Computer Security: Email Phishing, Types, Mitigation Techniques Report
VerifiedAdded on 2021/06/17
|13
|3200
|96
Report
AI Summary
This report delves into the pervasive issue of email phishing and its detrimental impact on businesses and individuals. It begins by defining phishing attacks as deceptive methods used to steal personal and financial data, highlighting the need for robust protection mechanisms. The report then outlines the problem description, emphasizing how attackers exploit fraudulent websites and deceptive emails to trick users into revealing sensitive information. It details the different types of phishing attacks, including clone phishing, spear phishing, and phone phishing, explaining their unique characteristics and targeting methods. Furthermore, the report explores various mitigation strategies, such as access control, proper training, checking email legitimacy, mismatched URL detection, subject line verification, and the installation of anti-phishing software. By examining the core issues, attack types, and mitigation methods, the report provides a comprehensive overview of email phishing, equipping readers with the knowledge needed to safeguard against such threats.

Running head: COMPUTER SECURITY
Computer Security: Safe Phishing Exercise
Name of the student:
Name of the university:
Computer Security: Safe Phishing Exercise
Name of the student:
Name of the university:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER SECURITY
Introduction
This report depicts the negative impact of email phishing and its affect in business and
industries. Not only large businesses but also it can eventually interrupt the content of the
confidentiality. Phishing attack is referred to as a method that is used for tricking the users by
unknowingly provide those personal and financial data or sending capital to the attackers 1. In
order to prevent the digitized system from the phishing attack it is necessary for the system
developer to adopt proper protection mechanism. In order to prevent these kinds of attack the
users should avoid clicking in unknown electronic mail contents and Links.
This report demonstrates the common phishing attacks and its potential damages
However after identifying this issues possible mitigation strategies are also needed to be
identified and those are also elaborated in this report. It has been found that the most common
form of phishing attack is a form of electronic message like email for providing links to what
appears to be legitimate site but is a malicious site that is generally controlled by the external
attackers2. These paper measures the role of phishing attack its possible classification and
counter measurements. Besides the details of phishing attack the possible mitigation strategies
are also developed and demonstrated in this report details.
1. Problem description
Theft is referred to as a very popular idea among the members who are having high level
of criminal intension. Financial records and other important belongings can eventually be
1 Cao, Y., Han, W. and Le, Y., 2008, October. Anti-phishing based on automated individual white-list.
In Proceedings of the 4th ACM workshop on Digital identity management (pp. 51-60). ACM.
2 Zhao, M., An, B. and Kiekintveld, C., 2016, February. Optimizing Personalized Email Filtering
Thresholds to Mitigate Sequential Spear Phishing Attacks. In AAAI (pp. 658-665).
Introduction
This report depicts the negative impact of email phishing and its affect in business and
industries. Not only large businesses but also it can eventually interrupt the content of the
confidentiality. Phishing attack is referred to as a method that is used for tricking the users by
unknowingly provide those personal and financial data or sending capital to the attackers 1. In
order to prevent the digitized system from the phishing attack it is necessary for the system
developer to adopt proper protection mechanism. In order to prevent these kinds of attack the
users should avoid clicking in unknown electronic mail contents and Links.
This report demonstrates the common phishing attacks and its potential damages
However after identifying this issues possible mitigation strategies are also needed to be
identified and those are also elaborated in this report. It has been found that the most common
form of phishing attack is a form of electronic message like email for providing links to what
appears to be legitimate site but is a malicious site that is generally controlled by the external
attackers2. These paper measures the role of phishing attack its possible classification and
counter measurements. Besides the details of phishing attack the possible mitigation strategies
are also developed and demonstrated in this report details.
1. Problem description
Theft is referred to as a very popular idea among the members who are having high level
of criminal intension. Financial records and other important belongings can eventually be
1 Cao, Y., Han, W. and Le, Y., 2008, October. Anti-phishing based on automated individual white-list.
In Proceedings of the 4th ACM workshop on Digital identity management (pp. 51-60). ACM.
2 Zhao, M., An, B. and Kiekintveld, C., 2016, February. Optimizing Personalized Email Filtering
Thresholds to Mitigate Sequential Spear Phishing Attacks. In AAAI (pp. 658-665).
2COMPUTER SECURITY
hijacked with the phishing attack. If proper security mechanisms are not adopted the, the data
will be easily hacked through external assaults. From outside the phishing attack looks like not at
all different from a normal official communication but though it looks similar but its negative
impact is very high. The attacker’s uses fraud website but the looks like an official one at the
same time the content of the messages are also not identified as a viral one from the outside. As
soon as the attackers send the emails to that person whom he or she wishes to attack a spam
message received by the receiver3. However, from outside, none of the receiver will be able to
identify that whether the message is a malicious one or not.
