Collaboration Tools, Cloud Computing, and Security in Modern Business
VerifiedAdded on 2023/06/08
|13
|3742
|133
Report
AI Summary
This report provides a comprehensive analysis of collaboration tools in the context of modern business, particularly in the digital age. It explores the impact of these tools, such as Slack and Webex, on business operations, especially during the COVID-19 pandemic. The report delves into the benefits, drawbacks, and applications of cloud computing and cloud storage, assessing their suitability for various business needs. It also addresses critical issues of data privacy and security, identifying challenges faced by individuals and businesses and suggesting potential protective measures. Furthermore, the report examines the cryptocurrency market, including the risks associated with investments, and the impact of events like the COVID-19 pandemic on the stability of cryptocurrencies like Tether. The report uses examples of companies like Boohoo Group Plc and Deliveroo to illustrate the practical application of these concepts, providing a well-rounded view of how businesses navigate the digital landscape.

Integrated Professional
Skills in Digital Age
Skills in Digital Age
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ABSTRACT
All size of businesses are now a days dependent on collaboration tools in some or other
form in today's present society. Each and every step of this process makes the utilization of
some form of communication which is based on collaboration tools directly or indirectly. In this
report the idea of how the tools of collaboration has affected the modern businesses. Various
challenges and repercussions on the today's businesses will be analysed as the part of the project.
In the utilization of these tools there is issue of security and privacy. Cryptocurrencies which is
the riskiest investment in market today. Justification of Tether the most stable crypto currency
is getting impacted by the withdrawals after Covid pandemic.
All size of businesses are now a days dependent on collaboration tools in some or other
form in today's present society. Each and every step of this process makes the utilization of
some form of communication which is based on collaboration tools directly or indirectly. In this
report the idea of how the tools of collaboration has affected the modern businesses. Various
challenges and repercussions on the today's businesses will be analysed as the part of the project.
In the utilization of these tools there is issue of security and privacy. Cryptocurrencies which is
the riskiest investment in market today. Justification of Tether the most stable crypto currency
is getting impacted by the withdrawals after Covid pandemic.

Table of Contents
INTRODUCTION...........................................................................................................................4
MAIN BODY...................................................................................................................................4
Identify the tools of collaboration & discuss about how it has assisted the business
organisation in the global pandemic Covid time ......................................................................4
Discussing of the pros,cons, applications and suitability in context with the cloud computing
in improved process of digitalization .........................................................................................6
Identifying the challenges of privacy and security and possible measures which may be
taken by the persons and firms for protection of the data .......................................................8
Potential measures which are undertaken by businesses and individuals for protecting
themselves from varied issues are as follows:............................................................................9
Discussion of bubble bursting procedure of cryptocurrency with proper justification.............10
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................13
INTRODUCTION...........................................................................................................................4
MAIN BODY...................................................................................................................................4
Identify the tools of collaboration & discuss about how it has assisted the business
organisation in the global pandemic Covid time ......................................................................4
Discussing of the pros,cons, applications and suitability in context with the cloud computing
in improved process of digitalization .........................................................................................6
Identifying the challenges of privacy and security and possible measures which may be
taken by the persons and firms for protection of the data .......................................................8
Potential measures which are undertaken by businesses and individuals for protecting
themselves from varied issues are as follows:............................................................................9
Discussion of bubble bursting procedure of cryptocurrency with proper justification.............10
CONCLUSION..............................................................................................................................12
REFERENCES..............................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Information and Communication Technology refers to the infrastructure and elements
which help the business organisations for enabling the contemporary process of computing. Ir is
vital for the handling of process of communication like media broad casting and system for
communication transmission and others(Palaiologou and Gray, 2019) . It enables for the
utilization of unique practices in businesses for the creation of value to the consumer in a
effectual way. It includes the entire digital technology which helps the business firm in
managing and absorption of the information in effectual way. For having the good
understanding of the communication and information technology, various examples are taken
for the consideration. The report presents the understanding of the collaboration tools utilization
in the place of work. It also includes the knowledge about the benefits and implication of the
cloud computing and e commerce in the contemporary place of the work. It also covers the
concerns of security and privacy threats for the business enterprise while utilizing internet. It
will also mention the cryptocurrencies bubble burst in the market.
MAIN BODY
Identify the tools of collaboration & discuss about how it has assisted the business
organisation in the global pandemic Covid time
Collaborative tools are known as the form of software application which allows the
employees for working together and share the knowledge with the others on the virtual way.
