College of Computing And Informatics Reports
VerifiedAdded on 2022/09/09
|5
|1761
|16
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Assignmen
t 3
College of Computing and Informatics
Student Details:
Name: Ayman Rafa Alamri
CRN: 21422
ID: 160079583
Instructions:
You must submit two separate copies (one Word file and one PDF file) using the Assignment Template on
Blackboard via the allocated folder. These files must not be in compressed format.
It is your responsibility to check and make sure that you have uploaded both the correct files.
Zero mark will be given if you try to bypass the SafeAssign (e.g. misspell words, remove spaces between words,
hide characters, use different character sets or languages other than English or any kind of manipulation).
Email submission will not be accepted.
You are advised to make your work clear and well-presented. This includes filling your information on the cover
page.
You must use this template, failing which will result in zero mark.
You MUST show all your work, and text must not be converted into an image, unless specified otherwise by the
question.
Late submission will result in ZERO mark.
The work should be your own, copying from students or other resources will result in ZERO mark.
Use Times New Roman font for all your answers.
E-Portals Development
IT405
t 3
College of Computing and Informatics
Student Details:
Name: Ayman Rafa Alamri
CRN: 21422
ID: 160079583
Instructions:
You must submit two separate copies (one Word file and one PDF file) using the Assignment Template on
Blackboard via the allocated folder. These files must not be in compressed format.
It is your responsibility to check and make sure that you have uploaded both the correct files.
Zero mark will be given if you try to bypass the SafeAssign (e.g. misspell words, remove spaces between words,
hide characters, use different character sets or languages other than English or any kind of manipulation).
Email submission will not be accepted.
You are advised to make your work clear and well-presented. This includes filling your information on the cover
page.
You must use this template, failing which will result in zero mark.
You MUST show all your work, and text must not be converted into an image, unless specified otherwise by the
question.
Late submission will result in ZERO mark.
The work should be your own, copying from students or other resources will result in ZERO mark.
Use Times New Roman font for all your answers.
E-Portals Development
IT405
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Pg. 1 Question ThreeQuestion Three
Question One
What is the difference between synchronous and asynchronous web methods?
Give an example of synchronous and asynchronous web methods? How can
we transform a synchronous web method to asynchronous web methods?
Synchronous web method are the type of execution that deals with direct query and
response system between client and server. In this communication, client sends request
to the server and wits until the server sends back the acknowledgement. The main
advantage of this method that it saves time for the overall operation (Niwa et al. 2015).
Some of the example of the Synchronous web methods are IP calling, Video calls,
login operations, website browsing, web user interface etc.
On other hand, the asynchronous operation takes time for the overall execution
of the process request. However in this method all the parties does not need to be
present at the same time to communicate. It does not require acknowledgement from
the server side to proceed the communication. This type of method is widely used in
the message and text based communication (Morton et al. 2018).Email is great
example of asynchronous web method where the presence of receiving party is not
required to receive the ml from the sender.
Web services only allow synchronous mode of operation. However using
synchronous method, it can be converted into asynchronous method. In between the
request and response message a correlation identifier is established. A refractor
receives the request at server end, sends it to the queue for processing later and
instantly sends acknowledge to the sender. When the response of the queued messages
are ready, the replies are sent to the address of the received messages. The correlation
identifier is used to identify the sender who has sent the request.
Learning
Outcome(s):
Recognize the
main elements of
portals
development.
1.5 Marks
Question One
What is the difference between synchronous and asynchronous web methods?
Give an example of synchronous and asynchronous web methods? How can
we transform a synchronous web method to asynchronous web methods?
Synchronous web method are the type of execution that deals with direct query and
response system between client and server. In this communication, client sends request
to the server and wits until the server sends back the acknowledgement. The main
advantage of this method that it saves time for the overall operation (Niwa et al. 2015).
Some of the example of the Synchronous web methods are IP calling, Video calls,
login operations, website browsing, web user interface etc.
On other hand, the asynchronous operation takes time for the overall execution
of the process request. However in this method all the parties does not need to be
present at the same time to communicate. It does not require acknowledgement from
the server side to proceed the communication. This type of method is widely used in
the message and text based communication (Morton et al. 2018).Email is great
example of asynchronous web method where the presence of receiving party is not
required to receive the ml from the sender.
