Cloud Computing and SDN Security Problems: A Comprehensive Report
VerifiedAdded on 2023/03/29
|12
|753
|96
Report
AI Summary
This report provides an overview of cloud computing and its associated network security challenges. It begins with an introduction to network security and cloud computing, highlighting its adoption by companies for data storage. The report then explores various cloud computing models, including Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS), along with their advantages. It delves into the importance of security information and identifies common security problems, such as staff issues, coding mistakes, and unauthorized devices. The report proposes solutions like a holistic approach and encryption to mitigate these problems. The conclusion emphasizes the role of technological advancements and cloud computing in enhancing security and reducing unauthorized data access. References to relevant research papers are also included.

COMMUNICATIONS NETWORK SECURITY
( CLOUD COMPUTING AND SOFTWARE DEFINED NETWORKS SECURITY PROBLEMS)
( CLOUD COMPUTING AND SOFTWARE DEFINED NETWORKS SECURITY PROBLEMS)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
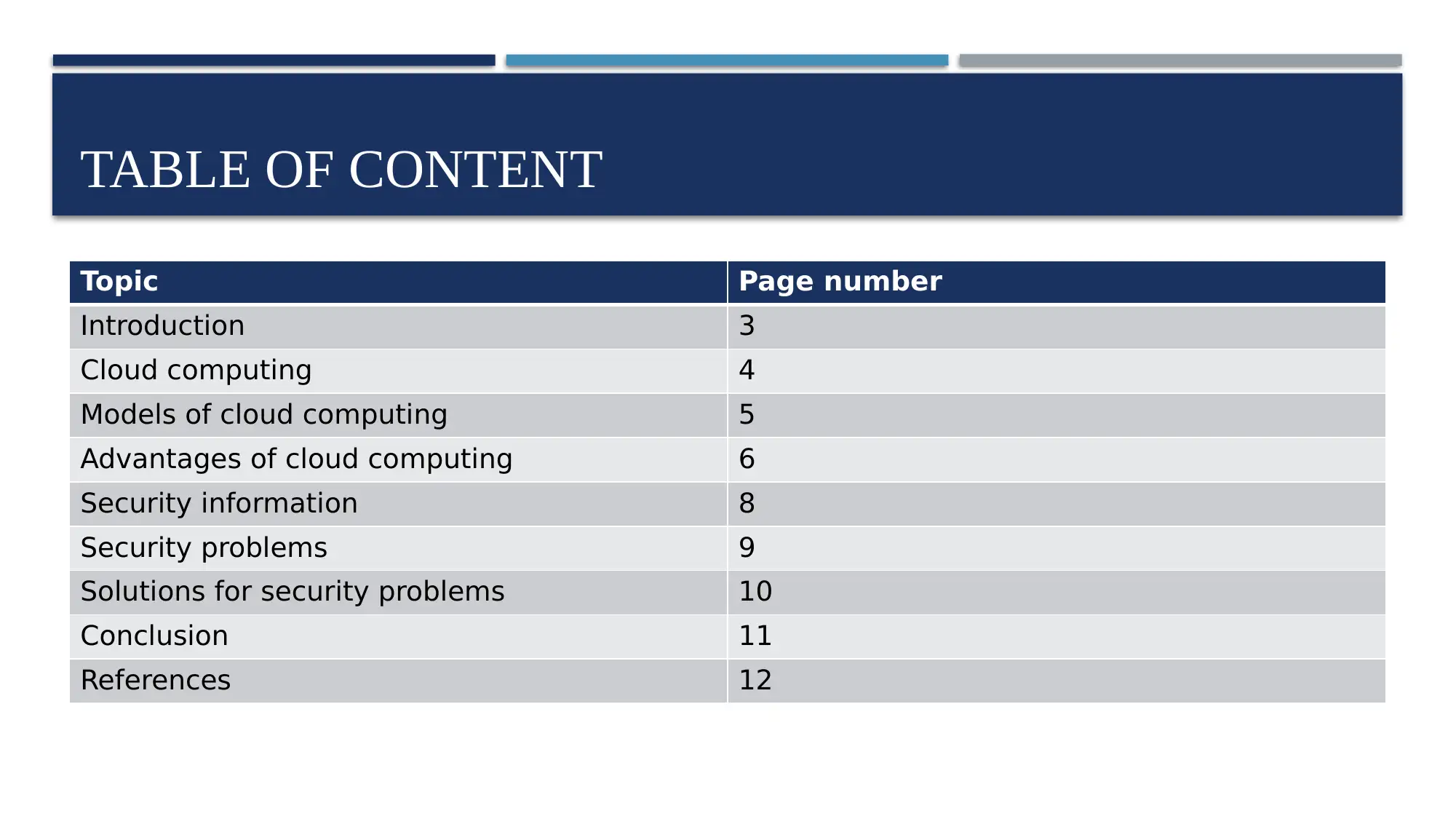
TABLE OF CONTENT
Topic Page number
Introduction 3
Cloud computing 4
Models of cloud computing 5
Advantages of cloud computing 6
Security information 8
Security problems 9
Solutions for security problems 10
Conclusion 11
References 12
Topic Page number
Introduction 3
Cloud computing 4
Models of cloud computing 5
Advantages of cloud computing 6
Security information 8
Security problems 9
Solutions for security problems 10
Conclusion 11
References 12

INTRODUCTION
Network securities are some kind of policies and practices which are adopted by some
organizations in order to prevent the misuse of data
The present report is based on cloud computing which is used by companies and
individual so that they can save their data at safe place.
