COIT20262 Advanced Network Security: Assignment 1 Term 1, 2019
VerifiedAdded on 2023/01/04
|7
|1721
|59
Homework Assignment
AI Summary
This document presents a solution to COIT20262 Advanced Network Security Assignment 1, Term 1 2019, focusing on key areas such as packet capture and analysis, cryptography, and denial of service (DoS) attacks. The packet capture analysis involves examining TCP and UDP packets, understanding message sequence charts, and extracting relevant information like IP addresses, MAC addresses, timestamps, and checksums. The cryptography section delves into the ethical implications of public keys, the use of digital certificates for secure key exchange, and the importance of digital signatures in improving asymmetric key encryption. The assignment also includes a research overview of DDoS attacks, differentiating them from DoS attacks, identifying entities involved in DDoS, and specifically analyzing ping flooding attacks along with mitigation strategies. References to various research papers are provided to support the analysis and solutions presented. Desklib offers this and many other solved assignments to aid students in their studies.
COIT20262 Assignment 1 Submission Term 1, 2019
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 1 Submission
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 1 Submission
Due date: 5pm Friday 26 April 2019 (Week 6) ASSESSMENT
Weighting: 40%
1Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 1 Submission Term 1, 2019
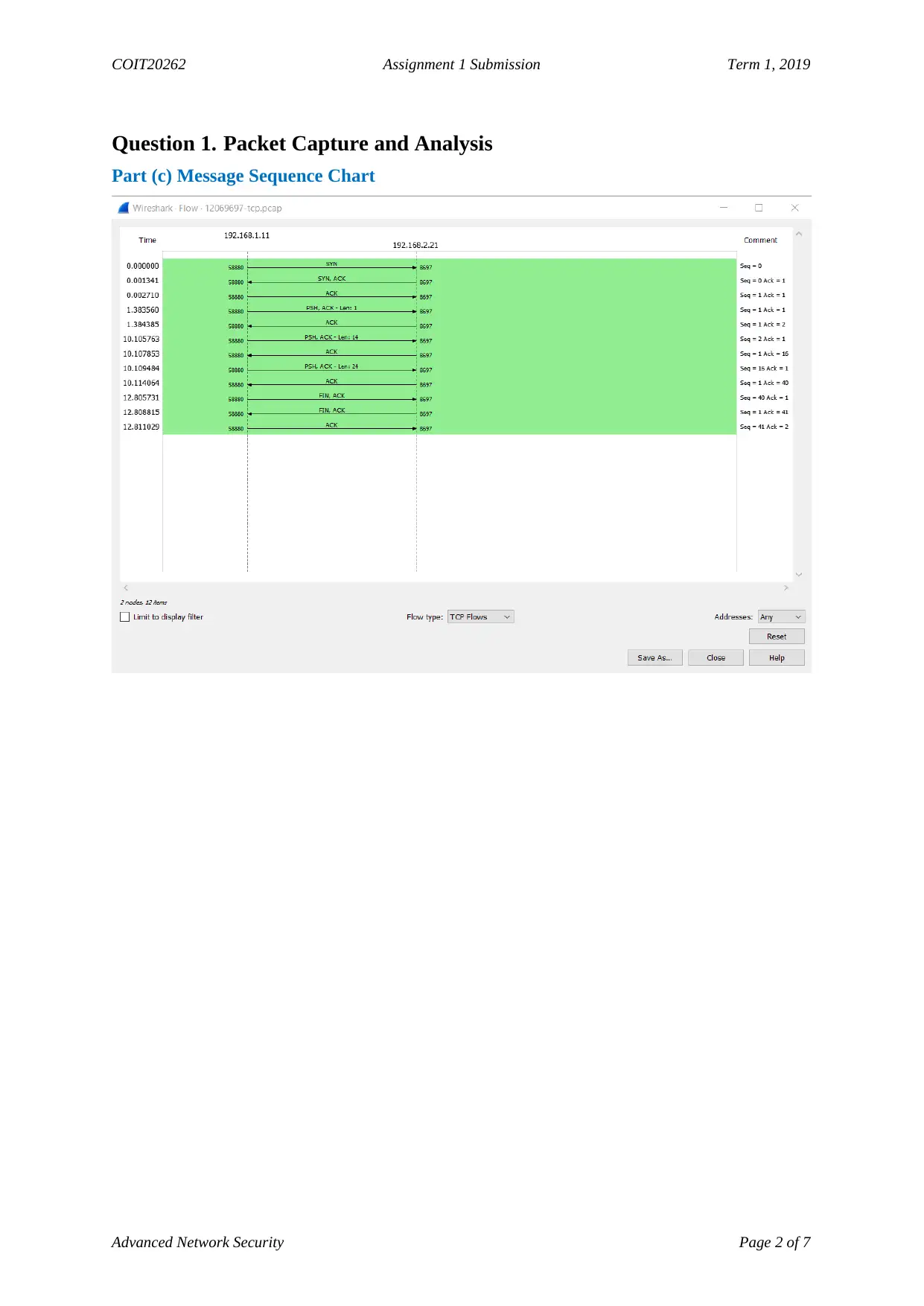
Question 1. Packet Capture and Analysis
Part (c) Message Sequence Chart
