Computer Forensics: Investigation, Resources, and Tools
Added on 2023-06-03
57 Pages7403 Words287 Views
computer forensics
Table of Contents
1. Introduction..............................................................................................................................2
2. Resources of Investigation.......................................................................................................2
3. Progress of Investigation........................................................................................................20
3.1 Issue 1 – Presenting content related to offence..................................................................20
3.2 Issue 2 – Identification of Ownership.................................................................................41
3.3 Issue 3 – Intention of the offence.......................................................................................43
3.4 Issue 4 – Quantity of files in the evidence..........................................................................43
3.5 Issue 5 – Software installed................................................................................................44
4. Conclusion..............................................................................................................................44
5. References..............................................................................................................................45
Appendix – a..................................................................................................................................50
Appendix –b...................................................................................................................................54
Page 1 of 57
1. Introduction..............................................................................................................................2
2. Resources of Investigation.......................................................................................................2
3. Progress of Investigation........................................................................................................20
3.1 Issue 1 – Presenting content related to offence..................................................................20
3.2 Issue 2 – Identification of Ownership.................................................................................41
3.3 Issue 3 – Intention of the offence.......................................................................................43
3.4 Issue 4 – Quantity of files in the evidence..........................................................................43
3.5 Issue 5 – Software installed................................................................................................44
4. Conclusion..............................................................................................................................44
5. References..............................................................................................................................45
Appendix – a..................................................................................................................................50
Appendix –b...................................................................................................................................54
Page 1 of 57

1. Introduction
The digital forensic which is used for the various purposes such as recovering the data,
investigating the data from the digital devices. The most widely recognized is to help or
invalidate a theory under the steady gaze of criminal or common courts. Criminal cases include
the supposed infringing upon of laws that are characterized by enactment and that are upheld by
the cops and arraigned by the state, for example, this feature is included in things like theft and
strike against the individual persons (Carracedo, 2007). Common cases then again manage
securing the rights and property of people and however may likewise be worried about legally
binding question between business substances where a type of computerized crime scene
investigation alluded to as electronic disclosure might be included (Cohen, 2012). These are the
different uses and procedures of the digital forensics and using this we can able to avoid these
issues. In this case study, the forensic image of the hard drive will be investigated (Goos,
Alberink & Ruifrok, 2006). The investigation will be completed with the help of tools which are
used in computer forensics. The intention, owner of the content, software will be investigated
and found.
2. Resources of Investigation
The investigation needs the following resources. They are victim or suspect, the system
from where the illegal content is accessed, forensic image of the system hard drive and the
forensic tools. The forensic tools are explained in below (Mahmood, Talabani & Baban, 2015).
FTK imager
FTK Imager is a tool and it is mainly used for evidence (acquiring the data). It is an
imaging tool and also used for preview the data. There are different features of FTK imager tool
and this tool will do the following things like creating the forensic images, preview the files as
well as folders, content previewing, exporting purposes, recovering the deleted files, creates file
hashes and generating the hash reports (Norell et al., 2014). FTK imager will also create the
copies of the original data without any changes for creating the original evidence ("13.
Fachtagung — FTK — Fertigungstechnologie Kleben Klebtechnik trifft automobilen
Page 2 of 57
The digital forensic which is used for the various purposes such as recovering the data,
investigating the data from the digital devices. The most widely recognized is to help or
invalidate a theory under the steady gaze of criminal or common courts. Criminal cases include
the supposed infringing upon of laws that are characterized by enactment and that are upheld by
the cops and arraigned by the state, for example, this feature is included in things like theft and
strike against the individual persons (Carracedo, 2007). Common cases then again manage
securing the rights and property of people and however may likewise be worried about legally
binding question between business substances where a type of computerized crime scene
investigation alluded to as electronic disclosure might be included (Cohen, 2012). These are the
different uses and procedures of the digital forensics and using this we can able to avoid these
issues. In this case study, the forensic image of the hard drive will be investigated (Goos,
Alberink & Ruifrok, 2006). The investigation will be completed with the help of tools which are
used in computer forensics. The intention, owner of the content, software will be investigated
and found.
2. Resources of Investigation
The investigation needs the following resources. They are victim or suspect, the system
from where the illegal content is accessed, forensic image of the system hard drive and the
forensic tools. The forensic tools are explained in below (Mahmood, Talabani & Baban, 2015).
