Computer Networks: Problem-Solving Report 2 - Solutions and Analysis
VerifiedAdded on 2020/02/24
|10
|1244
|118
Report
AI Summary
This report offers a detailed analysis of computer network problem-solving, focusing on congestion control mechanisms, routing protocols, and the advantages of DHCPv6 auto-configuration. The report explores open-loop and closed-loop congestion control, explaining retransmission and acknowledgement policies, as well as backpressure and choke packet techniques. It compares distance vector and link-state routing protocols, discussing their suitability for fast convergence and low traffic scenarios. Additionally, the report highlights the disadvantages of using a single public IP address, including cost and security concerns. The report also outlines the benefits of DHCPv6 auto-configuration over DHCPv4, particularly in terms of cost-effectiveness and suitability for wireless networks. The report provides packet exchange diagrams to illustrate network behavior and includes references to relevant academic sources.

Running head: COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
Computer Networks - Problem-Solving Report 2
Name of the Student
Name of the University
Author Note
Computer Networks - Problem-Solving Report 2
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
Table of Contents
Question 2..................................................................................................................................2
Part A.....................................................................................................................................2
Part B......................................................................................................................................5
Question 3..................................................................................................................................5
Part A.....................................................................................................................................5
Part B......................................................................................................................................6
References..................................................................................................................................7
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
Table of Contents
Question 2..................................................................................................................................2
Part A.....................................................................................................................................2
Part B......................................................................................................................................5
Question 3..................................................................................................................................5
Part A.....................................................................................................................................5
Part B......................................................................................................................................6
References..................................................................................................................................7

2
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
Question 2
Part A
I. Two mechanisms which can be used are:
Open-loop congestion control – in the process odd open loop congestion control there are
a set of congestion control policies, which are used to remove congestion as soon as it
happens. The different policies which are used in the process of removal of congestion
are:
o Retransmission policy – it the receiver of a packet stream thinks that one of the
received packet corrupt then the receiver may ask the sender to resend the same
packet again. This can cause congestion in the packet stream (Silva et al. 2015).
To avoid congestion a good transmission policy has to be applied to the network
line, which will be responsible for the removal of congestion in the transmission
line.
o Acknowledgement policy – sending of an acknowledgement back to the sender
can cause congestion due to the traffic used by the acknowledgement send. It
would be better to share only selective acknowledgement packets or to send after
a timer has expired (Forouzan and Hill 2006).
Closed-loop congestion control – for closed loop congestion control the routers can use
any of the following protocols to reduce the congestion in the transmission line:
o Backpressure of data stream can be used only in a virtual network. The receiver
stops accepting the packets and the packets are stuck in the stream (Zeeshan, Khan
and Jan 2016). This causes the sender to stop sending nay more packets and the
congestion breaks down after some time.
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
Question 2
Part A
I. Two mechanisms which can be used are:
Open-loop congestion control – in the process odd open loop congestion control there are
a set of congestion control policies, which are used to remove congestion as soon as it
happens. The different policies which are used in the process of removal of congestion
are:
o Retransmission policy – it the receiver of a packet stream thinks that one of the
received packet corrupt then the receiver may ask the sender to resend the same
packet again. This can cause congestion in the packet stream (Silva et al. 2015).
To avoid congestion a good transmission policy has to be applied to the network
line, which will be responsible for the removal of congestion in the transmission
line.
o Acknowledgement policy – sending of an acknowledgement back to the sender
can cause congestion due to the traffic used by the acknowledgement send. It
would be better to share only selective acknowledgement packets or to send after
a timer has expired (Forouzan and Hill 2006).
Closed-loop congestion control – for closed loop congestion control the routers can use
any of the following protocols to reduce the congestion in the transmission line:
o Backpressure of data stream can be used only in a virtual network. The receiver
stops accepting the packets and the packets are stuck in the stream (Zeeshan, Khan
and Jan 2016). This causes the sender to stop sending nay more packets and the
congestion breaks down after some time.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
o Sending of a choke packet, which would tell if there is a congestion in the line, or
not (Forouzan and Hill 2006).
