Computer & Networks Security: Design, Configuration, and IP Addressing Plan
VerifiedAdded on 2023/04/25
|21
|1751
|134
AI Summary
In this report we will discuss about computer & networks security and below are the summaries point:-
Design document includes network diagram, site map, and detailed list of network inventories.
Network inventories consist of network devices, network cables, and accessories required for the project.
IP addressing plan is specified with available IP addresses, subnet allocation, and subnet details.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: COMPUTER & NETWORKS SECURITY
Computer & Networks Security
Name of the Student
Name of the University
Author’s Note
Computer & Networks Security
Name of the Student
Name of the University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
COMPUTER & NETWORKS SECURITY
Table of Contents
Design Document.......................................................................................................................2
1. Network Diagram of the LAN...........................................................................................2
2. Site Map showing the deployment location.......................................................................2
3. Detailed list of the network inventories.............................................................................2
3.1. Network Device needed..................................................................................................2
3.2. Network Cables needed...................................................................................................3
3.3. Device and Accessories...................................................................................................3
4. IP Addressing Plan.............................................................................................................4
Configuration Document............................................................................................................8
1. Detailed configuration commands of routers and switches...............................................8
2. Screenshot demonstrating connection between subnetworks and gateway.....................16
Bibliography.............................................................................................................................20
COMPUTER & NETWORKS SECURITY
Table of Contents
Design Document.......................................................................................................................2
1. Network Diagram of the LAN...........................................................................................2
2. Site Map showing the deployment location.......................................................................2
3. Detailed list of the network inventories.............................................................................2
3.1. Network Device needed..................................................................................................2
3.2. Network Cables needed...................................................................................................3
3.3. Device and Accessories...................................................................................................3
4. IP Addressing Plan.............................................................................................................4
Configuration Document............................................................................................................8
1. Detailed configuration commands of routers and switches...............................................8
2. Screenshot demonstrating connection between subnetworks and gateway.....................16
Bibliography.............................................................................................................................20
2
COMPUTER & NETWORKS SECURITY
Design Document
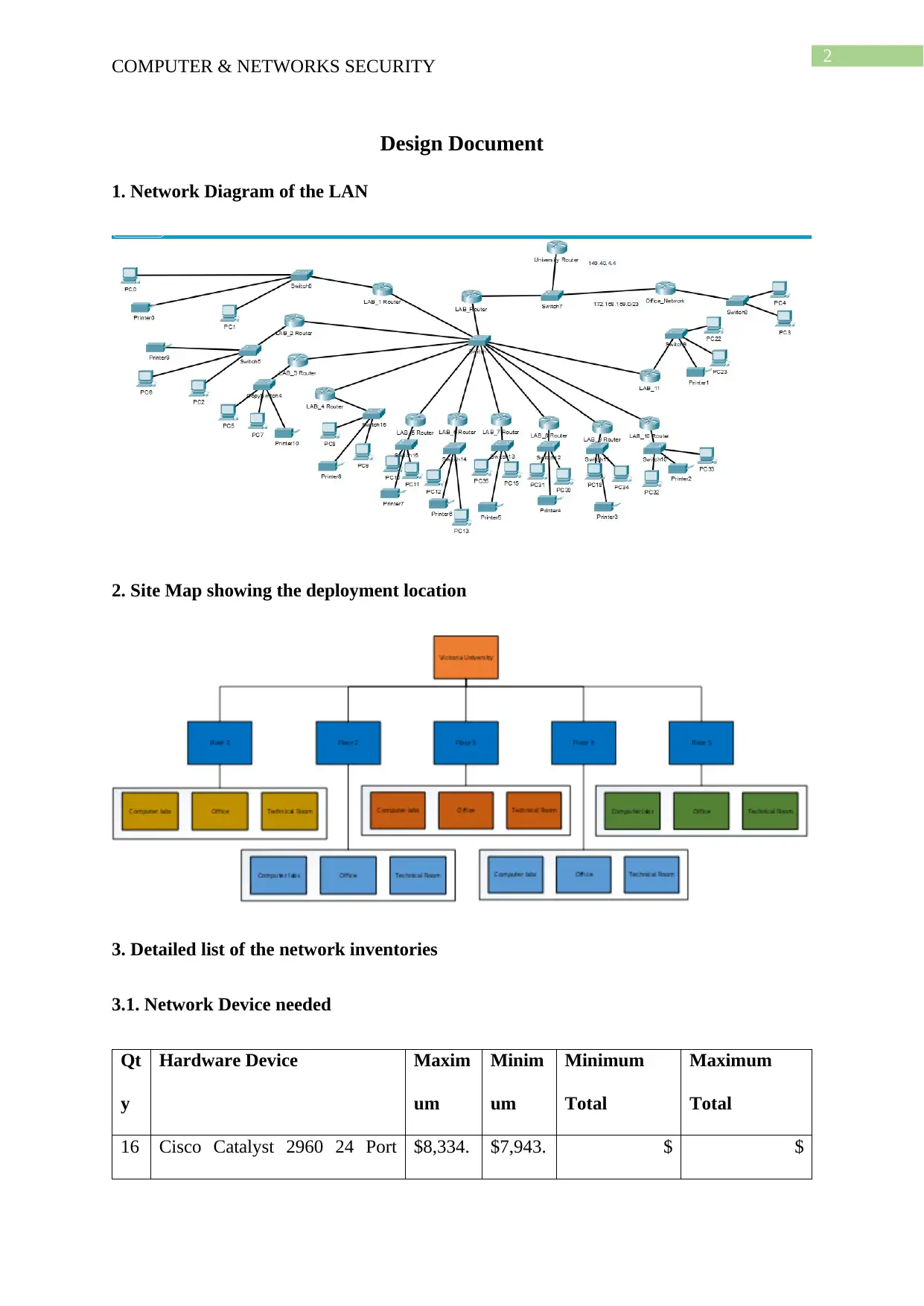
1. Network Diagram of the LAN
2. Site Map showing the deployment location
3. Detailed list of the network inventories
3.1. Network Device needed
Qt
y
Hardware Device Maxim
um
Minim
um
Minimum
Total
Maximum
Total
16 Cisco Catalyst 2960 24 Port $8,334. $7,943. $ $
COMPUTER & NETWORKS SECURITY
Design Document
1. Network Diagram of the LAN
2. Site Map showing the deployment location
3. Detailed list of the network inventories
3.1. Network Device needed
Qt
y
Hardware Device Maxim
um
Minim
um
Minimum
Total
Maximum
Total
16 Cisco Catalyst 2960 24 Port $8,334. $7,943. $ $
3
COMPUTER & NETWORKS SECURITY
Layer 3 switch. 00 00 1,333,44.00 1,27,088.00
6 Cisco Catalyst 2811 Series
Router.
