Computer Architecture Assignment Solution: ICT114, January 2020
VerifiedAdded on 2022/08/10
|9
|1428
|190
Homework Assignment
AI Summary
This document provides a comprehensive solution to a Computer Architecture assignment, specifically the ICT114 Tutor-Marked Assignment from January 2020. The solution addresses several key concepts, including 2's complement representation, binary and hexadecimal conversions, and logical operations. It details calculations for unsigned integers, including NOT (X AND Y) operations, subtraction using 1's complement, and multiplication steps. The document also explores IEEE 754 single-precision floating-point format for decimal number representation. Furthermore, the assignment covers memory organization, including ROM and RAM addressing, non-volatile memory types (flash, floppy, optical disks), and cache memory functionality. The solution also analyzes processor registers, addressing modes, and assembly language instructions, including move, add, and logical shift operations. Finally, it provides a program example to calculate the sum of student marks and explains the purpose of LSR instructions.

Running head: COMPUTER ARCHITECTURE
COMPUTER ARCHITECTURE
Name of the Student
Name of the University
Author Note
COMPUTER ARCHITECTURE
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER ARCHITECTURE
Question 1:
a)
In 2’s complement representation the MSB is the sign bit and the rest bits are used to
represent magnitude of the decimal number. Hence, when the number is 12 bit in 2’s
complement form then 11 bits are used to represent magnitude. Now, in unsigned form n bit
binary number can represent (2^n -1) integers from 1 to (2^n – 1). Thus for 12 bit signed 2’s
complement form 2* (2^11 – 1) numbers can be represented without 0. Hence, total of (2^12
– 1) decimal numbers can be represented in the range [-(2^n-1) to (2^n-1)] by a 12 bit 2’s
complement number.
b) X =15 F 016
Y =019 A16
Given, X and Y are 16 bit unsigned integers.
i) Hence, X = 0001 0101 1111 0000
Y = 0000 0001 1001 1010
ii) Now, NOT(X AND Y) = (XY)’ = X’ + Y’ (By De Morgan’s law)
X’ = (0001 0101 1111 0000)’ = 1110 1010 0000 1111
Y’ = (0000 0001 1001 1010)’ = 1111 1110 0110 0101
Now, X’ + Y’ = 1110 1010 0000 1111
+ 1111 1110 0110 0101
= 0001 1110 1000 0111 0100
Hence, NOT(X AND Y) = ( 0001 11101000 0111 0100 )2 = ( 1 E 874 ) 16
Question 1:
a)
In 2’s complement representation the MSB is the sign bit and the rest bits are used to
represent magnitude of the decimal number. Hence, when the number is 12 bit in 2’s
complement form then 11 bits are used to represent magnitude. Now, in unsigned form n bit
binary number can represent (2^n -1) integers from 1 to (2^n – 1). Thus for 12 bit signed 2’s
complement form 2* (2^11 – 1) numbers can be represented without 0. Hence, total of (2^12
– 1) decimal numbers can be represented in the range [-(2^n-1) to (2^n-1)] by a 12 bit 2’s
complement number.
b) X =15 F 016
Y =019 A16
Given, X and Y are 16 bit unsigned integers.
i) Hence, X = 0001 0101 1111 0000
Y = 0000 0001 1001 1010
ii) Now, NOT(X AND Y) = (XY)’ = X’ + Y’ (By De Morgan’s law)
X’ = (0001 0101 1111 0000)’ = 1110 1010 0000 1111
Y’ = (0000 0001 1001 1010)’ = 1111 1110 0110 0101
Now, X’ + Y’ = 1110 1010 0000 1111
+ 1111 1110 0110 0101
= 0001 1110 1000 0111 0100
Hence, NOT(X AND Y) = ( 0001 11101000 0111 0100 )2 = ( 1 E 874 ) 16

2COMPUTER ARCHITECTURE
iii) In this case X –Y is obtained by 1’s complement method.
First 1’s complement of Y = 1111 1110 0110 0101
Now, Y is added with X with binary addition technique.
0001 0101 1111 0000
+1111 1110 0110 0101
= 1 0001010001010101
Now, as the carry is 1 this carry is removed from the sum and added to the result to get the
result of subtraction.
1010001010101
+ 1
= 1 0100 0101 0110
Thus the result of subtraction in hexadecimal is ( 1456 )16.
The decimal equivalent of the result = 1*16^3 + 4*16^2 + 5*16 + 6*16^0 = 520610
iv) Now, when the computer registers are 16 bits wide then multiplication is performed in
step by step when Y is multiplied by 2 as given below.
1st step:
Y = 1 1001 1010
2 = 10
1 1001 1010*0 = 0 0000 0000
2nd step:
iii) In this case X –Y is obtained by 1’s complement method.
