Secure Wireless Network Implementation
VerifiedAdded on 2020/04/07
|14
|1542
|380
AI Summary
This assignment focuses on configuring a secure wireless network environment using WPA2-PSK encryption, RADIUS authentication, and certificate-based logins. It outlines the steps involved in setting up a Network Policy Server (NPS) on a Windows Server 2012R2 machine, configuring access points as RADIUS clients, and establishing client configuration on Windows 7 machines. The assignment emphasizes best practices for securing wireless networks and provides a comprehensive guide to implementing these security measures.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Table of Contents
1. Introduction................................................................................................................................1
Lab 4-Worksheet................................................................................................................................2
Software....................................................................................................................................11
2. Conclusion.................................................................................................................................14
References.........................................................................................................................................15
1
1. Introduction................................................................................................................................1
Lab 4-Worksheet................................................................................................................................2
Software....................................................................................................................................11
2. Conclusion.................................................................................................................................14
References.........................................................................................................................................15
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1. Introduction
The WPA2-PSK will be studied along with the WPA4-way handshake. The brute force
password crack will be used to extract the passphrase. The wireless network traffic will be
collected to find out the WEP key. For doing this action, some software and hardware tools are
required. By using the SSID, the AP WEP configuration will be performed. AP is an access
point. To connect wired LAN into wireless device, AP is used as a hub. It provides secure
connection. The MAC addresses of wireless network will be monitored. For providing the gain
address to the AP, MAC addresses will be predicted. MAC stands for Media Access Control. It
is a unique identifier. It is used for making the communication at the data link layer. The
Microsoft windows 2012 server will be installed. It will perform the authentication in active
directory domain. The client and server configuration of will be done in windows 2012 server
using some software and hardware. To carry out the MAC, address spoofing, WEP and WPA2
encryption, implementation is carried out in Kali Linux. Kali Linux is chosen to carry out the
process since it is easy for handling the encryption and recording, capturing and storing the
traffic. Kali Linux is one of the Linux platform derived based on Debian. Kali Linux is used for
penetration testing. Kali Linux has its host applications like back track, wire shark. Kali Linux
can be easily installed via bootable CD OR DVD. Kali Linux is mostly used for carrying out
forensic activities. Kali Linux has many tools. Some of the tools are wire shark, kismet, Maitego,
Ettercap and many. Kali Linux is also used for Ethical hacking techniques.
Lab 4-Worksheet
Certificate authority is nothing but the one which provides a digital certificate. The digital
certificate can be used to bind an entity’s key cryptographically. The certificate authority is the
one which determines the access of the document or the software or the network by other. The
web browsers are mostly programmed with certificate authorities and providing SSL certificate
comes under the duty of the certificate authority.NPS is the abbreviation of the Network Policy
Server.NPS comes under the role of RADIUS server. RADUS is the abbreviation of Remote
Authentication Dial-in User Service. It is almost similar to that of the IAS service.NPS server
allows you to create wide network access policies. RADIUS server manages three important
roles. The roles are accounting, authentication and authorization.
2
The WPA2-PSK will be studied along with the WPA4-way handshake. The brute force
password crack will be used to extract the passphrase. The wireless network traffic will be
collected to find out the WEP key. For doing this action, some software and hardware tools are
required. By using the SSID, the AP WEP configuration will be performed. AP is an access
point. To connect wired LAN into wireless device, AP is used as a hub. It provides secure
connection. The MAC addresses of wireless network will be monitored. For providing the gain
address to the AP, MAC addresses will be predicted. MAC stands for Media Access Control. It
is a unique identifier. It is used for making the communication at the data link layer. The
Microsoft windows 2012 server will be installed. It will perform the authentication in active
directory domain. The client and server configuration of will be done in windows 2012 server
using some software and hardware. To carry out the MAC, address spoofing, WEP and WPA2
encryption, implementation is carried out in Kali Linux. Kali Linux is chosen to carry out the
process since it is easy for handling the encryption and recording, capturing and storing the
traffic. Kali Linux is one of the Linux platform derived based on Debian. Kali Linux is used for
penetration testing. Kali Linux has its host applications like back track, wire shark. Kali Linux
can be easily installed via bootable CD OR DVD. Kali Linux is mostly used for carrying out
forensic activities. Kali Linux has many tools. Some of the tools are wire shark, kismet, Maitego,
Ettercap and many. Kali Linux is also used for Ethical hacking techniques.
