CO4509 Computer Security: Memcrashed Exploit, Solutions, and Impact
VerifiedAdded on 2023/04/11
|15
|3256
|143
Report
AI Summary
This report provides a comprehensive analysis of the Memcrashed vulnerability, a significant Distributed Denial of Service (DDoS) attack that leverages the Memcached protocol. The report begins with an introduction to key-value databases, explaining their principles and use within the context of Memcached. It then details the mechanics of the Memcrashed exploit, including how attackers utilize UDP reflection and IP spoofing to amplify traffic and overwhelm target servers. The report further explores potential solutions and mitigation strategies, such as disabling UDP support, implementing firewalls, and preventing IP spoofing. Finally, the report offers predictions on the future importance and effectiveness of the Memcrashed exploit, considering the evolving landscape of cyber threats and the need for robust security measures. The report includes several diagrams and figures to illustrate the concepts discussed, and it concludes with a list of references to support the information provided.

Running head: COMPUTER SECURITY ENGINEERING
Computer Security Engineering
Name of the Student
Name of the University
Author Note:
Computer Security Engineering
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER SECURITY ENGINEERING
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................2
Principles of Value Database.......................................................................................................2
Description of memcrashed Exploit............................................................................................4
Description of any solution of memcrashed exploit....................................................................8
Future importance and effectiveness of memcrashed exploit....................................................10
Conclusion.....................................................................................................................................11
References......................................................................................................................................12
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................2
Principles of Value Database.......................................................................................................2
Description of memcrashed Exploit............................................................................................4
Description of any solution of memcrashed exploit....................................................................8
Future importance and effectiveness of memcrashed exploit....................................................10
Conclusion.....................................................................................................................................11
References......................................................................................................................................12

2COMPUTER SECURITY ENGINEERING
Introduction
Memcrashed attack is considered to be as one of the largest attack which comes up with a
record of 1.35 Tbps. The attack was carried out by making use of Memcached like a UDP
reflection against the attack vector against Github. After this attack, various organization around
the globe have focused on critical alerts that focus on detection and mitigation of UDP reflection
attack like memcrashed. It mainly permits amplification of attacks that is of order and magnitude
much greater than this. DDoS (Distributed Denial of Service) attack is not a new kind of attack
but is an ever-increasing of cloud-based services. IoT based devices are making our life much
easier day by day. It is mainly seen as a result of launch of some of the massive attacks in
comparison to before. This particular exploit tool is completely written python language which
allows the user to send UDP packets with a list of Memcached server that is obtained from
Shodan (Choi et al. 2018). In the year 2016, this particular attack is considered to be as one of
the largest attack that comes up with 600 Gbps on DNS and generated traffic through IoT
devices. The response to this particular considered to be as one of the threat in the whole
community of internet. IoT based devices like Memcached needs to be discovered so that access
to this can be restricted.
The coming pages of the report help in gathering data with respect to key value and
principles of database. After that, a list of description has been provided with respect to me
crashed exploit. A list of possible solution has been provided with respect to memcrashed
exploit. The last section of the report mainly deals with respect to future importance and overall
effectiveness of memcrashed exploit.
Introduction
Memcrashed attack is considered to be as one of the largest attack which comes up with a
record of 1.35 Tbps. The attack was carried out by making use of Memcached like a UDP
reflection against the attack vector against Github. After this attack, various organization around
the globe have focused on critical alerts that focus on detection and mitigation of UDP reflection
attack like memcrashed. It mainly permits amplification of attacks that is of order and magnitude
much greater than this. DDoS (Distributed Denial of Service) attack is not a new kind of attack
but is an ever-increasing of cloud-based services. IoT based devices are making our life much
easier day by day. It is mainly seen as a result of launch of some of the massive attacks in
comparison to before. This particular exploit tool is completely written python language which
allows the user to send UDP packets with a list of Memcached server that is obtained from
Shodan (Choi et al. 2018). In the year 2016, this particular attack is considered to be as one of
the largest attack that comes up with 600 Gbps on DNS and generated traffic through IoT
devices. The response to this particular considered to be as one of the threat in the whole
community of internet. IoT based devices like Memcached needs to be discovered so that access
to this can be restricted.
