Computer Networking: Design, Implementation, and Maintenance
VerifiedAdded on 2024/05/21
|39
|4643
|493
AI Summary
This report delves into the fundamentals of computer networking, covering network types, systems, topologies, protocols, and hardware components. It explores the interdependency and functionality of different network elements and presents a network design implemented for 'sys-go.co.uk' using Cisco Packet Tracer. The report analyzes the network's communication and performance, comparing achieved results with expected outcomes. It also recommends potential enhancements for future demands and outlines a maintenance schedule for the network.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

NETWORKING
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
Introduction......................................................................................................................................1
LO1..................................................................................................................................................2
P1 Discuss the benefits and constraints of different network types and standards.....................2
P2 Explain the impact of network topology, communication and bandwidth requirements.......7
M1 Compare common networking principles and how protocols enable the effectiveness of
networked systems.......................................................................................................................9
LO2................................................................................................................................................10
P3 Discuss the operating principles of networking devices and server types...........................10
P4 Discuss the inter-dependence of workstation hardware with relevant networking software.
...................................................................................................................................................13
M2 Explore a range of server types and justify the selection of a server, considering a given
scenario regarding cost and performance optimisation.............................................................14
LO3................................................................................................................................................15
P5 Design a networked system to meet a given specification. (Sadiku, M.N., 2017. ).............15
P6 Test and evaluate the design to meet the requirements and analyse user feedback.............15
D2 Design a maintenance schedule to support the networked system......................................17
LO4................................................................................................................................................19
P7 Implement a networked system based on a prepared design................................................19
P8 Document and analyse test results against expected results.................................................22
M4 Recommend potential enhancements for the networked systems.......................................24
D3 Use critical reflection to evaluate own work and justify valid conclusions........................25
Conclusion.....................................................................................................................................26
References......................................................................................................................................27
Introduction......................................................................................................................................1
LO1..................................................................................................................................................2
P1 Discuss the benefits and constraints of different network types and standards.....................2
P2 Explain the impact of network topology, communication and bandwidth requirements.......7
M1 Compare common networking principles and how protocols enable the effectiveness of
networked systems.......................................................................................................................9
LO2................................................................................................................................................10
P3 Discuss the operating principles of networking devices and server types...........................10
P4 Discuss the inter-dependence of workstation hardware with relevant networking software.
...................................................................................................................................................13
M2 Explore a range of server types and justify the selection of a server, considering a given
scenario regarding cost and performance optimisation.............................................................14
LO3................................................................................................................................................15
P5 Design a networked system to meet a given specification. (Sadiku, M.N., 2017. ).............15
P6 Test and evaluate the design to meet the requirements and analyse user feedback.............15
D2 Design a maintenance schedule to support the networked system......................................17
LO4................................................................................................................................................19
P7 Implement a networked system based on a prepared design................................................19
P8 Document and analyse test results against expected results.................................................22
M4 Recommend potential enhancements for the networked systems.......................................24
D3 Use critical reflection to evaluate own work and justify valid conclusions........................25
Conclusion.....................................................................................................................................26
References......................................................................................................................................27

LIST OF TABLES
Table 1: Benefit and constraints of peer-to-peer and client server network....................................3
Table 2: Benefits and Constraints of different network types.........................................................4
Table 3: maintenance schedule......................................................................................................17
Table 4: Test result when compared between expected and attained result of the network design
.......................................................................................................................................................22
Table 1: Benefit and constraints of peer-to-peer and client server network....................................3
Table 2: Benefits and Constraints of different network types.........................................................4
Table 3: maintenance schedule......................................................................................................17
Table 4: Test result when compared between expected and attained result of the network design
.......................................................................................................................................................22

LIST OF FIGURES
Figure 1: Peer-to-peer network........................................................................................................2
Figure 2: Different types of computer network...............................................................................4
Figure 3: Wireless Standards..........................................................................................................6
Figure 4: Ethernet standards............................................................................................................6
Figure 5: Different network topology..............................................................................................7
Figure 6: Types of Network Topology............................................................................................7
Figure 7: Different Network protocols............................................................................................9
Figure 8: File server.......................................................................................................................10
Figure 9: Mail server.....................................................................................................................11
Figure 10: Web server...................................................................................................................11
Figure 11: Database server............................................................................................................12
Figure 12: Network design............................................................................................................15
Figure 13: IP address on computers...............................................................................................16
Figure 14: Printer configuration....................................................................................................16
Figure 15: Switch configuration for VLAN..................................................................................17
Figure 16: Router configuration....................................................................................................17
Figure 17: Web server configuration.............................................................................................18
Figure 18: DNS configuration.......................................................................................................18
Figure 19: User and password on mail server...............................................................................19
Figure 20: FTP configuration........................................................................................................19
Figure 21: Ping successful between design and sales department.................................................20
Figure 22: Ping failed when connecting outside the scope............................................................21
Figure 23: configuration of the router...........................................................................................26
Figure 24: Configuration of routing algorithm..............................................................................27
Figure 25: Configuration of Switch used in the network..............................................................27
Figure 26: Configuration of Server................................................................................................27
Figure 27: Configuration of DNS server in the network...............................................................28
Figure 1: Peer-to-peer network........................................................................................................2
Figure 2: Different types of computer network...............................................................................4
Figure 3: Wireless Standards..........................................................................................................6
Figure 4: Ethernet standards............................................................................................................6
Figure 5: Different network topology..............................................................................................7
Figure 6: Types of Network Topology............................................................................................7
Figure 7: Different Network protocols............................................................................................9
Figure 8: File server.......................................................................................................................10
Figure 9: Mail server.....................................................................................................................11
Figure 10: Web server...................................................................................................................11
Figure 11: Database server............................................................................................................12
Figure 12: Network design............................................................................................................15
Figure 13: IP address on computers...............................................................................................16
Figure 14: Printer configuration....................................................................................................16
Figure 15: Switch configuration for VLAN..................................................................................17
Figure 16: Router configuration....................................................................................................17
Figure 17: Web server configuration.............................................................................................18
Figure 18: DNS configuration.......................................................................................................18
Figure 19: User and password on mail server...............................................................................19
Figure 20: FTP configuration........................................................................................................19
Figure 21: Ping successful between design and sales department.................................................20
Figure 22: Ping failed when connecting outside the scope............................................................21
Figure 23: configuration of the router...........................................................................................26
Figure 24: Configuration of routing algorithm..............................................................................27
Figure 25: Configuration of Switch used in the network..............................................................27
Figure 26: Configuration of Server................................................................................................27
Figure 27: Configuration of DNS server in the network...............................................................28
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Introduction
Computer Networking stands for design and implementing a network for establishing
communication among the user with proper use of software and protocols. In this report,
fundamentals of computer networking are discussed covering network types, network systems,
various network topologies along with different protocols and standards used in a network
system. The report will address interdependent network components used in the organizational
network. The present report will provide network design, its implement implementation and
maintain the schedule. Brief knowledge for enhancing the system according to the future
requirement will be delivered. Different testing techniques and potential enhancement will also
be provided.
1
Computer Networking stands for design and implementing a network for establishing
communication among the user with proper use of software and protocols. In this report,
fundamentals of computer networking are discussed covering network types, network systems,
various network topologies along with different protocols and standards used in a network
system. The report will address interdependent network components used in the organizational
network. The present report will provide network design, its implement implementation and
maintain the schedule. Brief knowledge for enhancing the system according to the future
requirement will be delivered. Different testing techniques and potential enhancement will also
be provided.
1
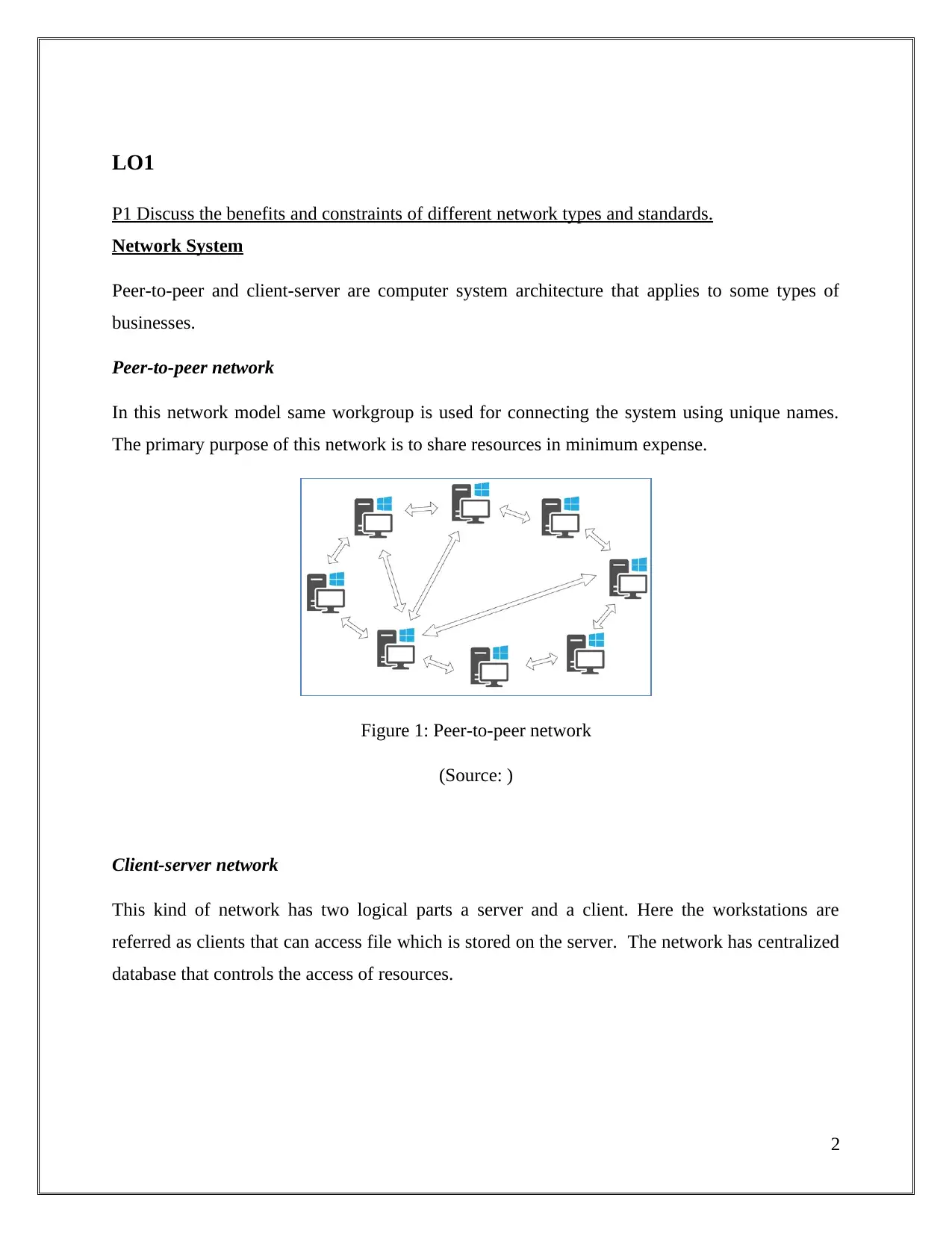
LO1
P1 Discuss the benefits and constraints of different network types and standards.
Network System
Peer-to-peer and client-server are computer system architecture that applies to some types of
businesses.
Peer-to-peer network
In this network model same workgroup is used for connecting the system using unique names.
The primary purpose of this network is to share resources in minimum expense.
Figure 1: Peer-to-peer network
(Source: )
Client-server network
This kind of network has two logical parts a server and a client. Here the workstations are
referred as clients that can access file which is stored on the server. The network has centralized
database that controls the access of resources.
2
P1 Discuss the benefits and constraints of different network types and standards.
Network System
Peer-to-peer and client-server are computer system architecture that applies to some types of
businesses.
Peer-to-peer network
In this network model same workgroup is used for connecting the system using unique names.
The primary purpose of this network is to share resources in minimum expense.
Figure 1: Peer-to-peer network
(Source: )
Client-server network
This kind of network has two logical parts a server and a client. Here the workstations are
referred as clients that can access file which is stored on the server. The network has centralized
database that controls the access of resources.
2
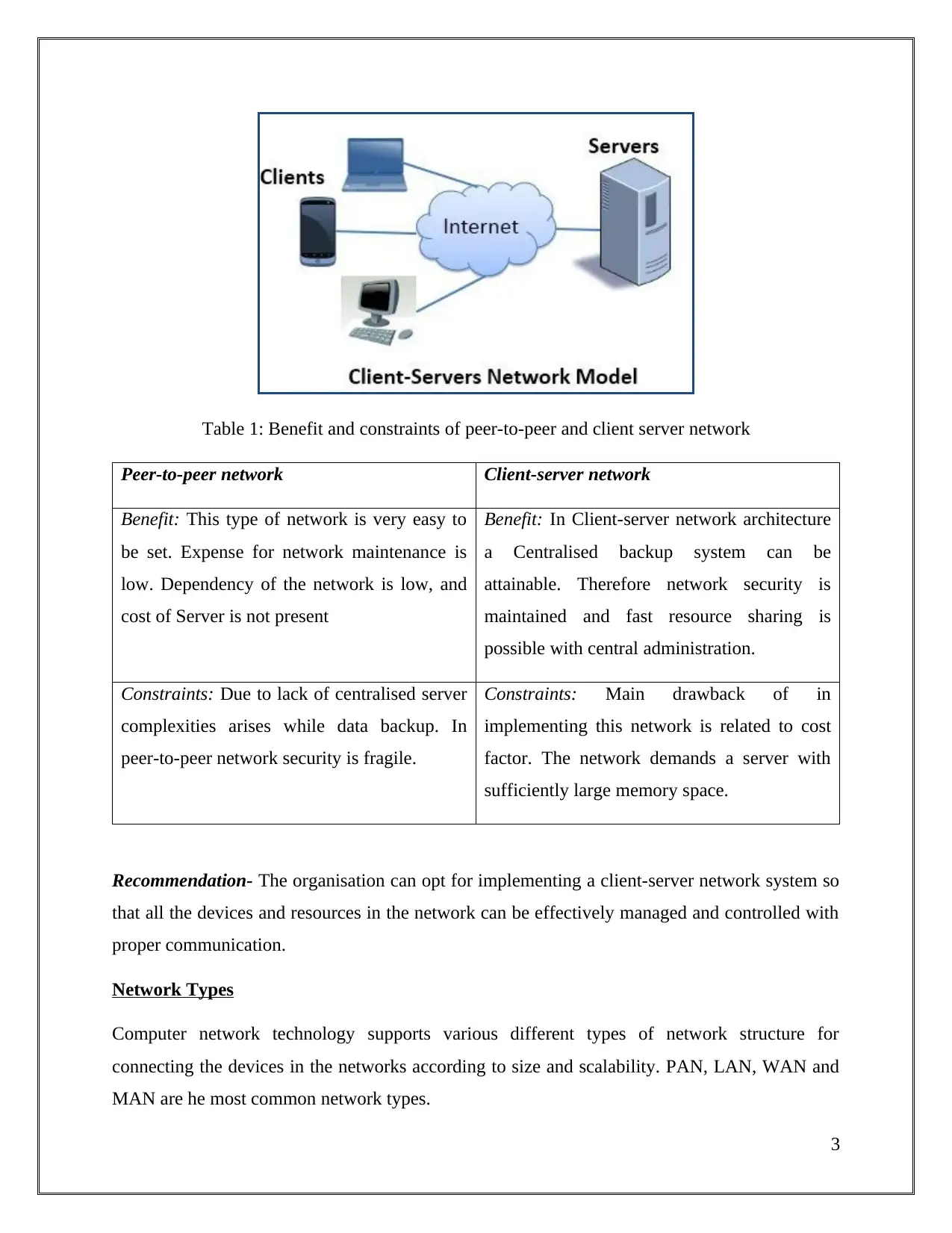
Table 1: Benefit and constraints of peer-to-peer and client server network
Peer-to-peer network Client-server network
Benefit: This type of network is very easy to
be set. Expense for network maintenance is
low. Dependency of the network is low, and
cost of Server is not present
Benefit: In Client-server network architecture
a Centralised backup system can be
attainable. Therefore network security is
maintained and fast resource sharing is
possible with central administration.
