In-Depth Analysis of Computer System Architecture and Functionality
VerifiedAdded on 2024/06/25
|37
|5816
|155
Report
AI Summary
This report provides an in-depth analysis of computer system architecture, beginning with an overview of the Von Neumann architecture and its key components such as the memory unit (including volatile and non-volatile memory, and memory hierarchy), hardware devices, and the relationship between hardware and software. It explains the purpose and operation of the Central Processing Unit (CPU), detailing its components like registers, ALU, control unit, and buses. The report also describes various operating systems (OS) including Ubuntu, Windows, and Mac OS X, discussing their purposes, uses, and hardware requirements. Furthermore, it explores the relationships between hardware and network addresses, including MAC and IP addresses, and discusses setting up computer-based network connectivity. Finally, the report addresses troubleshooting technical hardware and software issues, documenting solutions, and conducting maintenance activities to ensure optimal computer performance. Desklib offers students access to this report and many other solved assignments.

COMPUTER SYSTEM
ARCHITECTURE
ARCHITECTURE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction......................................................................................................................................1
Lo1...................................................................................................................................................2
P1 Identify the main subsystems of a computer and explain how they are organized and
connected.....................................................................................................................................2
P2 Explain the purpose of the Central Processing Unit (CPU) and include details on its
operation......................................................................................................................................6
Lo2...................................................................................................................................................8
P3 Describe a range of different operating systems including the purpose, use and hardware
requirements of each....................................................................................................................8
P4 Discuss the key features associated with the architecture of an operating system...............13
Lo3.................................................................................................................................................15
P5 Explain the relationships between hardware and network addresses including their use with
regards to networking devices and components........................................................................15
P6 Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity.......................................................................................19
Lo4.................................................................................................................................................20
P7 Use information gathering methods to assess troubleshoot and document solutions to a
number of different technical hardware, software and networking issues................................20
P8 Conduct and document a range of maintenance activities with regards to computer
hardware and software...............................................................................................................22
Conclusion.....................................................................................................................................31
References......................................................................................................................................32
Introduction......................................................................................................................................1
Lo1...................................................................................................................................................2
P1 Identify the main subsystems of a computer and explain how they are organized and
connected.....................................................................................................................................2
P2 Explain the purpose of the Central Processing Unit (CPU) and include details on its
operation......................................................................................................................................6
Lo2...................................................................................................................................................8
P3 Describe a range of different operating systems including the purpose, use and hardware
requirements of each....................................................................................................................8
P4 Discuss the key features associated with the architecture of an operating system...............13
Lo3.................................................................................................................................................15
P5 Explain the relationships between hardware and network addresses including their use with
regards to networking devices and components........................................................................15