$8,950.
00
$8,550.
00
$
53,700.00
$
51,300.00
5 Samsung Laser Printers 920 315 $
1,575.00
$
4,600.00
3.2. Network Cables needed
Cable Type Cost
Cat 5e 250’ for $24.00
Cat 6 250’ for $32.99
Cat 7 250’ for $95.00
Optical Fiber 250’ for $49.99
3.3. Device and Accessories
Qt
y
Hardware Maxim
um
Minim
um
Minimum
Total
Maximum
Total
2 Lacie 2 TB 10/100/1000 Back-up
Device
659 659 $
1,318.00
$
1,318.00
2 APC Back UPS RS 495 202 $
404.00
$
990.00
20 Netgear WG302 Managed
Wireless Access Point
331 331 $
6,620.00
$
6,620.00
36 Netgear GS108 Switch 8-port 159 159 $ $
COMPUTER & NETWORKS SECURITY
Layer 3 switch. 00 00 1,333,44.00 1,27,088.00
6 Cisco Catalyst 2811 Series
Router.
$8,950.
00
$8,550.
00
$
53,700.00
$
51,300.00
5 Samsung Laser Printers 920 315 $
1,575.00
$
4,600.00
3.2. Network Cables needed
Cable Type Cost
Cat 5e 250’ for $24.00
Cat 6 250’ for $32.99
Cat 7 250’ for $95.00
Optical Fiber 250’ for $49.99
3.3. Device and Accessories
Qt
y
Hardware Maxim
um
Minim
um
Minimum
Total
Maximum
Total
2 Lacie 2 TB 10/100/1000 Back-up
Device
659 659 $
1,318.00
$
1,318.00
2 APC Back UPS RS 495 202 $
404.00
$
990.00
20 Netgear WG302 Managed
Wireless Access Point
331 331 $
6,620.00
$
6,620.00
36 Netgear GS108 Switch 8-port 159 159 $ $
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4
COMPUTER & NETWORKS SECURITY
5,724.00 5,724.00
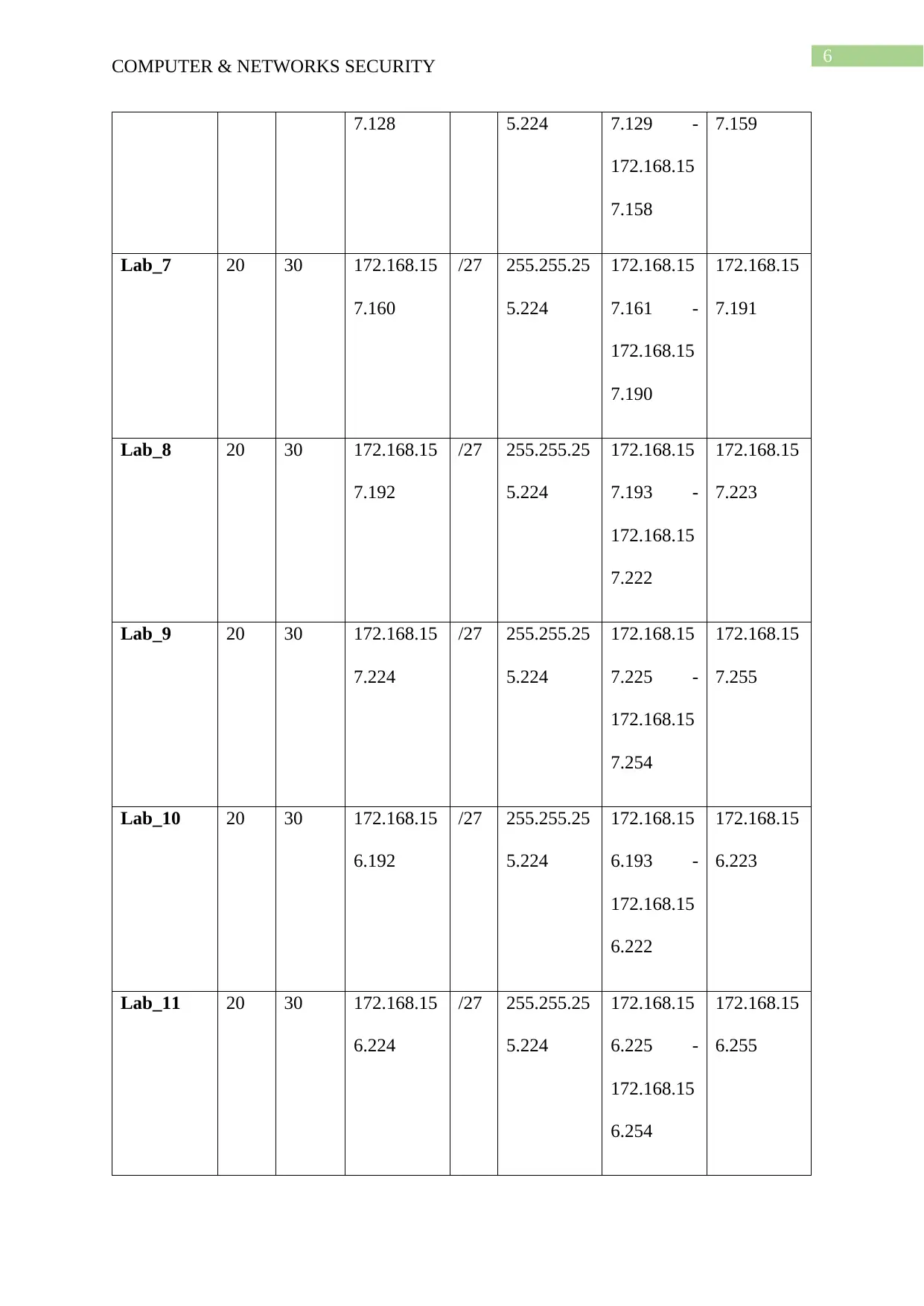
4. IP Addressing Plan
Network Address – 172.168.159.0/23
Available IP addresses in major network: 1022
Number of IP addresses needed: 348
Available IP addresses in allocated subnets: 502
About 52% of available major network address space is used
About 69% of subnetted network address space is used
Subnet
Name
Need
ed
Size
Alloca
ted
Size
Address Ma
sk
Dec Mask Assignable
Range
Broadcast
Network 2 2 172.168.15
8.16
/30 255.255.25
5.252
172.168.15
8.17 -
172.168.15
8.18
172.168.15
8.19
LAB_Netw
ork
11 14 172.168.15
8.0
/28 255.255.25
5.240
172.168.15
8.1 -
172.168.15
8.14
172.168.15
8.15
Office_Net
work
23 30 172.168.15
6.128
/27 255.255.25
5.224
172.168.15
6.129 -
172.168.15
COMPUTER & NETWORKS SECURITY
5,724.00 5,724.00
4. IP Addressing Plan
Network Address – 172.168.159.0/23
Available IP addresses in major network: 1022
Number of IP addresses needed: 348
Available IP addresses in allocated subnets: 502
About 52% of available major network address space is used
About 69% of subnetted network address space is used
Subnet
Name