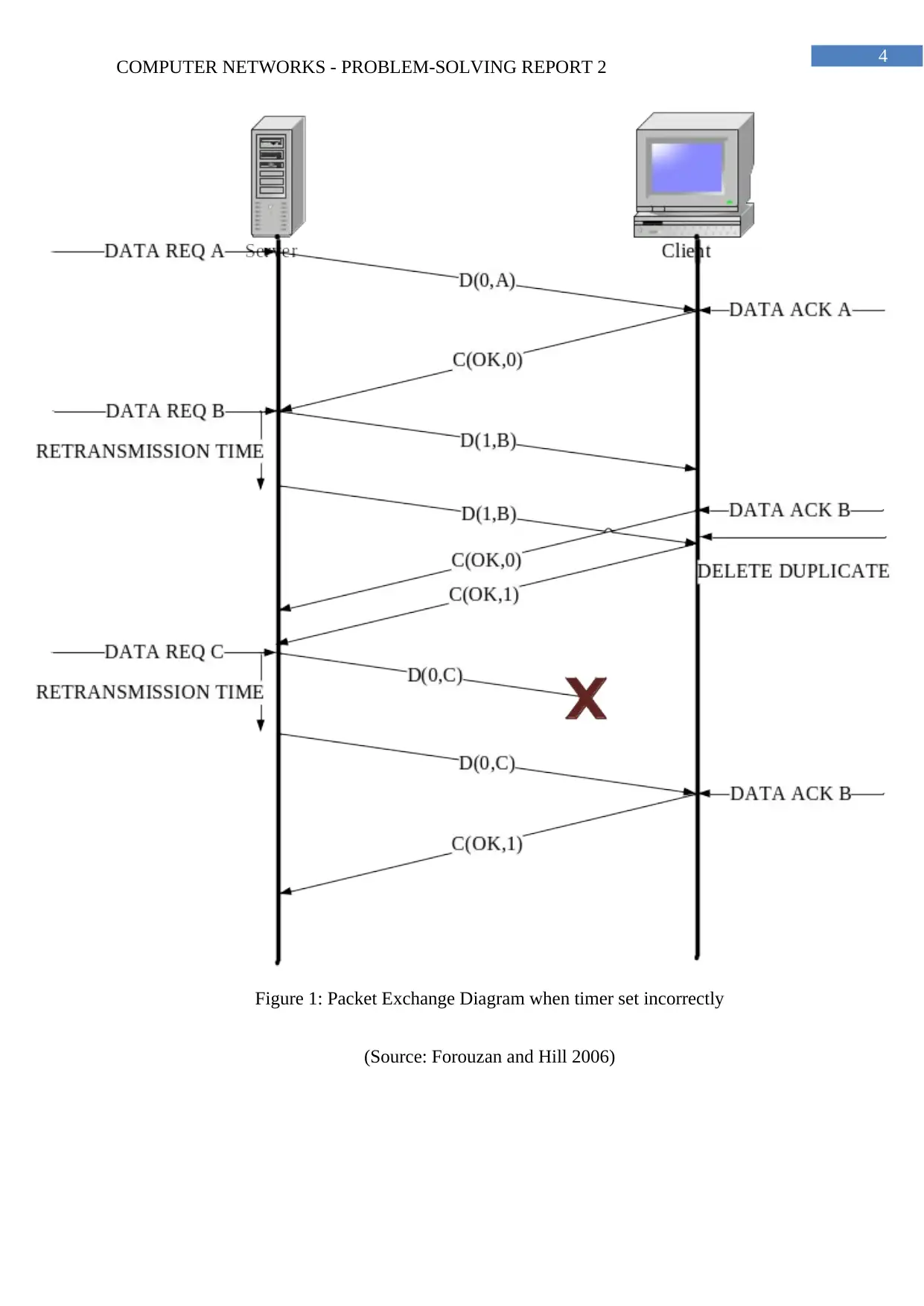
II. Packet Exchange Diagrams
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
o Sending of a choke packet, which would tell if there is a congestion in the line, or
not (Forouzan and Hill 2006).