Constraints: Due to lack of centralised server
complexities arises while data backup. In
peer-to-peer network security is fragile.
Constraints: Main drawback of in
implementing this network is related to cost
factor. The network demands a server with
sufficiently large memory space.
Recommendation- The organisation can opt for implementing a client-server network system so
that all the devices and resources in the network can be effectively managed and controlled with
proper communication.
Network Types
Computer network technology supports various different types of network structure for
connecting the devices in the networks according to size and scalability. PAN, LAN, WAN and
MAN are he most common network types.
3
Peer-to-peer network Client-server network
Benefit: This type of network is very easy to
be set. Expense for network maintenance is
low. Dependency of the network is low, and
cost of Server is not present
Benefit: In Client-server network architecture
a Centralised backup system can be
attainable. Therefore network security is
maintained and fast resource sharing is
possible with central administration.
Constraints: Due to lack of centralised server
complexities arises while data backup. In
peer-to-peer network security is fragile.
Constraints: Main drawback of in
implementing this network is related to cost
factor. The network demands a server with
sufficiently large memory space.
Recommendation- The organisation can opt for implementing a client-server network system so
that all the devices and resources in the network can be effectively managed and controlled with
proper communication.
Network Types
Computer network technology supports various different types of network structure for
connecting the devices in the networks according to size and scalability. PAN, LAN, WAN and
MAN are he most common network types.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Figure 2: Different types of computer network
Personal Area Network, PAN – the network is formed when a computer of an individual is
linked with his other gadgets like a telephone, mobile phone, table, modem, etc.
Local Area Network, LAN – When a group of people or system are connected to a network for
sharing data and devices in a small area like a campus, building or a room.
Wide Area Network, WAN– When two or more LAN network is linked with one another over
a wireless technology it called as WAN (Niephaus, et al 2015). It can be seen commonly in
business organisation.
Metropolitan area network, MAN – It is the extended version of LAN network forms
connecting devices. The network is comparatively larger then LAN and smaller than WAN
network.
Table 2: Benefits and Constraints of different network types
Type of
network
Personal Area
Network
Local Area
Network
Wide Area
Network
Metropolitan
area network
Benefit Maintenance
efforts and cost of
the set up is low.
data sharing and
resource sharing
can be done in
The network
structuring is
uncomplicated
LAN is
homogenous.
Implementation
Several devices
can be linked in
this type of
network. Provides
high performance
and maintenance.
Connection of
both wireless
and wired
devices is
possible.
Performance of
4
Network
Types
PAN LAN MAN WAN
Personal Area Network, PAN – the network is formed when a computer of an individual is
linked with his other gadgets like a telephone, mobile phone, table, modem, etc.
Local Area Network, LAN – When a group of people or system are connected to a network for
sharing data and devices in a small area like a campus, building or a room.
Wide Area Network, WAN– When two or more LAN network is linked with one another over
a wireless technology it called as WAN (Niephaus, et al 2015). It can be seen commonly in
business organisation.
Metropolitan area network, MAN – It is the extended version of LAN network forms
connecting devices. The network is comparatively larger then LAN and smaller than WAN
network.
Table 2: Benefits and Constraints of different network types
Type of
network
Personal Area
Network
Local Area
Network
Wide Area
Network
Metropolitan
area network
Benefit Maintenance
efforts and cost of
the set up is low.
data sharing and
resource sharing
can be done in
The network
structuring is
uncomplicated
LAN is
homogenous.
Implementation
Several devices
can be linked in
this type of
network. Provides
high performance
and maintenance.
Connection of
both wireless
and wired
devices is
possible.
Performance of
4
Network
Types
PAN LAN MAN WAN
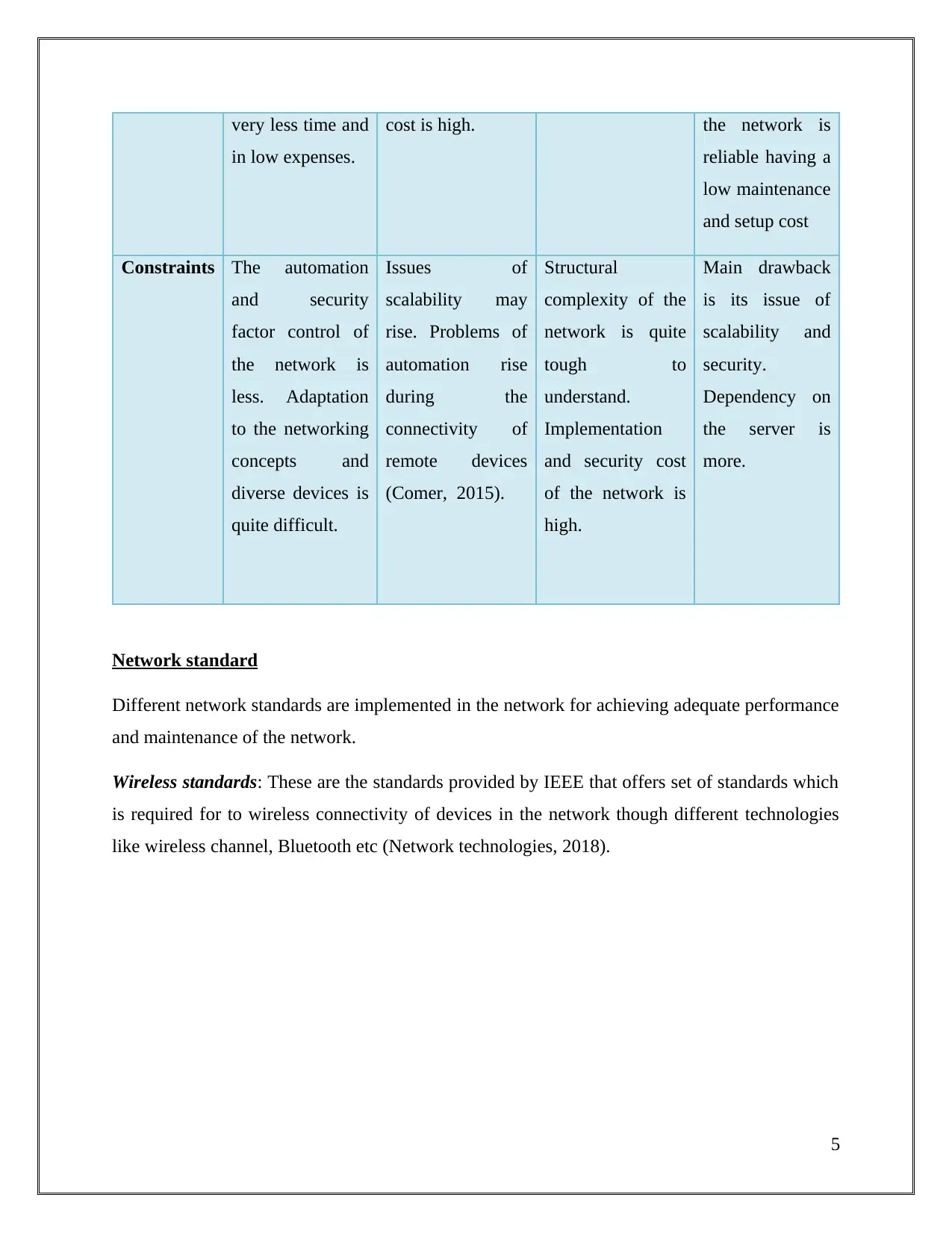
very less time and
in low expenses.
cost is high. the network is
reliable having a
low maintenance
and setup cost
Constraints The automation
and security
factor control of
the network is
less. Adaptation
to the networking
concepts and
diverse devices is
quite difficult.
Issues of
scalability may
rise. Problems of
automation rise
during the
connectivity of
remote devices
(Comer, 2015).
Structural
complexity of the
network is quite
tough to
understand.
Implementation
and security cost
of the network is
high.
Main drawback
is its issue of
scalability and
security.
Dependency on
the server is
more.
Network standard
Different network standards are implemented in the network for achieving adequate performance
and maintenance of the network.
Wireless standards: These are the standards provided by IEEE that offers set of standards which
is required for to wireless connectivity of devices in the network though different technologies
like wireless channel, Bluetooth etc (Network technologies, 2018).
5
in low expenses.
cost is high. the network is
reliable having a
low maintenance
and setup cost
Constraints The automation
and security
factor control of
the network is
less. Adaptation
to the networking
concepts and
diverse devices is
quite difficult.
Issues of
scalability may
rise. Problems of
automation rise
during the
connectivity of
remote devices
(Comer, 2015).
Structural
complexity of the
network is quite
tough to
understand.
Implementation
and security cost
of the network is
high.
Main drawback
is its issue of
scalability and
security.
Dependency on
the server is
more.
Network standard
Different network standards are implemented in the network for achieving adequate performance
and maintenance of the network.
Wireless standards: These are the standards provided by IEEE that offers set of standards which
is required for to wireless connectivity of devices in the network though different technologies
like wireless channel, Bluetooth etc (Network technologies, 2018).
5
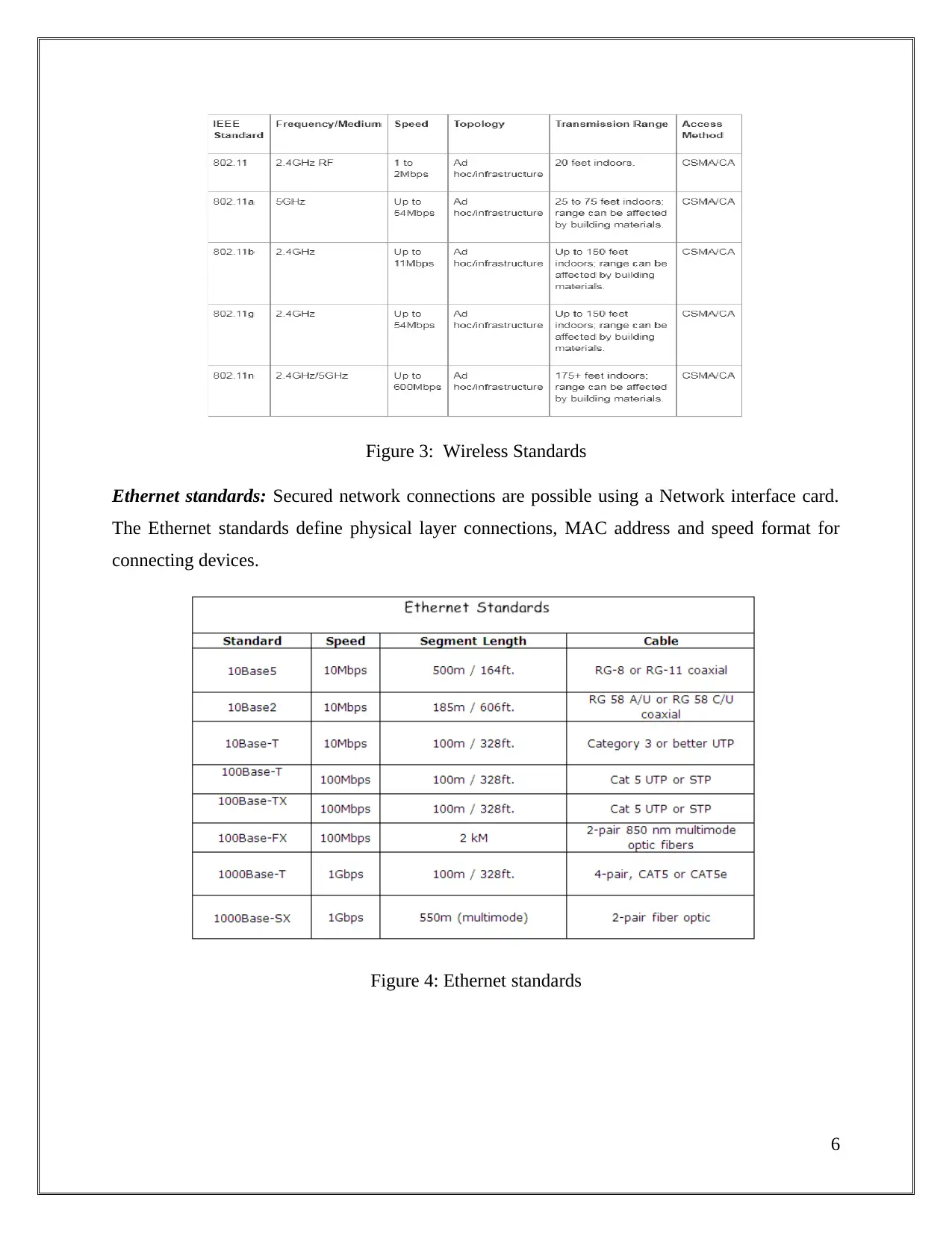
Figure 3: Wireless Standards
Ethernet standards: Secured network connections are possible using a Network interface card.
The Ethernet standards define physical layer connections, MAC address and speed format for
connecting devices.
Figure 4: Ethernet standards
6
Ethernet standards: Secured network connections are possible using a Network interface card.
The Ethernet standards define physical layer connections, MAC address and speed format for
connecting devices.
Figure 4: Ethernet standards
6
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
P2 Explain the impact of network topology, communication and bandwidth requirements.