Advanced Network Security Page 2 of 7
Question 1. Packet Capture and Analysis
Part (c) Message Sequence Chart
Advanced Network Security Page 2 of 7
COIT20262 Assignment 1 Submission Term 1, 2019
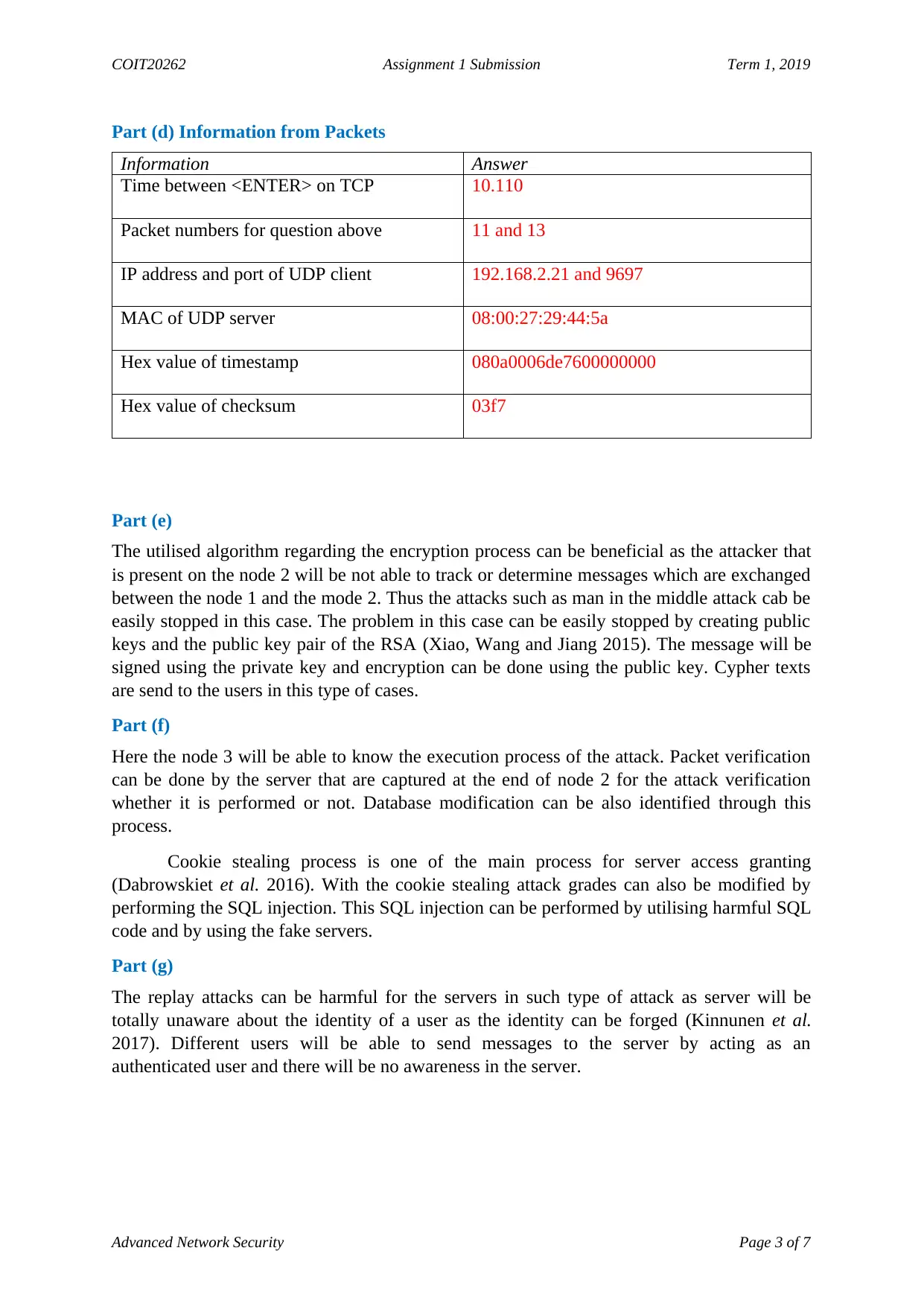
Part (d) Information from Packets
Information Answer
Time between <ENTER> on TCP 10.110
Packet numbers for question above 11 and 13
IP address and port of UDP client 192.168.2.21 and 9697
MAC of UDP server 08:00:27:29:44:5a
Hex value of timestamp 080a0006de7600000000
Hex value of checksum 03f7
Part (e)
The utilised algorithm regarding the encryption process can be beneficial as the attacker that
is present on the node 2 will be not able to track or determine messages which are exchanged
between the node 1 and the mode 2. Thus the attacks such as man in the middle attack cab be
easily stopped in this case. The problem in this case can be easily stopped by creating public
keys and the public key pair of the RSA (Xiao, Wang and Jiang 2015). The message will be
signed using the private key and encryption can be done using the public key. Cypher texts
are send to the users in this type of cases.
Part (f)
Here the node 3 will be able to know the execution process of the attack. Packet verification
can be done by the server that are captured at the end of node 2 for the attack verification
whether it is performed or not. Database modification can be also identified through this
process.
Cookie stealing process is one of the main process for server access granting
(Dabrowskiet et al. 2016). With the cookie stealing attack grades can also be modified by
performing the SQL injection. This SQL injection can be performed by utilising harmful SQL
