A Comprehensive Report on Computer Network Footprinting Investigation
VerifiedAdded on 2023/01/11
|20
|1358
|67
Report
AI Summary
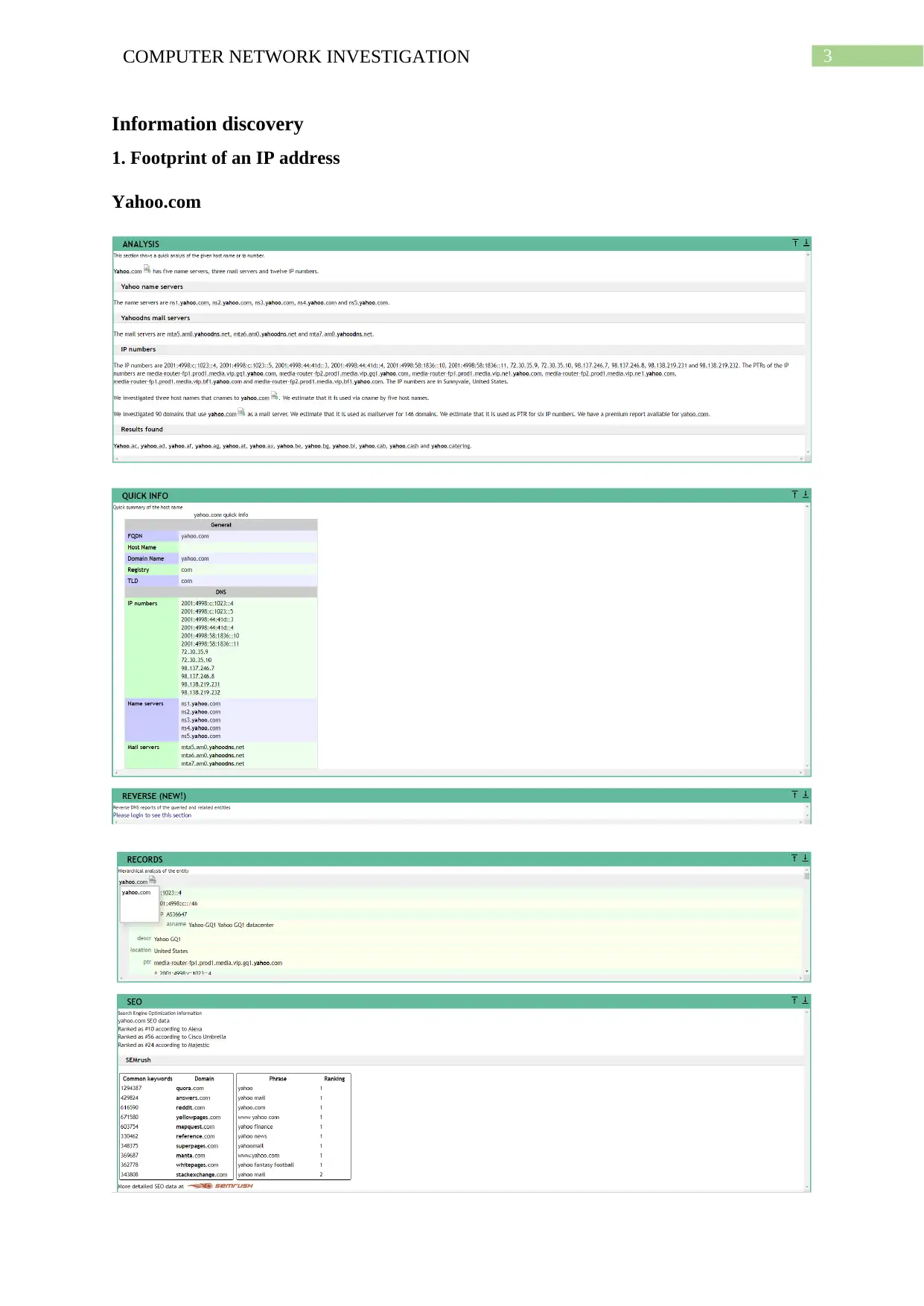
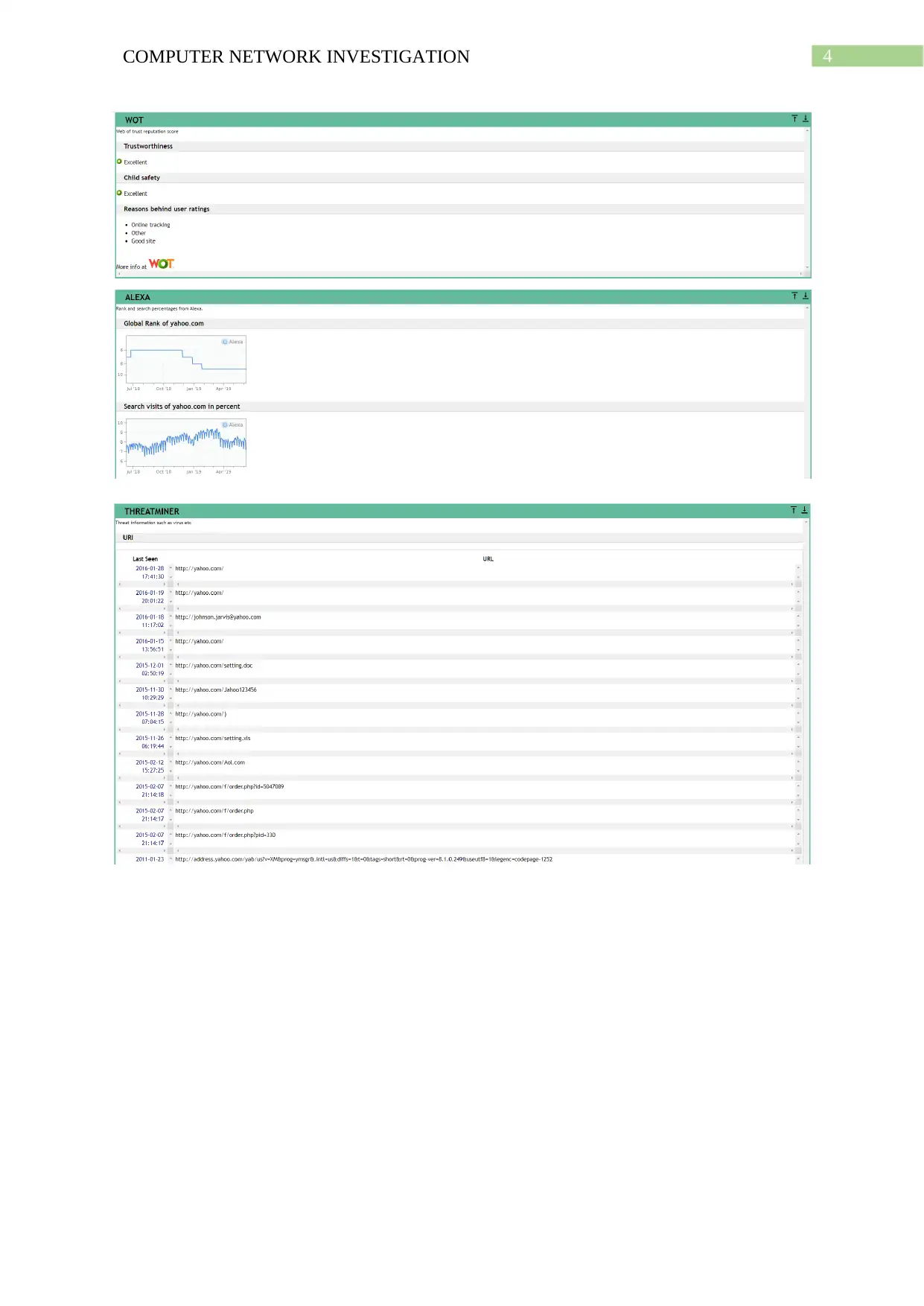
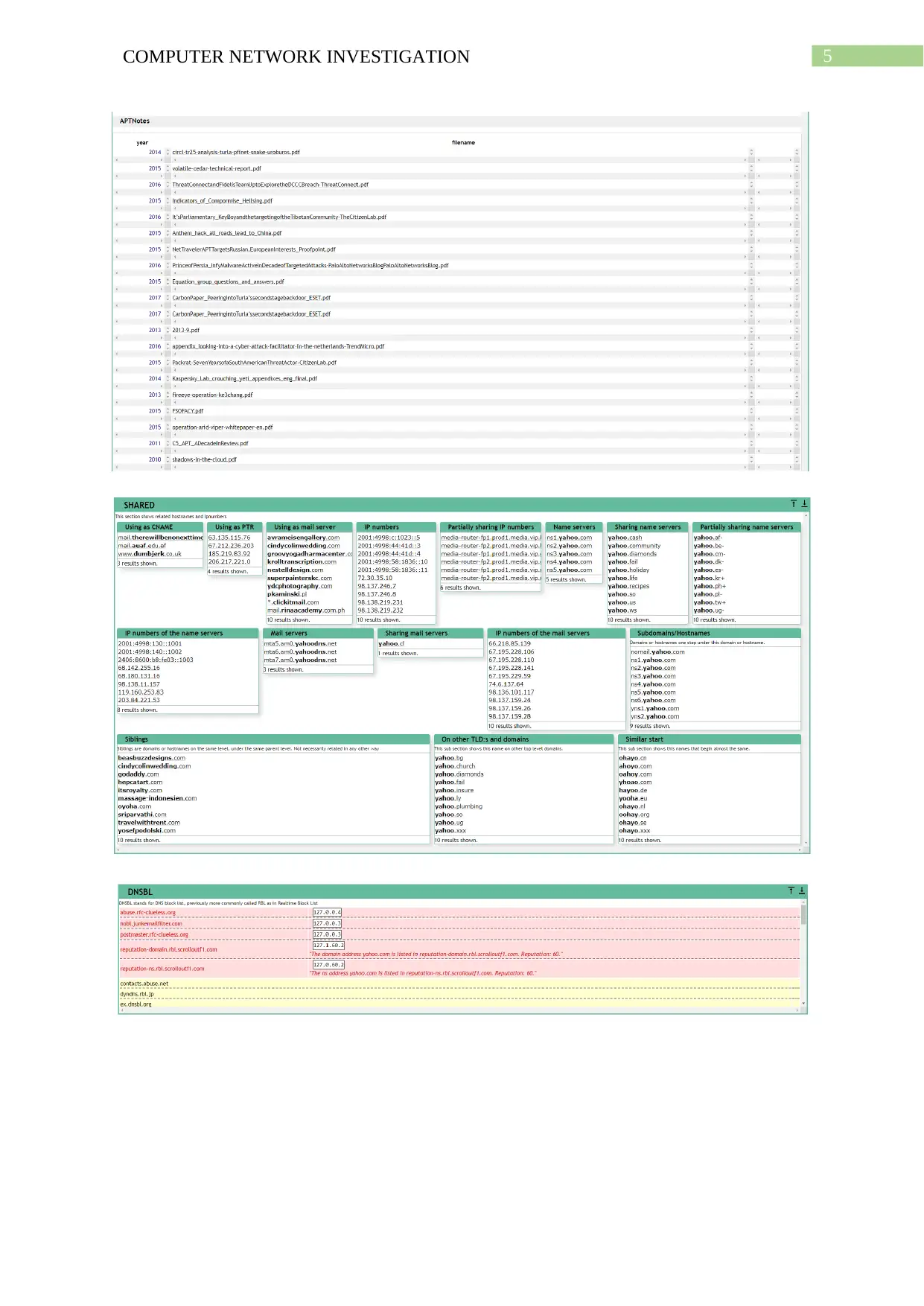
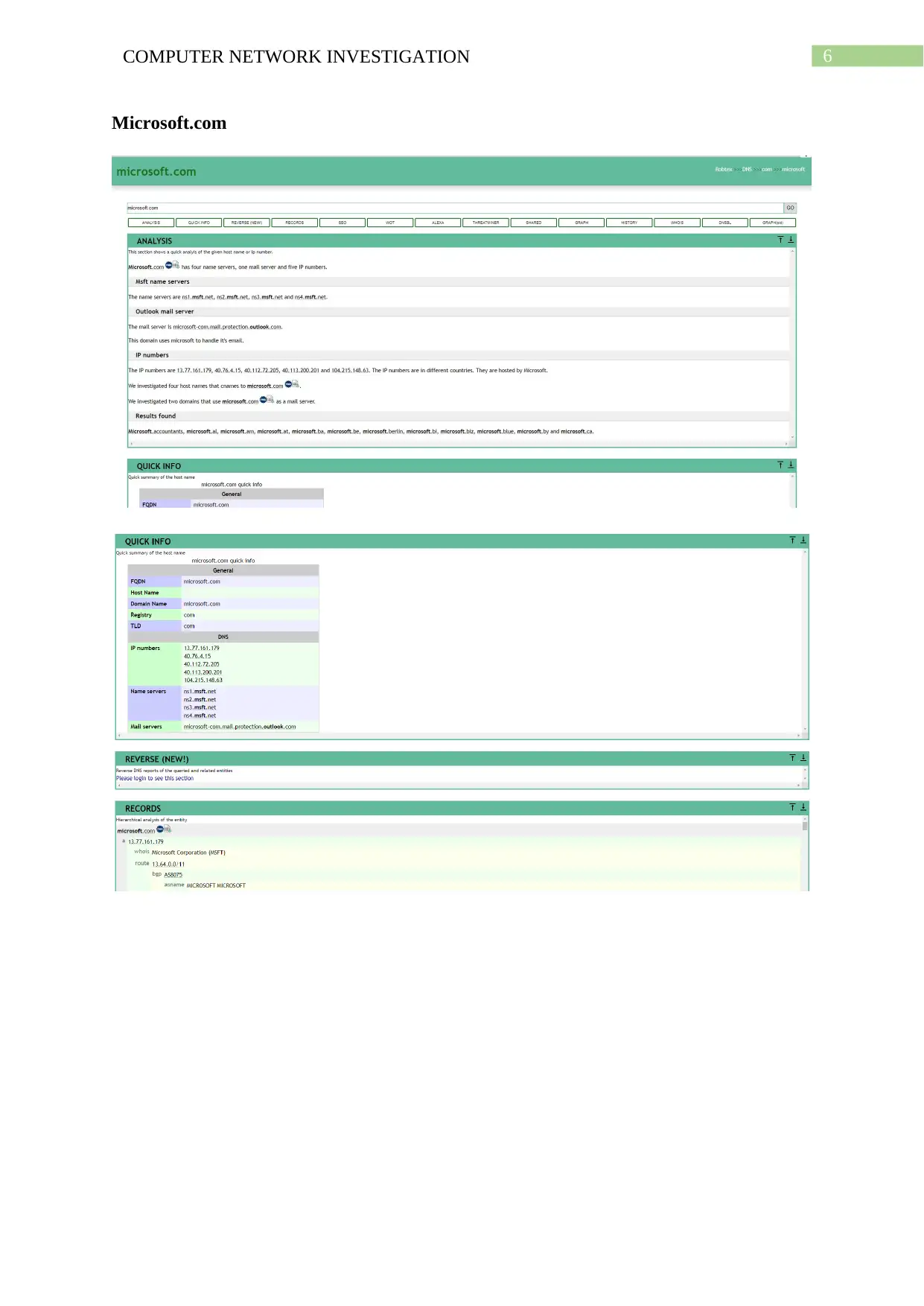