Web services only allow synchronous mode of operation. However using
synchronous method, it can be converted into asynchronous method. In between the
request and response message a correlation identifier is established. A refractor
receives the request at server end, sends it to the queue for processing later and
instantly sends acknowledge to the sender. When the response of the queued messages
are ready, the replies are sent to the address of the received messages. The correlation
identifier is used to identify the sender who has sent the request.
Learning
Outcome(s):
Recognize the
main elements of
portals
development.
1.5 Marks

Pg. 2 Question ThreeQuestion Three
Question Two
What is web cache? How a web cache work? Give an example of how a web
cache can assist a web portal (considering any busy website, explain how
caching can improve its performance)
A web cache can be a hardware device or software that stores the temporary
important data or static content of the most frequently visited website. It preloads the
contents when the websites are visited again (Songwattana, Theeramunkong and Vinh
2014). Ultimately storing cache data improves the response time of the operation and
less work for browser.
When a website and its contents are loaded from the main server in the browser,
a copy of the source file is stored within this cache memory. The storing is set for a
limited time which can be set by the users. Next whenever the website is visited again,
if the requested contents is stored in the cache memory then the web cache sends. It
does not require to go to the main server and load the contents again. If the requested is
not found in the cache memory then it redirect the user to the main server to load the
contents again in the browser (Trinh, Wu and Huang 2019). Again if the contents are
cacheable then web caches stores a copy of the content for future requests.
For example a busy social media website, where the contents of the home page
are not cacheable as it always shows new feeds. However the addition of the new feeds
are not very fast. The existing feeds and posts can be cacheable and when the user will
open the site it can show cached contents. After reloading or refreshing the webpage, it
will reach to the original server for latest feeds. On the web-based apps, this simple
features are used for better performance.
Learning
Outcome(s):
Evaluate the
effectiveness of
portals.
2 Marks
Question Two
What is web cache? How a web cache work? Give an example of how a web
cache can assist a web portal (considering any busy website, explain how
caching can improve its performance)
A web cache can be a hardware device or software that stores the temporary
important data or static content of the most frequently visited website. It preloads the
contents when the websites are visited again (Songwattana, Theeramunkong and Vinh
2014). Ultimately storing cache data improves the response time of the operation and
less work for browser.
When a website and its contents are loaded from the main server in the browser,
a copy of the source file is stored within this cache memory. The storing is set for a
limited time which can be set by the users. Next whenever the website is visited again,
if the requested contents is stored in the cache memory then the web cache sends. It
does not require to go to the main server and load the contents again. If the requested is
not found in the cache memory then it redirect the user to the main server to load the
contents again in the browser (Trinh, Wu and Huang 2019). Again if the contents are
cacheable then web caches stores a copy of the content for future requests.
For example a busy social media website, where the contents of the home page
are not cacheable as it always shows new feeds. However the addition of the new feeds
are not very fast. The existing feeds and posts can be cacheable and when the user will
open the site it can show cached contents. After reloading or refreshing the webpage, it
will reach to the original server for latest feeds. On the web-based apps, this simple
features are used for better performance.
Learning
Outcome(s):
Evaluate the
effectiveness of
portals.
2 Marks
Pg. 3 Question ThreeQuestion Three
Question Three
What is a reasonable web hosting configuration? Draw/picture a typical
configuration. Give any two reasons why is it a reasonable configurations?
