Commonwealth Bank of Australia Risk Assessment - Employee Devices
VerifiedAdded on 2020/04/01
|23
|5966
|42
Report
AI Summary
This report provides a detailed risk assessment of Commonwealth Bank of Australia's (CBA) implementation of an employee personal device (BYOD) policy. It examines the potential benefits, such as increased employee productivity and reduced hardware costs, alongside the significant risks, including data security breaches, device disparities, and potential costs for employees. The report delves into CBA's security posture, analyzing threats, vulnerabilities, and the potential consequences of security compromises. It explores data security risks in the context of financial services, legal and systematic risks. The report also discusses reasons for implementing a BYOD policy, the importance of monitoring, and the need for regulatory policies. The report concludes with a discussion on the return on investment (ROI) and the necessity for CBA to carefully evaluate the project's implications, develop comprehensive policies, and notify employees about the project's terms.

Commonwealth Bank of Australia Risk Assessment- Employee Personal Devices
Name
Institutional Affiliation
Date
Name
Institutional Affiliation
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

EXECUTIVE SUMMARY
As modern organizations continue to operate in the in the ever competitive environments, they
have been forced to come up with various strategies to meet current workplace demands. Among
the strategies that have been adopted by organizations is the use of technology in their
operations. The increase in the adoption of technology by organizations has come along with
associated risks touching on company’s data such as Data security risks. In Australia, for
example, data security has been an area of focus for many businesses especially due to the
significant rise in the cases of cyber crimes (Zahadat et al, 2015). Data security refers to all
digital privacy measures put in place to prohibit unauthorized persons to access computers
websites and databases. Data security which is also aimed at preventing data corruption has been
viewed as an essential component of all organizations using technology. Data security is also
referred to as IT security. Commonwealth Bank of Australia is a leading integrated financial
services provider that has branches in Europe, North America, New Zealand and Asia. The bank
offers some financial services, including share broking, funds management, business,
institutional, premium and retail banking, insurance and superannuation products and services
(Ballagas,et al,2014)
The Company among other guarantees provides its clients with 100% security guarantee about
their personal information and money. Among other strategies adopted by the company include
outsourcing for cyber security to reduce costs a move which has seen the Bank contemplate on
moving a number of its members of staff and functions related to its IT security to an offshore
location in India. In this, the company is focused on managing security assess by real-time
As modern organizations continue to operate in the in the ever competitive environments, they
have been forced to come up with various strategies to meet current workplace demands. Among
the strategies that have been adopted by organizations is the use of technology in their
operations. The increase in the adoption of technology by organizations has come along with
associated risks touching on company’s data such as Data security risks. In Australia, for
example, data security has been an area of focus for many businesses especially due to the
significant rise in the cases of cyber crimes (Zahadat et al, 2015). Data security refers to all
digital privacy measures put in place to prohibit unauthorized persons to access computers
websites and databases. Data security which is also aimed at preventing data corruption has been
viewed as an essential component of all organizations using technology. Data security is also
referred to as IT security. Commonwealth Bank of Australia is a leading integrated financial
services provider that has branches in Europe, North America, New Zealand and Asia. The bank
offers some financial services, including share broking, funds management, business,
institutional, premium and retail banking, insurance and superannuation products and services
(Ballagas,et al,2014)
The Company among other guarantees provides its clients with 100% security guarantee about
their personal information and money. Among other strategies adopted by the company include
outsourcing for cyber security to reduce costs a move which has seen the Bank contemplate on
moving a number of its members of staff and functions related to its IT security to an offshore
location in India. In this, the company is focused on managing security assess by real-time

monitoring the use of technology by staff as well as monitoring threats within and without the
bank (Smith, 2009).Bring your own device is a concept utilized in a situation where employees
are allowed to come in the workplace to go with personal devices such as computers, smart
phones, and tablets to be used in undertaking the daily activities. Allowing employees to bring
their own personal; devices at the workplace have been the cause of some of the challenges faced
by modern organizations with it has come some threats leading to the establishment of bringing
your own devices aimed at regulating access to organizational, technological resources using
their devices. Allowing employees to bring their devices might have a positive bearing on the
organization whose technology endowment is inadequate by enabling employees to come with
superior devices that can help in increasing efficiency and the overall productivity. On the other
hand, such a move can be detrimental to an organization’s health by making its data and
technologies prone to abuse from outside the organization (Chin, et al,2011)By deploying this
project, Commonwealth Bank of Australia will achieve both advantages and disadvantages.
