COIT20262 Advanced Network Security Assignment 1 Solution, Term 2 2019
VerifiedAdded on 2023/03/31
|7
|1214
|147
Homework Assignment
AI Summary
This document provides a solution to COIT20262 Advanced Network Security Assignment 1 from Term 2, 2019. It includes detailed answers and analysis for questions related to packet capture using tools like netcat and scp, covering aspects like message sequence charts, TCP connection details, and ...
COIT20262 Assignment 1 Submission Term 2, 2019
COIT20262 - Advanced Network Security, Term 2, 2019
Assignment 1 Submission
Due date: 10am Monday 26 August 2019
(Week 6)
ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
COIT20262 - Advanced Network Security, Term 2, 2019
Assignment 1 Submission
Due date: 10am Monday 26 August 2019
(Week 6)
ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 1 Submission Term 2, 2019
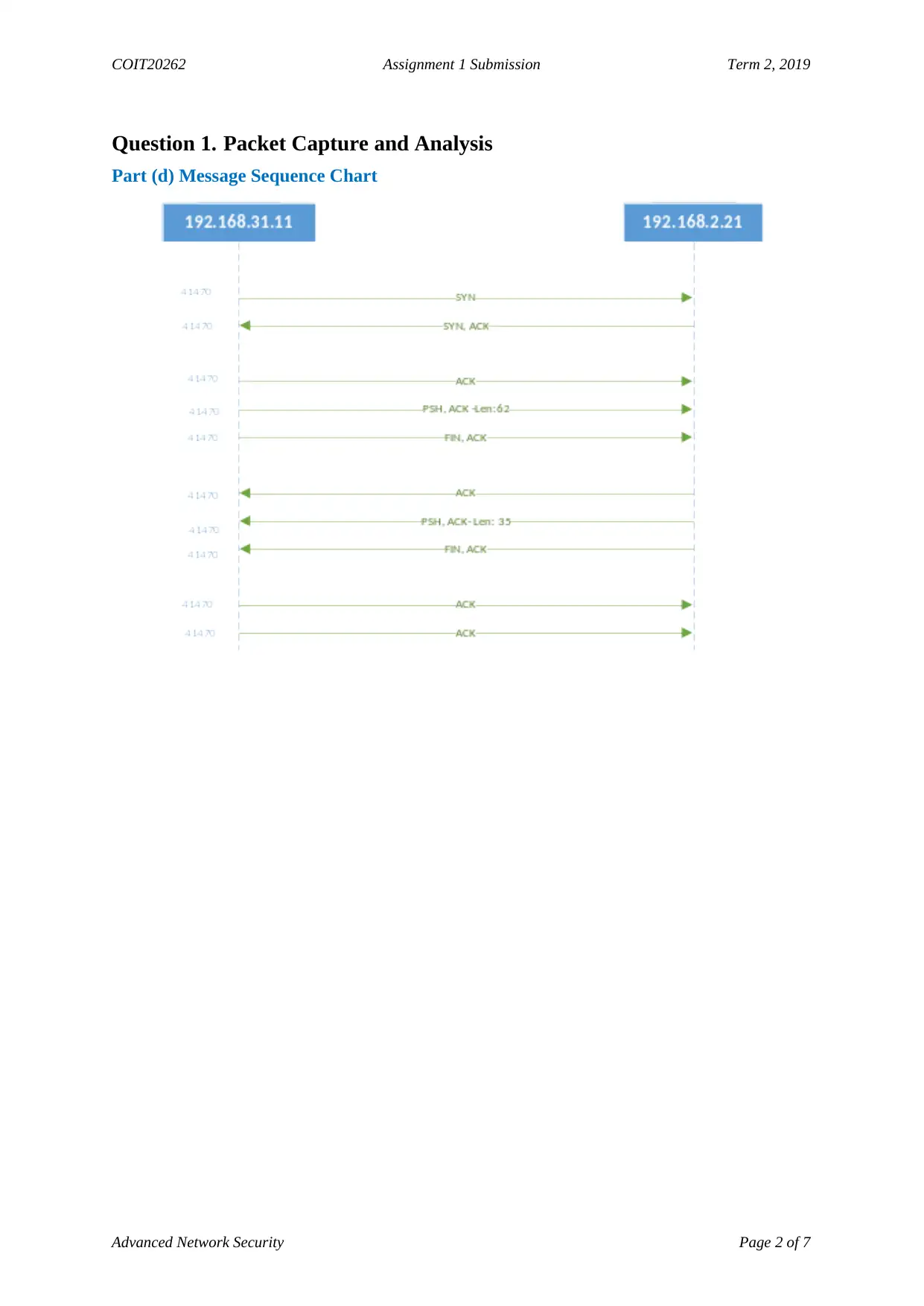
Question 1. Packet Capture and Analysis
Part (d) Message Sequence Chart
Advanced Network Security Page 2 of 7
Question 1. Packet Capture and Analysis
Part (d) Message Sequence Chart
Advanced Network Security Page 2 of 7
COIT20262 Assignment 1 Submission Term 2, 2019
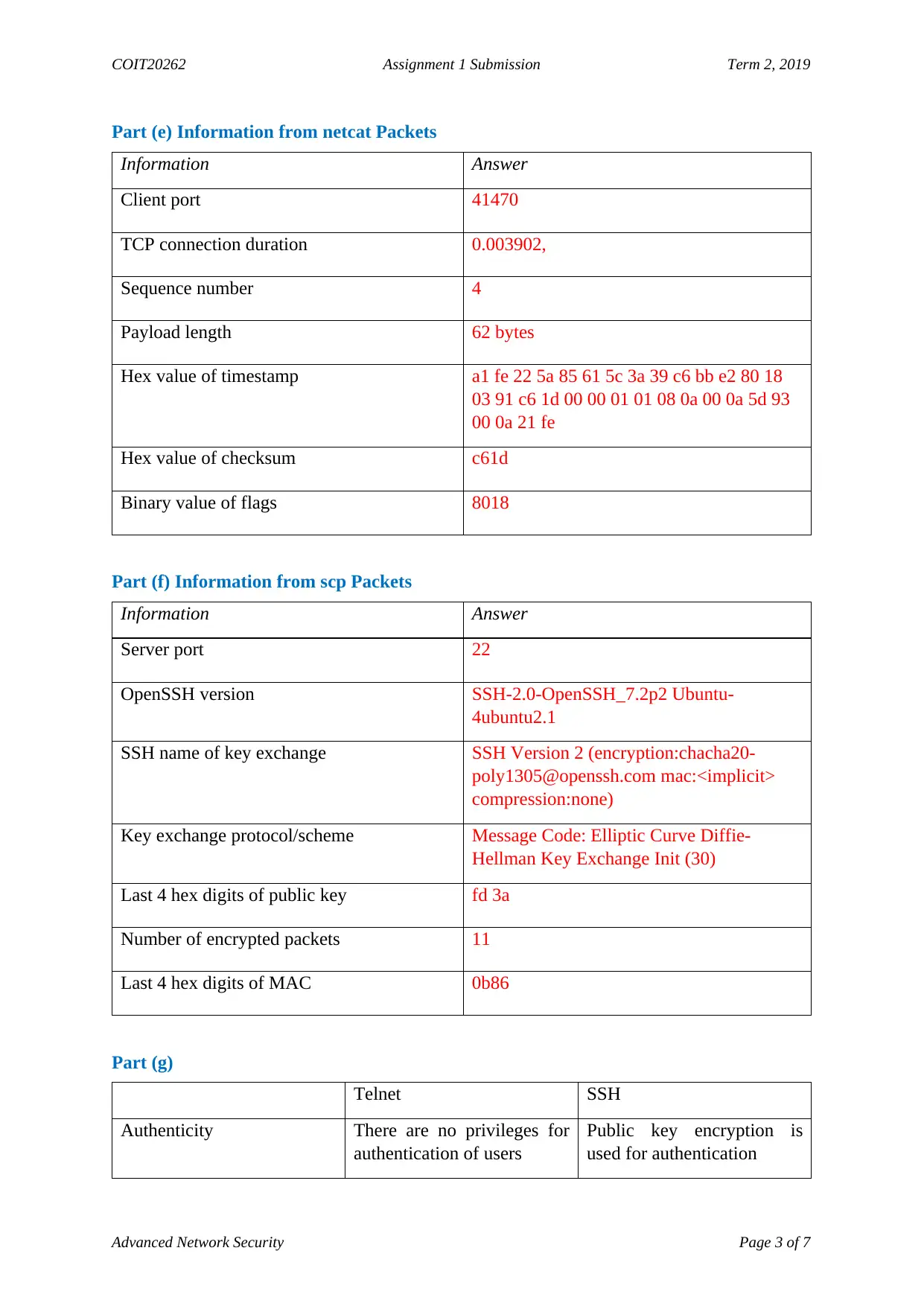
Part (e) Information from netcat Packets
Information Answer
Client port 41470
TCP connection duration 0.003902,
Sequence number 4
Payload length 62 bytes
Hex value of timestamp a1 fe 22 5a 85 61 5c 3a 39 c6 bb e2 80 18
03 91 c6 1d 00 00 01 01 08 0a 00 0a 5d 93
00 0a 21 fe
Hex value of checksum c61d
Binary value of flags 8018
Part (f) Information from scp Packets
Information Answer
Server port 22
OpenSSH version SSH-2.0-OpenSSH_7.2p2 Ubuntu-
4ubuntu2.1
SSH name of key exchange SSH Version 2 (encryption:chacha20-
poly1305@openssh.com mac:<implicit>
compression:none)