Lab 4-Worksheet
Certificate authority is nothing but the one which provides a digital certificate. The digital
certificate can be used to bind an entity’s key cryptographically. The certificate authority is the
one which determines the access of the document or the software or the network by other. The
web browsers are mostly programmed with certificate authorities and providing SSL certificate
comes under the duty of the certificate authority.NPS is the abbreviation of the Network Policy
Server.NPS comes under the role of RADIUS server. RADUS is the abbreviation of Remote
Authentication Dial-in User Service. It is almost similar to that of the IAS service.NPS server
allows you to create wide network access policies. RADIUS server manages three important
roles. The roles are accounting, authentication and authorization.
2

Objective
This activity will cover installing and configuring MS Windows 2012 Server as a
Certificate Authority and Radius Server, which will authenticate wireless clients in an
MS Active Directory Domain.
Hardware
Computers with recommended hardware for 1 x Windows Server 2012R2 x64 and 1 x
Windows 7 (using virtualization)
1 x Wireless USB adapter installed to 7 Client
1 x AP capable of configuring WPA / WPA2 Enterprise (RADIUS)
Software
MS Windows Server 2012R2
VM Ware Image: Windows Server 2012R2
MS Windows 7
Server configuration
This solution has been designed and tested using the following Active Directory configuration:
A single-domain Active Directory forest.
A domain functional level of Windows Server 2012 mode is used.
Configure the Windows 2012 server with the following:
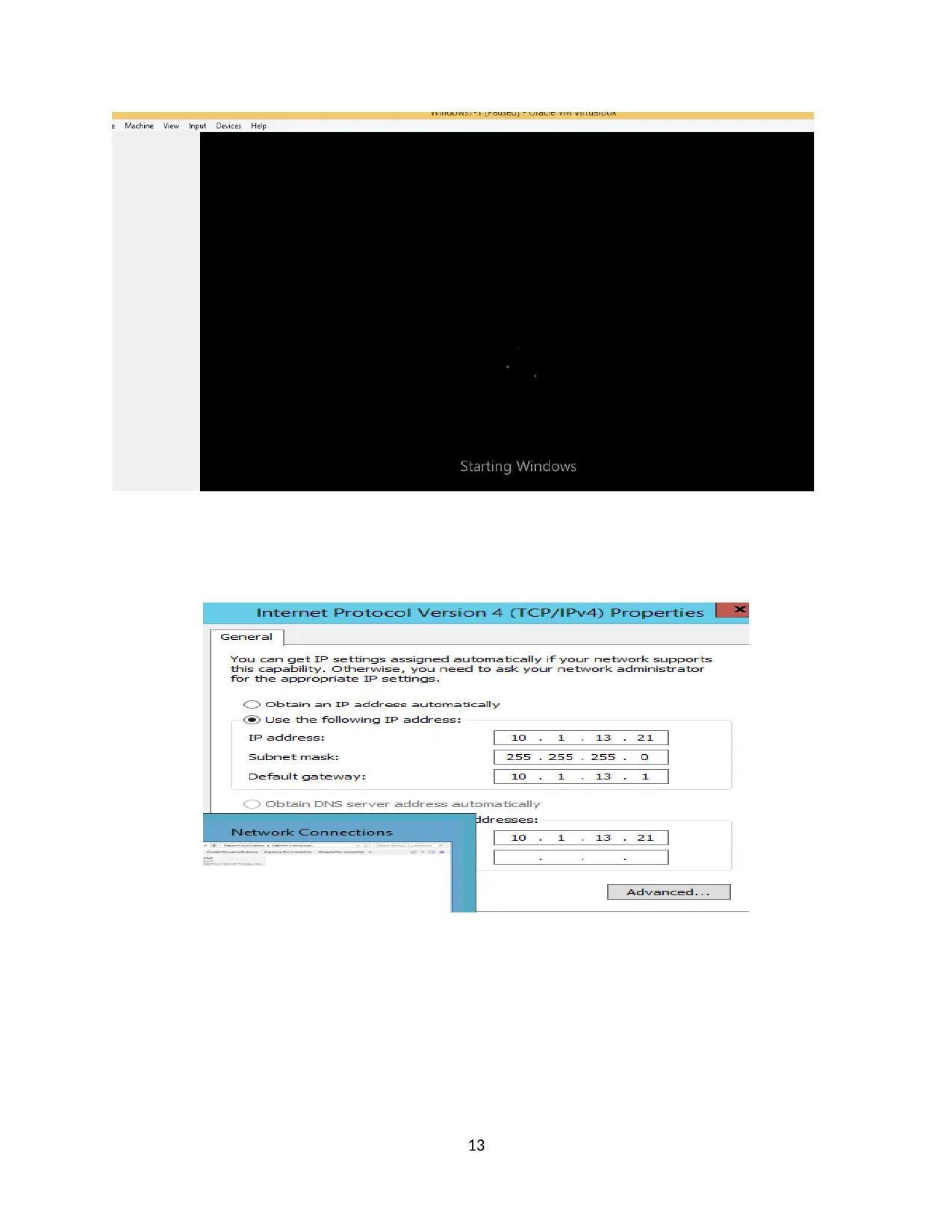
IP address: 10.1.x.21 (where x is the number given to you)
Subnet Mask:255.255.255.0
Gateway: 10.1.x.1
DNS: 10.1.x.21
Disable Netbios over TCP/IP under the Advanced > WINS tab
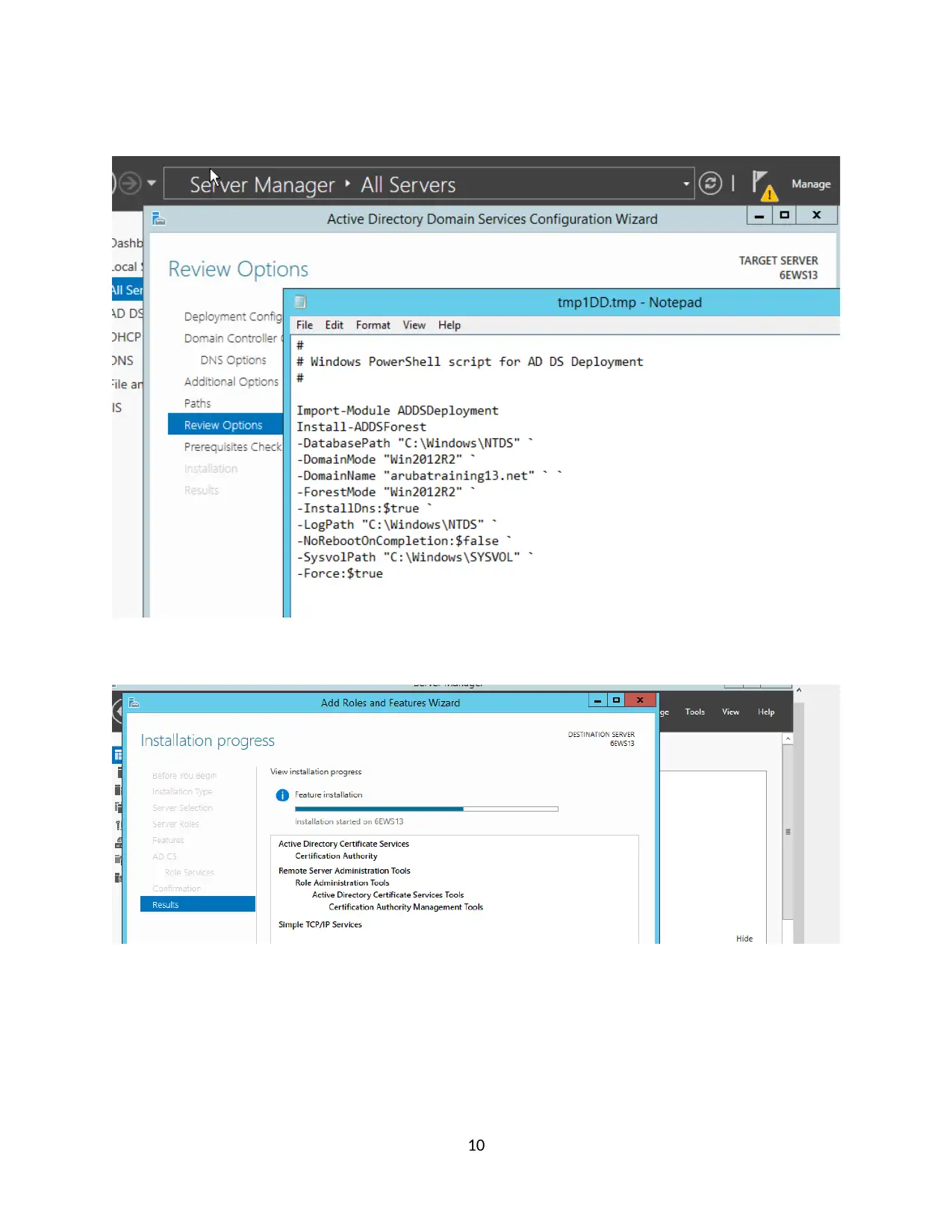
Configure the Windows 2012 Server as a Domain Controller
Use the domain name of arubatrainingX.net.
Raise the domain functional level to Windows Server 2012mode.
Client configuration
3
This activity will cover installing and configuring MS Windows 2012 Server as a
Certificate Authority and Radius Server, which will authenticate wireless clients in an
MS Active Directory Domain.
Hardware
Computers with recommended hardware for 1 x Windows Server 2012R2 x64 and 1 x
Windows 7 (using virtualization)
1 x Wireless USB adapter installed to 7 Client
1 x AP capable of configuring WPA / WPA2 Enterprise (RADIUS)
Software
MS Windows Server 2012R2
VM Ware Image: Windows Server 2012R2
MS Windows 7
Server configuration
This solution has been designed and tested using the following Active Directory configuration:
A single-domain Active Directory forest.
A domain functional level of Windows Server 2012 mode is used.
Configure the Windows 2012 server with the following:
IP address: 10.1.x.21 (where x is the number given to you)
Subnet Mask:255.255.255.0
Gateway: 10.1.x.1
DNS: 10.1.x.21
Disable Netbios over TCP/IP under the Advanced > WINS tab
Configure the Windows 2012 Server as a Domain Controller
Use the domain name of arubatrainingX.net.
Raise the domain functional level to Windows Server 2012mode.