First 1’s complement of Y = 1111 1110 0110 0101
Now, Y is added with X with binary addition technique.
0001 0101 1111 0000
+1111 1110 0110 0101
= 1 0001010001010101
Now, as the carry is 1 this carry is removed from the sum and added to the result to get the
result of subtraction.
1010001010101
+ 1
= 1 0100 0101 0110
Thus the result of subtraction in hexadecimal is ( 1456 )16.
The decimal equivalent of the result = 1*16^3 + 4*16^2 + 5*16 + 6*16^0 = 520610
iv) Now, when the computer registers are 16 bits wide then multiplication is performed in
step by step when Y is multiplied by 2 as given below.
1st step:
Y = 1 1001 1010
2 = 10
1 1001 1010*0 = 0 0000 0000
2nd step:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMPUTER ARCHITECTURE
Y = 1 1001 1010
1 1001 1010*1 = 1 1001 1010
3rd step:
0 0000 0000
+1 1001 1010
= 11 0011 0100
Hence, hexadecimal equivalent of the number is ( 334 )16.
v) Given X in binary form = 1 0101 1111 0000 = 561610
Right shifting for 4 times gives = 1 0101 1111 = 35110
Now, 5616/16 = 351
Hence, righting shifting a number by 4 times is equivalent to dividing the number by 16. This
is because one bit right shifting of binary number reduces it by factor of 2 as the base of
binary is 2. Hence, 4 times right shifting reduces the number by factor 2^4 = 16.
c) Given decimal number = -1.875.
Now, the sign is negative hence the sign bit is 1.
Now, whole number part in binary = 1
Fraction part in binary = 0.111
Hence, the number in binary = 1.1112
Hence, number is 1.111*2^0
Now, exponent = 0 + 127 (as single precision IEEE 754 format is followed).
Y = 1 1001 1010
1 1001 1010*1 = 1 1001 1010
3rd step:
0 0000 0000
+1 1001 1010
= 11 0011 0100
Hence, hexadecimal equivalent of the number is ( 334 )16.
v) Given X in binary form = 1 0101 1111 0000 = 561610
Right shifting for 4 times gives = 1 0101 1111 = 35110
Now, 5616/16 = 351
Hence, righting shifting a number by 4 times is equivalent to dividing the number by 16. This
is because one bit right shifting of binary number reduces it by factor of 2 as the base of
binary is 2. Hence, 4 times right shifting reduces the number by factor 2^4 = 16.
c) Given decimal number = -1.875.
Now, the sign is negative hence the sign bit is 1.
Now, whole number part in binary = 1
Fraction part in binary = 0.111
Hence, the number in binary = 1.1112
Hence, number is 1.111*2^0
Now, exponent = 0 + 127 (as single precision IEEE 754 format is followed).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER ARCHITECTURE
Exponent in binary = 1111111
Now, the number in IEEE 754 32 bit format where 23 bits for mantissa, 8 bits for exponent
and MSB is sign bit is
-1.875 = 1 01111111 11100000000000000000000
Question 2:
a)
i) Given the memory of the ROM is 48 Kbytes and 2 RAMs of 32 Kbytes each. Now,
addressing range after RAM is not used. Hence the total addressing capacity of the computer
system = 48 + 32*2 = 112 Kbytes of which 48 Kbytes is unused.
ii) The memory of the computer system has two parts namely the used memory part
containing addresses from 00000 to 2E000 and unused memory addresses from 2E001 to
2FFFF. The addresses are obtained by decoding method where chip select signals are
generated from address bus of each device in a system.
Memory map:
BLOCK 0
BLOCK 1
BLOCK 2
BLOCK 3
NOT USED
NOT USED
NOT USED
NOT USED
Exponent in binary = 1111111
Now, the number in IEEE 754 32 bit format where 23 bits for mantissa, 8 bits for exponent
and MSB is sign bit is
-1.875 = 1 01111111 11100000000000000000000
Question 2:
a)
i) Given the memory of the ROM is 48 Kbytes and 2 RAMs of 32 Kbytes each. Now,
addressing range after RAM is not used. Hence the total addressing capacity of the computer
system = 48 + 32*2 = 112 Kbytes of which 48 Kbytes is unused.
ii) The memory of the computer system has two parts namely the used memory part
containing addresses from 00000 to 2E000 and unused memory addresses from 2E001 to
2FFFF. The addresses are obtained by decoding method where chip select signals are
generated from address bus of each device in a system.
Memory map:
BLOCK 0
BLOCK 1
BLOCK 2
BLOCK 3
NOT USED
NOT USED
NOT USED
NOT USED

5COMPUTER ARCHITECTURE
b) Non-volatile memories are those memories that can hold data even if the power is turned
off. In non-volatile memory the data is not needed to be periodically refreshed. The three
different types of non-volatile memory are flash memory, floppy disks and optical disks.