In this context, it explains the concept of cloud computing and its networking issues
or problems which are faced by companies.
Network securities are some kind of policies and practices which are adopted by some
organizations in order to prevent the misuse of data
The present report is based on cloud computing which is used by companies and
individual so that they can save their data at safe place.
In this context, it explains the concept of cloud computing and its networking issues
or problems which are faced by companies.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CLOUD COMPUTING
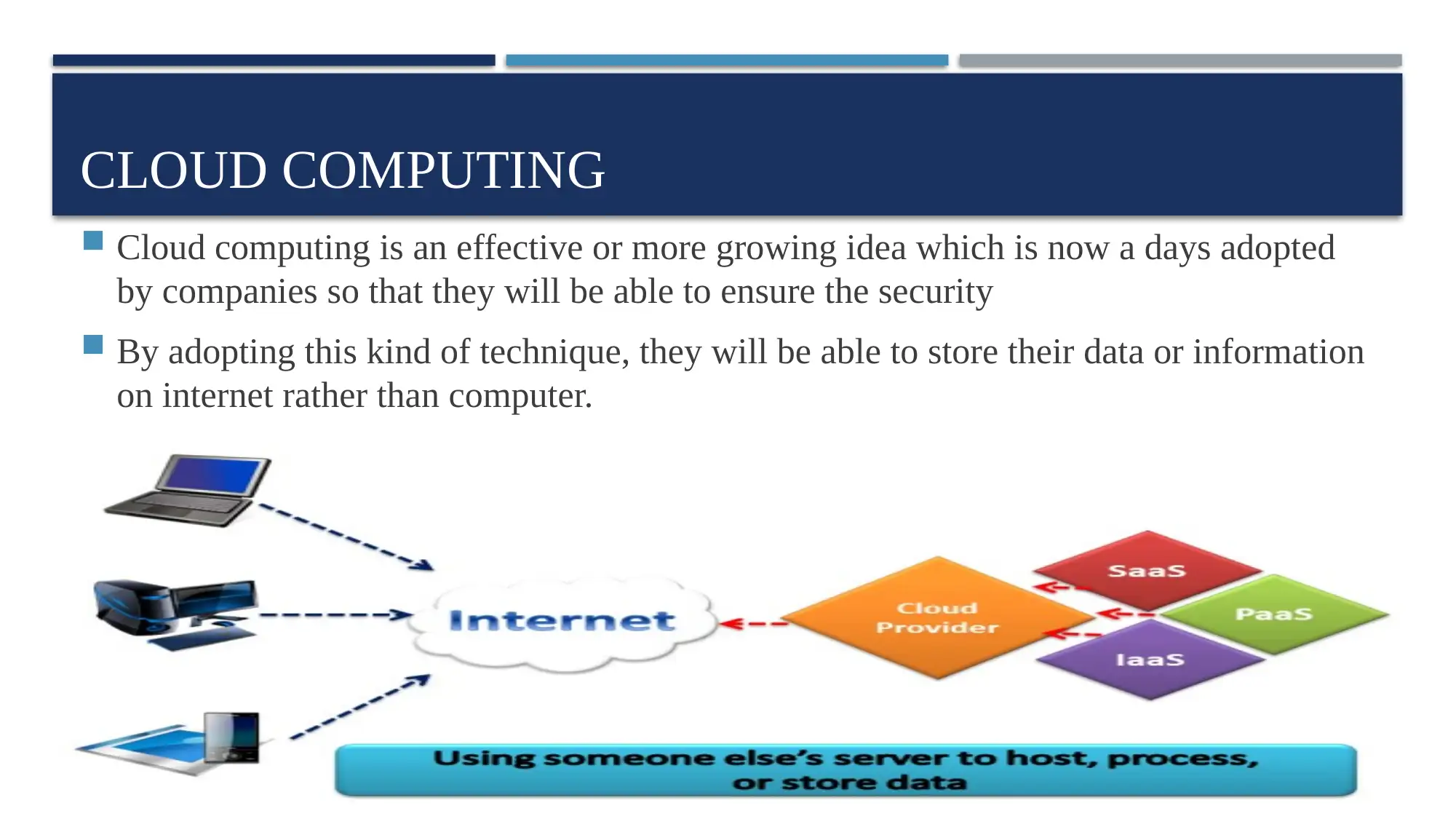
Cloud computing is an effective or more growing idea which is now a days adopted
by companies so that they will be able to ensure the security
By adopting this kind of technique, they will be able to store their data or information
on internet rather than computer.
