SIT202 Computer Networks - Problem Solving Report for Company Network
VerifiedAdded on 2023/06/07
|12
|2290
|406
Report
AI Summary
This report provides a comprehensive solution to a Computer Networks assignment, addressing key concepts such as IP addressing, packet encapsulation, and routing protocols. The solution begins by analyzing the source and destination addresses in outgoing packets and explains how a router manages incoming packets from a remote server, including the use of router entries. It then delves into the creation of IP packets from ICMP packets, detailing the relevant IP header fields and the process of determining local or remote destinations. The report further examines the role of MAC addresses in frame preparation and describes the steps involved in delivering a frame to the next device, including decapsulation, routing decisions, and encapsulation. The assignment also explores dynamic routing protocols, identifying suitable protocols like EIGRP and OSPF while explaining why others, such as BGP, are not appropriate for the given network. The report also covers network addresses, convergence properties of routing protocols, and the handling of packet failures, including timeout counters and retransmissions. The report is a valuable resource for students studying computer networks, offering a clear and detailed understanding of network protocols and configurations.

Running head: COMPUTER NETWORKS
SIT 202 Computer Networks
Name of the Students
Name of the University
Author’s Note
SIT 202 Computer Networks
Name of the Students
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
COMPUTER NETWORKS
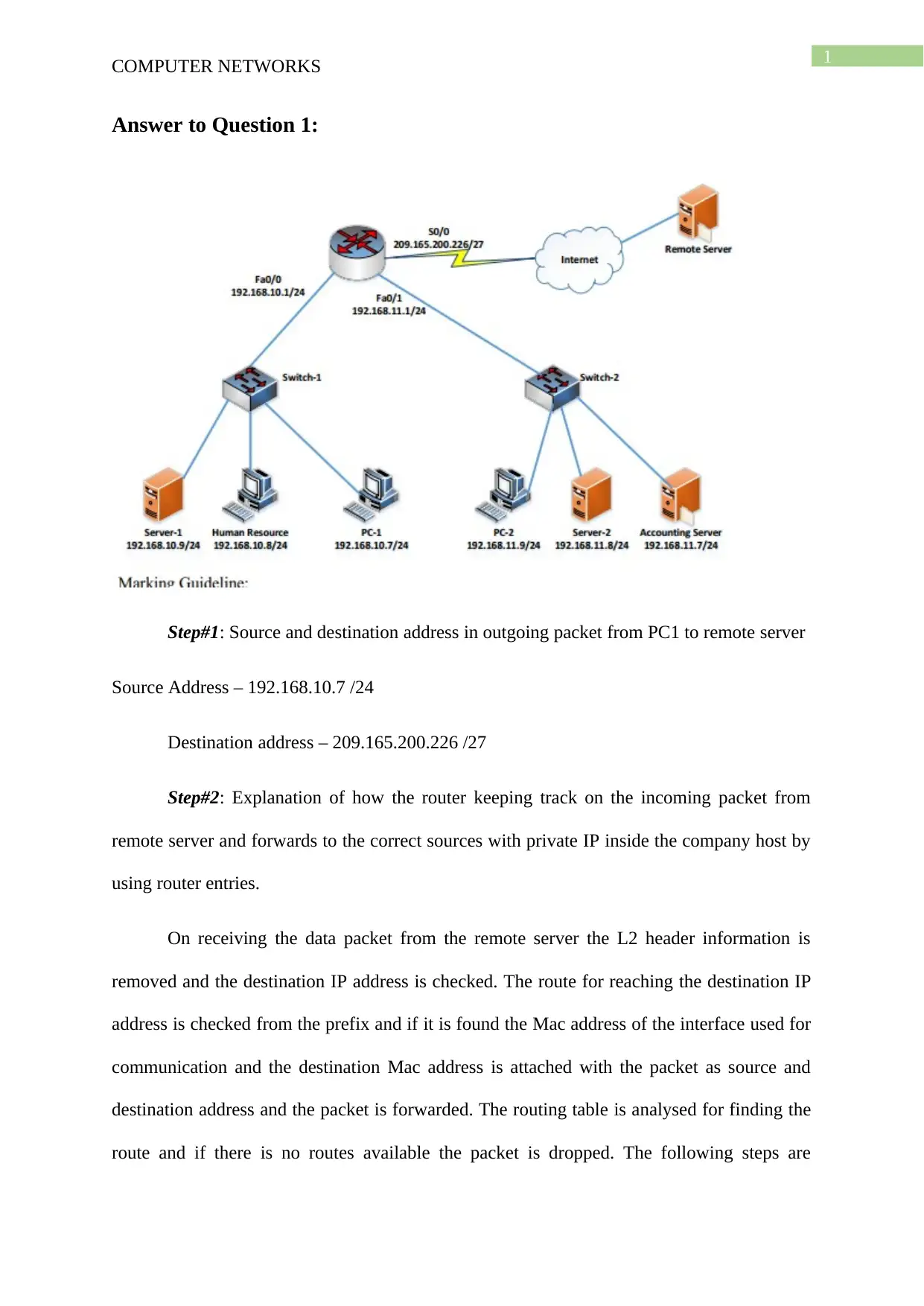
Answer to Question 1:
Step#1: Source and destination address in outgoing packet from PC1 to remote server
Source Address – 192.168.10.7 /24
Destination address – 209.165.200.226 /27
Step#2: Explanation of how the router keeping track on the incoming packet from
remote server and forwards to the correct sources with private IP inside the company host by
using router entries.
On receiving the data packet from the remote server the L2 header information is
removed and the destination IP address is checked. The route for reaching the destination IP
address is checked from the prefix and if it is found the Mac address of the interface used for
communication and the destination Mac address is attached with the packet as source and
destination address and the packet is forwarded. The routing table is analysed for finding the
route and if there is no routes available the packet is dropped. The following steps are
COMPUTER NETWORKS
Answer to Question 1:
Step#1: Source and destination address in outgoing packet from PC1 to remote server
Source Address – 192.168.10.7 /24
Destination address – 209.165.200.226 /27
Step#2: Explanation of how the router keeping track on the incoming packet from
remote server and forwards to the correct sources with private IP inside the company host by
