Firewall Comparison: Packet Filtering vs Application Layer vs Stateful
VerifiedAdded on 2022/08/22
|7
|958
|15
Report
AI Summary
This report provides a detailed comparison of three primary types of firewalls: packet filtering, application-layer, and stateful-inspection firewalls. It explains how each type of firewall operates, highlighting their key differences and functionalities. Packet filtering firewalls monitor incoming and outgoing packets based on IP addresses and ports. Application-layer firewalls control input, output, and access to applications or services by monitoring system service calls. Stateful-inspection firewalls track the operating state and characteristics of network connections to distinguish legitimate packets. The report includes diagrams illustrating each firewall type and concludes with references to support the information presented, offering a comprehensive overview for understanding firewall technologies. Desklib offers a range of similar solved assignments and study resources for students.

Running head: - COMPARISON OF FIREWALLS
COMPARISON OF FIREWALLS
Name of the Student
Name of the University
Author Note
COMPARISON OF FIREWALLS
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPARISON OF FIREWALLS
Table of Contents
1. Comparison of Firewalls:.......................................................................................................2
1.1 Packet filtering firewall:..............................................................................................2
1.2 Application-layer firewall:...............................................................................................3
1.3 Stateful-inspection firewall:.............................................................................................4
2. References:.............................................................................................................................6
Table of Contents
1. Comparison of Firewalls:.......................................................................................................2
1.1 Packet filtering firewall:..............................................................................................2
1.2 Application-layer firewall:...............................................................................................3
1.3 Stateful-inspection firewall:.............................................................................................4
2. References:.............................................................................................................................6

2COMPARISON OF FIREWALLS
1. Comparison of Firewalls:
Within the field of computing, Firewall refers to a system for network security that
specifically monitors as well as controls the traffic present on a network having a complete
dependency upon the security rules that have been previously determined. A firewall
explicitly creates a particular barrier in between the existing internal network along with that
of the external network, which is considered to be untrusted (Wool 2018). Such external
networks might be that of internet from where individual users gather information that might
be taken into their personal systems. Hence, the firewall might have the existence at the entry
node of the network or even within the system of the user.
There is the shared existence of primary three types of firewalls, which are,
i) Packet filtering firewall.
ii) Application-layer firewall.
iii) Stateful-inspection firewall.
1.1 Packet filtering firewall:
This particularly refers to the technique of utilizing the control network access by the
monitoring over the outgoing as well as the incoming packets along with allowing all of them
to pass or place a halt upon the source as well as the destination of the IP addresses, ports and
the protocols.
Network layer firewalls put forward the definition of filtering the rule sets, which
provision with higher efficiency within the mechanisms of security (Voronkov, Martucci and
Lindskog 2020). This particular type of firewall is also termed as static filtering.
1. Comparison of Firewalls:
Within the field of computing, Firewall refers to a system for network security that
specifically monitors as well as controls the traffic present on a network having a complete
dependency upon the security rules that have been previously determined. A firewall
explicitly creates a particular barrier in between the existing internal network along with that
of the external network, which is considered to be untrusted (Wool 2018). Such external
networks might be that of internet from where individual users gather information that might
be taken into their personal systems. Hence, the firewall might have the existence at the entry
node of the network or even within the system of the user.
There is the shared existence of primary three types of firewalls, which are,
i) Packet filtering firewall.
ii) Application-layer firewall.
iii) Stateful-inspection firewall.
1.1 Packet filtering firewall:
This particularly refers to the technique of utilizing the control network access by the
monitoring over the outgoing as well as the incoming packets along with allowing all of them
to pass or place a halt upon the source as well as the destination of the IP addresses, ports and
the protocols.
