MN604 IT Security Management: Computer Security Tools Demonstration
VerifiedAdded on 2023/06/12
|13
|3048
|206
Report
AI Summary
This report discusses penetration techniques for vulnerability detection and network security, focusing on Snort for intrusion detection. It details Snort's installation and configuration, including WinPcap, Snort rules, and configuration file adjustments. The report also covers Honey Pot and Nessus deployment, along with researching security vulnerabilities in applications, emphasizing risk mitigation through vulnerability identification and patching. Penetration techniques such as social engineering, web application testing, physical penetration testing, network service testing, client-side testing, and wireless security testing are explored. The report concludes that penetration testing helps organizations exploit network vulnerabilities and secure against external threats, with Snort and Nessus playing crucial roles in intrusion and vulnerability detection.

Running head: IT SECURITY MANAGEMENT
Demonstration of Computer Security Tools
Name of the student
Name of the University
Author’s Note
Demonstration of Computer Security Tools
Name of the student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT SECURITY MANAGEMENT
Table of Contents
Introduction...........................................................................................................................................2
Install/ Deploy of snort..........................................................................................................................2
Researching on security vulnerabilities of an application......................................................................4
2 Penetration techniques......................................................................................................................5
Conclusion.............................................................................................................................................6
References.............................................................................................................................................7
IT SECURITY MANAGEMENT
Table of Contents
Introduction...........................................................................................................................................2
Install/ Deploy of snort..........................................................................................................................2
Researching on security vulnerabilities of an application......................................................................4
2 Penetration techniques......................................................................................................................5
Conclusion.............................................................................................................................................6
References.............................................................................................................................................7

2
IT SECURITY MANAGEMENT
Introduction
The report is prepared for the discussion of the penetration techniques that can be used for
detection of the vulnerability of a system and secure the network from outside breaches. There are
different network penetration tools and that can be used for getting the access of the core network
devices and among them Snort is chosen for intrusion detection. Snot is a popular open source tool
that can be used for detection of the overlapping fragments and currently used in the assignment for
penetration testing of a network.
Install/ Deploy of snort
For the installation or deployment of snort three files are required to be downloaded that is
the WinPcap fr capturing the data packets, snort installer and the set of snort rules. The snort rules
package should be extracted after installation of the snort and the winpcap .exe files. A subfolder
should be created during the extraction of the snort rules file under the c:\Snort directory. The
contents of the rules folder should be extracted in the folder C:\Snort\rules and the contents of the
preproc_rules should be extracted to the Snort:\preproc_rules directory. The rest of the folders
should be ignored because they are created by sourcefire for Linux and windows does not support
those files.
After the completion of the installation of the components the repose of the program can be
checked using the following commands in the command prompt.
For changing the directory to snot program the following command is used:
C:\>cd \Snort\bin
The installed version of Snort can be checked using the command C: \Snort\bin>snort –V
The command C: \Snort\bin>snort –w is used for checking the details of the network
adapters connected with the system and configure the snort to listen to the particular adapter when
it runs.
IT SECURITY MANAGEMENT
Introduction
The report is prepared for the discussion of the penetration techniques that can be used for
detection of the vulnerability of a system and secure the network from outside breaches. There are
different network penetration tools and that can be used for getting the access of the core network
devices and among them Snort is chosen for intrusion detection. Snot is a popular open source tool
that can be used for detection of the overlapping fragments and currently used in the assignment for
penetration testing of a network.
Install/ Deploy of snort
For the installation or deployment of snort three files are required to be downloaded that is
the WinPcap fr capturing the data packets, snort installer and the set of snort rules. The snort rules
package should be extracted after installation of the snort and the winpcap .exe files. A subfolder
should be created during the extraction of the snort rules file under the c:\Snort directory. The
contents of the rules folder should be extracted in the folder C:\Snort\rules and the contents of the
preproc_rules should be extracted to the Snort:\preproc_rules directory. The rest of the folders
should be ignored because they are created by sourcefire for Linux and windows does not support
those files.
After the completion of the installation of the components the repose of the program can be
checked using the following commands in the command prompt.
