CO4509 - Computer Security: VM Image Security Evaluation Report
VerifiedAdded on 2022/12/23
|17
|3603
|52
Report
AI Summary
This report presents a comprehensive security evaluation of a provided VMware virtual machine image, focusing on the assessment of security vulnerabilities within the system. The investigation includes the installation of VMware and the exploration of the VM image, identifying potential security issues through various methods. The report details the process of investigating system security, utilizing security assessment tools and techniques to uncover weaknesses. The findings are presented, including the discovery of default credentials and other security flaws. Based on the investigation, a detailed proposal for securing the system is provided, encompassing recommendations such as setting strong passwords, implementing disk encryption, ensuring automatic security updates, hardening the web server, securing SSH, and managing user accounts effectively. The report aims to provide a complete overview of the security of the system, providing insights and actionable recommendations for enhancing its overall security posture. The report is a response to the assignment brief of CO4509 Computer Security module at the University of Central Lancashire.

Computer Security
Student Name:
Student ID:
Date of Submission:
Student Name:
Student ID:
Date of Submission:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Project Overview and Aim............................................................................................................1
2. Installation of VMware..................................................................................................................1
3. Investigation of the System Security.............................................................................................6
4. Obtained Results..........................................................................................................................11
5. Proposal: System Security for Ubuntu 18.04...............................................................................13
References...........................................................................................................................................15
1. Project Overview and Aim............................................................................................................1
2. Installation of VMware..................................................................................................................1
3. Investigation of the System Security.............................................................................................6
4. Obtained Results..........................................................................................................................11
5. Proposal: System Security for Ubuntu 18.04...............................................................................13
References...........................................................................................................................................15

1. Project Overview and Aim
In this era of technology, system security is highly essential. System security issues can
occur due to various reasons. The following report aims to reveal the insight behind these
reasons and solution for the issues. The basic things to understand the context of this report
requires understanding the Virtual Machine (VM), which is defined as an impression of a PC
or desktop that relies upon the computer engineering and gives the physical Computer's
functionality (Bento et al., 2019).
VMware Workstation helps the users to enable and install Virtual OS on a single
physical machine, and simultaneously utilize them with the original machine.In an enterprise,
if the desktops are managed using the VMware View, it benefits by increasing the security,
reliability, provides hardware independence, and increases the convenience too. It provides
restrictions to access the data and the sensitive data could be protected from being copied
onto a remote employee's home computer.
The context of this report depends on two firms and they are:
1) Widgets Inc. and
2) Benny Vandergast Inc.
Widgets Inc. facilitates with virtual machine images, though Benny Vandergast Inc. has
given a VMware to try for security reasons and it is expected to be utilized for the new web-
based electronic store.
The general view point of this report is security evaluation for the given VM images. In
this way, different security angles will be assessed and tried, to observe different security
issues. The assessment is suggested to be completed with the help of some exceptional
security assessment tools.In Security evaluation, the VM image files will be evaluated with
the following sections:
Investigation of the System security.
Usage and applying the system security tool.
Obtaining the results.
Proposal for system security.
2. Installation of VMware
This section presents the installation of VMware.
Thesteps required to install the VMware includes:
1
In this era of technology, system security is highly essential. System security issues can
occur due to various reasons. The following report aims to reveal the insight behind these
reasons and solution for the issues. The basic things to understand the context of this report
requires understanding the Virtual Machine (VM), which is defined as an impression of a PC
or desktop that relies upon the computer engineering and gives the physical Computer's
functionality (Bento et al., 2019).
VMware Workstation helps the users to enable and install Virtual OS on a single
physical machine, and simultaneously utilize them with the original machine.In an enterprise,
if the desktops are managed using the VMware View, it benefits by increasing the security,
reliability, provides hardware independence, and increases the convenience too. It provides
restrictions to access the data and the sensitive data could be protected from being copied
onto a remote employee's home computer.
The context of this report depends on two firms and they are:
1) Widgets Inc. and
2) Benny Vandergast Inc.
Widgets Inc. facilitates with virtual machine images, though Benny Vandergast Inc. has
given a VMware to try for security reasons and it is expected to be utilized for the new web-
based electronic store.
The general view point of this report is security evaluation for the given VM images. In
this way, different security angles will be assessed and tried, to observe different security
issues. The assessment is suggested to be completed with the help of some exceptional
security assessment tools.In Security evaluation, the VM image files will be evaluated with
the following sections:
Investigation of the System security.
Usage and applying the system security tool.
Obtaining the results.
Proposal for system security.
2. Installation of VMware
This section presents the installation of VMware.