using router entries.
On receiving the data packet from the remote server the L2 header information is
removed and the destination IP address is checked. The route for reaching the destination IP
address is checked from the prefix and if it is found the Mac address of the interface used for
communication and the destination Mac address is attached with the packet as source and
destination address and the packet is forwarded. The routing table is analysed for finding the
route and if there is no routes available the packet is dropped. The following steps are

2
COMPUTER NETWORKS
performed by the router after receiving the packet from the remote server and are given as
follows:
Step#1: Routing
A routing table is recorded by the router listing all the possible routes that can be used
for forwarding a data packet in the network with the details of the physical interface used for
establishing the connection. The network routes are learned by the router by static or dynamic
configurations. On receiving a data packet the layer 2 information are removed and layer 3
information are added for maintaining a track on the delivery of the data packet to the
destination address.
Step#2: Forwarding
On the selection of the routing interface the packets are moved using switching
procedure. Adjacency tables are used for the transmission of the data packets to the next hop
address.
Step#3: Encapsulation
The layer 3 information is used for the encapsulation and it does not changes until the
packet is delivered to the destination address. The layer 2 information can change based on
the medium of transmission and number of hops it passes.
COMPUTER NETWORKS
performed by the router after receiving the packet from the remote server and are given as
follows:
Step#1: Routing
A routing table is recorded by the router listing all the possible routes that can be used
for forwarding a data packet in the network with the details of the physical interface used for
establishing the connection. The network routes are learned by the router by static or dynamic
configurations. On receiving a data packet the layer 2 information are removed and layer 3
information are added for maintaining a track on the delivery of the data packet to the
destination address.
Step#2: Forwarding
On the selection of the routing interface the packets are moved using switching
procedure. Adjacency tables are used for the transmission of the data packets to the next hop
address.
Step#3: Encapsulation
The layer 3 information is used for the encapsulation and it does not changes until the
packet is delivered to the destination address. The layer 2 information can change based on
the medium of transmission and number of hops it passes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
COMPUTER NETWORKS
Answer to Question 2:
1) How IP packet is created from ICMP packet at PC-A, i.e., describe the encapsulation of
the ICMP payload into an IP packet (indicating values of relevant IP header fields).