Network Topology-
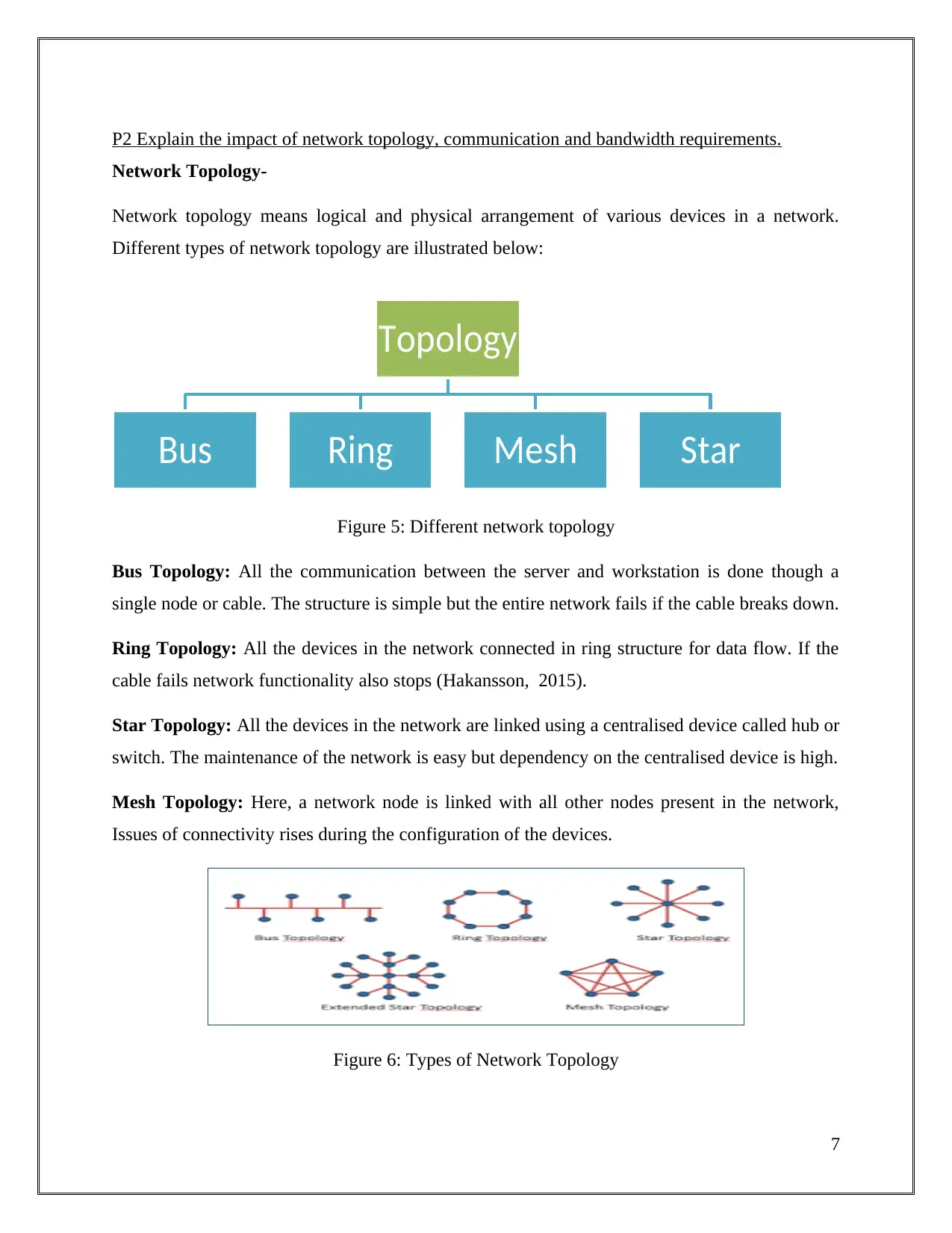
Network topology means logical and physical arrangement of various devices in a network.
Different types of network topology are illustrated below:
Figure 5: Different network topology
Bus Topology: All the communication between the server and workstation is done though a
single node or cable. The structure is simple but the entire network fails if the cable breaks down.
Ring Topology: All the devices in the network connected in ring structure for data flow. If the
cable fails network functionality also stops (Hakansson, 2015).
Star Topology: All the devices in the network are linked using a centralised device called hub or
switch. The maintenance of the network is easy but dependency on the centralised device is high.
Mesh Topology: Here, a network node is linked with all other nodes present in the network,
Issues of connectivity rises during the configuration of the devices.
Figure 6: Types of Network Topology
7
Topology
Bus Ring Mesh Star
Network Topology-
Network topology means logical and physical arrangement of various devices in a network.
Different types of network topology are illustrated below:
Figure 5: Different network topology
Bus Topology: All the communication between the server and workstation is done though a
single node or cable. The structure is simple but the entire network fails if the cable breaks down.
Ring Topology: All the devices in the network connected in ring structure for data flow. If the
cable fails network functionality also stops (Hakansson, 2015).
Star Topology: All the devices in the network are linked using a centralised device called hub or
switch. The maintenance of the network is easy but dependency on the centralised device is high.
Mesh Topology: Here, a network node is linked with all other nodes present in the network,
Issues of connectivity rises during the configuration of the devices.
Figure 6: Types of Network Topology
7
Topology
Bus Ring Mesh Star

Network topologies in simple words can be described as a format which is applied for
connecting all the network devices. For the present organization, the specific topology is applied
for attaining secure network and maintaining reliable network performance. For instance, Bus
topology can be used for implementing the devices for saving time as cost-cutting for network
maintenance. However, the performance of the network can be hampered if the load is high
affecting the network availability, performance, and reliability.
But on the other hand, the organization can configure al the device using star topology which is
expensive in comparison to the different topology. Separate cables are used for connecting the
devices. Therefore, tolerance power of the network is high concerning faults. Hence it can be
stated that, topology influence a system and its performance, security, reliability, and
availability.
8
connecting all the network devices. For the present organization, the specific topology is applied
for attaining secure network and maintaining reliable network performance. For instance, Bus
topology can be used for implementing the devices for saving time as cost-cutting for network
maintenance. However, the performance of the network can be hampered if the load is high
affecting the network availability, performance, and reliability.
But on the other hand, the organization can configure al the device using star topology which is
expensive in comparison to the different topology. Separate cables are used for connecting the
devices. Therefore, tolerance power of the network is high concerning faults. Hence it can be
stated that, topology influence a system and its performance, security, reliability, and
availability.
8
M1 Compare common networking principles and how protocols enable the effectiveness of
networked systems.
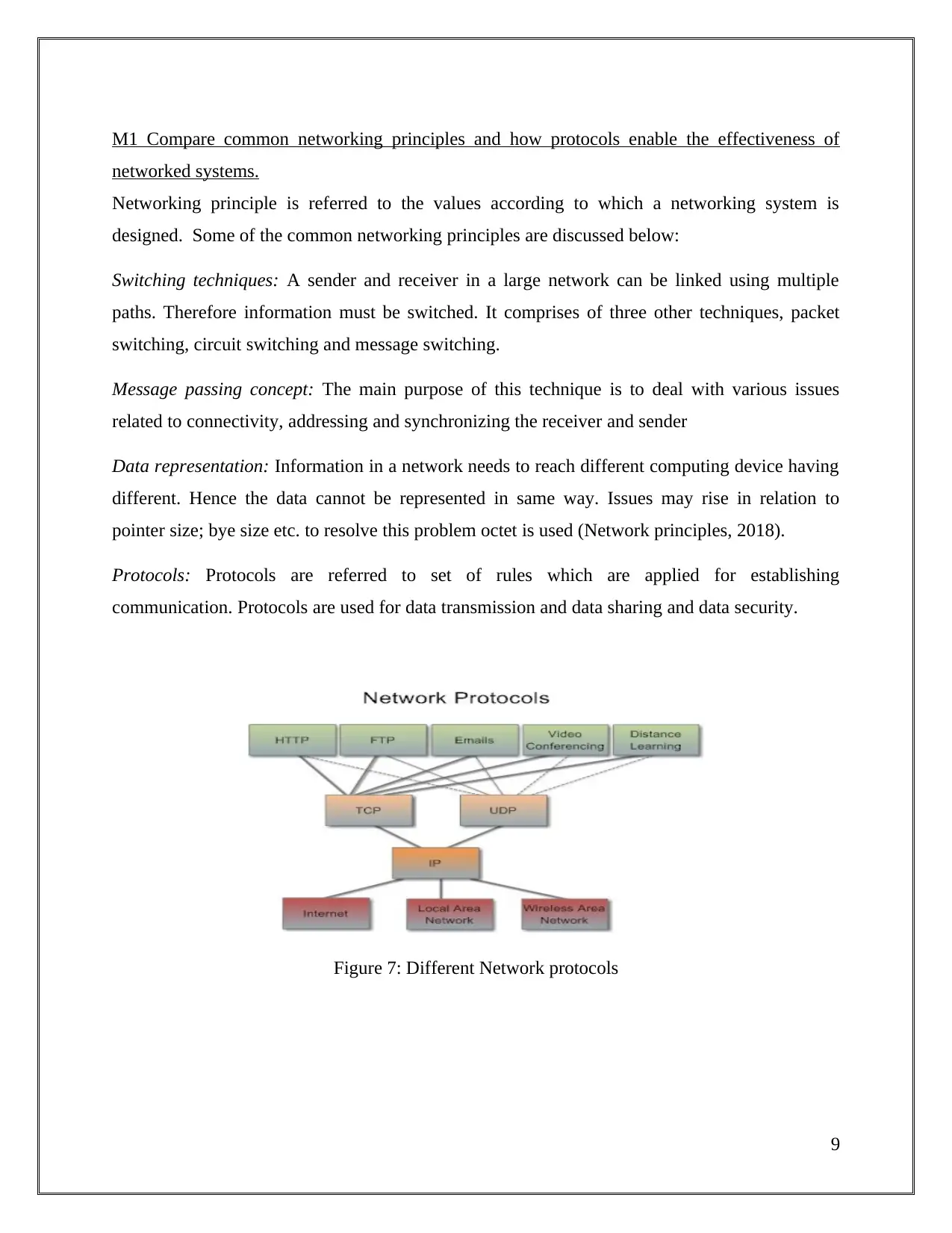
Networking principle is referred to the values according to which a networking system is
designed. Some of the common networking principles are discussed below:
Switching techniques: A sender and receiver in a large network can be linked using multiple
paths. Therefore information must be switched. It comprises of three other techniques, packet
switching, circuit switching and message switching.
Message passing concept: The main purpose of this technique is to deal with various issues
related to connectivity, addressing and synchronizing the receiver and sender
Data representation: Information in a network needs to reach different computing device having
different. Hence the data cannot be represented in same way. Issues may rise in relation to
pointer size; bye size etc. to resolve this problem octet is used (Network principles, 2018).
Protocols: Protocols are referred to set of rules which are applied for establishing
communication. Protocols are used for data transmission and data sharing and data security.
Figure 7: Different Network protocols
9
networked systems.
Networking principle is referred to the values according to which a networking system is
designed. Some of the common networking principles are discussed below:
Switching techniques: A sender and receiver in a large network can be linked using multiple
paths. Therefore information must be switched. It comprises of three other techniques, packet
switching, circuit switching and message switching.
Message passing concept: The main purpose of this technique is to deal with various issues
related to connectivity, addressing and synchronizing the receiver and sender
Data representation: Information in a network needs to reach different computing device having
different. Hence the data cannot be represented in same way. Issues may rise in relation to
pointer size; bye size etc. to resolve this problem octet is used (Network principles, 2018).
Protocols: Protocols are referred to set of rules which are applied for establishing
communication. Protocols are used for data transmission and data sharing and data security.
Figure 7: Different Network protocols
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

LO2
P3 Discuss the operating principles of networking devices and server types.
Standards and protocols for power management must be implemented in the network for
obtaining compatibility and interoperability of network design. A network can be made energy
efficient by applying these standards and protocols. Any networking devices within the
organisational network must not be a reason of hindrance affecting the system of internal power
management.
Different types of server
The computer network is efficient by implementation of various servers. Some of them is
discussed below:
File server: File server stores file and offers service of file sharing to user with proper file
permission. Using a file server is effective in accessing and updating a file in the network.
Figure 8: File server
(Source: http://dotw.wikia.com/wiki/File:File_server.jpg, 2018)
10
P3 Discuss the operating principles of networking devices and server types.
Standards and protocols for power management must be implemented in the network for
obtaining compatibility and interoperability of network design. A network can be made energy
efficient by applying these standards and protocols. Any networking devices within the
organisational network must not be a reason of hindrance affecting the system of internal power
management.
Different types of server
The computer network is efficient by implementation of various servers. Some of them is
discussed below:
File server: File server stores file and offers service of file sharing to user with proper file
permission. Using a file server is effective in accessing and updating a file in the network.
Figure 8: File server
(Source: http://dotw.wikia.com/wiki/File:File_server.jpg, 2018)
10

Print server- Print server is used for controlling and monitoring printing service. Queuing and
Priority list is managed by print server.
Mail server- Mail servers are used for managing and storing mails of a user. A user with
appropriate authentication details can access their mail at anytime and from anywhere.
Communication is offered to departments and employees using this kind of server (Bhushan, et
al 2014).
Figure 9: Mail server
(https://teczuz.com/install-complete-mail-server-postfix-webmail-debian-9/, 2018)
Web server- Data and Information in internet are present in form of webpage that is shared
when request are made. Managing of the shared information is done by web server using proper
address allocation.
11
Priority list is managed by print server.
Mail server- Mail servers are used for managing and storing mails of a user. A user with
appropriate authentication details can access their mail at anytime and from anywhere.
Communication is offered to departments and employees using this kind of server (Bhushan, et
al 2014).
Figure 9: Mail server
(https://teczuz.com/install-complete-mail-server-postfix-webmail-debian-9/, 2018)
Web server- Data and Information in internet are present in form of webpage that is shared
when request are made. Managing of the shared information is done by web server using proper
address allocation.
11
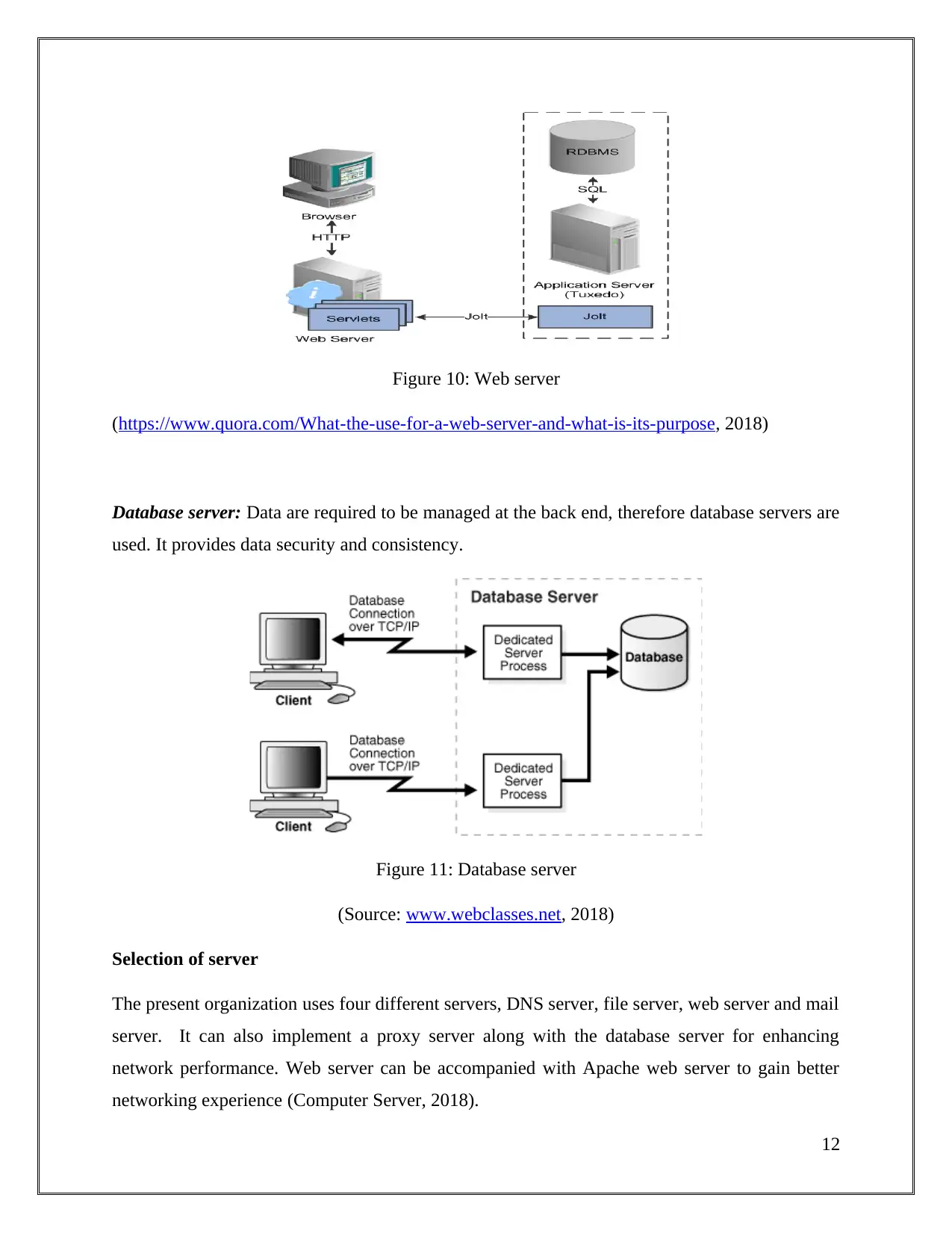
Figure 10: Web server
(https://www.quora.com/What-the-use-for-a-web-server-and-what-is-its-purpose, 2018)
Database server: Data are required to be managed at the back end, therefore database servers are
used. It provides data security and consistency.