Need
ed
Size
Alloca
ted
Size
Address Ma
sk
Dec Mask Assignable
Range
Broadcast
Network 2 2 172.168.15
8.16
/30 255.255.25
5.252
172.168.15
8.17 -
172.168.15
8.18
172.168.15
8.19
LAB_Netw
ork
11 14 172.168.15
8.0
/28 255.255.25
5.240
172.168.15
8.1 -
172.168.15
8.14
172.168.15
8.15
Office_Net
work
23 30 172.168.15
6.128
/27 255.255.25
5.224
172.168.15
6.129 -
172.168.15
5
COMPUTER & NETWORKS SECURITY
172.168.15
6.158
6.159
Lab_1 20 30 172.168.15
6.160
/27 255.255.25
5.224
172.168.15
6.161 -
172.168.15
6.190
172.168.15
6.191
Lab_2 20 30 172.168.15
7.0
/27 255.255.25
5.224
172.168.15
7.1 -
172.168.15
7.30
172.168.15
7.31
Lab_3 20 30 172.168.15
7.32
/27 255.255.25
5.224
172.168.15
7.33 -
172.168.15
7.62
172.168.15
7.63
Lab_4 20 30 172.168.15
7.64
/27 255.255.25
5.224
172.168.15
7.65 -
172.168.15
7.94
172.168.15
7.95
Lab_5 20 30 172.168.15
7.96
/27 255.255.25
5.224
172.168.15
7.97 -
172.168.15
7.126
172.168.15
7.127
Lab_6 20 30 172.168.15 /27 255.255.25 172.168.15 172.168.15
COMPUTER & NETWORKS SECURITY
172.168.15
6.158
6.159
Lab_1 20 30 172.168.15
6.160
/27 255.255.25
5.224
172.168.15
6.161 -
172.168.15
6.190
172.168.15
6.191
Lab_2 20 30 172.168.15
7.0
/27 255.255.25
5.224
172.168.15
7.1 -
172.168.15
7.30
172.168.15
7.31
Lab_3 20 30 172.168.15
7.32
/27 255.255.25
5.224
172.168.15
7.33 -
172.168.15
7.62
172.168.15
7.63
Lab_4 20 30 172.168.15
7.64
/27 255.255.25
5.224
172.168.15
7.65 -
172.168.15
7.94
172.168.15
7.95
Lab_5 20 30 172.168.15
7.96
/27 255.255.25
5.224
172.168.15
7.97 -
172.168.15
7.126
172.168.15
7.127
Lab_6 20 30 172.168.15 /27 255.255.25 172.168.15 172.168.15
6
COMPUTER & NETWORKS SECURITY
7.128 5.224 7.129 -
172.168.15
7.158
7.159
Lab_7 20 30 172.168.15
7.160
/27 255.255.25
5.224
172.168.15
7.161 -
172.168.15
7.190
172.168.15
7.191
Lab_8 20 30 172.168.15
7.192
/27 255.255.25
5.224
172.168.15
7.193 -
172.168.15
7.222
172.168.15
7.223
Lab_9 20 30 172.168.15
7.224
/27 255.255.25
5.224
172.168.15
7.225 -
172.168.15
7.254
172.168.15
7.255
Lab_10 20 30 172.168.15
6.192
/27 255.255.25
5.224
172.168.15
6.193 -
172.168.15
6.222
172.168.15
6.223
Lab_11 20 30 172.168.15
6.224
/27 255.255.25
5.224
172.168.15
6.225 -
172.168.15
6.254
172.168.15
6.255
COMPUTER & NETWORKS SECURITY
7.128 5.224 7.129 -
172.168.15
7.158
7.159
Lab_7 20 30 172.168.15
7.160
/27 255.255.25
5.224
172.168.15
7.161 -
172.168.15
7.190
172.168.15
7.191
Lab_8 20 30 172.168.15
7.192
/27 255.255.25
5.224
172.168.15