The coming pages of the report help in gathering data with respect to key value and
principles of database. After that, a list of description has been provided with respect to me
crashed exploit. A list of possible solution has been provided with respect to memcrashed
exploit. The last section of the report mainly deals with respect to future importance and overall
effectiveness of memcrashed exploit.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMPUTER SECURITY ENGINEERING
Discussion
Principles of Value Database
Key-Value database is also known as value store, is a kind of NoSQL database that
makes use of simple value method of data. Key-value emphasizes on the fact that database which
stores data like collection of value pairs. It is nothing but a method which is required for storing
data along with scaling it up. Key-value pair is well known concept in various coding languages.
Programming language is considered to be key value of associated array or even data structure.
Key-Value database is designed in such a way that it can store all the required data in the
form of documents. Some of the well-known key value that is in use are YAML, JSON, and
XML for encoding schemes which can be used for handling of data in a much better way.
Fig 1: Key-Value Database
(Source: Blott et al. 2015)
Discussion
Principles of Value Database
Key-Value database is also known as value store, is a kind of NoSQL database that
makes use of simple value method of data. Key-value emphasizes on the fact that database which
stores data like collection of value pairs. It is nothing but a method which is required for storing
data along with scaling it up. Key-value pair is well known concept in various coding languages.
Programming language is considered to be key value of associated array or even data structure.
Key-Value database is designed in such a way that it can store all the required data in the
form of documents. Some of the well-known key value that is in use are YAML, JSON, and
XML for encoding schemes which can be used for handling of data in a much better way.
Fig 1: Key-Value Database
(Source: Blott et al. 2015)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER SECURITY ENGINEERING
In Memcached, it is known to be one of the best kind of distributed in-memory cache
which will help in reduction of latency in the data process. It is mainly done in comparisons to
another kind of key-value storage. It is widely used in range for providing proper support to the
given cloud services and even web-based services. Objects of key-value objects come of two
parts that are key and value.
Key-value database is used for carrying a wide range of option like Set, delete and many
other options on the database (Lu, Shankar and Panda 2017). By making use of Get option, user
needs to submit the required key in the stored data. Key-value database comes up two vital
factors like
Time for response or even latency in the access of data.
Understanding the number of requests that can be complete in the provided time.
In memcached, Web-based services come up with huge number of servers that comes up
with huge number of request in the given time. As soon as the user request is gained by the help
of key, web services helps to gather access to nearby cluster. In the instances of user gained
object which is collected in memcached node it can define the overall cache hit. By this
particular method, access to real back-end database is not needed. It is one of the expensive kind
of input and output operation which requires to be ignored.
On the contrary, if the request object is not collected on the cluster then all the web-based
services can gather request object which is found on the back of the database. It is also found in
one of the memcached node (Wang et al. 2015). To have a clear understanding between the
distributed data, a set of Memcached server makes use of hash function along with proper key. It
is mainly done so that it can limit the order where the Memcached server can retrieve the
required object.
In Memcached, it is known to be one of the best kind of distributed in-memory cache
which will help in reduction of latency in the data process. It is mainly done in comparisons to
another kind of key-value storage. It is widely used in range for providing proper support to the
given cloud services and even web-based services. Objects of key-value objects come of two
parts that are key and value.
Key-value database is used for carrying a wide range of option like Set, delete and many
other options on the database (Lu, Shankar and Panda 2017). By making use of Get option, user
needs to submit the required key in the stored data. Key-value database comes up two vital
factors like
Time for response or even latency in the access of data.
Understanding the number of requests that can be complete in the provided time.
In memcached, Web-based services come up with huge number of servers that comes up
with huge number of request in the given time. As soon as the user request is gained by the help
of key, web services helps to gather access to nearby cluster. In the instances of user gained
object which is collected in memcached node it can define the overall cache hit. By this
particular method, access to real back-end database is not needed. It is one of the expensive kind
of input and output operation which requires to be ignored.