A reasonable configuration for web hosting depends on the requirement, such
as the number of websites, bandwidth requirement, operating system of the server
system, size of the resources etc. (Sutanto 2018). For a single website with adequate
size the reasonable configuration of the web hosting can include: A processor, memory
4 GB, storage 500 GB, Linux based operating system, 2 MB bandwidth etc. Normally
for the SSL or only http base websites can have 1-2 IP. However for more security
dedicated IPs are required for each of the secure sites. If a machine is chosen for
hosting, it should only do the hosting part. A backup of the website resource file
should be ready made in a 500 GB hard disk drive. A separate database server can be
ideal to achieve more security metrics. It has a separate firewall, multiple layer of
authentication and encrypted data. A typical configuration of a web hosting is shown
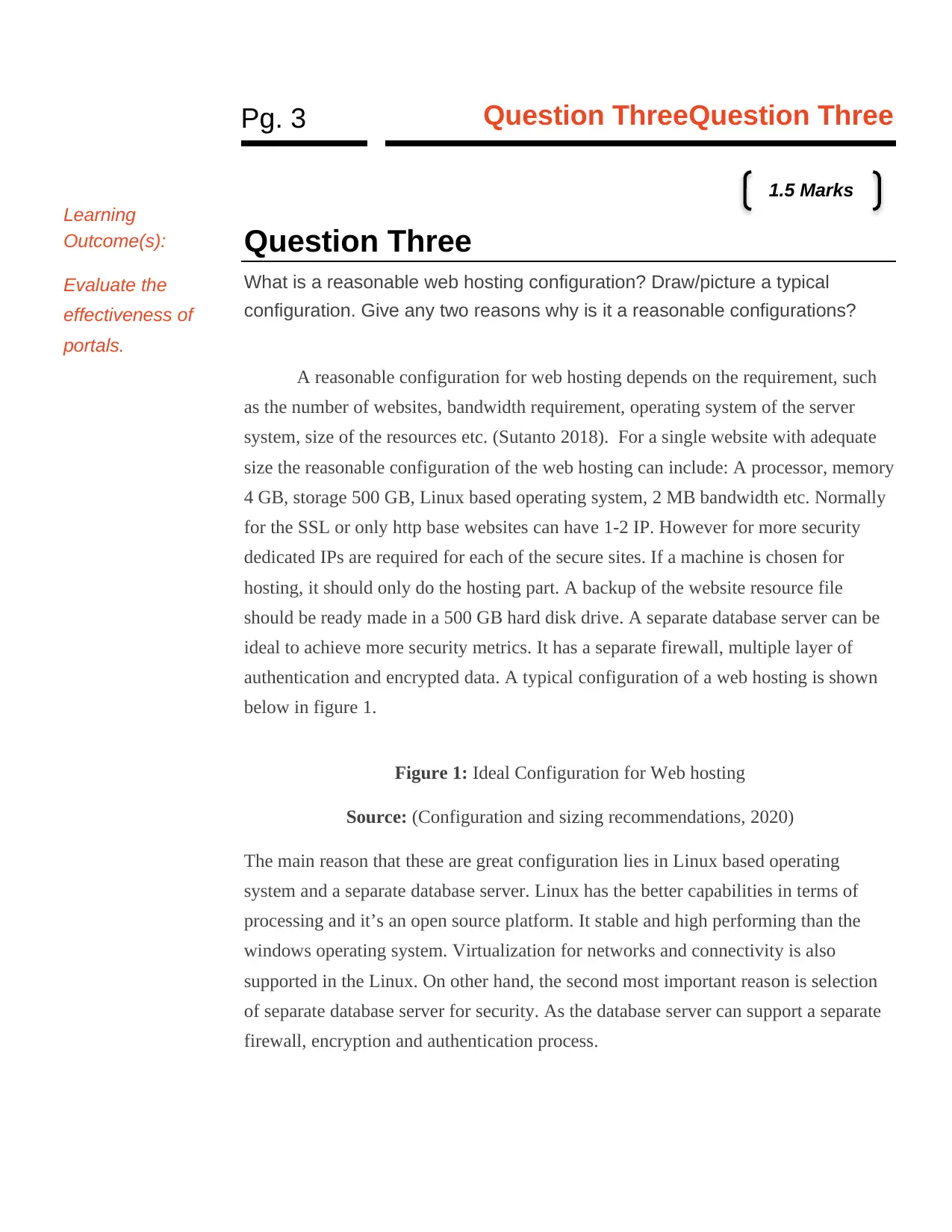
below in figure 1.
Figure 1: Ideal Configuration for Web hosting
Source: (Configuration and sizing recommendations, 2020)
The main reason that these are great configuration lies in Linux based operating
system and a separate database server. Linux has the better capabilities in terms of
processing and it’s an open source platform. It stable and high performing than the
windows operating system. Virtualization for networks and connectivity is also
supported in the Linux. On other hand, the second most important reason is selection
of separate database server for security. As the database server can support a separate
firewall, encryption and authentication process.
