CO4509 - Detailed Report on Memcrashed Vulnerability and Solutions
VerifiedAdded on 2023/04/06
|14
|3197
|498
Report
AI Summary
This report provides a comprehensive analysis of the memcrashed vulnerability, a Distributed Denial-of-Service (DDoS) attack that leverages memcached servers. It begins by explaining the principles of key-value databases and then delves into the specifics of the memcrashed exploit, detailing how attackers amplify traffic to overwhelm targeted victims. The report outlines various mitigation strategies, including memcached hardening, disabling UDP support, utilizing DDoS protection services, and configuring network hardware. Furthermore, it discusses the importance of protecting DNS servers and provides insights into the future impact and effectiveness of memcrashed attacks. The report concludes by emphasizing the need for robust security measures to defend against such vulnerabilities.

Running head: COMPUTER SECURITY
COMPUTER SECURITY
Name of Student
Name of the University
Author’s Note
COMPUTER SECURITY
Name of Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER SECURITY
Table of Contents
Introduction..........................................................................................................................2
Discussion............................................................................................................................2
Principles of key/value databases....................................................................................2
Description of memcrashed exploit.................................................................................3
How does memcrashed work?.........................................................................................4
Solution to the memcrashed exploit................................................................................5
Future importance and effectiveness of memcrashed......................................................8
Conclusion.........................................................................................................................10
References..........................................................................................................................11
Table of Contents
Introduction..........................................................................................................................2
Discussion............................................................................................................................2
Principles of key/value databases....................................................................................2
Description of memcrashed exploit.................................................................................3
How does memcrashed work?.........................................................................................4
Solution to the memcrashed exploit................................................................................5
Future importance and effectiveness of memcrashed......................................................8
Conclusion.........................................................................................................................10
References..........................................................................................................................11

2COMPUTER SECURITY
Introduction
Memcrashed is a process in which memcached is installed in a particular system or a
group of systems and which initiates security against the threat imposed by the memcrashed
attack. The memcached can be defined as a certain memory object system that is utilized in
caching; this process of caching is utilized for increasing the speed of numerous applications of
the dynamic web (Conklin, White & Cothren, 2015). Memcached is an open source; this has
been introduced in order to work with numerous open connections. The first vulnerability that
had been introduced was in the month of February, 2018. In the attack, the attackers had
launched and executed a very powerful amplification attack of DDoS (Egelman & Peer, 2015).
The vulnerability faced at this time had never been faced previously by any organization. This
particular assignment describes the principles followed by the key/value database, it further
discusses the memcrashed exploit and how it takes place. The report also presents some solutions
or countermeasures that can be implemented by the organizations facing memcrashed exploit.
The mentioned points have been presented in details in the discussion part of the assignment.
Discussion
Principles of key/value databases
A key-value database is also known as a key-value store, it is a data storage paradigm is
usually designed for the purpose of storing, managing and retrieving associative arrays. The key-
value store follows various principles; some principles include examining some options like
Bolt, RocksDB, GoLevelIDB and Badger (Hyder & Lung, 2018). Some more opetions hat are
examined include Go, B+ tree, Great read performance, C++, LSM (leveldb), a Better balance of
Introduction
Memcrashed is a process in which memcached is installed in a particular system or a
group of systems and which initiates security against the threat imposed by the memcrashed
attack. The memcached can be defined as a certain memory object system that is utilized in
caching; this process of caching is utilized for increasing the speed of numerous applications of
the dynamic web (Conklin, White & Cothren, 2015). Memcached is an open source; this has
been introduced in order to work with numerous open connections. The first vulnerability that
had been introduced was in the month of February, 2018. In the attack, the attackers had
launched and executed a very powerful amplification attack of DDoS (Egelman & Peer, 2015).
The vulnerability faced at this time had never been faced previously by any organization. This
particular assignment describes the principles followed by the key/value database, it further
discusses the memcrashed exploit and how it takes place. The report also presents some solutions
or countermeasures that can be implemented by the organizations facing memcrashed exploit.
The mentioned points have been presented in details in the discussion part of the assignment.