FTK imager
FTK Imager is a tool and it is mainly used for evidence (acquiring the data). It is an
imaging tool and also used for preview the data. There are different features of FTK imager tool
and this tool will do the following things like creating the forensic images, preview the files as
well as folders, content previewing, exporting purposes, recovering the deleted files, creates file
hashes and generating the hash reports (Norell et al., 2014). FTK imager will also create the
copies of the original data without any changes for creating the original evidence ("13.
Fachtagung — FTK — Fertigungstechnologie Kleben Klebtechnik trifft automobilen
Page 2 of 57

Leichtbau", 2013). A forensic toolkit is a software which mainly used for scanning the drives for
finding the contents in the various locations of the hard disk (Novozámský & Šorel, 2018). For
example, this tool will look for various information such as deleted emails, images, audios,
videos as well as any other file formats. This process is done in the FTK imager by saving an
image file in the hard disk and then scanning the drive using the image file and then recycle the
data in the drive (Saini & Kaur, 2016).
The features of FTK imaging tool are:
Forensic image creation
The FTK imaging tool will create forensic images in local disks such as
compact disks, and other USB devices (Cain, Brazelton & Dye, 2016).
Previewing folders and files
This FTK imaging tool can able to view the contents in the files as well as
folders.
Exporting
This tool is export the forensic images from the files and folders.
Create file hashes
FTK imaging tool will create the file hashes using the hash functions and
this is done by means of MD5 and SHA algorithms. Where MD is
message digest and SHA is the short form of the secure hash algorithm
(Yammen & Muneesawang, 2013).
There are different steps are there in the FTK Imager. They are Adding the evidence item and in
this step, we can able to add our own evidence using this "Add evidence item" option and we can
select our own image file by browsing the image from our files or folders. But the selected file
must be a virtual drive image ("Algorithm Based security System for Banknotes", 2018). Once
the file is selected then it open in the FTK imager tool and the evidence of the file is also created.
Autopsy
It is a software which is a forensics oriented tool kit and also an open source digital
forensics software which has many features in terms of effectiveness, performance, and
efficiency (Hamilton, 2015). This tool very fast in hard drive investigation and investigate the
Page 3 of 57
finding the contents in the various locations of the hard disk (Novozámský & Šorel, 2018). For
example, this tool will look for various information such as deleted emails, images, audios,
videos as well as any other file formats. This process is done in the FTK imager by saving an
image file in the hard disk and then scanning the drive using the image file and then recycle the
data in the drive (Saini & Kaur, 2016).
The features of FTK imaging tool are:
Forensic image creation
The FTK imaging tool will create forensic images in local disks such as
compact disks, and other USB devices (Cain, Brazelton & Dye, 2016).
Previewing folders and files
This FTK imaging tool can able to view the contents in the files as well as
folders.
Exporting
This tool is export the forensic images from the files and folders.
Create file hashes
FTK imaging tool will create the file hashes using the hash functions and
this is done by means of MD5 and SHA algorithms. Where MD is
message digest and SHA is the short form of the secure hash algorithm
(Yammen & Muneesawang, 2013).
There are different steps are there in the FTK Imager. They are Adding the evidence item and in
this step, we can able to add our own evidence using this "Add evidence item" option and we can
select our own image file by browsing the image from our files or folders. But the selected file
must be a virtual drive image ("Algorithm Based security System for Banknotes", 2018). Once
the file is selected then it open in the FTK imager tool and the evidence of the file is also created.
Autopsy
It is a software which is a forensics oriented tool kit and also an open source digital
forensics software which has many features in terms of effectiveness, performance, and
efficiency (Hamilton, 2015). This tool very fast in hard drive investigation and investigate the
Page 3 of 57

different problems and gives solution to those problems according to the user needs (Su,
Bouridane & Crookes, 2006). It is a GUI which displays the results according to the search made
by the user (Nasirahmadi, Hensel, Edwards & Sturm, 2016). Autopsy finds and analyze the
different kind of files such as file allocation table (FAT), archives such as zip files and JAR files
etc. this tools is used in the sleuth kit and this tool is also used for analyzing the forensic data in
the mobile devices as well as the computers. This tool is mainly used in these devices to find and
analyze the devices completely to check whether is there any kind of files are present in the
drives or not (Šafář, 2009).
