Analyzing ICMP and IP Protocols: A Communications and Networking Study
VerifiedAdded on 2023/01/17

Communications and Networking
Student Name
University Name
Note by the Author
Paraphrase This Document

Summary
This report aims to record and study the pinging, and tracing activities of three different
websites located in a different continent (Europe and North America) than the place from
where the network analysis is being conducted that is Asia. First the report performs a ping of
the website www.ece.ust.eu and discusses the IP address and ports of the source and
destination hosts as well as goes in depth into the protocol contents of ping request and reply
packets. Then the trace of another website www.inria.fr is conducted and thorough research
on ICMP packets and their comparison with that of the ping are made before finding the link
with the longest delay. Thereafter, a trace is performed on gaia.cs.umass.edu is performed in
PingPlotter to get a more comprehensive look at the nearest first hop routers, their location as
also the graph of the latencies of each step. This is a composite process conducted for three
different packet sizes (56 bytes, 2000 bytes, 3500 bytes). Here, the contents of the IP protocol
get further analysed and it is checked if datagrams got fragmented and also details and
comparison of the identified fragments for different packet sizes are performed after which
the report ends with concluding notes.

Table of Contents
Introduction................................................................................................................................5
Analysis of Traces......................................................................................................................5
Part A: Ping of website of another continent.........................................................................5
1. IP addresses of local host and that of destination host...................................................8
2. Reason for ICMP packets not having source port or destination port numbers.............8
3. Examining a ping request packet sent by local host (ICMP Type, Code numbers and
rest of the fields, number of bytes for checksum, sequence number and identifier fields)9
4. Examining a ping request packet sent by local host (ICMP Type, Code numbers and
rest of the fields, number of bytes for checksum, sequence number and identifier fields)
..........................................................................................................................................10
Part B: Trace route...............................................................................................................11
5. IP addresses of local host and that of destination host.................................................13
6. IP Protocol number if system was Linux or UNIX based and ICMP sent UDP
packets..............................................................................................................................13
7. Examining ICMP echo packet and whether it is different from ICMP ping query
packets..............................................................................................................................14
8. Examining contents of ICMP error packets which have more fields than ICMP echo
packets..............................................................................................................................15
9. Examining last 3 ICMP packets...................................................................................16
10. Link among tracert measurements where delay is significantly longer than the rest 17
Part C: Trace with PingPlotter and Latency Graph..............................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Select the first ICMP Echo Request message sent by your computer, and expand the
Internet Protocol part of the packet in the packet details window. What is the IP address
of your computer?............................................................................................................25
2. Within the IP packet header, what is the value in the upper layer protocol field?.......26
3. How many bytes are in the IP header? How many bytes are in the payload of the IP
datagram? Explain how you determined the number of payload bytes...........................26
4. Has this IP datagram been fragmented? Explain how you determined whether or not
the datagram has been fragmented...................................................................................27
5. Which fields in the IP datagram always change from one datagram to the next within
this series of ICMP messages sent by your computer?....................................................29
6. Which fields stay constant? Which of the fields must stay constant? Which fields must
change? Why?..................................................................................................................30
7. Describe the pattern you see in the values in the Identification field of the IP datagram
..........................................................................................................................................30
8. What is the value in the Identification field and the TTL field?..................................31
9. Do these values remain unchanged for all of the ICMP TTL-exceeded replies sent to
your computer by the nearest (first hop) router? Why?...................................................34
10. Find the first ICMP Echo Request message that was sent by your computer after you
changed the Packet Size in pingplotter to be 2000. Has that message been fragmented
across more than one IP datagram?..................................................................................35
11. Print out the first fragment of the fragmented IP datagram. What information in the
IP header indicates that the datagram been fragmented? What information in the IP
Paraphrase This Document

header indicates whether this is the first fragment versus a latter fragment? How long is
this IP datagram?..............................................................................................................36
12. Print out the second fragment of the fragmented IP datagram. What information in
the IP header indicates that this is not the first datagram fragment? Are the more
fragments? How can you tell?..........................................................................................38
13. What fields change in the IP header between the first and second fragment?...........39
14. How many fragments were created from the original datagram?..............................40
15. What fields change in the IP header among the fragments?......................................41
Conclusion................................................................................................................................41
Bibliography.............................................................................................................................42

Introduction
The following report records and studies the ping, and traceroute activities of three
different websites located in different continents (Europe and North America) than the place
from where the network analysis is being conducted that is Asia. The report begins by
performing a ping of the website www.ece.ust.eu and discusses the IP address and ports of
the source and destination hosts as well as goes in depth into the protocol contents of ping
request and reply packets. Then the trace of another website www.inria.fr is conducted and
thorough research on ICMP packets and their comparison with that of the ping are made
before finding the link with the longest delay. Thereafter, a trace is performed on
gaia.cs.umass.edu is performed in PingPlotter to get a more comprehensive look at the
nearest first hop routers, their location as also the graph of the latencies of each step. This is a
composite process conducted for three different packet sizes (56 bytes, 2000 bytes, 3500
bytes). Here, the contents of the IP protocol get further analysed and it is checked if
datagrams got fragmented and also details and comparison of the identified fragments for
different packet sizes are performed after which the report ends with concluding notes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Analysis of Traces
Part A: Ping of website of another continent
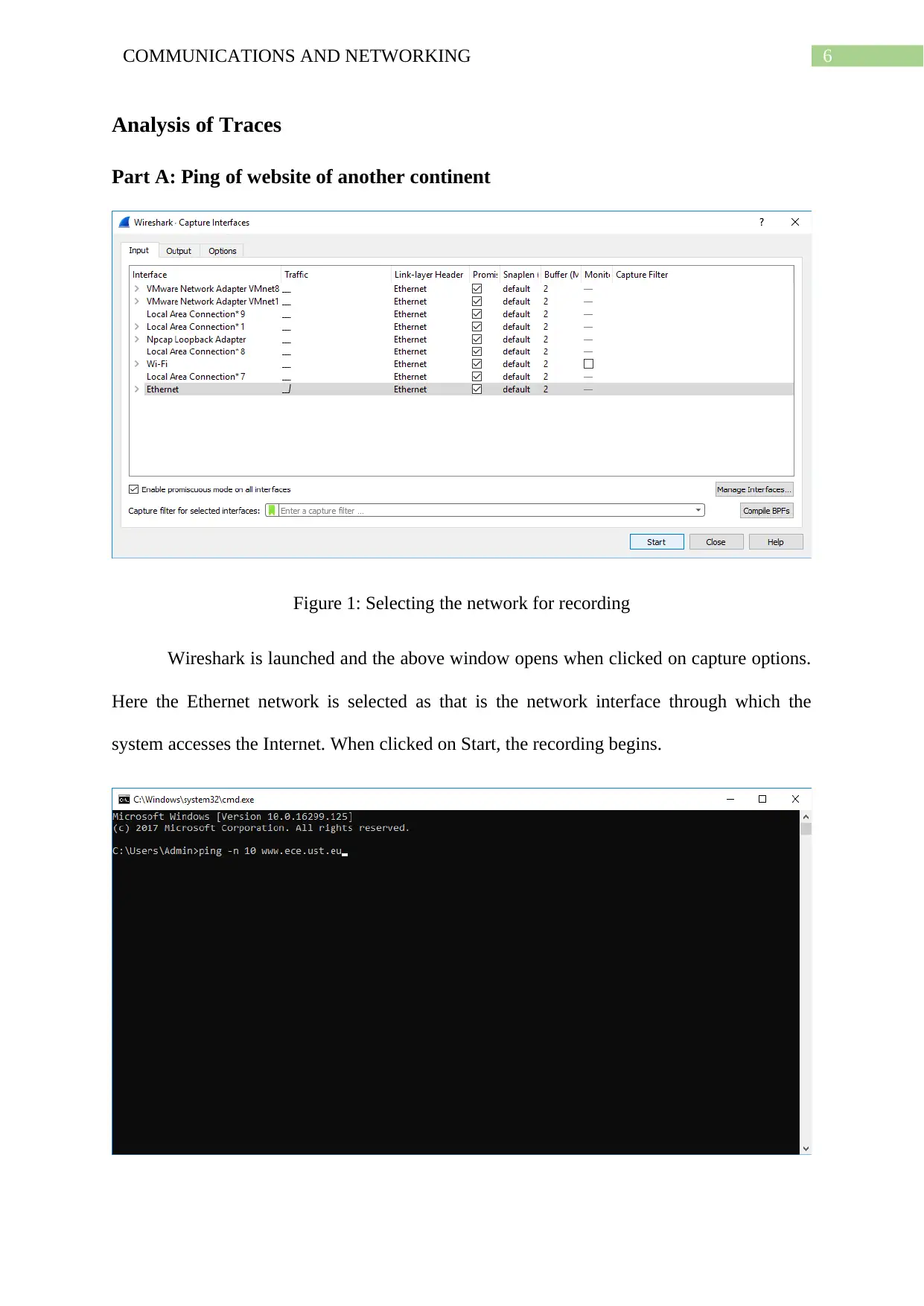
Figure 1: Selecting the network for recording
Wireshark is launched and the above window opens when clicked on capture options.
Here the Ethernet network is selected as that is the network interface through which the
system accesses the Internet. When clicked on Start, the recording begins.
Paraphrase This Document
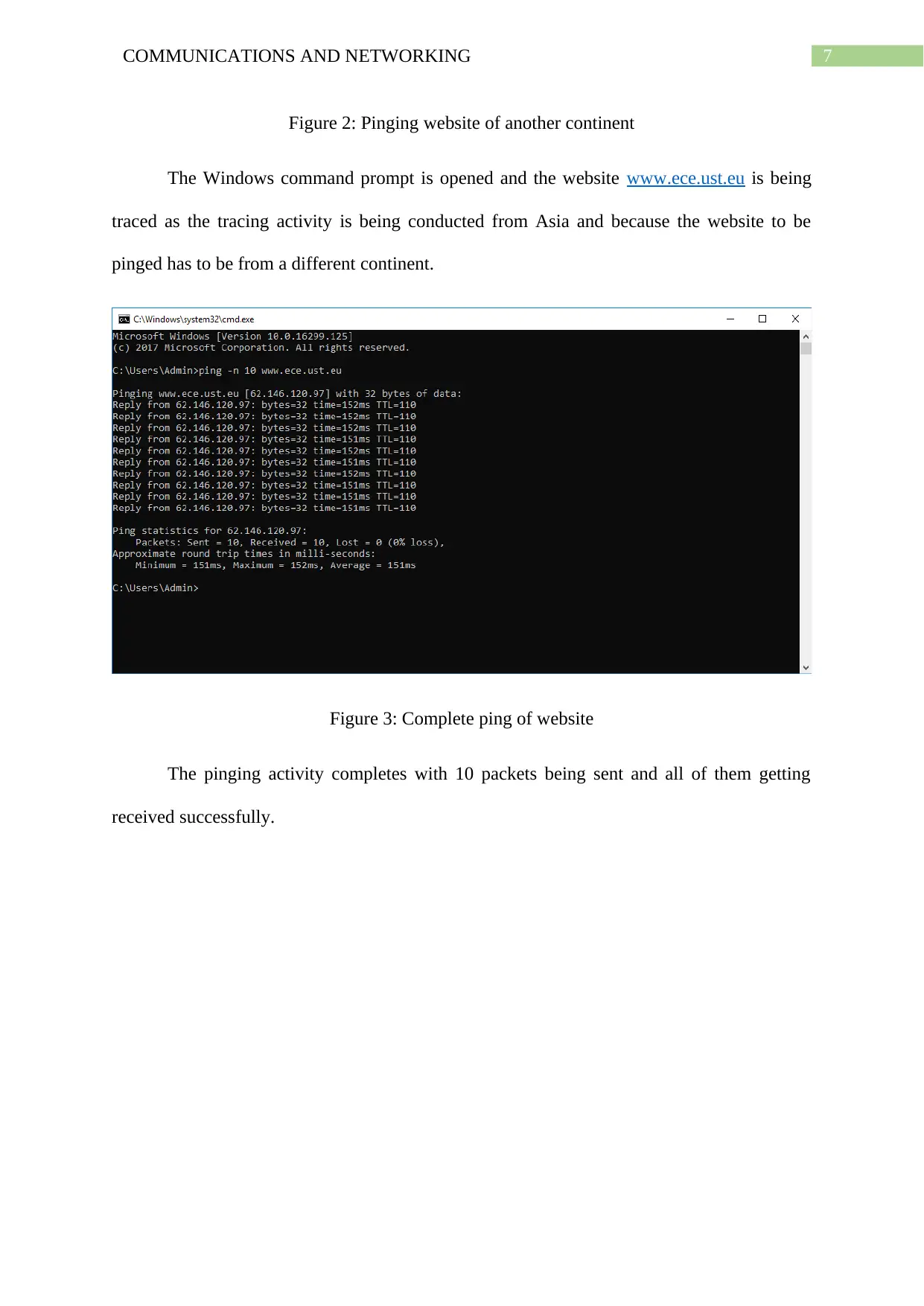
Figure 2: Pinging website of another continent
The Windows command prompt is opened and the website www.ece.ust.eu is being
traced as the tracing activity is being conducted from Asia and because the website to be
pinged has to be from a different continent.
Figure 3: Complete ping of website
The pinging activity completes with 10 packets being sent and all of them getting
received successfully.
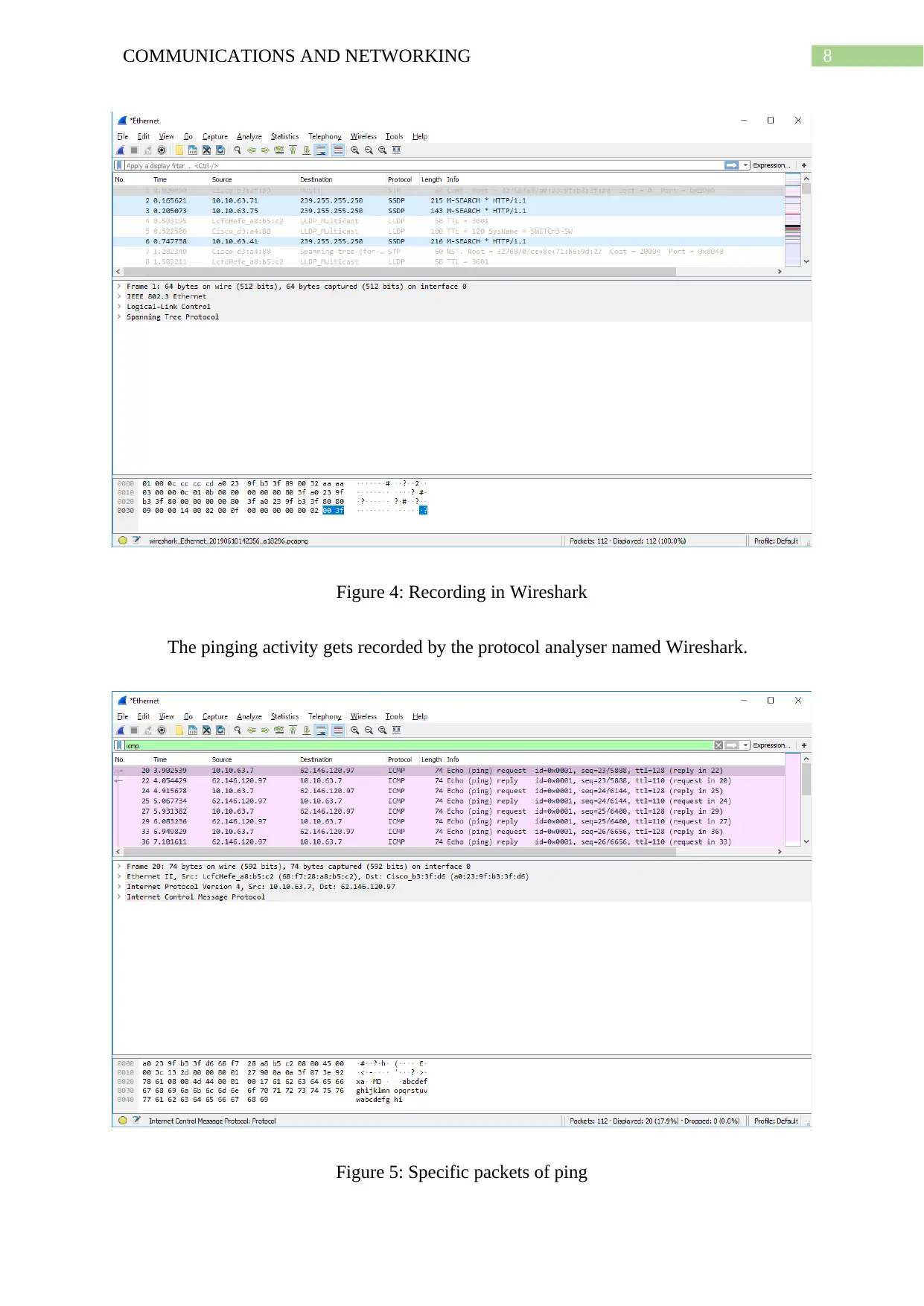
Figure 4: Recording in Wireshark
The pinging activity gets recorded by the protocol analyser named Wireshark.