Discussion
Principles of key/value databases
A key-value database is also known as a key-value store, it is a data storage paradigm is
usually designed for the purpose of storing, managing and retrieving associative arrays. The key-
value store follows various principles; some principles include examining some options like
Bolt, RocksDB, GoLevelIDB and Badger (Hyder & Lung, 2018). Some more opetions hat are
examined include Go, B+ tree, Great read performance, C++, LSM (leveldb), a Better balance of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMPUTER SECURITY
write or read performance, cgo and Wisckey, these options are included under the previously
mentioned options (Egelman & Peer, 2015). Some other principals include maintaining
simplicity; it follows the rule of utilizing numerous simple algorithms along with some simple
data structures for utilizing a key-value database into operations (O’Hare, 2018). One more
principal includes explicating. It sets out in building a key value database for certain purposes
and not for the purpose of delivering a specific generalized solution.
Description of memcrashed exploit
A memcached attack is a concept under the Distributed Denial-of-service (DDoS) attack.
This can be described as a cyber attack where a specific attacker attempts in overloading a
targeted victim using a specific amount of internet traffic. (Peltier, 2016) After that the attacker
spoofs various requests to the UDP memcached server that is vulnerable. It then floods the
victim that has been targeted with a certain amount of internet traffic that potentially overwhelms
the resources of the victim (Peltier, 2016). When the infrastructure of the target is overwhelmed,
it cannot process new requests and the traffic that is regular in nature is not allowed to access the
resource present on the internet, this as a result causes denial-of-service. The involvement of the
memcached servers in the field of DDoS attacks has been simple as well as effective; in this
attack the attacker sends a specific request to the server that has been targeted by them on the
port 11211 which then spoofs the victim’s IP address (Slocombe, 2018). The request that has
been sent to the server is then composed into several bytes whereas the response received might
be tens or thousands times bigger in size. This results in an amplification attack that is estimated
to be around 51,200 times bigger than the size of the request that has been provided initially.
write or read performance, cgo and Wisckey, these options are included under the previously
mentioned options (Egelman & Peer, 2015). Some other principals include maintaining
simplicity; it follows the rule of utilizing numerous simple algorithms along with some simple
data structures for utilizing a key-value database into operations (O’Hare, 2018). One more
principal includes explicating. It sets out in building a key value database for certain purposes
and not for the purpose of delivering a specific generalized solution.
Description of memcrashed exploit
A memcached attack is a concept under the Distributed Denial-of-service (DDoS) attack.
This can be described as a cyber attack where a specific attacker attempts in overloading a
targeted victim using a specific amount of internet traffic. (Peltier, 2016) After that the attacker
spoofs various requests to the UDP memcached server that is vulnerable. It then floods the
victim that has been targeted with a certain amount of internet traffic that potentially overwhelms
the resources of the victim (Peltier, 2016). When the infrastructure of the target is overwhelmed,
it cannot process new requests and the traffic that is regular in nature is not allowed to access the
resource present on the internet, this as a result causes denial-of-service. The involvement of the
memcached servers in the field of DDoS attacks has been simple as well as effective; in this
attack the attacker sends a specific request to the server that has been targeted by them on the
port 11211 which then spoofs the victim’s IP address (Slocombe, 2018). The request that has
been sent to the server is then composed into several bytes whereas the response received might
be tens or thousands times bigger in size. This results in an amplification attack that is estimated
to be around 51,200 times bigger than the size of the request that has been provided initially.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER SECURITY
How does memcrashed work?
Memcached attack operates in a similar manner to other DDoS amplification attacks like
NTP amplification as well as DNS amplification. This attack operates with the help of sending
various spoof requests to a specific server that is vulnerable in nature, this server then replies
with a huge amount of information that the request that had been sent initially (Sahay, Blanc &
Zhang, 2015). This magnifies the volume of traffic. An example of memcached attack can be
considered a case where someone calls up a specific restaurant and says he would like to order
one of every item present in the menu of that restaurant, the caller then requests the restaurant to
confirm the order in a specific number, in this case the number provided is the victim of the
attack (Stallings, 2017). After a while the restaurant calls and provides him the entire data
regarding the order that has been made to a person who did not request for the information. A
specific memcached attack can be implemented using various steps, the steps include
1. The attacker implants a huge amount of payload of information on the
memcached server that is exposed (Slocombe, 2018).