P6 Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity.......................................................................................19
Lo4.................................................................................................................................................20
P7 Use information gathering methods to assess troubleshoot and document solutions to a
number of different technical hardware, software and networking issues................................20
P8 Conduct and document a range of maintenance activities with regards to computer
hardware and software...............................................................................................................22
Conclusion.....................................................................................................................................31
References......................................................................................................................................32

LIST OF TABLES
Table 1: Type of register and it functions........................................................................................6
Table 2: types of buses....................................................................................................................7
Table 3: Feature and requirement of different OS.........................................................................11
Table 4: Comparison between MAC and IP address.....................................................................17
Table 1: Type of register and it functions........................................................................................6
Table 2: types of buses....................................................................................................................7
Table 3: Feature and requirement of different OS.........................................................................11
Table 4: Comparison between MAC and IP address.....................................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LIST OF FIGURES
Figure 1: Von Neumann Architecture.............................................................................................2
Figure 2: Memory Hierarchy of a computer system........................................................................3
Figure 3: Memories in computer system.........................................................................................4
Figure 4: Desktop of computer system having Ubuntu OS.............................................................9
Figure 5: Windows 10...................................................................................................................10
Figure 6: Screensort of MAC OS X..............................................................................................11
Figure 7: MAC address of a system..............................................................................................16
Figure 8: IP address in command prompt......................................................................................17
Figure 9: Start menu having the File explorer...............................................................................22
Figure 10: Open the Local Disk (C :)............................................................................................23
Figure 11: Optimizing the computer’s drive.................................................................................23
Figure 12: The drive is selected for Optimization.........................................................................24
Figure 13: Percentage of fragmentation........................................................................................24
Figure 14: Initializing the Defragmentation process.....................................................................25
Figure 15: Cleaning the browser’s history.....................................................................................26
Figure 16: Control panel is clicked................................................................................................27
Figure 17: System and security option is clicked..........................................................................28
Figure 18: Backup and Restore......................................................................................................28
Figure 19: Back up Storing............................................................................................................29
Figure 1: Von Neumann Architecture.............................................................................................2
Figure 2: Memory Hierarchy of a computer system........................................................................3
Figure 3: Memories in computer system.........................................................................................4
Figure 4: Desktop of computer system having Ubuntu OS.............................................................9
Figure 5: Windows 10...................................................................................................................10
Figure 6: Screensort of MAC OS X..............................................................................................11
Figure 7: MAC address of a system..............................................................................................16
Figure 8: IP address in command prompt......................................................................................17