Figure 5: Specific packets of ping
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Next the packets involved in the ping activity is separately listed by applying a filter
to show all packets of ICMP protocol. Thus the packets shown by Wireshark now are either
ping (request) or ping (reply) packet.
1. What is the IP address of your host? What is the IP address of the destination host?
As can be seen in Wireshark the IP address of the local host from where the ping of
the website is being made is 10.10.63.7 and the IP address of the destination host is
62.146.120.97.
2. Why is it that an ICMP packet does not have source and destination port numbers?
ICMP packets do not have port numbers for the source and destination because it is
designed for communicating with network layer information between the routers and hosts
instead of among processes of application layer.
Paraphrase This Document
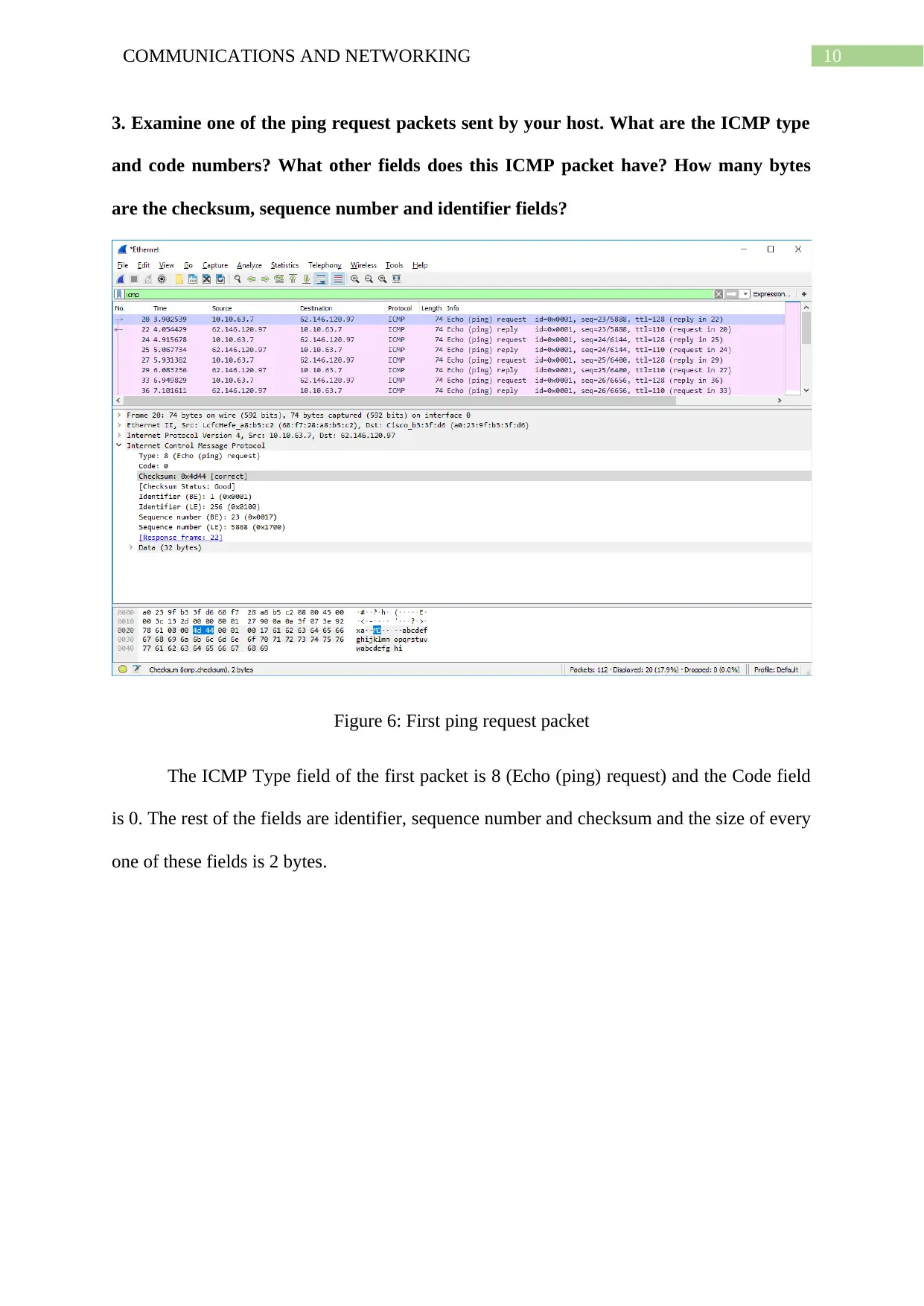
3. Examine one of the ping request packets sent by your host. What are the ICMP type
and code numbers? What other fields does this ICMP packet have? How many bytes
are the checksum, sequence number and identifier fields?
Figure 6: First ping request packet
The ICMP Type field of the first packet is 8 (Echo (ping) request) and the Code field
is 0. The rest of the fields are identifier, sequence number and checksum and the size of every
one of these fields is 2 bytes.
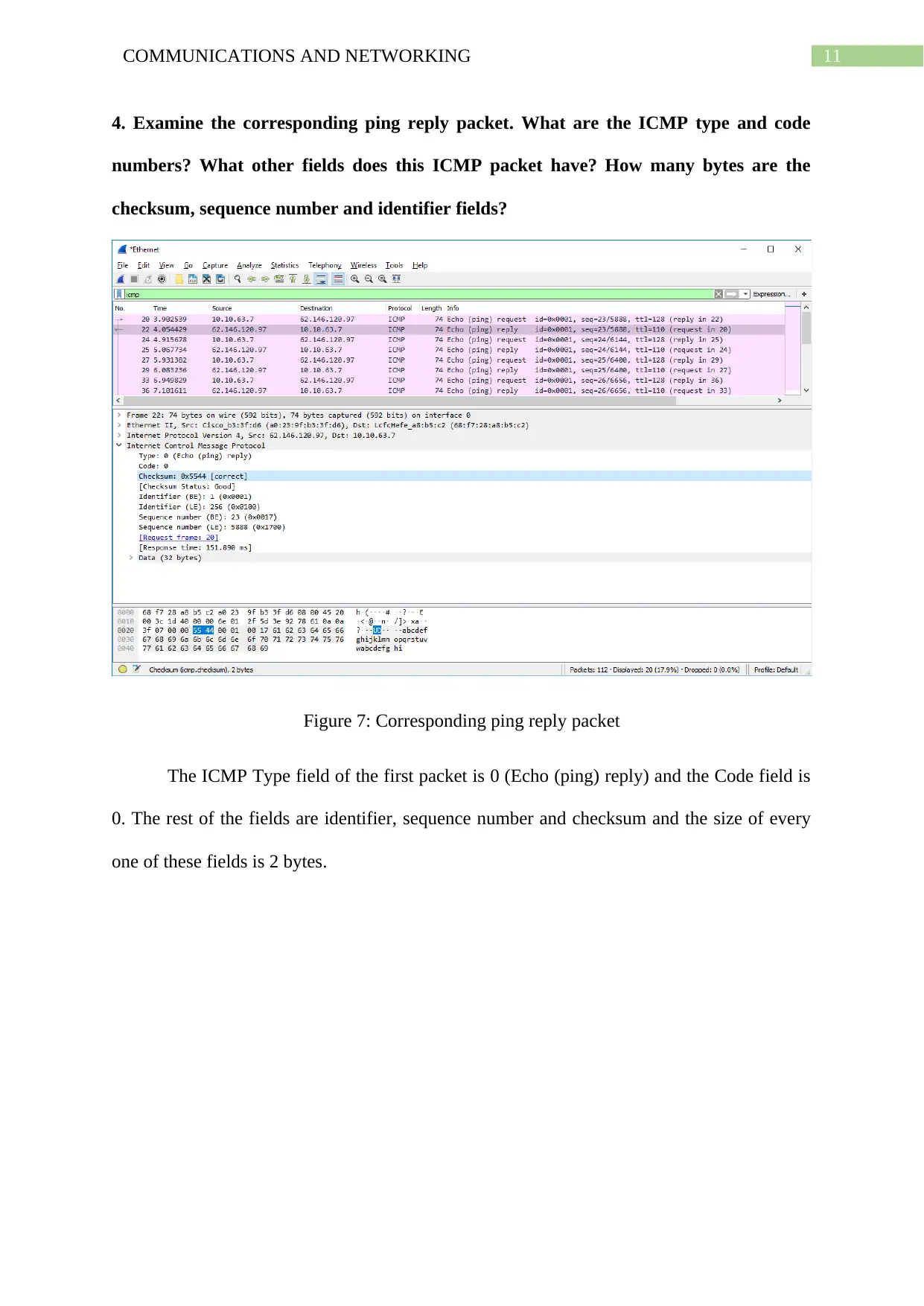
4. Examine the corresponding ping reply packet. What are the ICMP type and code
numbers? What other fields does this ICMP packet have? How many bytes are the
checksum, sequence number and identifier fields?
Figure 7: Corresponding ping reply packet
The ICMP Type field of the first packet is 0 (Echo (ping) reply) and the Code field is
0. The rest of the fields are identifier, sequence number and checksum and the size of every
one of these fields is 2 bytes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Part B: Trace route
Figure 8: Wireshark recording started
A new session of Wireshark is opened and the recording is again started on the
Ethernet network interface.
Figure 9: Trace route of www.inria.fr
Paraphrase This Document
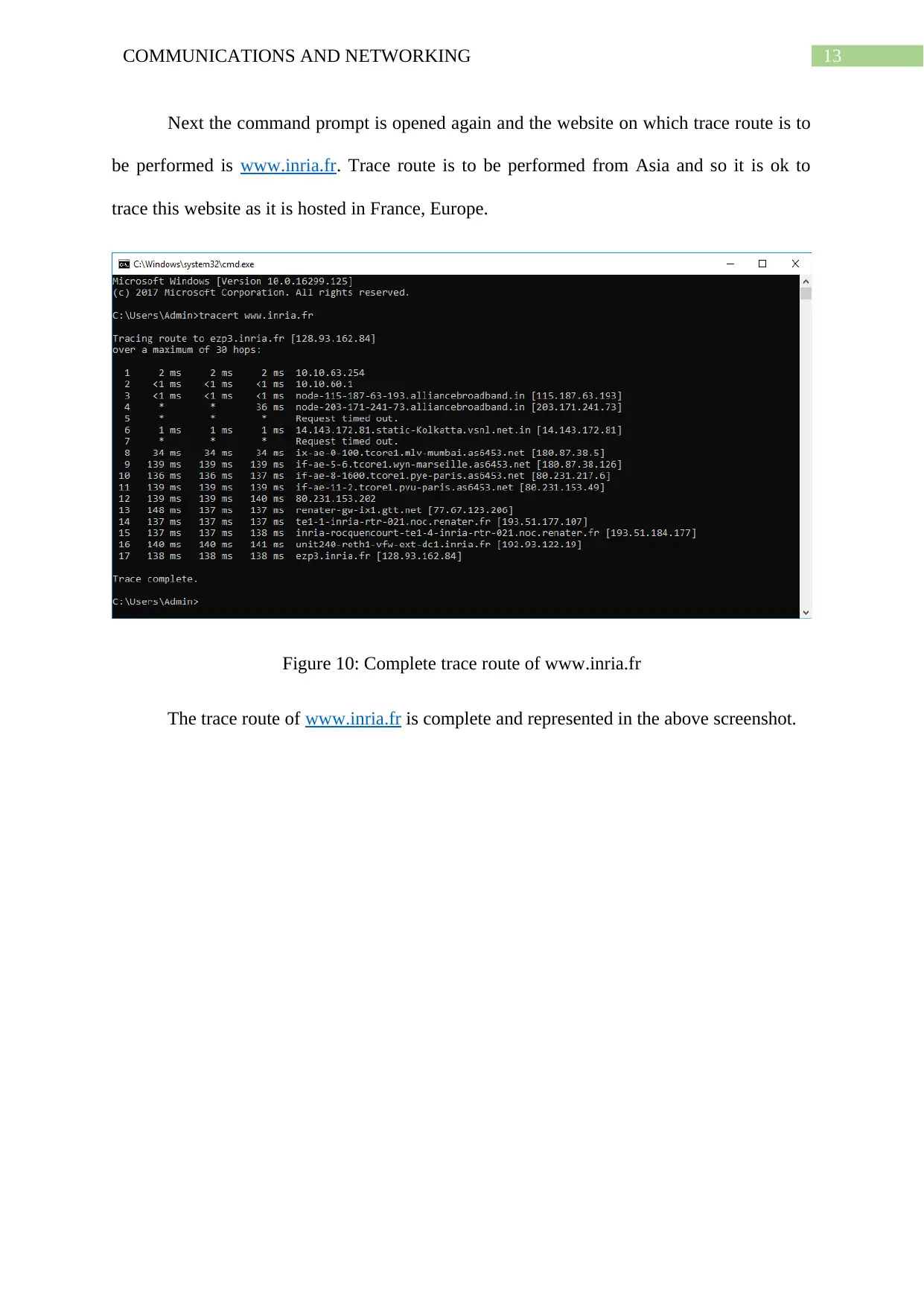
Next the command prompt is opened again and the website on which trace route is to
be performed is www.inria.fr. Trace route is to be performed from Asia and so it is ok to
trace this website as it is hosted in France, Europe.
Figure 10: Complete trace route of www.inria.fr
The trace route of www.inria.fr is complete and represented in the above screenshot.