code and by using the fake servers.
Part (g)
The replay attacks can be harmful for the servers in such type of attack as server will be
totally unaware about the identity of a user as the identity can be forged (Kinnunen et al.
2017). Different users will be able to send messages to the server by acting as an
authenticated user and there will be no awareness in the server.
Advanced Network Security Page 3 of 7
Part (d) Information from Packets
Information Answer
Time between <ENTER> on TCP 10.110
Packet numbers for question above 11 and 13
IP address and port of UDP client 192.168.2.21 and 9697
MAC of UDP server 08:00:27:29:44:5a
Hex value of timestamp 080a0006de7600000000
Hex value of checksum 03f7
Part (e)
The utilised algorithm regarding the encryption process can be beneficial as the attacker that
is present on the node 2 will be not able to track or determine messages which are exchanged
between the node 1 and the mode 2. Thus the attacks such as man in the middle attack cab be
easily stopped in this case. The problem in this case can be easily stopped by creating public
keys and the public key pair of the RSA (Xiao, Wang and Jiang 2015). The message will be
signed using the private key and encryption can be done using the public key. Cypher texts
are send to the users in this type of cases.
Part (f)
Here the node 3 will be able to know the execution process of the attack. Packet verification
can be done by the server that are captured at the end of node 2 for the attack verification
whether it is performed or not. Database modification can be also identified through this
process.