For changing the directory to snot program the following command is used:
C:\>cd \Snort\bin
The installed version of Snort can be checked using the command C: \Snort\bin>snort –V
The command C: \Snort\bin>snort –w is used for checking the details of the network
adapters connected with the system and configure the snort to listen to the particular adapter when
it runs.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
IT SECURITY MANAGEMENT
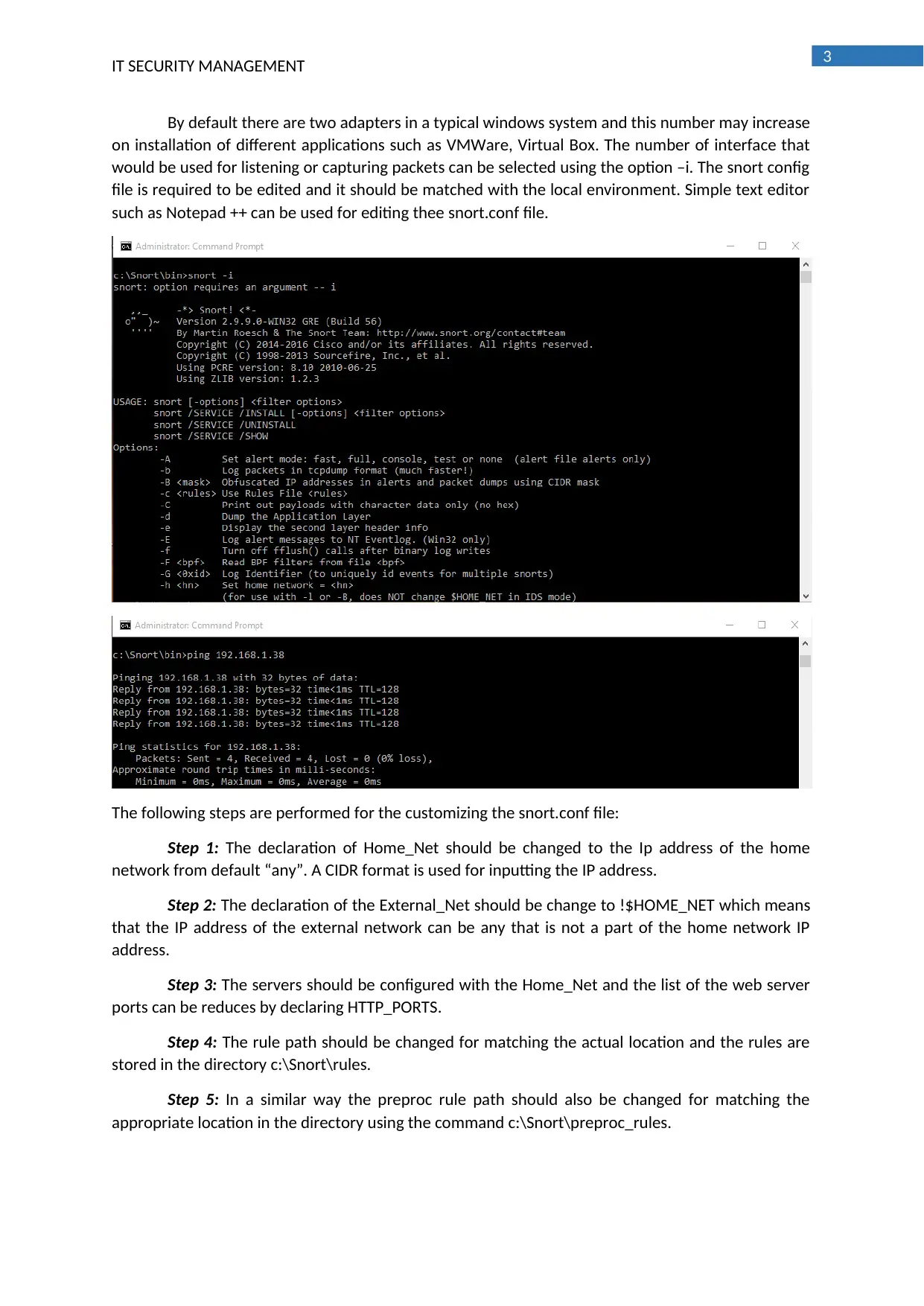
By default there are two adapters in a typical windows system and this number may increase
on installation of different applications such as VMWare, Virtual Box. The number of interface that
would be used for listening or capturing packets can be selected using the option –i. The snort config
file is required to be edited and it should be matched with the local environment. Simple text editor
such as Notepad ++ can be used for editing thee snort.conf file.
The following steps are performed for the customizing the snort.conf file:
Step 1: The declaration of Home_Net should be changed to the Ip address of the home
network from default “any”. A CIDR format is used for inputting the IP address.
Step 2: The declaration of the External_Net should be change to !$HOME_NET which means
that the IP address of the external network can be any that is not a part of the home network IP
address.
Step 3: The servers should be configured with the Home_Net and the list of the web server
ports can be reduces by declaring HTTP_PORTS.
Step 4: The rule path should be changed for matching the actual location and the rules are
stored in the directory c:\Snort\rules.
Step 5: In a similar way the preproc rule path should also be changed for matching the
appropriate location in the directory using the command c:\Snort\preproc_rules.
IT SECURITY MANAGEMENT
By default there are two adapters in a typical windows system and this number may increase
on installation of different applications such as VMWare, Virtual Box. The number of interface that
would be used for listening or capturing packets can be selected using the option –i. The snort config
file is required to be edited and it should be matched with the local environment. Simple text editor
such as Notepad ++ can be used for editing thee snort.conf file.
The following steps are performed for the customizing the snort.conf file:
Step 1: The declaration of Home_Net should be changed to the Ip address of the home
network from default “any”. A CIDR format is used for inputting the IP address.
Step 2: The declaration of the External_Net should be change to !$HOME_NET which means
that the IP address of the external network can be any that is not a part of the home network IP
address.
Step 3: The servers should be configured with the Home_Net and the list of the web server
ports can be reduces by declaring HTTP_PORTS.
Step 4: The rule path should be changed for matching the actual location and the rules are
stored in the directory c:\Snort\rules.