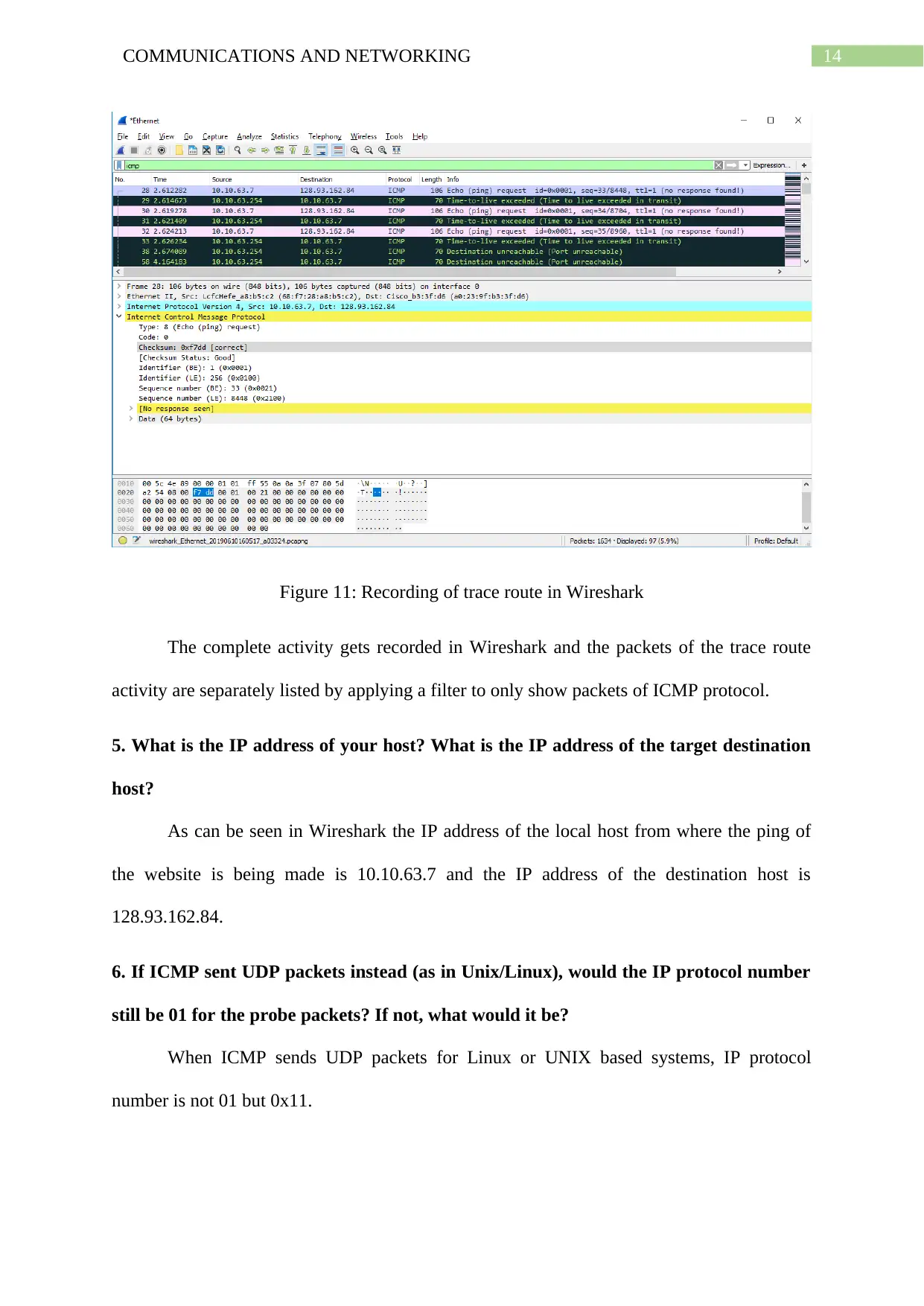
Figure 11: Recording of trace route in Wireshark
The complete activity gets recorded in Wireshark and the packets of the trace route
activity are separately listed by applying a filter to only show packets of ICMP protocol.
5. What is the IP address of your host? What is the IP address of the target destination
host?
As can be seen in Wireshark the IP address of the local host from where the ping of
the website is being made is 10.10.63.7 and the IP address of the destination host is
128.93.162.84.
6. If ICMP sent UDP packets instead (as in Unix/Linux), would the IP protocol number
still be 01 for the probe packets? If not, what would it be?
When ICMP sends UDP packets for Linux or UNIX based systems, IP protocol
number is not 01 but 0x11.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
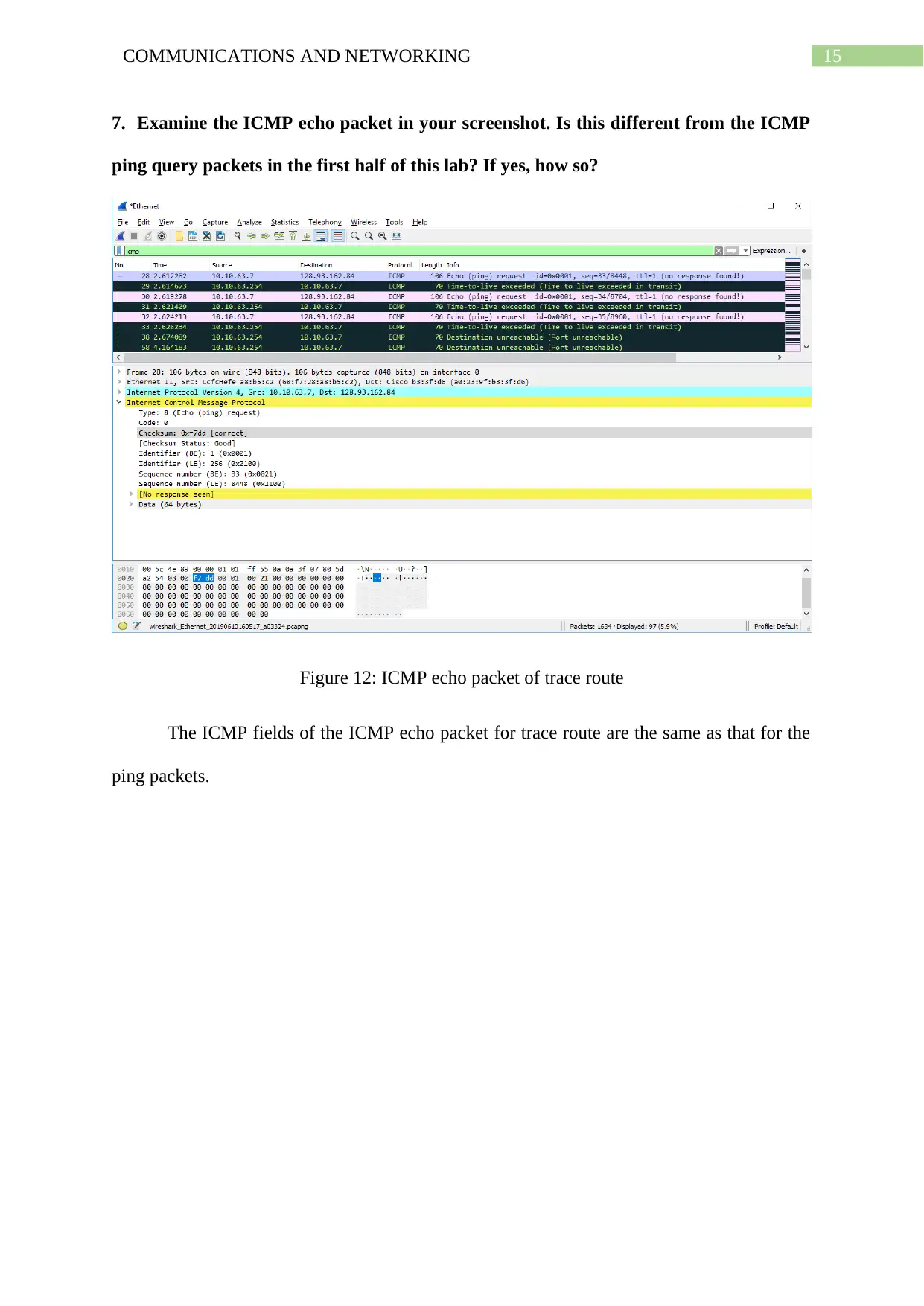
7. Examine the ICMP echo packet in your screenshot. Is this different from the ICMP
ping query packets in the first half of this lab? If yes, how so?
Figure 12: ICMP echo packet of trace route
The ICMP fields of the ICMP echo packet for trace route are the same as that for the
ping packets.
Paraphrase This Document
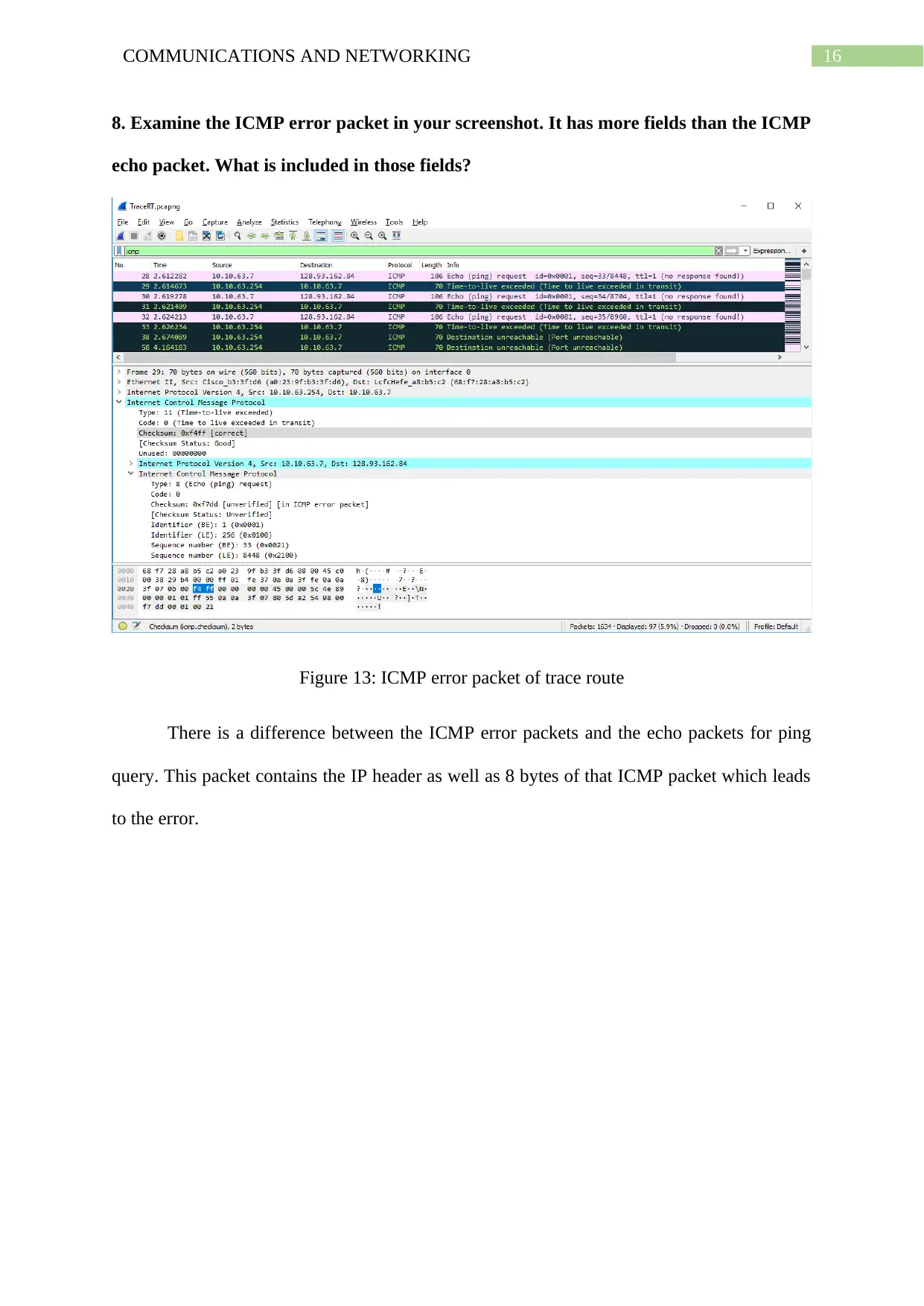
8. Examine the ICMP error packet in your screenshot. It has more fields than the ICMP
echo packet. What is included in those fields?
Figure 13: ICMP error packet of trace route
There is a difference between the ICMP error packets and the echo packets for ping
query. This packet contains the IP header as well as 8 bytes of that ICMP packet which leads
to the error.
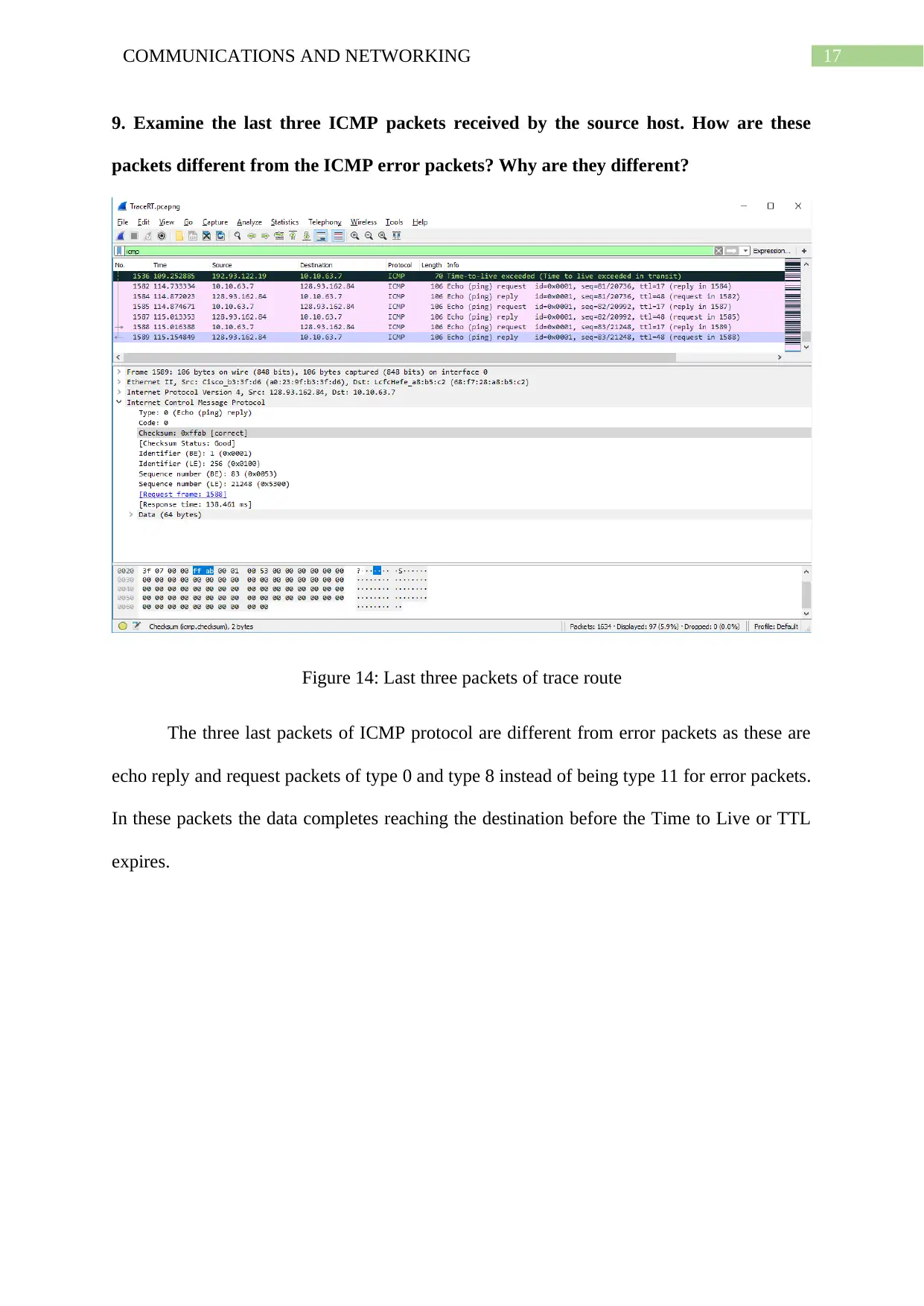
9. Examine the last three ICMP packets received by the source host. How are these
packets different from the ICMP error packets? Why are they different?
Figure 14: Last three packets of trace route
The three last packets of ICMP protocol are different from error packets as these are
echo reply and request packets of type 0 and type 8 instead of being type 11 for error packets.