These tools of collaboration assists the employees in performance of the activity of the
organisation from any where in the world. It enables for storing the vital document on the
cloud which is accessible by the any member of team or employee while working remotely. All
these tools of collaboration are very significant as it aids the employees for reducing the down
time and enhance the productivity(Potolia and Derivry-Plard, 2022). By the use of virtual tools
of collaboration the channels of communication may be improved effectively. Even in the Covid
19 pandemic and constant lock downs, various business organisation have selected to opt the
virtual software of collaborative which makes them for connecting with the employees in a
strategic way. 2 tools of collaboration which may be used at the place of work in context of
examples of Boohoo Group Plc and Deliveroo are discussed below-
Information and Communication Technology refers to the infrastructure and elements
which help the business organisations for enabling the contemporary process of computing. Ir is
vital for the handling of process of communication like media broad casting and system for
communication transmission and others(Palaiologou and Gray, 2019) . It enables for the
utilization of unique practices in businesses for the creation of value to the consumer in a
effectual way. It includes the entire digital technology which helps the business firm in
managing and absorption of the information in effectual way. For having the good
understanding of the communication and information technology, various examples are taken
for the consideration. The report presents the understanding of the collaboration tools utilization
in the place of work. It also includes the knowledge about the benefits and implication of the
cloud computing and e commerce in the contemporary place of the work. It also covers the
concerns of security and privacy threats for the business enterprise while utilizing internet. It
will also mention the cryptocurrencies bubble burst in the market.
MAIN BODY
Identify the tools of collaboration & discuss about how it has assisted the business
organisation in the global pandemic Covid time
Collaborative tools are known as the form of software application which allows the
employees for working together and share the knowledge with the others on the virtual way.
These tools of collaboration assists the employees in performance of the activity of the
organisation from any where in the world. It enables for storing the vital document on the
cloud which is accessible by the any member of team or employee while working remotely. All
these tools of collaboration are very significant as it aids the employees for reducing the down
time and enhance the productivity(Potolia and Derivry-Plard, 2022). By the use of virtual tools
of collaboration the channels of communication may be improved effectively. Even in the Covid
19 pandemic and constant lock downs, various business organisation have selected to opt the
virtual software of collaborative which makes them for connecting with the employees in a
strategic way. 2 tools of collaboration which may be used at the place of work in context of
examples of Boohoo Group Plc and Deliveroo are discussed below-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Slack- It is known as the tool of workplace communication which is the system
of quick messaging. It gives 2 methods by which the employees may
communicate with the other employees and their seniors in the formal way. It
organizes the conversations of the firms in to the channels where the employee
may come at single place for the sharing of suggestions and take decisions in the
better way. It has built the art of assisting the members of the team for
concentration and establish the culture which increased the productivity in a
strategic way. For ex- Deliveroo a United Kingdom based food delivery service
uses Slack for the management of remote and distributed work force for
connecting throughout the process of business. Slack offers the various software
application which aids the adjoining of work force on the remote basis
effectually. Other example of using the Slack is Airbnb where it aids the
executive in integration of external 3 parties in a strategic way. Slack Huddles
might act as the alternative for the video conferencing as it gives excellent
experience to the executives of the organisation while doing interaction with the
employees and clients as well(Sousa and Rocha, 2019).
Webex- It gives the various features at single times like video, audio and sharing
of content as well for delivering of wonderful experiences to the executives of the
organisation in engagement in meetings. It gives the flawless experience to the
users which aids the teams for performing the activities in a effective way. By
this the teams can collaborate and connect in a quick way which assists them in
improving the productivity. It permits the business organisation for making the
changes in communicating and streamlining the relationships of business
effectively(Teubner and Stockhinger, 2020). Various establishments are using this
tools as it is very simple in use and aids them for meeting with the employees and
consumers on the time stipulated. It also aids the executives in transferring the file
and remove the unwanted attendees from the meeting quickly. Beside from this
Webex also provides the features like sharing of screen, recording of cloud and
storage as well. It also has features such as the digital whiteboarding which aids
the executives of the organisation for presenting the presentations while doing
of quick messaging. It gives 2 methods by which the employees may
communicate with the other employees and their seniors in the formal way. It
organizes the conversations of the firms in to the channels where the employee
may come at single place for the sharing of suggestions and take decisions in the
better way. It has built the art of assisting the members of the team for
concentration and establish the culture which increased the productivity in a
strategic way. For ex- Deliveroo a United Kingdom based food delivery service
uses Slack for the management of remote and distributed work force for
connecting throughout the process of business. Slack offers the various software
application which aids the adjoining of work force on the remote basis
effectually. Other example of using the Slack is Airbnb where it aids the
executive in integration of external 3 parties in a strategic way. Slack Huddles
might act as the alternative for the video conferencing as it gives excellent
experience to the executives of the organisation while doing interaction with the
employees and clients as well(Sousa and Rocha, 2019).
