Hash Algorithm and Encryption Algorithm for Certificate Signature
Answering questions related to advanced network security, including topics such as certificates, encryption algorithms, access control, and firewalls.
9 Pages2432 Words48 Views
Added on 2023-01-20
About This Document
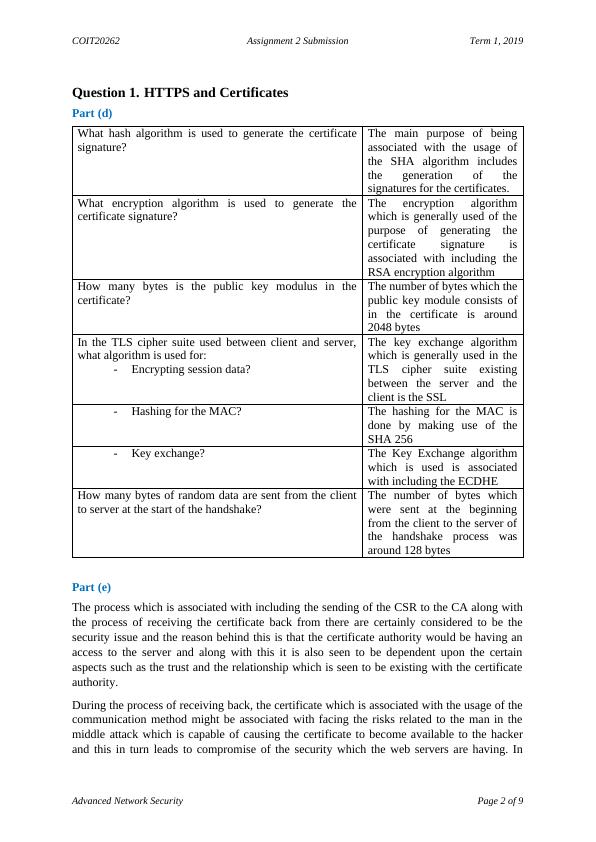
This document discusses the hash algorithm and encryption algorithm used for generating the certificate signature in advanced network security. It provides information on the number of bytes in the public key modulus and the algorithms used for encrypting session data, hashing for the MAC, and key exchange. Additionally, it explores the number of bytes of random data sent during the handshake process.
Hash Algorithm and Encryption Algorithm for Certificate Signature
Answering questions related to advanced network security, including topics such as certificates, encryption algorithms, access control, and firewalls.
Added on 2023-01-20
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
COIT20262 - Advanced Network Security
|7
|1530
|156
COIT20262 Assignment 2 Submission
|6
|821
|58
Advanced Network Security: Cryptography, Access Control, Firewalls, and Wireless Network Security
|11
|1783
|206
Advanced Network Security: Cryptography, HTTPS, Access Control, Firewalls, Wireless Security
|10
|1404
|169
Advanced Network Security : PDF
|10
|1144
|216
Advanced Network Security - PDF
|9
|1400
|70