way. A similar attack may be launched in which the private
keys are uploaded to a server owned by an attacker and resent to the business owner or victim
entity upon the honouring of the terms of the ransom. A hybrid method of encryption
involving both the host and host-server methods may be deployed to give full control of the
system to a hacker. All the methods have their respective advantages for the hacker and the
victim depending on the complexity of the hack.
Not Pay Ransom
The university may reject the ransom demands if it has an updated copy of all records of
information stored at a safe location. Also, if the attacked system is not crucial to the core
operation of the university, the systems could be repaired by performing fresh installation of
software to eliminate the problem and restore normal operation.
Advanced Network Security Page 7 of 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COIT20262 Assignment 1 Submission Term 2, 2019
Pay Ransom
If the attacked system is involved in the core operations of the university or company and its
availability is crucial, then the best decision is to honour the demands because delayed
services in reinstallation and backup attempts may disrupt normal services, thus driving
operations and profits down, whose cost may be irrecoverable. The method of payment may
take place depending on the preferences of the attacker. The cryptocurrency is the most
preferred method because it eliminates the need for physical contact and the money is
untraceable in most cases.
Recommendations
Universities ought to have systems that prevent the occurrence of ransom attacks. One
method is to restrict installs in such a manner that only administrators can install software on
any node using a confidential passphrase or password (Rankin, 2017). Another approach is
through policy formation to inform the procedures and practices around the workplace for
employees while dealing with networked equipment (Vacca, 2009). Intelligent firewalls that
monitor bidirectional web traffic may help to block any attempts to take over computing
resources by hackers.
Advanced Network Security Page 8 of 9
Pay Ransom
If the attacked system is involved in the core operations of the university or company and its
availability is crucial, then the best decision is to honour the demands because delayed
services in reinstallation and backup attempts may disrupt normal services, thus driving
operations and profits down, whose cost may be irrecoverable. The method of payment may
take place depending on the preferences of the attacker. The cryptocurrency is the most
preferred method because it eliminates the need for physical contact and the money is
untraceable in most cases.
Recommendations
Universities ought to have systems that prevent the occurrence of ransom attacks. One
method is to restrict installs in such a manner that only administrators can install software on
any node using a confidential passphrase or password (Rankin, 2017). Another approach is
through policy formation to inform the procedures and practices around the workplace for
employees while dealing with networked equipment (Vacca, 2009). Intelligent firewalls that
monitor bidirectional web traffic may help to block any attempts to take over computing
resources by hackers.
Advanced Network Security Page 8 of 9

COIT20262 Assignment 1 Submission Term 2, 2019
References
Aumasson, J.-P., 2017. Serious Cryptography: A Practical Introduction to Modern
Encryption. s.l.:No Starch Press.
Ballad, B., Ballad, T. & Banks, E., 2010. Access Control, Authentication, and Public Key
Infrastructure. s.l.:Jones & Bartlett Publishers.
Clarke, J., 2012. SQL Injection Attacks and Defense. s.l.:Elsevier.
Cole, E., 2011. Network Security Bible. John Wiley & Sons: s.n.
Liska, A. & Gallo, T., 2016. Ransomware: Defending Against Digital Extortion. s.l.:O'Reilly
Media, Inc.
Nestler, V. J., Harrison, K., Hirsch, M. P. & Conklin, W. A., 2014. Principles of Computer
Security Lab Manual, Fourth Edition. s.l.:McGraw Hill Professional.
Rankin, K., 2017. Linux Hardening in Hostile Networks: Server Security from TLS to Tor.
s.l.:Professional, Addison-Wesley.
Vacca, J. R., 2009. Computer and Information Security Handbook. s.l.:Morgan Kaufmann.
Advanced Network Security Page 9 of 9
References
Aumasson, J.-P., 2017. Serious Cryptography: A Practical Introduction to Modern
Encryption. s.l.:No Starch Press.
Ballad, B., Ballad, T. & Banks, E., 2010. Access Control, Authentication, and Public Key
Infrastructure. s.l.:Jones & Bartlett Publishers.
Clarke, J., 2012. SQL Injection Attacks and Defense. s.l.:Elsevier.
Cole, E., 2011. Network Security Bible. John Wiley & Sons: s.n.
Liska, A. & Gallo, T., 2016. Ransomware: Defending Against Digital Extortion. s.l.:O'Reilly
Media, Inc.
Nestler, V. J., Harrison, K., Hirsch, M. P. & Conklin, W. A., 2014. Principles of Computer
Security Lab Manual, Fourth Edition. s.l.:McGraw Hill Professional.
Rankin, K., 2017. Linux Hardening in Hostile Networks: Server Security from TLS to Tor.
s.l.:Professional, Addison-Wesley.
Vacca, J. R., 2009. Computer and Information Security Handbook. s.l.:Morgan Kaufmann.
Advanced Network Security Page 9 of 9
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