Webex- It gives the various features at single times like video, audio and sharing
of content as well for delivering of wonderful experiences to the executives of the
organisation in engagement in meetings. It gives the flawless experience to the
users which aids the teams for performing the activities in a effective way. By
this the teams can collaborate and connect in a quick way which assists them in
improving the productivity. It permits the business organisation for making the
changes in communicating and streamlining the relationships of business
effectively(Teubner and Stockhinger, 2020). Various establishments are using this
tools as it is very simple in use and aids them for meeting with the employees and
consumers on the time stipulated. It also aids the executives in transferring the file
and remove the unwanted attendees from the meeting quickly. Beside from this
Webex also provides the features like sharing of screen, recording of cloud and
storage as well. It also has features such as the digital whiteboarding which aids
the executives of the organisation for presenting the presentations while doing
remote work. For ex- the Boohoo Group Plc executives used the Webex for
organising the meetings and discussing the designs and other things. It also has
aided them in effectively in the lock down time when they worked remotely.
Discussing of the pros,cons, applications and suitability in context with the cloud computing in
improved process of digitalization
Cloud computing is refereed as the practice which is being used by the business
enterprise for hosting the various servers for managing the big data sets in the effective way.
Cloud computing is known as the vital establishments for protection of data and systems as well
from any cyber attack which is helpful for constant planning. It is significant as it assists in
assessment of sets of data in a fast way permitting them for conducting the operations of
business with reduced down time and increase in productivity. It also permits the employees for
being flexible in the working as it aids them for connecting with the virtual place of work
effectively(Sousa and Wilks, 2018).
Meanwhile the cloud storage is known as the model of computing used for the
information stockpiling in a strategic way. By this the users can upload retrieve and store the
data sets whenever required. Evaluation of the limitations, benefits, application and suitability
for the cloud storage and cloud computing is explained below-
Basis of Divergence Cloud Computing Cloud Storage
Meaning Cloud computing refers to the giving of
various services from internet like the
software , networking and servers.
Cloud storage is the sub part
of cloud computing which
assists in data storing for
upcoming use,
Advantages Cloud computing is very beneficial for
as it helps the firms for updating their
software & system by a automatic
It has various advantages
which are required for being
considered by the executives
organising the meetings and discussing the designs and other things. It also has
aided them in effectively in the lock down time when they worked remotely.
Discussing of the pros,cons, applications and suitability in context with the cloud computing in
improved process of digitalization
Cloud computing is refereed as the practice which is being used by the business
enterprise for hosting the various servers for managing the big data sets in the effective way.
Cloud computing is known as the vital establishments for protection of data and systems as well
from any cyber attack which is helpful for constant planning. It is significant as it assists in
assessment of sets of data in a fast way permitting them for conducting the operations of
business with reduced down time and increase in productivity. It also permits the employees for
being flexible in the working as it aids them for connecting with the virtual place of work
effectively(Sousa and Wilks, 2018).
Meanwhile the cloud storage is known as the model of computing used for the
information stockpiling in a strategic way. By this the users can upload retrieve and store the
data sets whenever required. Evaluation of the limitations, benefits, application and suitability
for the cloud storage and cloud computing is explained below-
Basis of Divergence Cloud Computing Cloud Storage
Meaning Cloud computing refers to the giving of
various services from internet like the
software , networking and servers.