2. The attacker then spoofs the HTTP GET request along with the particular IP
address of a specific victim who has been targeted.
3. The memcached server which receives a request, that tried to be helpful after
responding to the request, sends a huge reply to the specific target (Slocombe,
2018).
4. On the surrounding infrastructure or the targeted server is not able to process the
huge amount of information that has been initiated from the server of memcached
(Tatar, Konoth & Athanasopoulos, 2018). This results in overload as well as
denial of service to any other legitimate request.
How does memcrashed work?
Memcached attack operates in a similar manner to other DDoS amplification attacks like
NTP amplification as well as DNS amplification. This attack operates with the help of sending
various spoof requests to a specific server that is vulnerable in nature, this server then replies
with a huge amount of information that the request that had been sent initially (Sahay, Blanc &
Zhang, 2015). This magnifies the volume of traffic. An example of memcached attack can be
considered a case where someone calls up a specific restaurant and says he would like to order
one of every item present in the menu of that restaurant, the caller then requests the restaurant to
confirm the order in a specific number, in this case the number provided is the victim of the
attack (Stallings, 2017). After a while the restaurant calls and provides him the entire data
regarding the order that has been made to a person who did not request for the information. A
specific memcached attack can be implemented using various steps, the steps include
1. The attacker implants a huge amount of payload of information on the
memcached server that is exposed (Slocombe, 2018).
2. The attacker then spoofs the HTTP GET request along with the particular IP
address of a specific victim who has been targeted.
3. The memcached server which receives a request, that tried to be helpful after
responding to the request, sends a huge reply to the specific target (Slocombe,
2018).
4. On the surrounding infrastructure or the targeted server is not able to process the
huge amount of information that has been initiated from the server of memcached
(Tatar, Konoth & Athanasopoulos, 2018). This results in overload as well as
denial of service to any other legitimate request.
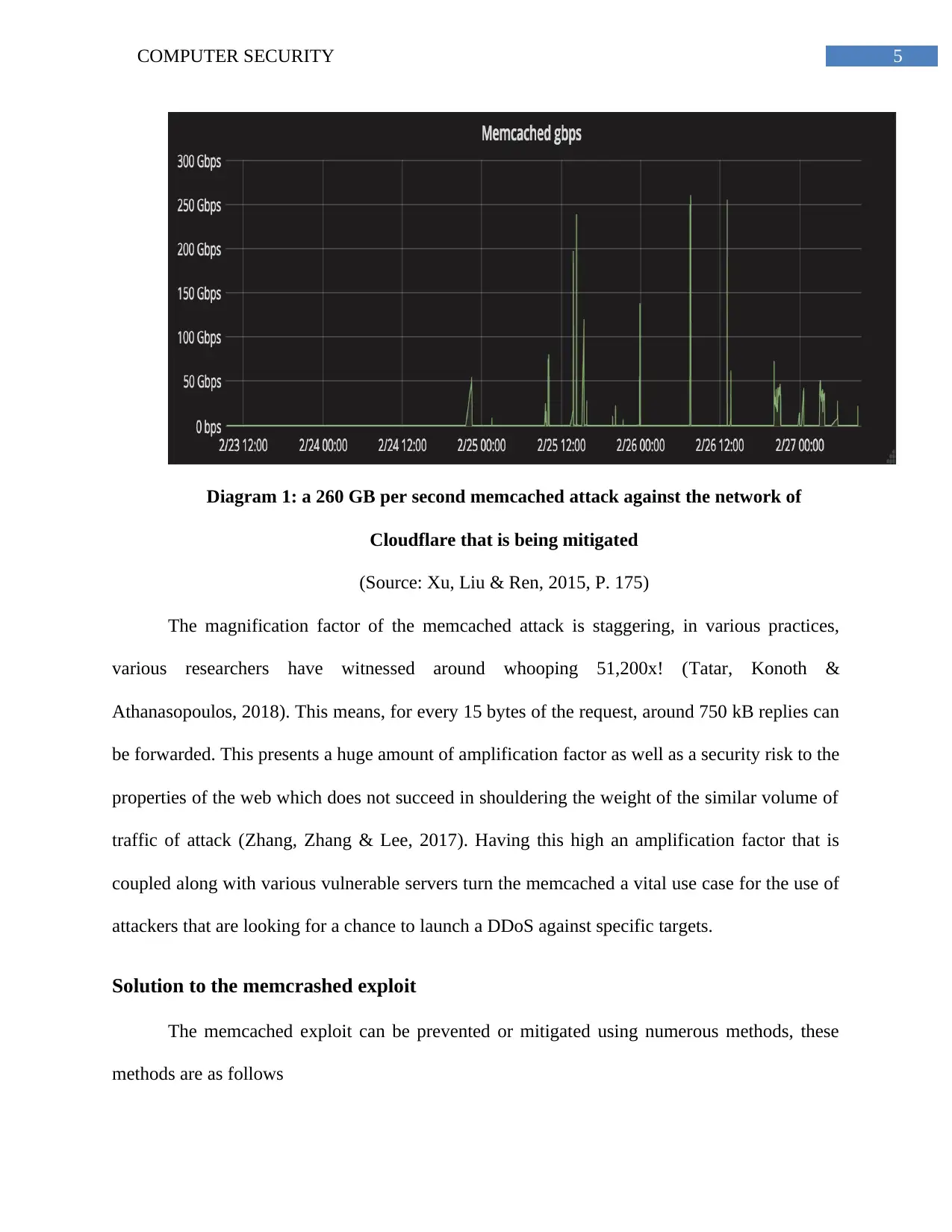
5COMPUTER SECURITY
Diagram 1: a 260 GB per second memcached attack against the network of
Cloudflare that is being mitigated
(Source: Xu, Liu & Ren, 2015, P. 175)
The magnification factor of the memcached attack is staggering, in various practices,