Among the expected benefits is the flexibility that comes with the use of personal devices,
minimizing operational costs and increased efficiency due to technological familiarity. Problems
that will accrue to the organization as a result of this move include compromised security, device
disparities whereby employees use different devices and finally it might be an extra cost to
employees, especially those who might not be in possession of such devices.
bank (Smith, 2009).Bring your own device is a concept utilized in a situation where employees
are allowed to come in the workplace to go with personal devices such as computers, smart
phones, and tablets to be used in undertaking the daily activities. Allowing employees to bring
their own personal; devices at the workplace have been the cause of some of the challenges faced
by modern organizations with it has come some threats leading to the establishment of bringing
your own devices aimed at regulating access to organizational, technological resources using
their devices. Allowing employees to bring their devices might have a positive bearing on the
organization whose technology endowment is inadequate by enabling employees to come with
superior devices that can help in increasing efficiency and the overall productivity. On the other
hand, such a move can be detrimental to an organization’s health by making its data and
technologies prone to abuse from outside the organization (Chin, et al,2011)By deploying this
project, Commonwealth Bank of Australia will achieve both advantages and disadvantages.
Among the expected benefits is the flexibility that comes with the use of personal devices,
minimizing operational costs and increased efficiency due to technological familiarity. Problems
that will accrue to the organization as a result of this move include compromised security, device
disparities whereby employees use different devices and finally it might be an extra cost to
employees, especially those who might not be in possession of such devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Table of Contents
EXECUTIVE SUMMARY.................................................................................................................................2
REVIEW OF THE PROJECT............................................................................................................................5
SECURITY POSTURE.....................................................................................................................................6
THREATS, VULNERABILITIES, AND CONSEQUENCES....................................................................................9
DATA SECURITY RISKS................................................................................................................................14
CONCLUSION.............................................................................................................................................15
REFERENCES..............................................................................................................................................16
EXECUTIVE SUMMARY.................................................................................................................................2
REVIEW OF THE PROJECT............................................................................................................................5
SECURITY POSTURE.....................................................................................................................................6
THREATS, VULNERABILITIES, AND CONSEQUENCES....................................................................................9
DATA SECURITY RISKS................................................................................................................................14
CONCLUSION.............................................................................................................................................15
REFERENCES..............................................................................................................................................16
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REVIEW OF THE PROJECT
Financial services refer to a range of financial services provided by various players in the
financial industry. They include services provided by banks, insurance companies, and
government-sponsored enterprises among others. In broad terms, institutions operating in the
financial sector are regarded as highly sensitive especially with regards to the security of their
systems. Financial service providers are virtually present all over the world even in remote areas
to satisfy the financial needs of individuals, groups, companies and other institutions (Gustav &
Kabanda,2016). The intermediary role played by financial service industry in Australia’s
economy is quite significant. Individuals, government agencies, businesses and nonprofit
organizations rely on this sector to either get funds when need be or dispose of excess cash
which is then lent out to those who need it, technologists play a significant role in facilitating this
transaction.
Clients .Clients are the most important asset to the Commonwealth Bank of Australia. The bank
is focused on establishing lasting cordial relationships with its various clients both depositors and
debtors. The bank's clients include retail clients, institutional investors, financial sponsors,
entrepreneurs, and corporations. Implementation of the project would mean that these client’s
needs attended to at any given time and with much efficiency (Felt,et al,2011)
Employees. Employees are an important shareholder and an important asset to the bank. The
company is focused on nurturing and developing the professional capability of their employees.
The project might be limiting to employees to employees without such devices and an
opportunity for those with the devices to enhance their professional prowess
Financial services refer to a range of financial services provided by various players in the
financial industry. They include services provided by banks, insurance companies, and
government-sponsored enterprises among others. In broad terms, institutions operating in the
financial sector are regarded as highly sensitive especially with regards to the security of their
systems. Financial service providers are virtually present all over the world even in remote areas
to satisfy the financial needs of individuals, groups, companies and other institutions (Gustav &
Kabanda,2016). The intermediary role played by financial service industry in Australia’s
economy is quite significant. Individuals, government agencies, businesses and nonprofit
organizations rely on this sector to either get funds when need be or dispose of excess cash
which is then lent out to those who need it, technologists play a significant role in facilitating this
transaction.