Cloud storage is the sub part
of cloud computing which
assists in data storing for
upcoming use,
Advantages Cloud computing is very beneficial for
as it helps the firms for updating their
software & system by a automatic
It has various advantages
which are required for being
considered by the executives
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
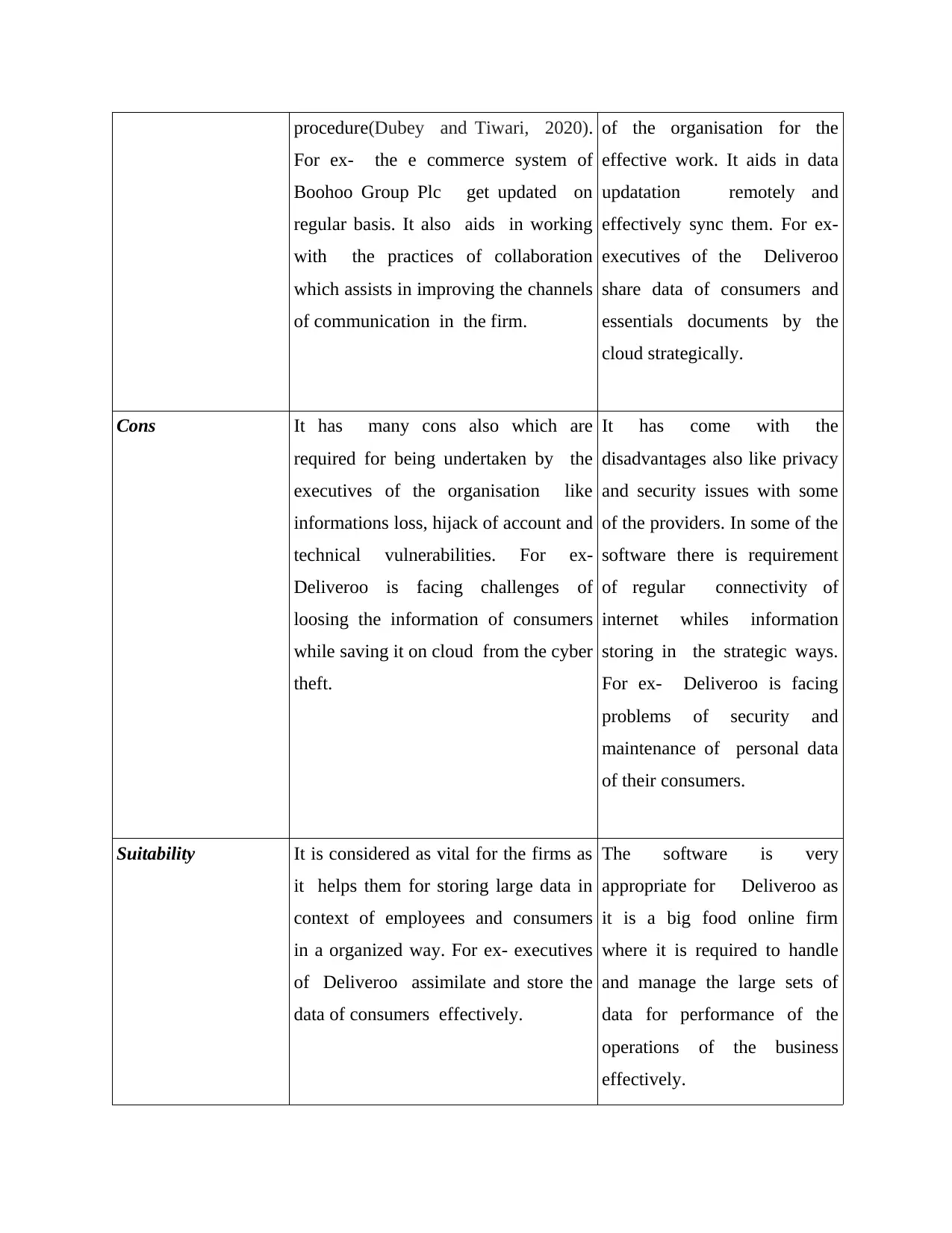
procedure(Dubey and Tiwari, 2020).
For ex- the e commerce system of
Boohoo Group Plc get updated on
regular basis. It also aids in working
with the practices of collaboration
which assists in improving the channels
of communication in the firm.
of the organisation for the
effective work. It aids in data
updatation remotely and
effectively sync them. For ex-
executives of the Deliveroo
share data of consumers and
essentials documents by the
cloud strategically.
Cons It has many cons also which are
required for being undertaken by the
executives of the organisation like
informations loss, hijack of account and
technical vulnerabilities. For ex-
Deliveroo is facing challenges of
loosing the information of consumers
while saving it on cloud from the cyber
theft.
It has come with the
disadvantages also like privacy
and security issues with some
of the providers. In some of the
software there is requirement
of regular connectivity of
internet whiles information
storing in the strategic ways.
For ex- Deliveroo is facing
problems of security and
maintenance of personal data
of their consumers.
Suitability It is considered as vital for the firms as
it helps them for storing large data in
context of employees and consumers
in a organized way. For ex- executives
of Deliveroo assimilate and store the
data of consumers effectively.
The software is very
appropriate for Deliveroo as
it is a big food online firm
where it is required to handle
and manage the large sets of
data for performance of the
operations of the business
effectively.
For ex- the e commerce system of
Boohoo Group Plc get updated on
regular basis. It also aids in working
with the practices of collaboration
which assists in improving the channels
of communication in the firm.
of the organisation for the
effective work. It aids in data
updatation remotely and
effectively sync them. For ex-
executives of the Deliveroo
share data of consumers and
essentials documents by the
cloud strategically.
Cons It has many cons also which are
required for being undertaken by the
executives of the organisation like
informations loss, hijack of account and
technical vulnerabilities. For ex-
Deliveroo is facing challenges of
loosing the information of consumers
while saving it on cloud from the cyber
theft.