various researchers have witnessed around whooping 51,200x! (Tatar, Konoth &
Athanasopoulos, 2018). This means, for every 15 bytes of the request, around 750 kB replies can
be forwarded. This presents a huge amount of amplification factor as well as a security risk to the
properties of the web which does not succeed in shouldering the weight of the similar volume of
traffic of attack (Zhang, Zhang & Lee, 2017). Having this high an amplification factor that is
coupled along with various vulnerable servers turn the memcached a vital use case for the use of
attackers that are looking for a chance to launch a DDoS against specific targets.
Solution to the memcrashed exploit
The memcached exploit can be prevented or mitigated using numerous methods, these
methods are as follows
Diagram 1: a 260 GB per second memcached attack against the network of
Cloudflare that is being mitigated
(Source: Xu, Liu & Ren, 2015, P. 175)
The magnification factor of the memcached attack is staggering, in various practices,
various researchers have witnessed around whooping 51,200x! (Tatar, Konoth &
Athanasopoulos, 2018). This means, for every 15 bytes of the request, around 750 kB replies can
be forwarded. This presents a huge amount of amplification factor as well as a security risk to the
properties of the web which does not succeed in shouldering the weight of the similar volume of
traffic of attack (Zhang, Zhang & Lee, 2017). Having this high an amplification factor that is
coupled along with various vulnerable servers turn the memcached a vital use case for the use of
attackers that are looking for a chance to launch a DDoS against specific targets.
Solution to the memcrashed exploit
The memcached exploit can be prevented or mitigated using numerous methods, these
methods are as follows
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPUTER SECURITY
Memcached hardening: suppose an organization is implementing memcached based on
the SANS, the organization must consider that the memcached server is hardened (Wang, Zheng
& Lou, 2015). This can be carried out by following various steps, some steps include opening an
etc or a memcached.conf in a particular text editor, locate the m parameter in it, after the
parameter is located, the value should be changed to minimum 1 GB, after that the l parameter
must be located, change the value of l parameter to minimum of 127.0.01 or a specific local host,
after setting the value, the changes must be changed to memcached.conf and then the text editor
must be closed (Slocombe, 2018). After that the memcached must be restarted.