Thesteps required to install the VMware includes:
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
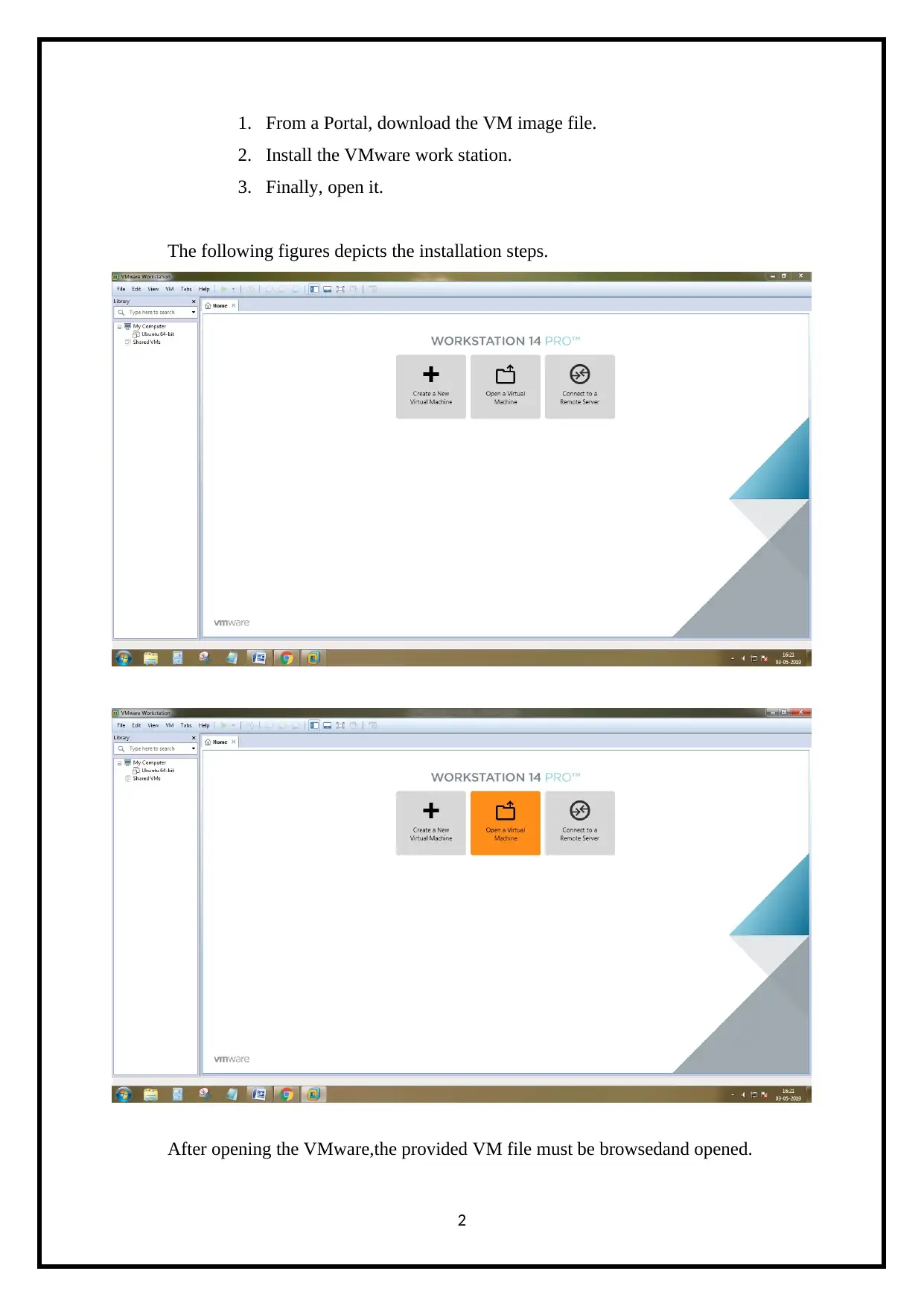
1. From a Portal, download the VM image file.
2. Install the VMware work station.
3. Finally, open it.
The following figures depicts the installation steps.
After opening the VMware,the provided VM file must be browsedand opened.
2
2. Install the VMware work station.
3. Finally, open it.
The following figures depicts the installation steps.
