Design and Implementation of Chatting Application over Cellular System
VerifiedAdded on 2023/01/19
|16
|2887
|22
Report
AI Summary
This report details the design and implementation of a chatting application with video streaming capabilities over a cellular system. It proposes a three-tier architecture enhanced with an edge layer for improved efficiency, utilizing encryption for secure data transmission. The cellular system is modified to optimize video streaming performance, employing network and proxy nodes for communication. The report covers system design, including cellular system and novel system architectures, along with software flowcharts. It also describes the implementation approach, focusing on SAN tunneling and distributed network services, and includes prototype implementation details. Performance verification, using Apache server tests, demonstrates the system's efficiency. The report concludes with a summary of the findings and references relevant literature.

Running head: COMPUTER NETWORKING ASSIGNMENT
Computer Networking Assignment
Video Streaming and Chatting Application over Cellular System
Name of the System
Name of the University
Author’s note:
Computer Networking Assignment
Video Streaming and Chatting Application over Cellular System
Name of the System
Name of the University
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER NETWORKING ASSIGNMENT
Executive Summary
The report reflects the design and implementation approach of an application that has chat and
video streaming option and communicate over a cellular system. The novel system architecture
shows that proposed application uses a three tier architecture. An additional layer which is
connected to the front end is edge layer that makes the processes efficient. The application use
the encryption method to secure the data. The cellular system has been modified to provide best
service for video streaming. The cellular system communicate through the network node and
proxy node.
Executive Summary
The report reflects the design and implementation approach of an application that has chat and
video streaming option and communicate over a cellular system. The novel system architecture
shows that proposed application uses a three tier architecture. An additional layer which is
connected to the front end is edge layer that makes the processes efficient. The application use
the encryption method to secure the data. The cellular system has been modified to provide best
service for video streaming. The cellular system communicate through the network node and
proxy node.

2COMPUTER NETWORKING ASSIGNMENT
Table of Contents
Introduction:....................................................................................................................................3
Background:.....................................................................................................................................3
System Design:................................................................................................................................4
Implementation:...............................................................................................................................8
Performance Verification:.............................................................................................................11
Conclusion:....................................................................................................................................13
Bibliography:.................................................................................................................................14
Table of Contents
Introduction:....................................................................................................................................3
Background:.....................................................................................................................................3
System Design:................................................................................................................................4
Implementation:...............................................................................................................................8
Performance Verification:.............................................................................................................11
Conclusion:....................................................................................................................................13
Bibliography:.................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMPUTER NETWORKING ASSIGNMENT
Introduction:
The three tier data center model is well known for its front-end, mid-tier and back-end
application approach. The front end is used for messaging, web and many other services to the
user. The mid-tier is used for managing the transaction processes and the back-end is used for
handing the database services (Okay & Ozdemir, 2016). The edge services tier has been used in
the proposed novel system architecture model for providing rich functions. The edge services
work in the cellular system environment for providing services like security, load balancing,
caching and various others.
The report includes the description of the proposed messaging system. This report
particularly describes a novel system architecture for a high-performance and scalable service
tier. It also provides an overview of the system design through Novel System Architecture and
software flowchart. The approach to the system implementation is provided to describe the
cellular system overview. Performance verification is also included within the report.
Background:
The system proposed in the report is a chatting application that has video streaming
option. The report does not concentrate on the platform in which the system will be
implemented. The system will have chatting option between the members. This application will
allow the users to create group so that more than one member can chat simultaneously with more
than one member. The system has the feature of video streaming. The proposed system only
accepts registered users to chat with other members. The system uses the phone number of the
user to register. Once registered, the same number can be verified from different devices to
access account. The system has inbuilt video streaming option.
Introduction:
The three tier data center model is well known for its front-end, mid-tier and back-end
application approach. The front end is used for messaging, web and many other services to the
user. The mid-tier is used for managing the transaction processes and the back-end is used for
handing the database services (Okay & Ozdemir, 2016). The edge services tier has been used in
the proposed novel system architecture model for providing rich functions. The edge services
work in the cellular system environment for providing services like security, load balancing,
caching and various others.
The report includes the description of the proposed messaging system. This report
particularly describes a novel system architecture for a high-performance and scalable service
tier. It also provides an overview of the system design through Novel System Architecture and
software flowchart. The approach to the system implementation is provided to describe the
cellular system overview. Performance verification is also included within the report.