The ICMP is a protocol that is used for reporting the errors in the network used for the
successful delivery of the data packets in the network. An IP header is used for the
encapsulation of the ICMP data and transmission of the message as a datagram. The entire IP
header of the original message is contained in the ICMP message. The header of the ICMP
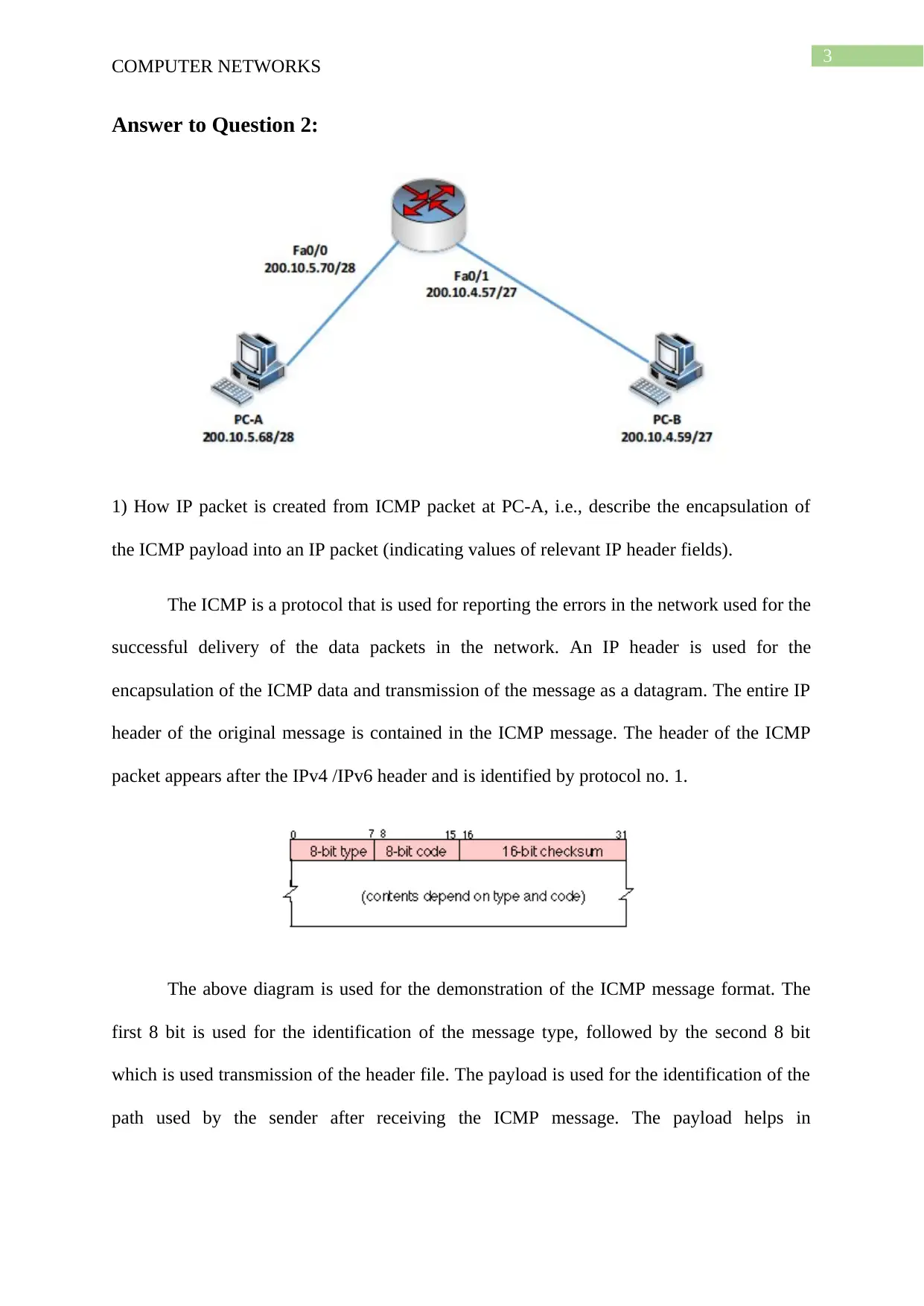
packet appears after the IPv4 /IPv6 header and is identified by protocol no. 1.