It has come with the
disadvantages also like privacy
and security issues with some
of the providers. In some of the
software there is requirement
of regular connectivity of
internet whiles information
storing in the strategic ways.
For ex- Deliveroo is facing
problems of security and
maintenance of personal data
of their consumers.
Suitability It is considered as vital for the firms as
it helps them for storing large data in
context of employees and consumers
in a organized way. For ex- executives
of Deliveroo assimilate and store the
data of consumers effectively.
The software is very
appropriate for Deliveroo as
it is a big food online firm
where it is required to handle
and manage the large sets of
data for performance of the
operations of the business
effectively.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
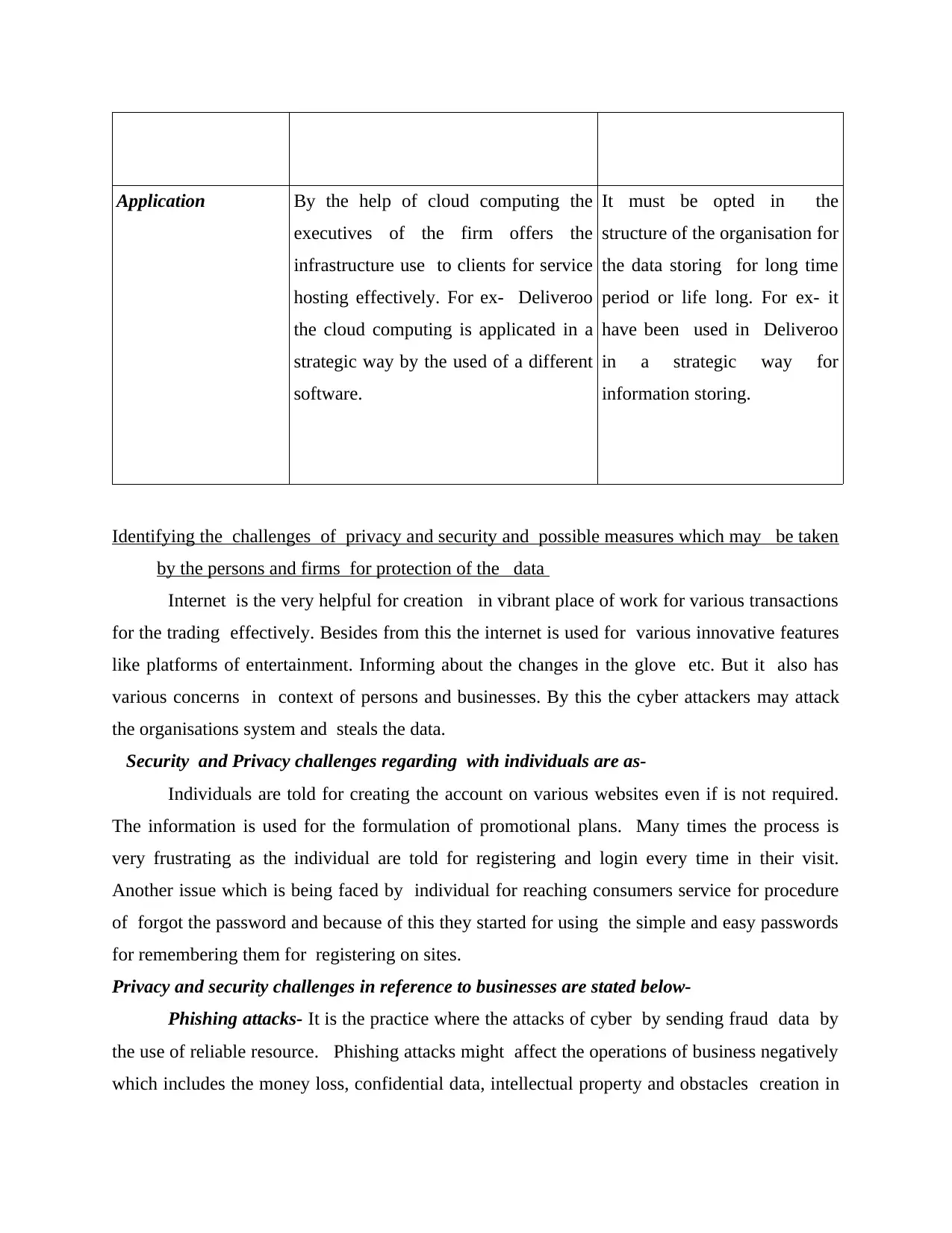
Application By the help of cloud computing the
executives of the firm offers the
infrastructure use to clients for service
hosting effectively. For ex- Deliveroo
the cloud computing is applicated in a
strategic way by the used of a different
software.