Access to more bandwidth: there are various ways that can be implemented in order to
prevent the memcached attack, for this purpose the basic activity that can be carried out is
getting access to more bandwidth (Sahay, Blanc & Zhang, 2015). This must be considered
because it provides the ability to handle more spikes in traffic that can occur due to any kind of
malicious activity. Preventing these kinds of attacks is possible by ensuring that the company has
a high level of bandwidth at the time of disposal as compared to any other attacker (Wang,
Zheng & Lou, 2015). When the level of attacks rises, this mitigation strategy does not actually
work. Besides this, getting access to more bandwidth increases the chances of the attackers to
overcome before they launch a particularly successful attack.
Disabling the UDP support: suppose an organization has implemented memcached, they
are supposed to disable the UDP support in case they are not using it at that time (Stallings,
2017). In case a particular developer is using it, and a UDP is getting utilized, they should
respond along with a particular strict size of the packet. Suppose, this is not followed, the
protocol would have very high changes to abuse (Yan, Yu & Gong, 2016). The organization
should also close down the port named 11211. The organization should also consider various
Memcached hardening: suppose an organization is implementing memcached based on
the SANS, the organization must consider that the memcached server is hardened (Wang, Zheng
& Lou, 2015). This can be carried out by following various steps, some steps include opening an
etc or a memcached.conf in a particular text editor, locate the m parameter in it, after the
parameter is located, the value should be changed to minimum 1 GB, after that the l parameter
must be located, change the value of l parameter to minimum of 127.0.01 or a specific local host,
after setting the value, the changes must be changed to memcached.conf and then the text editor
must be closed (Slocombe, 2018). After that the memcached must be restarted.
Access to more bandwidth: there are various ways that can be implemented in order to
prevent the memcached attack, for this purpose the basic activity that can be carried out is
getting access to more bandwidth (Sahay, Blanc & Zhang, 2015). This must be considered
because it provides the ability to handle more spikes in traffic that can occur due to any kind of
malicious activity. Preventing these kinds of attacks is possible by ensuring that the company has
a high level of bandwidth at the time of disposal as compared to any other attacker (Wang,
Zheng & Lou, 2015). When the level of attacks rises, this mitigation strategy does not actually
work. Besides this, getting access to more bandwidth increases the chances of the attackers to
overcome before they launch a particularly successful attack.
Disabling the UDP support: suppose an organization has implemented memcached, they
are supposed to disable the UDP support in case they are not using it at that time (Stallings,
2017). In case a particular developer is using it, and a UDP is getting utilized, they should
respond along with a particular strict size of the packet. Suppose, this is not followed, the
protocol would have very high changes to abuse (Yan, Yu & Gong, 2016). The organization
should also close down the port named 11211. The organization should also consider various
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COMPUTER SECURITY
mitigation services including in DDoS from numerous companies like Incapsula, CloudFlare and
Akamai.
Reflection risks: the reflection risk along with some more similar risks can be reduced
using various methods. The infrastructure of the network along with the server of memcached
should be configured by implementing various best practices of the industry standard (Yan,
Gong & Yu, 2017). Various practices such as binding the memcached in to a particular source of
IP can be utilized. The protection that is implemented the risks of addition, deletion, updating
would be decreased.
Configuring the hardware of network against an attack: there are various configuration
changes that must be carried out in the hardware that is used by the organization, these changes
are very simple in nature and they can be used by the company for preventing the memcached
attack (Slocombe, 2018). An example of this is that in case an organization has configured the
firewall or router for dropping the incoming packets of ICMP and then blocks the DNS response
which would arrive from numerous sources of the network that are external in nature (Sahay,
Blanc & Zhang, 2015). This strategy would help the organization in preventing numerous DNS
along with memcached attacks.
Deployment of an appliance for protection from memcrashed attack: various vendors
designed for the security such as NetScout Arbor, Radware, CheckPoint, Fortnite and Cisco
provide access to numerous appliances that generally blocks the firewall of the network. These
vendors are designed for the purpose of blocking these attacks; the attacks are blocked even
before the network is affected (D’Cruze, Wang & Sbeit, 2018). Thus is carried out with the
implementation of numerous techniques like performing a base lining for traffic behavioral and
this helps in blocking the abnormal traffic. This traffic is blocked based on various attack
mitigation services including in DDoS from numerous companies like Incapsula, CloudFlare and
Akamai.