Cookie stealing process is one of the main process for server access granting
(Dabrowskiet et al. 2016). With the cookie stealing attack grades can also be modified by
performing the SQL injection. This SQL injection can be performed by utilising harmful SQL
code and by using the fake servers.
Part (g)
The replay attacks can be harmful for the servers in such type of attack as server will be
totally unaware about the identity of a user as the identity can be forged (Kinnunen et al.
2017). Different users will be able to send messages to the server by acting as an
authenticated user and there will be no awareness in the server.
Advanced Network Security Page 3 of 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 1 Submission Term 1, 2019
Question 2. Cryptography
Part (c)
Attackers can utilise the public key to create new private key unethically. This can be harmful
in the sense that the attacker can use this created private key foe encryption and decryption of
the network traffics which may contain some sensitive information. For the vulnerability
impact detection length of the key and the public availability of it are the main assets.
Part (d)
The electronic certificates is one of the safest way for exchanging the public keys if these
certificates are signed digitally (Cheng et al. 2018). Thus the assessment teacher can use this
digitally signed electronics certificate for signing the public key digitally and following that
the signed pubic key can be distributed using the Moodle forum. The vital steps for this are
discussed below:
1. Pair of Private and Public key is generated.
2. User requests signed certificate from the tutor’s end.
3. Certificate holds public key and owner’s name.
4. Private Key utilises small data.
5. Symmetric key is utilised for encryption of a bulk amount of data.
6. Public Key verification is done by knowing the signed certificate.
Part (e)
Implementing the digital signature is one of the most efficient way of improving the
asymmetric key encryption. Message authentication and the exchange of public key can be
done using the certificates that are signed (Dowling et al. 2016). Authentication of the
messages is important to ensure that trusted sender has sent the message and for preserving
the data integrity which the message holds. Hashing is used here for generation of the
authentication code. Man in the middle attack can be stopped using the digital signature.
Digital signature is important stopping the adaptive chosen message attack and the forgery
attack while public key is shared.
Advanced Network Security Page 4 of 7
Question 2. Cryptography
Part (c)
Attackers can utilise the public key to create new private key unethically. This can be harmful
in the sense that the attacker can use this created private key foe encryption and decryption of
the network traffics which may contain some sensitive information. For the vulnerability
impact detection length of the key and the public availability of it are the main assets.
Part (d)
The electronic certificates is one of the safest way for exchanging the public keys if these
certificates are signed digitally (Cheng et al. 2018). Thus the assessment teacher can use this
digitally signed electronics certificate for signing the public key digitally and following that
the signed pubic key can be distributed using the Moodle forum. The vital steps for this are
discussed below:
1. Pair of Private and Public key is generated.
2. User requests signed certificate from the tutor’s end.
3. Certificate holds public key and owner’s name.
4. Private Key utilises small data.
5. Symmetric key is utilised for encryption of a bulk amount of data.
6. Public Key verification is done by knowing the signed certificate.
Part (e)
Implementing the digital signature is one of the most efficient way of improving the
asymmetric key encryption. Message authentication and the exchange of public key can be
done using the certificates that are signed (Dowling et al. 2016). Authentication of the
messages is important to ensure that trusted sender has sent the message and for preserving
the data integrity which the message holds. Hashing is used here for generation of the
authentication code. Man in the middle attack can be stopped using the digital signature.
Digital signature is important stopping the adaptive chosen message attack and the forgery
attack while public key is shared.
Advanced Network Security Page 4 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 1 Submission Term 1, 2019
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
DoS Attack: The DoS attack is also known as the Denial of Service attack where the attacker
is able to stop an authorised user of a system to access the system by making the system
unresponsive. For performing the attack perfectly, attacker sends a huge amount of network
traffic to the targeted system and due to this fact the targeted system fails to response those
traffics timely and becomes overloaded (Boraten and Kodi 2016). Thus the system becomes
unresponsive and all the security system of the system also becomes unresponsive due to
which it becomes vulnerable to various types of attacks.