Background:
The system proposed in the report is a chatting application that has video streaming
option. The report does not concentrate on the platform in which the system will be
implemented. The system will have chatting option between the members. This application will
allow the users to create group so that more than one member can chat simultaneously with more
than one member. The system has the feature of video streaming. The proposed system only
accepts registered users to chat with other members. The system uses the phone number of the
user to register. Once registered, the same number can be verified from different devices to
access account. The system has inbuilt video streaming option.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER NETWORKING ASSIGNMENT
The system uses the n-tier architecture to provide services to the members. The front-end
layer provides the interface to the member through which the user can send message, make video
streaming and access account. The user-side service is implemented in the front-end layer. This
layer is developed based on the Operating System platform of the device. The mid-tier layer has
the server-side scripts which process the member request and provide the service to the
customer. This layer is also connected to the third party services like data backup/recovery,
disaster management and many more. The mid-layer also responsible for determining the
business login. The third layer is the back-end layer which has the database. This database stores
data of messages, member, login and logout details, video streaming details and many more.
The system will use the technologies like System Area Network or SAN, programmable
network processors, Virtual Interface Architecture and standard high-density servers. The
cellular system will be implemented using the above mentioned technologies (Kenawell et al.,
2016). One important thing about the application that it will support one device per user at a
time. This means that system architecture will not allow information flow from two different
devices for a single member. As the network edge is driven by the requirements of more
available, efficient and scalable web services, large quantity of front-end servers will be used in
the content and load distribution for constructing fron-end servers.
System Design:
Cellular System Architecture: The proposed system architecture is included with various
functional nodes or elements. These nodes are interconnected with the VI architecture enabled
System Area Network fabric. These nodes can be enumerated for enabling the development of
proposed system along with different levels of scaling, functionality and scaling. The System
Area Network for the proposed system offers the fabric of interconnection regarding entire
The system uses the n-tier architecture to provide services to the members. The front-end
layer provides the interface to the member through which the user can send message, make video
streaming and access account. The user-side service is implemented in the front-end layer. This
layer is developed based on the Operating System platform of the device. The mid-tier layer has
the server-side scripts which process the member request and provide the service to the
customer. This layer is also connected to the third party services like data backup/recovery,
disaster management and many more. The mid-layer also responsible for determining the