Reflection risks: the reflection risk along with some more similar risks can be reduced
using various methods. The infrastructure of the network along with the server of memcached
should be configured by implementing various best practices of the industry standard (Yan,
Gong & Yu, 2017). Various practices such as binding the memcached in to a particular source of
IP can be utilized. The protection that is implemented the risks of addition, deletion, updating
would be decreased.
Configuring the hardware of network against an attack: there are various configuration
changes that must be carried out in the hardware that is used by the organization, these changes
are very simple in nature and they can be used by the company for preventing the memcached
attack (Slocombe, 2018). An example of this is that in case an organization has configured the
firewall or router for dropping the incoming packets of ICMP and then blocks the DNS response
which would arrive from numerous sources of the network that are external in nature (Sahay,
Blanc & Zhang, 2015). This strategy would help the organization in preventing numerous DNS
along with memcached attacks.
Deployment of an appliance for protection from memcrashed attack: various vendors
designed for the security such as NetScout Arbor, Radware, CheckPoint, Fortnite and Cisco
provide access to numerous appliances that generally blocks the firewall of the network. These
vendors are designed for the purpose of blocking these attacks; the attacks are blocked even
before the network is affected (D’Cruze, Wang & Sbeit, 2018). Thus is carried out with the
implementation of numerous techniques like performing a base lining for traffic behavioral and
this helps in blocking the abnormal traffic. This traffic is blocked based on various attack

8COMPUTER SECURITY
signatures that are known by the organization (Sahay, Blanc & Zhang, 2015). The vital drawback
of this mentioned approach includes the fact that these appliances are limited according to the
amount of traffic throughput which is handled by the organization. Numerous appliances that are
high-end in nature can be implemented which would allow them to inspect the traffic which has
a specific rate that is 80 Gbps or near to that (Cui, Yan & Li, 2016). In recent cases the
magnitude of memcrashed attack is usually of around 80 Gbps or even more than that, as a
result, numerous appliances are usually used for preventing the attacks.
Protection of DNS servers: the memcached attack might impose a serious threat on the
organization, suppose a malicious user has the ability to bring about the web servers of a specific
organization offline, this can be carried out by DDoSing the DNS servers used by the
organization. For this purpose, it is important to consider the fact that the DNS servers have a
specific level of redundancy (Kalliola, Lee & Lee, 2015). These redundancies must be placed in
numerous data centers behind various load balancers. It would be effective for the organization,
if they move to a cloud-based DN provider. This would be beneficial for the organization
because it would help them in proving a higher bandwidth along with various points of presence
at the data centers that are located across the world. These services are designed keeping in mind
the security against memcached attacks.
Future importance and effectiveness of memcrashed
Memcached has numerous important features that can be utilized by the organizations,
some of these features include speeding up the application process, in this case, the memcached
focuses on various best practices for the purpose of deploying it within the environment and
applications (Peltier, 2016). This includes what an organization must store and what they should
not, how the organizations must handle the distribution of data in a flexible manner, how to
signatures that are known by the organization (Sahay, Blanc & Zhang, 2015). The vital drawback
of this mentioned approach includes the fact that these appliances are limited according to the
amount of traffic throughput which is handled by the organization. Numerous appliances that are
high-end in nature can be implemented which would allow them to inspect the traffic which has
a specific rate that is 80 Gbps or near to that (Cui, Yan & Li, 2016). In recent cases the
magnitude of memcrashed attack is usually of around 80 Gbps or even more than that, as a
result, numerous appliances are usually used for preventing the attacks.
Protection of DNS servers: the memcached attack might impose a serious threat on the
organization, suppose a malicious user has the ability to bring about the web servers of a specific
organization offline, this can be carried out by DDoSing the DNS servers used by the
organization. For this purpose, it is important to consider the fact that the DNS servers have a
specific level of redundancy (Kalliola, Lee & Lee, 2015). These redundancies must be placed in
numerous data centers behind various load balancers. It would be effective for the organization,
if they move to a cloud-based DN provider. This would be beneficial for the organization
because it would help them in proving a higher bandwidth along with various points of presence
at the data centers that are located across the world. These services are designed keeping in mind
the security against memcached attacks.