DDoS Attack: The DDoS which stands for Distributed Denial of Service attack which is
similar with the DoS attack. Some malicious types of codes are utilised in this case for
intercepting normal traffic flow of the targeted system (Mallikarjunan, Muthupriya and
Shalinie 2016). Trojans are used in this case for performing the DDoS attack.
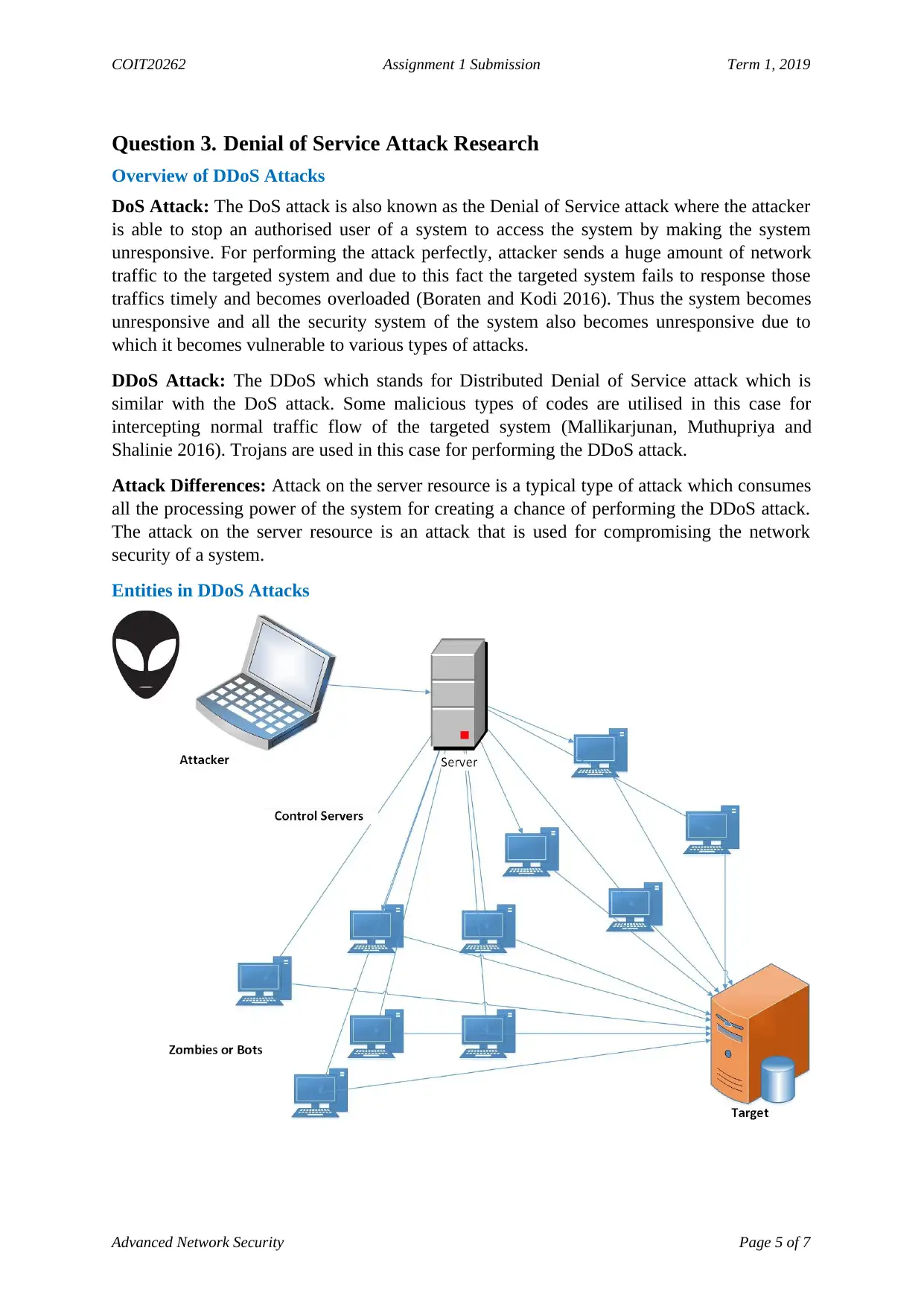
Attack Differences: Attack on the server resource is a typical type of attack which consumes
all the processing power of the system for creating a chance of performing the DDoS attack.