Figure 9: Start menu having the File explorer...............................................................................22
Figure 10: Open the Local Disk (C :)............................................................................................23
Figure 11: Optimizing the computer’s drive.................................................................................23
Figure 12: The drive is selected for Optimization.........................................................................24
Figure 13: Percentage of fragmentation........................................................................................24
Figure 14: Initializing the Defragmentation process.....................................................................25
Figure 15: Cleaning the browser’s history.....................................................................................26
Figure 16: Control panel is clicked................................................................................................27
Figure 17: System and security option is clicked..........................................................................28
Figure 18: Backup and Restore......................................................................................................28
Figure 19: Back up Storing............................................................................................................29
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Computer architecture is referred to the rules or the methods that are used for explaining,
function, implementation and organization of a computer system. Through the Computer
architecture various user commands are executed and accomplished. In this report, various
computer subsystems are illustrated. The report will be discussing about process or the Central
Processing Unit along with its operation. Presently, there are different types of operating system
for different user or system. The report will discuss about the OS along with its requirement and
features. In this report about relation and comparison between MAC and IP addresses will also
be provided. Lastly the report will discuss about maintenance task which a user need to
performed for maintaining proper functionality of computer system and also its components.
1
Computer architecture is referred to the rules or the methods that are used for explaining,
function, implementation and organization of a computer system. Through the Computer
architecture various user commands are executed and accomplished. In this report, various
computer subsystems are illustrated. The report will be discussing about process or the Central
Processing Unit along with its operation. Presently, there are different types of operating system
for different user or system. The report will discuss about the OS along with its requirement and
features. In this report about relation and comparison between MAC and IP addresses will also
be provided. Lastly the report will discuss about maintenance task which a user need to
performed for maintaining proper functionality of computer system and also its components.
1
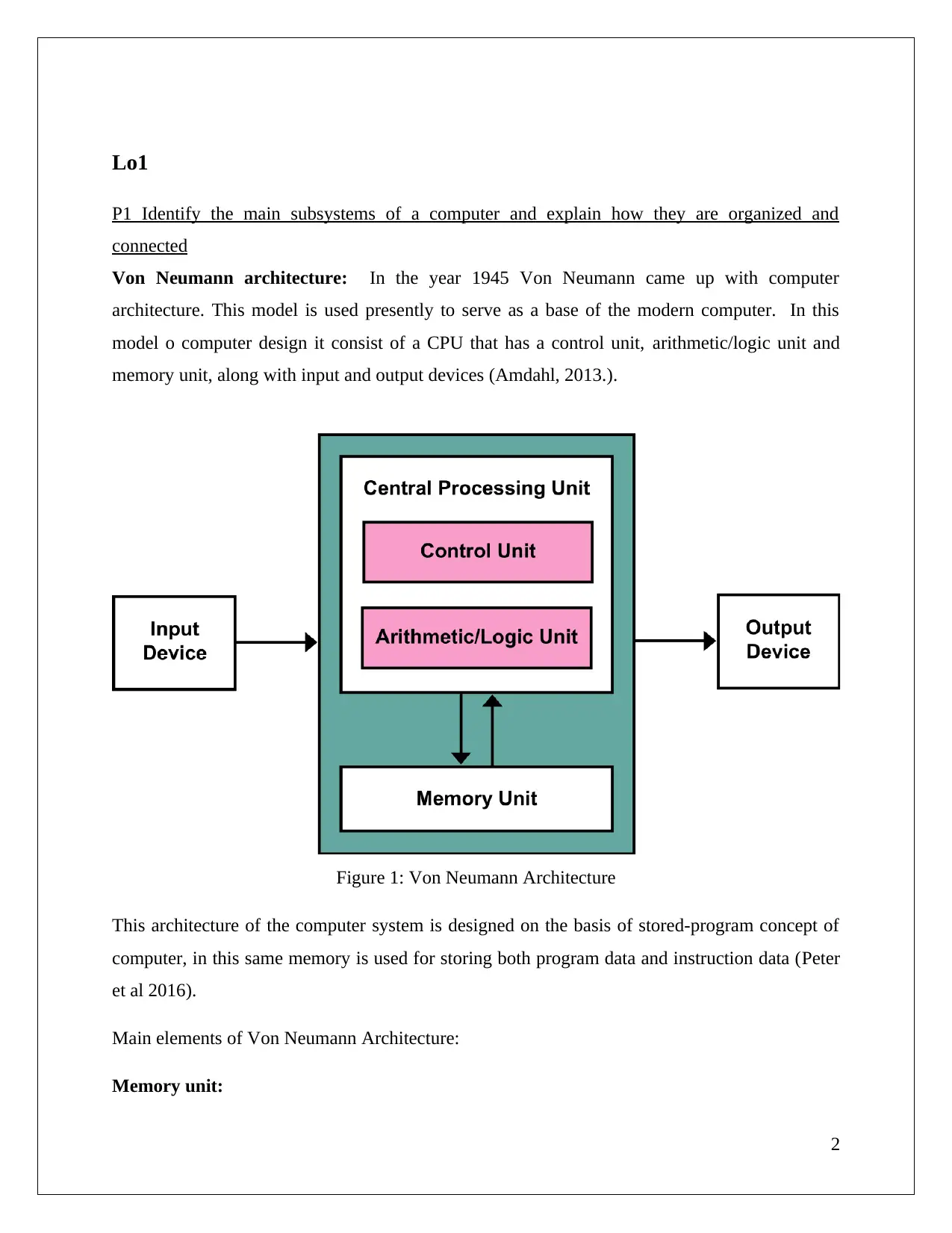
Lo1
P1 Identify the main subsystems of a computer and explain how they are organized and
connected
Von Neumann architecture: In the year 1945 Von Neumann came up with computer
architecture. This model is used presently to serve as a base of the modern computer. In this
model o computer design it consist of a CPU that has a control unit, arithmetic/logic unit and
memory unit, along with input and output devices (Amdahl, 2013.).
Figure 1: Von Neumann Architecture
This architecture of the computer system is designed on the basis of stored-program concept of
computer, in this same memory is used for storing both program data and instruction data (Peter
et al 2016).
Main elements of Von Neumann Architecture:
Memory unit:
2
P1 Identify the main subsystems of a computer and explain how they are organized and
connected
Von Neumann architecture: In the year 1945 Von Neumann came up with computer
architecture. This model is used presently to serve as a base of the modern computer. In this
model o computer design it consist of a CPU that has a control unit, arithmetic/logic unit and
memory unit, along with input and output devices (Amdahl, 2013.).
Figure 1: Von Neumann Architecture
This architecture of the computer system is designed on the basis of stored-program concept of
computer, in this same memory is used for storing both program data and instruction data (Peter
et al 2016).
Main elements of Von Neumann Architecture:
Memory unit:
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

This is referred to the collection of different storage devices together. The Memory unit
effectively stores all the binary information in form of bits. Broadly the Memory of a computer
system is classified into two different types: Volatile and No-Volatile memory. In case of
Volatile memory, the stored data get lost in case of discontinuity of power supply. While in case
of, Non-Volatile Memory data are stored permanently, even is the power supply get interrupted
data storage is not damaged.
Memory Hierarchy
Figure 2: Memory Hierarchy of a computer system
(Source: http://abhaycopi.blogspot.com/2014/04/memory-hierarchy.html, 2018)
With the help of memory hierarchy, the total memory present in a computer system can be
visualized. Memory system of a computer contains every storage devices including Main
Memory, Cache memory and Auxiliary Memory (Kolodner, 2014).