Network layer firewalls put forward the definition of filtering the rule sets, which
provision with higher efficiency within the mechanisms of security (Voronkov, Martucci and
Lindskog 2020). This particular type of firewall is also termed as static filtering.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3COMPARISON OF FIREWALLS
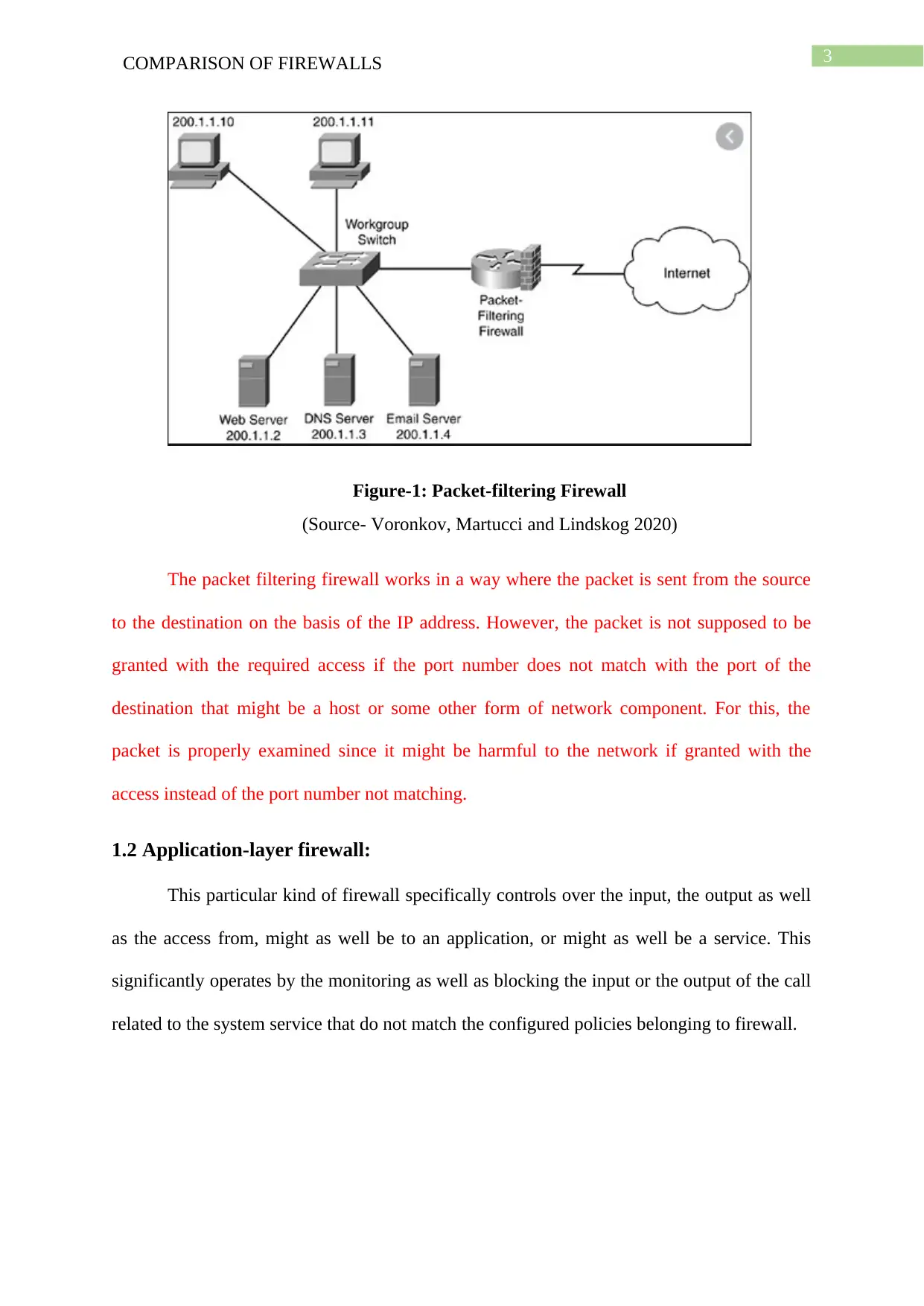
Figure-1: Packet-filtering Firewall
(Source- Voronkov, Martucci and Lindskog 2020)
The packet filtering firewall works in a way where the packet is sent from the source
to the destination on the basis of the IP address. However, the packet is not supposed to be
granted with the required access if the port number does not match with the port of the
destination that might be a host or some other form of network component. For this, the
packet is properly examined since it might be harmful to the network if granted with the
access instead of the port number not matching.
1.2 Application-layer firewall:
This particular kind of firewall specifically controls over the input, the output as well
as the access from, might as well be to an application, or might as well be a service. This
significantly operates by the monitoring as well as blocking the input or the output of the call
related to the system service that do not match the configured policies belonging to firewall.
Figure-1: Packet-filtering Firewall
(Source- Voronkov, Martucci and Lindskog 2020)
The packet filtering firewall works in a way where the packet is sent from the source
to the destination on the basis of the IP address. However, the packet is not supposed to be
granted with the required access if the port number does not match with the port of the
destination that might be a host or some other form of network component. For this, the
packet is properly examined since it might be harmful to the network if granted with the
access instead of the port number not matching.