7.193 -
172.168.15
7.222
172.168.15
7.223
Lab_9 20 30 172.168.15
7.224
/27 255.255.25
5.224
172.168.15
7.225 -
172.168.15
7.254
172.168.15
7.255
Lab_10 20 30 172.168.15
6.192
/27 255.255.25
5.224
172.168.15
6.193 -
172.168.15
6.222
172.168.15
6.223
Lab_11 20 30 172.168.15
6.224
/27 255.255.25
5.224
172.168.15
6.225 -
172.168.15
6.254
172.168.15
6.255
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
COMPUTER & NETWORKS SECURITY
Network_
Office
92 126 172.168.15
6.0
/25 255.255.25
5.128
172.168.15
6.1 -
172.168.15
6.126
172.168.15
6.127
COMPUTER & NETWORKS SECURITY
Network_
Office
92 126 172.168.15
6.0
/25 255.255.25
5.128
172.168.15
6.1 -
172.168.15
6.126
172.168.15
6.127

8
COMPUTER & NETWORKS SECURITY
Configuration Document
1. Detailed configuration commands of routers and switches
University_Router
Enable
Conf t
Hostname Uni_R1
interface FastEthernet0/0
ip address 140.40.4.4 255.255.0.0
no shut
exit
Lab_Router
Conf t
Hostname Lab_Router
Int fa 0/0
Ip add 172.168.158.17 255.255.255.252
No shut
Exit
Int fa 0/1
Ip address 172.168.158.14 255.255.255.240
COMPUTER & NETWORKS SECURITY
Configuration Document
1. Detailed configuration commands of routers and switches
University_Router
Enable
Conf t
Hostname Uni_R1
interface FastEthernet0/0
ip address 140.40.4.4 255.255.0.0
no shut
exit
Lab_Router
Conf t
Hostname Lab_Router
Int fa 0/0
Ip add 172.168.158.17 255.255.255.252
No shut
Exit
Int fa 0/1
Ip address 172.168.158.14 255.255.255.240

9
COMPUTER & NETWORKS SECURITY
No shut
Exit
Lab1 Router
Enable
Conf t
Hostname Lab1
Int fa 0/0
ip address 172.168.156.161 255.255.255.224
no shut
exit
int fa 0/1
ip address 172.168.158.1 255.255.255.240
no shut
exit
Lab2 Router
enable
config t
hostname Lab2
int fa 0/0
ip address 172.168.157.1 255.255.255.224
COMPUTER & NETWORKS SECURITY
No shut
Exit
Lab1 Router
Enable
Conf t
Hostname Lab1
Int fa 0/0
ip address 172.168.156.161 255.255.255.224
no shut
exit
int fa 0/1
ip address 172.168.158.1 255.255.255.240
no shut
exit
Lab2 Router
enable
config t
hostname Lab2
int fa 0/0
ip address 172.168.157.1 255.255.255.224
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
COMPUTER & NETWORKS SECURITY
no shut
exit
int fa 0/1
ip address 172.168.158.2 255.255.255.240
no shut
exit
Lab3 Router
enable
config t
hostname Lab3
int fa 0/0
ip address 172.168.157.33 255.255.255.224
no shut
exit
int fa 0/1
ip address 172.168.158.3 255.255.255.240
no shut
exit
Lab4 Router
enable