Key exchange protocol/scheme Message Code: Elliptic Curve Diffie-
Hellman Key Exchange Init (30)
Last 4 hex digits of public key fd 3a
Number of encrypted packets 11
Last 4 hex digits of MAC 0b86
Part (g)
Telnet SSH
Authenticity There are no privileges for
authentication of users
Public key encryption is
used for authentication
Advanced Network Security Page 3 of 7
Part (e) Information from netcat Packets
Information Answer
Client port 41470
TCP connection duration 0.003902,
Sequence number 4
Payload length 62 bytes
Hex value of timestamp a1 fe 22 5a 85 61 5c 3a 39 c6 bb e2 80 18
03 91 c6 1d 00 00 01 01 08 0a 00 0a 5d 93
00 0a 21 fe
Hex value of checksum c61d
Binary value of flags 8018
Part (f) Information from scp Packets
Information Answer
Server port 22
OpenSSH version SSH-2.0-OpenSSH_7.2p2 Ubuntu-
4ubuntu2.1
SSH name of key exchange SSH Version 2 (encryption:chacha20-
poly1305@openssh.com mac:<implicit>
compression:none)
Key exchange protocol/scheme Message Code: Elliptic Curve Diffie-
Hellman Key Exchange Init (30)
Last 4 hex digits of public key fd 3a
Number of encrypted packets 11
Last 4 hex digits of MAC 0b86
Part (g)
Telnet SSH
Authenticity There are no privileges for
authentication of users
Public key encryption is
used for authentication
Advanced Network Security Page 3 of 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 1 Submission Term 2, 2019
Confidentiality Data are transferred in plain
text
Data is sent in encrypted
format via a secure channel
Performance Bandwidth usage is low Bandwidth usage is higher
Part (h)
1. For the 32 bit or higher end CPU if there is no dedicated instruction ChahCha20 is
quicker when compared with AES since it is based on additional rotation XOR
(ARX). The ARX provides CPU friendly instruction but binary fields are used for