Cloud computing is an effective or more growing idea which is now a days adopted
by companies so that they will be able to ensure the security
By adopting this kind of technique, they will be able to store their data or information
on internet rather than computer.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MODELS OF CLOUD COMPUTING
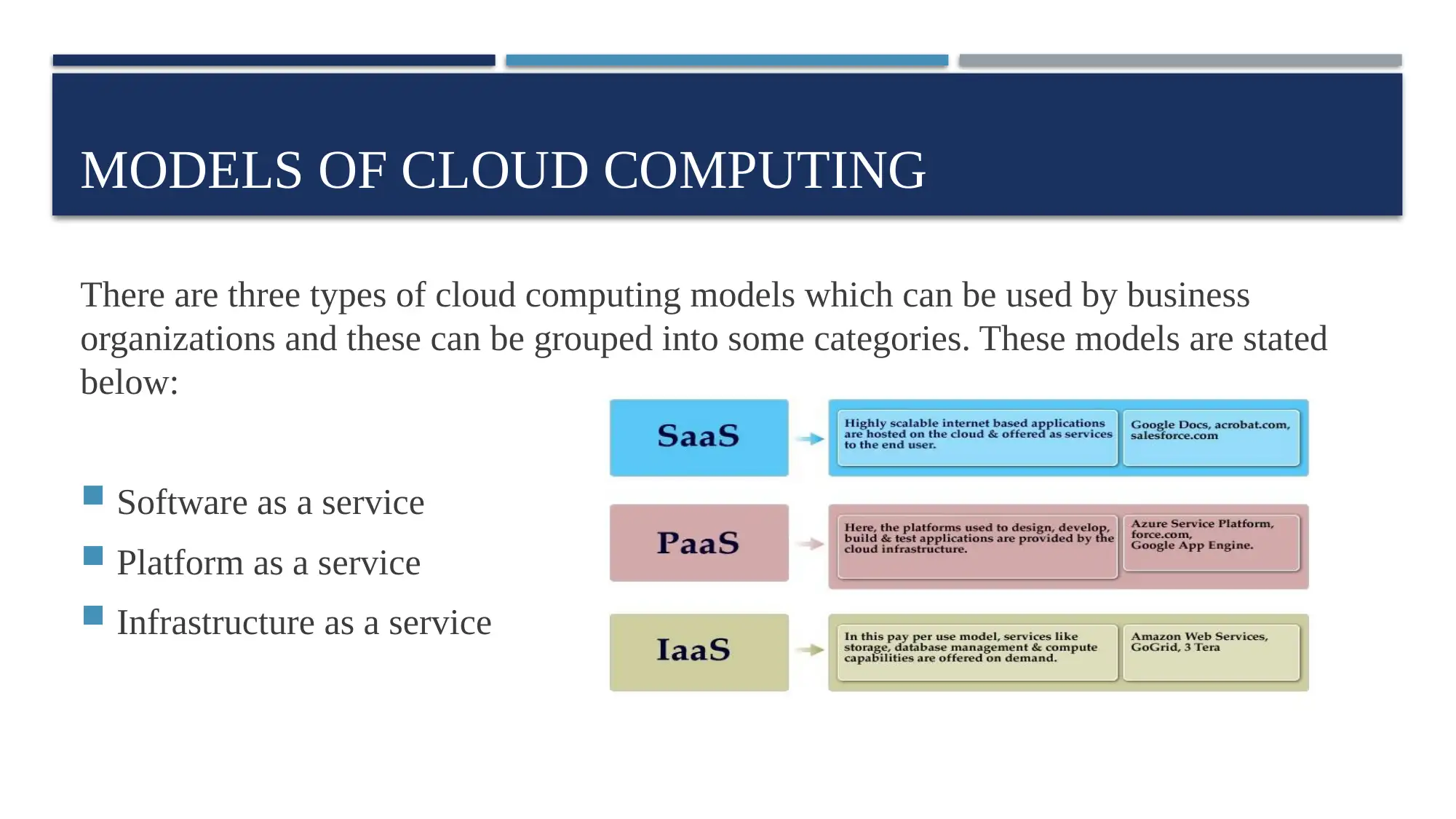
There are three types of cloud computing models which can be used by business
organizations and these can be grouped into some categories. These models are stated
below:
Software as a service
Platform as a service
Infrastructure as a service
There are three types of cloud computing models which can be used by business