In these packets the data completes reaching the destination before the Time to Live or TTL
expires.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
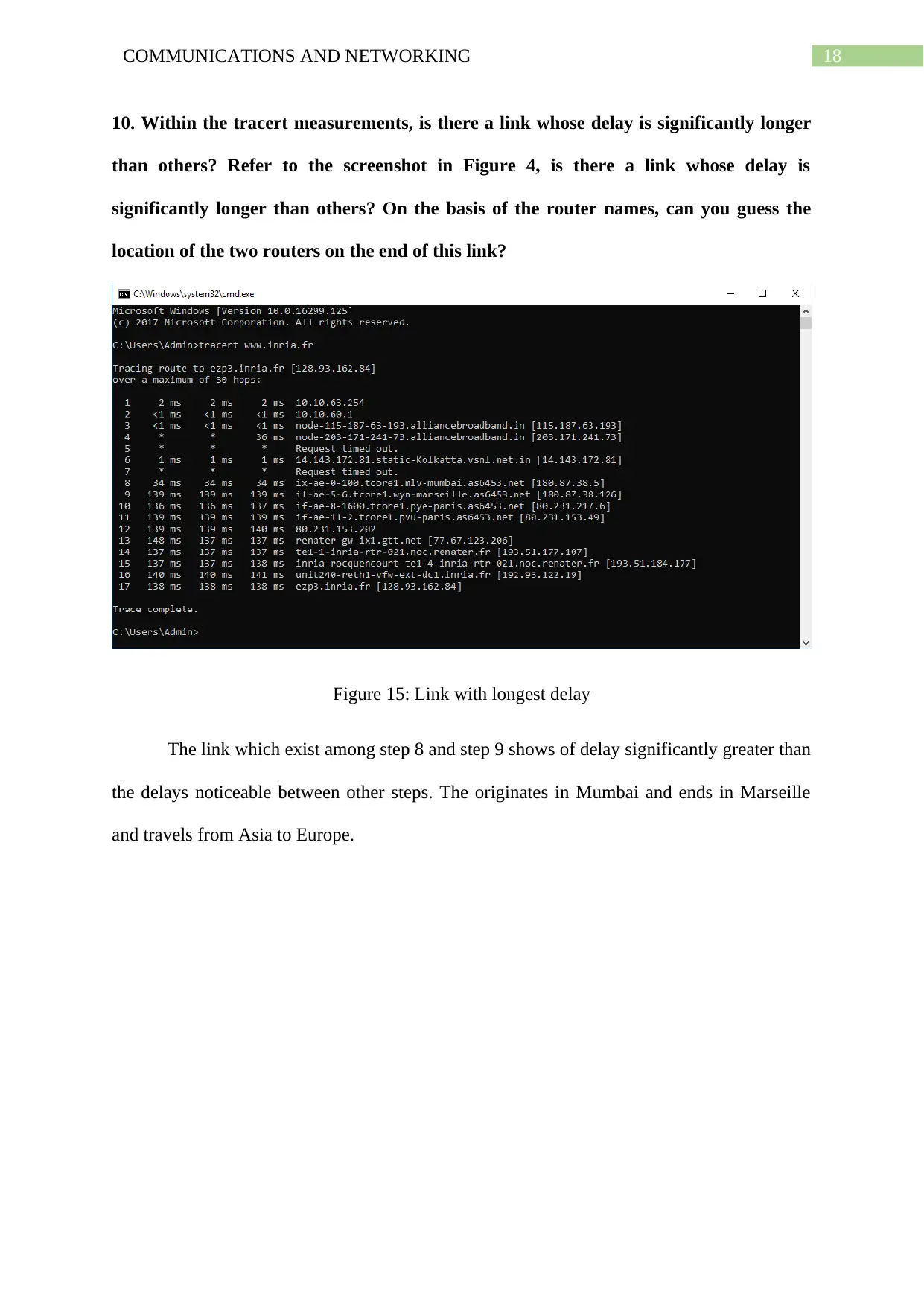
10. Within the tracert measurements, is there a link whose delay is significantly longer
than others? Refer to the screenshot in Figure 4, is there a link whose delay is
significantly longer than others? On the basis of the router names, can you guess the
location of the two routers on the end of this link?
Figure 15: Link with longest delay
The link which exist among step 8 and step 9 shows of delay significantly greater than
the delays noticeable between other steps. The originates in Mumbai and ends in Marseille
and travels from Asia to Europe.
Paraphrase This Document
Part C: Trace with PingPlotter and Latency Graph
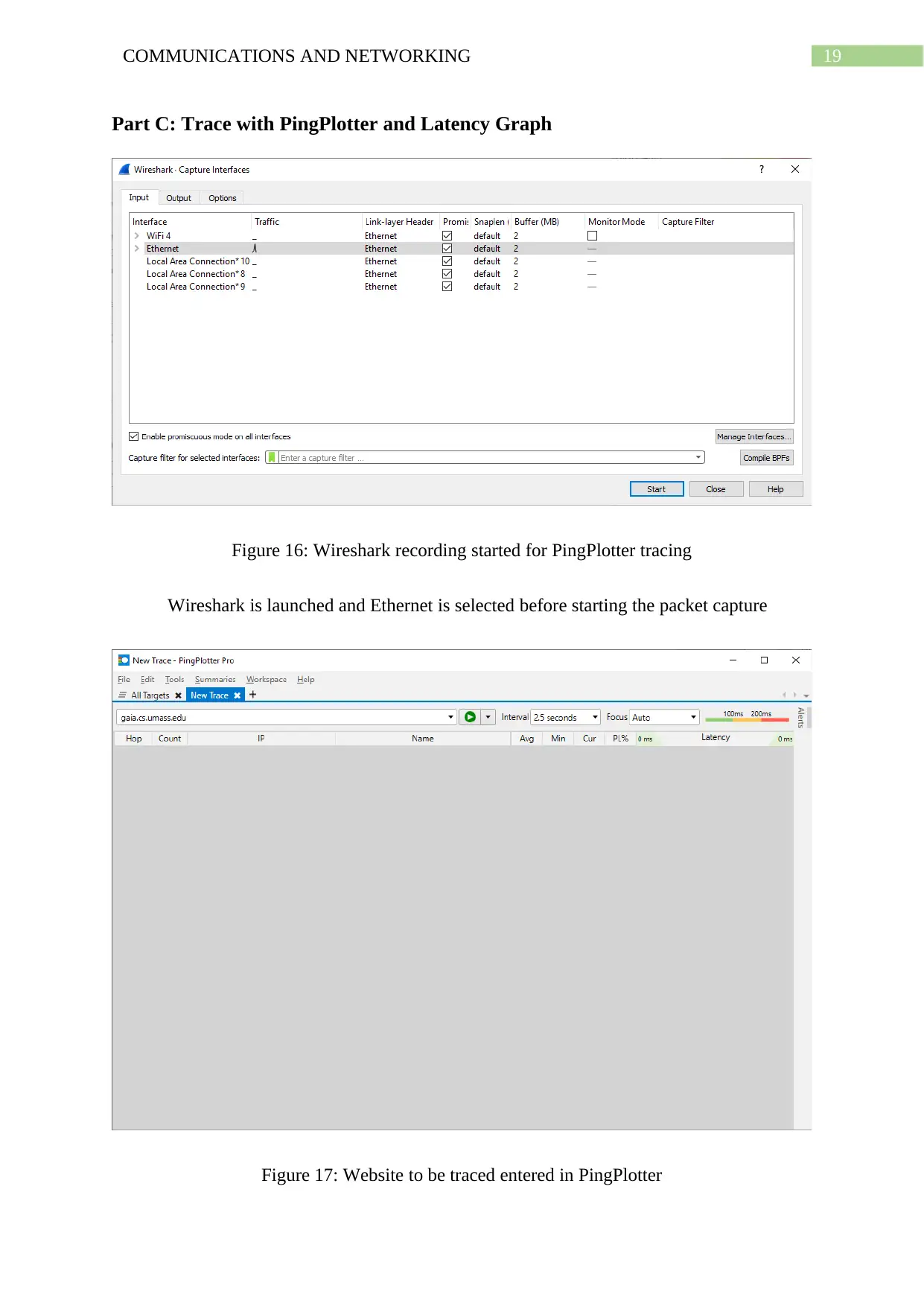
Figure 16: Wireshark recording started for PingPlotter tracing
Wireshark is launched and Ethernet is selected before starting the packet capture
Figure 17: Website to be traced entered in PingPlotter
The tracing utility PingPlotter is launched and the website gaia.cs.umass.edu is
entered there beside the start trace button.
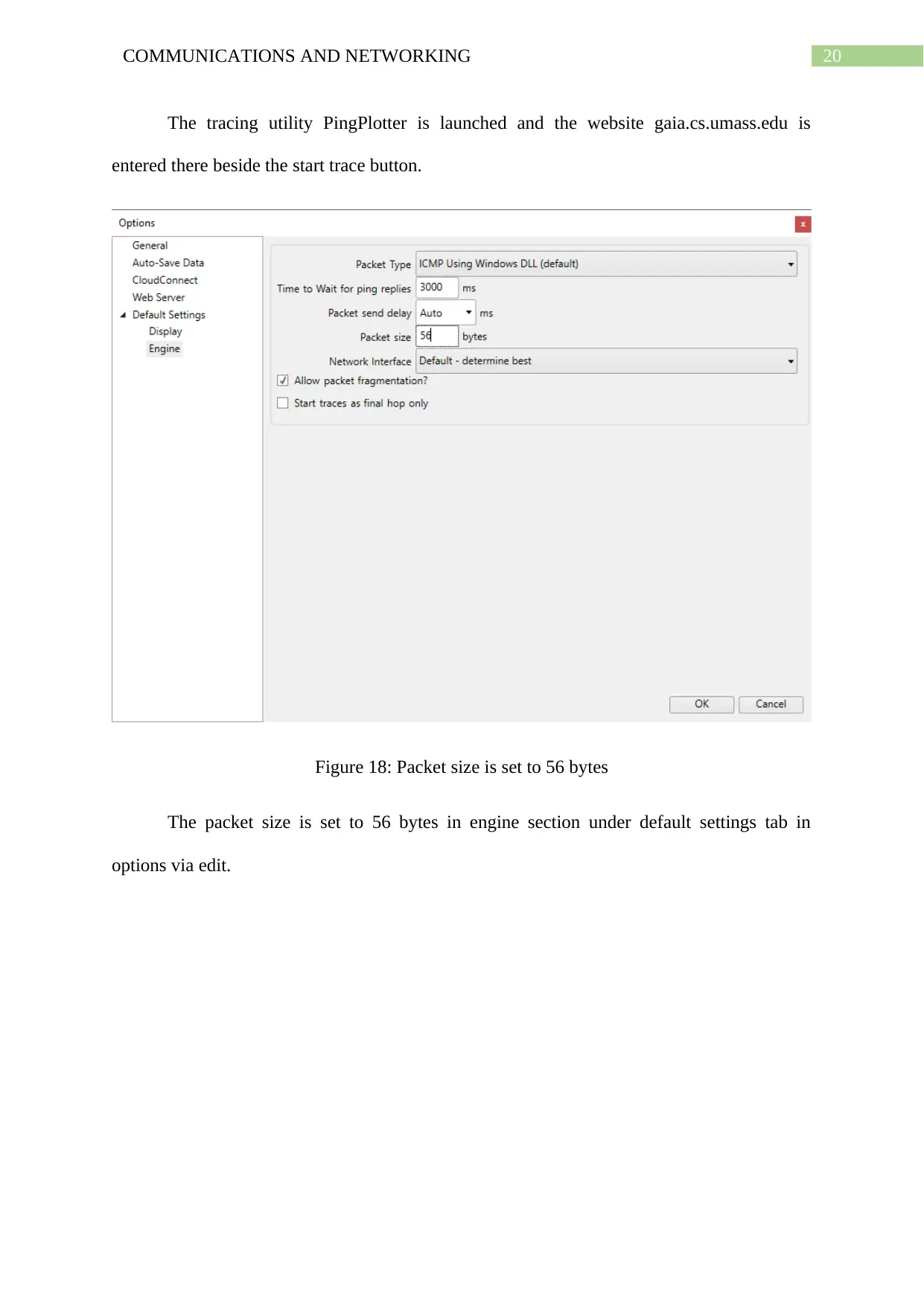
Figure 18: Packet size is set to 56 bytes
The packet size is set to 56 bytes in engine section under default settings tab in
options via edit.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
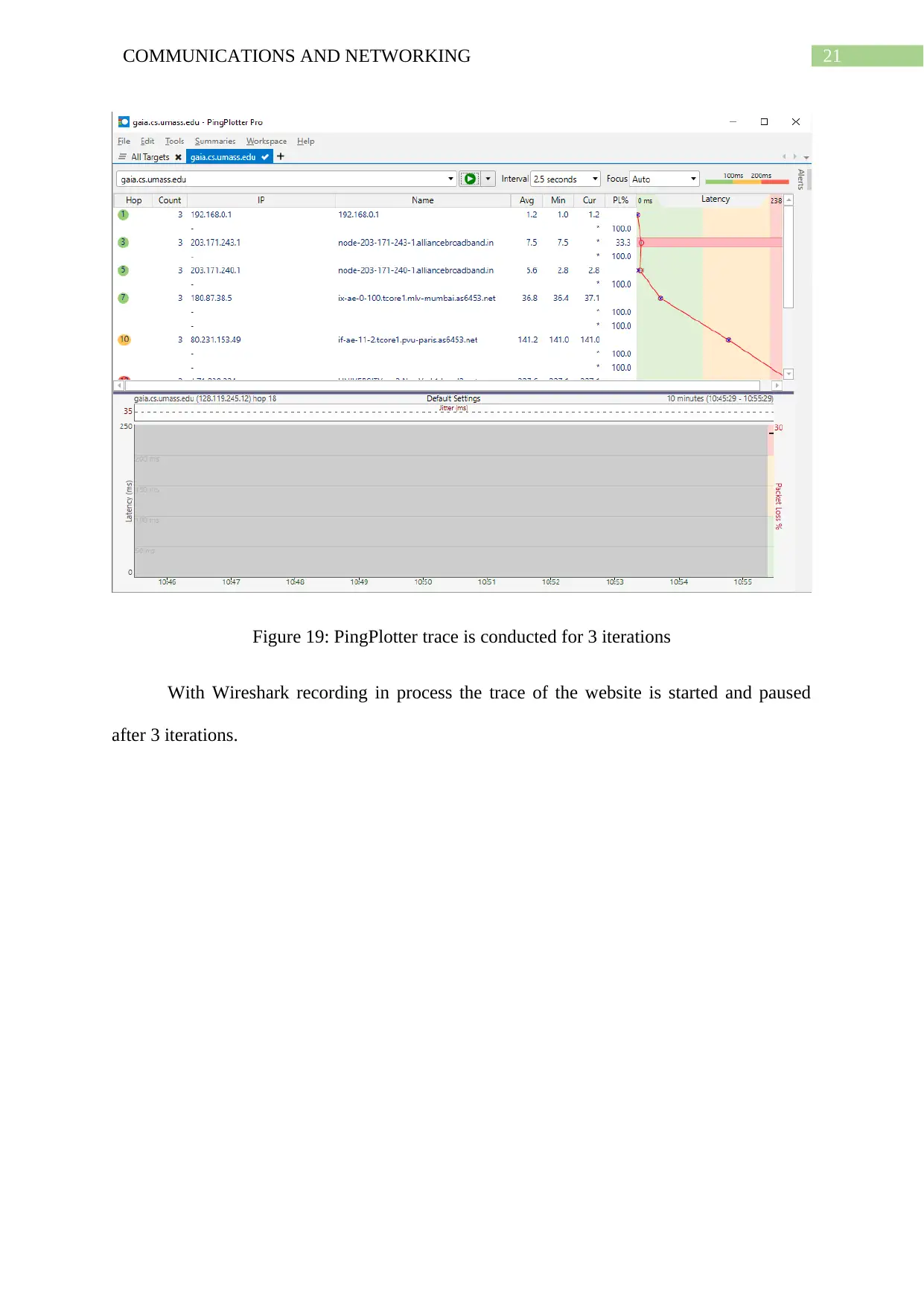
Figure 19: PingPlotter trace is conducted for 3 iterations
With Wireshark recording in process the trace of the website is started and paused
after 3 iterations.