Client configuration
3

Configure your Windows 7 Client (Wireless adapter) with the following:
IP address:10.1.x.101(where x is the number given to you)
Subnet Mask:255.255.255.0
Gateway: 10.1.x.1
DNS: 10.1.x.21
Configure your Windows 7 Client (Ethernet adapter) with the following; (make
sure you have installed your wireless adapter before changing your Ethernet IP
address)
IP address: 10.1.x.102(where x is the number given to you)
Subnet Mask:255.255.255.0
Gateway: 10.1.x.1
DNS: 10.1.x.21
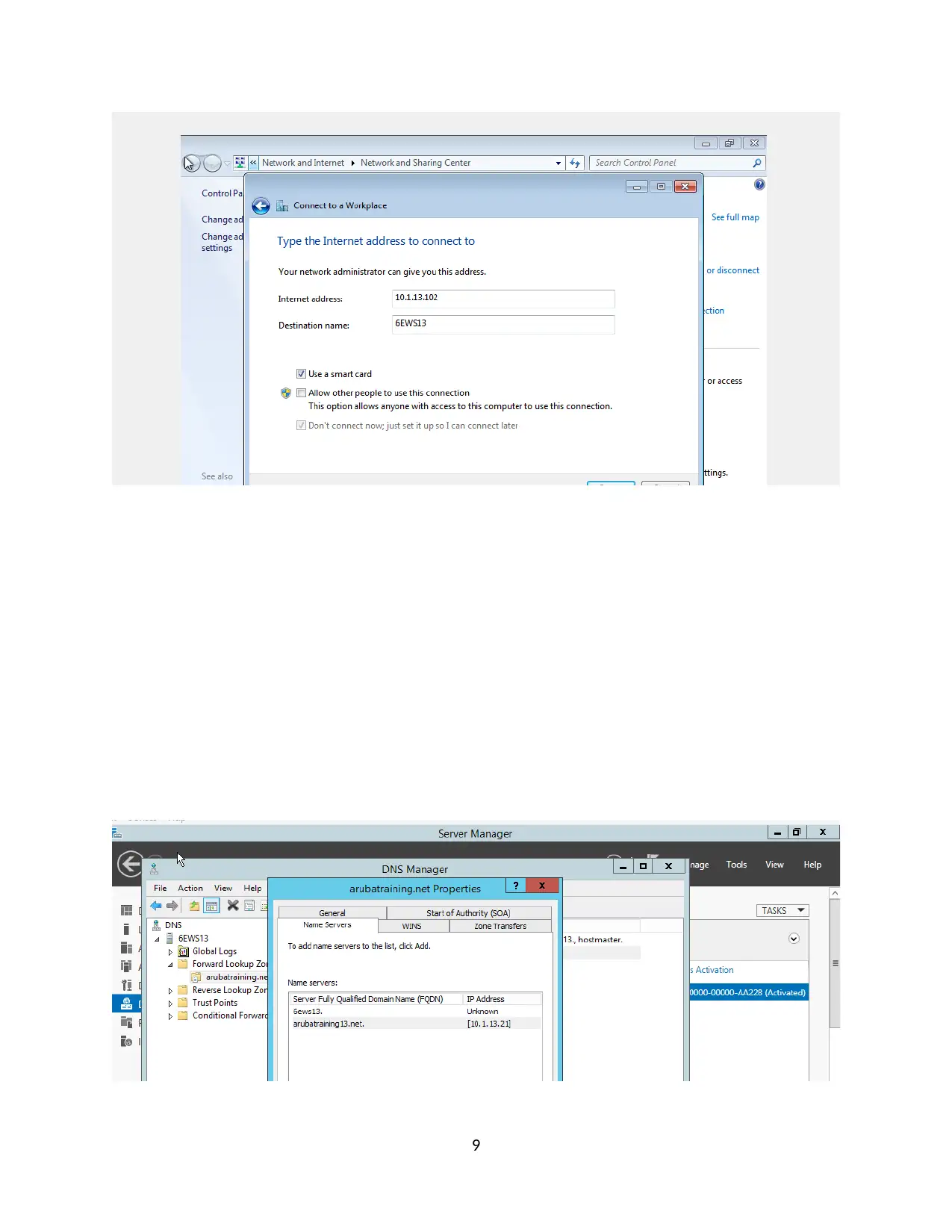
Join your client to the domain arubatrainingX.net
Install your USB Wireless adapter with drivers only.(Use Network and Sharing
Centre)
Creating users and groups
Create a user called Wireless, passwordPassword1
Create the groups from the tablebelow
The following groups are created
1. wireless LAN users
2. Wireless LAN computers
3. Wireless LAN access
4. Wireles LAN Computer Settings
Configuring the certificate
Install the Active Directory Certificate Services role
At the Role Services screen choose Certificate Authority.