organizations and these can be grouped into some categories. These models are stated
below:
Software as a service
Platform as a service
Infrastructure as a service

ADVANTAGES OF CLOUD COMPUTING
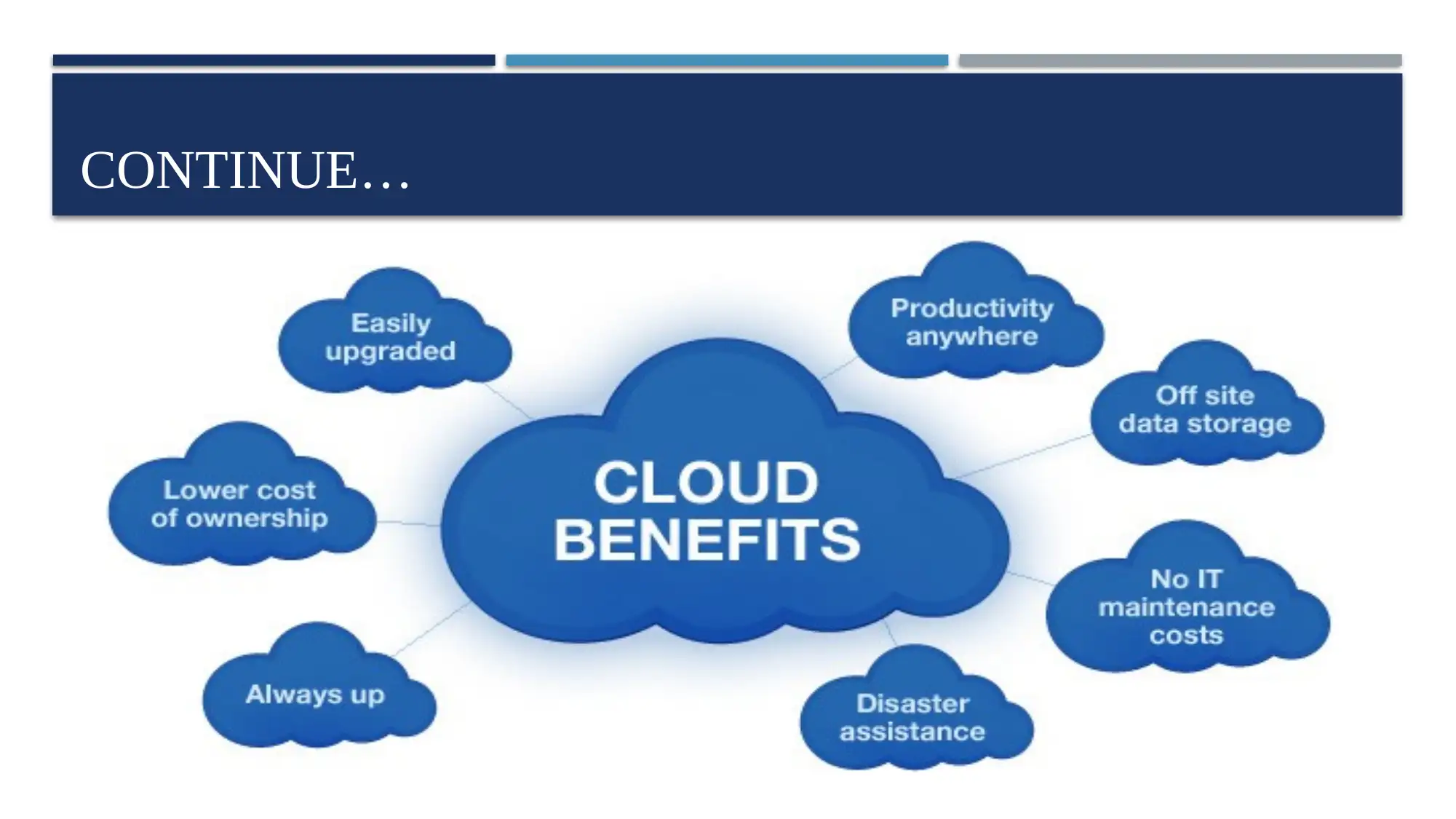
Cloud computing can reduce the overall cost or capital expenses which occur at the
time of purchasing some software and hardware
The cloud computing services are offered by providers to the people as per their
demands and requirements
Cloud computing can help the industry in order to enhance their productivity level
Companies can use cloud computing in order to store their data and maintain the large
amount of information in an effective manner.