1.2 Application-layer firewall:
This particular kind of firewall specifically controls over the input, the output as well
as the access from, might as well be to an application, or might as well be a service. This
significantly operates by the monitoring as well as blocking the input or the output of the call
related to the system service that do not match the configured policies belonging to firewall.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPARISON OF FIREWALLS
Figure-2: Application Layer Firewall
(Source- Li et al. 2017)
Hence, it can be stated that this particular type of firewall is established to control
over the traffic that is present within a network present upon any of the OSI layer until the
present application layer (Li et al. 2017). The Application-layer firewall has the control over
the services or the application to prevent unauthorized access into any individual system.
Hence, it can be stated that this particular type of firewall typically examines all the
contents that are present within the packets that need to be granted with the access. The
application layer firewall examines if the packet is maintaining a complete connection state
as well as a proper information regarding the sequence.
1.3 Stateful-inspection firewall:
Within the field of computing, Stateful-inspection firewall belongs to that particular
type of firewall having tracked over the operating state as well as the characteristics of the
network connection through which the traversal takes place (Diekmann et al. 2016). This
particular firewall apart from the above two is configured specifically to distinguish between
Figure-2: Application Layer Firewall
(Source- Li et al. 2017)
Hence, it can be stated that this particular type of firewall is established to control
over the traffic that is present within a network present upon any of the OSI layer until the
present application layer (Li et al. 2017). The Application-layer firewall has the control over
the services or the application to prevent unauthorized access into any individual system.
Hence, it can be stated that this particular type of firewall typically examines all the
contents that are present within the packets that need to be granted with the access. The
application layer firewall examines if the packet is maintaining a complete connection state
as well as a proper information regarding the sequence.
1.3 Stateful-inspection firewall:
Within the field of computing, Stateful-inspection firewall belongs to that particular
type of firewall having tracked over the operating state as well as the characteristics of the
network connection through which the traversal takes place (Diekmann et al. 2016). This
particular firewall apart from the above two is configured specifically to distinguish between