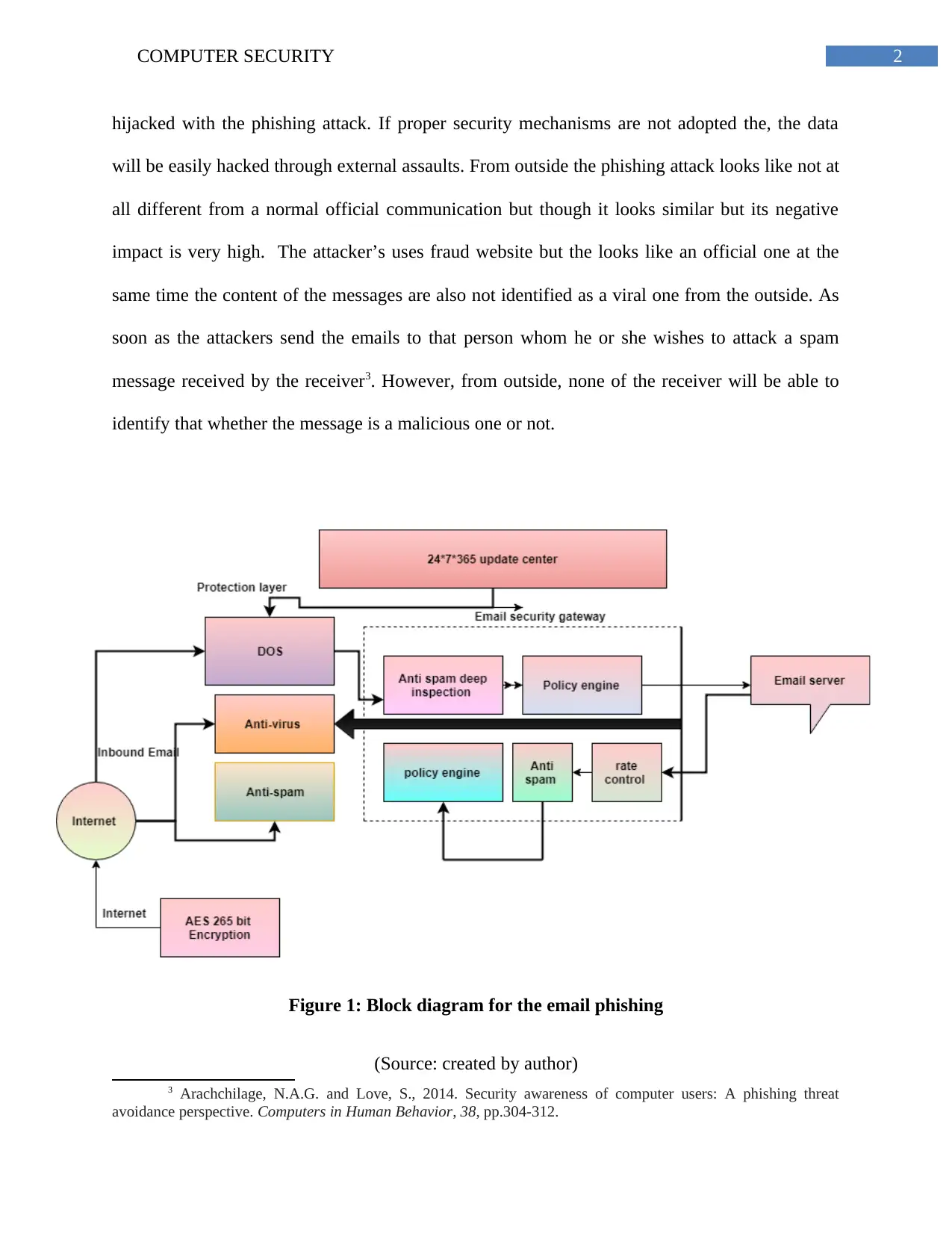
Figure 1: Block diagram for the email phishing
(Source: created by author)
3 Arachchilage, N.A.G. and Love, S., 2014. Security awareness of computer users: A phishing threat
avoidance perspective. Computers in Human Behavior, 38, pp.304-312.
hijacked with the phishing attack. If proper security mechanisms are not adopted the, the data
will be easily hacked through external assaults. From outside the phishing attack looks like not at
all different from a normal official communication but though it looks similar but its negative
impact is very high. The attacker’s uses fraud website but the looks like an official one at the
same time the content of the messages are also not identified as a viral one from the outside. As
soon as the attackers send the emails to that person whom he or she wishes to attack a spam
message received by the receiver3. However, from outside, none of the receiver will be able to
identify that whether the message is a malicious one or not.