Learning
Outcome(s):
Evaluate the
effectiveness of
portals.
1.5 Marks
Question Three
What is a reasonable web hosting configuration? Draw/picture a typical
configuration. Give any two reasons why is it a reasonable configurations?
A reasonable configuration for web hosting depends on the requirement, such
as the number of websites, bandwidth requirement, operating system of the server
system, size of the resources etc. (Sutanto 2018). For a single website with adequate
size the reasonable configuration of the web hosting can include: A processor, memory
4 GB, storage 500 GB, Linux based operating system, 2 MB bandwidth etc. Normally
for the SSL or only http base websites can have 1-2 IP. However for more security
dedicated IPs are required for each of the secure sites. If a machine is chosen for
hosting, it should only do the hosting part. A backup of the website resource file
should be ready made in a 500 GB hard disk drive. A separate database server can be
ideal to achieve more security metrics. It has a separate firewall, multiple layer of
authentication and encrypted data. A typical configuration of a web hosting is shown
below in figure 1.
Figure 1: Ideal Configuration for Web hosting
Source: (Configuration and sizing recommendations, 2020)
The main reason that these are great configuration lies in Linux based operating
system and a separate database server. Linux has the better capabilities in terms of
processing and it’s an open source platform. It stable and high performing than the
windows operating system. Virtualization for networks and connectivity is also
supported in the Linux. On other hand, the second most important reason is selection
of separate database server for security. As the database server can support a separate
firewall, encryption and authentication process.
Learning
Outcome(s):
Evaluate the
effectiveness of
portals.
1.5 Marks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Pg. 4 Question ThreeQuestion Three
References
Morton, M., Werner, J., Kintis, P., Snow, K., Antonakakis, M., Polychronakis, M. and
Monrose, F., 2018, April. Security risks in asynchronous web servers: When
performance optimizations amplify the impact of data-oriented attacks. In 2018 IEEE
European Symposium on Security and Privacy (EuroS&P) (pp. 167-182). IEEE.
Niwa, I., Osaragi, T., Oki, T. and Hirokawa, N., 2015. Development of Real Time
Synchronous Web Application for Posting and Utilizing Disaster Information.
In ISCRAM.
RStudio Support. 2020. Configuration And Sizing Recommendations. [online]
Available at: <https://support.rstudio.com/hc/en-us/articles/115002344588-
Configuration-and-sizing-recommendations> [Accessed 31 March 2020].
Songwattana, A., Theeramunkong, T. and Vinh, P.C., 2014. A learning-based approach
for web cache management. Mobile Networks and Applications, 19(2), pp.258-271.
Sutanto, F.I., 2018. WEB HOSTING USE ISPCONFIG (Doctoral dissertation, Unika
Soegijapranata Semarang).
Trinh, T., Wu, D. and Huang, J.Z., 2019. C3C: A New Static Content-Based Three-
Level Web Cache. IEEE Access, 7, pp.11796-11808.
References
Morton, M., Werner, J., Kintis, P., Snow, K., Antonakakis, M., Polychronakis, M. and
Monrose, F., 2018, April. Security risks in asynchronous web servers: When
performance optimizations amplify the impact of data-oriented attacks. In 2018 IEEE
European Symposium on Security and Privacy (EuroS&P) (pp. 167-182). IEEE.
Niwa, I., Osaragi, T., Oki, T. and Hirokawa, N., 2015. Development of Real Time
Synchronous Web Application for Posting and Utilizing Disaster Information.
In ISCRAM.
RStudio Support. 2020. Configuration And Sizing Recommendations. [online]
Available at: <https://support.rstudio.com/hc/en-us/articles/115002344588-
Configuration-and-sizing-recommendations> [Accessed 31 March 2020].
Songwattana, A., Theeramunkong, T. and Vinh, P.C., 2014. A learning-based approach
for web cache management. Mobile Networks and Applications, 19(2), pp.258-271.
Sutanto, F.I., 2018. WEB HOSTING USE ISPCONFIG (Doctoral dissertation, Unika
Soegijapranata Semarang).
Trinh, T., Wu, D. and Huang, J.Z., 2019. C3C: A New Static Content-Based Three-
Level Web Cache. IEEE Access, 7, pp.11796-11808.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