business login. The third layer is the back-end layer which has the database. This database stores
data of messages, member, login and logout details, video streaming details and many more.
The system will use the technologies like System Area Network or SAN, programmable
network processors, Virtual Interface Architecture and standard high-density servers. The
cellular system will be implemented using the above mentioned technologies (Kenawell et al.,
2016). One important thing about the application that it will support one device per user at a
time. This means that system architecture will not allow information flow from two different
devices for a single member. As the network edge is driven by the requirements of more
available, efficient and scalable web services, large quantity of front-end servers will be used in
the content and load distribution for constructing fron-end servers.
System Design:
Cellular System Architecture: The proposed system architecture is included with various
functional nodes or elements. These nodes are interconnected with the VI architecture enabled
System Area Network fabric. These nodes can be enumerated for enabling the development of
proposed system along with different levels of scaling, functionality and scaling. The System
Area Network for the proposed system offers the fabric of interconnection regarding entire
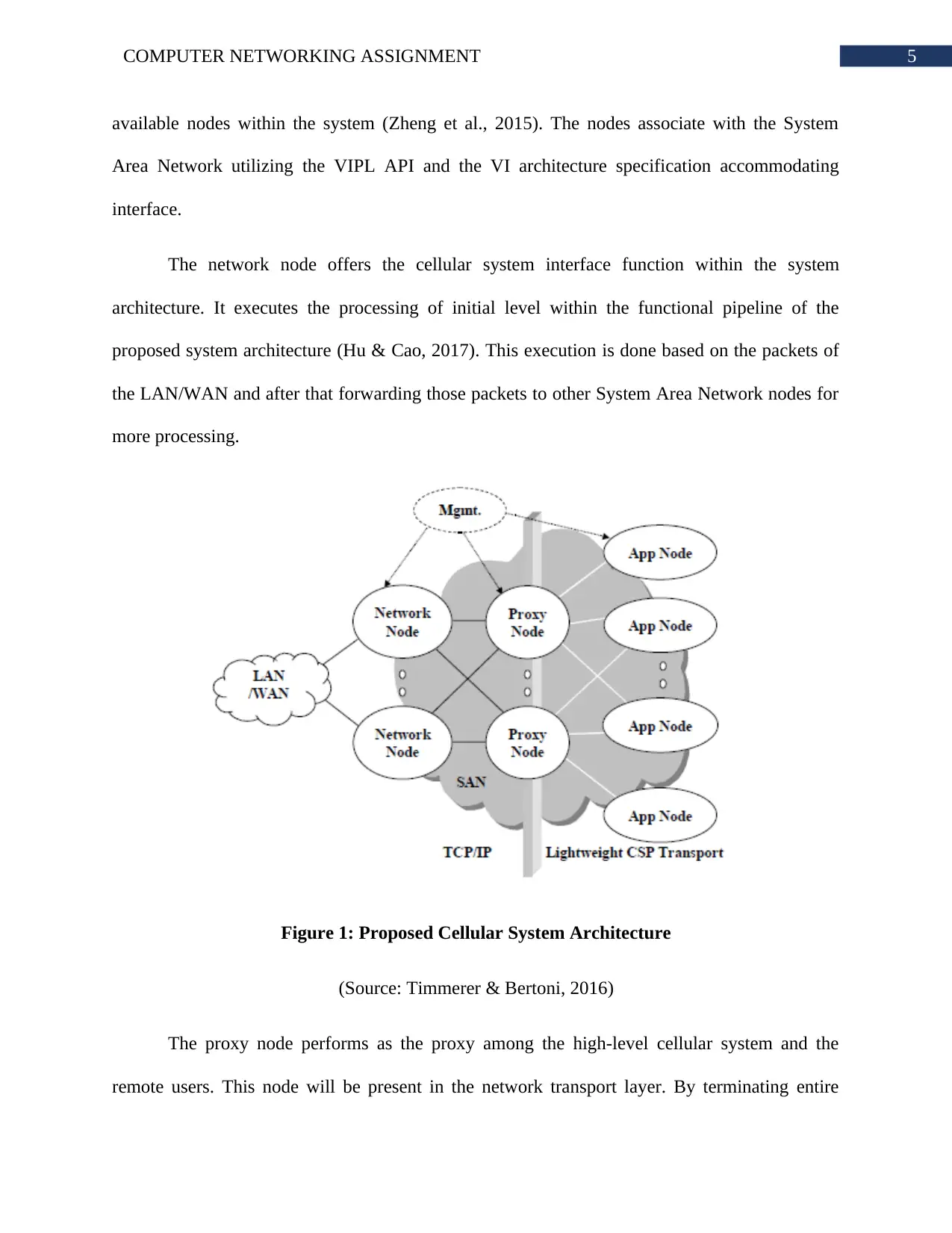
5COMPUTER NETWORKING ASSIGNMENT
available nodes within the system (Zheng et al., 2015). The nodes associate with the System
Area Network utilizing the VIPL API and the VI architecture specification accommodating
interface.
The network node offers the cellular system interface function within the system
architecture. It executes the processing of initial level within the functional pipeline of the
proposed system architecture (Hu & Cao, 2017). This execution is done based on the packets of
the LAN/WAN and after that forwarding those packets to other System Area Network nodes for
more processing.
Figure 1: Proposed Cellular System Architecture
(Source: Timmerer & Bertoni, 2016)
The proxy node performs as the proxy among the high-level cellular system and the
remote users. This node will be present in the network transport layer. By terminating entire
available nodes within the system (Zheng et al., 2015). The nodes associate with the System
Area Network utilizing the VIPL API and the VI architecture specification accommodating
interface.
The network node offers the cellular system interface function within the system
architecture. It executes the processing of initial level within the functional pipeline of the
proposed system architecture (Hu & Cao, 2017). This execution is done based on the packets of
the LAN/WAN and after that forwarding those packets to other System Area Network nodes for
more processing.
Figure 1: Proposed Cellular System Architecture
(Source: Timmerer & Bertoni, 2016)
The proxy node performs as the proxy among the high-level cellular system and the
remote users. This node will be present in the network transport layer. By terminating entire
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPUTER NETWORKING ASSIGNMENT
client TCP sessions, the proxy nodes performs the next level of processing. In order to turn on
the independent packet scaling and processing of application, the network transport layer de-
coupling is used (Shang et al., 2016). HTTP proxy service is a type of example, that the future
web based version of the proposed system can use.