After opening the VMware,the provided VM file must be browsedand opened.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
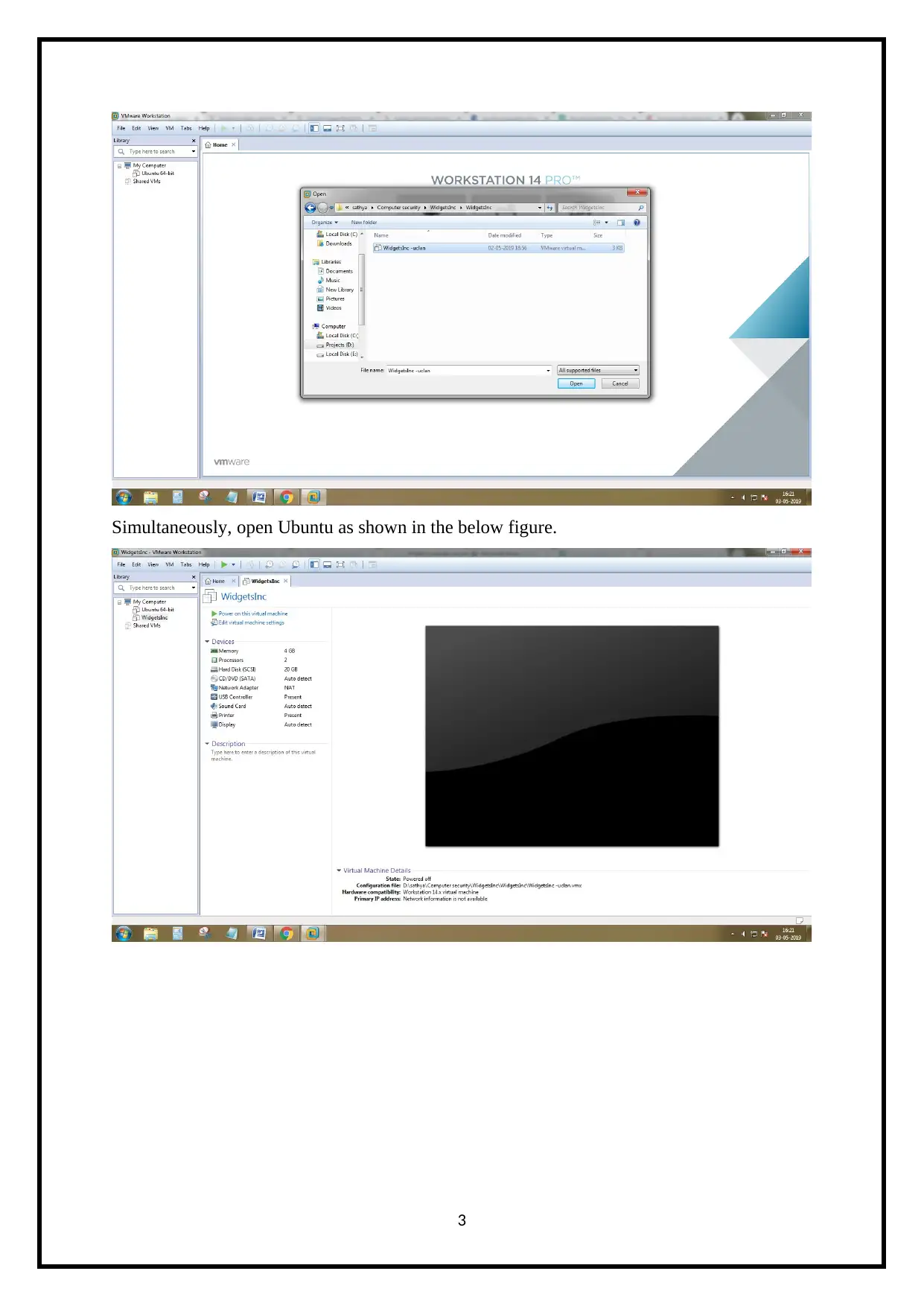
Simultaneously, open Ubuntu as shown in the below figure.
3
3
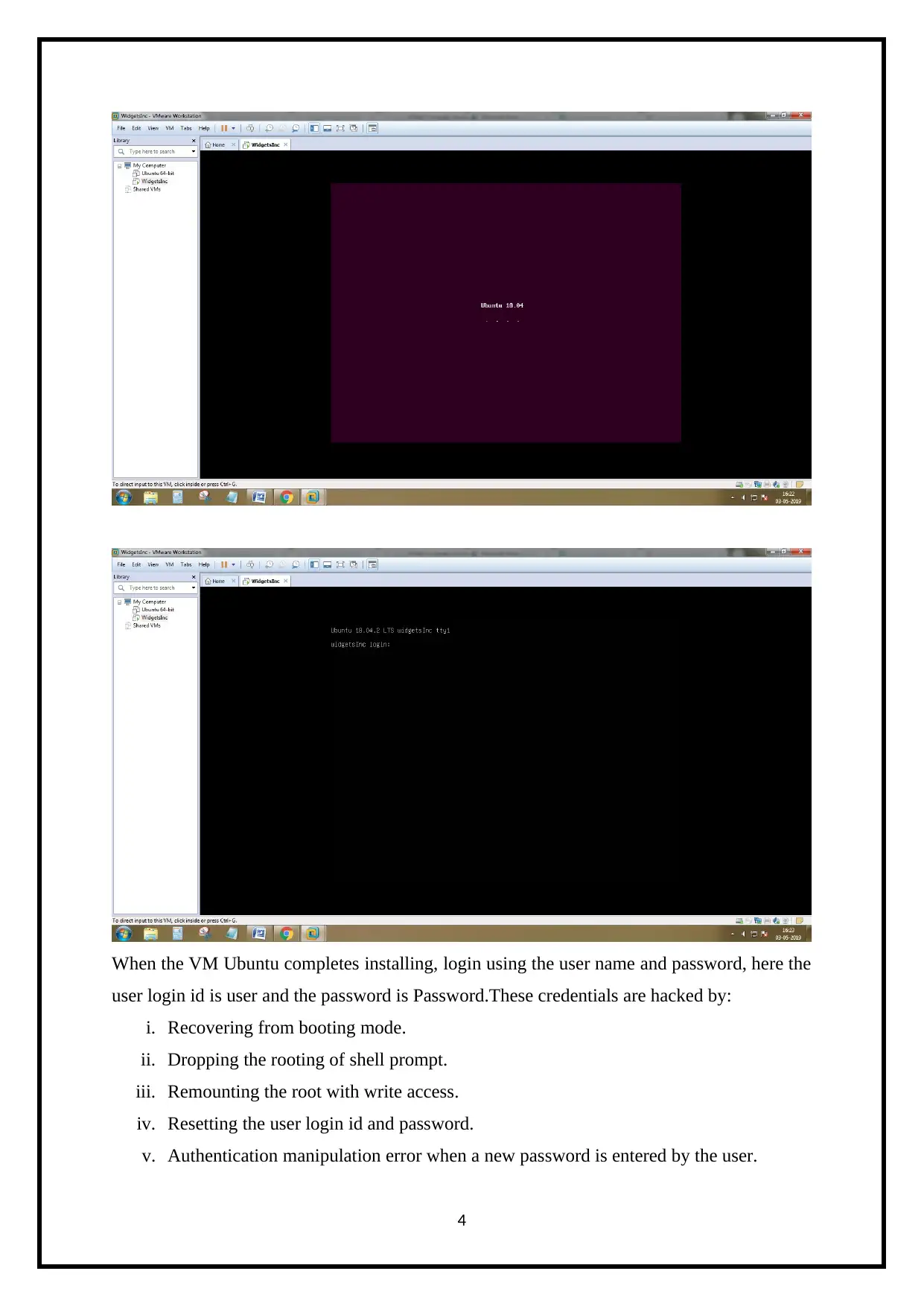
When the VM Ubuntu completes installing, login using the user name and password, here the
user login id is user and the password is Password.These credentials are hacked by:
i. Recovering from booting mode.