Flash memory retains data in absence of power supply and in this particular storage medium
the data can be electrically erased and then reprogrammed. Floppy was used in early
computers and this is also a non-volatile memory in which storage is made of a thin disk and
the magnetic storage medium is flexible. The optical disk is uses optical storage techniques to
read and write data. In this method laser beams are used to store data digitally for reading and
writing.
c) Cache memory is an intermediate storage between the processors and the registers and
Random Access Memory. The cache memory is placed inside the processor and CPU directly
access this. The operation of the cache memory can be described by its functionality. The
cache memory is used by the CPU for storing instructions and the data that is required in
repeated basis for execution of programs and thus the performance or speed of the whole
system is improved significantly. The cache memory feeds the CPU with data which is
frequently used and thus CPU does not need to access RAM for fetch same data over and
over again.
Question 3:
a) Given the address is of 16 bits from 0 to 15. Hence, the 16 bit processor can address 2^16
= 65536 memory locations.
b)
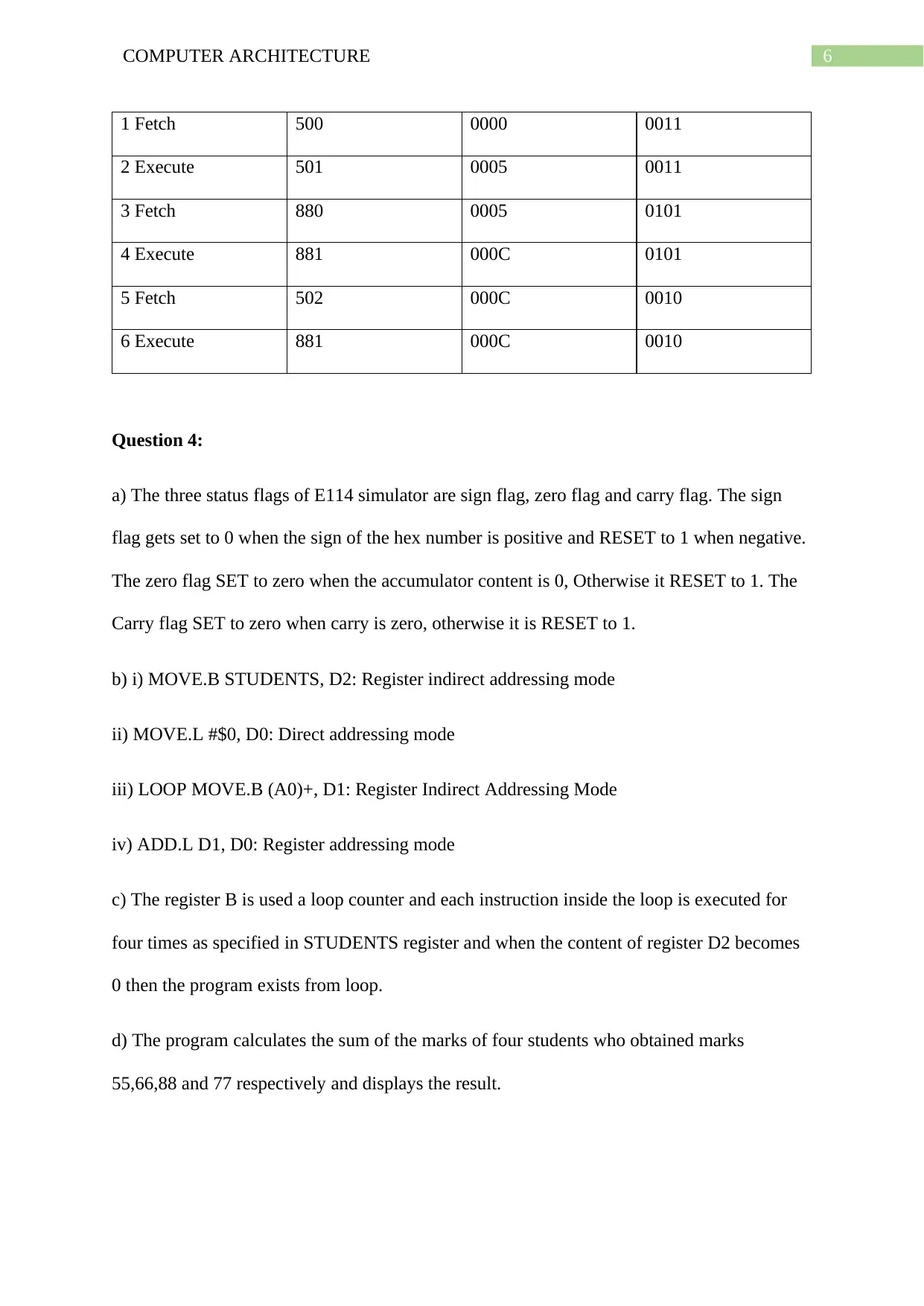
The contents of each registers PC, AC and IR while executing six steps is given below.