It must be opted in the
structure of the organisation for
the data storing for long time
period or life long. For ex- it
have been used in Deliveroo
in a strategic way for
information storing.
Identifying the challenges of privacy and security and possible measures which may be taken
by the persons and firms for protection of the data
Internet is the very helpful for creation in vibrant place of work for various transactions
for the trading effectively. Besides from this the internet is used for various innovative features
like platforms of entertainment. Informing about the changes in the glove etc. But it also has
various concerns in context of persons and businesses. By this the cyber attackers may attack
the organisations system and steals the data.
Security and Privacy challenges regarding with individuals are as-
Individuals are told for creating the account on various websites even if is not required.
The information is used for the formulation of promotional plans. Many times the process is
very frustrating as the individual are told for registering and login every time in their visit.
Another issue which is being faced by individual for reaching consumers service for procedure
of forgot the password and because of this they started for using the simple and easy passwords
for remembering them for registering on sites.
Privacy and security challenges in reference to businesses are stated below-
Phishing attacks- It is the practice where the attacks of cyber by sending fraud data by
the use of reliable resource. Phishing attacks might affect the operations of business negatively
which includes the money loss, confidential data, intellectual property and obstacles creation in
executives of the firm offers the
infrastructure use to clients for service
hosting effectively. For ex- Deliveroo
the cloud computing is applicated in a
strategic way by the used of a different
software.
It must be opted in the
structure of the organisation for
the data storing for long time
period or life long. For ex- it
have been used in Deliveroo
in a strategic way for
information storing.
Identifying the challenges of privacy and security and possible measures which may be taken
by the persons and firms for protection of the data
Internet is the very helpful for creation in vibrant place of work for various transactions
for the trading effectively. Besides from this the internet is used for various innovative features
like platforms of entertainment. Informing about the changes in the glove etc. But it also has
various concerns in context of persons and businesses. By this the cyber attackers may attack
the organisations system and steals the data.
Security and Privacy challenges regarding with individuals are as-
Individuals are told for creating the account on various websites even if is not required.
The information is used for the formulation of promotional plans. Many times the process is
very frustrating as the individual are told for registering and login every time in their visit.
Another issue which is being faced by individual for reaching consumers service for procedure
of forgot the password and because of this they started for using the simple and easy passwords
for remembering them for registering on sites.
Privacy and security challenges in reference to businesses are stated below-
Phishing attacks- It is the practice where the attacks of cyber by sending fraud data by
the use of reliable resource. Phishing attacks might affect the operations of business negatively
which includes the money loss, confidential data, intellectual property and obstacles creation in

the activities of the firm. Many firms in the world are suffering from the breach of data which is
streamline by attacks of phishing. But the attack may be done by the employees is also besides
from attackers as they know everything about the passwords and work. For ex- British Airways
official site was once hacked and converted in fraud site by the attackers. By this the data of
their clients was stolen by the phishers(Mishra and et, al., 2019).
This attack is done in different scenario like the email, phishing by clone and spoofing of
domain. As the email phishing the attacker may get access of personal data of clients of the
firms. By the clone phishing the attackers make the digital clone of email messages and replace
them with the bad one strategically. In the domain spoofing case the attackers spoof the names
of specific firms where the person get messages from the parent firm.
Weak passwords- This is to be consider as biggest threat for an enterprise as the practice
is consider as the invitation to cyber criminals for attack on the system and they can stole their
confidential information. This becomes problematic for relying on passwords to maintain
security. This is easy for remembering and devising various accounts with the assistance of
virtual aspects. Simple and weak password have a threat for breach, data, account take over and
other related aspects for cyber attack. As example, Deliveroo faces this kind of cyber attack at
time of doing the operations. From this, the confidential information is being stole and used for
wrong practices deal with employees of Marriott(Ihmeideh and Al-Maadadi, 2018).
Potential measures which are undertaken by businesses and individuals for protecting
themselves from varied issues are as follows:
Train staff members in an effective manner- It has been seen that, the most easy manner
which is used by the cyber criminals for accessing the data of the organisation is from the
workers(Beetham and Sharpe, 2019). It is very essential for the management to provide training
to the employees in such a manner that they are able to avoid or minimise the data breaches and
cyber attacks from the criminals. It is recommended to the workforce to use their common sense
before clicking on any link which is malicious or seems fraudulent. For example, the workers of
the British Airways should be provided proper training so that they can contribute in eliminating
the practices of information breach with regard to the business operations(Christians, 2019).