ii. Dropping the rooting of shell prompt.
iii. Remounting the root with write access.
iv. Resetting the user login id and password.
v. Authentication manipulation error when a new password is entered by the user.
4
user login id is user and the password is Password.These credentials are hacked by:
i. Recovering from booting mode.
ii. Dropping the rooting of shell prompt.
iii. Remounting the root with write access.
iv. Resetting the user login id and password.
v. Authentication manipulation error when a new password is entered by the user.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

It is common to get error messages as the file system is mounted using “read access
only.” The file system can be modified and remounted. Then, it must resetthe password and
using the new password when the user tries to login, it will have to face the following
security issues on the Ubuntu VM:
i. Problems of encrypt data communication.
ii. Problems of opening the SSL.
iii. Network services problems on the VM instance.
iv. Problems of malware.
v. Problems of Web server hardening
vi. Security patches
vii. Problems of Password setting.
viii. Problems of data backup.
3. Investigation of the System Security
A system’s security evaluation process is investigated in this section where a given
virtual machine image file is used, this area reveals the insights of the evaluation of VM. The
assessment of security is used to lookat a system to choose the system compliance based on
particular aspects like security norms, and model. It is viewing the system's behaviour by
attempting to enter the system. In Ubuntu 18.04, the given VM image file, security evaluation
is done based on the global standard to get the computer security affirmation. It is basically a
certificate thatshows the met satisfactions. The specification of security requirementsare used
to show the security targets to be met. The security assessment is used to do changes in the
configuration and utilizes the additional packages (Eka Pratama and Wiradarma, 2018).
Next, it checks the configuration manual to unveil how to set-up the evaluated
configuration, to give the necessary information to the administrator and user. Security
evaluation utilizes full disk encryption to increase the data affirmation in a system. It
empowers the users to encryption and guarantee data assurance. It additionally completes the
5
only.” The file system can be modified and remounted. Then, it must resetthe password and
using the new password when the user tries to login, it will have to face the following
security issues on the Ubuntu VM:
i. Problems of encrypt data communication.
ii. Problems of opening the SSL.
iii. Network services problems on the VM instance.
iv. Problems of malware.
v. Problems of Web server hardening
vi. Security patches
vii. Problems of Password setting.
viii. Problems of data backup.
3. Investigation of the System Security
A system’s security evaluation process is investigated in this section where a given
virtual machine image file is used, this area reveals the insights of the evaluation of VM. The
assessment of security is used to lookat a system to choose the system compliance based on
particular aspects like security norms, and model. It is viewing the system's behaviour by
attempting to enter the system. In Ubuntu 18.04, the given VM image file, security evaluation
is done based on the global standard to get the computer security affirmation. It is basically a
certificate thatshows the met satisfactions. The specification of security requirementsare used
to show the security targets to be met. The security assessment is used to do changes in the
configuration and utilizes the additional packages (Eka Pratama and Wiradarma, 2018).