Figure 1: Block diagram for the email phishing
(Source: created by author)
3 Arachchilage, N.A.G. and Love, S., 2014. Security awareness of computer users: A phishing threat
avoidance perspective. Computers in Human Behavior, 38, pp.304-312.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMPUTER SECURITY
In order to steal bank details and personnel confidential information this particular type
of attacks mechanism re used by the hackers. Once the message will be received and clicked by
the receiver their personal message contents will be hijacked.
For stealing the confidentiality of the consumers this particular attack takes place in the
retails online stores. There are many online shopping stores which are facing continuous this
kind of cyber attacks.
According to 4 phishing is a kind of social engineering where the attackers are also
identified as a phisher. The phishers are attempts to fetch legitimate confidentiality f the users or
the sensitive of credential information through mimicking the role of electronic communication.
During the development of any online store or shopping centre besides adopting the security
standards the developers should also consider necessary phishing attacks preventing mechanism.
Based on the background and details of the business necessary security is required to be adopted
by the developers. In this kind of attacks the attackers cannot directly get the password or
security code but influence the users to get attacked by clicking on the links and spam message
content.
In traditional stage of attacks the phishers used to copy the codes from the IOL websites
and all crafted pages those look similar like the part of the AOL. Besides phishing attack there
are some other attack mechanism are also there in terms of snooping, spoofing etc5. The cyber
criminals use all these attacks for hijacking the confidential info ration from the user’s server.
4 Fette, I., Sadeh, N. and Tomasic, A., 2006. Learning to detect phishing emails (No. CMU-ISRI-06-112).
CARNEGIE-MELLON UNIV PITTSBURGH PA DEPT OF COMPUTER SCIENCE.
5Shahriar, H., Klintic, T. and Clincy, V., 2015. Mobile phishing attacks and mitigation techniques. Journal of
Information Security, 6(03), p.206.
In order to steal bank details and personnel confidential information this particular type
of attacks mechanism re used by the hackers. Once the message will be received and clicked by
the receiver their personal message contents will be hijacked.
For stealing the confidentiality of the consumers this particular attack takes place in the
retails online stores. There are many online shopping stores which are facing continuous this
kind of cyber attacks.
According to 4 phishing is a kind of social engineering where the attackers are also
identified as a phisher. The phishers are attempts to fetch legitimate confidentiality f the users or
the sensitive of credential information through mimicking the role of electronic communication.
During the development of any online store or shopping centre besides adopting the security
standards the developers should also consider necessary phishing attacks preventing mechanism.
Based on the background and details of the business necessary security is required to be adopted
by the developers. In this kind of attacks the attackers cannot directly get the password or
security code but influence the users to get attacked by clicking on the links and spam message
content.
In traditional stage of attacks the phishers used to copy the codes from the IOL websites
and all crafted pages those look similar like the part of the AOL. Besides phishing attack there
are some other attack mechanism are also there in terms of snooping, spoofing etc5. The cyber
criminals use all these attacks for hijacking the confidential info ration from the user’s server.
4 Fette, I., Sadeh, N. and Tomasic, A., 2006. Learning to detect phishing emails (No. CMU-ISRI-06-112).
CARNEGIE-MELLON UNIV PITTSBURGH PA DEPT OF COMPUTER SCIENCE.
5Shahriar, H., Klintic, T. and Clincy, V., 2015. Mobile phishing attacks and mitigation techniques. Journal of
Information Security, 6(03), p.206.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER SECURITY
The phishing information flow is consists of five different components. If cyber criminals
who wish to hack confidential information from the server allows all these components work
combiningly to deliver the possible outcome. The five components of the information flow
include: user or the victim of the attack, phisher or the attacker, the phisher collector, phisher or
the casher and the financial institution. It can be said that a complete phishing attack defines
there different roles for the phishers.
The first role is the role of a mailer. These attackers send large number of email content
to that person or system which they wish to attack. They generally used the botnets for sending
this emails. These are directed towards the users to fraud websites6. Then comes the role of the
collectors who asset up the websites those are widely hosted by the compromised machines.
These machines again prompt the users for providing confidential information for achieving the
actual payouts. However, it has been found that in most of the cases between these phishers
monetary exchanges are offers.
On the other hand it can be said that, before delving into the phishing attack it is
important to clarify what s not actually phishing. Scam and auction fraud are not referred to as a
phishing of it do not found to be involved in obtaining the user’s confidential credentials7. After
surveying different latest banking details it has been found that, the banking details are hijacked
by the attackers through phishing attack.
6 Dhamija, R. and Tygar, J.D., 2005, July. The battle against phishing: Dynamic security skins.
In Proceedings of the 2005 symposium on Usable privacy and security (pp. 77-88). ACM.
7 Plössl, K., Federrath, H. and Nowey, T., 2005, August. Protection mechanisms against phishing attacks.
In International Conference on Trust, Privacy and Security in Digital Business (pp. 20-29). Springer, Berlin,
Heidelberg.