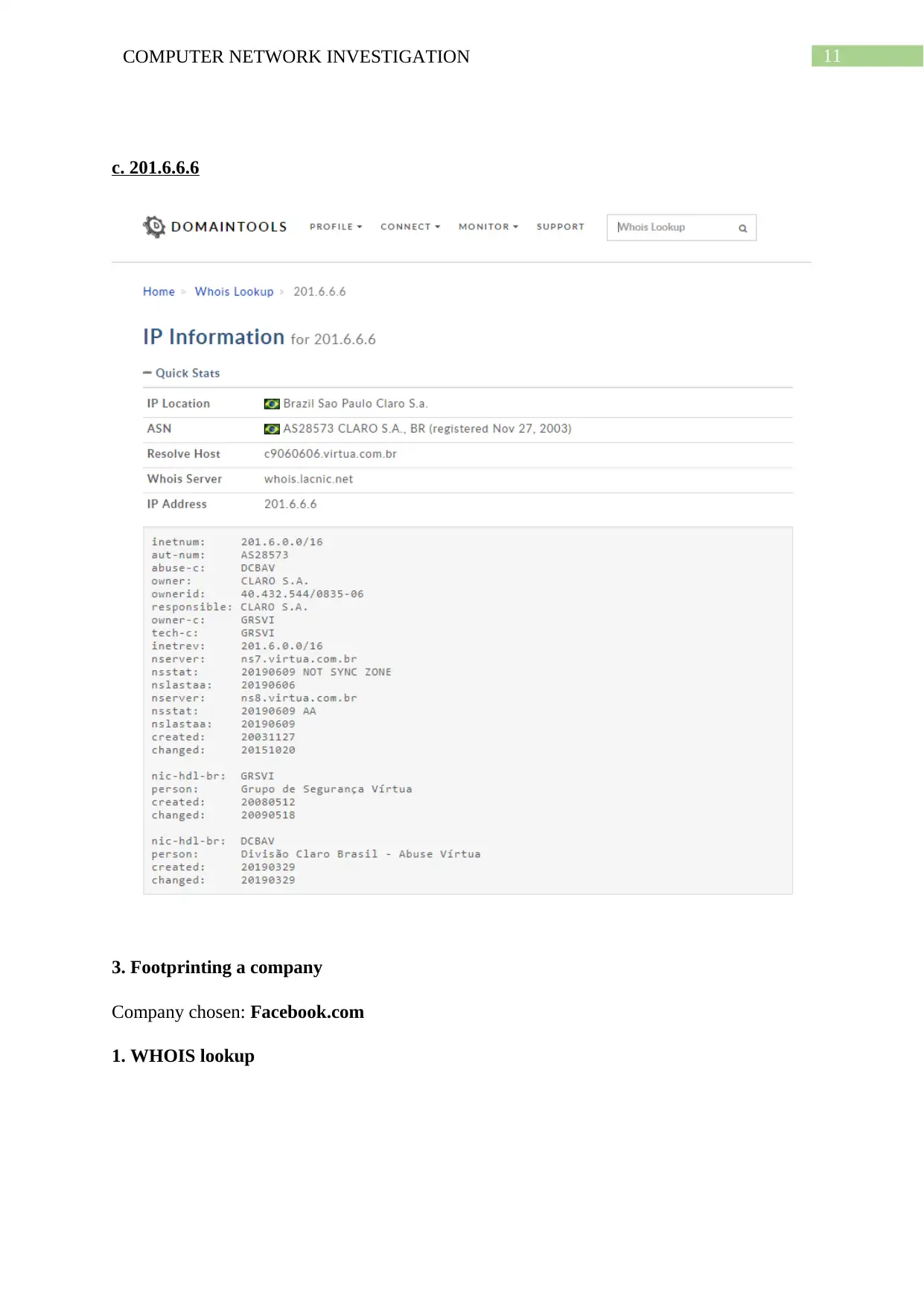
This report comprehensively investigates computer network footprinting, a crucial process in ethical hacking and cybersecurity. It begins with an introduction to footprinting, its uses, and the importance of information gathering. The report delves into the role of ICANN in managing internet resources and its relationship with Regional Internet Registries (RIRs) and Internet Service Providers (ISPs). It practically demonstrates footprinting techniques using WHOIS lookup, network vulnerability scans, subdomain searches, and Google dorking to gather information about a target system. The report analyzes the pros and cons of public network information and explores additional footprinting sources like search engines, social engineering, and social networking sites. It also discusses the Robtex IP blacklisting service. The conclusion summarizes the findings and emphasizes the significance of understanding footprinting for both attackers and defenders, providing insights into how this knowledge can be used for penetration testing and cybersecurity.
1 out of 20




![[object Object]](/_next/static/media/star-bottom.7253800d.svg)