Next, it checks the configuration manual to unveil how to set-up the evaluated
configuration, to give the necessary information to the administrator and user. Security
evaluation utilizes full disk encryption to increase the data affirmation in a system. It
empowers the users to encryption and guarantee data assurance. It additionally completes the
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
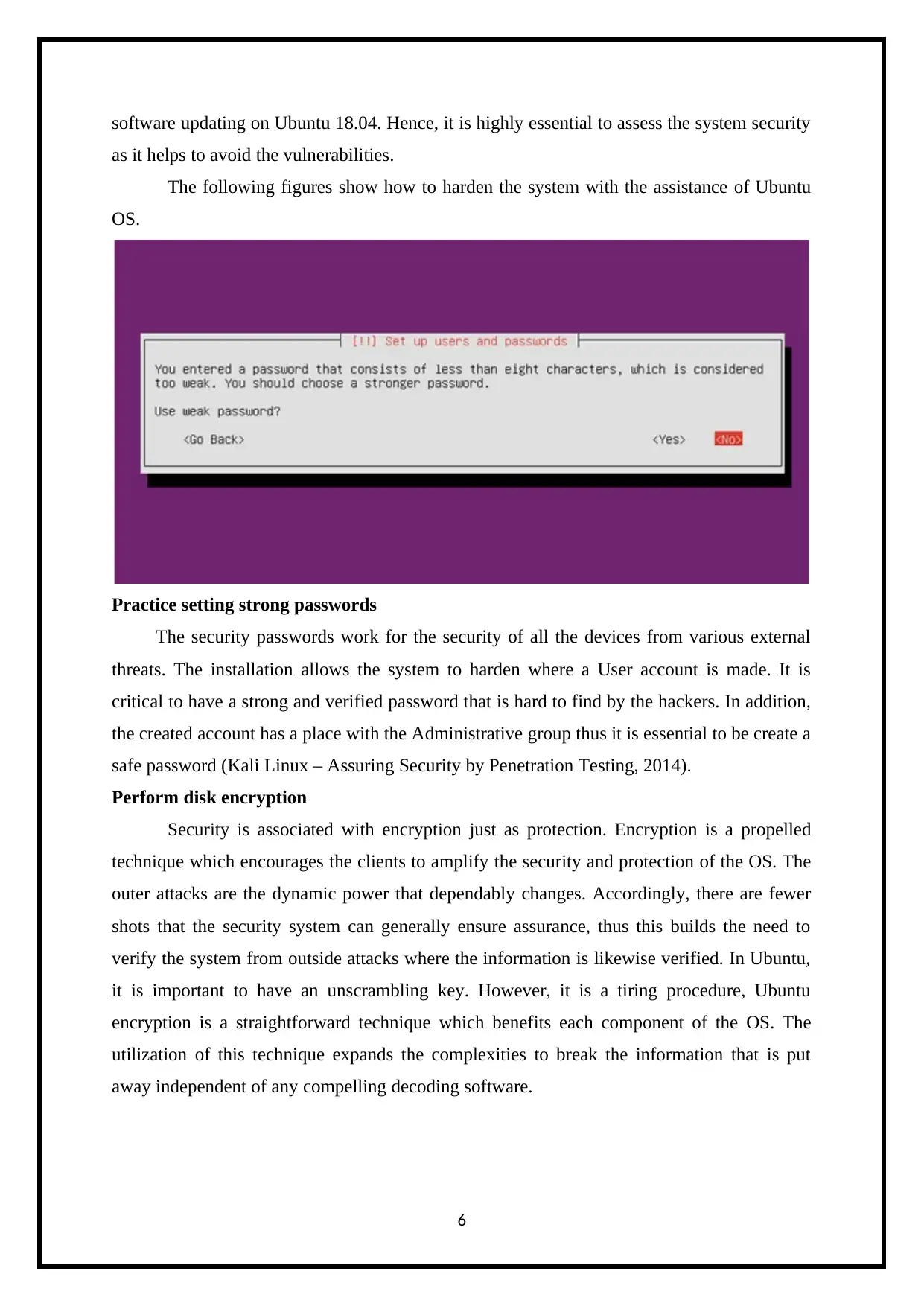
software updating on Ubuntu 18.04. Hence, it is highly essential to assess the system security
as it helps to avoid the vulnerabilities.
The following figures show how to harden the system with the assistance of Ubuntu
OS.
Practice setting strong passwords
The security passwords work for the security of all the devices from various external
threats. The installation allows the system to harden where a User account is made. It is
critical to have a strong and verified password that is hard to find by the hackers. In addition,
the created account has a place with the Administrative group thus it is essential to be create a
safe password (Kali Linux – Assuring Security by Penetration Testing, 2014).
Perform disk encryption
Security is associated with encryption just as protection. Encryption is a propelled
technique which encourages the clients to amplify the security and protection of the OS. The
outer attacks are the dynamic power that dependably changes. Accordingly, there are fewer
shots that the security system can generally ensure assurance, thus this builds the need to
verify the system from outside attacks where the information is likewise verified. In Ubuntu,
it is important to have an unscrambling key. However, it is a tiring procedure, Ubuntu
encryption is a straightforward technique which benefits each component of the OS. The
utilization of this technique expands the complexities to break the information that is put
away independent of any compelling decoding software.
6
as it helps to avoid the vulnerabilities.
The following figures show how to harden the system with the assistance of Ubuntu
OS.
Practice setting strong passwords
The security passwords work for the security of all the devices from various external
threats. The installation allows the system to harden where a User account is made. It is
critical to have a strong and verified password that is hard to find by the hackers. In addition,
the created account has a place with the Administrative group thus it is essential to be create a
safe password (Kali Linux – Assuring Security by Penetration Testing, 2014).
Perform disk encryption
Security is associated with encryption just as protection. Encryption is a propelled
technique which encourages the clients to amplify the security and protection of the OS. The
outer attacks are the dynamic power that dependably changes. Accordingly, there are fewer
shots that the security system can generally ensure assurance, thus this builds the need to
verify the system from outside attacks where the information is likewise verified. In Ubuntu,
it is important to have an unscrambling key. However, it is a tiring procedure, Ubuntu
encryption is a straightforward technique which benefits each component of the OS. The
utilization of this technique expands the complexities to break the information that is put
away independent of any compelling decoding software.