On the contrary, if the request object is not collected on the cluster then all the web-based
services can gather request object which is found on the back of the database. It is also found in
one of the memcached node (Wang et al. 2015). To have a clear understanding between the
distributed data, a set of Memcached server makes use of hash function along with proper key. It
is mainly done so that it can limit the order where the Memcached server can retrieve the
required object.

5COMPUTER SECURITY ENGINEERING
Description of memcrashed Exploit
Memcached DDoS (Distributed Denial of Services) attack is a kind of cyber-attack in
which the attackers attempt the overload of target victim by the help of internet traffic. Attackers
mainly spoof request to the vulnerable UDP of Memcached server. It is flooded to a target victim
by the help of internet traffic and overwhelming of the resources of the victim. In this, target
internet infrastructure is completely overloaded where new request cannot be processed easily.
Regular traffic cannot gain access to this particular internet based resources which results in
denial of service attack. Memcached is considered to be as one of the database caching systems
which is required for speeding up both websites and networks.
Fig 2: Report of Memcached attack
(Source: Kolias et al. 2017)
Memcached attack tends to work similarly to DDoS application tends to operate very
similar to attacks like NTP and DNS amplification. The whole attack works by providing
Description of memcrashed Exploit
Memcached DDoS (Distributed Denial of Services) attack is a kind of cyber-attack in
which the attackers attempt the overload of target victim by the help of internet traffic. Attackers
mainly spoof request to the vulnerable UDP of Memcached server. It is flooded to a target victim
by the help of internet traffic and overwhelming of the resources of the victim. In this, target
internet infrastructure is completely overloaded where new request cannot be processed easily.
Regular traffic cannot gain access to this particular internet based resources which results in
denial of service attack. Memcached is considered to be as one of the database caching systems
which is required for speeding up both websites and networks.
Fig 2: Report of Memcached attack
(Source: Kolias et al. 2017)
Memcached attack tends to work similarly to DDoS application tends to operate very
similar to attacks like NTP and DNS amplification. The whole attack works by providing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPUTER SECURITY ENGINEERING
spoofed request to each of the vulnerable servers. It then responds with huge amount of data in
comparisons to initial request that is magnification of huge volume of traffic. This particular
method or way of amplification attack is made possible due to memcached server that comes up
with the option of operation by making use of UDP protocol. It is a network protocol which
allows the user to send data without getting which is known as handshake. It is a well-known
process in network where both the sides agree to the communication. UDP is used because of
target host which is never consulted or even willing to receive data. It mainly allows the user to
receive huge amount of data allowing the user to send massive amount of data to the target
before the consent.
The attack of memcached can occur in list of four steps that are
The attacker can implant a huge amount of payload of data which is completely exposed
to the Memcached server.
The next step is attacker spoof for getting HTTP GET request along with IP address of
the victim.
Vulnerable Memcached server will receive the request which is looking for helpful
request by understanding the respond. It mainly provides huge amount of response to the
target
The target server or areas surrounding the infrastructure cannot process the huge amount
of data that is transmitted from Memcached server. It ultimately results in overloading
and denial of service to some of the legitimate needs.
The overall amplification factor of this particular attack is considered to be around
51,200. It merely highlights the fact 15 bytes’ request is sent along with 750 KB. It mainly
highlights the amplification factor and security risk of web properties. The total volume of this
spoofed request to each of the vulnerable servers. It then responds with huge amount of data in
comparisons to initial request that is magnification of huge volume of traffic. This particular
method or way of amplification attack is made possible due to memcached server that comes up
with the option of operation by making use of UDP protocol. It is a network protocol which
allows the user to send data without getting which is known as handshake. It is a well-known
process in network where both the sides agree to the communication. UDP is used because of
target host which is never consulted or even willing to receive data. It mainly allows the user to
receive huge amount of data allowing the user to send massive amount of data to the target
before the consent.
The attack of memcached can occur in list of four steps that are
The attacker can implant a huge amount of payload of data which is completely exposed
to the Memcached server.
The next step is attacker spoof for getting HTTP GET request along with IP address of
the victim.