The attack on the server resource is an attack that is used for compromising the network
security of a system.
Entities in DDoS Attacks
Advanced Network Security Page 5 of 7
Question 3. Denial of Service Attack Research
Overview of DDoS Attacks
DoS Attack: The DoS attack is also known as the Denial of Service attack where the attacker
is able to stop an authorised user of a system to access the system by making the system
unresponsive. For performing the attack perfectly, attacker sends a huge amount of network
traffic to the targeted system and due to this fact the targeted system fails to response those
traffics timely and becomes overloaded (Boraten and Kodi 2016). Thus the system becomes
unresponsive and all the security system of the system also becomes unresponsive due to
which it becomes vulnerable to various types of attacks.
DDoS Attack: The DDoS which stands for Distributed Denial of Service attack which is
similar with the DoS attack. Some malicious types of codes are utilised in this case for
intercepting normal traffic flow of the targeted system (Mallikarjunan, Muthupriya and
Shalinie 2016). Trojans are used in this case for performing the DDoS attack.
Attack Differences: Attack on the server resource is a typical type of attack which consumes
all the processing power of the system for creating a chance of performing the DDoS attack.
The attack on the server resource is an attack that is used for compromising the network
security of a system.
Entities in DDoS Attacks
Advanced Network Security Page 5 of 7

COIT20262 Assignment 1 Submission Term 1, 2019
Ping Flooding Attack
Ping Flooding Attack: Ping flooding attack is also considered as the ICMP attack which is a
subdivision of the DDoS attack. High amount of ICMP echo is forwarded to the targeted
system for making the system unstable by lowering its performance.
The ping flooding attack is done through utilising the ICMP echo which actually
overloads the capability of the system with numerous number of pings (Gunnam and Kumar
2017). The system unable to perform correctly in this type of situations and potential
vulnerability occurs in the system due to this. For performing the ping flooding attack IP
address is important to the attacker as without knowing the IP address of the targeted system
attacker will not be able to send a high amount of pings to the targeted system. Proper
sequence must be followed by the attacker for performing a perfect attack. The attacker also
need to ensure that sufficient bandwidth is available for performing the attack which needs to
be higher than the targeted system.
Mitigating Ping Flooding Attack
Mitigation of the Ping Flooding Attack: It has been assessed that one of the best way for
mitigating the ping flooding attack is utilising the Cloudfare software. With the Cloudfare
software reconfiguration of the firewall is also another way of effectively stopping the ping
flooding attack. Reconfiguration of the firewall blocks unnecessary pings from outside
network which reduces the chances of occurring the ping flooding attack.
Advanced Network Security Page 6 of 7
Ping Flooding Attack
Ping Flooding Attack: Ping flooding attack is also considered as the ICMP attack which is a
subdivision of the DDoS attack. High amount of ICMP echo is forwarded to the targeted
system for making the system unstable by lowering its performance.
The ping flooding attack is done through utilising the ICMP echo which actually
overloads the capability of the system with numerous number of pings (Gunnam and Kumar
2017). The system unable to perform correctly in this type of situations and potential
vulnerability occurs in the system due to this. For performing the ping flooding attack IP
address is important to the attacker as without knowing the IP address of the targeted system
attacker will not be able to send a high amount of pings to the targeted system. Proper
sequence must be followed by the attacker for performing a perfect attack. The attacker also
need to ensure that sufficient bandwidth is available for performing the attack which needs to
be higher than the targeted system.
Mitigating Ping Flooding Attack
Mitigation of the Ping Flooding Attack: It has been assessed that one of the best way for
mitigating the ping flooding attack is utilising the Cloudfare software. With the Cloudfare
software reconfiguration of the firewall is also another way of effectively stopping the ping
flooding attack. Reconfiguration of the firewall blocks unnecessary pings from outside
network which reduces the chances of occurring the ping flooding attack.