Future importance and effectiveness of memcrashed
Memcached has numerous important features that can be utilized by the organizations,
some of these features include speeding up the application process, in this case, the memcached
focuses on various best practices for the purpose of deploying it within the environment and
applications (Peltier, 2016). This includes what an organization must store and what they should
not, how the organizations must handle the distribution of data in a flexible manner, how to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMPUTER SECURITY
maintain the regulation of methods for the purpose of updating stored version of the data as well
as memcached. Memcached is also helpful in optimization of the speed that they are allowed to
access along with returning the information to the client. Memcached can also help an
organization in future by configuring to utilize a cache for sending back data that does not work
along with the dynamic nature of the applications that are mostly used by the organization
(Stallings, 2017). memcached provides a memory store that is generalized in nature which would
be helpful in holding almost anything such as native language objects, it also enables the
organization to store a wide variety of data and then accesses it from numerous applications as
well as environments (Hu, Hong & Chen, 2017). This allows an organization to utilize the spare
RAM in numerous servers in order to act as a memory cache for the purpose of pieces of data
that are frequently accessed. Memcached provides a temporary space of storage in the memory
of data which can be loaded from anywhere else.
With the usage of memcached, an organization would be able to store formatted data that
has been loaded from the database in the form which can be used readily on the web page. The
data is loaded from the RAM instead of the disk with the help of a database or any other
processing, due to this, the access to the data is instant, which means getting access of the data
does not consume much time (Ahmed, Kim & Park, 2017). Memcached usually acts like a cache
that can be used for the purpose of storing information that is utilized by the organization in its
day-to-day operations, this saves the organization from loading as well as processing data from
various sources that are slower in nature like database and disks.
maintain the regulation of methods for the purpose of updating stored version of the data as well
as memcached. Memcached is also helpful in optimization of the speed that they are allowed to
access along with returning the information to the client. Memcached can also help an
organization in future by configuring to utilize a cache for sending back data that does not work
along with the dynamic nature of the applications that are mostly used by the organization
(Stallings, 2017). memcached provides a memory store that is generalized in nature which would
be helpful in holding almost anything such as native language objects, it also enables the
organization to store a wide variety of data and then accesses it from numerous applications as
well as environments (Hu, Hong & Chen, 2017). This allows an organization to utilize the spare
RAM in numerous servers in order to act as a memory cache for the purpose of pieces of data
that are frequently accessed. Memcached provides a temporary space of storage in the memory
of data which can be loaded from anywhere else.
With the usage of memcached, an organization would be able to store formatted data that
has been loaded from the database in the form which can be used readily on the web page. The
data is loaded from the RAM instead of the disk with the help of a database or any other
processing, due to this, the access to the data is instant, which means getting access of the data
does not consume much time (Ahmed, Kim & Park, 2017). Memcached usually acts like a cache
that can be used for the purpose of storing information that is utilized by the organization in its
day-to-day operations, this saves the organization from loading as well as processing data from
various sources that are slower in nature like database and disks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10COMPUTER SECURITY
Conclusion
From the report presented above, it can be concluded that the memcrashed implements by
exploiting various programs of memcached. It is a particular open source, high-performance,
object-caching and distributed system. This can be used by numerous social networks such as
Facebook along with its creator named LiveJournal as a specific key value store for various
groups that are small in size and have arbitrary data. The memcached can be described as a
program that enables the organization to take care of huge chunks of data. it is also utilized for
the purpose of caching session data of a specific web server, this helps in speeding up the sites
and hence it creates issues. Most of the times, the incompetent system administrators expose
various memcached enabled servers present on the internet. Memcached is not supposed to be
available on the internet for the purpose of getting used by the public but because it is free of any
sort of authentication, it is very easy to use. This particular assignment provides a detailed
description of the concept of memcached. It further discusses the way the memcached attack
takes place and the vulnerabilities caused by it within an organization. This assignment further
discusses some strategies that can be utilized for the purpose of mitigating or preventing these
attacks from occurring in an organization. It also describes the future importance as well as the
effectiveness of the memcached. All the mention topics are described in details in the discussion
part of the report.