Select Enterprise CA and make it a Root CA
Create a New Private Key
4
IP address:10.1.x.101(where x is the number given to you)
Subnet Mask:255.255.255.0
Gateway: 10.1.x.1
DNS: 10.1.x.21
Configure your Windows 7 Client (Ethernet adapter) with the following; (make
sure you have installed your wireless adapter before changing your Ethernet IP
address)
IP address: 10.1.x.102(where x is the number given to you)
Subnet Mask:255.255.255.0
Gateway: 10.1.x.1
DNS: 10.1.x.21
Join your client to the domain arubatrainingX.net
Install your USB Wireless adapter with drivers only.(Use Network and Sharing
Centre)
Creating users and groups
Create a user called Wireless, passwordPassword1
Create the groups from the tablebelow
The following groups are created
1. wireless LAN users
2. Wireless LAN computers
3. Wireless LAN access
4. Wireles LAN Computer Settings
Configuring the certificate
Install the Active Directory Certificate Services role
At the Role Services screen choose Certificate Authority.
Select Enterprise CA and make it a Root CA
Create a New Private Key
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CA Name =ArubaTrainingX-CA
NPS installation
On Server1, in the Server Manager list pane, right-click Roles, and then click Add
Roles.
Install the Network Policy Server role service from the Network Policy and
Access Services role.
On the Installation Results page, verify that Installation succeeded appears in the
details pane, and then click Close.
The Network Policy Server role is installed on Server1.
Do not log off or shut down Server1 at this point.
Open Network Policy Server from the Administrative Tools menu.
Using the NPS tool, register NPS in Active Directory.
The Network Policy server now is registered in Active DirectoryIn the Network
Policy Server management tool list pane, click NPS (Local).
In the details pane under Standard Configuration, click RADIUS server for802.1X
Wireless or Wired Connections
Under click RADIUS server for 802.1X Wireless or Wired Connections, click
Configure 802.1X, specify Secure Wireless Connections and accept the default
name.
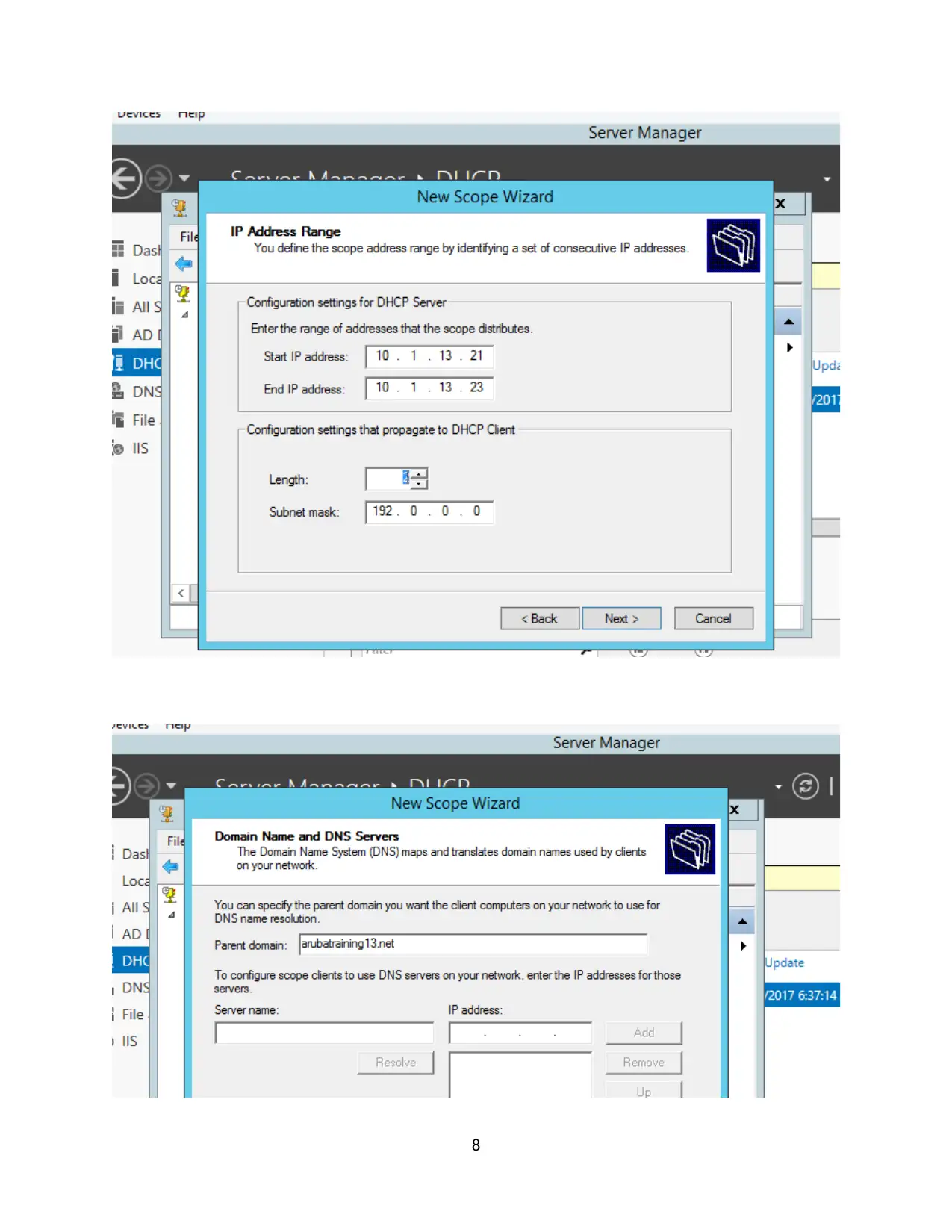
In the RADIUS clients dialog box, add your Wireless AP as a RADIUS client