The phishing information flow is consists of five different components. If cyber criminals
who wish to hack confidential information from the server allows all these components work
combiningly to deliver the possible outcome. The five components of the information flow
include: user or the victim of the attack, phisher or the attacker, the phisher collector, phisher or
the casher and the financial institution. It can be said that a complete phishing attack defines
there different roles for the phishers.
The first role is the role of a mailer. These attackers send large number of email content
to that person or system which they wish to attack. They generally used the botnets for sending
this emails. These are directed towards the users to fraud websites6. Then comes the role of the
collectors who asset up the websites those are widely hosted by the compromised machines.
These machines again prompt the users for providing confidential information for achieving the
actual payouts. However, it has been found that in most of the cases between these phishers
monetary exchanges are offers.
On the other hand it can be said that, before delving into the phishing attack it is
important to clarify what s not actually phishing. Scam and auction fraud are not referred to as a
phishing of it do not found to be involved in obtaining the user’s confidential credentials7. After
surveying different latest banking details it has been found that, the banking details are hijacked
by the attackers through phishing attack.
6 Dhamija, R. and Tygar, J.D., 2005, July. The battle against phishing: Dynamic security skins.
In Proceedings of the 2005 symposium on Usable privacy and security (pp. 77-88). ACM.
7 Plössl, K., Federrath, H. and Nowey, T., 2005, August. Protection mechanisms against phishing attacks.
In International Conference on Trust, Privacy and Security in Digital Business (pp. 20-29). Springer, Berlin,
Heidelberg.

5COMPUTER SECURITY
2. Type of phishing
Three different types of phishing attacks are there such as clone phishing, spear phishing,
phone phishing. Phishing attack has spear beyond the emails to involve the VOIP, SMS,
messaging, social networking sites and also even multiplayer games. Some major categories of
phishing attacks are mentioned below:
Clone phishing: In this kid of phishing attacks the attackers widely creates cloned emails
before attacking to the target person’s credentials. The attackers do this by getting data in terms
of content and recipients addresses from the emails those were delivered previously. Then the
attackers send the similar message content just by replacing the original content with malicious
links8. The attacker also employs address spoofing to ensure that the emails appear to be
forming the original email senders. The email is claimed to be a re send of the original or the
updated version as a major trapping strategy.
Spear phishing: Spear phishing targets only specific groups of people. It can be said
that, instead of the casting out of the thousand of the emails randomly this kind of attacks are
took place over a large number of people who are working for a single organization9. These
kinds of attacks are referred to as high level attacks which took place are large organizations or
businesses.
Phone phishing: These kinds of attacks are somewhere differs from the email attacks. In
this sort of attacks the victims are asked for dialing a particular number and as soon as the
8 Gansterer, W.N. and Pölz, D., 2009, April. E-mail classification for phishing defense. In European
Conference on Information Retrieval (pp. 449-460). Springer, Berlin, Heidelberg.
9 Wenyin, L., Huang, G., Xiaoyue, L., Deng, X. and Min, Z., 2005, August. Phishing Web page detection.
In Document Analysis and Recognition, 2005. Proceedings. Eighth International Conference on (pp. 560-564).
IEEE.
2. Type of phishing
Three different types of phishing attacks are there such as clone phishing, spear phishing,
phone phishing. Phishing attack has spear beyond the emails to involve the VOIP, SMS,
messaging, social networking sites and also even multiplayer games. Some major categories of
phishing attacks are mentioned below:
Clone phishing: In this kid of phishing attacks the attackers widely creates cloned emails
before attacking to the target person’s credentials. The attackers do this by getting data in terms
of content and recipients addresses from the emails those were delivered previously. Then the
attackers send the similar message content just by replacing the original content with malicious
links8. The attacker also employs address spoofing to ensure that the emails appear to be
forming the original email senders. The email is claimed to be a re send of the original or the
updated version as a major trapping strategy.
Spear phishing: Spear phishing targets only specific groups of people. It can be said
that, instead of the casting out of the thousand of the emails randomly this kind of attacks are
took place over a large number of people who are working for a single organization9. These
kinds of attacks are referred to as high level attacks which took place are large organizations or
businesses.
Phone phishing: These kinds of attacks are somewhere differs from the email attacks. In
this sort of attacks the victims are asked for dialing a particular number and as soon as the
8 Gansterer, W.N. and Pölz, D., 2009, April. E-mail classification for phishing defense. In European
Conference on Information Retrieval (pp. 449-460). Springer, Berlin, Heidelberg.
9 Wenyin, L., Huang, G., Xiaoyue, L., Deng, X. and Min, Z., 2005, August. Phishing Web page detection.
In Document Analysis and Recognition, 2005. Proceedings. Eighth International Conference on (pp. 560-564).
IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPUTER SECURITY
attackers dial the numbers the data stored in the server get hijacked and misused by the hijackers.
For traditional cases, phone equipments use to have dedicated lines thus voice over the internet
protocol has become a very easy one to manipulate.
These kinds of attacks have become a very common one due to the excessive usage of the
shared key10. Domain key identified mails allows the business organizations to take the major
responsibility for transmitting the information from the sender to the recipient. In order to
resolve the issues of phishing attack certain mitigation strategies are also elaborated below.
3. Mitigation Methods for Email Phishing
Email phishing has become one of the most major concerns for the users, who are
utilizing emails for communication purposes. It is an extremely dangerous and vulnerable cyber
threat that has acquired the entire world of technology11. This type of cyber threat is responsible
for causing various damages to the confidentiality and integrity of sensitive information or data
of the users. However, there are some of the most important mitigation strategies or methods for
the proper eradication of this cyber threat. The most important and significant methods for
mitigation of email phishing are given below:
i) Access Control: The first and the foremost method to mitigate the cyber threat of email
phishing is controlling the overall access. If the access of the utilization of emails will be
controlled properly, the chances of this type of threat are highly reduced or diminished. Emails
are considered as the most private and confidential data12. This type of data should not be shared
10Hegt, S., 2008. Analysis of current and future phishing attacks on internet banking services. Master Thesis,
Technische Universiteit Eindhoven.
11 Anandpara, V., Dingman, A., Jakobsson, M., Liu, D. and Roinestad, H., 2007, February. Phishing IQ
tests measure fear, not ability. In International Conference on Financial Cryptography and Data Security (pp. 362-
366). Springer, Berlin, Heidelberg.
12 Sharifi, M., Saberi, A., Vahidi, M. and Zorufi, M., 2007, December. A zero knowledge password proof
mutual authentication technique against real-time phishing attacks. In International Conference on Information
attackers dial the numbers the data stored in the server get hijacked and misused by the hijackers.
For traditional cases, phone equipments use to have dedicated lines thus voice over the internet
protocol has become a very easy one to manipulate.
These kinds of attacks have become a very common one due to the excessive usage of the
shared key10. Domain key identified mails allows the business organizations to take the major
responsibility for transmitting the information from the sender to the recipient. In order to
resolve the issues of phishing attack certain mitigation strategies are also elaborated below.
3. Mitigation Methods for Email Phishing
Email phishing has become one of the most major concerns for the users, who are
utilizing emails for communication purposes. It is an extremely dangerous and vulnerable cyber
threat that has acquired the entire world of technology11. This type of cyber threat is responsible
for causing various damages to the confidentiality and integrity of sensitive information or data
of the users. However, there are some of the most important mitigation strategies or methods for
the proper eradication of this cyber threat. The most important and significant methods for
mitigation of email phishing are given below:
i) Access Control: The first and the foremost method to mitigate the cyber threat of email
phishing is controlling the overall access. If the access of the utilization of emails will be
controlled properly, the chances of this type of threat are highly reduced or diminished. Emails
are considered as the most private and confidential data12. This type of data should not be shared
10Hegt, S., 2008. Analysis of current and future phishing attacks on internet banking services. Master Thesis,
Technische Universiteit Eindhoven.
11 Anandpara, V., Dingman, A., Jakobsson, M., Liu, D. and Roinestad, H., 2007, February. Phishing IQ
tests measure fear, not ability. In International Conference on Financial Cryptography and Data Security (pp. 362-
366). Springer, Berlin, Heidelberg.
12 Sharifi, M., Saberi, A., Vahidi, M. and Zorufi, M., 2007, December. A zero knowledge password proof
mutual authentication technique against real-time phishing attacks. In International Conference on Information
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COMPUTER SECURITY
with anyone and thus to maintain the confidentiality and integrity, access control is required. It
helps to selectively restrict the overall access to any specific place or data by means of placing a
firewall in between. The users, who try to access the confidential data or information without the
permission of the authorized users, are known as unauthorized users and this type of permission
is termed as authorization13. Access control restricts the overall usability of the emails and thus
this is the most effective way to mitigate the risk of email phishing.
ii) Proper Training: Another important to stop the email phishing is proper training. If
this type of discrepancy is observed within an organization, the users should be given proper
training so that they do not share any personal details over the emails. When they would be
cautious of this fact, they will not click on any other link provided by the unauthorized web sites
or unknown email sender. This would eventually reduce the chances of email phishing to a great
extent and the emails of the employees will be secured. The users should have the capability to
verify or differentiate the authorized or the unauthorized electronic mails. For this purpose,
significant training is required. All types of potential issues or damages are hence avoided easily.