Figure 11: Database server
(Source: www.webclasses.net, 2018)
Selection of server
The present organization uses four different servers, DNS server, file server, web server and mail
server. It can also implement a proxy server along with the database server for enhancing
network performance. Web server can be accompanied with Apache web server to gain better
networking experience (Computer Server, 2018).
12
(https://www.quora.com/What-the-use-for-a-web-server-and-what-is-its-purpose, 2018)
Database server: Data are required to be managed at the back end, therefore database servers are
used. It provides data security and consistency.
Figure 11: Database server
(Source: www.webclasses.net, 2018)
Selection of server
The present organization uses four different servers, DNS server, file server, web server and mail
server. It can also implement a proxy server along with the database server for enhancing
network performance. Web server can be accompanied with Apache web server to gain better
networking experience (Computer Server, 2018).
12
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

P4 Discuss the inter-dependence of workstation hardware with relevant networking software.
Computer in the network comprises of various hardware device some of the most significant
devices has been discussed below:
Network Interface Card (NIC)-NIC is an electronic circuit that is placed in the motherboard
effective in connecting various workstation and devices like switch and router in the network. Its
main function is to gather and send the data packet to the network (Fisher, et al. 2015).
Cables: Communication between the devices in the network is done through connectivity, and
for linking the device various types of cables are used that helps in sharing data. The choosing is
the cable is done by network size, topology, and physical layer. Some of the most commonly
used cables are twisted pairs, optical fiber and coaxial cables that not only connects the device
but also provides data security and reliability.
Processor- Processor is the brain of the computing devices it bond with the storage and memory
unit. From memory, data are fetched, and process and storage of the processed data are done in
the secondary memory. Intel Xeon processor can be used by the IT organization.
Input/output Devices- Input and output devices are the hardware and software devices that are
used for receiving and sending the data to and from the user.
All the components of the computer system are essential for effective implementation and
function of a network system ((Zhang, et al. 2014). These are the interdependent component of
the network because they provide networking facilities.
13
Computer in the network comprises of various hardware device some of the most significant
devices has been discussed below:
Network Interface Card (NIC)-NIC is an electronic circuit that is placed in the motherboard
effective in connecting various workstation and devices like switch and router in the network. Its
main function is to gather and send the data packet to the network (Fisher, et al. 2015).
Cables: Communication between the devices in the network is done through connectivity, and
for linking the device various types of cables are used that helps in sharing data. The choosing is
the cable is done by network size, topology, and physical layer. Some of the most commonly
used cables are twisted pairs, optical fiber and coaxial cables that not only connects the device
but also provides data security and reliability.
Processor- Processor is the brain of the computing devices it bond with the storage and memory
unit. From memory, data are fetched, and process and storage of the processed data are done in