Paraphrase This Document
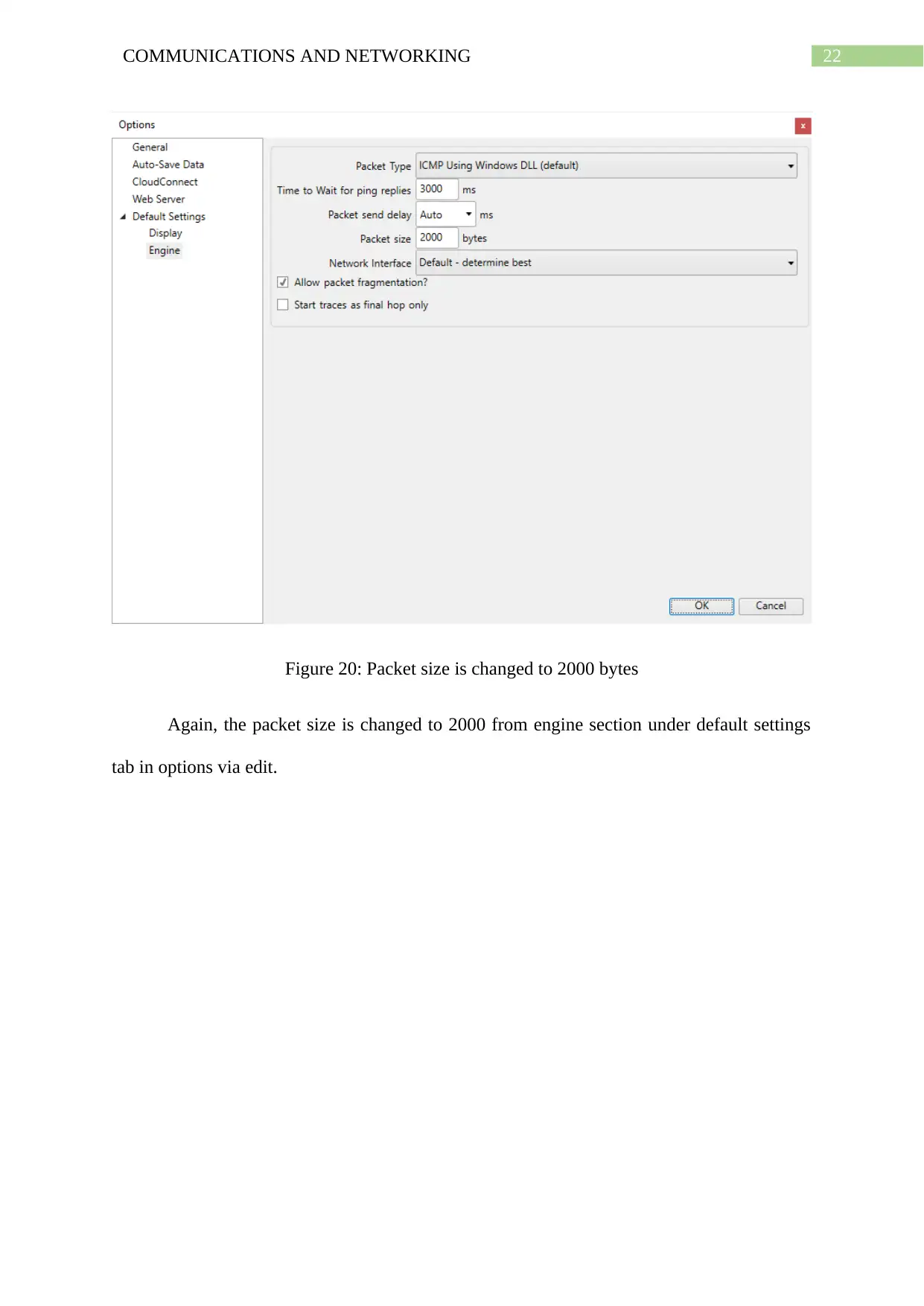
Figure 20: Packet size is changed to 2000 bytes
Again, the packet size is changed to 2000 from engine section under default settings
tab in options via edit.
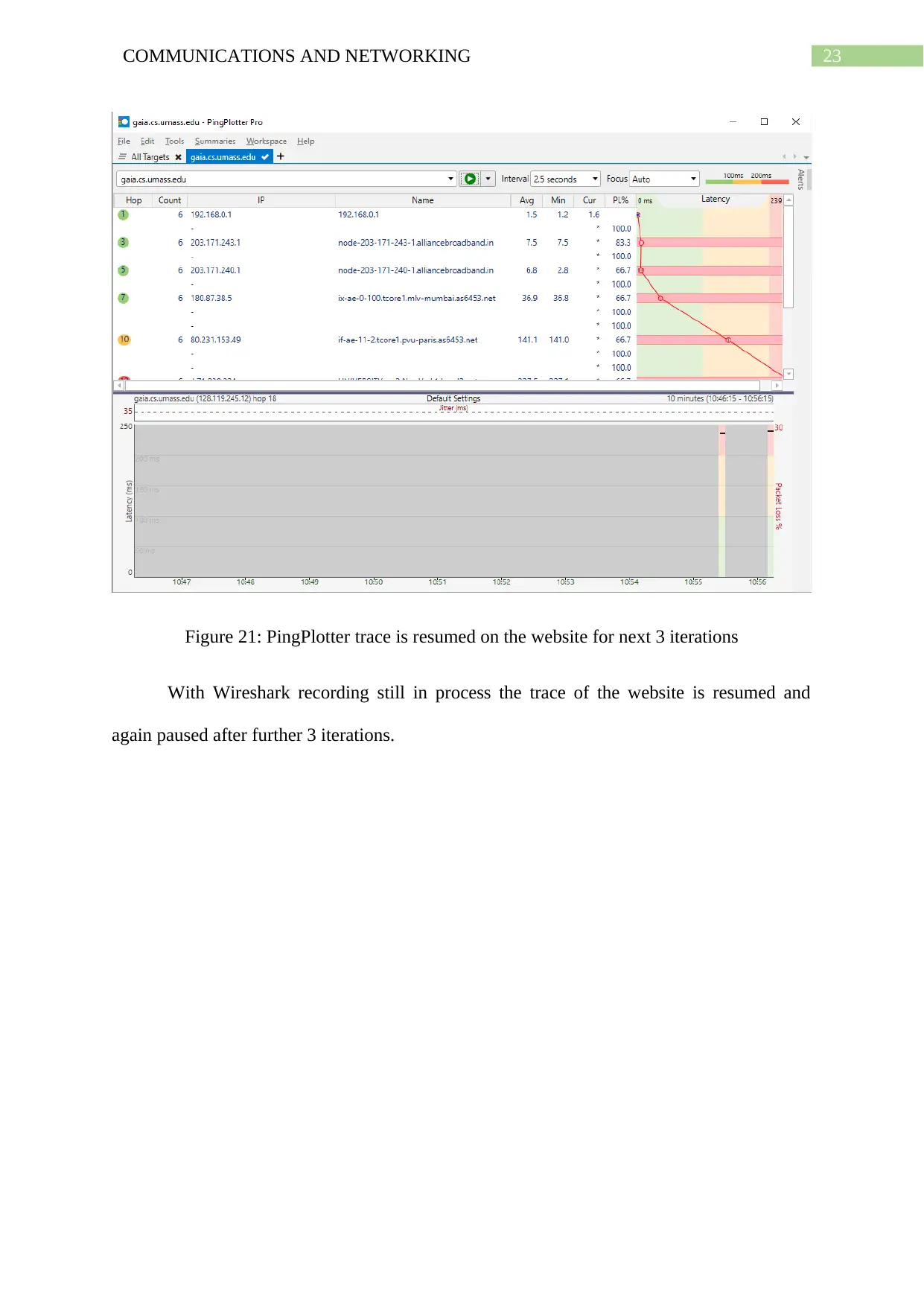
Figure 21: PingPlotter trace is resumed on the website for next 3 iterations
With Wireshark recording still in process the trace of the website is resumed and
again paused after further 3 iterations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
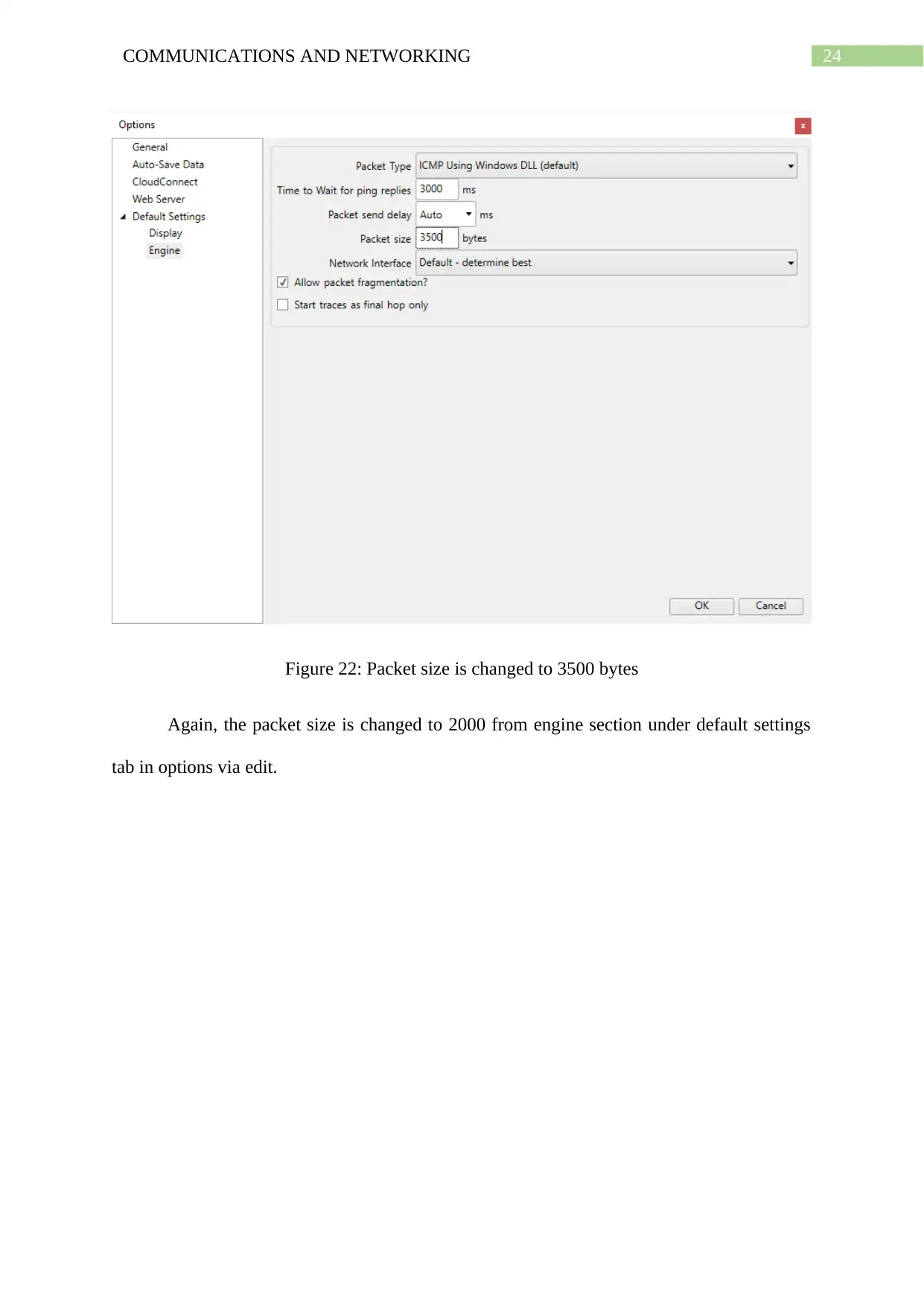
Figure 22: Packet size is changed to 3500 bytes
Again, the packet size is changed to 2000 from engine section under default settings
tab in options via edit.
Paraphrase This Document
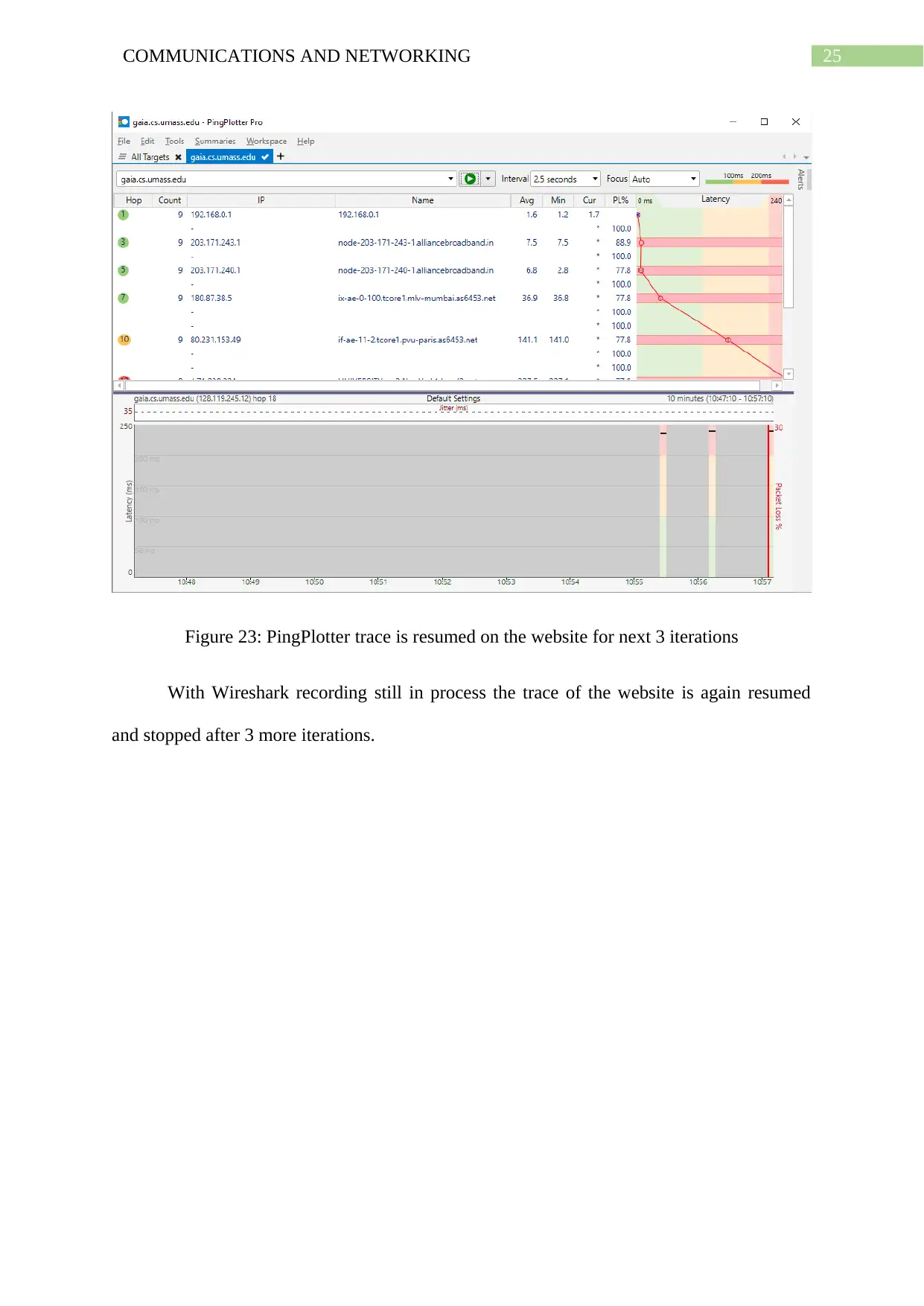
Figure 23: PingPlotter trace is resumed on the website for next 3 iterations
With Wireshark recording still in process the trace of the website is again resumed
and stopped after 3 more iterations.