COMPUTER & NETWORKS SECURITY
no shut
exit
int fa 0/1
ip address 172.168.158.2 255.255.255.240
no shut
exit
Lab3 Router
enable
config t
hostname Lab3
int fa 0/0
ip address 172.168.157.33 255.255.255.224
no shut
exit
int fa 0/1
ip address 172.168.158.3 255.255.255.240
no shut
exit
Lab4 Router
enable

11
COMPUTER & NETWORKS SECURITY
config t
hostname Lab4
int fa 0/0
ip address 172.168.157.65 255.255.255.224
no shut
exit
int fa 0/1
ip address 172.168.158.4 255.255.255.240
no shut
exit
Lab5 Router
enable
config t
hostname Lab5
int fa 0/0
ip address 172.168.157.97 255.255.255.224
no shut
exit
int fa 0/1
ip address 172.168.158.5 255.255.255.240
COMPUTER & NETWORKS SECURITY
config t
hostname Lab4
int fa 0/0
ip address 172.168.157.65 255.255.255.224
no shut
exit
int fa 0/1
ip address 172.168.158.4 255.255.255.240
no shut
exit
Lab5 Router
enable
config t
hostname Lab5
int fa 0/0
ip address 172.168.157.97 255.255.255.224
no shut
exit
int fa 0/1
ip address 172.168.158.5 255.255.255.240

12
COMPUTER & NETWORKS SECURITY
no shut
exit
Lab6 Router
Enable
config t
hostname Lab6
int fa 0/0
ip address 172.168.158.6 255.255.255.240
no shut
exit
int fa 0/1
ip address 172.168.157.129 255.255.255.224
no shut
exit
Lab7 Router
en
config t
hostname Lab7
int fa 0/0
ip address 172.168.158.7 255.255.255.240
COMPUTER & NETWORKS SECURITY
no shut
exit
Lab6 Router
Enable
config t
hostname Lab6
int fa 0/0
ip address 172.168.158.6 255.255.255.240
no shut
exit
int fa 0/1
ip address 172.168.157.129 255.255.255.224
no shut
exit
Lab7 Router
en
config t
hostname Lab7
int fa 0/0
ip address 172.168.158.7 255.255.255.240
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
COMPUTER & NETWORKS SECURITY
no shut
exit
int fa 0/1
ip address 172.168.157.161 255.255.255.224
no shut
exit
Lab8 Router
enable
config t
hostname Lab8
int fa 0/0
ip address 172.168.158.8 255.255.255.240
no shut
exit
int fa 0/1
ip address 172.168.157.193 255.255.255.224
no shut
exit
Lab9 Router
enable
COMPUTER & NETWORKS SECURITY
no shut
exit
int fa 0/1
ip address 172.168.157.161 255.255.255.224
no shut
exit
Lab8 Router
enable
config t
hostname Lab8
int fa 0/0
ip address 172.168.158.8 255.255.255.240
no shut
exit
int fa 0/1
ip address 172.168.157.193 255.255.255.224
no shut
exit
Lab9 Router
enable

14
COMPUTER & NETWORKS SECURITY
config t
hostname Lab9
int fa 0/0
ip address 172.168.158.9 255.255.255.240
no shut
exit
int fa 0/1
ip address 172.168.156.225 255.255.255.224