II. Packet Exchange Diagrams
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
Figure 1: Packet Exchange Diagram when timer set incorrectly
(Source: Forouzan and Hill 2006)
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
Figure 1: Packet Exchange Diagram when timer set incorrectly
(Source: Forouzan and Hill 2006)

5
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
(Source: Forouzan and Hill 2006)
Part B
Using a single public IP address has the following two disadvantages:
Expense – the amount of money that is required for a separate IP address has been
recently increased. Therefore, if the organization thinks that they will be using a separate
IP address then they would have to pay a lot of money to buy the IP (Monsanto Et Al.
2013).
Security – If there were, a use of a single IP in the organization then there would be free
flowing of the packets and requests through the routers. Any system control attempts and
spams are free to move through the network (Monsanto et al. 2013).
Question 3
Part A
I.
Distance Vector routing – each node in the network virtually constructs a one
dimensional array which consists of the cost or distance which has to be incurred for
sending a packet to the neighboring node. All the nodes know it the cost, which has to be
incurred for sending the packet to the node. Any node, which is inaccessible, is assign an
infinite cost (Forouzan and Hill 2006).
Link-State routing – there is no creation of any matrix for the cost which is to be incurred
for the transmission of data. In this method, all the nodes the cost needed of the
immediate neighboring node. If all the nodes know this kind of knowledge then the whole
network will be able to transfer packets within the network (Hoque et al. 2013).
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
(Source: Forouzan and Hill 2006)
Part B
Using a single public IP address has the following two disadvantages:
Expense – the amount of money that is required for a separate IP address has been
recently increased. Therefore, if the organization thinks that they will be using a separate
IP address then they would have to pay a lot of money to buy the IP (Monsanto Et Al.
2013).
Security – If there were, a use of a single IP in the organization then there would be free
flowing of the packets and requests through the routers. Any system control attempts and
spams are free to move through the network (Monsanto et al. 2013).
Question 3
Part A
I.
Distance Vector routing – each node in the network virtually constructs a one
dimensional array which consists of the cost or distance which has to be incurred for
sending a packet to the neighboring node. All the nodes know it the cost, which has to be
incurred for sending the packet to the node. Any node, which is inaccessible, is assign an
infinite cost (Forouzan and Hill 2006).
Link-State routing – there is no creation of any matrix for the cost which is to be incurred
for the transmission of data. In this method, all the nodes the cost needed of the
immediate neighboring node. If all the nodes know this kind of knowledge then the whole
network will be able to transfer packets within the network (Hoque et al. 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
II.
For fast convergence: Link state Routing will be suitable for this method as the cost
calculation of all the nodes need not be done during the establishment of the connection.
Only the cost of the neighboring nodes needs to be known which would make the
transmission to be faster (Hoque et al. 2013).
For Less traffic: Distance vector routing can be used for less traffic as the transmitter
node will know the cost of sending a packet to any node. This will help the transmitter to
send the node directly to the node without the interference from the other nodes (Goyal et
al. 2013).
Part B
I. Two advantages of using DHCPv6 auto configuration over the use of DHCPv4:
Cost Effective because the use of DHCPv6 provides more number of IP addresses than
the DHCPv4. This would help in better connectivity with the computer. The DNS would
not become a headache to be changed (Forouzan and Hill 2006).
Suitable for wireless networks as every interference has link local address, which would
help in correct connection between the workstations and the server.
II. The benefit of using auto configuration is that the client who is connected to a
network can check to see if the provided IP were there in the network. If it is
found to be present then the auto configuration, change the IP for up to 10 times to
fit the network. This will become helpful for the clients to make a network of
connections easily. Even if the connection is set to user configuration then also the
IP will be able to be changed automatically to fit in to thee network (Doi and
Gillmore 2016).
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
II.
For fast convergence: Link state Routing will be suitable for this method as the cost
calculation of all the nodes need not be done during the establishment of the connection.
Only the cost of the neighboring nodes needs to be known which would make the
transmission to be faster (Hoque et al. 2013).
For Less traffic: Distance vector routing can be used for less traffic as the transmitter
node will know the cost of sending a packet to any node. This will help the transmitter to
send the node directly to the node without the interference from the other nodes (Goyal et
al. 2013).