the secondary memory. Intel Xeon processor can be used by the IT organization.
Input/output Devices- Input and output devices are the hardware and software devices that are
used for receiving and sending the data to and from the user.
All the components of the computer system are essential for effective implementation and
function of a network system ((Zhang, et al. 2014). These are the interdependent component of
the network because they provide networking facilities.
13

M2 Explore a range of server types and justify the selection of a server, considering a given
scenario regarding cost and performance optimisation.
Sys-go.co.uk has three different departments. For establishing proper connectivity between these
departments different servers are used like e-mail server, web server, file server and DNS server.
Implementation of the server is effective in providing data sharing facilities though the
centralised server; along with flexibility in communication for its reliability (Bonald, and
Feuillet, 2013). For the web server installation in the organization $ 3500 is required to be
invested. File server installation requires about $4250, DNS server installation will take around
$7500. The network uses Intel Xeon processor that has primary memory of 32 GB. And lastly for
maintaining the peripheral control 8 TB is needed with server O.S as Windows 2012. Therefore,
the servers installed will be effective in attaining required performance and security of the
network as per organisational demand.
14
scenario regarding cost and performance optimisation.
Sys-go.co.uk has three different departments. For establishing proper connectivity between these
departments different servers are used like e-mail server, web server, file server and DNS server.
Implementation of the server is effective in providing data sharing facilities though the
centralised server; along with flexibility in communication for its reliability (Bonald, and
Feuillet, 2013). For the web server installation in the organization $ 3500 is required to be
invested. File server installation requires about $4250, DNS server installation will take around
$7500. The network uses Intel Xeon processor that has primary memory of 32 GB. And lastly for
maintaining the peripheral control 8 TB is needed with server O.S as Windows 2012. Therefore,
the servers installed will be effective in attaining required performance and security of the
network as per organisational demand.
14
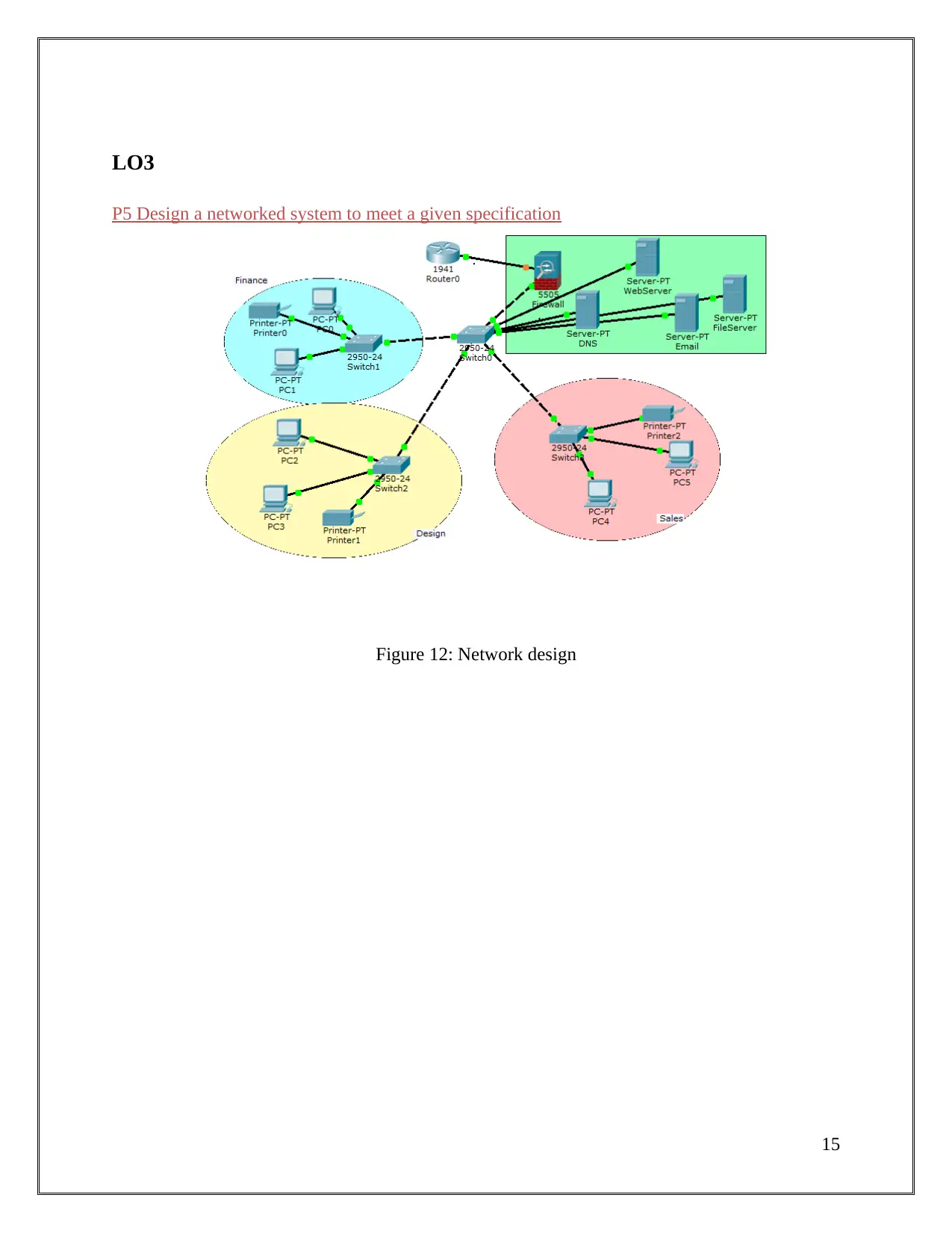
LO3
P5 Design a networked system to meet a given specification
Figure 12: Network design
15
P5 Design a networked system to meet a given specification
Figure 12: Network design
15
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
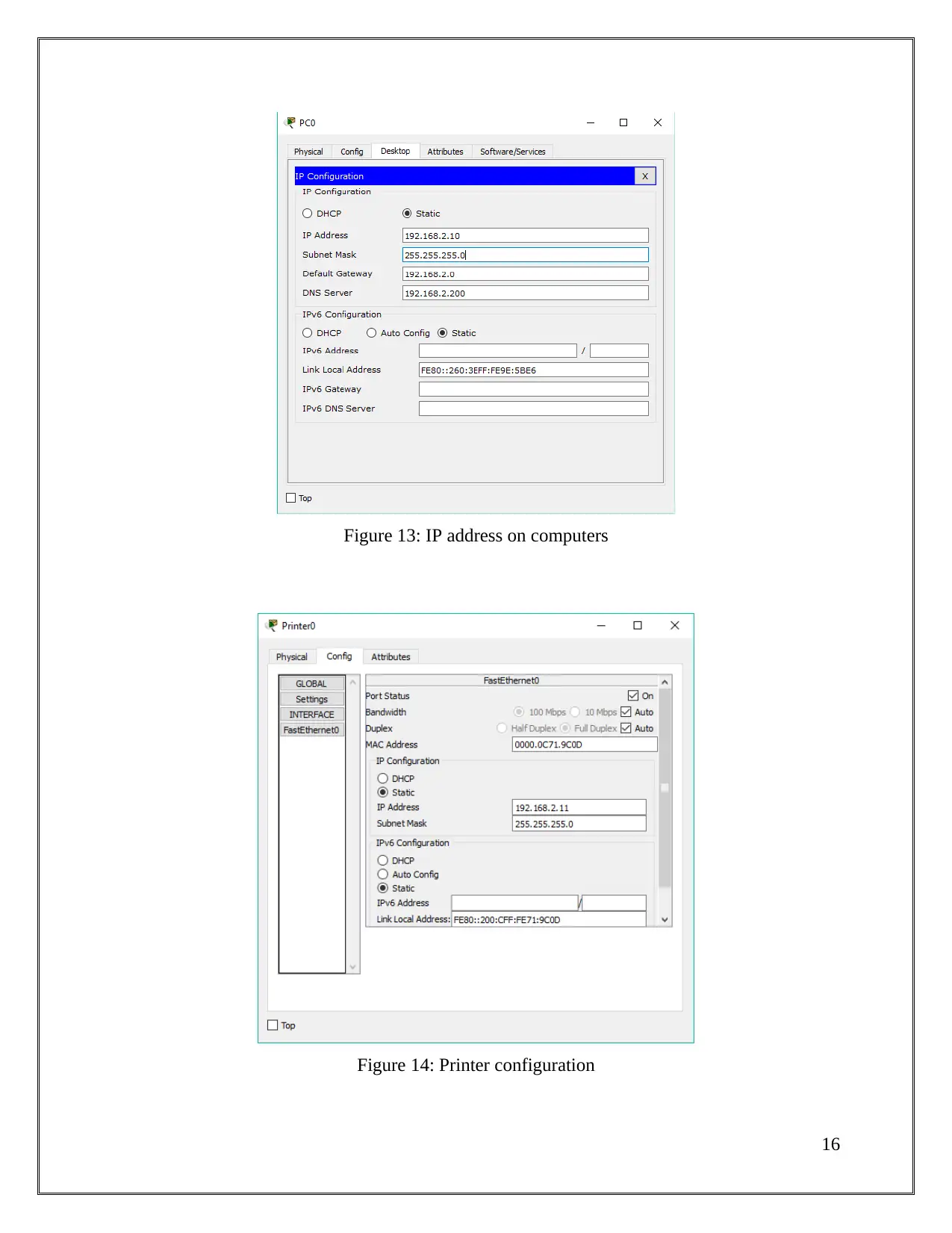
Figure 13: IP address on computers
Figure 14: Printer configuration
16
Figure 14: Printer configuration
16
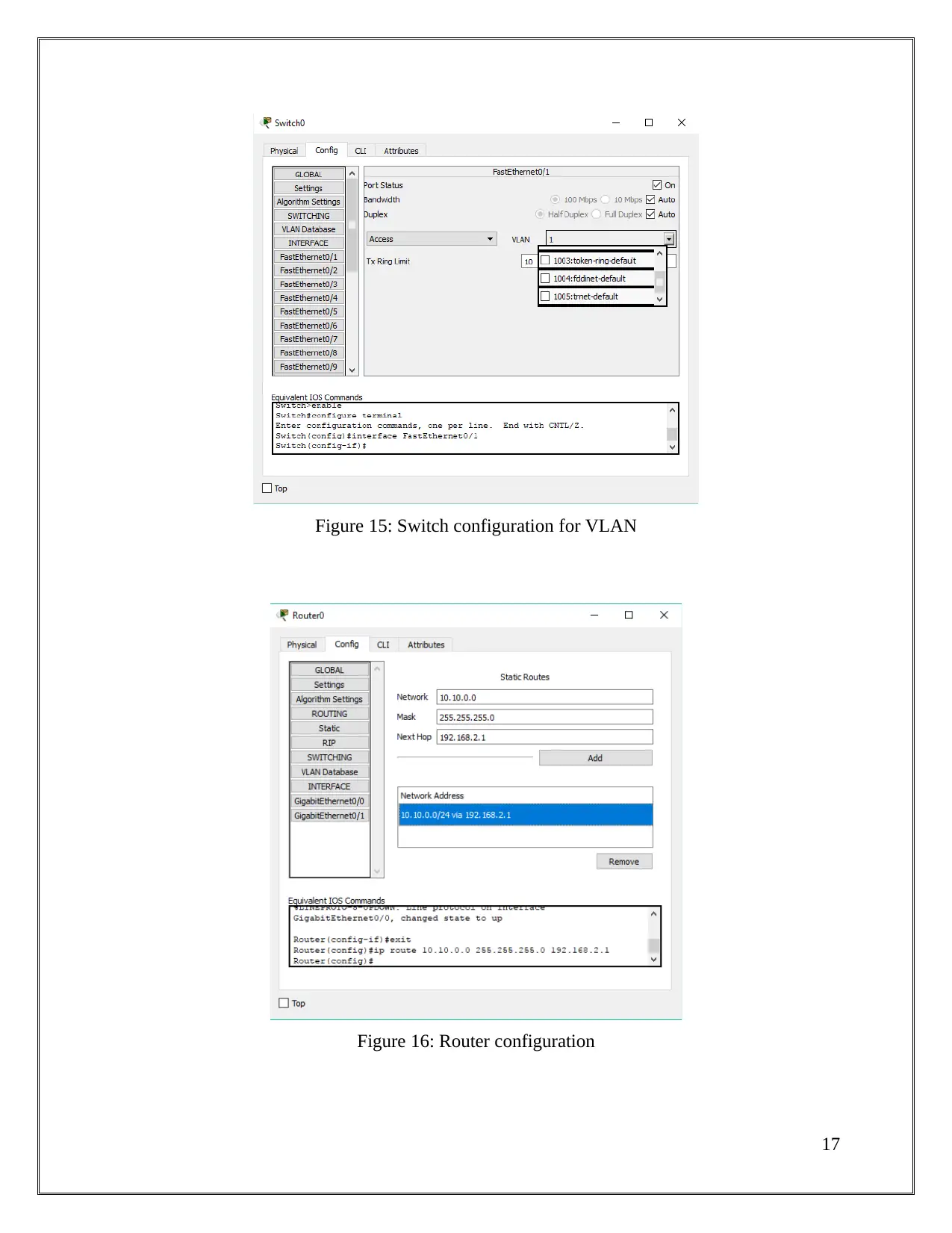
Figure 15: Switch configuration for VLAN
Figure 16: Router configuration
17
Figure 16: Router configuration
17
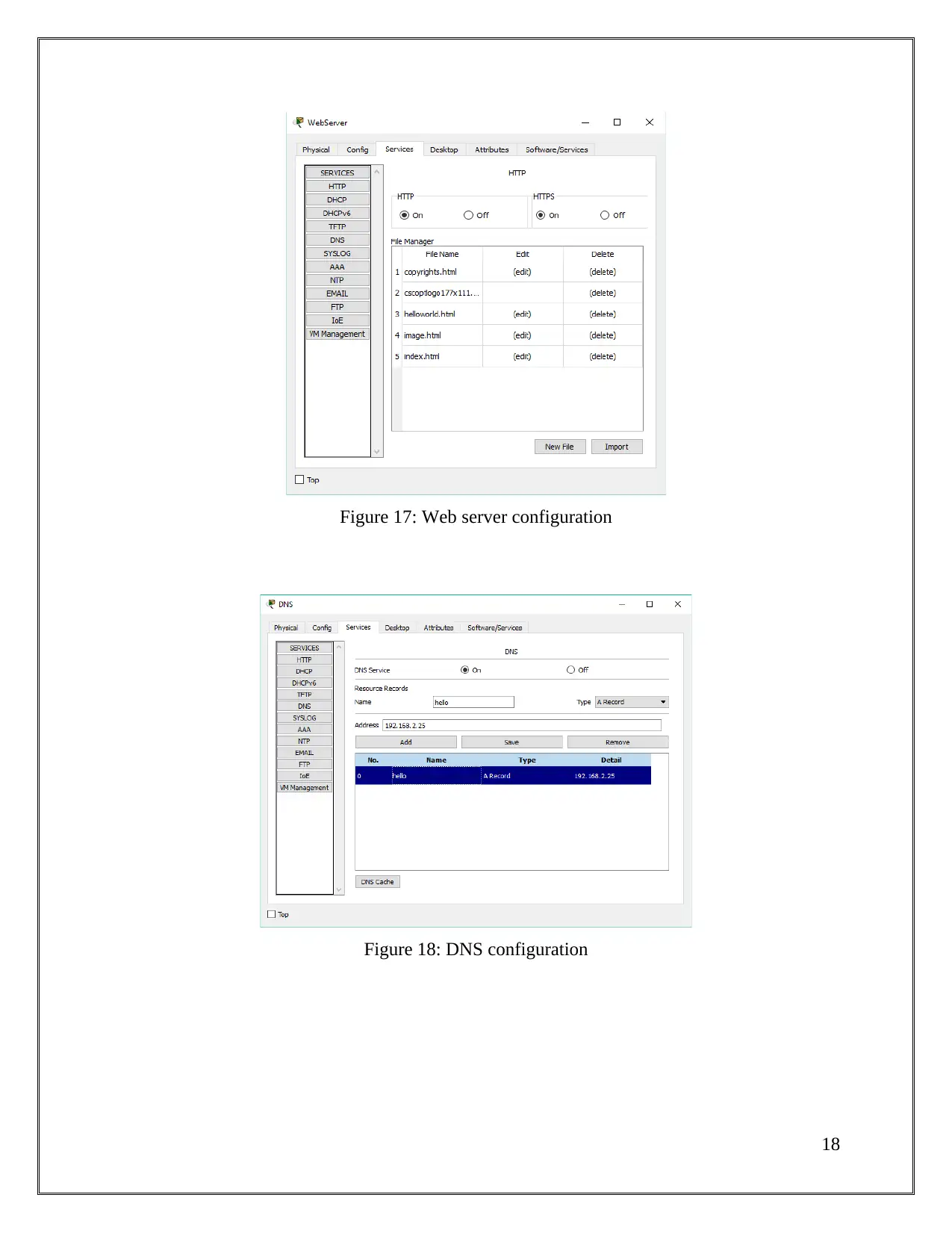
Figure 17: Web server configuration
Figure 18: DNS configuration
18
Figure 18: DNS configuration
18
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
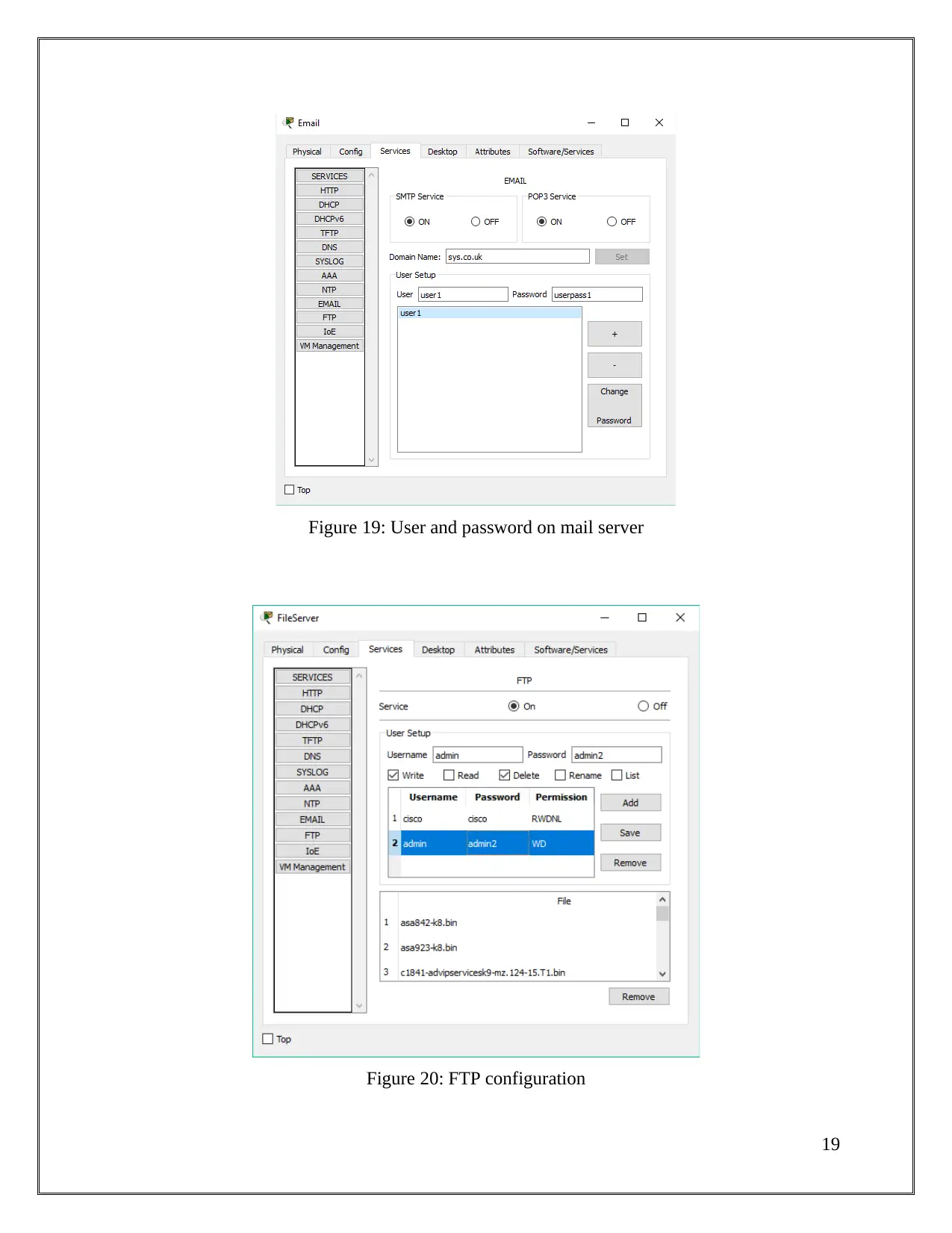
Figure 19: User and password on mail server
Figure 20: FTP configuration
19
Figure 20: FTP configuration
19
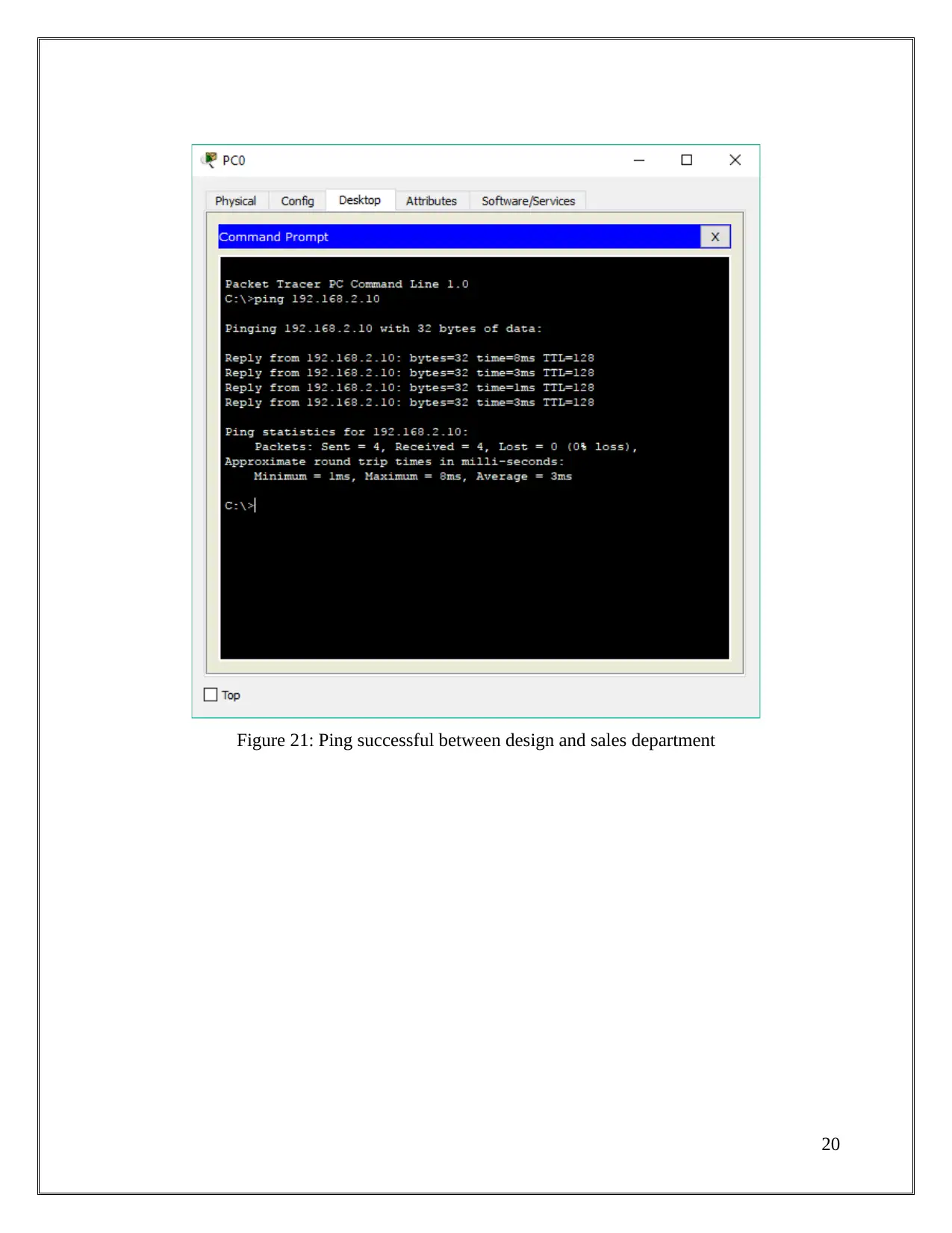
Figure 21: Ping successful between design and sales department
20
20
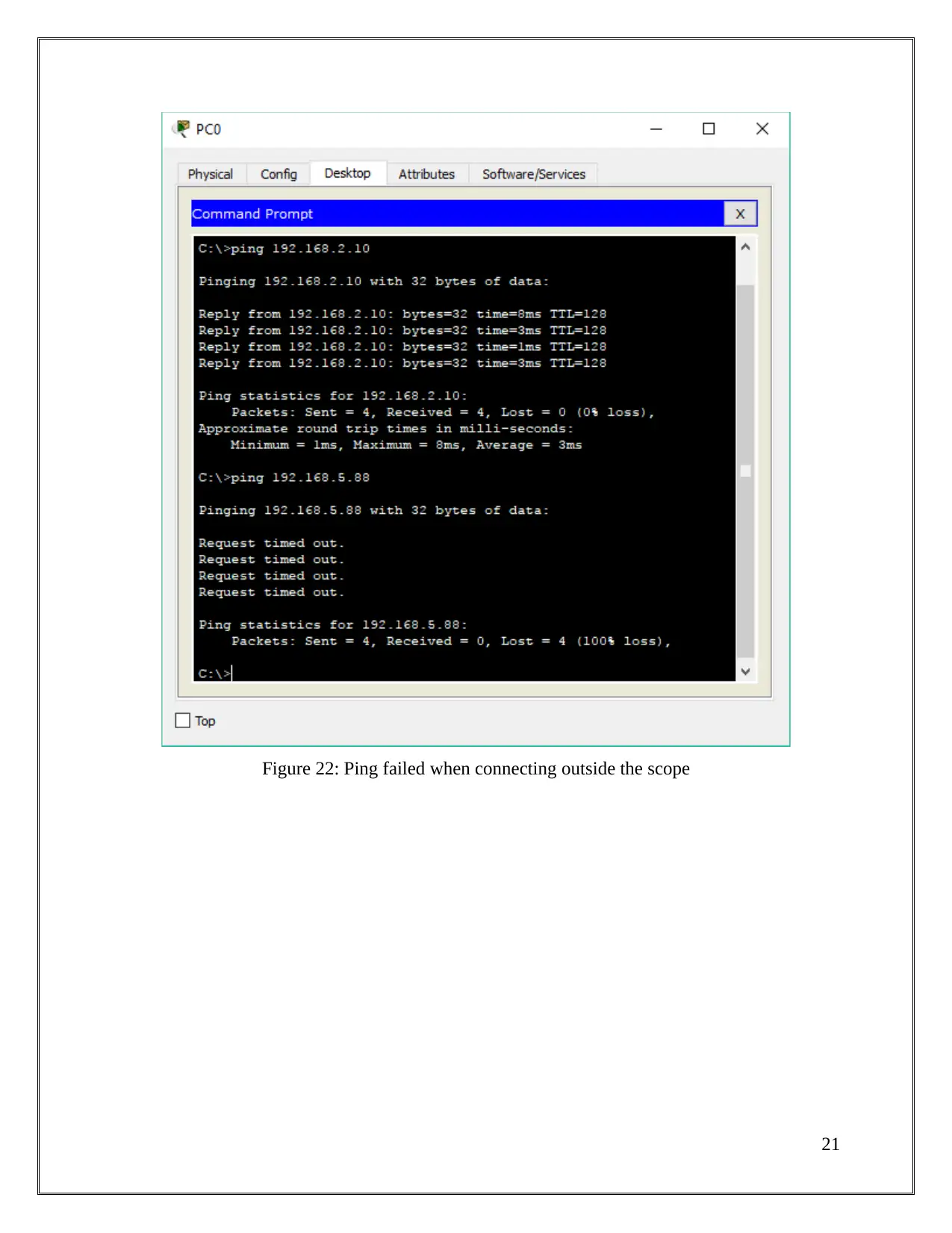
Figure 22: Ping failed when connecting outside the scope
21
21
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P6 Test and evaluate the design to meet the requirements and analyse user feedback.