no shut
exit
Lab10 Router
enable
config t
hostname Lab10
int fa 0/0
ip address 172.168.158.10 255.255.255.240
no shut
exit
int fa 0/1
ip address 172.168.156.193 255.255.255.224
COMPUTER & NETWORKS SECURITY
config t
hostname Lab9
int fa 0/0
ip address 172.168.158.9 255.255.255.240
no shut
exit
int fa 0/1
ip address 172.168.156.225 255.255.255.224
no shut
exit
Lab10 Router
enable
config t
hostname Lab10
int fa 0/0
ip address 172.168.158.10 255.255.255.240
no shut
exit
int fa 0/1
ip address 172.168.156.193 255.255.255.224

15
COMPUTER & NETWORKS SECURITY
no shut
exit
Lab11 Router
enable
config t
hostname Lab11
int fa 0/0
ip address 172.168.158.11 255.255.255.240
no shut
exit
int fa 0/1
ip address 172.168.156.225 255.255.255.224
no shut
exit
ip route 172.168.158.0 255.255.255.0 172.168.158.14
ip route 172.168.156.0 255.255.255.0 172.168.158.18
Office Router
enable
config t
hostname OfficeRouter
COMPUTER & NETWORKS SECURITY
no shut
exit
Lab11 Router
enable
config t
hostname Lab11
int fa 0/0
ip address 172.168.158.11 255.255.255.240
no shut
exit
int fa 0/1
ip address 172.168.156.225 255.255.255.224
no shut
exit
ip route 172.168.158.0 255.255.255.0 172.168.158.14
ip route 172.168.156.0 255.255.255.0 172.168.158.18
Office Router
enable
config t
hostname OfficeRouter
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16
COMPUTER & NETWORKS SECURITY
int fa0/0
ip address 172.168.158.18 255.255.255.252
no shut
exit
int fa 0/1
ip address 172.168.156.1 255.255.255.128
no shut
exit
2. Screenshot demonstrating connection between subnetworks and gateway
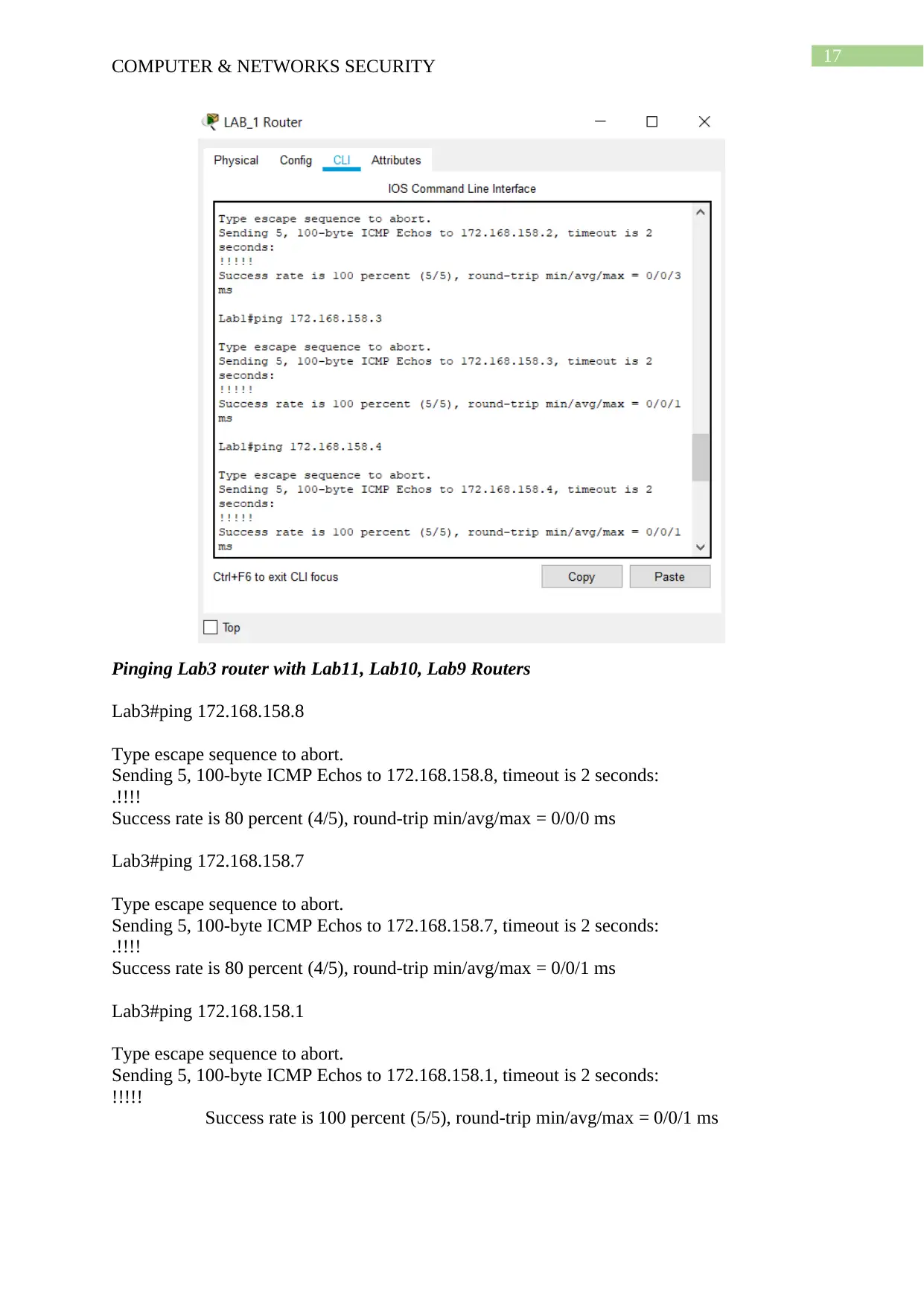
Pinging Lab1 router with Lab2, Lab3, Lab4 Routers
Lab1#ping 172.168.158.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/3 ms
Lab1#ping 172.168.158.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/1 ms
Lab1#ping 172.168.158.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/1 ms
COMPUTER & NETWORKS SECURITY
int fa0/0
ip address 172.168.158.18 255.255.255.252
no shut
exit
int fa 0/1
ip address 172.168.156.1 255.255.255.128
no shut
exit
2. Screenshot demonstrating connection between subnetworks and gateway
Pinging Lab1 router with Lab2, Lab3, Lab4 Routers
Lab1#ping 172.168.158.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/3 ms
Lab1#ping 172.168.158.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/1 ms
Lab1#ping 172.168.158.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/1 ms