Conclusion
From the report presented above, it can be concluded that the memcrashed implements by
exploiting various programs of memcached. It is a particular open source, high-performance,
object-caching and distributed system. This can be used by numerous social networks such as
Facebook along with its creator named LiveJournal as a specific key value store for various
groups that are small in size and have arbitrary data. The memcached can be described as a
program that enables the organization to take care of huge chunks of data. it is also utilized for
the purpose of caching session data of a specific web server, this helps in speeding up the sites
and hence it creates issues. Most of the times, the incompetent system administrators expose
various memcached enabled servers present on the internet. Memcached is not supposed to be
available on the internet for the purpose of getting used by the public but because it is free of any
sort of authentication, it is very easy to use. This particular assignment provides a detailed
description of the concept of memcached. It further discusses the way the memcached attack
takes place and the vulnerabilities caused by it within an organization. This assignment further
discusses some strategies that can be utilized for the purpose of mitigating or preventing these
attacks from occurring in an organization. It also describes the future importance as well as the
effectiveness of the memcached. All the mention topics are described in details in the discussion
part of the report.

11COMPUTER SECURITY
References
Ahmed, M. E., Kim, H., & Park, M. (2017, October). Mitigating dns query-based ddos attacks
with machine learning on software-defined networking. In MILCOM 2017-2017 IEEE
Military Communications Conference (MILCOM) (pp. 11-16). IEEE.
Conklin, W.A., White, G., Cothren, C., Davis, R. & Williams, D., (2015). Principles of computer
security. McGraw-Hill Education Group.
Cui, Y., Yan, L., Li, S., Xing, H., Pan, W., Zhu, J., & Zheng, X. (2016). SD-Anti-DDoS: Fast
and efficient DDoS defense in software-defined networks. Journal of Network and
Computer Applications, 68, 65-79.
D’Cruze, H., Wang, P., Sbeit, R. O., & Ray, A. (2018). A software-defined networking (SDN)
approach to mitigating DDoS attacks. In Information Technology-New Generations(pp.
141-145). Springer, Cham.
Egelman, S. & Peer, E., (2015), April. Scaling the security wall: Developing a security behavior
intentions scale (sebis). In Proceedings of the 33rd Annual ACM Conference on Human
Factors in Computing Systems (pp. 2873-2882). ACM.
Hu, D., Hong, P., & Chen, Y. (2017, December). Fadm: Ddos flooding attack detection and
mitigation system in software-defined networking. In GLOBECOM 2017-2017 IEEE
Global Communications Conference (pp. 1-7). IEEE.
Hyder, H.K. & Lung, C.H., (2018), December. Closed-Loop DDoS Mitigation System in
Software Defined Networks. In 2018 IEEE Conference on Dependable and Secure
Computing (DSC) (pp. 1-6). IEEE.
References
Ahmed, M. E., Kim, H., & Park, M. (2017, October). Mitigating dns query-based ddos attacks
with machine learning on software-defined networking. In MILCOM 2017-2017 IEEE
Military Communications Conference (MILCOM) (pp. 11-16). IEEE.
Conklin, W.A., White, G., Cothren, C., Davis, R. & Williams, D., (2015). Principles of computer
security. McGraw-Hill Education Group.
Cui, Y., Yan, L., Li, S., Xing, H., Pan, W., Zhu, J., & Zheng, X. (2016). SD-Anti-DDoS: Fast
and efficient DDoS defense in software-defined networks. Journal of Network and
Computer Applications, 68, 65-79.
D’Cruze, H., Wang, P., Sbeit, R. O., & Ray, A. (2018). A software-defined networking (SDN)
approach to mitigating DDoS attacks. In Information Technology-New Generations(pp.
141-145). Springer, Cham.
Egelman, S. & Peer, E., (2015), April. Scaling the security wall: Developing a security behavior
intentions scale (sebis). In Proceedings of the 33rd Annual ACM Conference on Human
Factors in Computing Systems (pp. 2873-2882). ACM.
Hu, D., Hong, P., & Chen, Y. (2017, December). Fadm: Ddos flooding attack detection and
mitigation system in software-defined networking. In GLOBECOM 2017-2017 IEEE
Global Communications Conference (pp. 1-7). IEEE.
Hyder, H.K. & Lung, C.H., (2018), December. Closed-Loop DDoS Mitigation System in
Software Defined Networks. In 2018 IEEE Conference on Dependable and Secure
Computing (DSC) (pp. 1-6). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