Step 5: In a similar way the preproc rule path should also be changed for matching the
appropriate location in the directory using the command c:\Snort\preproc_rules.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
IT SECURITY MANAGEMENT
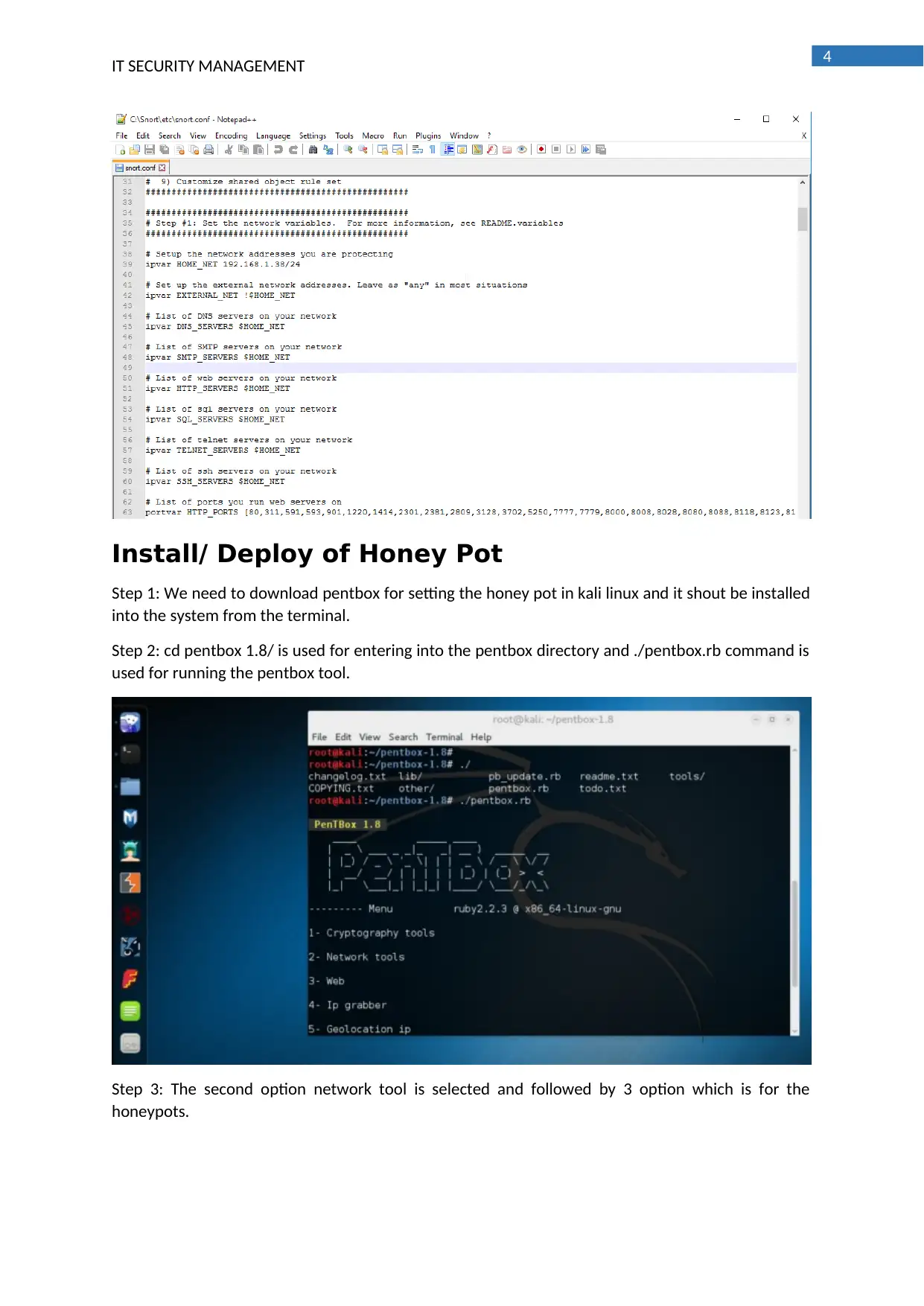
Install/ Deploy of Honey Pot
Step 1: We need to download pentbox for setting the honey pot in kali linux and it shout be installed
into the system from the terminal.
Step 2: cd pentbox 1.8/ is used for entering into the pentbox directory and ./pentbox.rb command is
used for running the pentbox tool.
Step 3: The second option network tool is selected and followed by 3 option which is for the
honeypots.
IT SECURITY MANAGEMENT
Install/ Deploy of Honey Pot
Step 1: We need to download pentbox for setting the honey pot in kali linux and it shout be installed
into the system from the terminal.
Step 2: cd pentbox 1.8/ is used for entering into the pentbox directory and ./pentbox.rb command is
used for running the pentbox tool.
Step 3: The second option network tool is selected and followed by 3 option which is for the
honeypots.