6
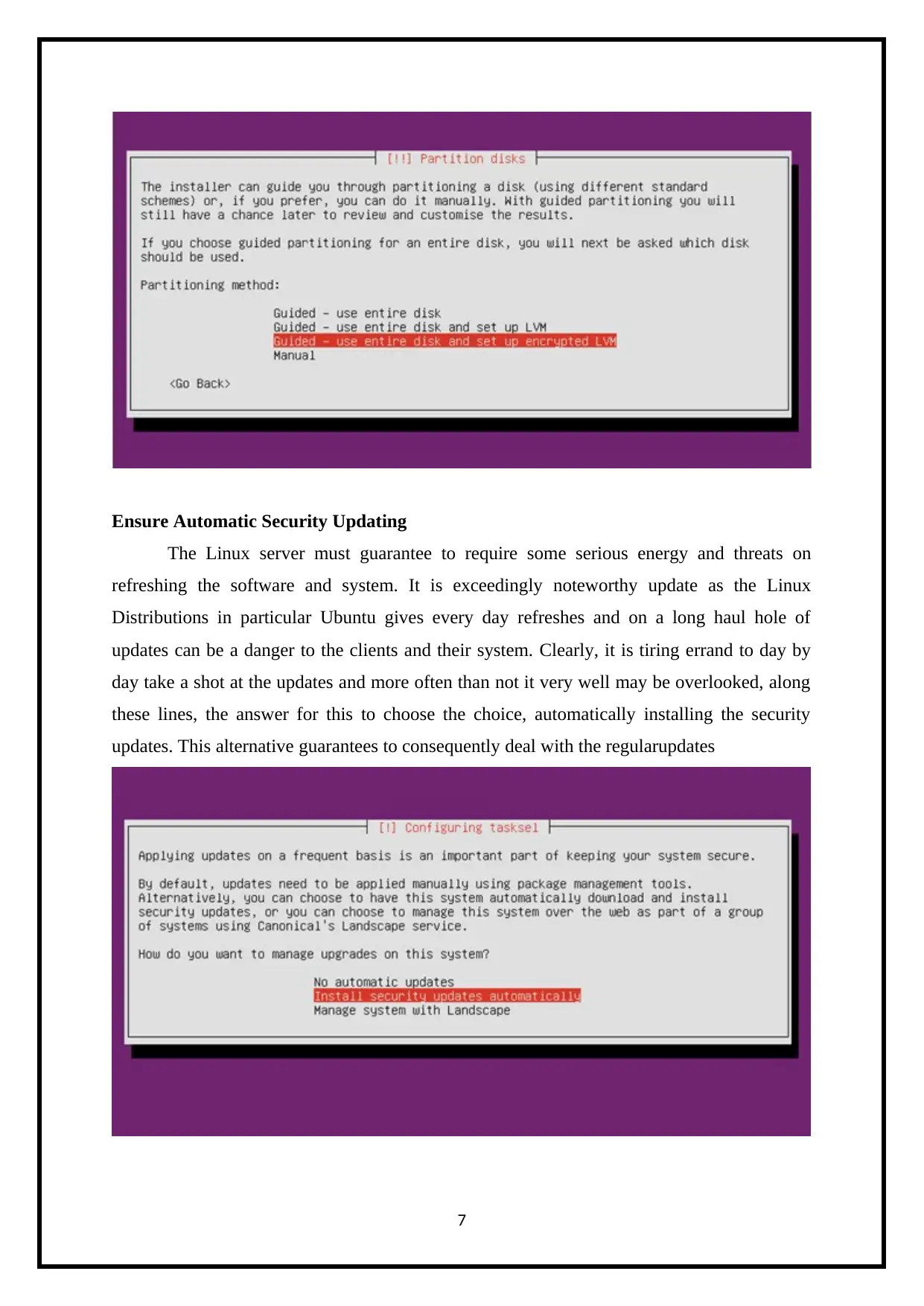
Ensure Automatic Security Updating
The Linux server must guarantee to require some serious energy and threats on
refreshing the software and system. It is exceedingly noteworthy update as the Linux
Distributions in particular Ubuntu gives every day refreshes and on a long haul hole of
updates can be a danger to the clients and their system. Clearly, it is tiring errand to day by
day take a shot at the updates and more often than not it very well may be overlooked, along
these lines, the answer for this to choose the choice, automatically installing the security
updates. This alternative guarantees to consequently deal with the regularupdates
7
The Linux server must guarantee to require some serious energy and threats on
refreshing the software and system. It is exceedingly noteworthy update as the Linux
Distributions in particular Ubuntu gives every day refreshes and on a long haul hole of
updates can be a danger to the clients and their system. Clearly, it is tiring errand to day by
day take a shot at the updates and more often than not it very well may be overlooked, along
these lines, the answer for this to choose the choice, automatically installing the security
updates. This alternative guarantees to consequently deal with the regularupdates
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Update the Software
The system software shows an automatic method, which the user selects. Irrespective
of the fact that there exists a manual alternative for updating the software, but the users
prefers to select an automatic or the auto option.