The above diagram is used for the demonstration of the ICMP message format. The
first 8 bit is used for the identification of the message type, followed by the second 8 bit
which is used transmission of the header file. The payload is used for the identification of the
path used by the sender after receiving the ICMP message. The payload helps in
COMPUTER NETWORKS
Answer to Question 2:
1) How IP packet is created from ICMP packet at PC-A, i.e., describe the encapsulation of
the ICMP payload into an IP packet (indicating values of relevant IP header fields).
The ICMP is a protocol that is used for reporting the errors in the network used for the
successful delivery of the data packets in the network. An IP header is used for the
encapsulation of the ICMP data and transmission of the message as a datagram. The entire IP
header of the original message is contained in the ICMP message. The header of the ICMP
packet appears after the IPv4 /IPv6 header and is identified by protocol no. 1.
The above diagram is used for the demonstration of the ICMP message format. The
first 8 bit is used for the identification of the message type, followed by the second 8 bit
which is used transmission of the header file. The payload is used for the identification of the
path used by the sender after receiving the ICMP message. The payload helps in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
COMPUTER NETWORKS
identification of the reason for the generation of the ICMP message and program which
generated the packet.
2) How IP at PC-A determines whether PC-B is a local or remote destination including any
calculations performed.
The ARP table of the router is checked for the getting the destination address and if it
is not found the request is forwarded to the next hop address. The Arp table of the next hop
address is checked for finding the destination IP address and deliver the data packets to the
remote destination address.
3) Once the location is determined in (2), a destination MAC address is required to prepare a
frame. If PC-B is in remote, which device’s MAC address will be used for encapsulation of
IP packet into a frame; mention the IP of that devices? Explain why this device.
The MAC address is needed for the encapsulation of the ICMP for the header in the
IP network layer. The correct destination address is verified using the IP address and its
associated Mac address and handling the errors in the transmission of the data packets in the
network. The frame prepared contains the Ethernet header, IP header, ICMP header, user data
and the Ethernet CRC. After the determination of the IP address the destination physical
address is analysed for the preparation of the frame. If the PC B is the remote the MAC
address of the PC A is used for the encapsulation of the IP packet and the IP address
200.10.5.68 is mentioned for the device. This device is used since it is the destination IP
address and the packet is transferred from PC B to PC A. The network access layer is used
for the construction of the PDU and the management of the communication layer.
4) Once the frame is prepared and given to the physical layer of PC-A, list and briefly
describe the remaining steps to deliver the frame to next device’s IP protocol, including
COMPUTER NETWORKS
identification of the reason for the generation of the ICMP message and program which
generated the packet.
2) How IP at PC-A determines whether PC-B is a local or remote destination including any
calculations performed.
The ARP table of the router is checked for the getting the destination address and if it
is not found the request is forwarded to the next hop address. The Arp table of the next hop
address is checked for finding the destination IP address and deliver the data packets to the
remote destination address.
3) Once the location is determined in (2), a destination MAC address is required to prepare a
frame. If PC-B is in remote, which device’s MAC address will be used for encapsulation of
IP packet into a frame; mention the IP of that devices? Explain why this device.
The MAC address is needed for the encapsulation of the ICMP for the header in the
IP network layer. The correct destination address is verified using the IP address and its
associated Mac address and handling the errors in the transmission of the data packets in the
network. The frame prepared contains the Ethernet header, IP header, ICMP header, user data
and the Ethernet CRC. After the determination of the IP address the destination physical
address is analysed for the preparation of the frame. If the PC B is the remote the MAC
address of the PC A is used for the encapsulation of the IP packet and the IP address
200.10.5.68 is mentioned for the device. This device is used since it is the destination IP
address and the packet is transferred from PC B to PC A. The network access layer is used
for the construction of the PDU and the management of the communication layer.
4) Once the frame is prepared and given to the physical layer of PC-A, list and briefly
describe the remaining steps to deliver the frame to next device’s IP protocol, including

5
COMPUTER NETWORKS
decapsulation, routing decisions, and encapsulation, until the ICMP payload can be processed
at PC-B.