Questionnaire is prepared fo0r the employees of the organisation for knowing the network status
according to is performance and security.
1. Rate the network design on the basis of networking speed.
a. Very good b. Good c. satisfactory d. Not
satisfactory
2. Are you capable accessing the internet 24/7?
a. Yes b. No c. Not really
3. Do you think that your file in the server is safe?
a. Yes b. No c. Do not know.
4. Is data security maintained in the network?
a. Yes b. No c. Do not know.
5. Lack of data security is because of?
a. LAN b. Firewall c. Server
22
Questionnaire is prepared fo0r the employees of the organisation for knowing the network status
according to is performance and security.
1. Rate the network design on the basis of networking speed.
a. Very good b. Good c. satisfactory d. Not
satisfactory
2. Are you capable accessing the internet 24/7?
a. Yes b. No c. Not really
3. Do you think that your file in the server is safe?
a. Yes b. No c. Do not know.
4. Is data security maintained in the network?
a. Yes b. No c. Do not know.
5. Lack of data security is because of?
a. LAN b. Firewall c. Server
22
60%
25%
15%
Network
Good satisfactory not satisfied
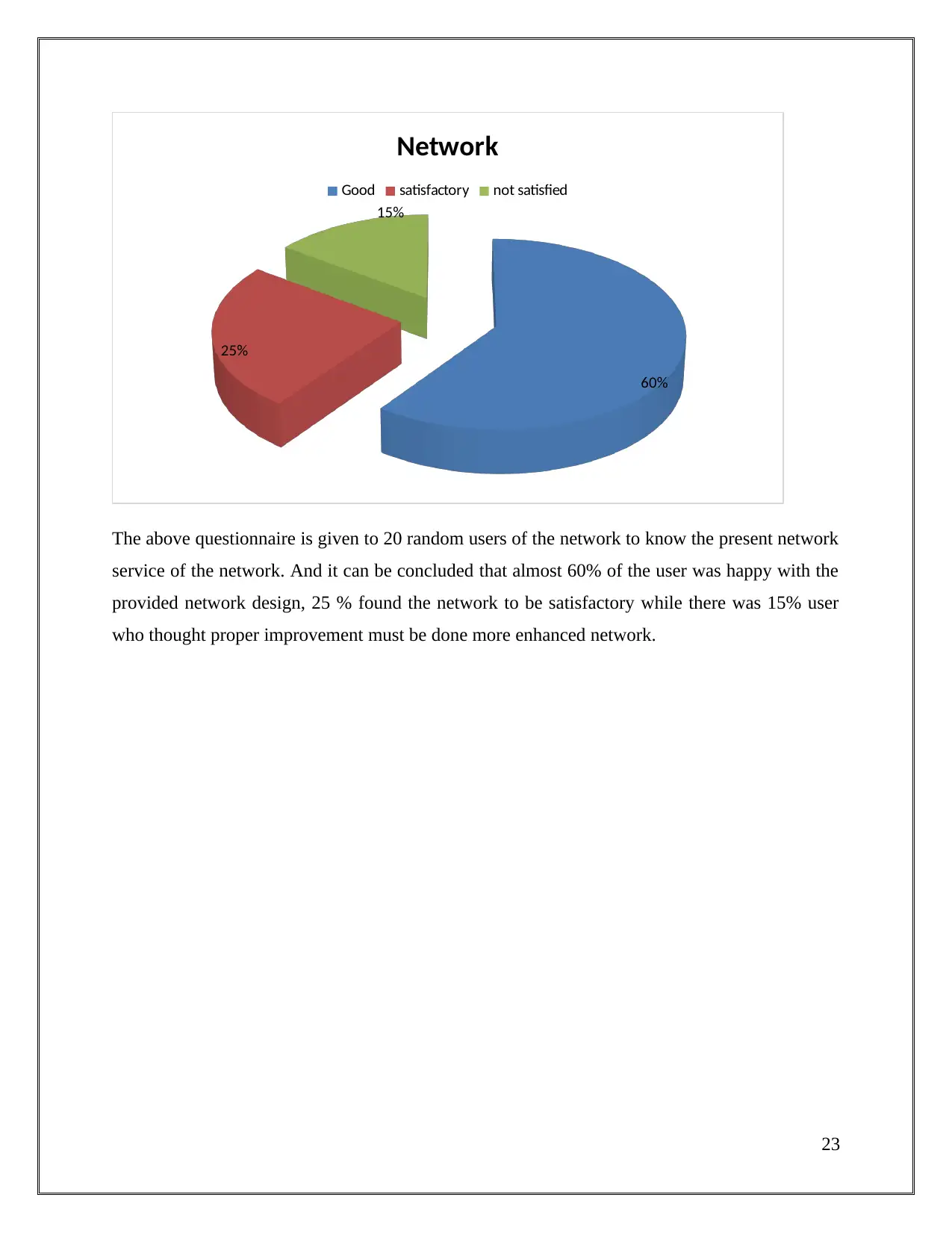
The above questionnaire is given to 20 random users of the network to know the present network
service of the network. And it can be concluded that almost 60% of the user was happy with the
provided network design, 25 % found the network to be satisfactory while there was 15% user
who thought proper improvement must be done more enhanced network.
23
25%
15%
Network
Good satisfactory not satisfied
The above questionnaire is given to 20 random users of the network to know the present network
service of the network. And it can be concluded that almost 60% of the user was happy with the
provided network design, 25 % found the network to be satisfactory while there was 15% user
who thought proper improvement must be done more enhanced network.
23
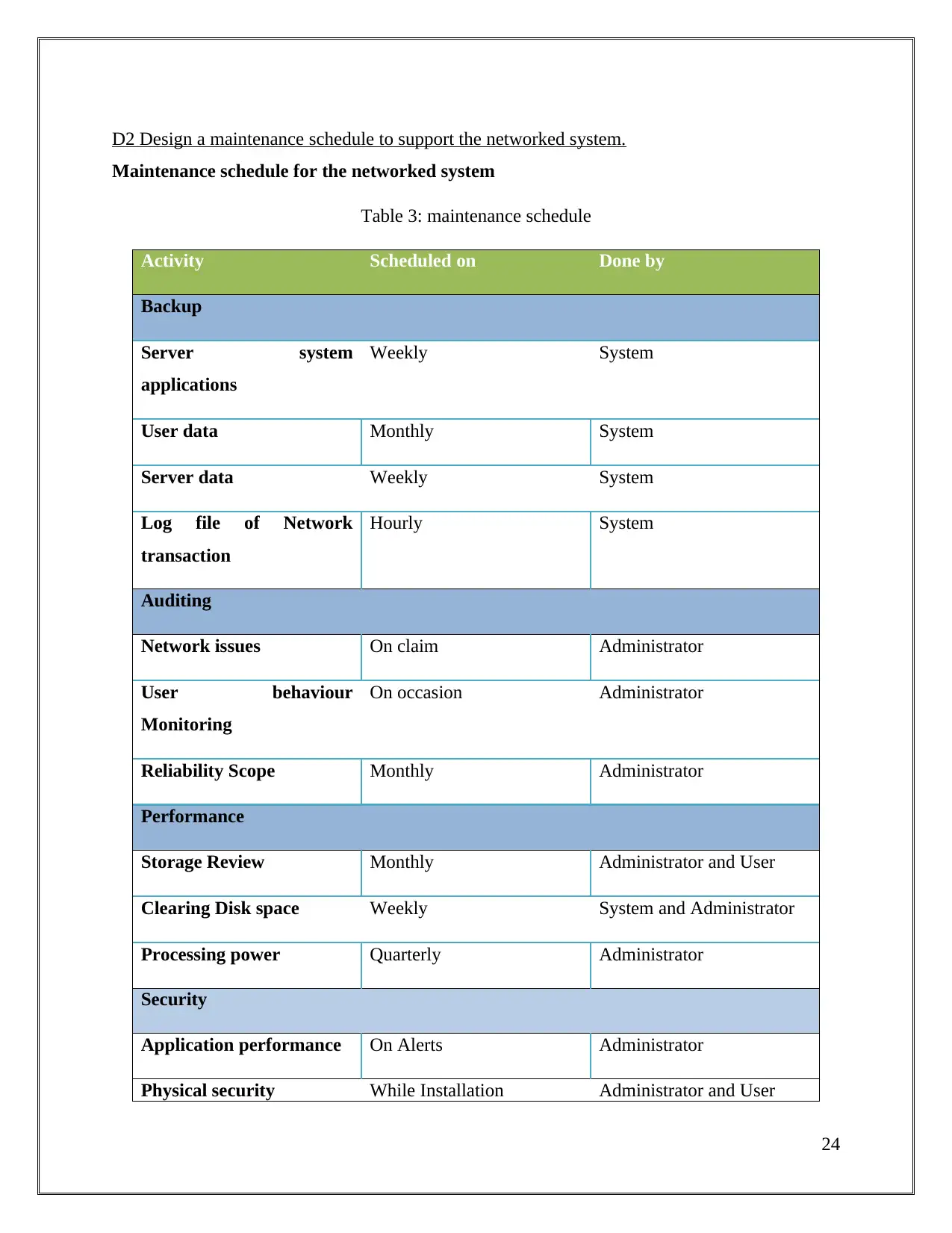
D2 Design a maintenance schedule to support the networked system.