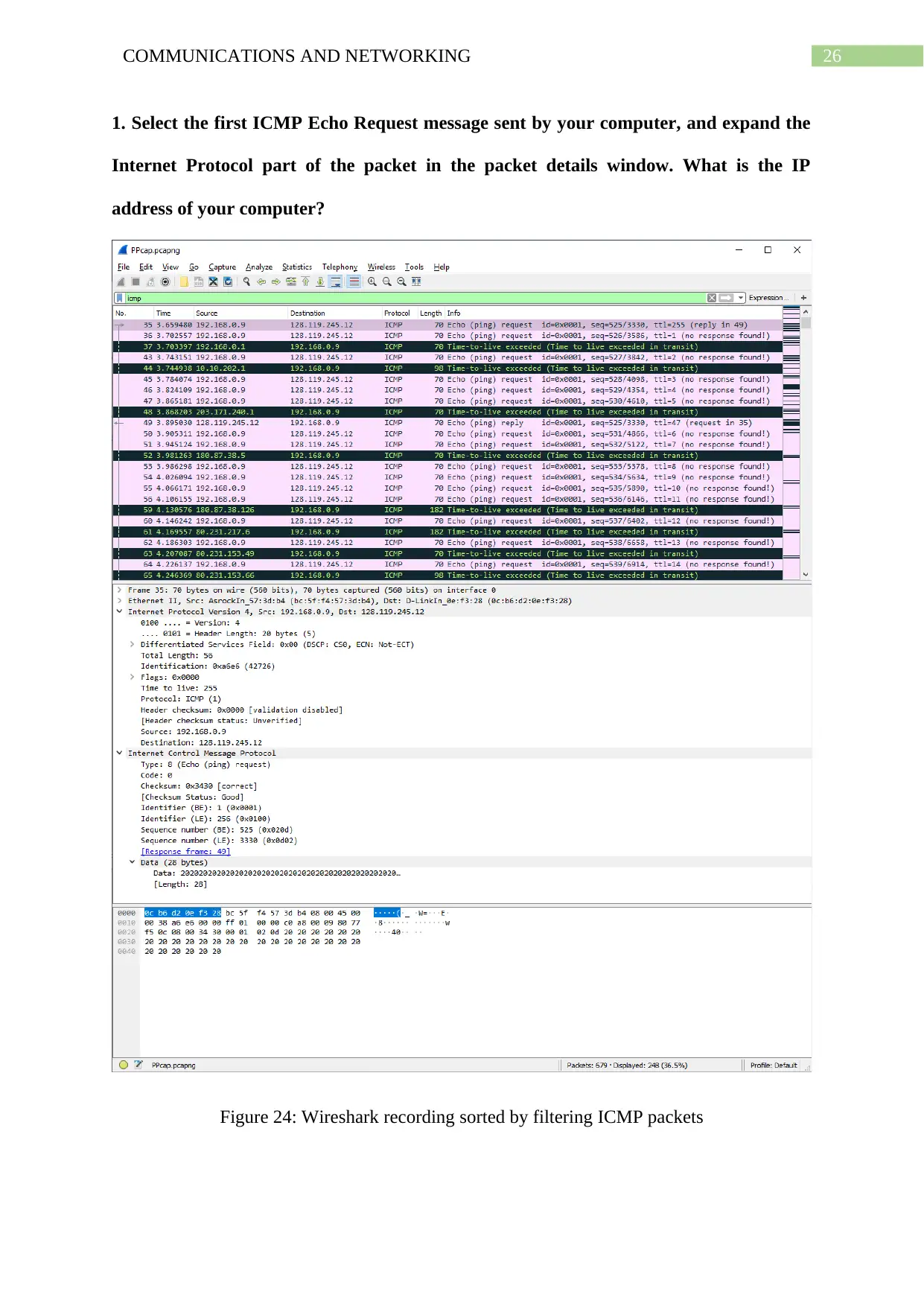
1. Select the first ICMP Echo Request message sent by your computer, and expand the
Internet Protocol part of the packet in the packet details window. What is the IP
address of your computer?
Figure 24: Wireshark recording sorted by filtering ICMP packets
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The ICMP packets are filtered in Wireshark using the filter ‘icmp’ for listing every
communication packet having protocol ICMP. Then the first packet of ICMP protocol for
echo request gets selected. Next, Internet Protocol part of the packet in Wireshark is opened
in contents window of that protocol. 192.168.0.9 is found to be the IP address of the source
host
and 128.119.245.12 is identified as the IP address of the destination host.
2. Within the IP packet header, what is the value in the upper layer protocol field?
ICMP (1) is the Upper layer protocol field’s value in the IP packet header.
3. How many bytes are in the IP header? How many bytes are in the payload of the IP
datagram? Explain how you determined the number of payload bytes.
IP header has 20 number of bytes while IP datagram payload has the following
Total length equals 56 bytes, out of which header length equals 20 bytes and as a result,
length of the payload becomes (56 – 20) or 36 bytes
Paraphrase This Document
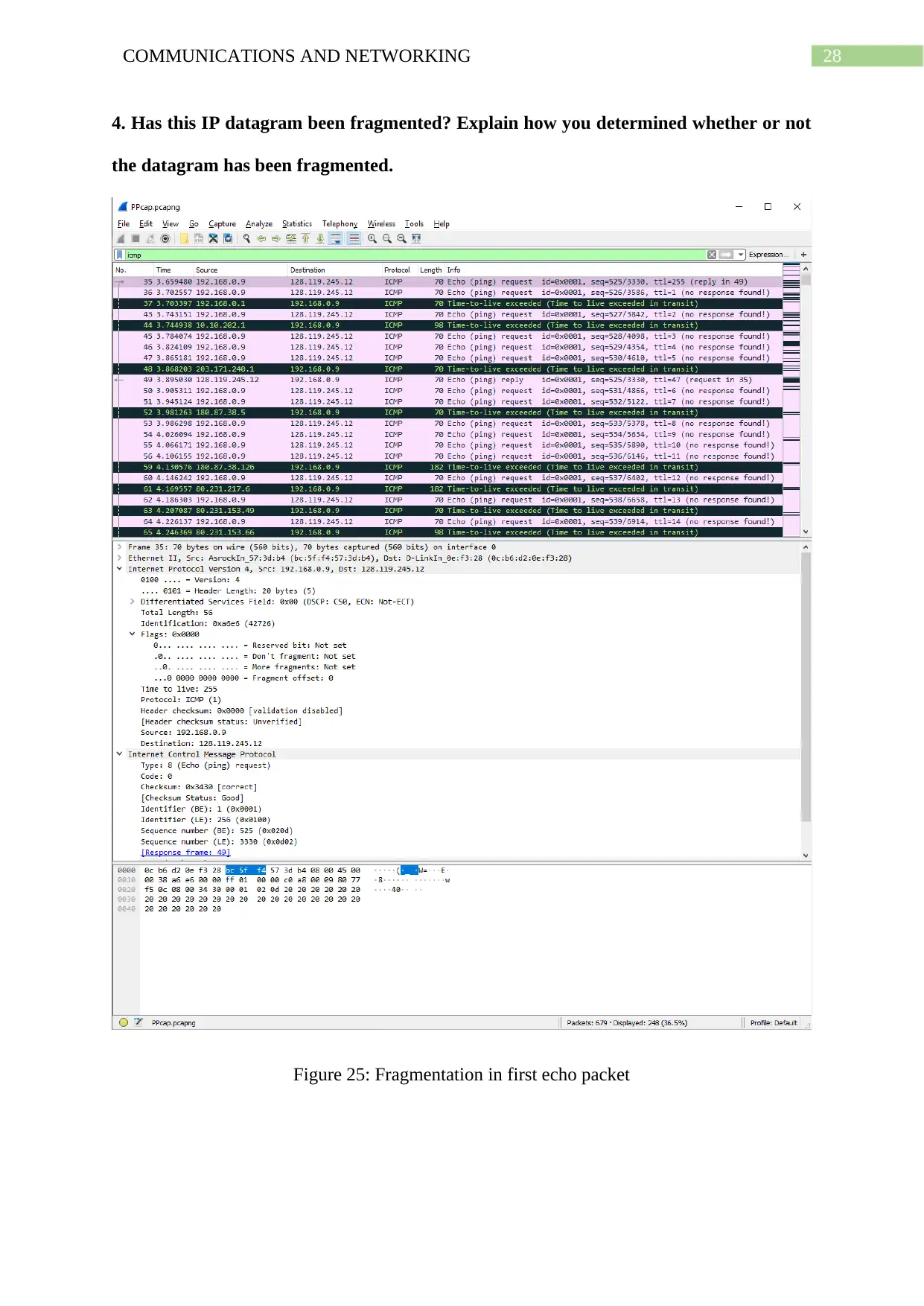
4. Has this IP datagram been fragmented? Explain how you determined whether or not
the datagram has been fragmented.
Figure 25: Fragmentation in first echo packet

Value of flags is 0x0000 as also value of don’t fragment and more fragments not set
whereas fragment offset also 0. This can only mean that the current datagram has not yet
been fragmented.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
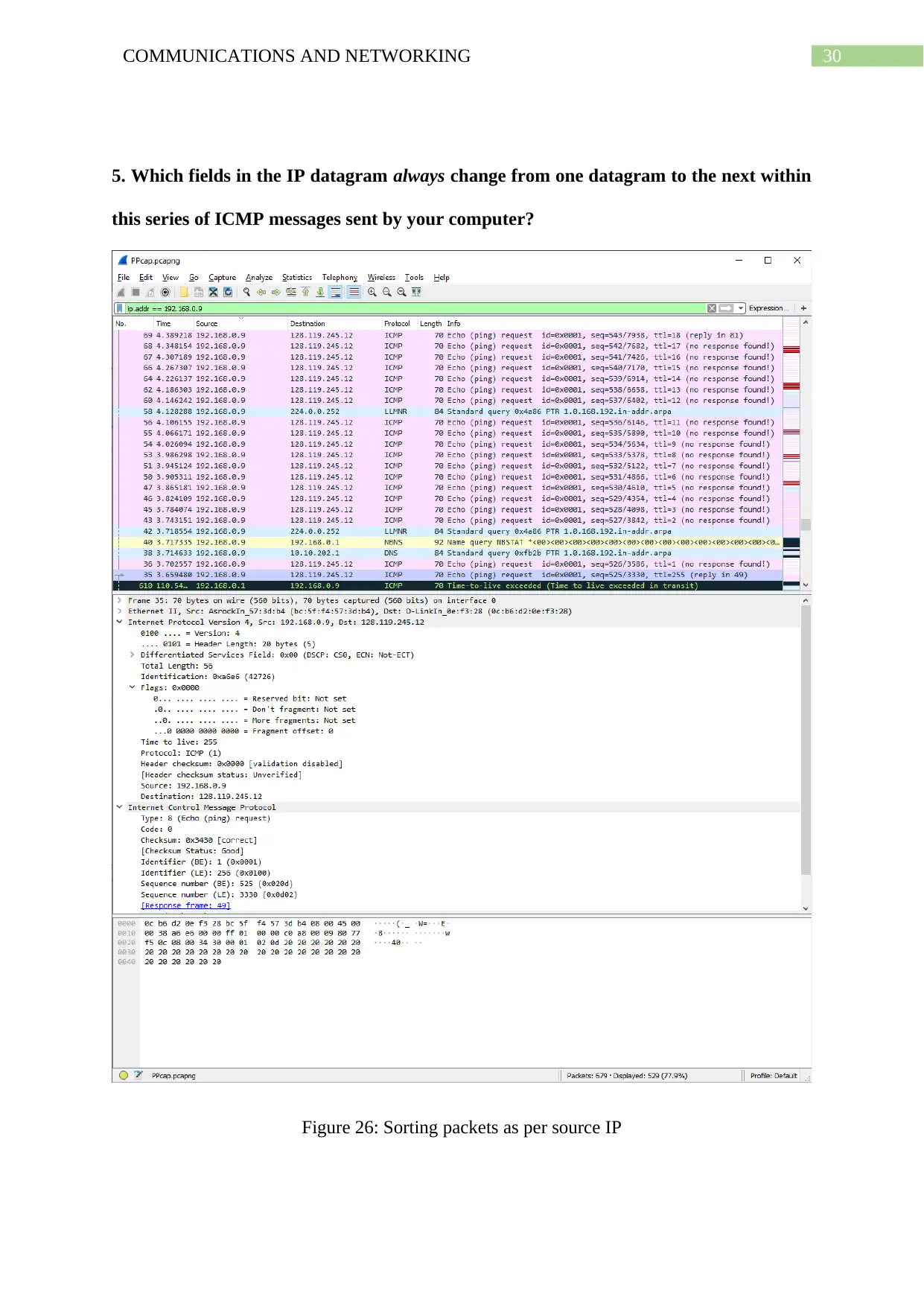
5. Which fields in the IP datagram always change from one datagram to the next within
this series of ICMP messages sent by your computer?
Figure 26: Sorting packets as per source IP
Paraphrase This Document

Packets are now sorted based on the IP address of the source host along with a small
arrow that points downward on the source column only. Also, the Internet Protocol part is
expanded.
Here, two fields time to live (TTL) field and identification field are changing with
every next datagram of the ICMP messages sent from computer.
6. Which fields stay constant? Which of the fields must stay constant? Which fields must
change? Why?
IPv4 or Internet Protocol version 4 stays constant. Header lengths don’t change here
since IPv4 is being used throughout the process. Also stays constant is source host IP address
as the same computer is conducting the entire PingPlotting trace activity. Destination IP too
don’t change because the same website (gaia.cs.umass.edu) is being traced for all packet
sizes. Protocols has to be the same since the filter to list packets of ICMP protocol is applied
and hence differentiated services as also upper layer protocol values do not change. Since
verification is disabled, header checksum does not change either.
Those fields which keeps on changing are identification field of all the IP datagrams.
The value of such identification fields decreases in number for every next packet.
Also changing is the field called Time to live (TTL) which is usual for all trace route
activities.