Part B
I. Two advantages of using DHCPv6 auto configuration over the use of DHCPv4:
Cost Effective because the use of DHCPv6 provides more number of IP addresses than
the DHCPv4. This would help in better connectivity with the computer. The DNS would
not become a headache to be changed (Forouzan and Hill 2006).
Suitable for wireless networks as every interference has link local address, which would
help in correct connection between the workstations and the server.
II. The benefit of using auto configuration is that the client who is connected to a
network can check to see if the provided IP were there in the network. If it is
found to be present then the auto configuration, change the IP for up to 10 times to
fit the network. This will become helpful for the clients to make a network of
connections easily. Even if the connection is set to user configuration then also the
IP will be able to be changed automatically to fit in to thee network (Doi and
Gillmore 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
References
Doi, Y. and Gillmore, M., 2016. Multicast Protocol for Low-Power and Lossy Networks
(MPL) Parameter Configuration Option for DHCPv6 (No. RFC 7774).
Forouzan, A. and Hill, G., 2006. Data Communications and Networking, by Behrouz.
Forouzan.
Goyal, M.K., Verma, Y.K., Bassi, P. and Misra, P.K., 2013. Performance Analysis of Ad Hoc
On-Demand Distance Vector Routing and Dynamic Source Routing Using NS2 Simulation.
In Mobile Communication and Power Engineering (pp. 390-396). Springer, Berlin,
Heidelberg.
Hoque, A.K.M., Amin, S.O., Alyyan, A., Zhang, B., Zhang, L. and Wang, L., 2013, August.
NLSR: named-data link state routing protocol. In Proceedings of the 3rd ACM SIGCOMM
workshop on Information-centric networking (pp. 15-20). ACM.
Monsanto, C., Reich, J., Foster, N., Rexford, J. and Walker, D., 2013, April. Composing
Software Defined Networks. In NSDI (Vol. 13, pp. 1-13).
Silva, A.P., Burleigh, S., Hirata, C.M. and Obraczka, K., 2015. A survey on congestion
control for delay and disruption tolerant networks. Ad Hoc Networks, 25, pp.480-494.
Zeeshan, M., Khan, F. and Jan, S.R., 2016. Congestion Detection and Mitigation Protocols
for Wireless Sensor Networks. International Journal of Scientific Research in Computer
Science, Engineering and Information Technology.
COMPUTER NETWORKS - PROBLEM-SOLVING REPORT 2
References
Doi, Y. and Gillmore, M., 2016. Multicast Protocol for Low-Power and Lossy Networks
(MPL) Parameter Configuration Option for DHCPv6 (No. RFC 7774).
Forouzan, A. and Hill, G., 2006. Data Communications and Networking, by Behrouz.
Forouzan.
Goyal, M.K., Verma, Y.K., Bassi, P. and Misra, P.K., 2013. Performance Analysis of Ad Hoc
On-Demand Distance Vector Routing and Dynamic Source Routing Using NS2 Simulation.
In Mobile Communication and Power Engineering (pp. 390-396). Springer, Berlin,
Heidelberg.
Hoque, A.K.M., Amin, S.O., Alyyan, A., Zhang, B., Zhang, L. and Wang, L., 2013, August.
NLSR: named-data link state routing protocol. In Proceedings of the 3rd ACM SIGCOMM
workshop on Information-centric networking (pp. 15-20). ACM.
Monsanto, C., Reich, J., Foster, N., Rexford, J. and Walker, D., 2013, April. Composing
Software Defined Networks. In NSDI (Vol. 13, pp. 1-13).
Silva, A.P., Burleigh, S., Hirata, C.M. and Obraczka, K., 2015. A survey on congestion
control for delay and disruption tolerant networks. Ad Hoc Networks, 25, pp.480-494.
Zeeshan, M., Khan, F. and Jan, S.R., 2016. Congestion Detection and Mitigation Protocols
for Wireless Sensor Networks. International Journal of Scientific Research in Computer
Science, Engineering and Information Technology.

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