Application Node is responsible for hosting the well-known applications. Taken as an
example, directory service, mail services and web services. High-density standardized server
hardware is used for building the application node. This node will be used in the SAN network.
System Architecture: The system will have a UI for the member. This UI will be in the
top level of the n-tier system architecture. The server side scripting will be done in the second
layer of the architecture. The receiver and sender application will have same configuration. The
system will be consisted of encoding and decoding technology. The encryption technology will
be used at the middle layer of the architecture. This will ensure that data transmission is secure
and no one other than receiver can read the actual message. The video streaming will be using
the same encryption method.
Each message transmitted from the send end to the receiver end will be stored in a
database. This database will be in the third layer of the architecture. The database will store the
message, receiver, sender, date, status and many more data. The major advantage of the proposed
architecture is that it can allow the system to provide service in real time. The real time data flow
will allow the system to show if the user is typing or not. The user will not need to refresh the
page or screen to see the updated content.
client TCP sessions, the proxy nodes performs the next level of processing. In order to turn on
the independent packet scaling and processing of application, the network transport layer de-
coupling is used (Shang et al., 2016). HTTP proxy service is a type of example, that the future
web based version of the proposed system can use.
Application Node is responsible for hosting the well-known applications. Taken as an
example, directory service, mail services and web services. High-density standardized server
hardware is used for building the application node. This node will be used in the SAN network.
System Architecture: The system will have a UI for the member. This UI will be in the
top level of the n-tier system architecture. The server side scripting will be done in the second
layer of the architecture. The receiver and sender application will have same configuration. The