Clients .Clients are the most important asset to the Commonwealth Bank of Australia. The bank
is focused on establishing lasting cordial relationships with its various clients both depositors and
debtors. The bank's clients include retail clients, institutional investors, financial sponsors,
entrepreneurs, and corporations. Implementation of the project would mean that these client’s
needs attended to at any given time and with much efficiency (Felt,et al,2011)
Employees. Employees are an important shareholder and an important asset to the bank. The
company is focused on nurturing and developing the professional capability of their employees.
The project might be limiting to employees to employees without such devices and an
opportunity for those with the devices to enhance their professional prowess

There are some legislation that would determine the ability of Commonwealth Bank of Australia
to implement the project which includes Archives Act 1983, Privacy Act 1988 and Freedom of
Information Act 1982 which were established as a necessity as a result of the risks that emanate
from allowing employees to bring own devices at the workplace. If it can implement the project,
the Bank will, therefore, be required to put in place certain control measures to ensure that it
meets all legal obligations (Watkins, 2014). The bank would, therefore, be required to examine
the implications of the project to both the business and its overall security. As per best standards
requirements, commonwealth bank of Australia would be required to determine the implication
of the project by analyzing an already existing real example, identify the existing regulations and
legislation to facilitate compliance, put in place various support measures, both financial and
technical and finally roll out the project. The realization of this is solely dependent on the ICT
department or the technological department of the Bank. Financial institutions are affected by
many risks which can be categorized into.
Credit risks
Credit risks occur as a result of failure by debtors to pay what they owe a bank. Failure to pay
can be as a result of inability by the debtor or unwillingness to pay. Credit risks are likely to
affect Banks operations, its shareholders as well as its ability to issue fresh loans (Acharya, et
al,2017)
Legal risks
Legal risks occur as a result of violation of legal standards set by government institutions as well
as other regulatory bodies in which financial institutions are supposed to abide by. Legal risks
to implement the project which includes Archives Act 1983, Privacy Act 1988 and Freedom of
Information Act 1982 which were established as a necessity as a result of the risks that emanate
from allowing employees to bring own devices at the workplace. If it can implement the project,
the Bank will, therefore, be required to put in place certain control measures to ensure that it
meets all legal obligations (Watkins, 2014). The bank would, therefore, be required to examine
the implications of the project to both the business and its overall security. As per best standards
requirements, commonwealth bank of Australia would be required to determine the implication
of the project by analyzing an already existing real example, identify the existing regulations and
legislation to facilitate compliance, put in place various support measures, both financial and
technical and finally roll out the project. The realization of this is solely dependent on the ICT
department or the technological department of the Bank. Financial institutions are affected by
many risks which can be categorized into.
Credit risks
Credit risks occur as a result of failure by debtors to pay what they owe a bank. Failure to pay
can be as a result of inability by the debtor or unwillingness to pay. Credit risks are likely to
affect Banks operations, its shareholders as well as its ability to issue fresh loans (Acharya, et
al,2017)
Legal risks
Legal risks occur as a result of violation of legal standards set by government institutions as well
as other regulatory bodies in which financial institutions are supposed to abide by. Legal risks
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

affecting financial institutions include violation of security and fraud laws. Legal risks can have
adverse effect towards the operation and the reputation of a financial institution like the
Commonwealth Bank of Australia.
Systematic risks
Systematic risks occur as a result of changes in the value of an organization’s assets. Systematic
risks occur mostly a s a result of changes in the prevailing economic conditions such as changes
in interests rates, changes in foreign exchange among others. Systematic risks can also have a
significant impact on the operations of Bank (Acharya, et al,2017)
With the possibility the occurrence of many risks therefore, any Financial Institution is therefore
required to be aware of these risks among others so that it can put in place policies of identifying
and addressing the risks before they can have a significant impact on their operations.
SECURITY POSTURE
Modern organizations are faced with a myriad of challenges which continue to threaten their
survival. While challenges can present an opportunity for an organization to put in place
measures to avoid more devastating challenges, the emergence of serious challenges that can
lead to ultimate incapacitation of an organization. Of major concern is the financial service
sector whose data security is paramount especially due to the adverse effects that can result from
any serious threat through infringement of banks systems and databases. Such data these would
adversely affect not only the bank but also its various stakeholders who depend on the services
offered by the bank (Shim, et al,2013)The management of Commonwealth Bank of Australia
especially those in the IT department are tasked with the responsibility of ensuring that such
adverse effect towards the operation and the reputation of a financial institution like the
Commonwealth Bank of Australia.