Maintenance schedule for the networked system
Table 3: maintenance schedule
Activity Scheduled on Done by
Backup
Server system
applications
Weekly System
User data Monthly System
Server data Weekly System
Log file of Network
transaction
Hourly System
Auditing
Network issues On claim Administrator
User behaviour
Monitoring
On occasion Administrator
Reliability Scope Monthly Administrator
Performance
Storage Review Monthly Administrator and User
Clearing Disk space Weekly System and Administrator
Processing power Quarterly Administrator
Security
Application performance On Alerts Administrator
Physical security While Installation Administrator and User
24
Maintenance schedule for the networked system
Table 3: maintenance schedule
Activity Scheduled on Done by
Backup
Server system
applications
Weekly System
User data Monthly System
Server data Weekly System
Log file of Network
transaction
Hourly System
Auditing
Network issues On claim Administrator
User behaviour
Monitoring
On occasion Administrator
Reliability Scope Monthly Administrator
Performance
Storage Review Monthly Administrator and User
Clearing Disk space Weekly System and Administrator
Processing power Quarterly Administrator
Security
Application performance On Alerts Administrator
Physical security While Installation Administrator and User
24
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
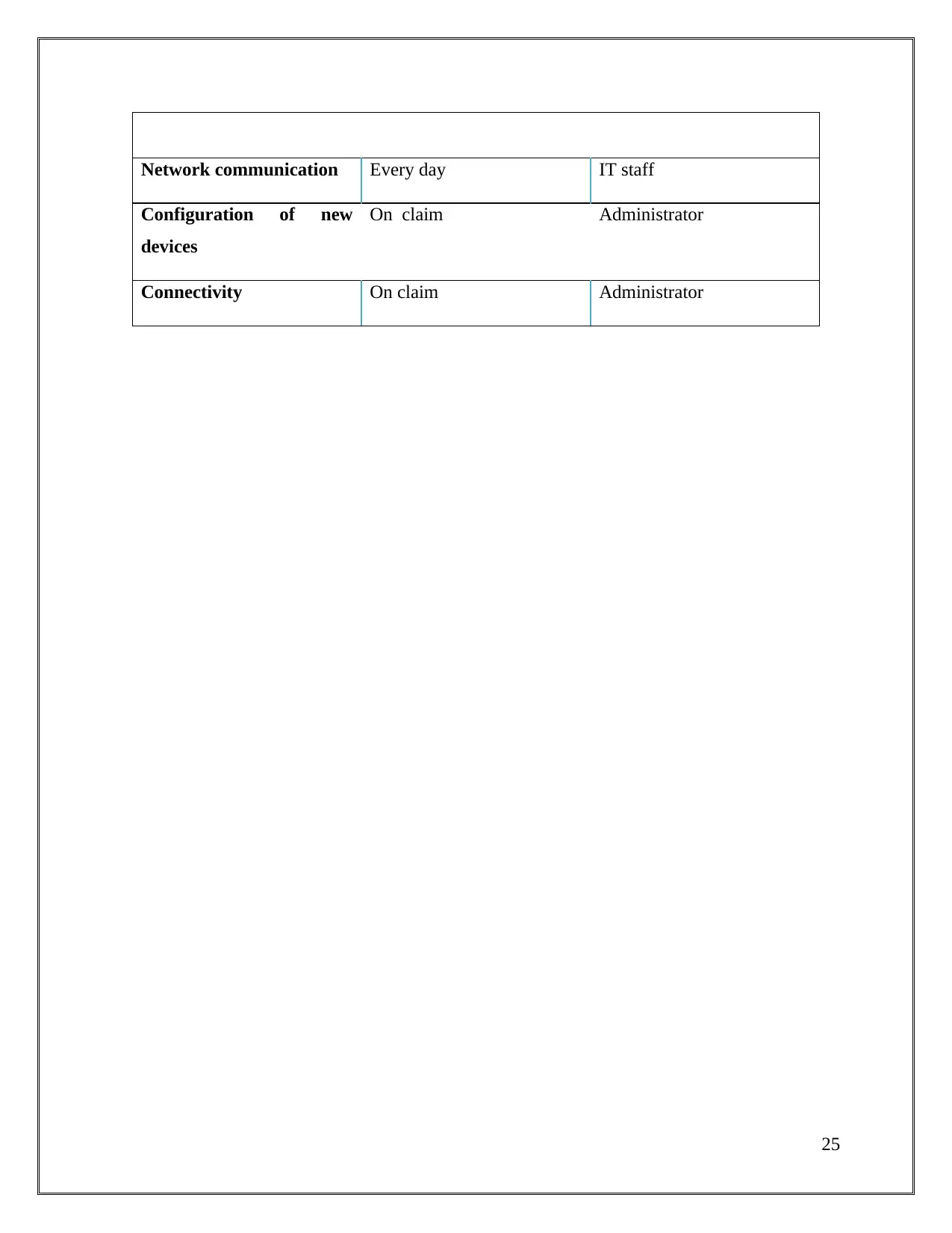
Network communication Every day IT staff
Configuration of new
devices
On claim Administrator
Connectivity On claim Administrator
25
Configuration of new
devices
On claim Administrator
Connectivity On claim Administrator
25
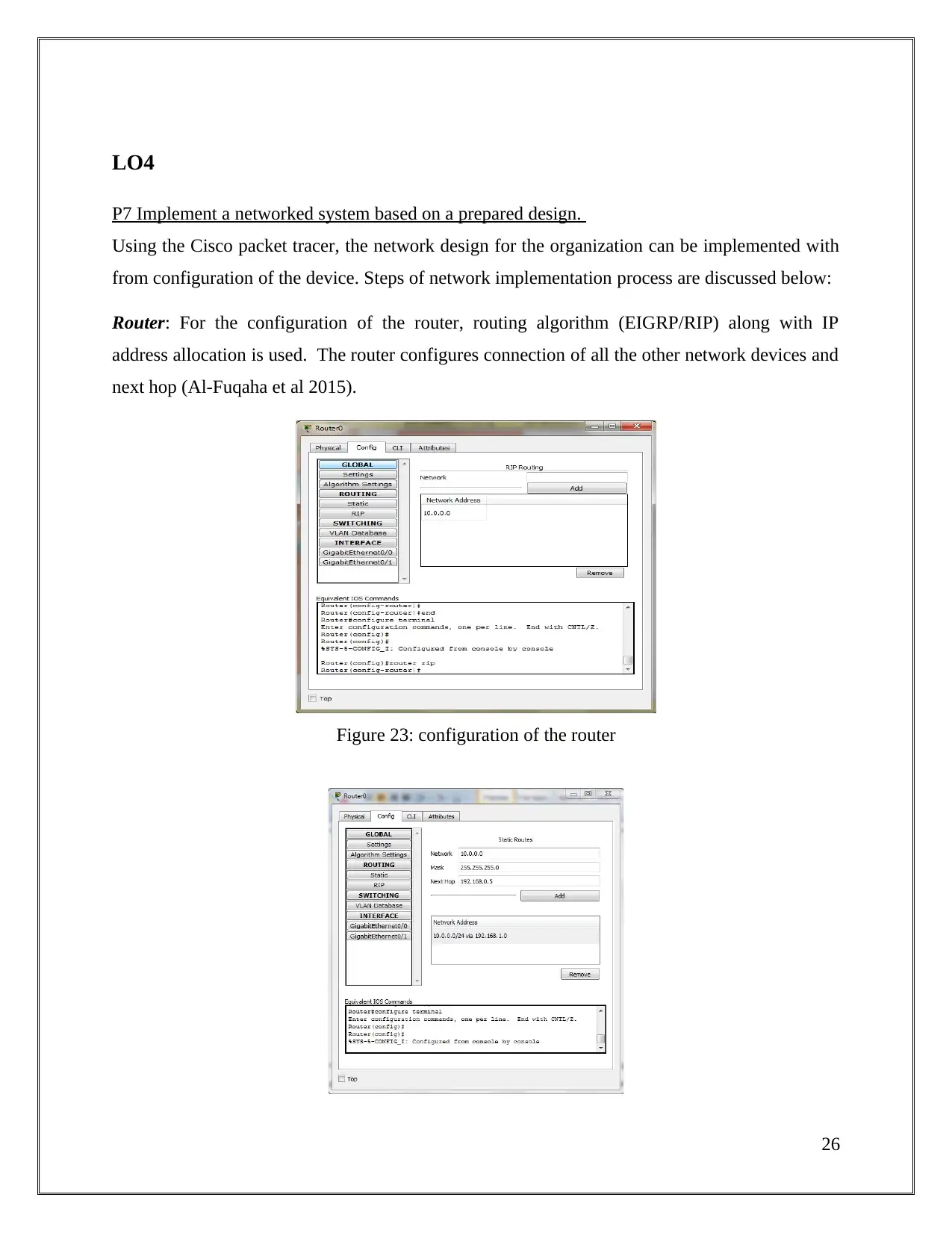
LO4
P7 Implement a networked system based on a prepared design.
Using the Cisco packet tracer, the network design for the organization can be implemented with
from configuration of the device. Steps of network implementation process are discussed below:
Router: For the configuration of the router, routing algorithm (EIGRP/RIP) along with IP
address allocation is used. The router configures connection of all the other network devices and
next hop (Al-Fuqaha et al 2015).
Figure 23: configuration of the router
26
P7 Implement a networked system based on a prepared design.
Using the Cisco packet tracer, the network design for the organization can be implemented with
from configuration of the device. Steps of network implementation process are discussed below:
Router: For the configuration of the router, routing algorithm (EIGRP/RIP) along with IP
address allocation is used. The router configures connection of all the other network devices and
next hop (Al-Fuqaha et al 2015).
Figure 23: configuration of the router
26

Figure 24: Configuration of routing algorithm
Switches: Switch is used for configuring other network devices and the Virtual local area
network for establishing communication among them. For Ethernet connections switches are
configured.
Figure 25: Configuration of Switch used in the network
Server: the network has 4 separate server, mail server, web server, file server and DNS server.
These servers in the network are configured for address pooling and IP address for connectivity.
Figure 26: Configuration of Server
27
Switches: Switch is used for configuring other network devices and the Virtual local area
network for establishing communication among them. For Ethernet connections switches are
configured.
Figure 25: Configuration of Switch used in the network
Server: the network has 4 separate server, mail server, web server, file server and DNS server.
These servers in the network are configured for address pooling and IP address for connectivity.
Figure 26: Configuration of Server
27
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
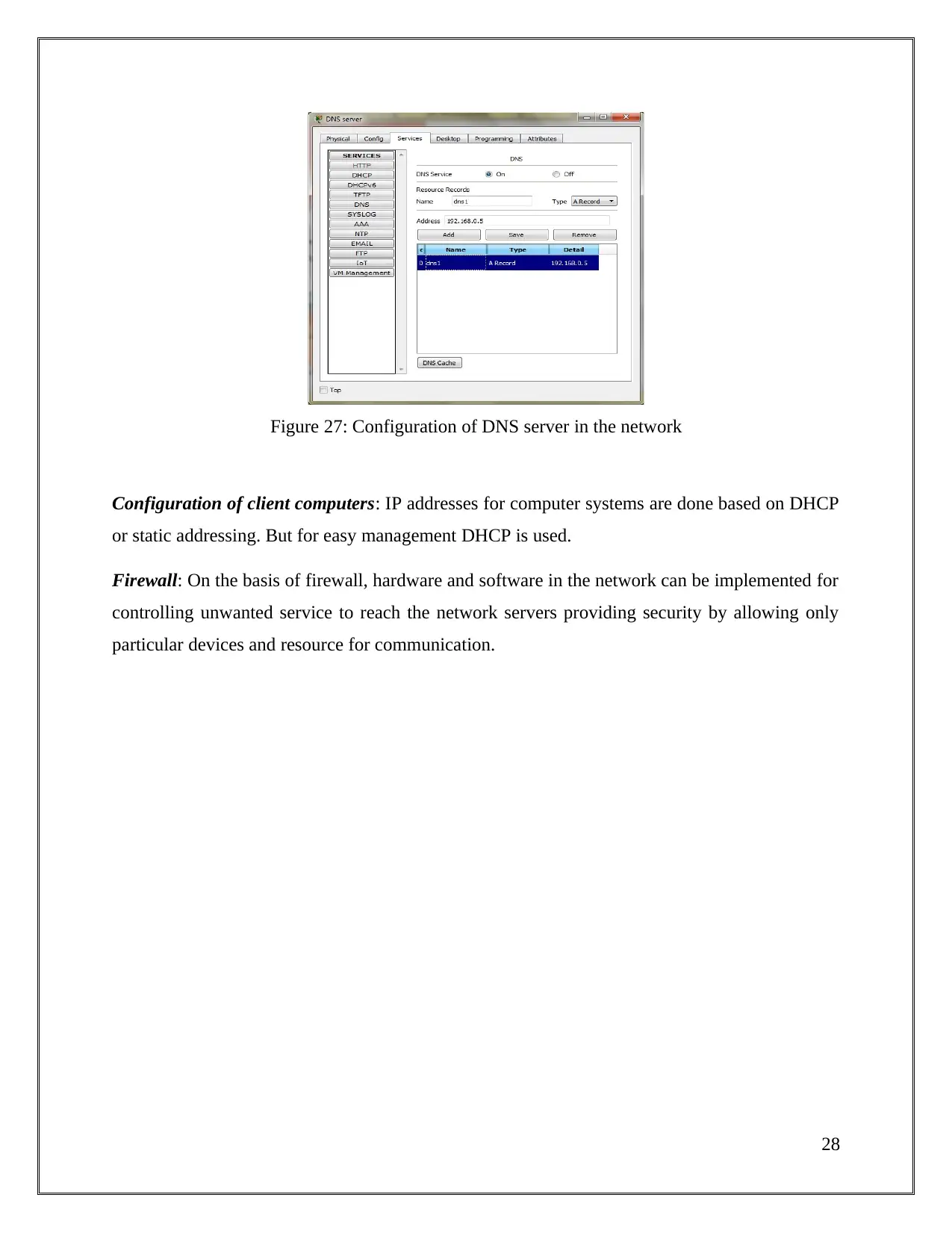
Figure 27: Configuration of DNS server in the network
Configuration of client computers: IP addresses for computer systems are done based on DHCP
or static addressing. But for easy management DHCP is used.
Firewall: On the basis of firewall, hardware and software in the network can be implemented for
controlling unwanted service to reach the network servers providing security by allowing only
particular devices and resource for communication.
28
Configuration of client computers: IP addresses for computer systems are done based on DHCP
or static addressing. But for easy management DHCP is used.
Firewall: On the basis of firewall, hardware and software in the network can be implemented for
controlling unwanted service to reach the network servers providing security by allowing only
particular devices and resource for communication.
28
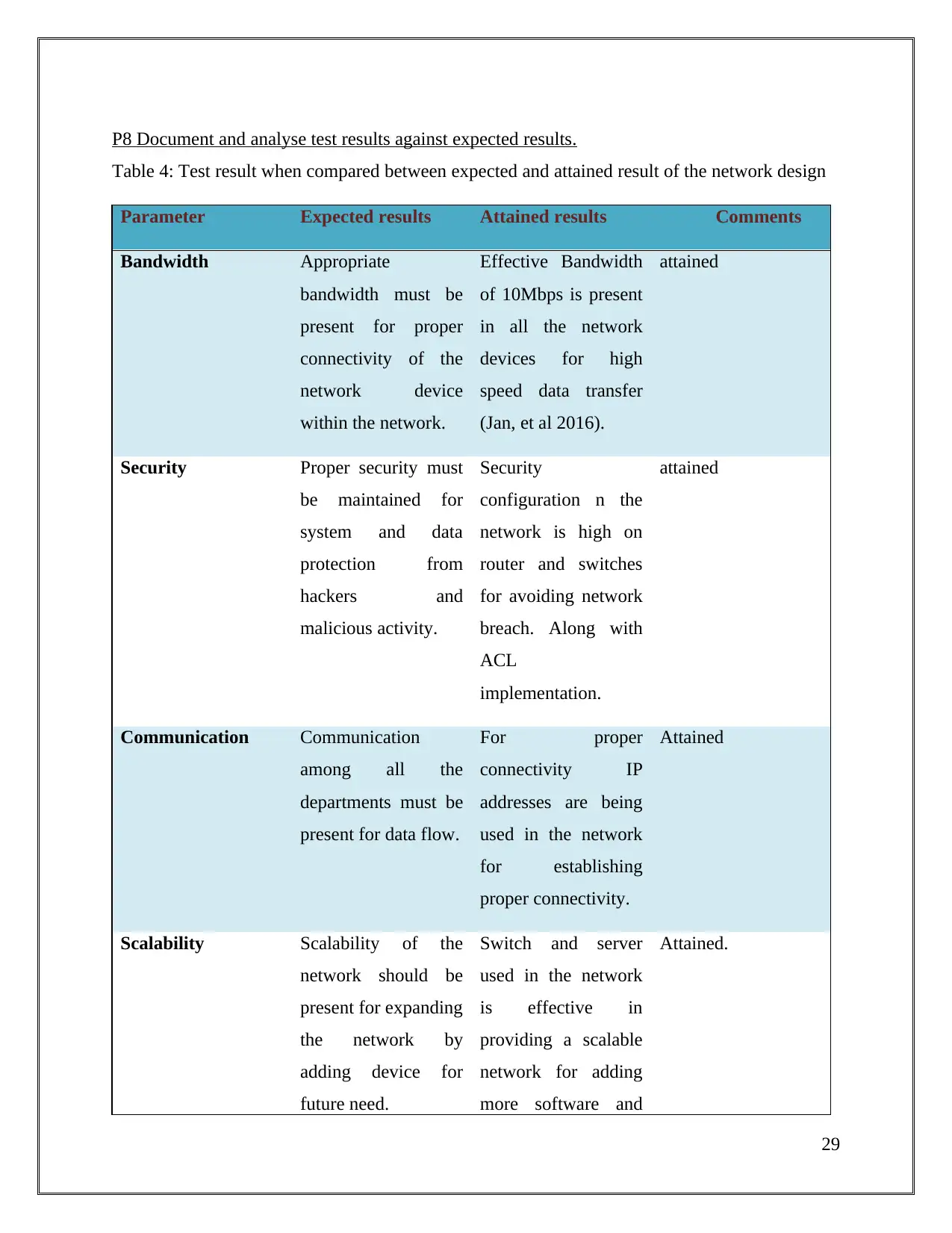
P8 Document and analyse test results against expected results.