After the preparation of the frame for the development of the physical layer of the PC
A the IP address check the address of the destination host by comparing the IP and the subnet
mask. Since the host A and host B are in the different subnet the MAC address of B is used
for mapping. An ARP request is generated for the analysis of the destination MAC and IP
address. The source destination Mac address is added to the Ethernet header for the creation
of the frame. On finding the IP address of the destination address in the ARP table the data
packet is forwarded and if no entry is found a new entry is created. The router reads the
destination Mac address and the frame is flooded to the interface for delivering it to the
destination address. On receiving the frame the host B removes the Ethernet frame and gives
ARP request to the ARP.
Answer to Question 3:
1. Identify two dynamic routing protocols that will work for the routers below.
COMPUTER NETWORKS
decapsulation, routing decisions, and encapsulation, until the ICMP payload can be processed
at PC-B.
After the preparation of the frame for the development of the physical layer of the PC
A the IP address check the address of the destination host by comparing the IP and the subnet
mask. Since the host A and host B are in the different subnet the MAC address of B is used
for mapping. An ARP request is generated for the analysis of the destination MAC and IP
address. The source destination Mac address is added to the Ethernet header for the creation
of the frame. On finding the IP address of the destination address in the ARP table the data
packet is forwarded and if no entry is found a new entry is created. The router reads the
destination Mac address and the frame is flooded to the interface for delivering it to the
destination address. On receiving the frame the host B removes the Ethernet frame and gives
ARP request to the ARP.
Answer to Question 3:
1. Identify two dynamic routing protocols that will work for the routers below.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
COMPUTER NETWORKS
The two dynamic routing protocols that can work for the routers are EIGRP and
OSPF.
2. Also mention a dynamic routing protocol that will not work.
The BGP protocol would not work for the given network framework.
3. Explain your answer for 1 and 2, why (1) will work and (2) will not work.
EIGRP and OSF would work for the configuration of the route because the OSPF
routing protocol has the capability of scaling to any size of network and the EIGRP is also
similar to the OSPF.
EIGRP is used for generating minimum traffic in the network and it utilizes the
resources of the network very minimally. It sends the hello packets in the network and if
there is any change in the network the changes in the routing table is shared instead of
sharing the whole routing information.
The OSPF routing protocol is used for large network where the router determines the
shortest path for delivering the data packets and reduce the waiting time. The use of the
OSPF routing protocol help in detection of the network changes immediately with the help of
multicasting of data packets. A new path for reaching the destination address found if there is
a change in the network. The best path is selected based of the cost metrics not on the number
of hop count and is efficient for delivering the data packets.
The border gateway protocol does not works for the given network diagram because
for the border gateway protocol more than one dedicated connection is required that would
select the best route that have the shortest path for reaching the internet.
4. What will be the network addresses when you configure the dynamic routing in the
routers?
COMPUTER NETWORKS
The two dynamic routing protocols that can work for the routers are EIGRP and
OSPF.
2. Also mention a dynamic routing protocol that will not work.
The BGP protocol would not work for the given network framework.
3. Explain your answer for 1 and 2, why (1) will work and (2) will not work.
EIGRP and OSF would work for the configuration of the route because the OSPF
routing protocol has the capability of scaling to any size of network and the EIGRP is also
similar to the OSPF.
EIGRP is used for generating minimum traffic in the network and it utilizes the
resources of the network very minimally. It sends the hello packets in the network and if
there is any change in the network the changes in the routing table is shared instead of
sharing the whole routing information.
The OSPF routing protocol is used for large network where the router determines the
shortest path for delivering the data packets and reduce the waiting time. The use of the
OSPF routing protocol help in detection of the network changes immediately with the help of
multicasting of data packets. A new path for reaching the destination address found if there is
a change in the network. The best path is selected based of the cost metrics not on the number
of hop count and is efficient for delivering the data packets.
The border gateway protocol does not works for the given network diagram because
for the border gateway protocol more than one dedicated connection is required that would
select the best route that have the shortest path for reaching the internet.