Systematic risks
Systematic risks occur as a result of changes in the value of an organization’s assets. Systematic
risks occur mostly a s a result of changes in the prevailing economic conditions such as changes
in interests rates, changes in foreign exchange among others. Systematic risks can also have a
significant impact on the operations of Bank (Acharya, et al,2017)
With the possibility the occurrence of many risks therefore, any Financial Institution is therefore
required to be aware of these risks among others so that it can put in place policies of identifying
and addressing the risks before they can have a significant impact on their operations.
SECURITY POSTURE
Modern organizations are faced with a myriad of challenges which continue to threaten their
survival. While challenges can present an opportunity for an organization to put in place
measures to avoid more devastating challenges, the emergence of serious challenges that can
lead to ultimate incapacitation of an organization. Of major concern is the financial service
sector whose data security is paramount especially due to the adverse effects that can result from
any serious threat through infringement of banks systems and databases. Such data these would
adversely affect not only the bank but also its various stakeholders who depend on the services
offered by the bank (Shim, et al,2013)The management of Commonwealth Bank of Australia
especially those in the IT department are tasked with the responsibility of ensuring that such
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

threats are mitigated. It is their sole responsibility to protect the Banks systems, data and the
privacy of its clients by adequately managing the bank's financial information. Amid the
increasing level of competition in the Australian financial sector, the Bank has no option but
striving at providing the best data security measures in the industry. Commonwealth Bank of
Australia has been viewed to be way ahead of its main competitors in as far as information
security is concerned. With the many strategies undertaken by the Bank, implementation of the
project allowing employees to bring their devices to the workplace is likely to have huge
implications on its operations because employees might have unauthorized access to some of its
crucial information from their devices which might lead to loss, damage or manipulation of data.
While the project might have both positive and negative implications, it will be necessary for the
Bank to undertake sufficient research to find out whether the benefits surpass the negative
outcomes (Thomson,2012).
Monitoring is key in managing any sensitive data or information form an organization. By
allowing employees to bring their own devices this practice which is highly encouraged at the
Bank is likely to be affected. Among the implications of this project to the bank is the reduction
of system security assurance. The bank will also be able to monitor the working of their
employees because the use of personal devices makes it relatively hard for the management to
distinguish when employees are using the devices for personal undertakings or work-related
tasks. The project will also facilitate deviation from the banks secured use of sensitive
information to the unsecured use of such information. It is also possible that such devices might
be stolen thus risking the Bank’s sensitive information. The project also comes with an
additional budget for the company, implication on its human resources, compliance regulations
as well as legal obligations and liabilities. To regulate such implications, Commonwealth Bank
privacy of its clients by adequately managing the bank's financial information. Amid the
increasing level of competition in the Australian financial sector, the Bank has no option but
striving at providing the best data security measures in the industry. Commonwealth Bank of
Australia has been viewed to be way ahead of its main competitors in as far as information
security is concerned. With the many strategies undertaken by the Bank, implementation of the
project allowing employees to bring their devices to the workplace is likely to have huge
implications on its operations because employees might have unauthorized access to some of its
crucial information from their devices which might lead to loss, damage or manipulation of data.
While the project might have both positive and negative implications, it will be necessary for the
Bank to undertake sufficient research to find out whether the benefits surpass the negative
outcomes (Thomson,2012).
Monitoring is key in managing any sensitive data or information form an organization. By
allowing employees to bring their own devices this practice which is highly encouraged at the
Bank is likely to be affected. Among the implications of this project to the bank is the reduction
of system security assurance. The bank will also be able to monitor the working of their
employees because the use of personal devices makes it relatively hard for the management to
distinguish when employees are using the devices for personal undertakings or work-related
tasks. The project will also facilitate deviation from the banks secured use of sensitive
information to the unsecured use of such information. It is also possible that such devices might
be stolen thus risking the Bank’s sensitive information. The project also comes with an
additional budget for the company, implication on its human resources, compliance regulations
as well as legal obligations and liabilities. To regulate such implications, Commonwealth Bank
of Australia will need to put in place regulatory policies stipulating the terms of use of personal
devices (Miller,Voas & Hurlburt,2012).