5
IT SECURITY MANAGEMENT
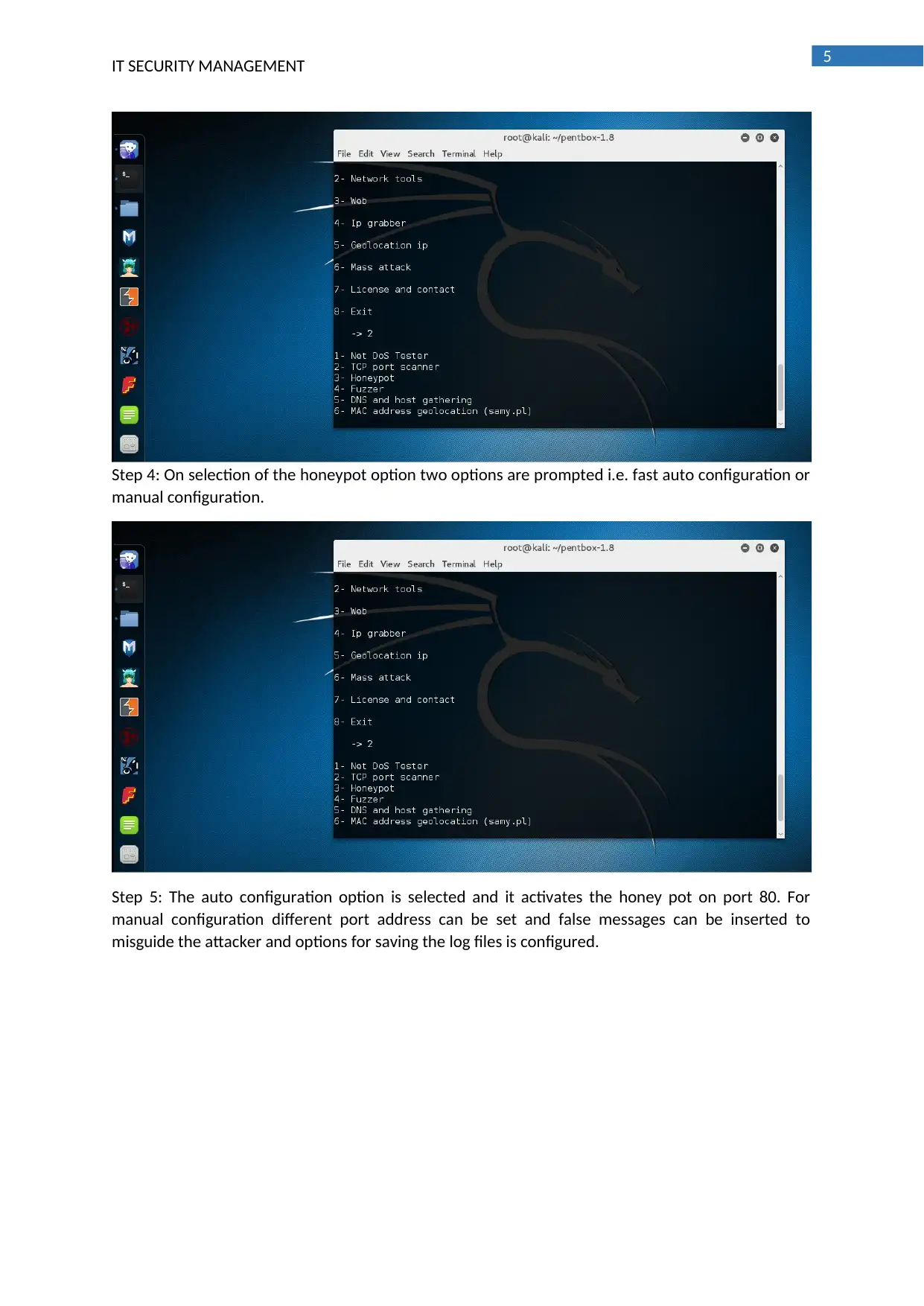
Step 4: On selection of the honeypot option two options are prompted i.e. fast auto configuration or
manual configuration.
Step 5: The auto configuration option is selected and it activates the honey pot on port 80. For
manual configuration different port address can be set and false messages can be inserted to
misguide the attacker and options for saving the log files is configured.
IT SECURITY MANAGEMENT
Step 4: On selection of the honeypot option two options are prompted i.e. fast auto configuration or
manual configuration.
Step 5: The auto configuration option is selected and it activates the honey pot on port 80. For
manual configuration different port address can be set and false messages can be inserted to
misguide the attacker and options for saving the log files is configured.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IT SECURITY MANAGEMENT
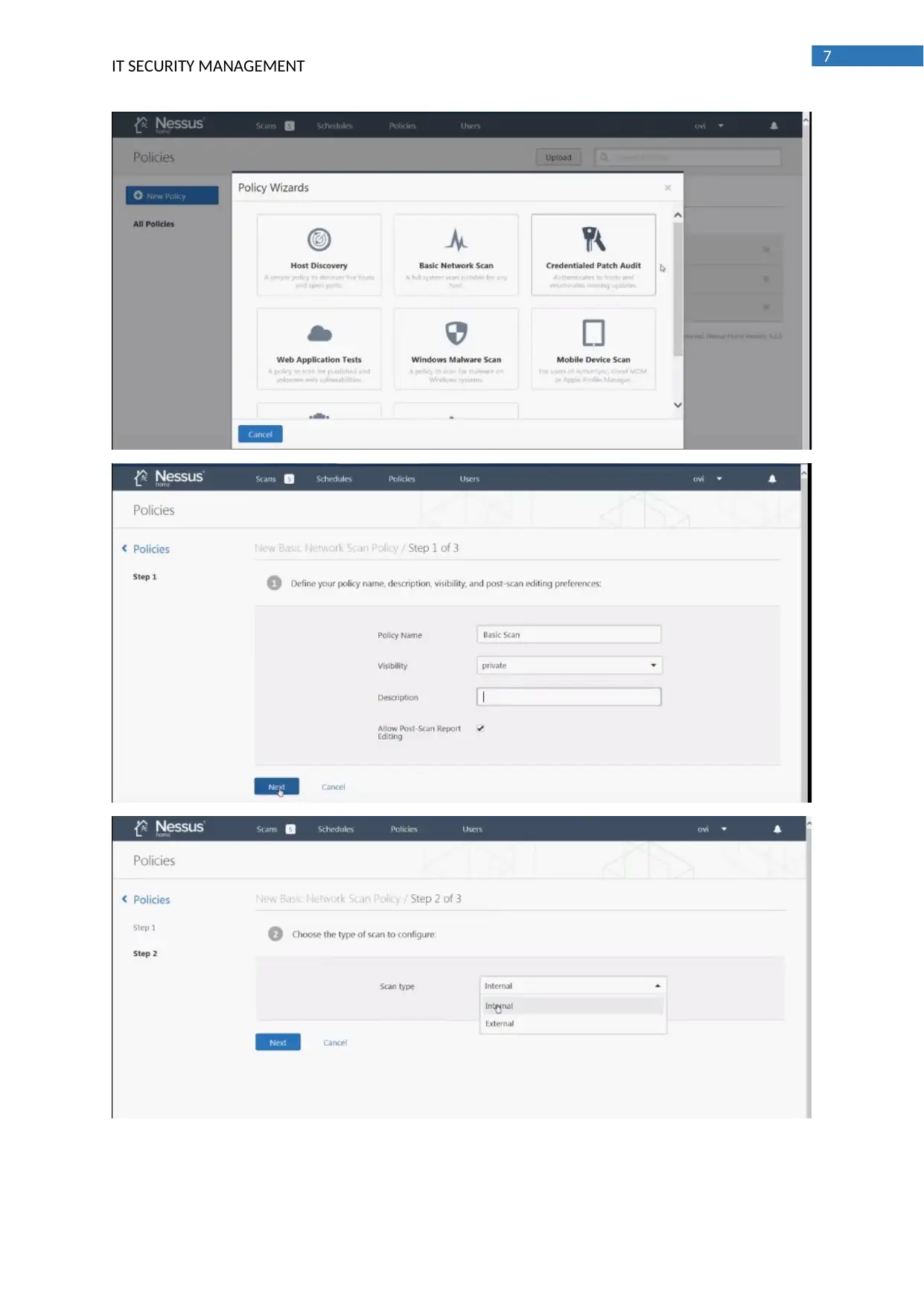
Install/ Deploy of Nessus
For installation and deployment of Nessus a windows machine is used and it can be
deployed using the cmd command line interface or the GUI graphical user interface can also be used
for the installation. The default options are selected for the installation of Nessus and on the
configuration option the agent key values should be entered followed by the server (host) and the
value of the groups. Different strategies can be followed for the deployment of the Nessus and it is
also supported by all the platforms.
IT SECURITY MANAGEMENT
Install/ Deploy of Nessus
For installation and deployment of Nessus a windows machine is used and it can be
deployed using the cmd command line interface or the GUI graphical user interface can also be used
for the installation. The default options are selected for the installation of Nessus and on the
configuration option the agent key values should be entered followed by the server (host) and the
value of the groups. Different strategies can be followed for the deployment of the Nessus and it is
also supported by all the platforms.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
IT SECURITY MANAGEMENT
IT SECURITY MANAGEMENT

8
IT SECURITY MANAGEMENT
Researching on security vulnerabilities of an
application
The current networking environment is extremely vulnerable and thus research should be
made for protecting the software vendor and protecting the users for to keep the sensitive
information securely. For beginning with the research the basic vulnerability acting on a system
should be identified. The vulnerability includes the flaws in the software applications and security
engineers should be consulted for the identification of vulnerabilities on the system. The
vulnerability research helps in mitigation of the risk by discovering the weakness and installation of
patches for blocking the source. The installation of antivirus programs can help in eliminating the