Vulnerable Memcached server will receive the request which is looking for helpful
request by understanding the respond. It mainly provides huge amount of response to the
target
The target server or areas surrounding the infrastructure cannot process the huge amount
of data that is transmitted from Memcached server. It ultimately results in overloading
and denial of service to some of the legitimate needs.
The overall amplification factor of this particular attack is considered to be around
51,200. It merely highlights the fact 15 bytes’ request is sent along with 750 KB. It mainly
highlights the amplification factor and security risk of web properties. The total volume of this
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COMPUTER SECURITY ENGINEERING
attack cannot be shoulder easily. By the help of large amplification factor which is coupled with
Memcached server. It is a prime use for various attackers that are planning to launch DDoS
attack against the target.
Memcrashed is known to be as one of the obscure amplification attack vectors which is
done by making use of Memcached protocol coming from 11211 UDP port. The basic idea
behind all kind of amplification of attack is very much same (Ain et al. 2016). IP-spoofing helps
the attackers to provide request to vulnerable UDP server. Unknowingly the request is forged
then politely the overall response is prepared. This particular issue comes into picture due to
unsuspecting of target host and overwhelming of the resources. Amplification attacks are
considered to be very much effective in nature. It happens because of the fact that it allows the
attackers to limit IP spoofing capacity like 1 Gbps for launching attacks. The main factor is all
about amplification of attack within the given bandwidth.
The key components behind these memcrashed attack are UDP port 11211, DNS
reflection and DNS amplification. DNS amplification attack makes use of DNS reflection and
amplification based technique which is needed for forming a potent DDoS (Behal and Kumar
2017). In this attacker can spoof can be IP spending which is sent to vulnerable UDP server.
Then the DNS server will respond back to the spoofed host but not to the victim. The collected
response will begin to overwhelm the draining sources result in DDoS attack. The second part of
this attack is DNS amplification. It is mainly carried out by the help of vulnerabilities that are
there in the misconfigured server. The attackers can easily turn a given small query into a large
one.
attack cannot be shoulder easily. By the help of large amplification factor which is coupled with
Memcached server. It is a prime use for various attackers that are planning to launch DDoS
attack against the target.
Memcrashed is known to be as one of the obscure amplification attack vectors which is
done by making use of Memcached protocol coming from 11211 UDP port. The basic idea
behind all kind of amplification of attack is very much same (Ain et al. 2016). IP-spoofing helps
the attackers to provide request to vulnerable UDP server. Unknowingly the request is forged
then politely the overall response is prepared. This particular issue comes into picture due to
unsuspecting of target host and overwhelming of the resources. Amplification attacks are
considered to be very much effective in nature. It happens because of the fact that it allows the
attackers to limit IP spoofing capacity like 1 Gbps for launching attacks. The main factor is all
about amplification of attack within the given bandwidth.
The key components behind these memcrashed attack are UDP port 11211, DNS
reflection and DNS amplification. DNS amplification attack makes use of DNS reflection and
amplification based technique which is needed for forming a potent DDoS (Behal and Kumar
2017). In this attacker can spoof can be IP spending which is sent to vulnerable UDP server.
Then the DNS server will respond back to the spoofed host but not to the victim. The collected
response will begin to overwhelm the draining sources result in DDoS attack. The second part of
this attack is DNS amplification. It is mainly carried out by the help of vulnerabilities that are
there in the misconfigured server. The attackers can easily turn a given small query into a large
one.