Keep software updated- The cyber criminals identifies the areas where the organisation
has weakness such as not updating the software on a regular time period. It is imperative for the
streamline by attacks of phishing. But the attack may be done by the employees is also besides
from attackers as they know everything about the passwords and work. For ex- British Airways
official site was once hacked and converted in fraud site by the attackers. By this the data of
their clients was stolen by the phishers(Mishra and et, al., 2019).
This attack is done in different scenario like the email, phishing by clone and spoofing of
domain. As the email phishing the attacker may get access of personal data of clients of the
firms. By the clone phishing the attackers make the digital clone of email messages and replace
them with the bad one strategically. In the domain spoofing case the attackers spoof the names
of specific firms where the person get messages from the parent firm.
Weak passwords- This is to be consider as biggest threat for an enterprise as the practice
is consider as the invitation to cyber criminals for attack on the system and they can stole their
confidential information. This becomes problematic for relying on passwords to maintain
security. This is easy for remembering and devising various accounts with the assistance of
virtual aspects. Simple and weak password have a threat for breach, data, account take over and
other related aspects for cyber attack. As example, Deliveroo faces this kind of cyber attack at
time of doing the operations. From this, the confidential information is being stole and used for
wrong practices deal with employees of Marriott(Ihmeideh and Al-Maadadi, 2018).
Potential measures which are undertaken by businesses and individuals for protecting
themselves from varied issues are as follows:
Train staff members in an effective manner- It has been seen that, the most easy manner
which is used by the cyber criminals for accessing the data of the organisation is from the
workers(Beetham and Sharpe, 2019). It is very essential for the management to provide training
to the employees in such a manner that they are able to avoid or minimise the data breaches and
cyber attacks from the criminals. It is recommended to the workforce to use their common sense
before clicking on any link which is malicious or seems fraudulent. For example, the workers of
the British Airways should be provided proper training so that they can contribute in eliminating
the practices of information breach with regard to the business operations(Christians, 2019).
Keep software updated- The cyber criminals identifies the areas where the organisation
has weakness such as not updating the software on a regular time period. It is imperative for the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

managers of the companies to properly update the software for protecting the system from cyber
attacks.
Backup of data- In regard to any cyber attack, there should be a backup of the
information and data prior to the attack which assists in avoiding the downtime and also the
financial loss which can be suffered by the organisation. For example, the managers of Deliveroo
should keep backup of their data in a systematic manner which will help them to avoid loss of
their relevant information in case of any cyber attacks(Liu and Ko, 2019).
The individuals should also pay attention when performing any transaction online. The
should protect the passwords in such a way that it cannot be accessed by anyone else. They
should not click on any link unknowingly since it can negatively impact the personal information
of the bank details.
Discussion of bubble bursting procedure of cryptocurrency with proper justification
Cryptocurrency can be defined as a virtual currency which is used as an secondary option
for payment. It is developed by using the algorithms which are encrypted. It helps the
cryptocurrencies in working as a currency and digital accounting system. It is not regulated or
governed by any body rather it uses decentralised system for recording the transactions.
In the financial language, bubble can be considered as a state where the asset remains stable for a
long time period and then grows eventually. Burst can be termed as state where the price of the
asset quickly reduces. The cause of these bubbles and burst are considered a riskiest source of
investment for the investors as business housed are very slow in processing the adoption of
blockchain systems. The governments of different nations have not recognised cryptocurrencies
as standard system of payment as it is very risky in nature.
Tether which is a multibillion dollar stable coin and is considered as largest bank in the
cryptocurrency economy has also withdraws cash in May due to the crash of market. It is very
certain that bubble bursting lead to drastically decrease in the prices in the market. It is also very
clear with the example of Tether that cryptocurrencies performs in the approach of bubble
bursting. It has also be witnessed that other cryptocurrencies like Bitcoin and Ethereum are also
experiencing downtime from beginning of May. For example, Bitcoin has fell down below
attacks.
Backup of data- In regard to any cyber attack, there should be a backup of the
information and data prior to the attack which assists in avoiding the downtime and also the
financial loss which can be suffered by the organisation. For example, the managers of Deliveroo
should keep backup of their data in a systematic manner which will help them to avoid loss of
their relevant information in case of any cyber attacks(Liu and Ko, 2019).
The individuals should also pay attention when performing any transaction online. The
should protect the passwords in such a way that it cannot be accessed by anyone else. They
should not click on any link unknowingly since it can negatively impact the personal information
of the bank details.
Discussion of bubble bursting procedure of cryptocurrency with proper justification
Cryptocurrency can be defined as a virtual currency which is used as an secondary option
for payment. It is developed by using the algorithms which are encrypted. It helps the
cryptocurrencies in working as a currency and digital accounting system. It is not regulated or
governed by any body rather it uses decentralised system for recording the transactions.