security flaws protect the system from data corruption, data theft, and data loss.
Some problems are faced during the vulnerability research because there are different
controversies faced by the network research team for disclosing a mixed result for the end users.
The change in the landscape of the vulnerability research can help in increasing the awareness that
any of the user can be a victim of cyber-attacks. For the analysis of the security vulnerability it is
important to find the weakness of the system and patch them quickly for the establishment of the
security policy and secure the system form external agents. For exposing the vulnerabilities of the
applications manual and technical audits are needed to be done and different research service
should be followed based on the type of the application such as client based, web based or server
based applications. The vulnerability research service should also follow the following critical
vulnerabilities for the exploitation of the loop holes.
Validation of the inputs
Buffer overrun
Dangling pointers
SQL injection
Remote code execution
Code injection and
Bypassing the authentication
IT SECURITY MANAGEMENT
Researching on security vulnerabilities of an
application
The current networking environment is extremely vulnerable and thus research should be
made for protecting the software vendor and protecting the users for to keep the sensitive
information securely. For beginning with the research the basic vulnerability acting on a system
should be identified. The vulnerability includes the flaws in the software applications and security
engineers should be consulted for the identification of vulnerabilities on the system. The
vulnerability research helps in mitigation of the risk by discovering the weakness and installation of
patches for blocking the source. The installation of antivirus programs can help in eliminating the
security flaws protect the system from data corruption, data theft, and data loss.
Some problems are faced during the vulnerability research because there are different
controversies faced by the network research team for disclosing a mixed result for the end users.
The change in the landscape of the vulnerability research can help in increasing the awareness that
any of the user can be a victim of cyber-attacks. For the analysis of the security vulnerability it is
important to find the weakness of the system and patch them quickly for the establishment of the
security policy and secure the system form external agents. For exposing the vulnerabilities of the
applications manual and technical audits are needed to be done and different research service
should be followed based on the type of the application such as client based, web based or server
based applications. The vulnerability research service should also follow the following critical
vulnerabilities for the exploitation of the loop holes.