Reasons for implementing a BYOD Policy
There are numerous reasons to why an organization can organization can adopt the use of a
BYOD policy which include improving the real time productivity and engagement of employees
because the policy makes them more satisfied and provide results from any location, creating a
smarter and skilled labor force, to introduce a more flexible strategy at the work place, reduce
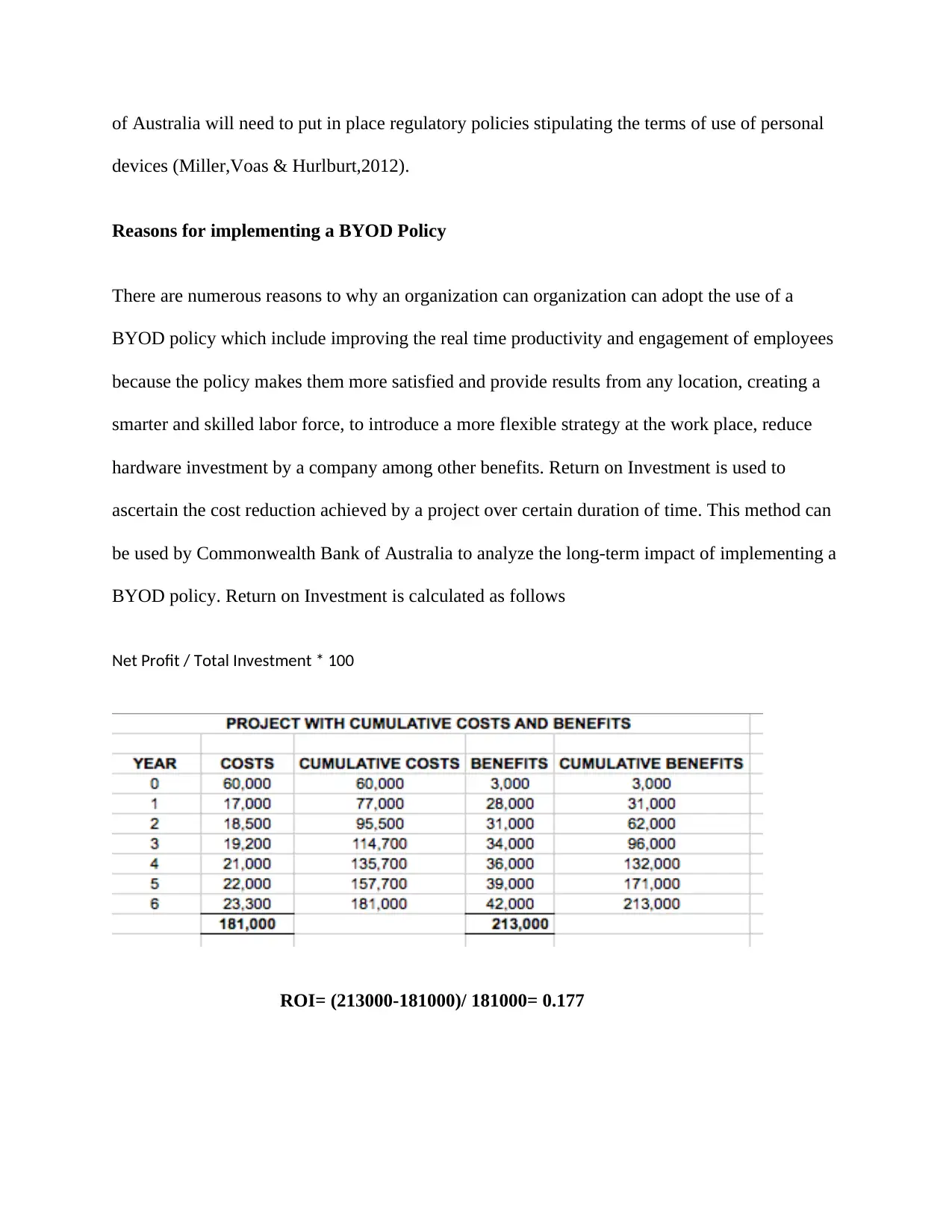
hardware investment by a company among other benefits. Return on Investment is used to
ascertain the cost reduction achieved by a project over certain duration of time. This method can
be used by Commonwealth Bank of Australia to analyze the long-term impact of implementing a
BYOD policy. Return on Investment is calculated as follows
Net Profit / Total Investment * 100
ROI= (213000-181000)/ 181000= 0.177
devices (Miller,Voas & Hurlburt,2012).