4. What will be the network addresses when you configure the dynamic routing in the
routers?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
COMPUTER NETWORKS
The network address used for the configuration of the router with the dynamic routing in the
routers are given below:
Router 1:
Network 172.16.10.0
Network 10.10.10.0
Router 2:
Network 172.16.20.0
Network 10.10.10.0
5. Compare the routing protocols in the above with respect to their convergence properties.
Depending upon the size of the network the routing protocols are discussed below:
OSPF – OSPF is suitable for the large enterprise networks and it is dependent on the
link state methodology. The SPF algorithm is used for calculating the shortest path and
getting the information of the other router connected in the network. The shortest path
between the routers are calculated with the calculation of the cost metrics. The formula for
the calculation of the cost metric is 100000000 / bandwidth (bps). For wider bandwidth the
cost is reduced. There are no limitation if the number of hops in the network increases and it
has the ability to handle VLSM while the RIP cannot. The convergence rate is much faster
than the RIP since the changes in the routing table are shared with the hops.
EIGRP – It is a hybrid protocol and used for both the link state and the distance
vector routing protocols. All the routes to reach the destination address are stored in the
routing table and it enables faster convergence. The neighbouring routing information is
stored in the routing table and it operates based on the neighbour discovery, reliable transport
COMPUTER NETWORKS
The network address used for the configuration of the router with the dynamic routing in the
routers are given below:
Router 1:
Network 172.16.10.0
Network 10.10.10.0
Router 2:
Network 172.16.20.0
Network 10.10.10.0
5. Compare the routing protocols in the above with respect to their convergence properties.
Depending upon the size of the network the routing protocols are discussed below:
OSPF – OSPF is suitable for the large enterprise networks and it is dependent on the
link state methodology. The SPF algorithm is used for calculating the shortest path and
getting the information of the other router connected in the network. The shortest path
between the routers are calculated with the calculation of the cost metrics. The formula for
the calculation of the cost metric is 100000000 / bandwidth (bps). For wider bandwidth the
cost is reduced. There are no limitation if the number of hops in the network increases and it
has the ability to handle VLSM while the RIP cannot. The convergence rate is much faster
than the RIP since the changes in the routing table are shared with the hops.
