COIT20262: Advanced Network Security Assignment 1, Term 1, 2019
VerifiedAdded on 2023/02/01
|7
|1514
|20
Homework Assignment
AI Summary
This assignment solution for COIT20262, Advanced Network Security, covers several key areas of network security. The solution begins with packet capture and analysis, including message sequence charts and information extracted from packets, addressing vulnerabilities like man-in-the-middle atta...
COIT20262 Assignment 1 Submission Term 1, 2019
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 1 Submission
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 1 Submission
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 1 Submission Term 1, 2019
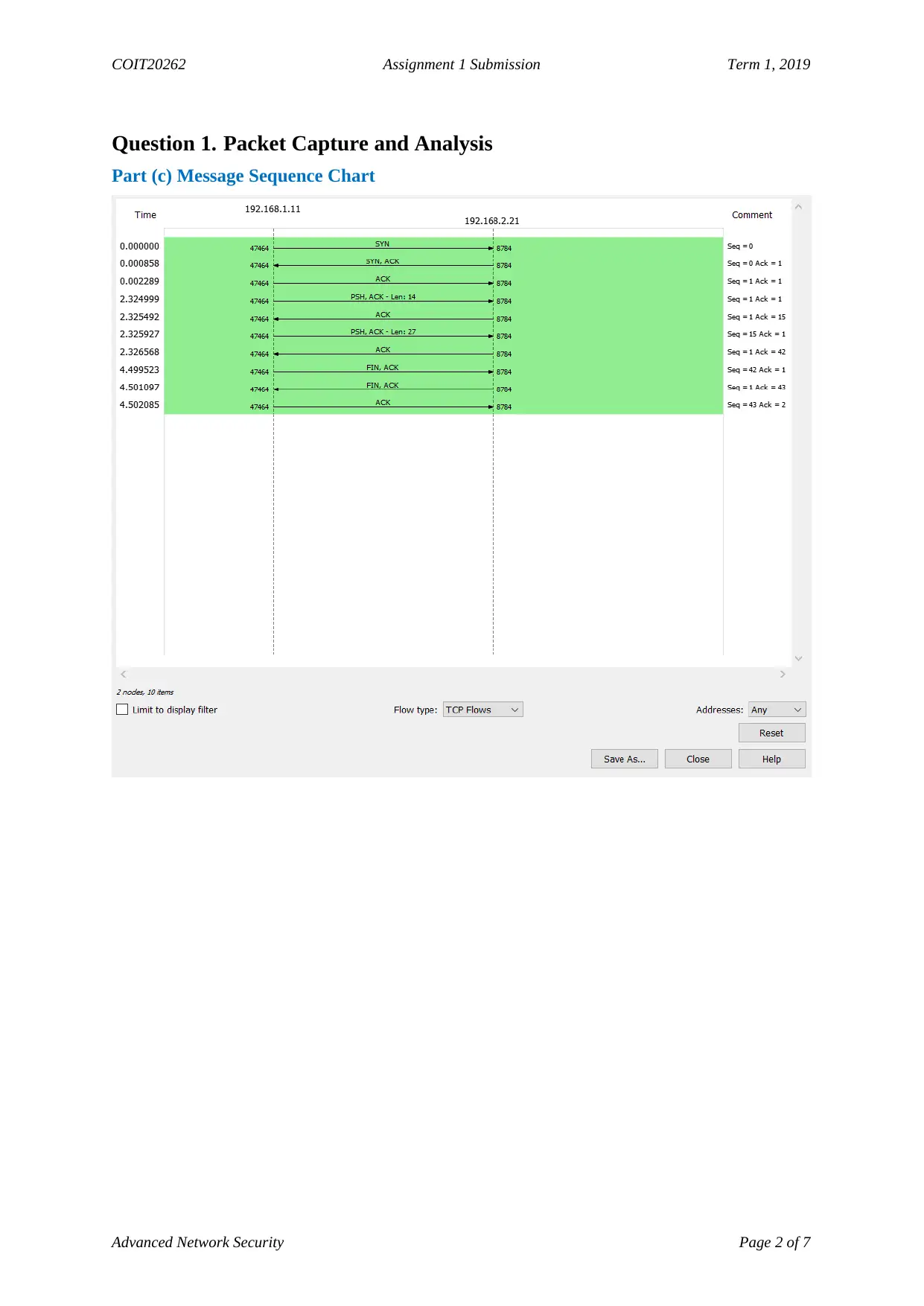
Question 1. Packet Capture and Analysis
Part (c) Message Sequence Chart
Advanced Network Security Page 2 of 7