7. Describe the pattern you see in the values in the Identification field of the IP
datagram
The value of identification decreases for every upcoming datagram
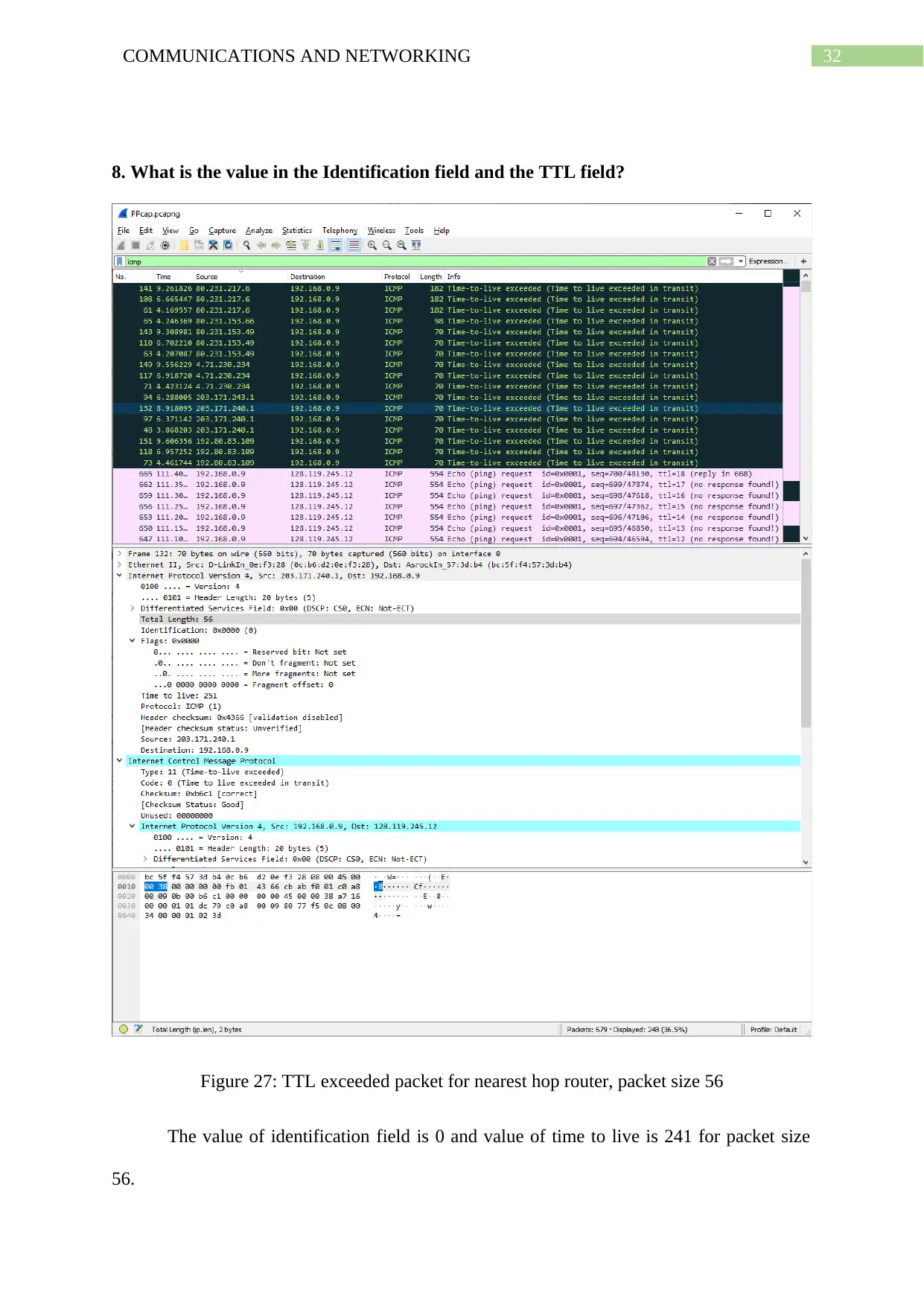
8. What is the value in the Identification field and the TTL field?
Figure 27: TTL exceeded packet for nearest hop router, packet size 56
The value of identification field is 0 and value of time to live is 241 for packet size
56.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
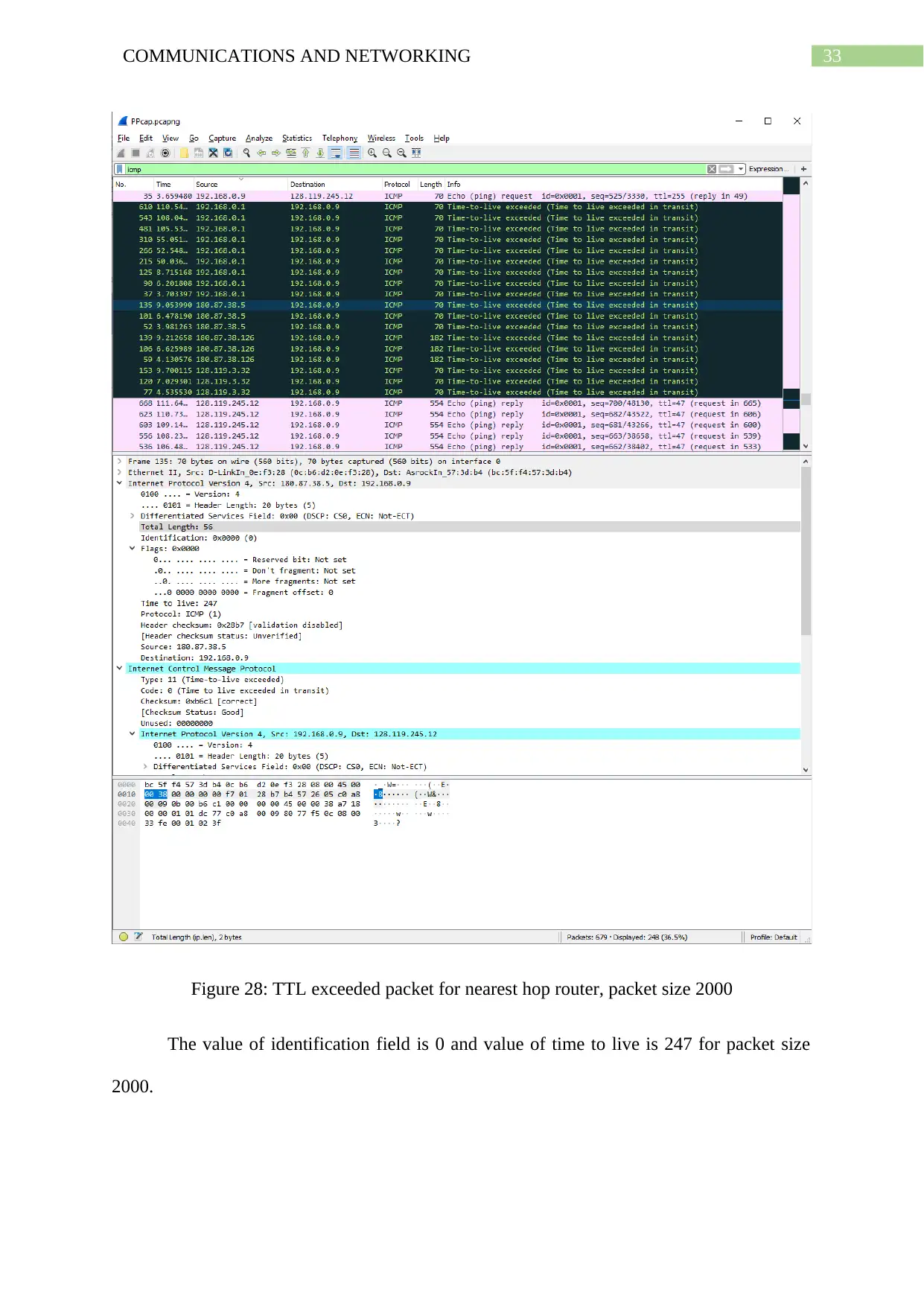
Figure 28: TTL exceeded packet for nearest hop router, packet size 2000
The value of identification field is 0 and value of time to live is 247 for packet size
2000.
Paraphrase This Document
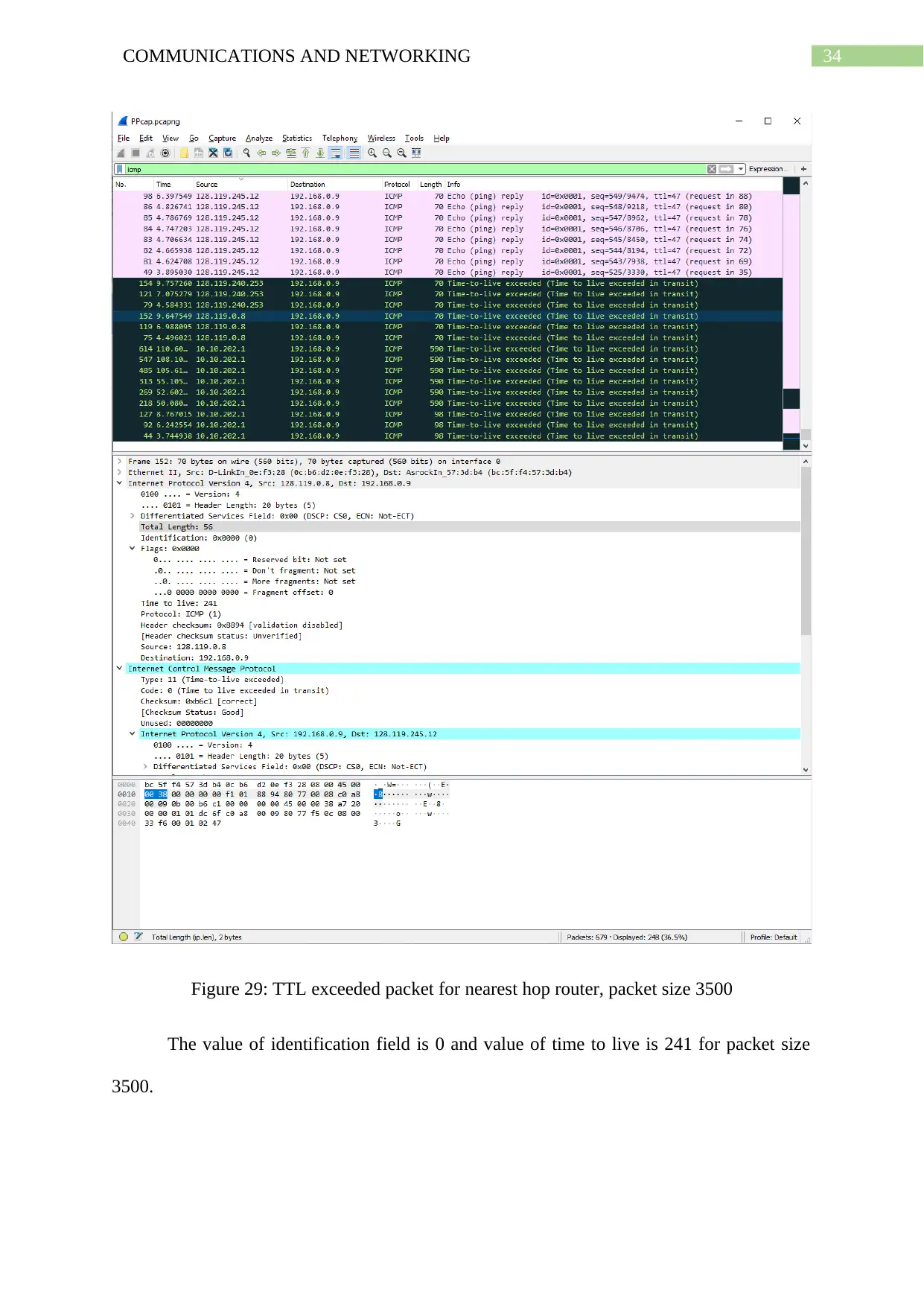
Figure 29: TTL exceeded packet for nearest hop router, packet size 3500
The value of identification field is 0 and value of time to live is 241 for packet size
3500.

9. Do these values remain unchanged for all of the ICMP TTL-exceeded replies sent to
your computer by the nearest (first hop) router? Why?
The fields of ICMP TTL exceeded by a factor of 6 each time as the same trace route is
run, first 3 times for 56, then for 2000 and lastly for 3500.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
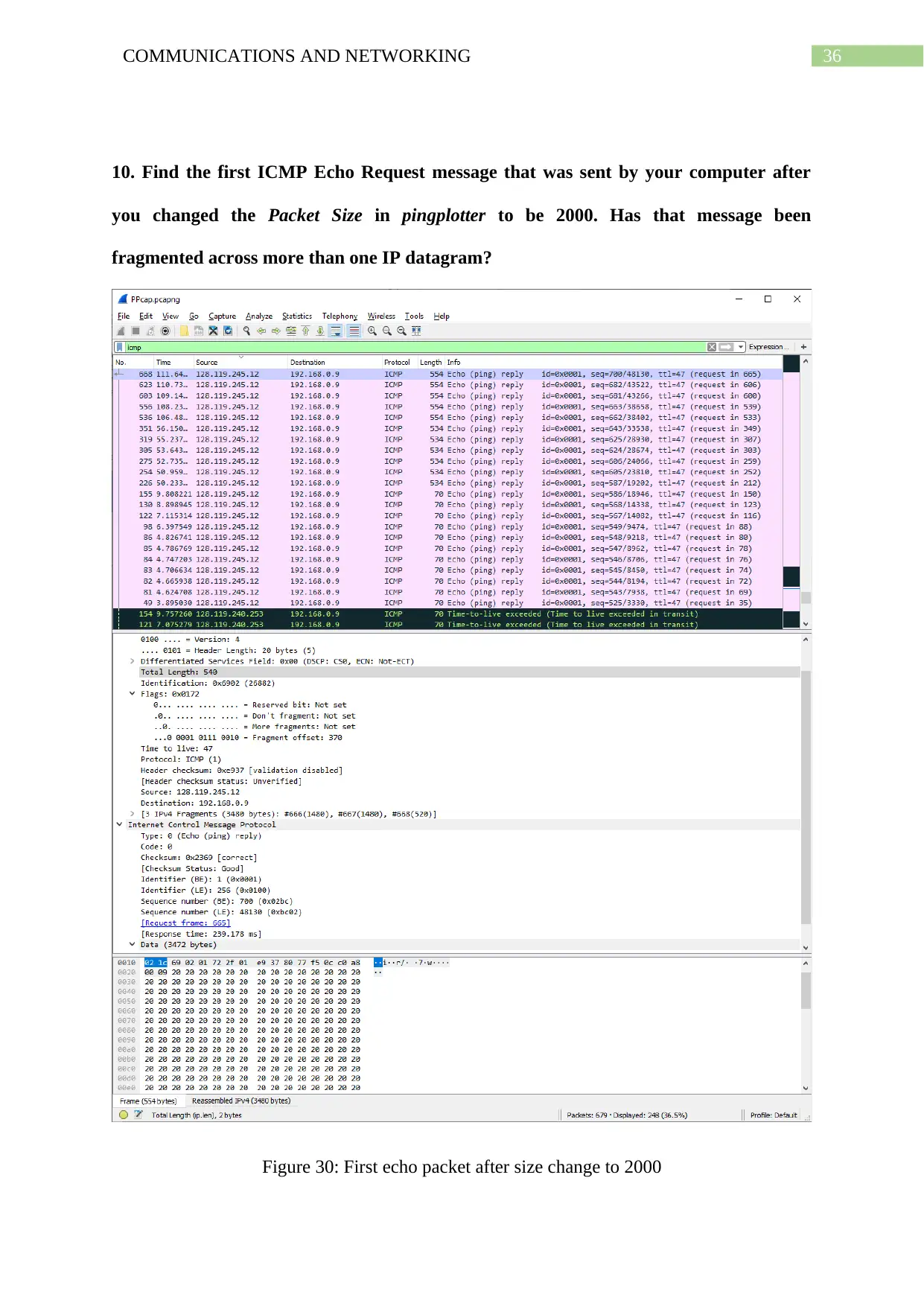
10. Find the first ICMP Echo Request message that was sent by your computer after
you changed the Packet Size in pingplotter to be 2000. Has that message been
fragmented across more than one IP datagram?
Figure 30: First echo packet after size change to 2000
Paraphrase This Document
From the offset it can be noted that wireshark is showing all the fragments together
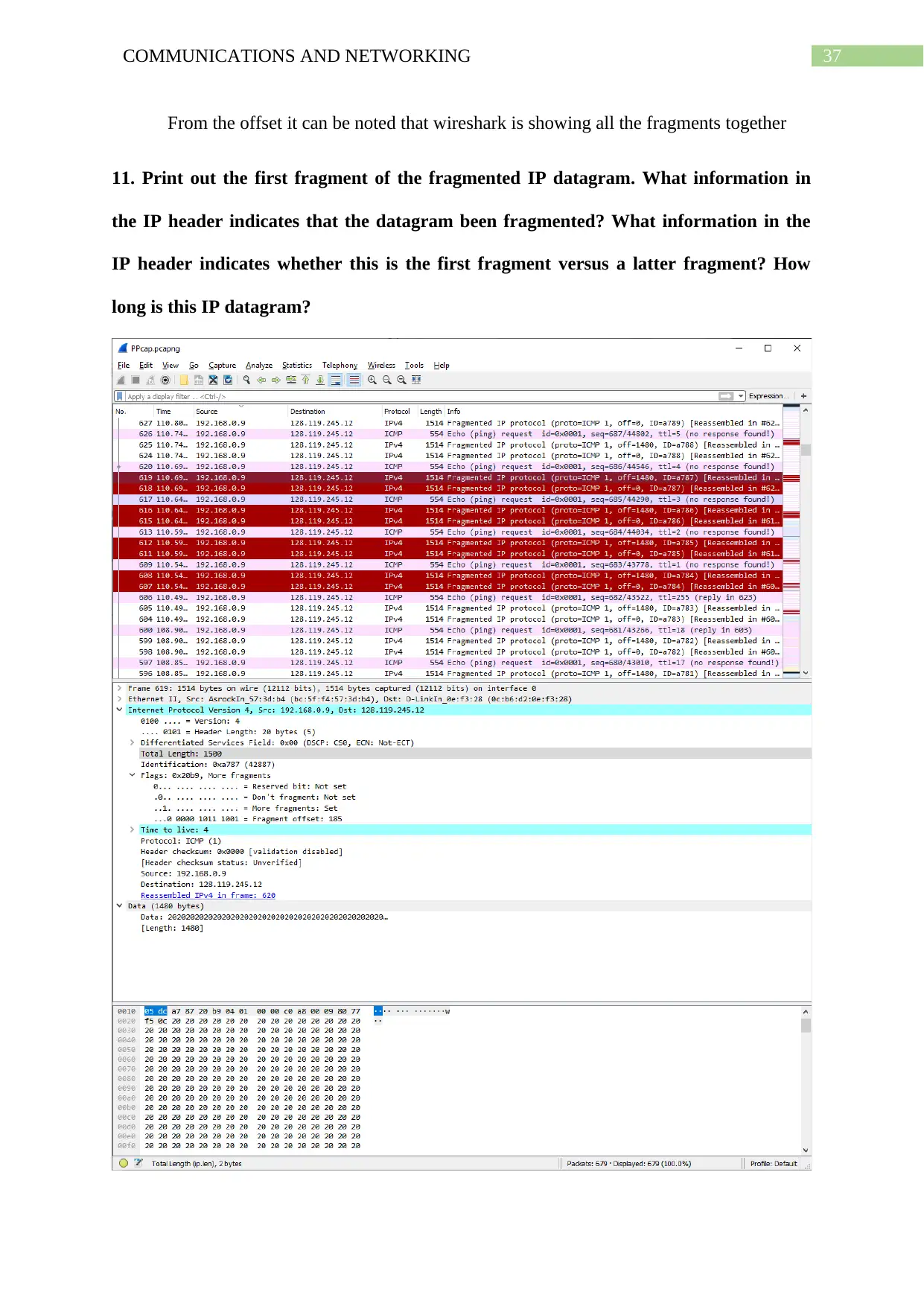
11. Print out the first fragment of the fragmented IP datagram. What information in
the IP header indicates that the datagram been fragmented? What information in the
IP header indicates whether this is the first fragment versus a latter fragment? How
long is this IP datagram?