EIGRP – It is a hybrid protocol and used for both the link state and the distance
vector routing protocols. All the routes to reach the destination address are stored in the
routing table and it enables faster convergence. The neighbouring routing information is
stored in the routing table and it operates based on the neighbour discovery, reliable transport

8
COMPUTER NETWORKS
protocol, dual finite state machine and protocol dependent module. A unicast message is sent
by the router configured with EIGRP protocol and it does not require the confirmation. It
assigns a sequence number that increases when a new packet is sent by the router.
COMPUTER NETWORKS
protocol, dual finite state machine and protocol dependent module. A unicast message is sent
by the router configured with EIGRP protocol and it does not require the confirmation. It
assigns a sequence number that increases when a new packet is sent by the router.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
COMPUTER NETWORKS
Answer to Question 4:
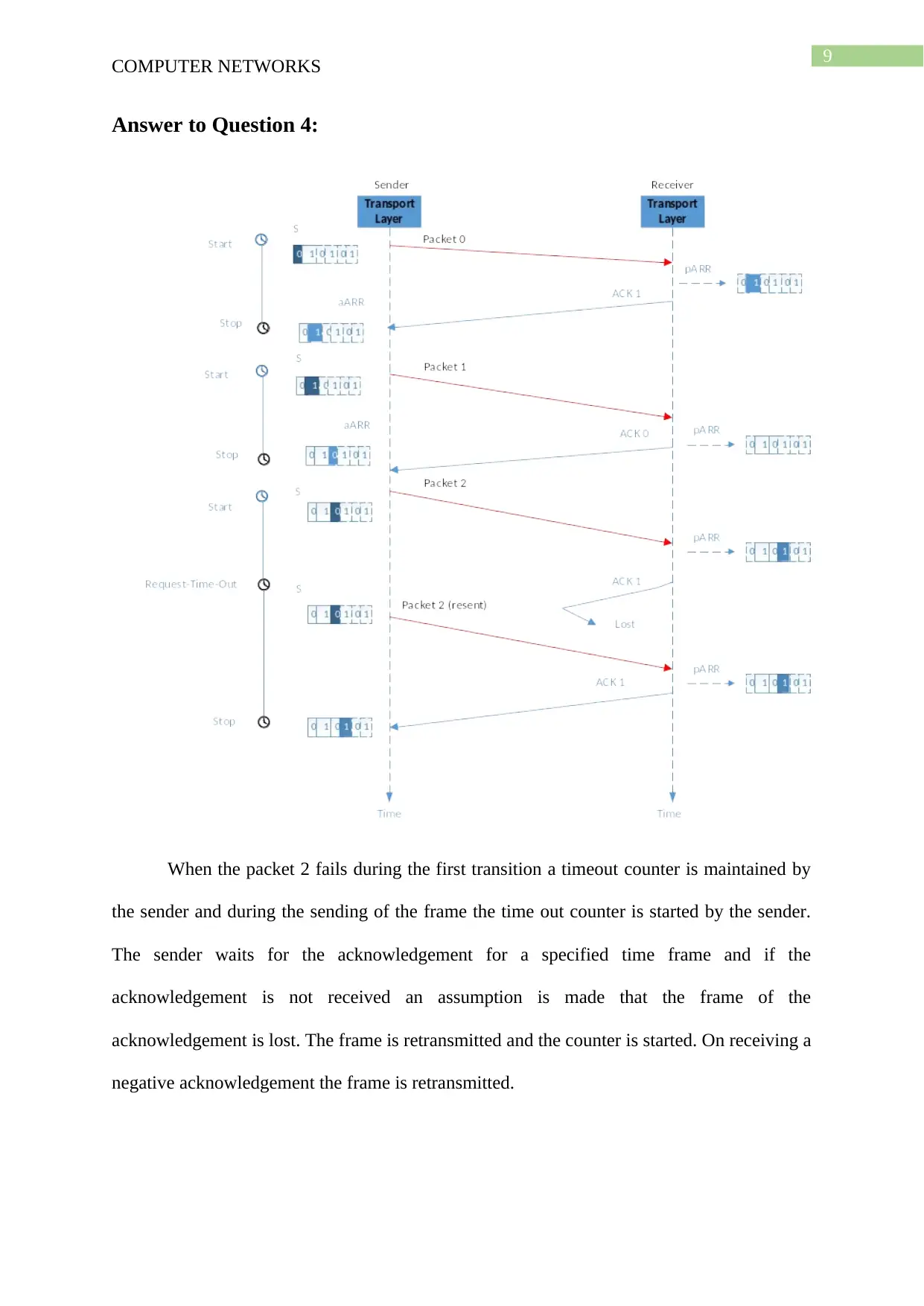
When the packet 2 fails during the first transition a timeout counter is maintained by
the sender and during the sending of the frame the time out counter is started by the sender.
The sender waits for the acknowledgement for a specified time frame and if the
acknowledgement is not received an assumption is made that the frame of the
acknowledgement is lost. The frame is retransmitted and the counter is started. On receiving a
negative acknowledgement the frame is retransmitted.
COMPUTER NETWORKS
Answer to Question 4:
When the packet 2 fails during the first transition a timeout counter is maintained by
the sender and during the sending of the frame the time out counter is started by the sender.
The sender waits for the acknowledgement for a specified time frame and if the
acknowledgement is not received an assumption is made that the frame of the
acknowledgement is lost. The frame is retransmitted and the counter is started. On receiving a
negative acknowledgement the frame is retransmitted.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
COMPUTER NETWORKS
Bibliography
Annan, R.K., Amoako, R.O. and Agyepong, J.T., 2018. Comparative Analysis of the Re-
Convergence Ability of RIP, OSPF and EIGRP Routing Protocols. International Journal of
Innovative Research and Development, 7(7).
Archana, C., 2015. Analysis of RIPv2, OSPF, EIGRP Configuration on router Using CISCO
Packet tracer. International Journal of Engineering Science and Innovative Technology
(IJESIT) Volume, 4.
Hong, S., Xu, L., Wang, H. and Gu, G., 2015, February. Poisoning Network Visibility in
Software-Defined Networks: New Attacks and Countermeasures. In NDSS (Vol. 15, pp. 8-
11).