Question 1. Packet Capture and Analysis
Part (c) Message Sequence Chart
Advanced Network Security Page 2 of 7
COIT20262 Assignment 1 Submission Term 1, 2019
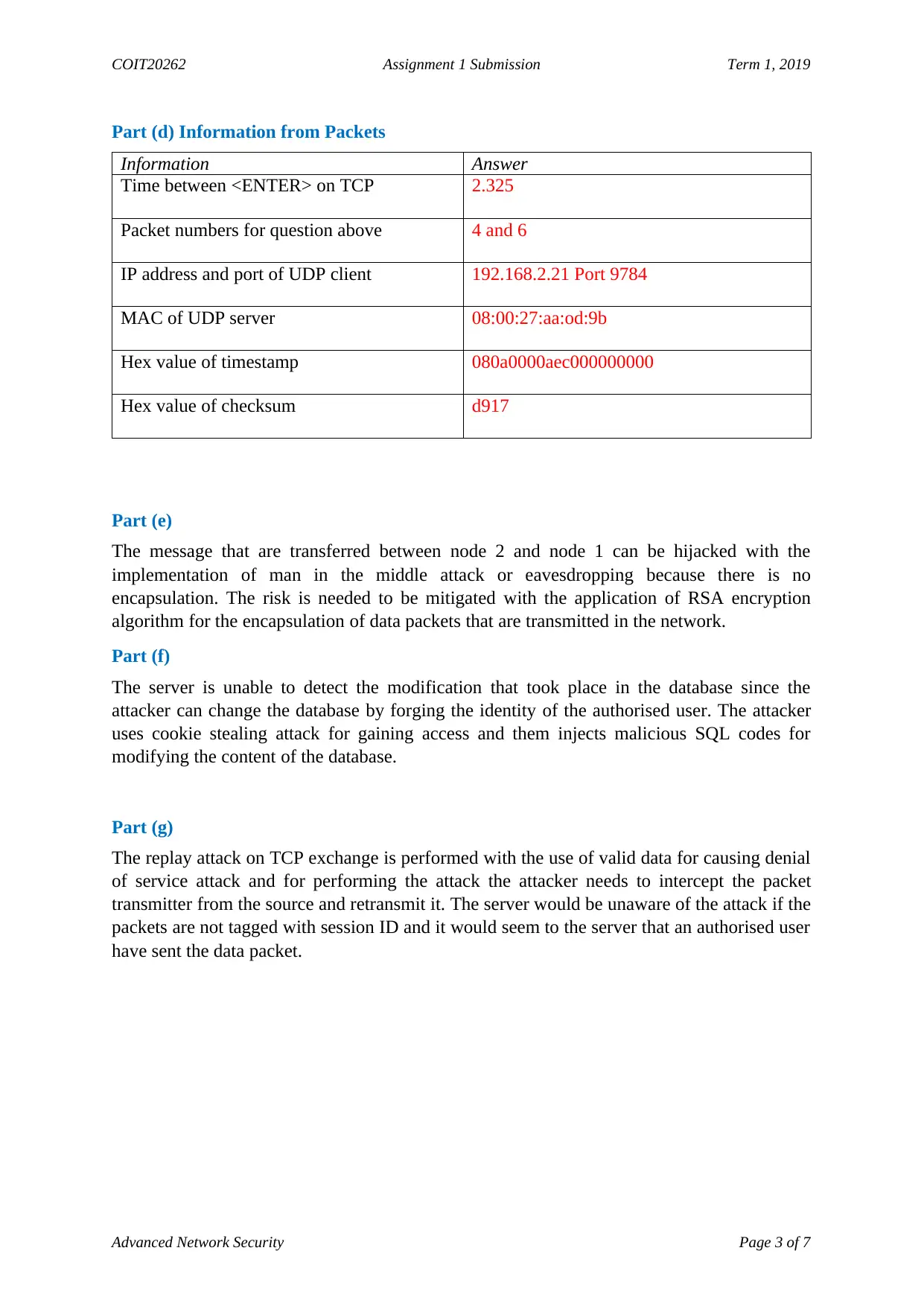
Part (d) Information from Packets
Information Answer
Time between <ENTER> on TCP 2.325
Packet numbers for question above 4 and 6
IP address and port of UDP client 192.168.2.21 Port 9784
MAC of UDP server 08:00:27:aa:od:9b
Hex value of timestamp 080a0000aec000000000
Hex value of checksum d917
Part (e)
The message that are transferred between node 2 and node 1 can be hijacked with the
implementation of man in the middle attack or eavesdropping because there is no
encapsulation. The risk is needed to be mitigated with the application of RSA encryption
algorithm for the encapsulation of data packets that are transmitted in the network.