Reasons for implementing a BYOD Policy
There are numerous reasons to why an organization can organization can adopt the use of a
BYOD policy which include improving the real time productivity and engagement of employees
because the policy makes them more satisfied and provide results from any location, creating a
smarter and skilled labor force, to introduce a more flexible strategy at the work place, reduce
hardware investment by a company among other benefits. Return on Investment is used to
ascertain the cost reduction achieved by a project over certain duration of time. This method can
be used by Commonwealth Bank of Australia to analyze the long-term impact of implementing a
BYOD policy. Return on Investment is calculated as follows
Net Profit / Total Investment * 100
ROI= (213000-181000)/ 181000= 0.177
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Commonwealth Bank of Australia must, therefore, undertake an evaluation of the merits and
demerits of the project and its overall implications on the Banks' goals and mission. This will
then be followed by formulation of policies to regulate the use of personal devices and the
general security of the Banks systems. The Bank may also hire the services of solution providers
whose main responsibilities will be assessing the risks associated with the project, formulation of
different projects to govern the project as well as coming up with control measures to facilitate
implementation of these policies. Commonwealth Bank of Australia will, therefore, be required
to notify their employees on what to expect upon implementation of the project regarding the
privacy of their personal information which might need to be subjected to company monitoring
(Pillay,et al,2013)
Implementation of BYOD project will require the bank to consider its ability to remove the
banks information from employees devices upon their departure from the bank, clarify on what
devices, platforms, and networks that can be used in these devices including any associated
prohibitions to use such devices, avail a procedure to address possible theft of these devices in
order to protect Banks Information and clarifying on the consequences of any violations from
employees regarding the use of personal devices. The bank should also establish its ability to
access and have control over information belonging to it including the use of mobile device
management system as well as identify support limitations resulting from these devices to ensure
that they are addressed. Before implementing the Common program wealth Bank is also required
to analyze how the project is likely to affect the various stakeholders and the bank at large and
therefore it should solicit views from its employees, the finance department, its legal advisers
and finally its technological team (Ghosh, Gajar & Rai,2013).
demerits of the project and its overall implications on the Banks' goals and mission. This will
then be followed by formulation of policies to regulate the use of personal devices and the
general security of the Banks systems. The Bank may also hire the services of solution providers
whose main responsibilities will be assessing the risks associated with the project, formulation of
different projects to govern the project as well as coming up with control measures to facilitate
implementation of these policies. Commonwealth Bank of Australia will, therefore, be required
to notify their employees on what to expect upon implementation of the project regarding the
privacy of their personal information which might need to be subjected to company monitoring
(Pillay,et al,2013)
Implementation of BYOD project will require the bank to consider its ability to remove the
banks information from employees devices upon their departure from the bank, clarify on what
devices, platforms, and networks that can be used in these devices including any associated
prohibitions to use such devices, avail a procedure to address possible theft of these devices in
order to protect Banks Information and clarifying on the consequences of any violations from
employees regarding the use of personal devices. The bank should also establish its ability to
access and have control over information belonging to it including the use of mobile device
management system as well as identify support limitations resulting from these devices to ensure
that they are addressed. Before implementing the Common program wealth Bank is also required
to analyze how the project is likely to affect the various stakeholders and the bank at large and
therefore it should solicit views from its employees, the finance department, its legal advisers
and finally its technological team (Ghosh, Gajar & Rai,2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The solution lies in the Bank’s ability to use smart policies and compliance; such policies would
include an adoption of a formal mobile policy that stipulates consequences of violation,
sufficient security measures use of training programs to solve mobile liabilities. A mobile policy
would include ensuring that each device that is being used by an employee is remote wipe
enabled. Although the process might require much time and resources, it will save the Bank a
significant amount of resources that it might incur in an instance where these devices are used to
break the law (Moyer,2013).
THREATS, VULNERABILITIES, AND CONSEQUENCES
Although highly considered for their useful functionality and high efficiency at the workplace,
technological devices such as iPads, mobile phones, laptops, and ipads have come with
numerous challenges that continue to affect not only employees but also their employers. Recent
studies have shown an increase in the usage of usage of own smart phones and tablets for
business with the number expected to keep rising (Morrow,2012). The number of Companies
allowing employees to make use of their devices for business has also continued to rise with a
recent research predicting that at least 38% of global companies will have implemented Bring
Your Device into their operations. This is also a trend that has been witnessed 2017 which has
recorded a significant increase in the level of usage of personal devices by employees at the
workplace. This is to signify perhaps the Importance that some employers attach to the use of
personal devices for business. However, adoption of BYOD Policy requires employers to shift
their focus to remain updated on changes in technology as well as being mindful of data security
and privacy issues (Lebek, Degirmenci & Breitner, 2013).
include an adoption of a formal mobile policy that stipulates consequences of violation,
sufficient security measures use of training programs to solve mobile liabilities. A mobile policy
would include ensuring that each device that is being used by an employee is remote wipe
enabled. Although the process might require much time and resources, it will save the Bank a
significant amount of resources that it might incur in an instance where these devices are used to
break the law (Moyer,2013).