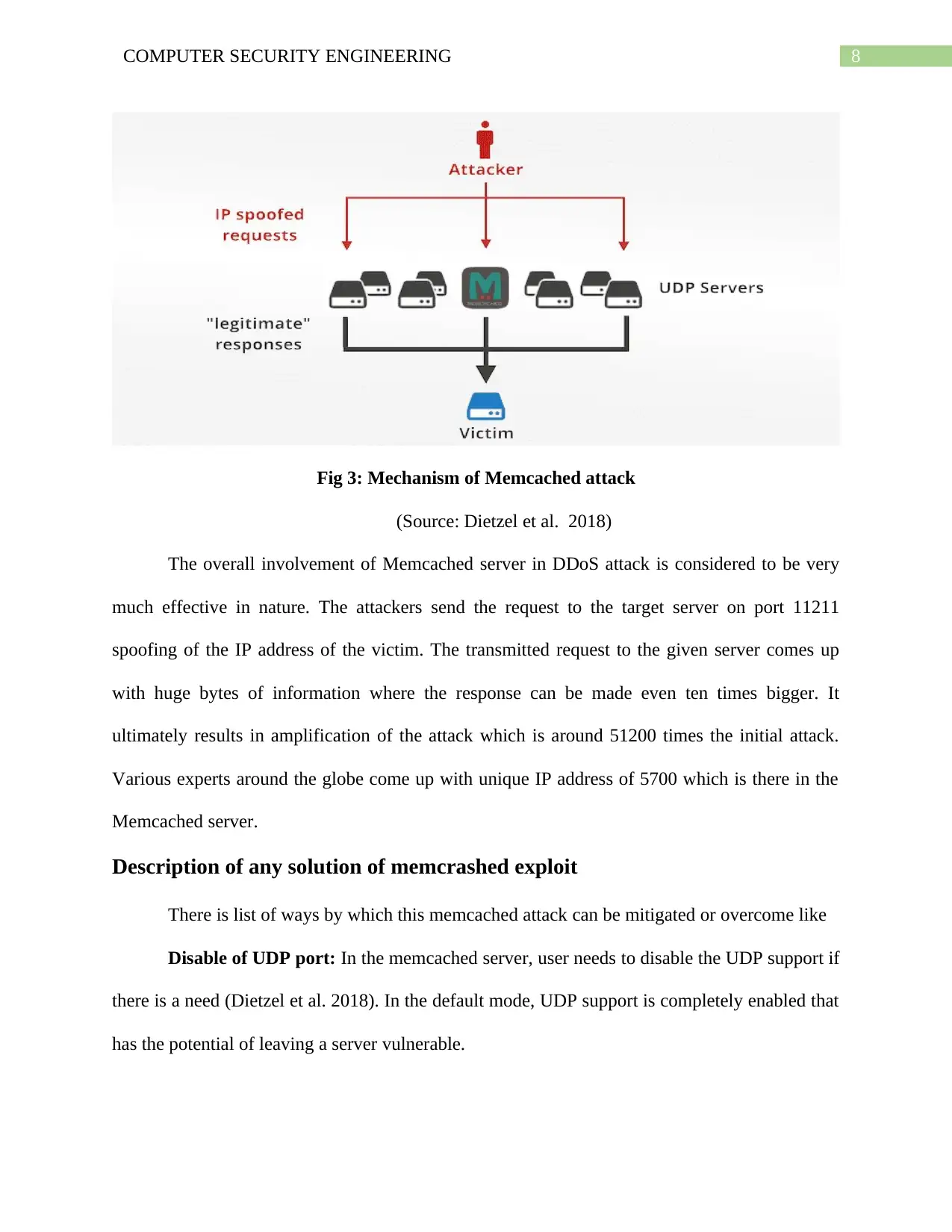
8COMPUTER SECURITY ENGINEERING
Fig 3: Mechanism of Memcached attack
(Source: Dietzel et al. 2018)
The overall involvement of Memcached server in DDoS attack is considered to be very
much effective in nature. The attackers send the request to the target server on port 11211
spoofing of the IP address of the victim. The transmitted request to the given server comes up
with huge bytes of information where the response can be made even ten times bigger. It
ultimately results in amplification of the attack which is around 51200 times the initial attack.
Various experts around the globe come up with unique IP address of 5700 which is there in the
Memcached server.
Description of any solution of memcrashed exploit
There is list of ways by which this memcached attack can be mitigated or overcome like
Disable of UDP port: In the memcached server, user needs to disable the UDP support if
there is a need (Dietzel et al. 2018). In the default mode, UDP support is completely enabled that
has the potential of leaving a server vulnerable.
Fig 3: Mechanism of Memcached attack
(Source: Dietzel et al. 2018)
The overall involvement of Memcached server in DDoS attack is considered to be very
much effective in nature. The attackers send the request to the target server on port 11211
spoofing of the IP address of the victim. The transmitted request to the given server comes up
with huge bytes of information where the response can be made even ten times bigger. It
ultimately results in amplification of the attack which is around 51200 times the initial attack.