Mixcolumns and Sbox in AES for computation that uses look up table for becoming
more efficient.
2. Since lookup tables are used by the AES with an index it makes it vulnerable to cache
timing attack and this problem can be resolved with the implementation of
Chahcha20.
Question 2. Cryptography
Part (c)
The information that are needed to be encrypted have different size and format and
information contained in it. The algorithm is a different set of instruction for carrying out
different operation and solve the problems. The algorithm is used for listing the instruction
and carry an operation. The different algorithm is used for accomplishing problem solving
quickly.
Part (d)
For MD5 hash function is 128 bits and 256 bits for SHA 256, the hash function can be
computer by any person for a given input and the result obtained is similar. In some cases,
two distinct inputs can also generate the same result and is known as collision. The MD5
algorithm is broken in terms of collision and no longer considered as trustworthy.
Part (e)
The use of MD5 algorithm, can open new threat such as masquerade attack since the identity
of the user can be forged for gaining unauthorised access of the message using legitimate
access identification. The public key of the sender can be accessed for having access of the
encrypted message and cause harm to the system.
Part (f)
The detection of suspicious activity of the user can help in prevention of this type of attacks.
The application of innovative algorithm can easily solve the problem.
Part (g)
The application of the algorithm in the network can help in detecting the activity of the user
when multiple attempts are made for getting the access of the information. An alert can be
generated for more than one attempt and the attack can be resisted.