Validation of the inputs
Buffer overrun
Dangling pointers
SQL injection
Remote code execution
Code injection and
Bypassing the authentication
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT SECURITY MANAGEMENT
The test result should include the details of the issues identified from the application, technical
and strategic recommendations and the results obtained from the exploitation.
2 Penetration techniques
The penetration techniques is used for analysing the security vulnerabilities after the evaluation
of the network or the systems with the implementation of malicious methodology. The penetration
technique exploits the current weakness and errors in the configuration codes and the main purpose
of the penetration techniques is to secure the organizational data from the unauthorised users. On
the successful identification of the vulnerability it is used by the tester for accessing the sensitive
information of the organization. The following are the types of penetration techniques that can be
used are as follows:
Social Engineering test – It is used for the exploitation of the personal data, passwords and
sensitive organizational information. It can be caused due to human errors. Security policy
and standards should be used for avoiding this type of vulnerability and conduction of
security audits helps in removal of the flaws.
Web application test – Software methodology is used for the exposure of the security
threats and the web applications, software programs installed in the targeted system are
exploited for analysis of the flaws.
Physical penetration test – It is used for the application of sensitive data protection by
testing all the network devices for any possibility of breach and the testing is not relevant as
the software testing.
Network service test – The open ports in the network are identified using different network
analysis tool and the network devices are reconfigured for mitigation of the risk.
Client side test – the client side software applications are analysed for the exploitation of the
vulnerabilities.
Wireless security test – The intruders can intrude in the network through the unsecured
wireless access points and thus some security algorithms should be applied for restricting
the unauthorised users to connect with the organizational network.
There are different commercial tools such as Nessus, Nmap, metasploit that can be used for
penetration testing. The penetration technique can be done manually or using automated tools and
moreover both the manual and the automatic process can be combined for analysing the
vulnerability of a network. For the selection of the best penetration tool are given below:
Ease of deployment, configuration and usability of the tool.
The tool must be used for scanning the system easily.
The vulnerability can be categorized according to their severity and it should be verified
automatically.
It should be able to re verify the previous vulnerability found in the system
It should be able to create logs and reports
Nessus is used for the identification of the vulnerability, issues for configuration and the
malware that can be used by the attacker for intruding into the computer’s network. The main
features of the Nessus is easy to use and policy can be created easily on few clicks. For the detection
of the vulnerabilities different technologies are used and it can accommodate the growth of the
network. Nessus can be accessed from any web browser and it is used for It consists of the following
terminology such as
IT SECURITY MANAGEMENT
The test result should include the details of the issues identified from the application, technical
and strategic recommendations and the results obtained from the exploitation.
2 Penetration techniques
The penetration techniques is used for analysing the security vulnerabilities after the evaluation
of the network or the systems with the implementation of malicious methodology. The penetration
technique exploits the current weakness and errors in the configuration codes and the main purpose
of the penetration techniques is to secure the organizational data from the unauthorised users. On
the successful identification of the vulnerability it is used by the tester for accessing the sensitive
information of the organization. The following are the types of penetration techniques that can be
used are as follows:
Social Engineering test – It is used for the exploitation of the personal data, passwords and
sensitive organizational information. It can be caused due to human errors. Security policy
and standards should be used for avoiding this type of vulnerability and conduction of
security audits helps in removal of the flaws.
Web application test – Software methodology is used for the exposure of the security
threats and the web applications, software programs installed in the targeted system are
exploited for analysis of the flaws.
Physical penetration test – It is used for the application of sensitive data protection by
testing all the network devices for any possibility of breach and the testing is not relevant as
the software testing.
Network service test – The open ports in the network are identified using different network
analysis tool and the network devices are reconfigured for mitigation of the risk.
Client side test – the client side software applications are analysed for the exploitation of the
vulnerabilities.
Wireless security test – The intruders can intrude in the network through the unsecured
wireless access points and thus some security algorithms should be applied for restricting
the unauthorised users to connect with the organizational network.
There are different commercial tools such as Nessus, Nmap, metasploit that can be used for
penetration testing. The penetration technique can be done manually or using automated tools and
moreover both the manual and the automatic process can be combined for analysing the
vulnerability of a network. For the selection of the best penetration tool are given below:
Ease of deployment, configuration and usability of the tool.
The tool must be used for scanning the system easily.
The vulnerability can be categorized according to their severity and it should be verified
automatically.
It should be able to re verify the previous vulnerability found in the system
It should be able to create logs and reports
Nessus is used for the identification of the vulnerability, issues for configuration and the
malware that can be used by the attacker for intruding into the computer’s network. The main
features of the Nessus is easy to use and policy can be created easily on few clicks. For the detection
of the vulnerabilities different technologies are used and it can accommodate the growth of the
network. Nessus can be accessed from any web browser and it is used for It consists of the following
terminology such as
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT SECURITY MANAGEMENT
Policy – It is used for configure the setting and perform a scan on the network.
Scan – It is used for finding the associated list of Ip address and the domain names
Report – it is used for creating a specific instance of the scan performed
Plugin – It is used for creating security check and the plugin can be FTP, Webservers and for
Cisco devices.