system will be consisted of encoding and decoding technology. The encryption technology will
be used at the middle layer of the architecture. This will ensure that data transmission is secure
and no one other than receiver can read the actual message. The video streaming will be using
the same encryption method.
Each message transmitted from the send end to the receiver end will be stored in a
database. This database will be in the third layer of the architecture. The database will store the
message, receiver, sender, date, status and many more data. The major advantage of the proposed
architecture is that it can allow the system to provide service in real time. The real time data flow
will allow the system to show if the user is typing or not. The user will not need to refresh the
page or screen to see the updated content.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
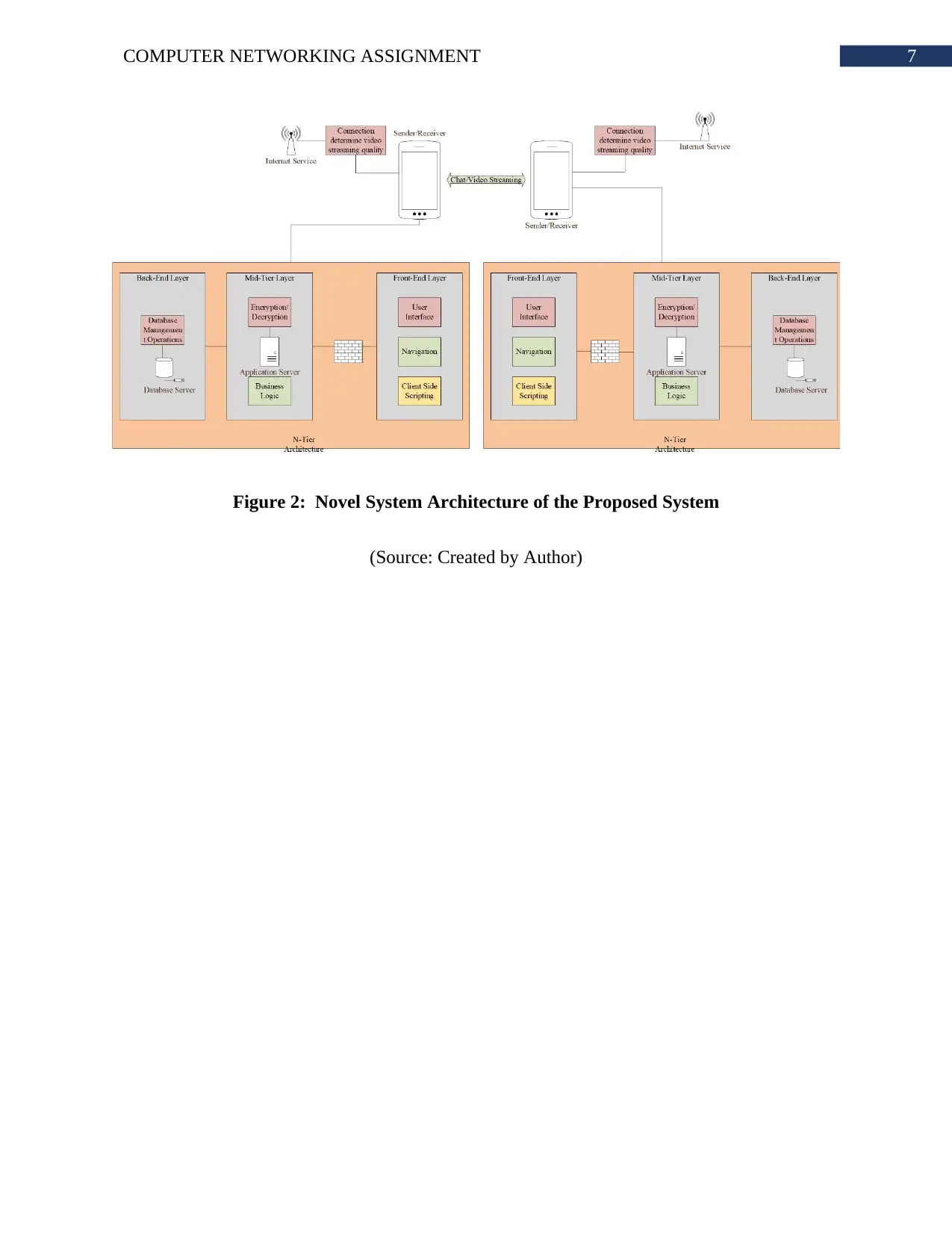
7COMPUTER NETWORKING ASSIGNMENT
Figure 2: Novel System Architecture of the Proposed System
(Source: Created by Author)
Figure 2: Novel System Architecture of the Proposed System
(Source: Created by Author)
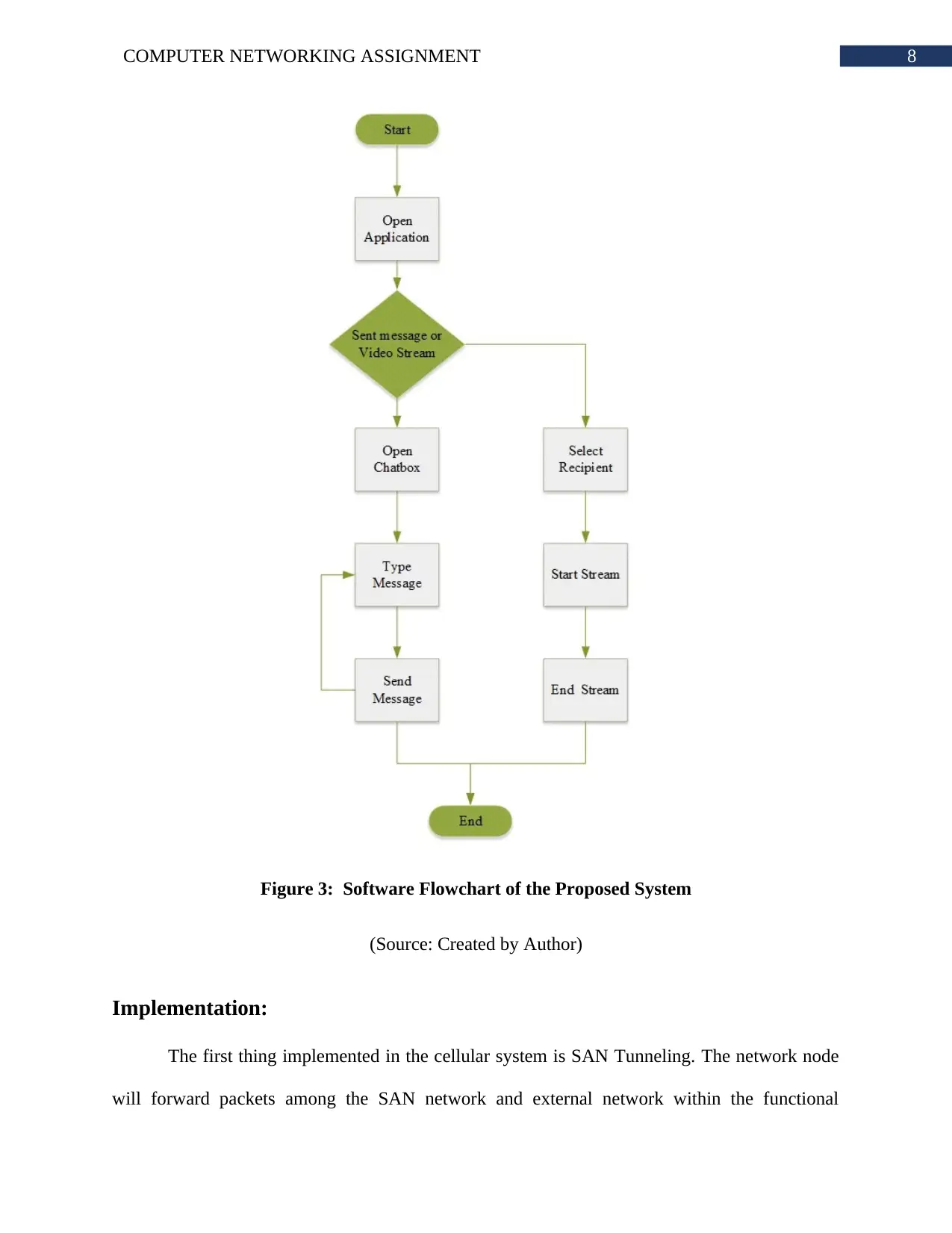
8COMPUTER NETWORKING ASSIGNMENT
Figure 3: Software Flowchart of the Proposed System
(Source: Created by Author)
Implementation:
The first thing implemented in the cellular system is SAN Tunneling. The network node
will forward packets among the SAN network and external network within the functional
Figure 3: Software Flowchart of the Proposed System
(Source: Created by Author)
Implementation:
The first thing implemented in the cellular system is SAN Tunneling. The network node
will forward packets among the SAN network and external network within the functional
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMPUTER NETWORKING ASSIGNMENT
pipeline. A SAN tunnel (VI) based IPC mechanism will be established so that proxy nodes and
network nodes can communicate properly. In order to achieve this mechanism, the network
packet encapsulation is done in the System Area Network packet header information. This
mechanism is highly recommended to implement as it will allow processing of TCP/IP packets
by the proxy nodes at the level of user using VI architecture (Pickard et al., 2017). TCP flow
identification, TCP/IP header compaction and TCP checksum off-loading may use the packet