17
COMPUTER & NETWORKS SECURITY
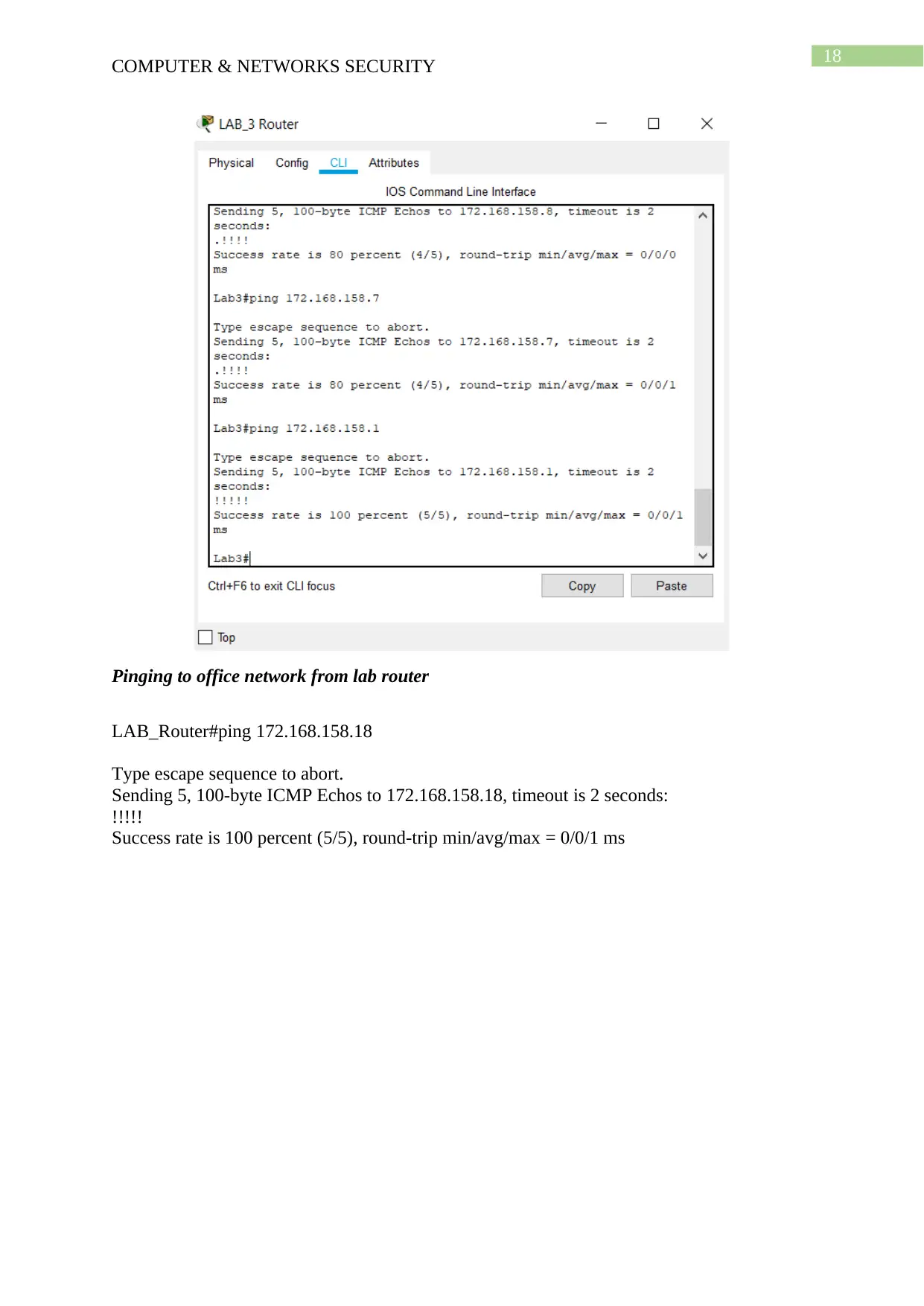
Pinging Lab3 router with Lab11, Lab10, Lab9 Routers
Lab3#ping 172.168.158.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.8, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms
Lab3#ping 172.168.158.7
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.7, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/1 ms
Lab3#ping 172.168.158.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/1 ms
COMPUTER & NETWORKS SECURITY
Pinging Lab3 router with Lab11, Lab10, Lab9 Routers
Lab3#ping 172.168.158.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.8, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms
Lab3#ping 172.168.158.7
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.7, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/1 ms
Lab3#ping 172.168.158.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/1 ms
18
COMPUTER & NETWORKS SECURITY
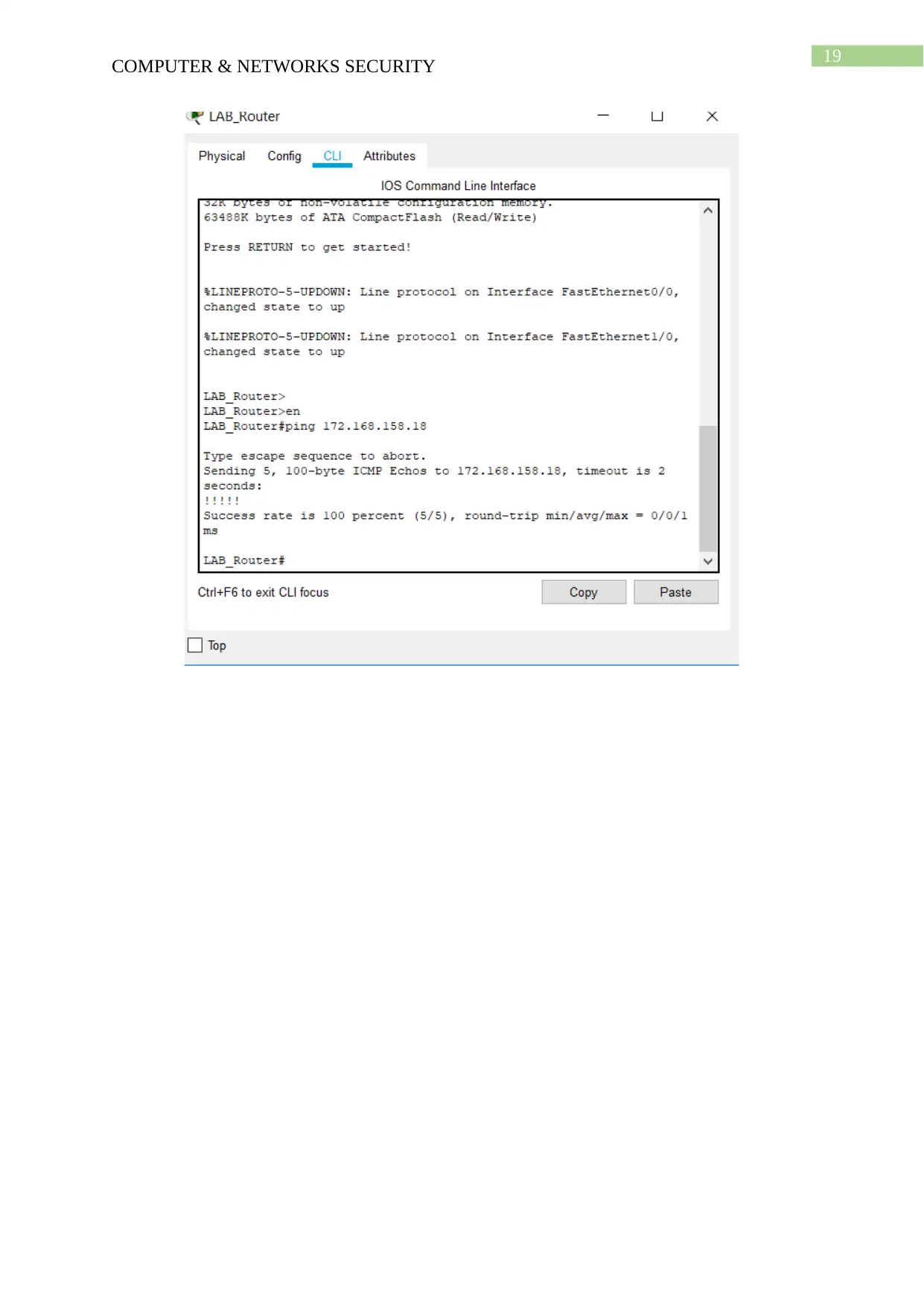
Pinging to office network from lab router
LAB_Router#ping 172.168.158.18
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.18, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/1 ms
COMPUTER & NETWORKS SECURITY
Pinging to office network from lab router
LAB_Router#ping 172.168.158.18
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.168.158.18, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/1 ms
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
19
COMPUTER & NETWORKS SECURITY
COMPUTER & NETWORKS SECURITY

20
COMPUTER & NETWORKS SECURITY
Bibliography
[1].de Oliveira, Francisco Kelsen, and Alex Sandro Gomes. "A developemnt model of
units of learning for multiple platforms." Information Systems and Technologies
(CISTI), 2015 10th Iberian Conference on. IEEE, 2015.
[2].Ma, Li, Ai-Min Luo, and Jiong Fu. "An object Petri net based modeling method for
combat organization process in human view." Wavelet Active Media Technology and
Information Processing (ICCWAMTIP), 2016 13th International Computer
Conference on. IEEE, 2016.
[3].Nofriansyah, Dicky, Zulham Effendi, and Mukhlis Ramadhan. "APPLICATION OF
DISCRETE HOPFIELD ALGORTIHM TYPE ARTIFICIAL NEURAL NETWORK
FOR PATTERN RECOGNITION OF EYE’S IRIS." Jurnal SAINTIKOM Vol 16.1,
2017.
[4].Samson, Andrew J., et al. "Neuronal networks provide rapid neuroprotection against
spreading toxicity." Scientific reports 6, 2016: 33746.