Snot can also be used for penetration testing and it is required to be installed in different
location for getting the visibility of the network and aiming the attacks that could be done on the
network. The installation of the snort outside the firewall helps in monitoring the data traffic that
are hitting the site and the basic requirement for installation of the snort outside the firewall is a
switch with the capability of port mirroring. For the installation of the snort inside the firewall the
sensor should be placed in the demilitarized zone and the logs should be matched from the external
sensor for collection of data about the network and validation of the firewall rules for fixing the
problem that are exploited in the network. The snot can also be installed on each of the servers
installed in the network and it helps in creation of a lightweight intrusion detection system. The
sensors are easy to deploy and can be installed everywhere in the network for monitoring the
current activity of the network. There is no requirement for the inclusion of the SQL, FTP and HTTP
rules on the mail servers and in the same manner there is no requirement to include the HTTP
exploitation in the Apache based Web servers installed in the network.
Conclusion
From the above report it can be concluded that performing the penetration techniques can
help the organization to exploit the vulnerability of the current network and secure it from external
agents for accessing the sensitive information of the network. Snort can be used for detecting the
intrusion and the Nessus is used for the exploitation of the vulnerability of the system. Moreover
using Nessus tool security application policy can be created for its application in the organizational
network and improve the security of the organizational information’s. Different type of policy such
as web application scan policy can be created for automating the testing procedure and the basic
scan template can be used creating a new scan and the targeted IP address and the domain name
should be inputted for starting the scan of the network. Thus it is important to find the flaws in the
current system and eliminate the vulnerabilities identified in the current system.
IT SECURITY MANAGEMENT
Policy – It is used for configure the setting and perform a scan on the network.
Scan – It is used for finding the associated list of Ip address and the domain names
Report – it is used for creating a specific instance of the scan performed
Plugin – It is used for creating security check and the plugin can be FTP, Webservers and for
Cisco devices.
Snot can also be used for penetration testing and it is required to be installed in different
location for getting the visibility of the network and aiming the attacks that could be done on the
network. The installation of the snort outside the firewall helps in monitoring the data traffic that
are hitting the site and the basic requirement for installation of the snort outside the firewall is a
switch with the capability of port mirroring. For the installation of the snort inside the firewall the
sensor should be placed in the demilitarized zone and the logs should be matched from the external
sensor for collection of data about the network and validation of the firewall rules for fixing the
problem that are exploited in the network. The snot can also be installed on each of the servers
installed in the network and it helps in creation of a lightweight intrusion detection system. The
sensors are easy to deploy and can be installed everywhere in the network for monitoring the
current activity of the network. There is no requirement for the inclusion of the SQL, FTP and HTTP
rules on the mail servers and in the same manner there is no requirement to include the HTTP
exploitation in the Apache based Web servers installed in the network.
Conclusion
From the above report it can be concluded that performing the penetration techniques can
help the organization to exploit the vulnerability of the current network and secure it from external
agents for accessing the sensitive information of the network. Snort can be used for detecting the
intrusion and the Nessus is used for the exploitation of the vulnerability of the system. Moreover
using Nessus tool security application policy can be created for its application in the organizational
network and improve the security of the organizational information’s. Different type of policy such
as web application scan policy can be created for automating the testing procedure and the basic
scan template can be used creating a new scan and the targeted IP address and the domain name
should be inputted for starting the scan of the network. Thus it is important to find the flaws in the
current system and eliminate the vulnerabilities identified in the current system.

11
IT SECURITY MANAGEMENT
Bibliography
[1]. Antrobus, Rob, Sylvain Frey, Benjamin Green, and Awais Rashid. "Simaticscan: Towards a
specialised vulnerability scanner for industrial control systems." BCS, 2016.
[2]. Arambatzis, Theodoros, Ioannis Lazaridis, and Sotirios Pouros. "Modern Windows Server
Operating Systems Vulnerabilities." In The Third International Conference on Computer
Science, Computer Engineering, and Social Media (CSCESM2016), p. 29. 2016.
[3]. Bul'ajoul, Waleed, Anne James, and Mandeep Pannu. "Improving network intrusion
detection system performance through quality of service configuration and parallel
technology." Journal of Computer and System Sciences 81, no. 6 (2015): 981-999.
[4]. Coffey, Kyle, Richard Smith, Leandros Maglaras, and Helge Janicke. "Vulnerability Analysis of
Network Scanning on SCADA Systems." Security and Communication Networks2018 (2018).
[5]. El, Malaka, Emma McMahon, Sagar Samtani, Mark Patton, and Hsinchun Chen.
"Benchmarking vulnerability scanners: An experiment on SCADA devices and scientific
instruments." In Intelligence and Security Informatics (ISI), 2017 IEEE International
Conference on, pp. 83-88. IEEE, 2017.
[6]. Hacke, U.G., Venturas, M.D., MacKinnon, E.D., Jacobsen, A.L., Sperry, J.S. and Pratt, R.B.,
2015. The standard centrifuge method accurately measures vulnerability curves of long‐
vesselled olive stems. New Phytologist, 205(1), pp.116-127.
[7]. Kenkre, Poonam Sinai, Anusha Pai, and Louella Colaco. "Real time intrusion detection and
prevention system." In Proceedings of the 3rd International Conference on Frontiers of
Intelligent Computing: Theory and Applications (FICTA) 2014, pp. 405-411. Springer, Cham,
2015.
[8]. Khari, Manju, and Neha Singh. "Web Services Vulnerability Testing Using Open source
Security Scanners: An experimental Study." International Journal of Advanced Engineering
and Global Technology (IJAEGT) (2014): 790-799.
[9]. Kuvaiskii, Dmitrii, Somnath Chakrabarti, and Mona Vij. "Snort Intrusion Detection System
with Intel Software Guard Extension (Intel SGX)." arXiv preprint arXiv:1802.00508(2018).