Figure 31: First fragment of fragmented IP datagram
Total length of IP datagram appears to be 1500 while ‘More fragments’ is set and
value is 1. Fragment offset has value of 185. This is enough to suggest the datagram is
fragmented. Out of the four fragments its identification is higher and hence it is the first
fragment.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
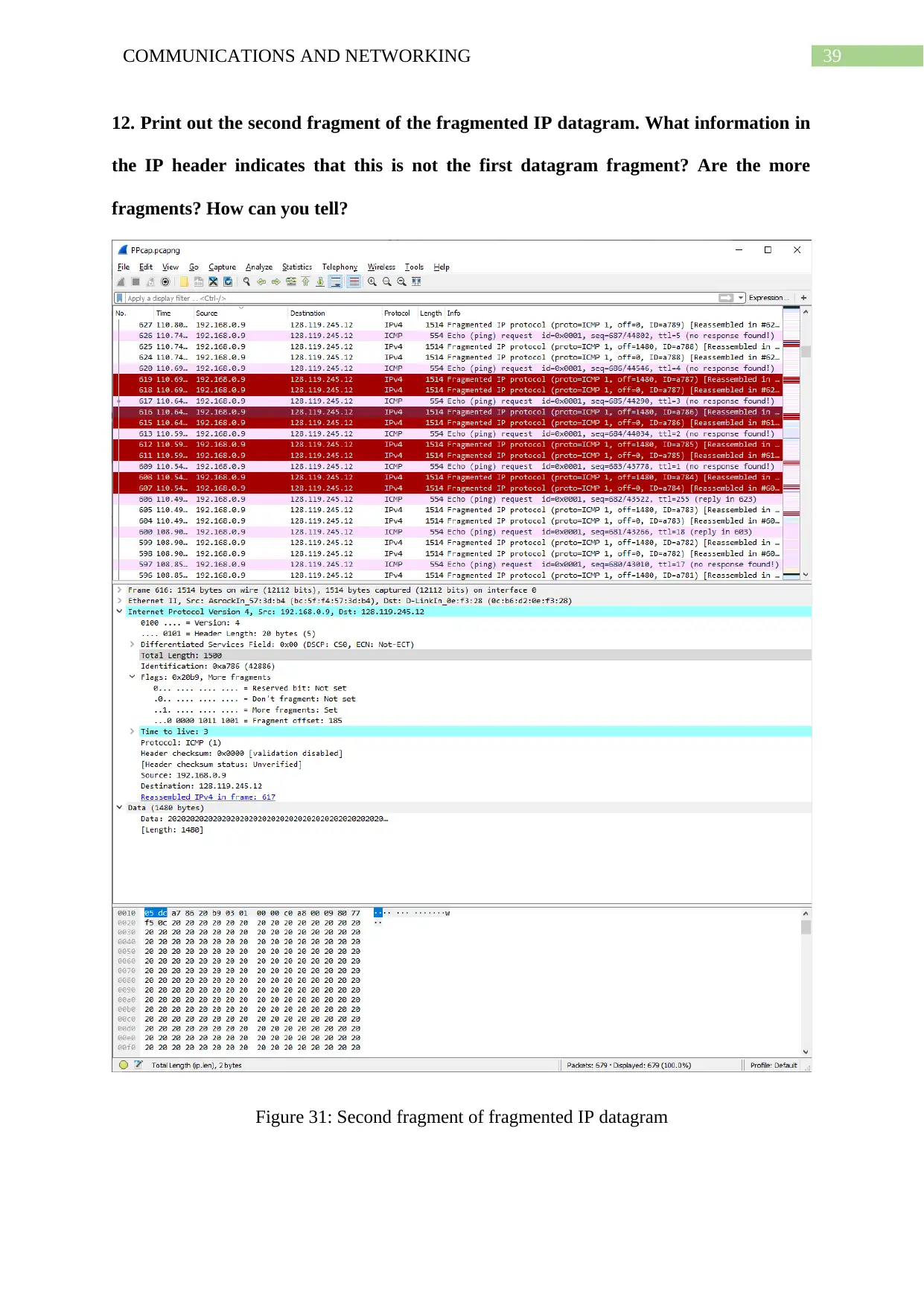
12. Print out the second fragment of the fragmented IP datagram. What information in
the IP header indicates that this is not the first datagram fragment? Are the more
fragments? How can you tell?
Figure 31: Second fragment of fragmented IP datagram
Paraphrase This Document

The identification field value is less than that of previous packet of first fragment,
hence this is the second fragment and more fragments set to 1 means, more fragments exist.
13. What fields change in the IP header between the first and second fragment?
The fields identification and TTL (4, 3) changes between the first and second
fragments.
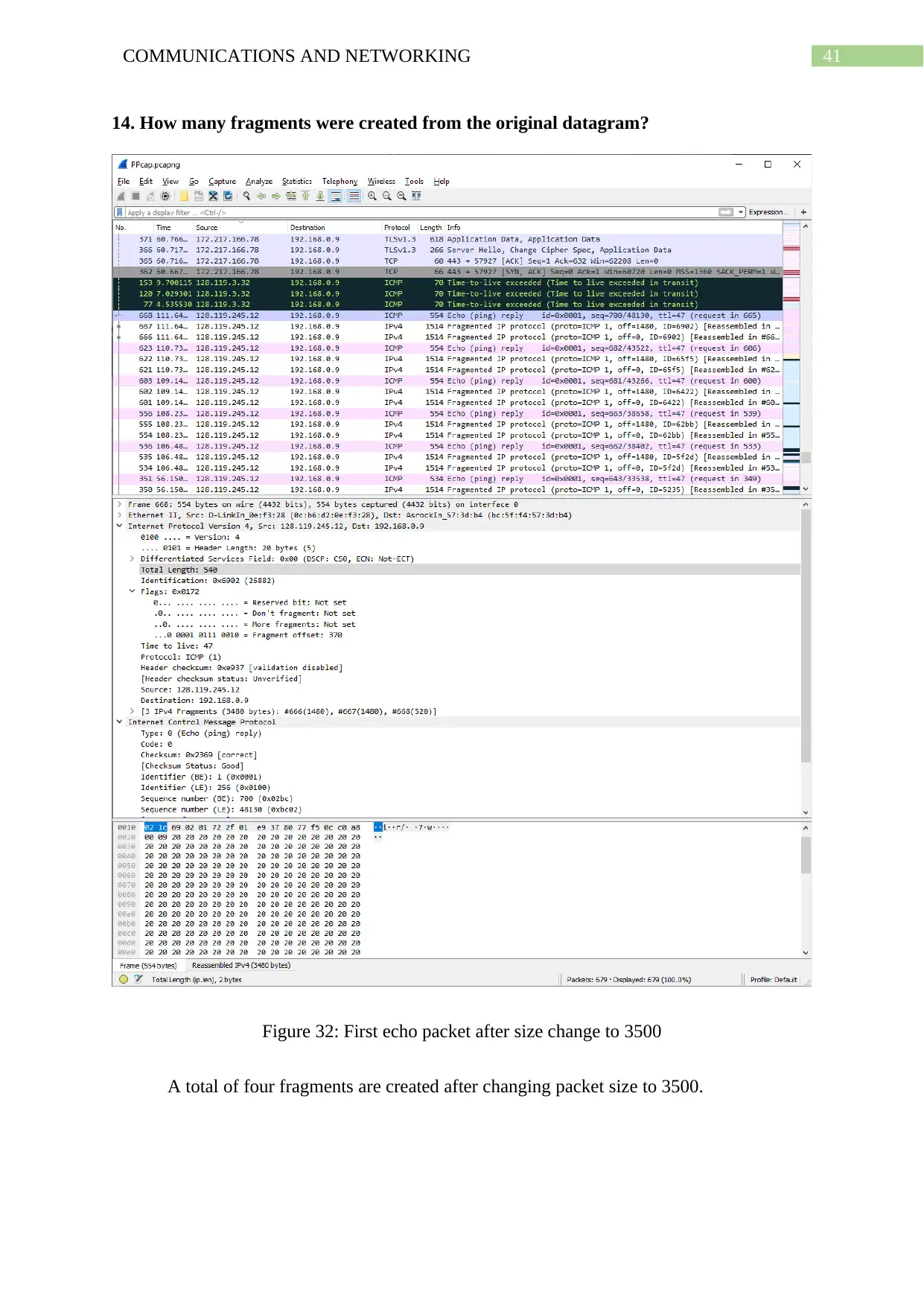
14. How many fragments were created from the original datagram?
Figure 32: First echo packet after size change to 3500
A total of four fragments are created after changing packet size to 3500.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

15. What fields change in the IP header among the fragments?
The fields that change among the four fragments are identification and TTL (4, 3, 2,
1).
Conclusion
To conclude this report succeeds in accurately recording and conducting a thorough
study of the ping, and traceroute activities of three different websites located in different
continents (Europe and North America) than the place from where the network analysis is
being conducted that is Asia. The report is observed to perform a ping of the website
www.ece.ust.eu and discusses the IP address and ports of the source and destination hosts as
well as goes in depth into the protocol contents of ping request and reply packets. Then the
trace of another website www.inria.fr is conducted and thorough research on ICMP packets
and their comparison with that of the ping are made before finding the link with the longest
delay. Thereafter, a trace is performed on gaia.cs.umass.edu is performed in PingPlotter to get
a more comprehensive look at the nearest first hop routers, their location as also the graph of
the latencies of each step. This is a composite process conducted for three different packet
sizes (56 bytes, 2000 bytes, 3500 bytes). Here, the contents of the IP protocol get further
analysed and it is checked if datagrams got fragmented and also details and comparison of the
identified fragments for different packet sizes are performed.
Bibliography
Abusair, M., Di Marco, A. and Inverardi, P., 2017, September. An empirical approach for
determining context of mobile systems. In Proceedings of the 11th European Conference on
Software Architecture: Companion Proceedings (pp. 71-77). ACM.
Paraphrase This Document

Aly, M., Khomh, F., Guéhéneuc, Y.G., Washizaki, H. and Yacout, S., 2018. Is Fragmentation
a Threat to the Success of the Internet of Things?. IEEE Internet of Things Journal, 6(1),
pp.472-487.
Bouyeddou, B., Harrou, F., Sun, Y. and Kadri, B., 2018. Detection of smurf flooding attacks
using Kullback-Leibler-based scheme.
Brown, J.D. and Willink, T.J., 2018. ARP Cache Poisoning and Routing Loops in ad Hoc
Networks. Mobile Networks and Applications, 23(5), pp.1306-1317.
Davis, R.C., 2015. Teaching the network: A brief demonstration of the internet's structure for
information literacy instruction. Behavioral & Social Sciences Librarian, 34(2), pp.88-94.
Elamaran, V., Arunkumar, N., Babu, G.V., Balaji, V.S., Gómez, J., Figueroa, C. and
Ramirez-González, G., 2018. Exploring DNS, HTTP, and ICMP response time computations
on brain signal/image databases using a packet sniffer tool. IEEE Access, 6, pp.59672-59678.
Glasser, D., 2018. Longitudinal study of large-scale traceroute results. Naval Postgraduate
School Monterey United States.
Guo, H. and Heidemann, J., 2018, March. Detecting ICMP rate limiting in the Internet. In
International Conference on Passive and Active Network Measurement (pp. 3-17). Springer,
Cham.
Harshita, H., 2017. Detection and prevention of ICMP flood DDOS attack. International
Journal of New Technology and Research, 3(3).
Huston, G., Hinden, R., Troan, O., Gont, F. and Fragile, I.F.C., 2018. Internet Area WG R.
Bonica Internet-Draft Juniper Networks Intended status: Best Current Practice F. Baker
Expires: December 12, 2018 Unaffiliated.

Huston, G., Hinden, R., Troan, O., Gont, F. and Fragile, I.F.C., 2018. Internet Area WG R.
Bonica Internet-Draft Juniper Networks Intended status: Best Current Practice F. Baker
Expires: January 24, 2019 Unaffiliated.
Lone, Q., Luckie, M., Korczyński, M. and van Eeten, M., 2017, March. Using loops observed
in traceroute to infer the ability to spoof. In International Conference on Passive and Active
Network Measurement (pp. 229-241). Springer, Cham.
Mandalari, A.M., Lutu, A., Briscoe, B., Bagnulo, M. and Alay, O., 2018. Measuring ECN++:
Good News for++, Bad News for ECN over Mobile. IEEE Communications Magazine, 56(3),
pp.180-186.
Mirsky, Y., Kalbo, N., Elovici, Y. and Shabtai, A., 2018. Vesper: Using Echo Analysis to
Detect Man-in-the-Middle Attacks in LANs. IEEE Transactions on Information Forensics
and Security, 14(6), pp.1638-1653.
Morandi, I., Bronzino, F., Teixeira, R. and Sundaresan, S., 2019, March. Service Traceroute:
Tracing Paths of Application Flows. In International Conference on Passive and Active
Network Measurement (pp. 116-128). Springer, Cham.
Mosko, M. and Wood, C.A., 2015, October. Secure fragmentation for content centric
networking. In 2015 IEEE 12th International Conference on Mobile Ad Hoc and Sensor
Systems (pp. 506-512). IEEE.
Nakibly, G., Schcolnik, J. and Rubin, Y., 2016. Website-targeted false content injection by
network operators. In 25th {USENIX} Security Symposium ({USENIX} Security 16) (pp. 227-
244).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Papadopoulos, G.Z., Thubert, P., Tsakalidis, S. and Montavont, N., 2018, October. RFC
4944: Per-hop Fragmentation and Reassembly Issues. In 2018 IEEE Conference on
Standards for Communications and Networking (CSCN) (pp. 1-6). IEEE.
Ramon, J. and Williams, D., 2017. Downtime Tracker. iCascade, 1(1).
Ravaioli, R., Urvoy-Keller, G. and Barakat, C., 2015, June. Characterizing icmp rate
limitation on routers. In 2015 IEEE International Conference on Communications (ICC) (pp.
6043-6049). IEEE.
Sayadi, S., Abbes, T. and Bouhoula, A., 2017, October. Detection of Covert Channels Over
ICMP Protocol. In 2017 IEEE/ACS 14th International Conference on Computer Systems and
Applications (AICCSA) (pp. 1247-1252). IEEE.
Suradi, A. and Prasetyo, H.J., 2015. CONTINGENCY PLANNING PADA WEBSITE
UNIVERSITAS WIDYA DHARMA. Jurnal Teknologi Informasi Respati, 10(29).
Tilli, J.M. and Kantola, R., 2017, September. Data plane protocols and fragmentation for 5G.
In 2017 IEEE Conference on Standards for Communications and Networking (CSCN) (pp.
207-213). IEEE.
Vegoda, L., 2017. Updates to Special-Purpose IP Address Registries draft-bchv-rfc6890bis-
07.
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
© 2024 | Zucol Services PVT LTD | All rights reserved.