Part (f)
The server is unable to detect the modification that took place in the database since the
attacker can change the database by forging the identity of the authorised user. The attacker
uses cookie stealing attack for gaining access and them injects malicious SQL codes for
modifying the content of the database.
Part (g)
The replay attack on TCP exchange is performed with the use of valid data for causing denial
of service attack and for performing the attack the attacker needs to intercept the packet
transmitter from the source and retransmit it. The server would be unaware of the attack if the
packets are not tagged with session ID and it would seem to the server that an authorised user
have sent the data packet.
Advanced Network Security Page 3 of 7
Part (d) Information from Packets
Information Answer
Time between <ENTER> on TCP 2.325
Packet numbers for question above 4 and 6
IP address and port of UDP client 192.168.2.21 Port 9784
MAC of UDP server 08:00:27:aa:od:9b
Hex value of timestamp 080a0000aec000000000
Hex value of checksum d917
Part (e)
The message that are transferred between node 2 and node 1 can be hijacked with the
implementation of man in the middle attack or eavesdropping because there is no
encapsulation. The risk is needed to be mitigated with the application of RSA encryption
algorithm for the encapsulation of data packets that are transmitted in the network.
Part (f)
The server is unable to detect the modification that took place in the database since the
attacker can change the database by forging the identity of the authorised user. The attacker
uses cookie stealing attack for gaining access and them injects malicious SQL codes for
modifying the content of the database.
Part (g)
The replay attack on TCP exchange is performed with the use of valid data for causing denial
of service attack and for performing the attack the attacker needs to intercept the packet
transmitter from the source and retransmit it. The server would be unaware of the attack if the
packets are not tagged with session ID and it would seem to the server that an authorised user
have sent the data packet.
Advanced Network Security Page 3 of 7
You're viewing a preview
Unlock full access by subscribing today!

COIT20262 Assignment 1 Submission Term 1, 2019
Question 2. Cryptography
Part (c)
Here the main two methods of distributing the public keys are distributing it through email or
posting it to the Moodle forum. The email uses authentication process for transferring the
public keys among the specific peoples. Authentication only protects the messages between
sender and receiver from the external threats, but there is no protection shield between sender
and the receiver which can lead to some potential threats of security such as forgery and
denial or receiving message. Considering the Moodle forum post, this is also vulnerable to
the security as hackers can hack any of the student id and can access the private key from
there. The possible attack in this case are the key conformation attack, known message attack
and the known message attack.
Part (d)
Here most efficient way for securely distributing the public key through the Moodle website
is the digital signature. The digital signature is more than the authentication process and it
includes both the authentication process and the encryption process. For the attaching the
public key to the forum some modification must be done on the public key. This public key
must be encrypted property. At the time of receiving the key, proper verification is also
needed so that it can be ensured that intended receiver has received the key successfully. The
main steps in this digital signature process is that the signature must be following a bit pattern
for every individual signature which is depending on signed message. After the distribution
there should be a local copy of that digital signature.
Part (e)
The security scheme of the digital signature is very much advanced than the normal
authentication as it provides the encryption over the authentication, thus the only way of
decrypting message is using decryption key. Due to this reason this is considered more
secured than the previous authentication process. As the digital signature is capable of
preserving authenticity of the resources it can effectively stop the man in the middle attack.