They should know that no organization would ask for any confidential or sensitive data or
information from their users. When such an email comes into the inbox of the user; they should
verify the fact, whether it is from an authorized user or not.
iii) Checking Legitimacy of Emails: The third important way to mitigate the cyber threat
of email phishing is to check the legitimacy of the electronic mails of the users. The users should
take a closer look on the display name of the sender while clicking on the email for the purpose
Systems Security (pp. 254-258). Springer, Berlin, Heidelberg.
13 Kim, Y.G., Cho, S., Lee, J.S., Lee, M.S., Kim, I.H. and Kim, S.H., 2008, June. Method for evaluating the
security risk of a website against phishing attacks. In International Conference on Intelligence and Security
Informatics (pp. 21-31). Springer, Berlin, Heidelberg.
with anyone and thus to maintain the confidentiality and integrity, access control is required. It
helps to selectively restrict the overall access to any specific place or data by means of placing a
firewall in between. The users, who try to access the confidential data or information without the
permission of the authorized users, are known as unauthorized users and this type of permission
is termed as authorization13. Access control restricts the overall usability of the emails and thus
this is the most effective way to mitigate the risk of email phishing.
ii) Proper Training: Another important to stop the email phishing is proper training. If
this type of discrepancy is observed within an organization, the users should be given proper
training so that they do not share any personal details over the emails. When they would be
cautious of this fact, they will not click on any other link provided by the unauthorized web sites
or unknown email sender. This would eventually reduce the chances of email phishing to a great
extent and the emails of the employees will be secured. The users should have the capability to
verify or differentiate the authorized or the unauthorized electronic mails. For this purpose,
significant training is required. All types of potential issues or damages are hence avoided easily.
They should know that no organization would ask for any confidential or sensitive data or
information from their users. When such an email comes into the inbox of the user; they should
verify the fact, whether it is from an authorized user or not.
iii) Checking Legitimacy of Emails: The third important way to mitigate the cyber threat
of email phishing is to check the legitimacy of the electronic mails of the users. The users should
take a closer look on the display name of the sender while clicking on the email for the purpose
Systems Security (pp. 254-258). Springer, Berlin, Heidelberg.
13 Kim, Y.G., Cho, S., Lee, J.S., Lee, M.S., Kim, I.H. and Kim, S.H., 2008, June. Method for evaluating the
security risk of a website against phishing attacks. In International Conference on Intelligence and Security
Informatics (pp. 21-31). Springer, Berlin, Heidelberg.

8COMPUTER SECURITY
of reading it14. This would help them in understanding whether the sender is legitimate or not.
Moreover, the legitimacy of the electronic mails is also checked by this. All the organizations
utilize a specific domain for the emails or URLs, so that the email, which is originating from a
separate domain, is marked with red flag.
iv) Checking for Mismatched URLs: The next important method to mitigate the cyber
threat of email phishing is the proper checking of the mismatched or wrong URLs. When the
embedded URL seems properly valid, it should be hovered for showing a separate web address.
Moreover, the users must be avoiding clicking on various links within emails unless and until
these emails are absolutely sure of the fact that the links are legitimate.
v) Checking of Proper Subject: Another significant method or way to mitigate the
several cyber threat of email phishing is checking of the subject of the sent electronic mail15.
Most of the phishing mails do not comprise of any generic subject or greeting, hence, it should
be verified that the electronic mail contains a proper greeting and relevant subject. If this type of
subject is absent, the email should be avoided and even discarded. The discarding of emails
should be done only if the sender is unknown to the receiver16. Often, a known sender send
emails with no subject. This type of emails should not be discarded by the receiver.
vi) Installation of Anti Phishing Software: Another important way to mitigate the email
phishing is to install the anti phishing software within the system. If the system will not comprise
14 Kim, Y.G., Cho, S., Lee, J.S., Lee, M.S., Kim, I.H. and Kim, S.H., 2008, June. Method for evaluating the
security risk of a website against phishing attacks. In International Conference on Intelligence and Security
Informatics (pp. 21-31). Springer, Berlin, Heidelberg.
15 Dodge Jr, R.C., Carver, C. and Ferguson, A.J., 2007. Phishing for user security awareness. computers &
security, 26(1), pp.73-80.
16 Arachchilage, N.A.G. and Love, S., 2014. Security awareness of computer users: A phishing threat
avoidance perspective. Computers in Human Behavior, 38, pp.304-312.
of reading it14. This would help them in understanding whether the sender is legitimate or not.
Moreover, the legitimacy of the electronic mails is also checked by this. All the organizations
utilize a specific domain for the emails or URLs, so that the email, which is originating from a
separate domain, is marked with red flag.
iv) Checking for Mismatched URLs: The next important method to mitigate the cyber
threat of email phishing is the proper checking of the mismatched or wrong URLs. When the
embedded URL seems properly valid, it should be hovered for showing a separate web address.