3
effectively stores all the binary information in form of bits. Broadly the Memory of a computer
system is classified into two different types: Volatile and No-Volatile memory. In case of
Volatile memory, the stored data get lost in case of discontinuity of power supply. While in case
of, Non-Volatile Memory data are stored permanently, even is the power supply get interrupted
data storage is not damaged.
Memory Hierarchy
Figure 2: Memory Hierarchy of a computer system
(Source: http://abhaycopi.blogspot.com/2014/04/memory-hierarchy.html, 2018)
With the help of memory hierarchy, the total memory present in a computer system can be
visualized. Memory system of a computer contains every storage devices including Main
Memory, Cache memory and Auxiliary Memory (Kolodner, 2014).
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
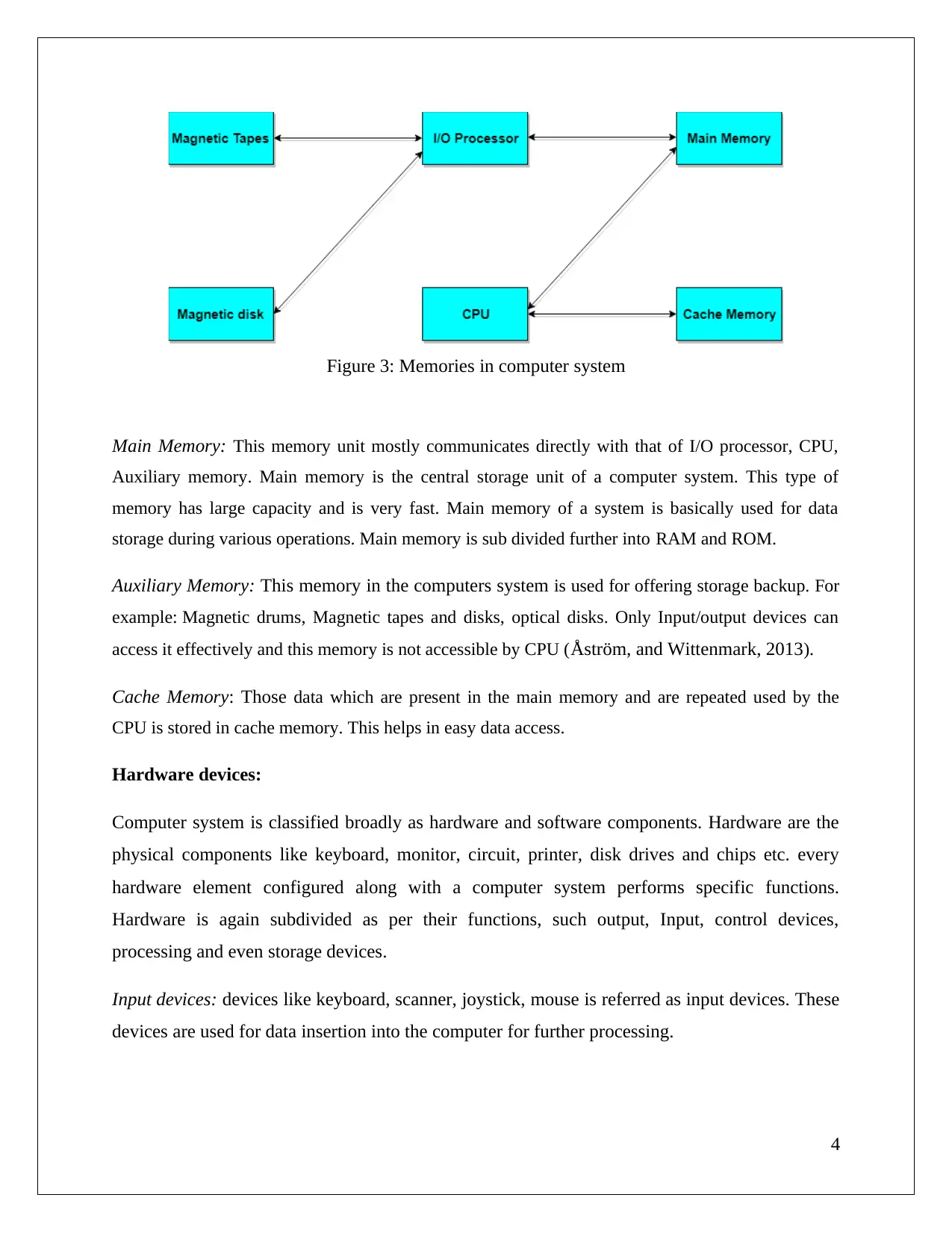
Figure 3: Memories in computer system
Main Memory: This memory unit mostly communicates directly with that of I/O processor, CPU,
Auxiliary memory. Main memory is the central storage unit of a computer system. This type of
memory has large capacity and is very fast. Main memory of a system is basically used for data
storage during various operations. Main memory is sub divided further into RAM and ROM.