Autopsy tool is considered as the game changer in the digital forensic software tools. It
creates new milestones in the digital forensic pieces of evidence analyzing the process. The most
important thing this software is completely free (IB, 2017). Even though the developers of this
software developed this software tool by adding as many features as possible. Unlike other
software tools this software tool not created for the commercial purposes. The main motto of this
tool is to provide the high quality digital forensic environment to the investigators as relatively
lower price than other software tools. Even though this software consists of the high level
platform integrity than some other commercial software tools. This software runs all the major
operating systems commonly used (MJ, 2016). It also supports all type of file formats for
analyzing. Normally the analyzing the drive take hours but this tool has the powerful search
engine. It can capable of analyzing the same thing within some minutes (B.Arun &
S.K.Prashanth, 2012). Because this tool analyze the files by finding the keywords identified from
the drive. This tool uses the multiple ingest modules for effectively use the multicores. This
process increases the speed of analysis to the unbelievable range (Morgan et al., 2017). This tool
has the most effective system which avoids the analysis of unallocated space to reduce the
analysis time to the considerable amount. The ingest modules provides the results when it found.
So that the researcher doesn’t need to wait for completion of the entire examination process.
Most of the activities involved in the process of analysis are automated in this software tool. So
that the researcher no need to concentrate on silly things during the examination process
(Teixeira J, 2017). Because of the automation process the accuracy of the results are also too
high than the traditional process. It is highly beneficial for the investigators. Even we can use this
software tool for the recovery process also. This software can effectively recover the deleted files
from the system (Thali et al., 2003).
Page 4 of 57
Bouridane & Crookes, 2006). It is a GUI which displays the results according to the search made
by the user (Nasirahmadi, Hensel, Edwards & Sturm, 2016). Autopsy finds and analyze the
different kind of files such as file allocation table (FAT), archives such as zip files and JAR files
etc. this tools is used in the sleuth kit and this tool is also used for analyzing the forensic data in
the mobile devices as well as the computers. This tool is mainly used in these devices to find and
analyze the devices completely to check whether is there any kind of files are present in the
drives or not (Šafář, 2009).
Autopsy tool is considered as the game changer in the digital forensic software tools. It
creates new milestones in the digital forensic pieces of evidence analyzing the process. The most
important thing this software is completely free (IB, 2017). Even though the developers of this
software developed this software tool by adding as many features as possible. Unlike other
software tools this software tool not created for the commercial purposes. The main motto of this
tool is to provide the high quality digital forensic environment to the investigators as relatively
lower price than other software tools. Even though this software consists of the high level
platform integrity than some other commercial software tools. This software runs all the major
operating systems commonly used (MJ, 2016). It also supports all type of file formats for
analyzing. Normally the analyzing the drive take hours but this tool has the powerful search
engine. It can capable of analyzing the same thing within some minutes (B.Arun &
S.K.Prashanth, 2012). Because this tool analyze the files by finding the keywords identified from
the drive. This tool uses the multiple ingest modules for effectively use the multicores. This
process increases the speed of analysis to the unbelievable range (Morgan et al., 2017). This tool
has the most effective system which avoids the analysis of unallocated space to reduce the
analysis time to the considerable amount. The ingest modules provides the results when it found.
So that the researcher doesn’t need to wait for completion of the entire examination process.
Most of the activities involved in the process of analysis are automated in this software tool. So
that the researcher no need to concentrate on silly things during the examination process
(Teixeira J, 2017). Because of the automation process the accuracy of the results are also too
high than the traditional process. It is highly beneficial for the investigators. Even we can use this
software tool for the recovery process also. This software can effectively recover the deleted files
from the system (Thali et al., 2003).
Page 4 of 57

Features of Autopsy
There are different kinds of features are there in the autopsy tool. They are Unicode string
extraction, email analysis, registry analysis, keyword search, file type detection, media playback,
robust file system analysis, timeline analysis etc. using this different features the evidence is
easily identified and analyzed in the autopsy tool ("Fusion Algorithm Based Security System
with Multiple Sensors", 2017). This tool also analyzes the different input formats. The different
input formats analysis in the autopsy tool are disk image analysis, local drive analysis, and local
folder or file analysis etc. (Geradts & Bijhold, 2002).
Apart from the general feature, the autopsy tool has other features such as reporting. In
this reporting feature, the different report and those investigations were created and this
information is retrieved by the investigator after the configuration ("Multi Security System
Based On Honeypot Using Kerberos Algorithm", 2018).