Step PC at start of cycle AC at end of cycle IR at end of cycle
b) Non-volatile memories are those memories that can hold data even if the power is turned
off. In non-volatile memory the data is not needed to be periodically refreshed. The three
different types of non-volatile memory are flash memory, floppy disks and optical disks.
Flash memory retains data in absence of power supply and in this particular storage medium
the data can be electrically erased and then reprogrammed. Floppy was used in early
computers and this is also a non-volatile memory in which storage is made of a thin disk and
the magnetic storage medium is flexible. The optical disk is uses optical storage techniques to
read and write data. In this method laser beams are used to store data digitally for reading and
writing.
c) Cache memory is an intermediate storage between the processors and the registers and
Random Access Memory. The cache memory is placed inside the processor and CPU directly
access this. The operation of the cache memory can be described by its functionality. The
cache memory is used by the CPU for storing instructions and the data that is required in
repeated basis for execution of programs and thus the performance or speed of the whole
system is improved significantly. The cache memory feeds the CPU with data which is
frequently used and thus CPU does not need to access RAM for fetch same data over and
over again.
Question 3:
a) Given the address is of 16 bits from 0 to 15. Hence, the 16 bit processor can address 2^16
= 65536 memory locations.
b)
The contents of each registers PC, AC and IR while executing six steps is given below.
Step PC at start of cycle AC at end of cycle IR at end of cycle
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6COMPUTER ARCHITECTURE
1 Fetch 500 0000 0011
2 Execute 501 0005 0011
3 Fetch 880 0005 0101
4 Execute 881 000C 0101
5 Fetch 502 000C 0010
6 Execute 881 000C 0010
Question 4:
a) The three status flags of E114 simulator are sign flag, zero flag and carry flag. The sign
flag gets set to 0 when the sign of the hex number is positive and RESET to 1 when negative.
The zero flag SET to zero when the accumulator content is 0, Otherwise it RESET to 1. The
Carry flag SET to zero when carry is zero, otherwise it is RESET to 1.
b) i) MOVE.B STUDENTS, D2: Register indirect addressing mode
ii) MOVE.L #$0, D0: Direct addressing mode
iii) LOOP MOVE.B (A0)+, D1: Register Indirect Addressing Mode
iv) ADD.L D1, D0: Register addressing mode
c) The register B is used a loop counter and each instruction inside the loop is executed for
four times as specified in STUDENTS register and when the content of register D2 becomes
0 then the program exists from loop.
d) The program calculates the sum of the marks of four students who obtained marks
55,66,88 and 77 respectively and displays the result.
1 Fetch 500 0000 0011
2 Execute 501 0005 0011
3 Fetch 880 0005 0101
4 Execute 881 000C 0101
5 Fetch 502 000C 0010
6 Execute 881 000C 0010
Question 4:
a) The three status flags of E114 simulator are sign flag, zero flag and carry flag. The sign
flag gets set to 0 when the sign of the hex number is positive and RESET to 1 when negative.
The zero flag SET to zero when the accumulator content is 0, Otherwise it RESET to 1. The
Carry flag SET to zero when carry is zero, otherwise it is RESET to 1.
b) i) MOVE.B STUDENTS, D2: Register indirect addressing mode
ii) MOVE.L #$0, D0: Direct addressing mode
iii) LOOP MOVE.B (A0)+, D1: Register Indirect Addressing Mode
iv) ADD.L D1, D0: Register addressing mode
c) The register B is used a loop counter and each instruction inside the loop is executed for
four times as specified in STUDENTS register and when the content of register D2 becomes
0 then the program exists from loop.
d) The program calculates the sum of the marks of four students who obtained marks
55,66,88 and 77 respectively and displays the result.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COMPUTER ARCHITECTURE
e) The LSR instruction is used to set the content of D0. By logical shifting of the content of
D0 the trailing two zeroes of D0 content is removed so that less memory is consumed in the
program.
f)
Program to add two numbers:
ORG $3000
START MOVE.B $2000,D1
MOVE.B $2001,D0
ADD.L D1,D0
MOVE.B D0, $2002
END START
e) The LSR instruction is used to set the content of D0. By logical shifting of the content of
D0 the trailing two zeroes of D0 content is removed so that less memory is consumed in the
program.
f)
Program to add two numbers:
ORG $3000
START MOVE.B $2000,D1
MOVE.B $2001,D0
ADD.L D1,D0
MOVE.B D0, $2002
END START

8COMPUTER ARCHITECTURE
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