Various experts around the globe come up with unique IP address of 5700 which is there in the
Memcached server.
Description of any solution of memcrashed exploit
There is list of ways by which this memcached attack can be mitigated or overcome like
Disable of UDP port: In the memcached server, user needs to disable the UDP support if
there is a need (Dietzel et al. 2018). In the default mode, UDP support is completely enabled that
has the potential of leaving a server vulnerable.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMPUTER SECURITY ENGINEERING
Firewall mismatched server: By the help of firewall Memcached from the internet,
system administrator can make use of UDP for Memcached which is needed for exposure.
Prevention of IP spoofing: If the IP address can be spoofed then DDoS can make use of
vulnerability for directing traffic to the victims of the network. IP spoofing can be prevented for
large number of solution that cannot be implemented by any of the system administrator. It
requires transit of the providers which does not allow any kind of packets for leaving the
network. It comes up with source of IP address that is originating outside the given network.
There is large number of organization like internet service providers which can filter the overall
traffic in network like packets which leave the network. It does not allow to pretend to be a form
of network that comes up different network of someone else. If some of the major transit is
provided or implemented by the help of this filtration, spoofing based attack can disappear in the
span of given time.
Development of Software with reduced UDP response: Another method which can be
used for elimination of amplification attack is to completely remove the amplification factor
which is coming for request. If the given data is provided as a result of UDP request, then the
request is smaller or equal to the given initial request where the amplification is not that much
longer.
Currently, there are two proof of concept attack code has been released for amplification
of Memcached technique. It is considered to be as one of the danger because a large number of
people can make it useful for launching Memcached DDoS attack (Choi et al. 2018). One of the
PoC code is written in Python scripting language which makes use of Shodan search engine API.
It is mainly needed for updating list of vulnerable Memcached server which requires
Firewall mismatched server: By the help of firewall Memcached from the internet,
system administrator can make use of UDP for Memcached which is needed for exposure.
Prevention of IP spoofing: If the IP address can be spoofed then DDoS can make use of
vulnerability for directing traffic to the victims of the network. IP spoofing can be prevented for
large number of solution that cannot be implemented by any of the system administrator. It
requires transit of the providers which does not allow any kind of packets for leaving the
network. It comes up with source of IP address that is originating outside the given network.
There is large number of organization like internet service providers which can filter the overall
traffic in network like packets which leave the network. It does not allow to pretend to be a form
of network that comes up different network of someone else. If some of the major transit is
provided or implemented by the help of this filtration, spoofing based attack can disappear in the
span of given time.
Development of Software with reduced UDP response: Another method which can be
used for elimination of amplification attack is to completely remove the amplification factor
which is coming for request. If the given data is provided as a result of UDP request, then the
request is smaller or equal to the given initial request where the amplification is not that much
longer.
Currently, there are two proof of concept attack code has been released for amplification
of Memcached technique. It is considered to be as one of the danger because a large number of
people can make it useful for launching Memcached DDoS attack (Choi et al. 2018). One of the
PoC code is written in Python scripting language which makes use of Shodan search engine API.
It is mainly needed for updating list of vulnerable Memcached server which requires
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10COMPUTER SECURITY ENGINEERING
involvement of Memcached DDoS based attack. While the second exploiting code is completely
written in C programming which makes use of list of vulnerable server.
When these two PoC exploits for Memcached DDoS attack have been released online
then organization around the globe have come up with kill switch mechanism. It is mainly
needed for analyzing the vulnerability of Memcached. Various organization around the globe
have accepted the fact there are many issues in Memcached server. This particular issue will help
the attackers to make modification or even steal required data from website and API. At present,
there are more than 95,000 servers on worldwide platform that allows connection between TCP
or UDP port of 11211 from internet (Blott et al. 2015). It is seen if there is involvement of army
machine then it will result in memcrashed DDoS attack. There are around 95,000 servers that are
being used on worldwide platform which allows connection on this port from internet. The
overall potential of this particular attack is considered to be very much significant in nature.