Table 4: Test result when compared between expected and attained result of the network design
Parameter Expected results Attained results Comments
Bandwidth Appropriate
bandwidth must be
present for proper
connectivity of the
network device
within the network.
Effective Bandwidth
of 10Mbps is present
in all the network
devices for high
speed data transfer
(Jan, et al 2016).
attained
Security Proper security must
be maintained for
system and data
protection from
hackers and
malicious activity.
Security
configuration n the
network is high on
router and switches
for avoiding network
breach. Along with
ACL
implementation.
attained
Communication Communication
among all the
departments must be
present for data flow.
For proper
connectivity IP
addresses are being
used in the network
for establishing
proper connectivity.
Attained
Scalability Scalability of the
network should be
present for expanding
the network by
adding device for
future need.
Switch and server
used in the network
is effective in
providing a scalable
network for adding
more software and
Attained.
29
Table 4: Test result when compared between expected and attained result of the network design
Parameter Expected results Attained results Comments
Bandwidth Appropriate
bandwidth must be
present for proper
connectivity of the
network device
within the network.
Effective Bandwidth
of 10Mbps is present
in all the network
devices for high
speed data transfer
(Jan, et al 2016).
attained
Security Proper security must
be maintained for
system and data
protection from
hackers and
malicious activity.
Security
configuration n the
network is high on
router and switches
for avoiding network
breach. Along with
ACL
implementation.
attained
Communication Communication
among all the
departments must be
present for data flow.
For proper
connectivity IP
addresses are being
used in the network
for establishing
proper connectivity.
Attained
Scalability Scalability of the
network should be
present for expanding
the network by
adding device for
future need.
Switch and server
used in the network
is effective in
providing a scalable
network for adding
more software and
Attained.
29

hardware
devices(Robertazzi,
2012. ).
From the test results of the present network for the organisation it can be concluded that the
network hence implemented is effective in providing service as per demands and requirements of
the organization.
30
devices(Robertazzi,
2012. ).
From the test results of the present network for the organisation it can be concluded that the
network hence implemented is effective in providing service as per demands and requirements of
the organization.
30
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
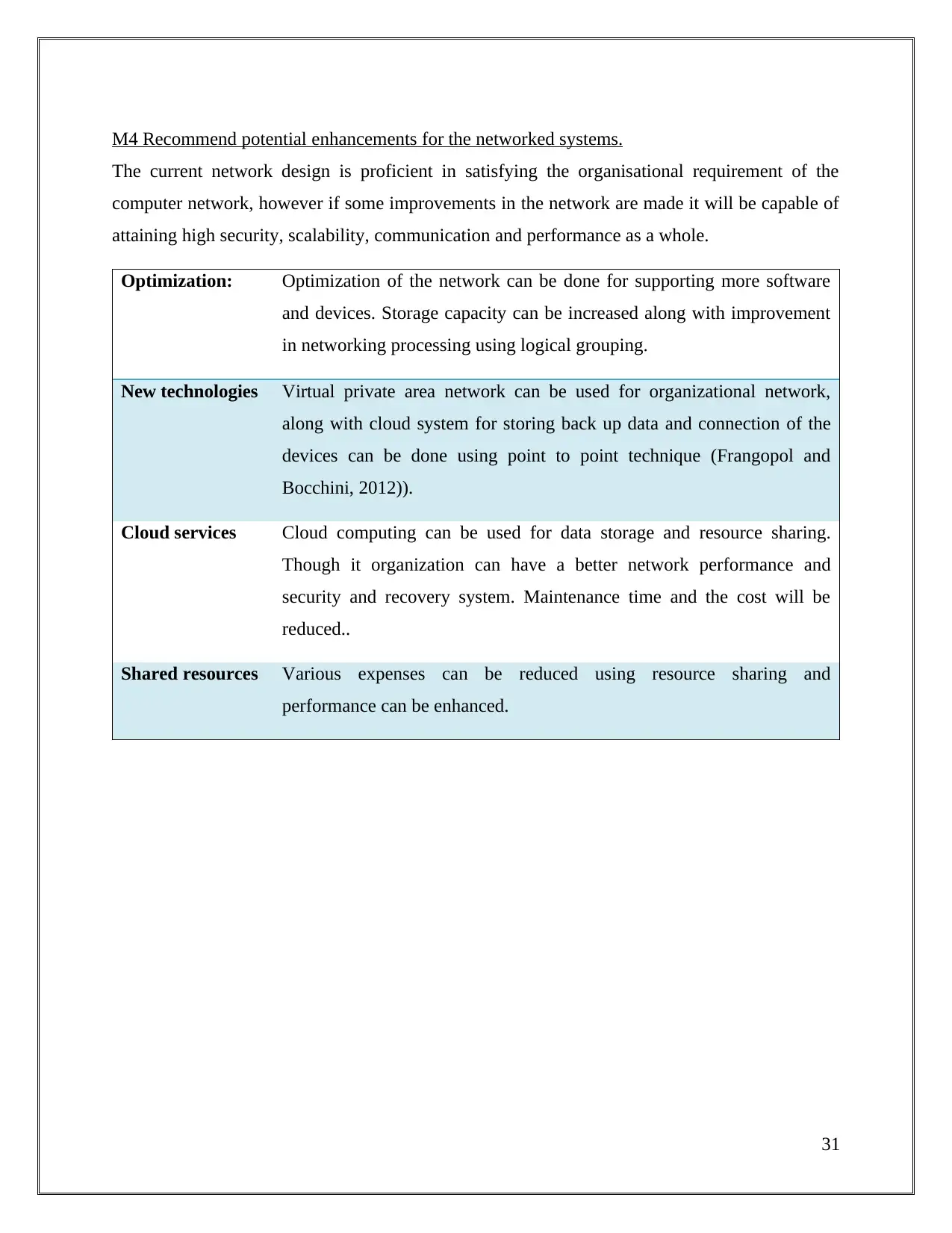
M4 Recommend potential enhancements for the networked systems.
The current network design is proficient in satisfying the organisational requirement of the
computer network, however if some improvements in the network are made it will be capable of
attaining high security, scalability, communication and performance as a whole.
Optimization: Optimization of the network can be done for supporting more software
and devices. Storage capacity can be increased along with improvement
in networking processing using logical grouping.
New technologies Virtual private area network can be used for organizational network,
along with cloud system for storing back up data and connection of the
devices can be done using point to point technique (Frangopol and
Bocchini, 2012)).
Cloud services Cloud computing can be used for data storage and resource sharing.
Though it organization can have a better network performance and
security and recovery system. Maintenance time and the cost will be
reduced..
Shared resources Various expenses can be reduced using resource sharing and
performance can be enhanced.
31
The current network design is proficient in satisfying the organisational requirement of the
computer network, however if some improvements in the network are made it will be capable of
attaining high security, scalability, communication and performance as a whole.
Optimization: Optimization of the network can be done for supporting more software
and devices. Storage capacity can be increased along with improvement
in networking processing using logical grouping.
New technologies Virtual private area network can be used for organizational network,
along with cloud system for storing back up data and connection of the
devices can be done using point to point technique (Frangopol and
Bocchini, 2012)).
Cloud services Cloud computing can be used for data storage and resource sharing.
Though it organization can have a better network performance and
security and recovery system. Maintenance time and the cost will be
reduced..
Shared resources Various expenses can be reduced using resource sharing and
performance can be enhanced.
31

D3 Use critical reflection to evaluate own work and justify valid conclusions.
From the provided design for the organizational network and its implementation is found to be
effectual for delivering adequate connectivity of devices. All the demands and requirement of the
organization was achieved efficiently offering high performance and security of equipment and
data flowing in the network (Holzhauser, 2017). The organizational network is implemented
using proper cables and appropriate and updated hardware and software components so that
required connectivity can be attained along with security and reliability. Ping commands have
been used for checking connectivity of the network device, and their result makes it clear that the
achieved network is as per the required of the organization.
32
From the provided design for the organizational network and its implementation is found to be
effectual for delivering adequate connectivity of devices. All the demands and requirement of the
organization was achieved efficiently offering high performance and security of equipment and
data flowing in the network (Holzhauser, 2017). The organizational network is implemented
using proper cables and appropriate and updated hardware and software components so that
required connectivity can be attained along with security and reliability. Ping commands have
been used for checking connectivity of the network device, and their result makes it clear that the
achieved network is as per the required of the organization.
32

Conclusion
Fundamentals of networking system have been discussed in the above report. Network types,
systems, topologies, protocols along with hardware system have been studied. Interdependency
and functionality of different network components are discussed. A network designed with the
help of Cisco Packet Tracer has been developed and implemented for ‘sys-go.co.uk’ that uses
LAN network for connecting all the devices in the network. The Networks is then tested for its
communication and performance. In tabulation form results of the network is compared
considering the expected result. At last the report provided with improvement scope for the
network for future demand along with maintenance schedule.
33
Fundamentals of networking system have been discussed in the above report. Network types,
systems, topologies, protocols along with hardware system have been studied. Interdependency
and functionality of different network components are discussed. A network designed with the
help of Cisco Packet Tracer has been developed and implemented for ‘sys-go.co.uk’ that uses
LAN network for connecting all the devices in the network. The Networks is then tested for its
communication and performance. In tabulation form results of the network is compared
considering the expected result. At last the report provided with improvement scope for the
network for future demand along with maintenance schedule.
33
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Books and Journals
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M. and Ayyash, M., 2015. Internet of
things: A survey on enabling technologies, protocols, and applications. IEEE Communications
Surveys & Tutorials, 17(4), pp.2347-2376.
Bhushan, N., Li, J., Malladi, D., Gilmore, R., Brenner, D., Damnjanovic, A., Sukhavasi, R.,
Patel, C. and Geirhofer, S., 2014. Network densification: the dominant theme for wireless
evolution into 5G. IEEE Communications Magazine, 52(2), pp.82-89.
Bonald, T. and Feuillet, M., 2013. Network performance analysis. John Wiley & Sons.
Comer, D., 2015. Computer networks and internets. Pearson.
Fisher, R., Ledwaba, L., Hancke, G. and Kruger, C., 2015. Open hardware: A role to play in
wireless sensor networks?. Sensors, 15(3), pp.6818-6844.
Frangopol, D.M. and Bocchini, P., 2012. Bridge network performance, maintenance and
optimisation under uncertainty: accomplishments and challenges. Structure and Infrastructure
Engineering, 8(4), pp.341-356.
Hakansson, H. ed., 2015. Industrial Technological Development (Routledge Revivals): A
Network Approach. Routledge.
Holzhauser, M., 2017. Generalized Network Improvement and Packing Problems. Springer.
Jan, S.R., Shah, S.T.U., Johar, Z.U., Shah, Y. and Khan, F., 2016. An Innovative Approach to
Investigate Various Software Testing Techniques and Strategies. International Journal of
Scientific Research in Science, Engineering and Technology (IJSRSET), Print ISSN, pp.2395-
1990.
Niephaus, C., Aliu, O.G., Kretschmer, M., Hadzic, S. and Ghinea, G., 2015. Wireless Back-haul:
a software defined network enabled wireless Back-haul network architecture for future 5G
networks. IET Networks, 4(6), pp.287-295.
34
Books and Journals
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M. and Ayyash, M., 2015. Internet of
things: A survey on enabling technologies, protocols, and applications. IEEE Communications
Surveys & Tutorials, 17(4), pp.2347-2376.
Bhushan, N., Li, J., Malladi, D., Gilmore, R., Brenner, D., Damnjanovic, A., Sukhavasi, R.,
Patel, C. and Geirhofer, S., 2014. Network densification: the dominant theme for wireless
evolution into 5G. IEEE Communications Magazine, 52(2), pp.82-89.
Bonald, T. and Feuillet, M., 2013. Network performance analysis. John Wiley & Sons.
Comer, D., 2015. Computer networks and internets. Pearson.
Fisher, R., Ledwaba, L., Hancke, G. and Kruger, C., 2015. Open hardware: A role to play in
wireless sensor networks?. Sensors, 15(3), pp.6818-6844.
Frangopol, D.M. and Bocchini, P., 2012. Bridge network performance, maintenance and
optimisation under uncertainty: accomplishments and challenges. Structure and Infrastructure
Engineering, 8(4), pp.341-356.
Hakansson, H. ed., 2015. Industrial Technological Development (Routledge Revivals): A
Network Approach. Routledge.
Holzhauser, M., 2017. Generalized Network Improvement and Packing Problems. Springer.
Jan, S.R., Shah, S.T.U., Johar, Z.U., Shah, Y. and Khan, F., 2016. An Innovative Approach to
Investigate Various Software Testing Techniques and Strategies. International Journal of
Scientific Research in Science, Engineering and Technology (IJSRSET), Print ISSN, pp.2395-
1990.
Niephaus, C., Aliu, O.G., Kretschmer, M., Hadzic, S. and Ghinea, G., 2015. Wireless Back-haul:
a software defined network enabled wireless Back-haul network architecture for future 5G
networks. IET Networks, 4(6), pp.287-295.
34

Robertazzi, T.G., 2012. Computer networks and systems: queueing theory and performance
evaluation. Springer Science & Business Media.
Sadiku, M.N., 2017. Simulation of Local Area Networks: 0. CRC Press.
Zhang, L., Afanasyev, A., Burke, J., Jacobson, V., Crowley, P., Papadopoulos, C., Wang, L. and
Zhang, B., 2014. Named data networking. ACM SIGCOMM Computer Communication
Review, 44(3), pp.66-73.
Online references
Network technologies, 2018 [Online][Accessed
Through]<http://www.cs.virginia.edu/~jorg/teaching/cs457/slides/Example-networks.pdf>
[Accessed On: 23rd April 2018]
Network principles, 2018 [Online][Accessed
Through]https://www.gov.uk/government/publications/network-principles/network-principles
[Accessed On: 23rd April 2018]
Computer Server, 2018 [Online][Accessed Through https://www.lifewire.com/servers-in-
computer-networking-817380 [Accessed On: 23rd April 2018]
35
evaluation. Springer Science & Business Media.
Sadiku, M.N., 2017. Simulation of Local Area Networks: 0. CRC Press.
Zhang, L., Afanasyev, A., Burke, J., Jacobson, V., Crowley, P., Papadopoulos, C., Wang, L. and
Zhang, B., 2014. Named data networking. ACM SIGCOMM Computer Communication
Review, 44(3), pp.66-73.
Online references
Network technologies, 2018 [Online][Accessed
Through]<http://www.cs.virginia.edu/~jorg/teaching/cs457/slides/Example-networks.pdf>
[Accessed On: 23rd April 2018]
Network principles, 2018 [Online][Accessed
Through]https://www.gov.uk/government/publications/network-principles/network-principles
[Accessed On: 23rd April 2018]
Computer Server, 2018 [Online][Accessed Through https://www.lifewire.com/servers-in-
computer-networking-817380 [Accessed On: 23rd April 2018]
35
1 out of 39
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





