Communications and Networking
Form a group of 2 students and complete the lab according to the instructions. Answer all questions, provide screenshots, and explain your answers in 1-2 sentences. Include a coversheet with group members and contributions. Refer to relevant materials for guidance.
46 Pages4791 Words23 Views
Added on 2023-01-17
About This Document
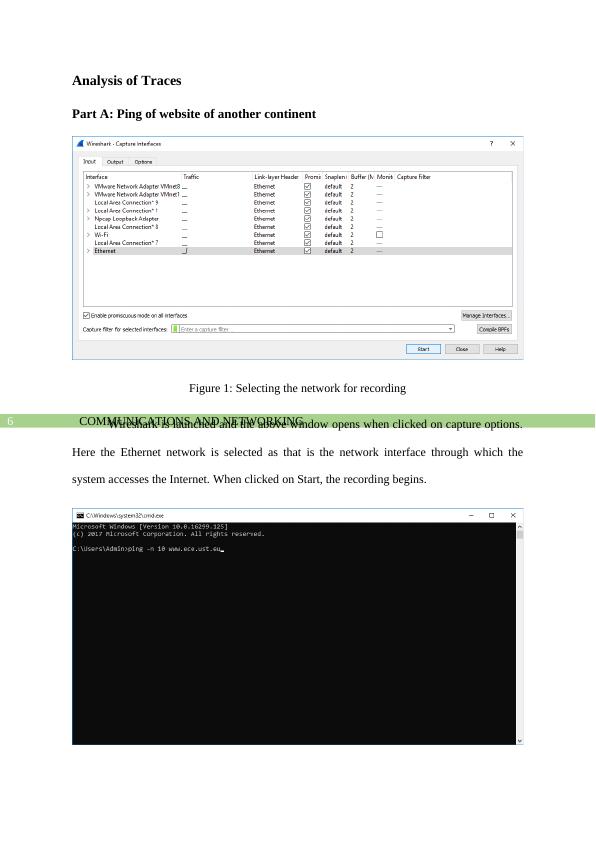
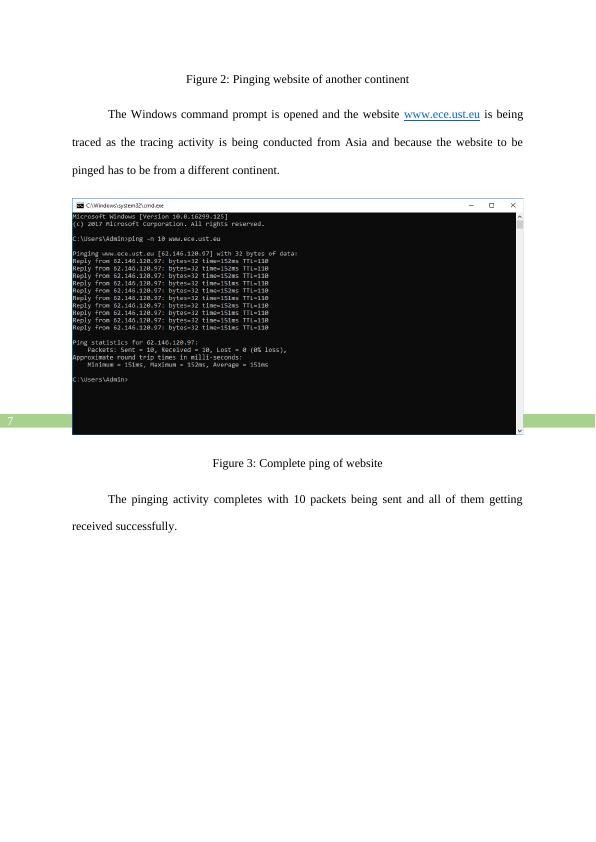
This report aims to record and study the pinging, and tracing activities of three different websites located in a different continent (Europe and North America) than the place from where the network analysis is being conducted that is Asia. First the report performs a ping of the website www.ece.ust.eu and discusses the IP address and ports of the source and destination hosts as well as goes in depth into the protocol contents of ping request and reply packets.
Communications and Networking
Form a group of 2 students and complete the lab according to the instructions. Answer all questions, provide screenshots, and explain your answers in 1-2 sentences. Include a coversheet with group members and contributions. Refer to relevant materials for guidance.
Added on 2023-01-17
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Research and Analysis of Networks
|23
|1613
|478
Data Communication: ICMP and Ping, ICMP and Traceroute, Captured Trace, Fragmentation
|14
|1747
|221
ICMP Protocols with Wireshark
|17
|2228
|389
Data Communication
|18
|1719
|295
Networking and Communication
|14
|1369
|163
Packet Capture of Websites through Pinging and Tracing Methods
|40
|2589
|38