Cloud computing can reduce the overall cost or capital expenses which occur at the
time of purchasing some software and hardware
The cloud computing services are offered by providers to the people as per their
demands and requirements
Cloud computing can help the industry in order to enhance their productivity level
Companies can use cloud computing in order to store their data and maintain the large
amount of information in an effective manner.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CONTINUE…
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY INFORMATION
An organization implemented some strategies then it is necessary for them to perform
some practices so that overall data can be prevented and after that unauthorised users
will not be able to access the company’s information.
The term security information is used when an enterprise has to secure their
electronic as well as physical data. This can also be referred as cyber security which
is used to prevent the computers from any theft.
An organization implemented some strategies then it is necessary for them to perform
some practices so that overall data can be prevented and after that unauthorised users
will not be able to access the company’s information.
The term security information is used when an enterprise has to secure their
electronic as well as physical data. This can also be referred as cyber security which
is used to prevent the computers from any theft.

SECURITY PROBLEMS
There are some security problems which are associated with the organization and
their confidentiality level of information
Some list of issues is there like company’s staff members, coding mistakes,
unauthorised machines or devices, servers, local admin, disabled security software’s,
applications and so on.
There are some security problems which are associated with the organization and
their confidentiality level of information
Some list of issues is there like company’s staff members, coding mistakes,
unauthorised machines or devices, servers, local admin, disabled security software’s,
applications and so on.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SOLUTIONS FOR SECURITY PROBLEMS
When some security issues are arising then due to these company’s overall performance
can get affected in negative manner. There are some solutions which are described
below:
A new holistic approach should be adopted by an enterprise so that overall activities
can be managed and by getting some solutions from user’s security issues can be
overcome.
Encryption is a technique which can be used by business organizations in order to
secure their information.
Some small risks which are identified can also be removed like coding mistakes can
be resolved by updating the software’s on continuous basis.
When some security issues are arising then due to these company’s overall performance
can get affected in negative manner. There are some solutions which are described
below:
A new holistic approach should be adopted by an enterprise so that overall activities
can be managed and by getting some solutions from user’s security issues can be
overcome.
Encryption is a technique which can be used by business organizations in order to
secure their information.
Some small risks which are identified can also be removed like coding mistakes can
be resolved by updating the software’s on continuous basis.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CONCLUSION
From the above carried out analysis or findings, it can be interpreted that
technological advancements are the kind of practices which are performed by
companies in order to enhance their security level.
Cloud computing is used by them so that they can secure their data on cloud and due
to which unauthorised access of data can be reduced.
From the above carried out analysis or findings, it can be interpreted that
technological advancements are the kind of practices which are performed by
companies in order to enhance their security level.
Cloud computing is used by them so that they can secure their data on cloud and due
to which unauthorised access of data can be reduced.

REFERENCES
Subashini, S. and Kavitha, V., 2011. A survey on security issues in service delivery
models of cloud computing. Journal of network and computer applications. 34(1).
pp.1-11.
Calheiros, R.N. and et. al., 2011. CloudSim: a toolkit for modeling and simulation of
cloud computing environments and evaluation of resource provisioning algorithms.
Software: Practice and experience. 41(1). pp.23-50.
Beloglazov, A., Abawajy, J. and Buyya, R., 2012. Energy-aware resource allocation
heuristics for efficient management of data centers for cloud computing. Future
generation computer systems. 28(5). pp.755-768.
Subashini, S. and Kavitha, V., 2011. A survey on security issues in service delivery
models of cloud computing. Journal of network and computer applications. 34(1).
pp.1-11.
Calheiros, R.N. and et. al., 2011. CloudSim: a toolkit for modeling and simulation of
cloud computing environments and evaluation of resource provisioning algorithms.
Software: Practice and experience. 41(1). pp.23-50.
Beloglazov, A., Abawajy, J. and Buyya, R., 2012. Energy-aware resource allocation
heuristics for efficient management of data centers for cloud computing. Future
generation computer systems. 28(5). pp.755-768.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




