Computer Information System and FISMA Compliance Report Analysis
VerifiedAdded on 2021/05/31
|6
|1056
|52
Report
AI Summary
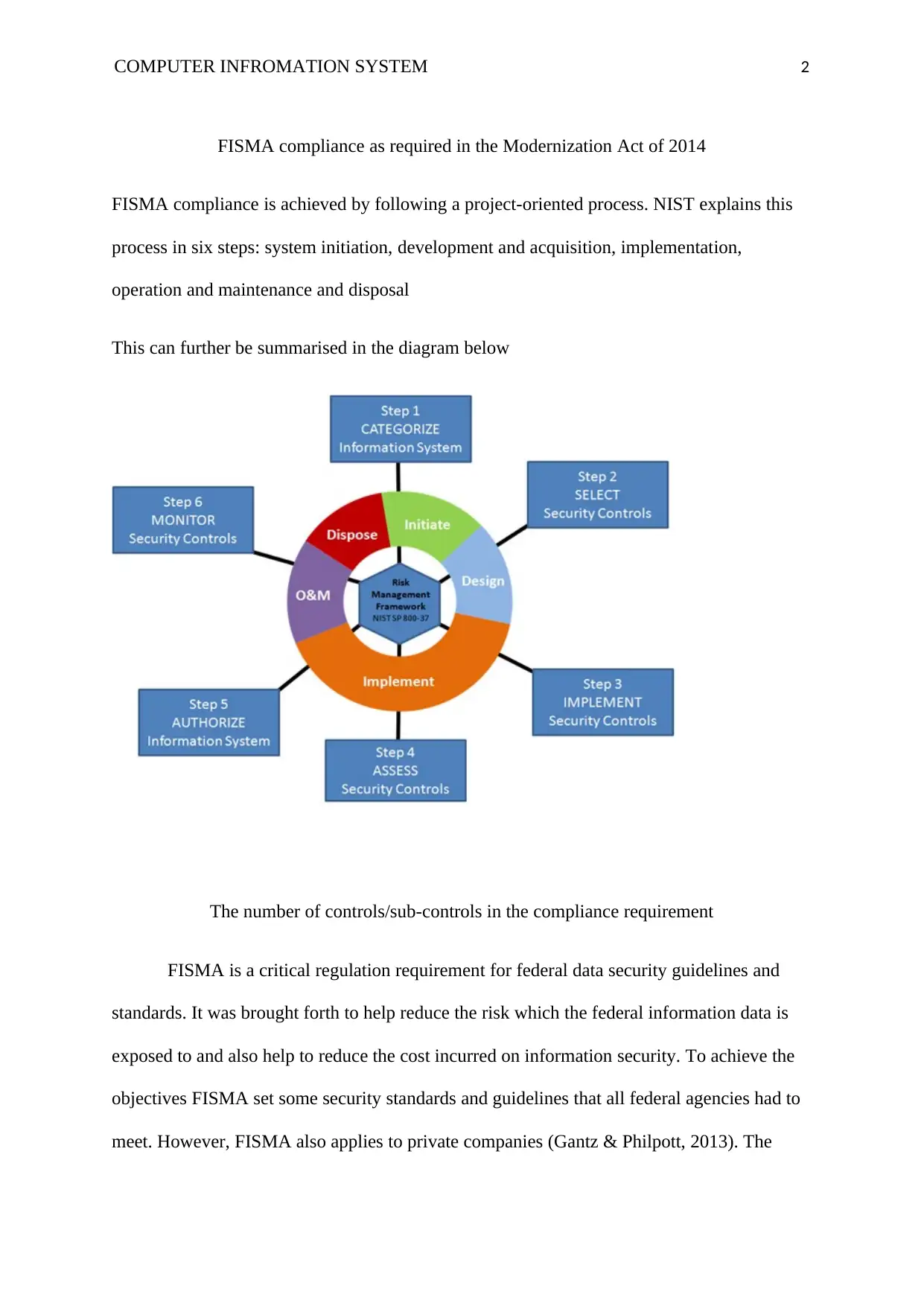
This report delves into the critical aspects of FISMA (Federal Information Security Modernization Act) compliance, a crucial regulation for federal data security. It outlines the project-oriented process for achieving FISMA compliance, as defined by NIST, encompassing system initiation, development, implementation, operation, and disposal. The report highlights the role of NIST in establishing security standards and guidelines, including publications like FIPS 200, NIST 800, and FIPS 199, with a focus on NIST SP 800-53, which provides a catalog of security controls. It explores the Risk Management Framework as a complementary approach and details the four phases of the certification and accreditation process: planning and initiation, certification, accreditation, and continuous monitoring. The report also discusses how organizations are migrating to NIST 800-53 and adapting their Risk Management Framework based on SP 800-37, which includes steps like assessing, selecting, implementing, and authorizing security controls. This analysis provides a comprehensive understanding of FISMA compliance and its practical application in securing federal information systems.
1 out of 6












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)