with address of 10.1.x.254.
In the Shared Secret dialog box, select Manual and specify and confirm the shared
secret no of Password1 and then click OK and Next.
In the Configure Authentication Methods dialog box, select Microsoft: Protected
EAP (PEAP) click Configure, confirm the Certificate has been issued and click
OK and Next.
On the Specify User Groups page, add the group Wireless LAN Access and click
Next.
On the Configure Traffic Controls page, accept the default settings.
5
NPS installation
On Server1, in the Server Manager list pane, right-click Roles, and then click Add
Roles.
Install the Network Policy Server role service from the Network Policy and
Access Services role.
On the Installation Results page, verify that Installation succeeded appears in the
details pane, and then click Close.
The Network Policy Server role is installed on Server1.
Do not log off or shut down Server1 at this point.
Open Network Policy Server from the Administrative Tools menu.
Using the NPS tool, register NPS in Active Directory.
The Network Policy server now is registered in Active DirectoryIn the Network
Policy Server management tool list pane, click NPS (Local).
In the details pane under Standard Configuration, click RADIUS server for802.1X
Wireless or Wired Connections
Under click RADIUS server for 802.1X Wireless or Wired Connections, click
Configure 802.1X, specify Secure Wireless Connections and accept the default
name.
In the RADIUS clients dialog box, add your Wireless AP as a RADIUS client
with address of 10.1.x.254.
In the Shared Secret dialog box, select Manual and specify and confirm the shared
secret no of Password1 and then click OK and Next.
In the Configure Authentication Methods dialog box, select Microsoft: Protected
EAP (PEAP) click Configure, confirm the Certificate has been issued and click
OK and Next.
On the Specify User Groups page, add the group Wireless LAN Access and click
Next.
On the Configure Traffic Controls page, accept the default settings.
5

Finish the wizard.
Close the Network Policy Server administrative tool.
Ensure the Administrator, wireless user accounts are members of the Wireless
LAN Access group.