Hardening the Web server
The procedure of Web Server Hardening improves the security of a server with
various ways that outcomes in profoundly verified server working foundation. The reason is
propelled security estimates which are utilized when the server hardening process
happens.The Secure Sockets Layer (SSL) and the TLS indicates a standard method that
verifies the web connection and protects the sensitive information which must be shared
between a couple or more systems, at that point, it keeps the programmers from changing the
exchanged information and an individual’s personal details. In a Linux system, SSL and TLS
must be streamlined with the assistance of server hardening and deals withsystem security
and systemspeed.
Selecting Certificates from the recognized Sources
Get certification from specialized and reputable servicesfor online security.
Optimizing TLS Handshake
Utilization of "three-way" handshake guarantees to utilize the typical TCP
connection,, for setting up a safe connection.
Enabling the Persistent Connections
In a single connection, numerous requests can be made with a persistent
connection. The new SSL connection is required when an individual wish to
visit a site that is secure when contrasted with multiple times in the only a
couple of minutes. Utilization of a diligent connection, only for a single time
then it can start the SSL connection that evacuates the required extra additional
handshakes.
Use of CDN
The websites influence CDNs to propel its page load speed. This aide in sending and
makes the CDN advance the SSL/TLS displays. Guarantee to manage the mutual estimates
that are recorded in the earlier entry identified with TLS handshake and industrious
connection foundation. Using the latest SSL form similarly as TLS which must be sought
after reliably. The reason for utilizing new forms are the insufficient old adaptations, which
are uncommonly defenceless against the viruses and bugs. There must be an ability to
8
The system software shows an automatic method, which the user selects. Irrespective
of the fact that there exists a manual alternative for updating the software, but the users
prefers to select an automatic or the auto option.
Hardening the Web server
The procedure of Web Server Hardening improves the security of a server with
various ways that outcomes in profoundly verified server working foundation. The reason is
propelled security estimates which are utilized when the server hardening process
happens.The Secure Sockets Layer (SSL) and the TLS indicates a standard method that
verifies the web connection and protects the sensitive information which must be shared
between a couple or more systems, at that point, it keeps the programmers from changing the
exchanged information and an individual’s personal details. In a Linux system, SSL and TLS
must be streamlined with the assistance of server hardening and deals withsystem security
and systemspeed.
Selecting Certificates from the recognized Sources
Get certification from specialized and reputable servicesfor online security.
Optimizing TLS Handshake
Utilization of "three-way" handshake guarantees to utilize the typical TCP
connection,, for setting up a safe connection.
Enabling the Persistent Connections
In a single connection, numerous requests can be made with a persistent
connection. The new SSL connection is required when an individual wish to
visit a site that is secure when contrasted with multiple times in the only a
couple of minutes. Utilization of a diligent connection, only for a single time
then it can start the SSL connection that evacuates the required extra additional
handshakes.
Use of CDN
The websites influence CDNs to propel its page load speed. This aide in sending and
makes the CDN advance the SSL/TLS displays. Guarantee to manage the mutual estimates
that are recorded in the earlier entry identified with TLS handshake and industrious
connection foundation. Using the latest SSL form similarly as TLS which must be sought
after reliably. The reason for utilizing new forms are the insufficient old adaptations, which
are uncommonly defenceless against the viruses and bugs. There must be an ability to
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

perceive certain viewpoints regarding what is the requirement, for instance, the general
system or the Security System's execution for the server. Typical and consistent tests drove
on the approved websites for SSL/TLS must be driven. Guarantee to perceive the parts that
require Performance when contrasted with security and correspondingly check where security
is fundamental than execution. Use the inbuilt development tools, for example, system
security audit in the Linux System.
User Accounts
The Ubuntu Single Sign-On account can be used to approve the desktop applications.
The production of accounts can be used to access the server. This is basic for the system
administration. The clients absent much pressure can access the servers while using the
system openly by the SCP (Secure Copy) and SSH. The Secure Copy implies the command
line tool that is used to recreate or trade the files starting with one host then onto the next
host. It uses a similar security system, like SSH program.
Risks ofUser Account
Any system in spite of being verified and solid it by and large needs rebooting. Regardless,
we have found that there are a couple of systems that continually run and work relentlessly.
Additionally, the investigated system ends up being helpless against the threats that were
recently settled inside a system either local or the outside threats. The actualuser must know
about the downsides to understand the issues. Here, the activity of system hardening is basic
and critical. Every system is prescribed to lead system hardening, which can slaughter such
defaults and issues that happen in any system (greghub.com, 2019).
Open SSH security and System Hardening
In a Linux system, to guarantee system administration the SSH is prescribed
convention as it is critical for server management. Most of the Linux based systems have this
convention and run based on this. The default setting alludes to the unaltered configuration.
The Linux System hardening is a standout amongst the best way to deal with decrease the
potential system attacks. Consequent to modifying the configuration document it is
fundamental to test the legitimacy before the administration is reloaded. Then, constantly
check the SSH's status before the sending. What's more, frequently a well-recorded way to
deal with arrangement with the system check supports to make things simple. The SSH
configuration test guarantees and perceive the system Functioning and Non-Functioning.
Encrypting all the traffic gives extra security from the network sniffing and diverse attacks.