header of VI through enabling the SAN tunneling. A TCP flow labeling method is to be
implemented based on the VI Architecture. This technique will allow efficient TCP packet flows
lookups efficiently. This technique include TCP packets encapsulated tunneling over VI
connections. The utilization of labelling of TCP flow will enable the lookup which is based on
simple indexing. The cellular system will generate a flow identifier at the time of establishing
initial TCP connection.
Another cellular system implementation is done through establishing distributed network
services. The architecture of the system will enable two levels of network services. This will
allow the cellular system to execute layer 2 to layer 4 execution along with the layer 5 to layer 7
processing. The network load balancing service can be developed in the cellular system using
this Distributed Network Services.
Prototype Implementation: The method of prototype implementation helps in providing
a practical experience for the building of CSP system.
i. Application and SAN Transport – Based on the need for constructing the
prototype for the existing technologies, the Gigabit Ethernet was used and was
considered to provide switched interconnect between the system elements
pipeline. A SAN tunnel (VI) based IPC mechanism will be established so that proxy nodes and
network nodes can communicate properly. In order to achieve this mechanism, the network
packet encapsulation is done in the System Area Network packet header information. This
mechanism is highly recommended to implement as it will allow processing of TCP/IP packets
by the proxy nodes at the level of user using VI architecture (Pickard et al., 2017). TCP flow
identification, TCP/IP header compaction and TCP checksum off-loading may use the packet
header of VI through enabling the SAN tunneling. A TCP flow labeling method is to be
implemented based on the VI Architecture. This technique will allow efficient TCP packet flows
lookups efficiently. This technique include TCP packets encapsulated tunneling over VI
connections. The utilization of labelling of TCP flow will enable the lookup which is based on
simple indexing. The cellular system will generate a flow identifier at the time of establishing
initial TCP connection.