Auxiliary Memory: This memory in the computers system is used for offering storage backup. For
example: Magnetic drums, Magnetic tapes and disks, optical disks. Only Input/output devices can
access it effectively and this memory is not accessible by CPU (Åström, and Wittenmark, 2013).
Cache Memory: Those data which are present in the main memory and are repeated used by the
CPU is stored in cache memory. This helps in easy data access.
Hardware devices:
Computer system is classified broadly as hardware and software components. Hardware are the
physical components like keyboard, monitor, circuit, printer, disk drives and chips etc. every
hardware element configured along with a computer system performs specific functions.
Hardware is again subdivided as per their functions, such output, Input, control devices,
processing and even storage devices.
Input devices: devices like keyboard, scanner, joystick, mouse is referred as input devices. These
devices are used for data insertion into the computer for further processing.
4
Main Memory: This memory unit mostly communicates directly with that of I/O processor, CPU,
Auxiliary memory. Main memory is the central storage unit of a computer system. This type of
memory has large capacity and is very fast. Main memory of a system is basically used for data
storage during various operations. Main memory is sub divided further into RAM and ROM.
Auxiliary Memory: This memory in the computers system is used for offering storage backup. For
example: Magnetic drums, Magnetic tapes and disks, optical disks. Only Input/output devices can
access it effectively and this memory is not accessible by CPU (Åström, and Wittenmark, 2013).
Cache Memory: Those data which are present in the main memory and are repeated used by the
CPU is stored in cache memory. This helps in easy data access.
Hardware devices:
Computer system is classified broadly as hardware and software components. Hardware are the
physical components like keyboard, monitor, circuit, printer, disk drives and chips etc. every
hardware element configured along with a computer system performs specific functions.
Hardware is again subdivided as per their functions, such output, Input, control devices,
processing and even storage devices.
Input devices: devices like keyboard, scanner, joystick, mouse is referred as input devices. These
devices are used for data insertion into the computer for further processing.
4

Output devices: Monitor, Printer comes under the category of output devices, these elements
takes the processed data from the CPU and make them available for user or other systems.
Processing device: Data are processed according to the instruction given.
Control devices: They are used for coordinating various activities within the computer system.
Storage devices: Main purpose of these devices is for keeping and storing various data that can
be used later (Organick, 2014).
The primary hardware works along with software system so that it can perform various
computing activities such as organizing information, calculations and even for connecting other
computer systems. With the help of various software components all the hardware components
are controlled and activated.
The computer software is referred to the set of instructions or programs that are written in
different programming languages such as JAVA, C++, and Python. This instruction governs the
operations of the computer. Software is further classified as application software and system
software (Card, 2017).
Relationship between various hardware and software components:
All the hardware and software component of a computer system are independent. Both the
components work together so that suitable output can be yield. Hardware devices are useless in
case the software is not supportive and vice versa. If instruction is not appropriate the hardware
fails to perform its activities accurately. The hardware is configured along with proper software
package for a particular job. Software is referred to an interface that is created between the user
and the hardware components.
5
takes the processed data from the CPU and make them available for user or other systems.
Processing device: Data are processed according to the instruction given.
Control devices: They are used for coordinating various activities within the computer system.
Storage devices: Main purpose of these devices is for keeping and storing various data that can
be used later (Organick, 2014).
The primary hardware works along with software system so that it can perform various
computing activities such as organizing information, calculations and even for connecting other
computer systems. With the help of various software components all the hardware components
are controlled and activated.
The computer software is referred to the set of instructions or programs that are written in
different programming languages such as JAVA, C++, and Python. This instruction governs the
operations of the computer. Software is further classified as application software and system
software (Card, 2017).