Advanced Network Security Page 6 of 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 1 Submission Term 1, 2019
References:
Boraten, T. and Kodi, A.K., 2016, May. Mitigation of denial of service attack with hardware
trojans in noc architectures. In 2016 IEEE international parallel and distributed processing
symposium (IPDPS) (pp. 1091-1100). IEEE.
Cheng, J. C., Lee, N. Y., Chi, C., and Chen, Y. H. (2018, April). Blockchain and smart
contract for digital certificate. In 2018 IEEE international conference on applied system
invention (ICASI) (pp. 1046-1051). IEEE.
Dabrowski, A., Merzdovnik, G., Kommenda, N. and Weippl, E., 2016, May. Browser history
stealing with captive Wi-Fi portals. In 2016 IEEE Security and Privacy Workshops (SPW)
(pp. 234-240). IEEE.
Dowling, B., Günther, F., Herath, U. and Stebila, D., 2016, September. Secure logging
schemes and certificate transparency. In European Symposium on Research in Computer
Security (pp. 140-158). Springer, Cham.
Gunnam, G.R. and Kumar, S., 2017. Do ICMP Security Attacks Have Same Impact on
Servers?. Journal of Information Security, 8(03), p.274.
Kinnunen, T., Sahidullah, M., Delgado, H., Todisco, M., Evans, N., Yamagishi, J. and Lee,
K.A., 2017. The ASVspoof 2017 challenge: Assessing the limits of replay spoofing attack
detection.
Mallikarjunan, K. N., Muthupriya, K., and Shalinie, S. M. (2016, January). A survey of
distributed denial of service attack. In 2016 10th International Conference on Intelligent
Systems and Control (ISCO) (pp. 1-6). IEEE.
Xiao, Z., Wang, Y. and Jiang, Z., 2015, June. Research and implementation of four-prime
RSA digital signature algorithm. In 2015 IEEE/ACIS 14th International Conference on
Computer and Information Science (ICIS) (pp. 545-549). IEEE.
Advanced Network Security Page 7 of 7
References:
Boraten, T. and Kodi, A.K., 2016, May. Mitigation of denial of service attack with hardware
trojans in noc architectures. In 2016 IEEE international parallel and distributed processing
symposium (IPDPS) (pp. 1091-1100). IEEE.
Cheng, J. C., Lee, N. Y., Chi, C., and Chen, Y. H. (2018, April). Blockchain and smart
contract for digital certificate. In 2018 IEEE international conference on applied system
invention (ICASI) (pp. 1046-1051). IEEE.
Dabrowski, A., Merzdovnik, G., Kommenda, N. and Weippl, E., 2016, May. Browser history
stealing with captive Wi-Fi portals. In 2016 IEEE Security and Privacy Workshops (SPW)
(pp. 234-240). IEEE.
Dowling, B., Günther, F., Herath, U. and Stebila, D., 2016, September. Secure logging
schemes and certificate transparency. In European Symposium on Research in Computer
Security (pp. 140-158). Springer, Cham.
Gunnam, G.R. and Kumar, S., 2017. Do ICMP Security Attacks Have Same Impact on
Servers?. Journal of Information Security, 8(03), p.274.
Kinnunen, T., Sahidullah, M., Delgado, H., Todisco, M., Evans, N., Yamagishi, J. and Lee,
K.A., 2017. The ASVspoof 2017 challenge: Assessing the limits of replay spoofing attack
detection.
Mallikarjunan, K. N., Muthupriya, K., and Shalinie, S. M. (2016, January). A survey of
distributed denial of service attack. In 2016 10th International Conference on Intelligent
Systems and Control (ISCO) (pp. 1-6). IEEE.
Xiao, Z., Wang, Y. and Jiang, Z., 2015, June. Research and implementation of four-prime
RSA digital signature algorithm. In 2015 IEEE/ACIS 14th International Conference on
Computer and Information Science (ICIS) (pp. 545-549). IEEE.
Advanced Network Security Page 7 of 7
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