[5].Wang, Chao. "Deep Learning Accelerators YangYang Zhao, chao wang, Lei gong, Xi
Li, aiLi wang, anD Xuehai Zhou." High Performance Computing for Big Data.
Chapman and Hall/CRC, 2017. 169-188.
[6].Zhabelova, Gulnara, and Valeriy Vyatkin. "Towards a Design Methodology for
Agent-Based Automation of Smart Grid." International Conference on Industrial
Applications of Holonic and Multi-Agent Systems. Springer, Cham, 2015.
[7].Zhou, Derong. "A Survey on Campus Network Log." Advances in Materials,
Machinery, Electrical Engineering, AMMEE 2017. Atlantis Press, 2017.
[8]. Islam, Akm Zahidul. Modality shift in design process: Understanding the rationale
behind modality shift and its effect on architectural design. University of Missouri-
Columbia, 2015.
COMPUTER & NETWORKS SECURITY
Bibliography
[1].de Oliveira, Francisco Kelsen, and Alex Sandro Gomes. "A developemnt model of
units of learning for multiple platforms." Information Systems and Technologies
(CISTI), 2015 10th Iberian Conference on. IEEE, 2015.
[2].Ma, Li, Ai-Min Luo, and Jiong Fu. "An object Petri net based modeling method for
combat organization process in human view." Wavelet Active Media Technology and
Information Processing (ICCWAMTIP), 2016 13th International Computer
Conference on. IEEE, 2016.
[3].Nofriansyah, Dicky, Zulham Effendi, and Mukhlis Ramadhan. "APPLICATION OF
DISCRETE HOPFIELD ALGORTIHM TYPE ARTIFICIAL NEURAL NETWORK
FOR PATTERN RECOGNITION OF EYE’S IRIS." Jurnal SAINTIKOM Vol 16.1,
2017.
[4].Samson, Andrew J., et al. "Neuronal networks provide rapid neuroprotection against
spreading toxicity." Scientific reports 6, 2016: 33746.
[5].Wang, Chao. "Deep Learning Accelerators YangYang Zhao, chao wang, Lei gong, Xi
Li, aiLi wang, anD Xuehai Zhou." High Performance Computing for Big Data.
Chapman and Hall/CRC, 2017. 169-188.
[6].Zhabelova, Gulnara, and Valeriy Vyatkin. "Towards a Design Methodology for
Agent-Based Automation of Smart Grid." International Conference on Industrial
Applications of Holonic and Multi-Agent Systems. Springer, Cham, 2015.
[7].Zhou, Derong. "A Survey on Campus Network Log." Advances in Materials,
Machinery, Electrical Engineering, AMMEE 2017. Atlantis Press, 2017.
[8]. Islam, Akm Zahidul. Modality shift in design process: Understanding the rationale
behind modality shift and its effect on architectural design. University of Missouri-
Columbia, 2015.
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