The main problem in this case that the digital signature can be stolen from the original owner
and can be used for decrypting the message unethically.
Advanced Network Security Page 4 of 7
Question 2. Cryptography
Part (c)
Here the main two methods of distributing the public keys are distributing it through email or
posting it to the Moodle forum. The email uses authentication process for transferring the
public keys among the specific peoples. Authentication only protects the messages between
sender and receiver from the external threats, but there is no protection shield between sender
and the receiver which can lead to some potential threats of security such as forgery and
denial or receiving message. Considering the Moodle forum post, this is also vulnerable to
the security as hackers can hack any of the student id and can access the private key from
there. The possible attack in this case are the key conformation attack, known message attack
and the known message attack.
Part (d)
Here most efficient way for securely distributing the public key through the Moodle website
is the digital signature. The digital signature is more than the authentication process and it
includes both the authentication process and the encryption process. For the attaching the
public key to the forum some modification must be done on the public key. This public key
must be encrypted property. At the time of receiving the key, proper verification is also
needed so that it can be ensured that intended receiver has received the key successfully. The
main steps in this digital signature process is that the signature must be following a bit pattern
for every individual signature which is depending on signed message. After the distribution
there should be a local copy of that digital signature.
Part (e)
The security scheme of the digital signature is very much advanced than the normal
authentication as it provides the encryption over the authentication, thus the only way of
decrypting message is using decryption key. Due to this reason this is considered more
secured than the previous authentication process. As the digital signature is capable of
preserving authenticity of the resources it can effectively stop the man in the middle attack.
The main problem in this case that the digital signature can be stolen from the original owner
and can be used for decrypting the message unethically.
Advanced Network Security Page 4 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 1 Submission Term 1, 2019
Question 3. Denial of Service Attack Research
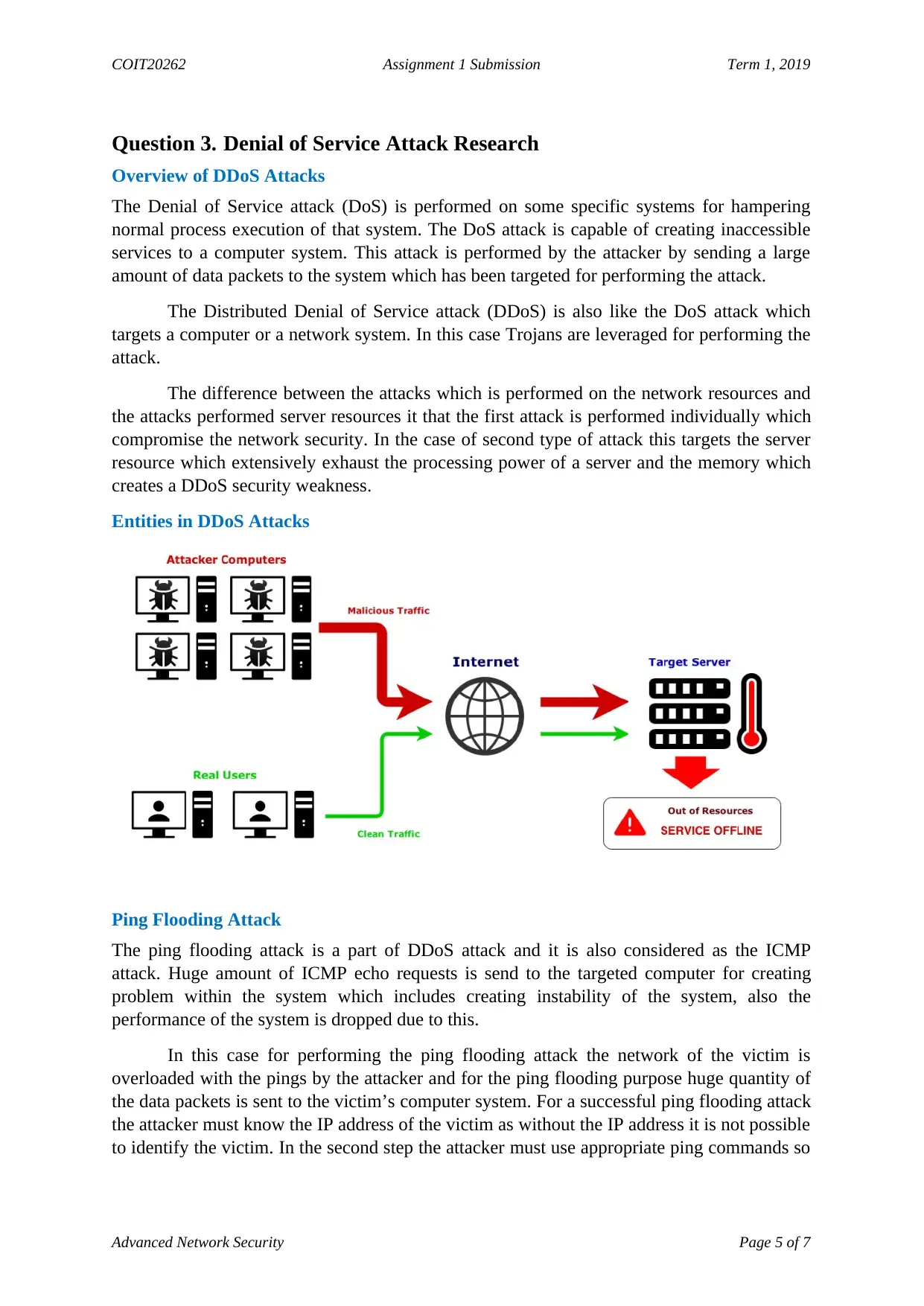
Overview of DDoS Attacks
The Denial of Service attack (DoS) is performed on some specific systems for hampering
normal process execution of that system. The DoS attack is capable of creating inaccessible
services to a computer system. This attack is performed by the attacker by sending a large