OS forensics
OSForensics is a tool which allows us to identifying the different sort of files. The main
theme of this OSForensics is to find and identify whether any suspicious files are there in drive.
It also identifies the different activities such as hash matching, binary data finding and other
analysis in emails and other memory locations (Jáuregui-Lobera & Bola�os R�os, 2011). The
latest version of the OSForensics is version and this version there are different features and when
compared with the previous versions this version has a lot of features like the analysis is very
faster and the analysis is done in various platforms. The various platforms are disk imaging,
database files, operating systems, work benches etc. (Qi & Li, 2014)
The different features of OSForensics are finding the files in a short period of time, email
archive search is also possible, easy to recover the deleted images as well as other files, password
recovery is also possible, discovering the files even in the hidden areas, collecting the system
information, uncovering the recent activities etc. these are the different features of the
OSForensics. Among these features, the main feature of the OSForensics, discovering the
forensic evidence in a short period of time is the main feature (Raja, 2018).
Page 5 of 57
There are different kinds of features are there in the autopsy tool. They are Unicode string
extraction, email analysis, registry analysis, keyword search, file type detection, media playback,
robust file system analysis, timeline analysis etc. using this different features the evidence is
easily identified and analyzed in the autopsy tool ("Fusion Algorithm Based Security System
with Multiple Sensors", 2017). This tool also analyzes the different input formats. The different
input formats analysis in the autopsy tool are disk image analysis, local drive analysis, and local
folder or file analysis etc. (Geradts & Bijhold, 2002).
Apart from the general feature, the autopsy tool has other features such as reporting. In
this reporting feature, the different report and those investigations were created and this
information is retrieved by the investigator after the configuration ("Multi Security System
Based On Honeypot Using Kerberos Algorithm", 2018).
OS forensics
OSForensics is a tool which allows us to identifying the different sort of files. The main
theme of this OSForensics is to find and identify whether any suspicious files are there in drive.
It also identifies the different activities such as hash matching, binary data finding and other
analysis in emails and other memory locations (Jáuregui-Lobera & Bola�os R�os, 2011). The
latest version of the OSForensics is version and this version there are different features and when
compared with the previous versions this version has a lot of features like the analysis is very
faster and the analysis is done in various platforms. The various platforms are disk imaging,
database files, operating systems, work benches etc. (Qi & Li, 2014)
The different features of OSForensics are finding the files in a short period of time, email
archive search is also possible, easy to recover the deleted images as well as other files, password
recovery is also possible, discovering the files even in the hidden areas, collecting the system
information, uncovering the recent activities etc. these are the different features of the
OSForensics. Among these features, the main feature of the OSForensics, discovering the
forensic evidence in a short period of time is the main feature (Raja, 2018).
Page 5 of 57

Features of OSForensics
Same as FTK imaging tool and autopsy there are the variety of features are there in the
OSForensics. The different features of the OSForensics include memory viewer and dumper,
hash set management, drive imaging, registry viewer, file name searching, mismatched file
search, detecting the recent activities, restoring the deleted files, file encrypting features etc. (S &
D, 2017)
Hash set management
After the creation for the collection of hash tables for storing purpose then the hash set
management is possible in the OSForensics (Zafar, 2000).
Restoring the deleted files
It is the important feature and using this feature the restoring operations are easy and this
feature mainly used in the OSForensics to recover the deleted file (Malakiene & Gogelis, 2007).
File encrypting features
This OS forensics has uses different encrypting algorithms and hence the security
features in this tool are very high. Message digest algorithm and secured hash algorithm are the
different algorithms which are used in the OSForensics (Verolme & Mieremet, 2017).
File name searching
It is the main feature in the OSForensics tool and using this tool the easy searching is
possible. The File name searching is the feature and using this search the different file formats
were identified. The different file formats include the image, audio, video etc.
Installation of autopsy
Autopsy installation process stars with the process of downloading the autopsy software
from their site. They provide this tool for zero cost. From their site any one can able to download
this tool. Here the latest autopsy tool is downloaded. After that we need to open the file
destination. Then we need to click the autopsy setup file. By this activity the user can able to see
Page 6 of 57
Same as FTK imaging tool and autopsy there are the variety of features are there in the
OSForensics. The different features of the OSForensics include memory viewer and dumper,
hash set management, drive imaging, registry viewer, file name searching, mismatched file
search, detecting the recent activities, restoring the deleted files, file encrypting features etc. (S &
D, 2017)
Hash set management
After the creation for the collection of hash tables for storing purpose then the hash set
management is possible in the OSForensics (Zafar, 2000).