Also, it is accessible in various stages. Similarly, it is conceivable to execute the SSH port
9
system or the Security System's execution for the server. Typical and consistent tests drove
on the approved websites for SSL/TLS must be driven. Guarantee to perceive the parts that
require Performance when contrasted with security and correspondingly check where security
is fundamental than execution. Use the inbuilt development tools, for example, system
security audit in the Linux System.
User Accounts
The Ubuntu Single Sign-On account can be used to approve the desktop applications.
The production of accounts can be used to access the server. This is basic for the system
administration. The clients absent much pressure can access the servers while using the
system openly by the SCP (Secure Copy) and SSH. The Secure Copy implies the command
line tool that is used to recreate or trade the files starting with one host then onto the next
host. It uses a similar security system, like SSH program.
Risks ofUser Account
Any system in spite of being verified and solid it by and large needs rebooting. Regardless,
we have found that there are a couple of systems that continually run and work relentlessly.
Additionally, the investigated system ends up being helpless against the threats that were
recently settled inside a system either local or the outside threats. The actualuser must know
about the downsides to understand the issues. Here, the activity of system hardening is basic
and critical. Every system is prescribed to lead system hardening, which can slaughter such
defaults and issues that happen in any system (greghub.com, 2019).
Open SSH security and System Hardening
In a Linux system, to guarantee system administration the SSH is prescribed
convention as it is critical for server management. Most of the Linux based systems have this
convention and run based on this. The default setting alludes to the unaltered configuration.
The Linux System hardening is a standout amongst the best way to deal with decrease the
potential system attacks. Consequent to modifying the configuration document it is
fundamental to test the legitimacy before the administration is reloaded. Then, constantly
check the SSH's status before the sending. What's more, frequently a well-recorded way to
deal with arrangement with the system check supports to make things simple. The SSH
configuration test guarantees and perceive the system Functioning and Non-Functioning.
Encrypting all the traffic gives extra security from the network sniffing and diverse attacks.
Also, it is accessible in various stages. Similarly, it is conceivable to execute the SSH port
9

sending to give information security. The SSH server is commonly used to help server
authentication. It is sheltered yet we can regardless complete a couple of changes for cutting
edge security. It suits the security stages like Ubuntu Security, where the system is protected
from any potential attacks.The following are the main features which are essential for setting
up the SSH security:
a) Utilize different port other than 22 (i.e., the default port)
b) Disable the direct root login.
c) Only use the Protocol SSH 2.
d) Utilize public keys in place of passwords.
e) Use of X11 forwarding
f) Disable the empty passwords.
g) Enable two-factor authentication.
h) Use strong passwords and passphrase for SSH users/keys
i) Disable port forwarding
j) Configure an Idle Timeout Interval.
k) Make any required changes to the remote system.
l) Restrict the SSH logins to a particular IP address.
Ubuntu's system security starts with software hardening and after that the other
connected applications. Ubuntu's system security begins with system software hardening and
after that, the related applications pursued by the used fundamental software. The best
arrangement is to implement day by day and on-time filters with vital updates for the system,
which keeps its working viable. For SSH security, the fundamental tool incorporates Lynis
software. It is an audit tool which does testing and from Unix-based systems, it accumulates
security information. It is anything but difficult to utilize and gives the security answers
rapidly, to take immediate steps.
4. Obtained Results
Coming up next are the outcomes received from the examination by utilizing a system
security tool. On Ubuntu 18.04, Lynis auditing tool is utilized to perform system security. It
is an open source security audit tool, which is beneficial in assessing the security of a VM
system. Based on these highlights, this tool was chosen for the Linux Platform. It is
advantageous for the security experts and system admins to check the system for any security
10
authentication. It is sheltered yet we can regardless complete a couple of changes for cutting
edge security. It suits the security stages like Ubuntu Security, where the system is protected
from any potential attacks.The following are the main features which are essential for setting
up the SSH security:
a) Utilize different port other than 22 (i.e., the default port)
b) Disable the direct root login.
c) Only use the Protocol SSH 2.
d) Utilize public keys in place of passwords.
e) Use of X11 forwarding
f) Disable the empty passwords.
g) Enable two-factor authentication.
h) Use strong passwords and passphrase for SSH users/keys
i) Disable port forwarding
j) Configure an Idle Timeout Interval.
k) Make any required changes to the remote system.
l) Restrict the SSH logins to a particular IP address.
Ubuntu's system security starts with software hardening and after that the other
connected applications. Ubuntu's system security begins with system software hardening and
after that, the related applications pursued by the used fundamental software. The best
arrangement is to implement day by day and on-time filters with vital updates for the system,
which keeps its working viable. For SSH security, the fundamental tool incorporates Lynis
software. It is an audit tool which does testing and from Unix-based systems, it accumulates
security information. It is anything but difficult to utilize and gives the security answers
rapidly, to take immediate steps.
4. Obtained Results
Coming up next are the outcomes received from the examination by utilizing a system
security tool. On Ubuntu 18.04, Lynis auditing tool is utilized to perform system security. It
is an open source security audit tool, which is beneficial in assessing the security of a VM
system. Based on these highlights, this tool was chosen for the Linux Platform. It is
advantageous for the security experts and system admins to check the system for any security
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