amount of data packets to the system which has been targeted for performing the attack.
The Distributed Denial of Service attack (DDoS) is also like the DoS attack which
targets a computer or a network system. In this case Trojans are leveraged for performing the
attack.
The difference between the attacks which is performed on the network resources and
the attacks performed server resources it that the first attack is performed individually which
compromise the network security. In the case of second type of attack this targets the server
resource which extensively exhaust the processing power of a server and the memory which
creates a DDoS security weakness.
Entities in DDoS Attacks
Ping Flooding Attack
The ping flooding attack is a part of DDoS attack and it is also considered as the ICMP
attack. Huge amount of ICMP echo requests is send to the targeted computer for creating
problem within the system which includes creating instability of the system, also the
performance of the system is dropped due to this.
In this case for performing the ping flooding attack the network of the victim is
overloaded with the pings by the attacker and for the ping flooding purpose huge quantity of
the data packets is sent to the victim’s computer system. For a successful ping flooding attack
the attacker must know the IP address of the victim as without the IP address it is not possible
to identify the victim. In the second step the attacker must use appropriate ping commands so
Advanced Network Security Page 5 of 7
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
The Denial of Service attack (DoS) is performed on some specific systems for hampering
normal process execution of that system. The DoS attack is capable of creating inaccessible
services to a computer system. This attack is performed by the attacker by sending a large
amount of data packets to the system which has been targeted for performing the attack.
The Distributed Denial of Service attack (DDoS) is also like the DoS attack which
targets a computer or a network system. In this case Trojans are leveraged for performing the
attack.
The difference between the attacks which is performed on the network resources and
the attacks performed server resources it that the first attack is performed individually which
compromise the network security. In the case of second type of attack this targets the server
resource which extensively exhaust the processing power of a server and the memory which
creates a DDoS security weakness.
Entities in DDoS Attacks
Ping Flooding Attack
The ping flooding attack is a part of DDoS attack and it is also considered as the ICMP
attack. Huge amount of ICMP echo requests is send to the targeted computer for creating
problem within the system which includes creating instability of the system, also the
performance of the system is dropped due to this.