[10]. Orth, Ulrich, Richard W. Robins, Laurenz L. Meier, and Rand D. Conger. "Refining the
vulnerability model of low self-esteem and depression: Disentangling the effects of genuine
self-esteem and narcissism." Journal of Personality and Social Psychology 110, no. 1 (2016):
133.
[11]. Peureux, Fabien. "Risk-Driven Vulnerability Testing: Results from eHealth
Experiments Using Patterns and Model-Based Approach." In Risk Assessment and Risk-
Driven Testing: Third International Workshop, RISK 2015, Berlin, Germany, June 15, 2015.
Revised Selected Papers, vol. 9488, p. 93. Springer, 2015.
[12]. Schiff, G. D., M. G. Amato, T. Eguale, J. J. Boehne, Adam Wright, Ross Koppel, A. H.
Rashidee et al. "Computerised physician order entry-related medication errors: analysis of
reported errors and vulnerability testing of current systems." BMJ Qual Saf 24, no. 4 (2015):
264-271.
[13]. Shapiro, Rebecca, Sergey Bratus, Edmond Rogers, and Sean Smith. "Do-it-yourself
SCADA vulnerability testing with LZFuzz." accessed April 15 (2017).
[14]. Tabassum, Faria, and Abu Mohammad Faisal. "Vulnerability testing in online
shopping android applications." In Humanitarian Technology Conference (R10-HTC), 2017
IEEE Region 10, pp. 654-657. IEEE, 2017.
IT SECURITY MANAGEMENT
Bibliography
[1]. Antrobus, Rob, Sylvain Frey, Benjamin Green, and Awais Rashid. "Simaticscan: Towards a
specialised vulnerability scanner for industrial control systems." BCS, 2016.
[2]. Arambatzis, Theodoros, Ioannis Lazaridis, and Sotirios Pouros. "Modern Windows Server
Operating Systems Vulnerabilities." In The Third International Conference on Computer
Science, Computer Engineering, and Social Media (CSCESM2016), p. 29. 2016.
[3]. Bul'ajoul, Waleed, Anne James, and Mandeep Pannu. "Improving network intrusion
detection system performance through quality of service configuration and parallel
technology." Journal of Computer and System Sciences 81, no. 6 (2015): 981-999.
[4]. Coffey, Kyle, Richard Smith, Leandros Maglaras, and Helge Janicke. "Vulnerability Analysis of
Network Scanning on SCADA Systems." Security and Communication Networks2018 (2018).
[5]. El, Malaka, Emma McMahon, Sagar Samtani, Mark Patton, and Hsinchun Chen.
"Benchmarking vulnerability scanners: An experiment on SCADA devices and scientific
instruments." In Intelligence and Security Informatics (ISI), 2017 IEEE International
Conference on, pp. 83-88. IEEE, 2017.
[6]. Hacke, U.G., Venturas, M.D., MacKinnon, E.D., Jacobsen, A.L., Sperry, J.S. and Pratt, R.B.,
2015. The standard centrifuge method accurately measures vulnerability curves of long‐
vesselled olive stems. New Phytologist, 205(1), pp.116-127.
[7]. Kenkre, Poonam Sinai, Anusha Pai, and Louella Colaco. "Real time intrusion detection and
prevention system." In Proceedings of the 3rd International Conference on Frontiers of
Intelligent Computing: Theory and Applications (FICTA) 2014, pp. 405-411. Springer, Cham,
2015.
[8]. Khari, Manju, and Neha Singh. "Web Services Vulnerability Testing Using Open source
Security Scanners: An experimental Study." International Journal of Advanced Engineering
and Global Technology (IJAEGT) (2014): 790-799.
[9]. Kuvaiskii, Dmitrii, Somnath Chakrabarti, and Mona Vij. "Snort Intrusion Detection System
with Intel Software Guard Extension (Intel SGX)." arXiv preprint arXiv:1802.00508(2018).
[10]. Orth, Ulrich, Richard W. Robins, Laurenz L. Meier, and Rand D. Conger. "Refining the
vulnerability model of low self-esteem and depression: Disentangling the effects of genuine
self-esteem and narcissism." Journal of Personality and Social Psychology 110, no. 1 (2016):
133.
[11]. Peureux, Fabien. "Risk-Driven Vulnerability Testing: Results from eHealth
Experiments Using Patterns and Model-Based Approach." In Risk Assessment and Risk-
Driven Testing: Third International Workshop, RISK 2015, Berlin, Germany, June 15, 2015.
Revised Selected Papers, vol. 9488, p. 93. Springer, 2015.
[12]. Schiff, G. D., M. G. Amato, T. Eguale, J. J. Boehne, Adam Wright, Ross Koppel, A. H.
Rashidee et al. "Computerised physician order entry-related medication errors: analysis of
reported errors and vulnerability testing of current systems." BMJ Qual Saf 24, no. 4 (2015):
264-271.
[13]. Shapiro, Rebecca, Sergey Bratus, Edmond Rogers, and Sean Smith. "Do-it-yourself
SCADA vulnerability testing with LZFuzz." accessed April 15 (2017).
[14]. Tabassum, Faria, and Abu Mohammad Faisal. "Vulnerability testing in online
shopping android applications." In Humanitarian Technology Conference (R10-HTC), 2017
IEEE Region 10, pp. 654-657. IEEE, 2017.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