Moreover, the users must be avoiding clicking on various links within emails unless and until
these emails are absolutely sure of the fact that the links are legitimate.
v) Checking of Proper Subject: Another significant method or way to mitigate the
several cyber threat of email phishing is checking of the subject of the sent electronic mail15.
Most of the phishing mails do not comprise of any generic subject or greeting, hence, it should
be verified that the electronic mail contains a proper greeting and relevant subject. If this type of
subject is absent, the email should be avoided and even discarded. The discarding of emails
should be done only if the sender is unknown to the receiver16. Often, a known sender send
emails with no subject. This type of emails should not be discarded by the receiver.
vi) Installation of Anti Phishing Software: Another important way to mitigate the email
phishing is to install the anti phishing software within the system. If the system will not comprise
14 Kim, Y.G., Cho, S., Lee, J.S., Lee, M.S., Kim, I.H. and Kim, S.H., 2008, June. Method for evaluating the
security risk of a website against phishing attacks. In International Conference on Intelligence and Security
Informatics (pp. 21-31). Springer, Berlin, Heidelberg.
15 Dodge Jr, R.C., Carver, C. and Ferguson, A.J., 2007. Phishing for user security awareness. computers &
security, 26(1), pp.73-80.
16 Arachchilage, N.A.G. and Love, S., 2014. Security awareness of computer users: A phishing threat
avoidance perspective. Computers in Human Behavior, 38, pp.304-312.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMPUTER SECURITY
of this type of software, there is always a high chance that such emails would be coming and no
notification would be provided. However, if an anti phishing software is present or is installed
within the system, the victim can easily mitigate this type of risk or threat and their emails would
be safe and secured.
The above-mentioned methods are extremely useful for any user to mitigate the overall
risk of email phishing.
Conclusion
Therefore, from the above discussion, it can be concluded that email phishing is the sole
attempt for the purpose of obtaining any type of sensitive information from the electronic mails
like credit card credentials, passwords, usernames and many more. This is mainly done for
various malicious reasons by means of remaining disguised as one of the most trustworthy
entities within electronic communication. The email phishing is subsequently carried out by the
email spoofing or even instant messaging. The users are often directed in entering their personal
information within any particular fake web site. The users cannot differentiate amongst the legal
or the illegal administrators of the web site. The most significant victims of this type of cyber
threat are banks, social web sites, IT administrators, auction sites and online payment processors.
The phishing emails mainly comprise of various links of the web sites, which are responsible for
distributing malware. It is one of the most important example of the social engineering technique
that is utilized for deceiving the users and also exploiting the weaknesses within the recent
security of web site. The above report has properly outlined the entire concept of email phishing
with relevant details. There are various potential damages that are possible with email phishing.
All of these potential damages of the email phishing are properly mentioned here. Moreover, the
of this type of software, there is always a high chance that such emails would be coming and no
notification would be provided. However, if an anti phishing software is present or is installed
within the system, the victim can easily mitigate this type of risk or threat and their emails would
be safe and secured.
The above-mentioned methods are extremely useful for any user to mitigate the overall
risk of email phishing.
Conclusion
Therefore, from the above discussion, it can be concluded that email phishing is the sole
attempt for the purpose of obtaining any type of sensitive information from the electronic mails
like credit card credentials, passwords, usernames and many more. This is mainly done for
various malicious reasons by means of remaining disguised as one of the most trustworthy
entities within electronic communication. The email phishing is subsequently carried out by the
email spoofing or even instant messaging. The users are often directed in entering their personal
information within any particular fake web site. The users cannot differentiate amongst the legal
or the illegal administrators of the web site. The most significant victims of this type of cyber
threat are banks, social web sites, IT administrators, auction sites and online payment processors.
The phishing emails mainly comprise of various links of the web sites, which are responsible for
distributing malware. It is one of the most important example of the social engineering technique
that is utilized for deceiving the users and also exploiting the weaknesses within the recent
security of web site. The above report has properly outlined the entire concept of email phishing
with relevant details. There are various potential damages that are possible with email phishing.
All of these potential damages of the email phishing are properly mentioned here. Moreover, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10COMPUTER SECURITY
users could be in great danger as it compromises with the security and confidentiality of the
users. Significant mitigation methods are also given here.