THREATS, VULNERABILITIES, AND CONSEQUENCES
Although highly considered for their useful functionality and high efficiency at the workplace,
technological devices such as iPads, mobile phones, laptops, and ipads have come with
numerous challenges that continue to affect not only employees but also their employers. Recent
studies have shown an increase in the usage of usage of own smart phones and tablets for
business with the number expected to keep rising (Morrow,2012). The number of Companies
allowing employees to make use of their devices for business has also continued to rise with a
recent research predicting that at least 38% of global companies will have implemented Bring
Your Device into their operations. This is also a trend that has been witnessed 2017 which has
recorded a significant increase in the level of usage of personal devices by employees at the
workplace. This is to signify perhaps the Importance that some employers attach to the use of
personal devices for business. However, adoption of BYOD Policy requires employers to shift
their focus to remain updated on changes in technology as well as being mindful of data security
and privacy issues (Lebek, Degirmenci & Breitner, 2013).

For the Commonwealth Bank of Australia, the implementation of the project allowing employees
to use their devices for business will, therefore, come with threats, vulnerabilities, and
consequences for both the Bank and its Employees. As such, the Bank will find it necessary to
focus on changes in technology and regularly address security and privacy issues arising a result
of the project (Garba,et al,2015)
There are various risks associated with the implementation of the project. By allowing its
employees to use personal devices for official purposes, the Bank will commit itself to any
violations committed by their employees through the use of personal devices, For any offense
broken by their employees, Commonwealth Bank of Australia will be held responsible (Ghosh,
Gajar & Rai, 2013). A good example of such risks would be where a driver of the bank causes an
accident because of using a cell phone while driving as it was the case of the COCA-COLA
Company driver who hit a woman while on the phone in 2016. The cases of Employers being
sued for employee use of personal devices have been on the rise in the recent past ( Bzur,
2013).There, therefore, some risks that Commonwealth Bank of Australia will be faced with as a
result of implementing this project.
Abstracted driving
Distracted driving is one of the most common risks that result from the use of personal devices at
work. The impact of this can be quite huge for a company. The use of mobile phones by drivers
while driving can result in unwarranted legal battles as well as penalties due to injuries or deaths
of road users. Risks associated with distracted driving is, therefore, one of the risks that
Commonwealth Bank of Australia is likely to be faced with as a result of allowing employees to
use their devices at work (French, Guo & Shim,2014).
to use their devices for business will, therefore, come with threats, vulnerabilities, and
consequences for both the Bank and its Employees. As such, the Bank will find it necessary to
focus on changes in technology and regularly address security and privacy issues arising a result
of the project (Garba,et al,2015)
There are various risks associated with the implementation of the project. By allowing its
employees to use personal devices for official purposes, the Bank will commit itself to any
violations committed by their employees through the use of personal devices, For any offense
broken by their employees, Commonwealth Bank of Australia will be held responsible (Ghosh,
Gajar & Rai, 2013). A good example of such risks would be where a driver of the bank causes an
accident because of using a cell phone while driving as it was the case of the COCA-COLA
Company driver who hit a woman while on the phone in 2016. The cases of Employers being
sued for employee use of personal devices have been on the rise in the recent past ( Bzur,
2013).There, therefore, some risks that Commonwealth Bank of Australia will be faced with as a
result of implementing this project.
Abstracted driving
Distracted driving is one of the most common risks that result from the use of personal devices at
work. The impact of this can be quite huge for a company. The use of mobile phones by drivers
while driving can result in unwarranted legal battles as well as penalties due to injuries or deaths
of road users. Risks associated with distracted driving is, therefore, one of the risks that
Commonwealth Bank of Australia is likely to be faced with as a result of allowing employees to
use their devices at work (French, Guo & Shim,2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