In the financial language, bubble can be considered as a state where the asset remains stable for a
long time period and then grows eventually. Burst can be termed as state where the price of the
asset quickly reduces. The cause of these bubbles and burst are considered a riskiest source of
investment for the investors as business housed are very slow in processing the adoption of
blockchain systems. The governments of different nations have not recognised cryptocurrencies
as standard system of payment as it is very risky in nature.
Tether which is a multibillion dollar stable coin and is considered as largest bank in the
cryptocurrency economy has also withdraws cash in May due to the crash of market. It is very
certain that bubble bursting lead to drastically decrease in the prices in the market. It is also very
clear with the example of Tether that cryptocurrencies performs in the approach of bubble
bursting. It has also be witnessed that other cryptocurrencies like Bitcoin and Ethereum are also
experiencing downtime from beginning of May. For example, Bitcoin has fell down below
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

$26,000 in last 16 months for the first time (Bitcoin crash: Market anomaly or bubble burst,
2022). Even the exchange platforms which acts as mediators of transaction have also seen
downward trend in their performance.
Stable coins are regarded as the true source in relation to the crypto world which involves
a large segment of trading volumes of assets in a digital form.
Tokens are considered as a prime instrument which can be used for making the payments,
lending from any person and other related activities. All these are based on blockchain
technology(Guillén-Gámez and et, al., 2021).
Ethereum is regarded as the most powerful cryptocurrency in the market and it is also on
the verge of bursting and exploding in a proper manner. This artificial currency is considered as
highly volatile which keeps the money of the investors in a riskiest situation.
However, market analyst have predicted that the rise and fall of Ethereum and Bitcoin prices are
not considered for bubble bursting as these are on the verge of inflation hedge. Bitcoin has been
tagged a safe option for the investors since its adoption has been increasing in a significant
manner. Ethereum does not have a fixed supply even though the coin burning has made this
cryptocurrency rare(Huda, 2018).
2022). Even the exchange platforms which acts as mediators of transaction have also seen
downward trend in their performance.
Stable coins are regarded as the true source in relation to the crypto world which involves
a large segment of trading volumes of assets in a digital form.
Tokens are considered as a prime instrument which can be used for making the payments,
lending from any person and other related activities. All these are based on blockchain
technology(Guillén-Gámez and et, al., 2021).
Ethereum is regarded as the most powerful cryptocurrency in the market and it is also on
the verge of bursting and exploding in a proper manner. This artificial currency is considered as
highly volatile which keeps the money of the investors in a riskiest situation.
However, market analyst have predicted that the rise and fall of Ethereum and Bitcoin prices are
not considered for bubble bursting as these are on the verge of inflation hedge. Bitcoin has been
tagged a safe option for the investors since its adoption has been increasing in a significant
manner. Ethereum does not have a fixed supply even though the coin burning has made this
cryptocurrency rare(Huda, 2018).

CONCLUSION
It can be concluded from the report that , information and communication technology
plays a very crucial role in transforming the operations of the business. There are various
collaborative methods which are very essential in helping the managers of the organisation in
addressing the issue and solving the problems. The two collaborative tools which are mostly
used by the companies are Slack and Webex. The internet provides various features such as
accessing the large data sets, entertainment and many more. It has also gave opportunity to
various privacy and security issues in the business organisations like weak passwords, insider
threats and phishing attacks. Cyber attack is regarded as a intentional exploitation of system and
the networks. Cloud computing is related to providing differential networks and servers to the
businesses for keeping the information. Cloud Storage is considered as an essential aspect of
keeping the back up of information in a systematic manner. Cryptocurrencies are considered as
very riskiest market where investments have to be done through critical evaluation in an effective
manner.
It can be concluded from the report that , information and communication technology
plays a very crucial role in transforming the operations of the business. There are various
collaborative methods which are very essential in helping the managers of the organisation in
addressing the issue and solving the problems. The two collaborative tools which are mostly
used by the companies are Slack and Webex. The internet provides various features such as
accessing the large data sets, entertainment and many more. It has also gave opportunity to
various privacy and security issues in the business organisations like weak passwords, insider
threats and phishing attacks. Cyber attack is regarded as a intentional exploitation of system and
the networks. Cloud computing is related to providing differential networks and servers to the
businesses for keeping the information. Cloud Storage is considered as an essential aspect of
keeping the back up of information in a systematic manner. Cryptocurrencies are considered as
very riskiest market where investments have to be done through critical evaluation in an effective
manner.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