Restoring the deleted files
It is the important feature and using this feature the restoring operations are easy and this
feature mainly used in the OSForensics to recover the deleted file (Malakiene & Gogelis, 2007).
File encrypting features
This OS forensics has uses different encrypting algorithms and hence the security
features in this tool are very high. Message digest algorithm and secured hash algorithm are the
different algorithms which are used in the OSForensics (Verolme & Mieremet, 2017).
File name searching
It is the main feature in the OSForensics tool and using this tool the easy searching is
possible. The File name searching is the feature and using this search the different file formats
were identified. The different file formats include the image, audio, video etc.
Installation of autopsy
Autopsy installation process stars with the process of downloading the autopsy software
from their site. They provide this tool for zero cost. From their site any one can able to download
this tool. Here the latest autopsy tool is downloaded. After that we need to open the file
destination. Then we need to click the autopsy setup file. By this activity the user can able to see
Page 6 of 57

the run as administrator option. This option need to be pressed (Wen & Yu, 2003). Then the
installation wizard for installing the Autopsy software will open. The user can able to install this
software by simply following the installation wizard. First the user required to select the
appropriate installation location for this software. After selecting the installation location the user
needs to click on the install button ("A Review of: “Computer Evidence: Collection &
Preservation. By C. L. T. Brown”", 2006). Then we can able to the installation progress wizard.
It shows the installation progress details. This process takes some time to complete. After that
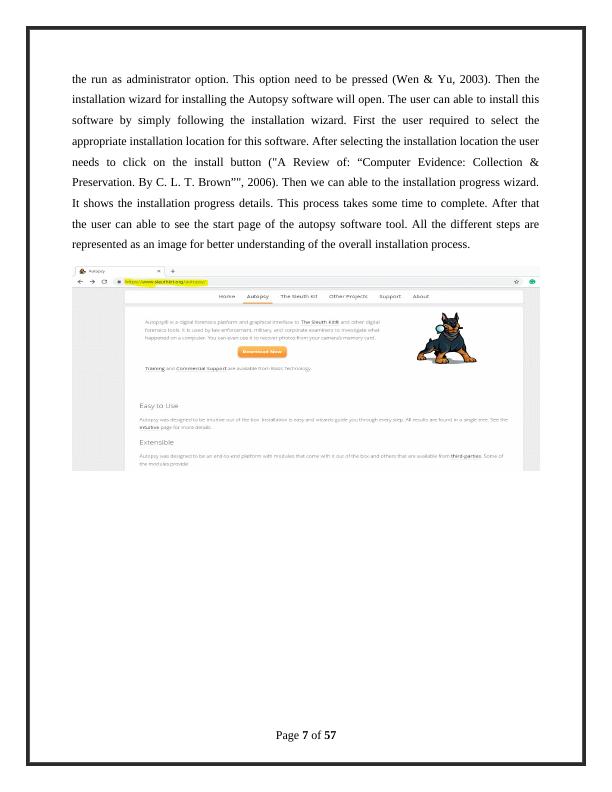
the user can able to see the start page of the autopsy software tool. All the different steps are
represented as an image for better understanding of the overall installation process.
Page 7 of 57
installation wizard for installing the Autopsy software will open. The user can able to install this
software by simply following the installation wizard. First the user required to select the
appropriate installation location for this software. After selecting the installation location the user
needs to click on the install button ("A Review of: “Computer Evidence: Collection &
Preservation. By C. L. T. Brown”", 2006). Then we can able to the installation progress wizard.
It shows the installation progress details. This process takes some time to complete. After that
the user can able to see the start page of the autopsy software tool. All the different steps are
represented as an image for better understanding of the overall installation process.
Page 7 of 57
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Computer Forensics: Strategies and Resources for Investigationlg...
|47
|5976
|157
Computer Forensics Investigation on Clown Content Offence in Western Australialg...
|47
|6608
|329
MN624 Digital Forensics - Assignmentlg...
|19
|1225
|41
Demonstration of Autopsylg...
|22
|1475
|22
Digital Forensics Tool FTK Imagerlg...
|7
|1395
|29
Computer Forensics: Tools and Techniques for Digital Investigationlg...
|68
|6481
|239