Recommendations
The important recommendations for the victims of email phishing are given below:
i) The first recommendation is to restrict the total access of the usernames and passwords
of the email account. This would eventually restrict the access of the data and the unauthorized
users cannot access the information.
ii) The second significant recommendation for the victims of email phishing is to restrict
the overall usability of physical systems. Due to the restriction of physical systems, the hackers
or the attackers cannot access the email and hence the chances of this type of cyber threat are
reduced.
iii) The third recommendation is to deploy a continuous monitoring, detection as well as
response for the emails. A verification link is one of them. The users could be able to track down
the activities, if any unauthorized user accesses the emails or email accounts.
iv) The next recommendation is to limit the execution. There are various application
control solutions that are responsible for mitigating the risks of execution. This type of
methodology should be incorporated within any system for ensuring that only the specific list of
authorized binaries would be running on the various systems.
users could be in great danger as it compromises with the security and confidentiality of the
users. Significant mitigation methods are also given here.
Recommendations
The important recommendations for the victims of email phishing are given below:
i) The first recommendation is to restrict the total access of the usernames and passwords
of the email account. This would eventually restrict the access of the data and the unauthorized
users cannot access the information.
ii) The second significant recommendation for the victims of email phishing is to restrict
the overall usability of physical systems. Due to the restriction of physical systems, the hackers
or the attackers cannot access the email and hence the chances of this type of cyber threat are
reduced.
iii) The third recommendation is to deploy a continuous monitoring, detection as well as
response for the emails. A verification link is one of them. The users could be able to track down
the activities, if any unauthorized user accesses the emails or email accounts.
iv) The next recommendation is to limit the execution. There are various application
control solutions that are responsible for mitigating the risks of execution. This type of
methodology should be incorporated within any system for ensuring that only the specific list of
authorized binaries would be running on the various systems.

11COMPUTER SECURITY
References
Arachchilage, N.A.G. and Love, S., 2014. Security awareness of computer users: A phishing
threat avoidance perspective. Computers in Human Behavior, 38, pp.304-312.
Cao, Y., Han, W. and Le, Y., 2008, October. Anti-phishing based on automated individual white-
list. In Proceedings of the 4th ACM workshop on Digital identity management (pp. 51-60).
ACM.
Dhamija, R. and Tygar, J.D., 2005, July. The battle against phishing: Dynamic security skins.
In Proceedings of the 2005 symposium on Usable privacy and security (pp. 77-88). ACM.
Dodge Jr, R.C., Carver, C. and Ferguson, A.J., 2007. Phishing for user security
awareness. computers & security, 26(1), pp.73-80.
Fette, I., Sadeh, N. and Tomasic, A., 2006. Learning to detect phishing emails (No. CMU-ISRI-
06-112). CARNEGIE-MELLON UNIV PITTSBURGH PA DEPT OF COMPUTER SCIENCE.
Gansterer, W.N. and Pölz, D., 2009, April. E-mail classification for phishing defense.
In European Conference on Information Retrieval (pp. 449-460). Springer, Berlin, Heidelberg.
Hegt, S., 2008. Analysis of current and future phishing attacks on internet banking
services. Master Thesis, Technische Universiteit Eindhoven.
Kim, Y.G., Cho, S., Lee, J.S., Lee, M.S., Kim, I.H. and Kim, S.H., 2008, June. Method for
evaluating the security risk of a website against phishing attacks. In International Conference on
Intelligence and Security Informatics (pp. 21-31). Springer, Berlin, Heidelberg.
References
Arachchilage, N.A.G. and Love, S., 2014. Security awareness of computer users: A phishing
threat avoidance perspective. Computers in Human Behavior, 38, pp.304-312.
Cao, Y., Han, W. and Le, Y., 2008, October. Anti-phishing based on automated individual white-
list. In Proceedings of the 4th ACM workshop on Digital identity management (pp. 51-60).
ACM.
Dhamija, R. and Tygar, J.D., 2005, July. The battle against phishing: Dynamic security skins.
In Proceedings of the 2005 symposium on Usable privacy and security (pp. 77-88). ACM.
Dodge Jr, R.C., Carver, C. and Ferguson, A.J., 2007. Phishing for user security
awareness. computers & security, 26(1), pp.73-80.
Fette, I., Sadeh, N. and Tomasic, A., 2006. Learning to detect phishing emails (No. CMU-ISRI-
06-112). CARNEGIE-MELLON UNIV PITTSBURGH PA DEPT OF COMPUTER SCIENCE.
Gansterer, W.N. and Pölz, D., 2009, April. E-mail classification for phishing defense.
In European Conference on Information Retrieval (pp. 449-460). Springer, Berlin, Heidelberg.
Hegt, S., 2008. Analysis of current and future phishing attacks on internet banking
services. Master Thesis, Technische Universiteit Eindhoven.
Kim, Y.G., Cho, S., Lee, J.S., Lee, M.S., Kim, I.H. and Kim, S.H., 2008, June. Method for
evaluating the security risk of a website against phishing attacks. In International Conference on
Intelligence and Security Informatics (pp. 21-31). Springer, Berlin, Heidelberg.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