5COMPARISON OF FIREWALLS
the network packets that are legitimate belonging to differently existing types of various
connections in regards to the network.
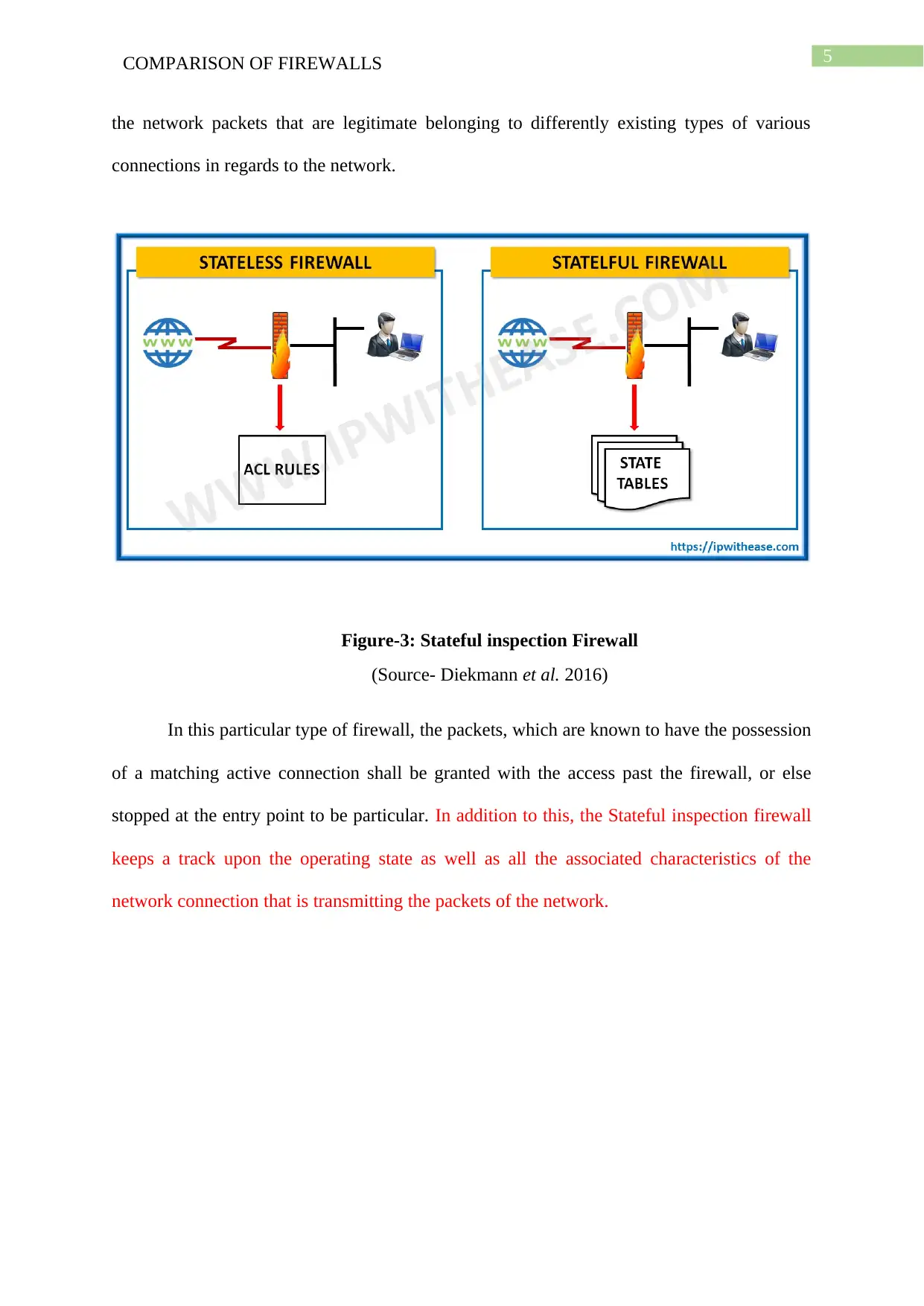
Figure-3: Stateful inspection Firewall
(Source- Diekmann et al. 2016)
In this particular type of firewall, the packets, which are known to have the possession
of a matching active connection shall be granted with the access past the firewall, or else
stopped at the entry point to be particular. In addition to this, the Stateful inspection firewall
keeps a track upon the operating state as well as all the associated characteristics of the
network connection that is transmitting the packets of the network.
the network packets that are legitimate belonging to differently existing types of various
connections in regards to the network.
Figure-3: Stateful inspection Firewall
(Source- Diekmann et al. 2016)
In this particular type of firewall, the packets, which are known to have the possession
of a matching active connection shall be granted with the access past the firewall, or else
stopped at the entry point to be particular. In addition to this, the Stateful inspection firewall
keeps a track upon the operating state as well as all the associated characteristics of the
network connection that is transmitting the packets of the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPARISON OF FIREWALLS
2. References:
Diekmann, C., Michaelis, J., Haslbeck, M. and Carle, G., 2016, May. Verified iptables
firewall analysis. In 2016 IFIP Networking Conference (IFIP Networking) and Workshops
(pp. 252-260). IEEE.
Li, H., Deng, J., Hu, H., Wang, K.C., Ahn, G.J., Zhao, Z. and Han, W., 2017, June. Poster:
On the Safety and Efficiency of Virtual Firewall Elasticity Control. In Proceedings of the
22nd ACM on Symposium on Access Control Models and Technologies (pp. 129-131).
Voronkov, A., Martucci, L.A. and Lindskog, S., 2020. Measuring the usability of firewall
rule sets. IEEE Access, 8, pp.27106-27121.
Wool, A., 2018. Trends in Firewall Configuration Errors.
2. References:
Diekmann, C., Michaelis, J., Haslbeck, M. and Carle, G., 2016, May. Verified iptables
firewall analysis. In 2016 IFIP Networking Conference (IFIP Networking) and Workshops
(pp. 252-260). IEEE.
Li, H., Deng, J., Hu, H., Wang, K.C., Ahn, G.J., Zhao, Z. and Han, W., 2017, June. Poster:
On the Safety and Efficiency of Virtual Firewall Elasticity Control. In Proceedings of the
22nd ACM on Symposium on Access Control Models and Technologies (pp. 129-131).
Voronkov, A., Martucci, L.A. and Lindskog, S., 2020. Measuring the usability of firewall
rule sets. IEEE Access, 8, pp.27106-27121.
Wool, A., 2018. Trends in Firewall Configuration Errors.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