Relationship between various hardware and software components:
All the hardware and software component of a computer system are independent. Both the
components work together so that suitable output can be yield. Hardware devices are useless in
case the software is not supportive and vice versa. If instruction is not appropriate the hardware
fails to perform its activities accurately. The hardware is configured along with proper software
package for a particular job. Software is referred to an interface that is created between the user
and the hardware components.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

P2 Explain the purpose of the Central Processing Unit (CPU) and include details on its operation
CPU is brain of a computer system, performs every function related to processing with a
computing device. CPU receives the input data that are fetch by a user, executes them according
to the instruction provided, processes and sent back the processed data to the output devices for
the user. Processor has the main function to controlling flow of data from one device to another.
For establishing communication between the I/O devices microchip is used that is present in the
motherboard of the CPU. The main purpose of a CPU in a computer system is to carry
out various program instructions. And every processor is designed mostly for executing
particular instruction set (Comer, 2017).
Components of CPU
Registers: These are the area in the CPU that is for high speed storage. Before processing, all
the data should be stored in a register.
Table 1: Type of register and it functions
Type of register Function
Memory Address Register
(MAR)
Memory location of the data must be accessed
Current Instruction Register
(CIR)
It has the current instruction while processing
Program Counter (PC) It consist of address for the next instruction
Accumulator (Acc) It stores the result of intermediate arithmetic and logic
Memory Data Register
(MDR)
MDR stores data which is to be transferred from or to the
from memory
Arithmetic and Logic Unit: ALU supports and allows all the arithmetic and logical operations.
Control Unit: This unit is used for controlling the computer’s operation. Control unit provides
control and timing signals that computer components required.
Buses: Buses are used for transmission of data from one computer part to another. It connects all
the major internal components of the computer to CPU and the memory unit.
6
CPU is brain of a computer system, performs every function related to processing with a
computing device. CPU receives the input data that are fetch by a user, executes them according
to the instruction provided, processes and sent back the processed data to the output devices for
the user. Processor has the main function to controlling flow of data from one device to another.
For establishing communication between the I/O devices microchip is used that is present in the
motherboard of the CPU. The main purpose of a CPU in a computer system is to carry
out various program instructions. And every processor is designed mostly for executing
particular instruction set (Comer, 2017).
Components of CPU
Registers: These are the area in the CPU that is for high speed storage. Before processing, all
the data should be stored in a register.
Table 1: Type of register and it functions
Type of register Function
Memory Address Register
(MAR)
Memory location of the data must be accessed
Current Instruction Register
(CIR)
It has the current instruction while processing
Program Counter (PC) It consist of address for the next instruction
Accumulator (Acc) It stores the result of intermediate arithmetic and logic
Memory Data Register
(MDR)
MDR stores data which is to be transferred from or to the
from memory
Arithmetic and Logic Unit: ALU supports and allows all the arithmetic and logical operations.
Control Unit: This unit is used for controlling the computer’s operation. Control unit provides
control and timing signals that computer components required.
Buses: Buses are used for transmission of data from one computer part to another. It connects all
the major internal components of the computer to CPU and the memory unit.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CPU system comprised of a control bus, data bus and address bus.
Table 2: types of buses
Types of buses Function
Control Bus This bus carries control commands or signals from CPU for
controlling and coordinating the order of all activities within a
computer system
Address Bus They are meant for carrying data addresses between memory and the
processor
Data Bus It carries data between memory unit, processor, and input/output
devices
Memory Unit: The memory unit consists of RAM and it sometimes is also referred as main
memory or primary memory. This memory is very fast and can be directly accessible by CPU.
RAM has different partitions (Dautenhahn et al 2015). And every partition has address and
contents. Addresses are uniquely identifying every location in the memory.
Function of CPU
For meeting the main purpose of a CPU, the process performs series of function that are
explained below:
Fetch: In this function, information and data are retrieved from its memory address and the data
is stored in the Current Instruction register (CIR). the program counter or PC is used for storing
the address of the instruction provided. Once the instruction is fetched the PC is then updated.
This supports the CPU to know the address of a instruction that need to be fetched next.