Memcached protocol has been designed in such a way that it can work without login or even
password. The attackers can trigger into the vulnerability and make modification of the data
which is reinserted in the cache. “Flush_all” countermeasures make use of vulnerable server
which is very much large in size. There is some malicious payload which are planted by the
attackers that is effective in the scenario. Kill switch mechanism help the individual to send the
attack back to the attacking server for halting DDoS attack. Till now, no side effect of this has
been observed.
involvement of Memcached DDoS based attack. While the second exploiting code is completely
written in C programming which makes use of list of vulnerable server.
When these two PoC exploits for Memcached DDoS attack have been released online
then organization around the globe have come up with kill switch mechanism. It is mainly
needed for analyzing the vulnerability of Memcached. Various organization around the globe
have accepted the fact there are many issues in Memcached server. This particular issue will help
the attackers to make modification or even steal required data from website and API. At present,
there are more than 95,000 servers on worldwide platform that allows connection between TCP
or UDP port of 11211 from internet (Blott et al. 2015). It is seen if there is involvement of army
machine then it will result in memcrashed DDoS attack. There are around 95,000 servers that are
being used on worldwide platform which allows connection on this port from internet. The
overall potential of this particular attack is considered to be very much significant in nature.
Memcached protocol has been designed in such a way that it can work without login or even
password. The attackers can trigger into the vulnerability and make modification of the data
which is reinserted in the cache. “Flush_all” countermeasures make use of vulnerable server
which is very much large in size. There is some malicious payload which are planted by the
attackers that is effective in the scenario. Kill switch mechanism help the individual to send the
attack back to the attacking server for halting DDoS attack. Till now, no side effect of this has
been observed.

11COMPUTER SECURITY ENGINEERING
Fig 4: Rate of Memcached Attack
(Source: Lu, Shankar and Panda 2017)
DDoS attack that Memcached the server is made possible because a large number of
organization which is operating it has failed to implement some of the basic practices. Threat
actors in the wild that are abused for Memcached server in the upcoming attacks. It is mainly
done because of a large of people are exposed on the internet platform. Security organization
recommends disabling the UDP Ports unless it is required by the organization. The main focus is
on isolation of Memcached server which is available on internet. For counter measuring this kind
of attack, organization needs to fix the vulnerable protocols and IP spoofing.
Future importance and effectiveness of memcrashed exploit
In the last few years, the number of DDoS attack like memcrashed have doubled and
various organization is experiencing around 8 attacks on average day. The biggest issue that can
be encountered is that DDoS attack has become more complex and deceptive in nature. On 28
Feb 2018, Github has experienced an attack (Wang et al. 2015). The organization claims to
suffer around 1.35 terabits of data for every second which is needed for traffic making.
Memcrashed attack is considered to be as one most powerful attack till now. Smaller attacks
would have occurred but these would be all about testing the vector of the attack. It mainly
Fig 4: Rate of Memcached Attack
(Source: Lu, Shankar and Panda 2017)
DDoS attack that Memcached the server is made possible because a large number of
organization which is operating it has failed to implement some of the basic practices. Threat
actors in the wild that are abused for Memcached server in the upcoming attacks. It is mainly
done because of a large of people are exposed on the internet platform. Security organization
recommends disabling the UDP Ports unless it is required by the organization. The main focus is
on isolation of Memcached server which is available on internet. For counter measuring this kind
of attack, organization needs to fix the vulnerable protocols and IP spoofing.
Future importance and effectiveness of memcrashed exploit
In the last few years, the number of DDoS attack like memcrashed have doubled and
various organization is experiencing around 8 attacks on average day. The biggest issue that can
be encountered is that DDoS attack has become more complex and deceptive in nature. On 28
Feb 2018, Github has experienced an attack (Wang et al. 2015). The organization claims to
suffer around 1.35 terabits of data for every second which is needed for traffic making.
Memcrashed attack is considered to be as one most powerful attack till now. Smaller attacks
would have occurred but these would be all about testing the vector of the attack. It mainly
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