Another cellular system implementation is done through establishing distributed network
services. The architecture of the system will enable two levels of network services. This will
allow the cellular system to execute layer 2 to layer 4 execution along with the layer 5 to layer 7
processing. The network load balancing service can be developed in the cellular system using
this Distributed Network Services.
Prototype Implementation: The method of prototype implementation helps in providing
a practical experience for the building of CSP system.
i. Application and SAN Transport – Based on the need for constructing the
prototype for the existing technologies, the Gigabit Ethernet was used and was
considered to provide switched interconnect between the system elements
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10COMPUTER NETWORKING ASSIGNMENT
(McQuistin, Perkins & Fayed, 2016). A Modular-VI Architecture (M-VIA) was
also used for providing an interface within each of the element of the system.
ii. Network Node – The prototype CSP network node made use of an Intel IXP1200
network processor. The IXP1200 can be defined as a single chip network
processor that would be comprised of interfaces based on media access devices
and external memories. The internal architecture of IXP1200 would comprise of
certain functional units: SRAM and SDRAM memory interface, RISC engines
and one StrongARM.
iii. Proxy Node – In this prototype, there was a standard rack mounted with 800 MHz
Pentium III Processor. These servers would be running on Linux OS and would
be thus considered as proxy nodes. The proxy node makes use of TCP/IP in order
to communicate with WAN/LAN clients (Takano et al., 2014). In this system, the
SAN Proxy service could be used as a user-level multithreaded application that
employs a pool of worker threads. Each of the worker thread would be specialized
for performing work over a subset of functions that would be associated with the
processing of TCP/IP, initial discovery mechanism and protocol translation or
decoupling.
iv. Application Node – In the designed prototype, there was an introduction of Socket
Filter module for intercepting each of the socket-related function calls that would
be comprising of legacy applications. In an environment consisting of Windows
NT, the module of socket filter would be dynamically loaded in the form of a
dynamically loadable library (DLL).
(McQuistin, Perkins & Fayed, 2016). A Modular-VI Architecture (M-VIA) was
also used for providing an interface within each of the element of the system.
ii. Network Node – The prototype CSP network node made use of an Intel IXP1200
network processor. The IXP1200 can be defined as a single chip network
processor that would be comprised of interfaces based on media access devices
and external memories. The internal architecture of IXP1200 would comprise of
certain functional units: SRAM and SDRAM memory interface, RISC engines
and one StrongARM.
iii. Proxy Node – In this prototype, there was a standard rack mounted with 800 MHz
Pentium III Processor. These servers would be running on Linux OS and would
be thus considered as proxy nodes. The proxy node makes use of TCP/IP in order
to communicate with WAN/LAN clients (Takano et al., 2014). In this system, the
SAN Proxy service could be used as a user-level multithreaded application that
employs a pool of worker threads. Each of the worker thread would be specialized
for performing work over a subset of functions that would be associated with the
processing of TCP/IP, initial discovery mechanism and protocol translation or
decoupling.
iv. Application Node – In the designed prototype, there was an introduction of Socket
Filter module for intercepting each of the socket-related function calls that would
be comprising of legacy applications. In an environment consisting of Windows
NT, the module of socket filter would be dynamically loaded in the form of a
dynamically loadable library (DLL).
11COMPUTER NETWORKING ASSIGNMENT
v. Management Node – The primary functions of the management node that was
implemented within the prototype was to maintain a certain centralized CSP
information database. It would be helpful in setting of policies for other nodes and
thus also facilitate the operations based on initial discovery (Gandino,
Montrucchio & Rebaudengo, 2014). The other nodes would mostly register with
the management node and thus inform them about the certain capabilities.