In this case for performing the ping flooding attack the network of the victim is
overloaded with the pings by the attacker and for the ping flooding purpose huge quantity of
the data packets is sent to the victim’s computer system. For a successful ping flooding attack
the attacker must know the IP address of the victim as without the IP address it is not possible
to identify the victim. In the second step the attacker must use appropriate ping commands so
Advanced Network Security Page 5 of 7

COIT20262 Assignment 1 Submission Term 1, 2019
that the ping flooding attack can be executed. To ensure that the attack will be performed
without any type of disturbance the attacker need to have greater bandwidth from the victim.
Mitigating Ping Flooding Attack
To mitigate the ping flooding attack various types of software can be used. One example of
this type of software is the Cloudfare. Rather than the software, firewall of the system can be
also used in this case for performing the attack. In this case the perimeter of the firewall can
be reconfigured for disallowing the pings which are originating from an outside network.
This is an effective way of stopping the ping flooding attack.
Advanced Network Security Page 6 of 7
that the ping flooding attack can be executed. To ensure that the attack will be performed
without any type of disturbance the attacker need to have greater bandwidth from the victim.
Mitigating Ping Flooding Attack
To mitigate the ping flooding attack various types of software can be used. One example of
this type of software is the Cloudfare. Rather than the software, firewall of the system can be
also used in this case for performing the attack. In this case the perimeter of the firewall can
be reconfigured for disallowing the pings which are originating from an outside network.
This is an effective way of stopping the ping flooding attack.
Advanced Network Security Page 6 of 7
You're viewing a preview
Unlock full access by subscribing today!

COIT20262 Assignment 1 Submission Term 1, 2019
Bibliography:
Baishya, R. C., Hoque, N., & Bhattacharyya, D. K. (2017). DDoS Attack Detection Using
Unique Source IP Deviation. IJ Network Security, 19(6), 929-939.
Pham, T. N. D., Yeo, C. K., Yanai, N., & Fujiwara, T. (2018). Detecting flooding attack and
accommodating burst traffic in delay-tolerant networks. IEEE Transactions on
Vehicular Technology, 67(1), 795-808.
Kaur, P., Kumar, M., & Bhandari, A. (2017). A review of detection approaches for
distributed denial of service attacks. Systems Science & Control Engineering, 5(1),
301-320.
Phan, T. V., & Park, M. (2019). Efficient Distributed Denial-of-Service Attack Defense in
SDN-Based Cloud. IEEE Access, 7, 18701-18714.
Luo, S., Wu, J., Li, J., & Pei, B. (2015, August). A defense mechanism for distributed denial
of service attack in software-defined networks. In 2015 Ninth International
Conference on Frontier of Computer Science and Technology (pp. 325-329). IEEE.
Tian, Y., Tran, V., & Kuerban, M. (2019, January). DOS Attack Mitigation Strategies on
SDN Controller. In 2019 IEEE 9th Annual Computing and Communication Workshop
and Conference (CCWC) (pp. 0701-0707). IEEE.
Advanced Network Security Page 7 of 7
Bibliography:
Baishya, R. C., Hoque, N., & Bhattacharyya, D. K. (2017). DDoS Attack Detection Using
Unique Source IP Deviation. IJ Network Security, 19(6), 929-939.
Pham, T. N. D., Yeo, C. K., Yanai, N., & Fujiwara, T. (2018). Detecting flooding attack and
accommodating burst traffic in delay-tolerant networks. IEEE Transactions on
Vehicular Technology, 67(1), 795-808.
Kaur, P., Kumar, M., & Bhandari, A. (2017). A review of detection approaches for
distributed denial of service attacks. Systems Science & Control Engineering, 5(1),
301-320.
Phan, T. V., & Park, M. (2019). Efficient Distributed Denial-of-Service Attack Defense in
SDN-Based Cloud. IEEE Access, 7, 18701-18714.
Luo, S., Wu, J., Li, J., & Pei, B. (2015, August). A defense mechanism for distributed denial
of service attack in software-defined networks. In 2015 Ninth International
Conference on Frontier of Computer Science and Technology (pp. 325-329). IEEE.
Tian, Y., Tran, V., & Kuerban, M. (2019, January). DOS Attack Mitigation Strategies on
SDN Controller. In 2019 IEEE 9th Annual Computing and Communication Workshop
and Conference (CCWC) (pp. 0701-0707). IEEE.
Advanced Network Security Page 7 of 7
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