Advanced Network Security Page 4 of 7
Confidentiality Data are transferred in plain
text
Data is sent in encrypted
format via a secure channel
Performance Bandwidth usage is low Bandwidth usage is higher
Part (h)
1. For the 32 bit or higher end CPU if there is no dedicated instruction ChahCha20 is
quicker when compared with AES since it is based on additional rotation XOR
(ARX). The ARX provides CPU friendly instruction but binary fields are used for
Mixcolumns and Sbox in AES for computation that uses look up table for becoming
more efficient.
2. Since lookup tables are used by the AES with an index it makes it vulnerable to cache
timing attack and this problem can be resolved with the implementation of
Chahcha20.
Question 2. Cryptography
Part (c)
The information that are needed to be encrypted have different size and format and
information contained in it. The algorithm is a different set of instruction for carrying out
different operation and solve the problems. The algorithm is used for listing the instruction
and carry an operation. The different algorithm is used for accomplishing problem solving
quickly.
Part (d)
For MD5 hash function is 128 bits and 256 bits for SHA 256, the hash function can be
computer by any person for a given input and the result obtained is similar. In some cases,
two distinct inputs can also generate the same result and is known as collision. The MD5
algorithm is broken in terms of collision and no longer considered as trustworthy.
Part (e)
The use of MD5 algorithm, can open new threat such as masquerade attack since the identity
of the user can be forged for gaining unauthorised access of the message using legitimate
access identification. The public key of the sender can be accessed for having access of the
encrypted message and cause harm to the system.
Part (f)
The detection of suspicious activity of the user can help in prevention of this type of attacks.
The application of innovative algorithm can easily solve the problem.
Part (g)
The application of the algorithm in the network can help in detecting the activity of the user
when multiple attempts are made for getting the access of the information. An alert can be
generated for more than one attempt and the attack can be resisted.
Advanced Network Security Page 4 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COIT20262 Assignment 1 Submission Term 2, 2019
Advanced Network Security Page 5 of 7
Advanced Network Security Page 5 of 7

COIT20262 Assignment 1 Submission Term 2, 2019
Question 3. Malware Research
What is ransomware?
Malware which threatens data publication of victim or blockage of data access until payment
of ransom is termed as ransomware. Ransomware is disastrous to an organization or to an
individual. Any important data available in network or system is in danger. Data recovery is
difficult which may need the services of data recovery expert.
Infection Methods
Multiple ransomware methods are used in different networks, applications based on SaaS.
Enlightened toolkits that exploit vulnerabilities are known as exploit kits. When a website is
visited by a victim, exploit kits can be executed. The attacker sends an email with email
attachments containing malware. Ransomware is downloaded unknowingly when the email is
opened, infecting the system and holding the files for ransom.
Role of Cryptography
The technique of securing communication in presence of third parties is termed as
cryptography. The encryption technique where a similar key is used by the receiver and the
sender is called symmetric-key cryptography. Security layer is added and verification of data
authenticity is done using cryptography’s hash functions.
Not Pay Ransom
Public awareness deficiency is a reason for payment of ransom to the attackers who control
the files and computer system. Huge amount of money is paid which strengthens criminal’s
faith upon their work. Prevention of ransom attacks can be done by making loss to
ransomware. Ransom money is not required to be paid if the data is kept in a location as
backup.
Pay Ransom
Payment of ransom can be workable option. Even if the ransom money is paid by the
university, there is no assurance for recovery of data. Cryptocurrency is used as payment of
ransom money with range value of a couple of hundred to a million dollars to unlock the
files.
Recommendations
Anti-malware software can be installed in systems to find and destroy scamp programs.
Security scans test the enterprise software and websites to search known malwares which can
infect the application. Spam filters can be used for blocking emails with suspicious
attachments.
Advanced Network Security Page 6 of 7
Question 3. Malware Research
What is ransomware?
Malware which threatens data publication of victim or blockage of data access until payment
of ransom is termed as ransomware. Ransomware is disastrous to an organization or to an
individual. Any important data available in network or system is in danger. Data recovery is
difficult which may need the services of data recovery expert.
Infection Methods
Multiple ransomware methods are used in different networks, applications based on SaaS.
Enlightened toolkits that exploit vulnerabilities are known as exploit kits. When a website is
visited by a victim, exploit kits can be executed. The attacker sends an email with email
attachments containing malware. Ransomware is downloaded unknowingly when the email is
opened, infecting the system and holding the files for ransom.