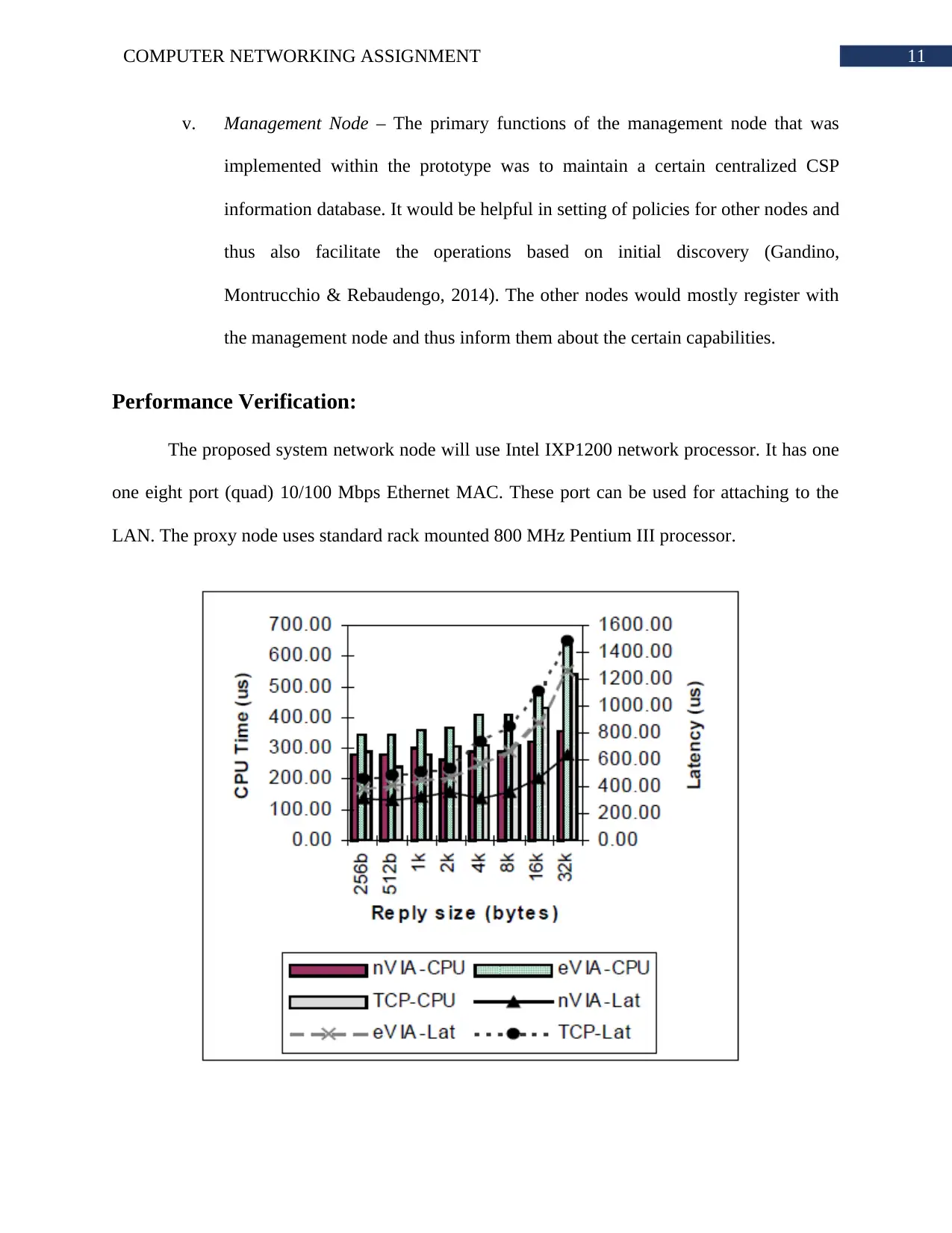
Performance Verification:
The proposed system network node will use Intel IXP1200 network processor. It has one
one eight port (quad) 10/100 Mbps Ethernet MAC. These port can be used for attaching to the
LAN. The proxy node uses standard rack mounted 800 MHz Pentium III processor.
v. Management Node – The primary functions of the management node that was
implemented within the prototype was to maintain a certain centralized CSP
information database. It would be helpful in setting of policies for other nodes and
thus also facilitate the operations based on initial discovery (Gandino,
Montrucchio & Rebaudengo, 2014). The other nodes would mostly register with
the management node and thus inform them about the certain capabilities.
Performance Verification:
The proposed system network node will use Intel IXP1200 network processor. It has one
one eight port (quad) 10/100 Mbps Ethernet MAC. These port can be used for attaching to the
LAN. The proxy node uses standard rack mounted 800 MHz Pentium III processor.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