Decode: Here, the CPU identifies the op-code or operation code part of an instruction. This Op-
code tells about the operation to be performed. In case, the op-code needs CPU to react on some
data then second part of instruction contains the memory address where the data has been stored.
Execute: this is the last step where the control unit links to the parts of processor which are
actually required for execution of instruction (Rainie et al 2013).
7
Table 2: types of buses
Types of buses Function
Control Bus This bus carries control commands or signals from CPU for
controlling and coordinating the order of all activities within a
computer system
Address Bus They are meant for carrying data addresses between memory and the
processor
Data Bus It carries data between memory unit, processor, and input/output
devices
Memory Unit: The memory unit consists of RAM and it sometimes is also referred as main
memory or primary memory. This memory is very fast and can be directly accessible by CPU.
RAM has different partitions (Dautenhahn et al 2015). And every partition has address and
contents. Addresses are uniquely identifying every location in the memory.
Function of CPU
For meeting the main purpose of a CPU, the process performs series of function that are
explained below:
Fetch: In this function, information and data are retrieved from its memory address and the data
is stored in the Current Instruction register (CIR). the program counter or PC is used for storing
the address of the instruction provided. Once the instruction is fetched the PC is then updated.
This supports the CPU to know the address of a instruction that need to be fetched next.
Decode: Here, the CPU identifies the op-code or operation code part of an instruction. This Op-
code tells about the operation to be performed. In case, the op-code needs CPU to react on some
data then second part of instruction contains the memory address where the data has been stored.
Execute: this is the last step where the control unit links to the parts of processor which are
actually required for execution of instruction (Rainie et al 2013).
7

Lo2
P3 Describe a range of different operating systems including the purpose, use and hardware
requirements of each.
Operating system (OS) is referred to that program which is loaded initially into computer system
through boot program. OS is responsible for managing other application programs present in the
computer. Application programs uses operating system for making requests to offer services
through pre-defined API (application program interface). Users can directly interact with OS
though user interface like graphical user interface (GUI) and command line.
Services the OS perform for the corresponding applications:
The multitasking operating system can support multiple programs running in same
instance of time. Operating system effectively determines order of applications run and
allocates time accordingly (Freiberger, 2014).
OS manages the internal memory sharing between different applications.
Operating system is responsible for handling the input and output hardware devices of a
computer system.
OS also offers parallel processing, they manages program division.
Some of the most common desktop operating systems are Windows, Linux and OS X. even
though every OS is different from one another. They mostly provide GUI (graphical user
interface), and manages computer’s folders and files. It supports installation and running of
programs that are exclusively written for OS. Linux and Windows can be installed effectively in
any standard hardware of computer system, whereas OS X has been designed absolutely to run
only on system of Apple.
Most commonly known operating systems are Microsoft Windows, Mac OS X, Ubuntu and
Linux.
Ubuntu: This is one of the most used OS that is built on Debian's architecture and infrastructure.
The operating system consists of desktop, Linux server, tablet operating system versions etc. this
8
P3 Describe a range of different operating systems including the purpose, use and hardware
requirements of each.
Operating system (OS) is referred to that program which is loaded initially into computer system
through boot program. OS is responsible for managing other application programs present in the
computer. Application programs uses operating system for making requests to offer services
through pre-defined API (application program interface). Users can directly interact with OS
though user interface like graphical user interface (GUI) and command line.
Services the OS perform for the corresponding applications:
The multitasking operating system can support multiple programs running in same
instance of time. Operating system effectively determines order of applications run and
allocates time accordingly (Freiberger, 2014).
OS manages the internal memory sharing between different applications.
Operating system is responsible for handling the input and output hardware devices of a
computer system.
OS also offers parallel processing, they manages program division.
Some of the most common desktop operating systems are Windows, Linux and OS X. even
though every OS is different from one another. They mostly provide GUI (graphical user
interface), and manages computer’s folders and files. It supports installation and running of
programs that are exclusively written for OS. Linux and Windows can be installed effectively in
any standard hardware of computer system, whereas OS X has been designed absolutely to run
only on system of Apple.
Most commonly known operating systems are Microsoft Windows, Mac OS X, Ubuntu and
Linux.
Ubuntu: This is one of the most used OS that is built on Debian's architecture and infrastructure.
The operating system consists of desktop, Linux server, tablet operating system versions etc. this
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 37
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