Li, P., Jia, Y., Feng, M., Ye, C., Chen, F. and Fan, H., 2016. A real-time software defined
radio platform for LTE-advanced heterogeneous networks. Journal of
Communications, 11(3), pp.263-275.
Liu, X., 2015. Atypical hierarchical routing protocols for wireless sensor networks: A
review. IEEE Sensors Journal, 15(10), pp.5372-5383.
Minakhmetov, A., Ware, C. and Iannone, L., 2018, March. Optical networks throughput
enhancement via TCP stop-and-wait on hybrid switches. In 2018 Optical Fiber
Communications Conference and Exposition (OFC) (pp. 1-3). IEEE.
Mohammed, M.A., Degadzor, A.F. and Asante, M., 2016. Performance Analysis of Enhanced
Interior Gateway Routing Protocol (EIGRP) Over Open Shortest Path First (OSPF) Protocol
with Opnet.
Nunes, I.O., Celes, C., de Melo, P.O.V. and Loureiro, A.A., 2017. GROUPS-NET: Group
meetings aware routing in multi-hop D2D networks. Computer Networks, 127, pp.94-108.
COMPUTER NETWORKS
Bibliography
Annan, R.K., Amoako, R.O. and Agyepong, J.T., 2018. Comparative Analysis of the Re-
Convergence Ability of RIP, OSPF and EIGRP Routing Protocols. International Journal of
Innovative Research and Development, 7(7).
Archana, C., 2015. Analysis of RIPv2, OSPF, EIGRP Configuration on router Using CISCO
Packet tracer. International Journal of Engineering Science and Innovative Technology
(IJESIT) Volume, 4.
Hong, S., Xu, L., Wang, H. and Gu, G., 2015, February. Poisoning Network Visibility in
Software-Defined Networks: New Attacks and Countermeasures. In NDSS (Vol. 15, pp. 8-
11).
Li, P., Jia, Y., Feng, M., Ye, C., Chen, F. and Fan, H., 2016. A real-time software defined
radio platform for LTE-advanced heterogeneous networks. Journal of
Communications, 11(3), pp.263-275.
Liu, X., 2015. Atypical hierarchical routing protocols for wireless sensor networks: A
review. IEEE Sensors Journal, 15(10), pp.5372-5383.
Minakhmetov, A., Ware, C. and Iannone, L., 2018, March. Optical networks throughput
enhancement via TCP stop-and-wait on hybrid switches. In 2018 Optical Fiber
Communications Conference and Exposition (OFC) (pp. 1-3). IEEE.
Mohammed, M.A., Degadzor, A.F. and Asante, M., 2016. Performance Analysis of Enhanced
Interior Gateway Routing Protocol (EIGRP) Over Open Shortest Path First (OSPF) Protocol
with Opnet.
Nunes, I.O., Celes, C., de Melo, P.O.V. and Loureiro, A.A., 2017. GROUPS-NET: Group
meetings aware routing in multi-hop D2D networks. Computer Networks, 127, pp.94-108.

11
COMPUTER NETWORKS
Rehman, A.U., Yang, L.L. and Hanzo, L., 2015, May. Performance of cognitive hybrid
automatic repeat request: Stop-and-wait. In Vehicular Technology Conference (VTC Spring),
2015 IEEE 81st (pp. 1-5). IEEE.
Zafar, S., Tariq, H. and Manzoor, K., 2016. Throughput and delay analysis of AODV, DSDV
and DSR routing protocols in mobile ad hoc networks. International Journal of Computer
Networks and Applications (IJCNA), 3(2), pp.1-7.
COMPUTER NETWORKS
Rehman, A.U., Yang, L.L. and Hanzo, L., 2015, May. Performance of cognitive hybrid
automatic repeat request: Stop-and-wait. In Vehicular Technology Conference (VTC Spring),
2015 IEEE 81st (pp. 1-5). IEEE.
Zafar, S., Tariq, H. and Manzoor, K., 2016. Throughput and delay analysis of AODV, DSDV
and DSR routing protocols in mobile ad hoc networks. International Journal of Computer
Networks and Applications (IJCNA), 3(2), pp.1-7.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