Role of Cryptography
The technique of securing communication in presence of third parties is termed as
cryptography. The encryption technique where a similar key is used by the receiver and the
sender is called symmetric-key cryptography. Security layer is added and verification of data
authenticity is done using cryptography’s hash functions.
Not Pay Ransom
Public awareness deficiency is a reason for payment of ransom to the attackers who control
the files and computer system. Huge amount of money is paid which strengthens criminal’s
faith upon their work. Prevention of ransom attacks can be done by making loss to
ransomware. Ransom money is not required to be paid if the data is kept in a location as
backup.
Pay Ransom
Payment of ransom can be workable option. Even if the ransom money is paid by the
university, there is no assurance for recovery of data. Cryptocurrency is used as payment of
ransom money with range value of a couple of hundred to a million dollars to unlock the
files.
Recommendations
Anti-malware software can be installed in systems to find and destroy scamp programs.
Security scans test the enterprise software and websites to search known malwares which can
infect the application. Spam filters can be used for blocking emails with suspicious
attachments.
Advanced Network Security Page 6 of 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 1 Submission Term 2, 2019
Bibliography
Ambrosin, M., Conti, M., De Gaspari, F. and Devarajan, N., 2016, November. Amplified
distributed denial of service attack in software defined networking. In 2016 8th IFIP
International Conference on New Technologies, Mobility and Security (NTMS) (pp. 1-4).
IEEE.
Kinnunen, T., Sahidullah, M., Delgado, H., Todisco, M., Evans, N., Yamagishi, J. and Lee,
K.A., 2017. The ASVspoof 2017 challenge: Assessing the limits of replay spoofing attack
detection.
Mahjabin, T., Xiao, Y., Sun, G. and Jiang, W., 2017. A survey of distributed denial-of-
service attack, prevention, and mitigation techniques. International Journal of Distributed
Sensor Networks, 13(12), p.1550147717741463.
Meneses, F., Fuertes, W., Sancho, J., Salvador, S., Flores, D., Aules, H., Castro, F., Torres, J.,
Miranda, A. and Nuela, D., 2016. RSA encryption algorithm optimization to improve
performance and security level of network messages. Int. J. Comput. Sci. Netw. Secur., 16(8),
pp.55-62.
Yoo, Y., Azarderakhsh, R., Jalali, A., Jao, D. and Soukharev, V., 2017, April. A post-
quantum digital signature scheme based on supersingular isogenies. In International
Conference on Financial Cryptography and Data Security (pp. 163-181). Springer, Cham.
Zhang, X., Long, J., Wang, Z. and Cheng, H., 2016. Lossless and reversible data hiding in
encrypted images with public-key cryptography. IEEE Transactions on Circuits and Systems
for Video Technology, 26(9), pp.1622-1631.
Advanced Network Security Page 7 of 7
Bibliography
Ambrosin, M., Conti, M., De Gaspari, F. and Devarajan, N., 2016, November. Amplified
distributed denial of service attack in software defined networking. In 2016 8th IFIP
International Conference on New Technologies, Mobility and Security (NTMS) (pp. 1-4).
IEEE.
Kinnunen, T., Sahidullah, M., Delgado, H., Todisco, M., Evans, N., Yamagishi, J. and Lee,
K.A., 2017. The ASVspoof 2017 challenge: Assessing the limits of replay spoofing attack
detection.
Mahjabin, T., Xiao, Y., Sun, G. and Jiang, W., 2017. A survey of distributed denial-of-
service attack, prevention, and mitigation techniques. International Journal of Distributed
Sensor Networks, 13(12), p.1550147717741463.
Meneses, F., Fuertes, W., Sancho, J., Salvador, S., Flores, D., Aules, H., Castro, F., Torres, J.,
Miranda, A. and Nuela, D., 2016. RSA encryption algorithm optimization to improve
performance and security level of network messages. Int. J. Comput. Sci. Netw. Secur., 16(8),
pp.55-62.
Yoo, Y., Azarderakhsh, R., Jalali, A., Jao, D. and Soukharev, V., 2017, April. A post-
quantum digital signature scheme based on supersingular isogenies. In International
Conference on Financial Cryptography and Data Security (pp. 163-181). Springer, Cham.
Zhang, X., Long, J., Wang, Z. and Cheng, H., 2016. Lossless and reversible data hiding in
encrypted images with public-key cryptography. IEEE Transactions on Circuits and Systems
for Video Technology, 26(9), pp.1622-1631.
Advanced Network Security Page 7 of 7
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