Ensure the PC you are logging in from is part of the Wireless LAN Access group
Configuration of a radius client
Configure the Access Point as a RADIUS Client
Configure W7Client1as an enterprise Wireless LAN Client
Aiding the certificate authentication by the modification of Radius network
In the Network Policy Server management tool list pane, click NPS (Local) –
Policies - Network Policy
Right-Click Secure Wireless Connections.
From the Constraints tab under Configure Authentication Methods dialog box,
select Microsoft: Protected EAP (PEAP) click Configure, confirm the Certificate
has been issued and click OK and Next.
Now change the authentication method from Password to Smart of other
certificate by clicking the Add button and choosing the Certificates… option –
then click OK make sure that certificates is at the top.
Close the Network Policy Server administrative tool
Configuration of W7client
Open Network and Sharing Centre
Click on Manage wireless networks
Modify the existing wireless network profile.
Click on Change connection settings.
Click the Security tab
6
Close the Network Policy Server administrative tool.
Ensure the Administrator, wireless user accounts are members of the Wireless
LAN Access group.
Ensure the PC you are logging in from is part of the Wireless LAN Access group
Configuration of a radius client
Configure the Access Point as a RADIUS Client
Configure W7Client1as an enterprise Wireless LAN Client
Aiding the certificate authentication by the modification of Radius network
In the Network Policy Server management tool list pane, click NPS (Local) –
Policies - Network Policy
Right-Click Secure Wireless Connections.
From the Constraints tab under Configure Authentication Methods dialog box,
select Microsoft: Protected EAP (PEAP) click Configure, confirm the Certificate
has been issued and click OK and Next.
Now change the authentication method from Password to Smart of other
certificate by clicking the Add button and choosing the Certificates… option –
then click OK make sure that certificates is at the top.
Close the Network Policy Server administrative tool
Configuration of W7client
Open Network and Sharing Centre
Click on Manage wireless networks
Modify the existing wireless network profile.
Click on Change connection settings.
Click the Security tab
6

Confirm that the network authentication method is set to Microsoft: Smart card
or other certificates
If you have successfully connected, disable the Local Area Connection and reboot
your computer and try logging onto the domain using wireless only.
7
or other certificates
If you have successfully connected, disable the Local Area Connection and reboot
your computer and try logging onto the domain using wireless only.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8
9
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Software
MS Windows Server 2012R2 x64 (Username: Administrator, password: Password1)
VMWare Image: Windows Server 2012R2 x64
MS Windows 7
11
MS Windows Server 2012R2 x64 (Username: Administrator, password: Password1)
VMWare Image: Windows Server 2012R2 x64
MS Windows 7
11
12
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Conclusion
The WPA2-PSK would cover the WPA4-way handshake. The brute force password crack
would be used to extract the passphrase. The wireless network traffic would be collected
to find out the WEP key. For doing this action, some software and hardware tools are
required. By using the SSID, the AP WEP configuration would be performed. The MAC
addresses of wireless network would be monitored. For providing the gain address to the
AP, MAC addresses would be predicted. The Microsoft windows 2012 server would be
installed. It would perform the authentication in active directory domain. The client and
server configuration of would be done in windows 2012 server using some software and
hardware.
References
1. Ramachandran, V., & Buchanan, C. Kali Linux wireless penetration testing.
2. Wrightson, T. (2012). Wireless network security. New York: McGraw-Hill
14
The WPA2-PSK would cover the WPA4-way handshake. The brute force password crack
would be used to extract the passphrase. The wireless network traffic would be collected
to find out the WEP key. For doing this action, some software and hardware tools are
required. By using the SSID, the AP WEP configuration would be performed. The MAC
addresses of wireless network would be monitored. For providing the gain address to the
AP, MAC addresses would be predicted. The Microsoft windows 2012 server would be
installed. It would perform the authentication in active directory domain. The client and
server configuration of would be done in windows 2012 server using some software and
hardware.
References
1. Ramachandran, V., & Buchanan, C. Kali Linux wireless penetration testing.
2. Wrightson, T. (2012). Wireless network security. New York: McGraw-Hill
14
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





