Understanding Computer Architecture: Hardware, CPU, and OS Features
VerifiedAdded on 2024/06/07
|29
|5864
|381
Report
AI Summary
This report provides a comprehensive overview of computer system architecture, beginning with an introduction to the role of computers in modern society and a discussion of the Von Neumann architecture, including its key components such as the memory unit, control unit, input/output, and arithmetic logic unit (ALU). It details the different types of memory (primary, secondary, cache), explains the function and components of the Central Processing Unit (CPU), and categorizes the key features and services provided by various operating systems like Windows, Mac OS X, Linux, Android, and iOS. The report also discusses the architecture of operating systems, including the kernel, API, and essential services such as user interface, memory management, and file management. The document concludes by emphasizing the relationship between hardware and software, illustrating how software triggers hardware to perform specific tasks.

COMPUTER SYSTEM ARCHITECTURE
Introduction: In this era of technology computer has an important role in a human being. In every field
related to human services such as education, medical, defiance, etc. nothing can be done without a
computer. A computer is an electronic machine that interacts with the user, take his input and provide
result according to his operation and also provide facilities for storing the data. Another advantage of the
computer is that it provides the networking facility to the users in which users can share the data among
them from different locations.
In this chapter, I have discussed computer architecture and how it works. I included following things
about the computer, Von Neumann architecture of the computer and its part such as I/O, memory unit,
control unit, and arithmetic and logical unit. I discussed the operating system and its key features or its
services. And I designed a prototype network for the ACME as a consultant for ACME (O’Reilly, 2018).
Introduction: In this era of technology computer has an important role in a human being. In every field
related to human services such as education, medical, defiance, etc. nothing can be done without a
computer. A computer is an electronic machine that interacts with the user, take his input and provide
result according to his operation and also provide facilities for storing the data. Another advantage of the
computer is that it provides the networking facility to the users in which users can share the data among
them from different locations.
In this chapter, I have discussed computer architecture and how it works. I included following things
about the computer, Von Neumann architecture of the computer and its part such as I/O, memory unit,
control unit, and arithmetic and logical unit. I discussed the operating system and its key features or its
services. And I designed a prototype network for the ACME as a consultant for ACME (O’Reilly, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

LO1 Explain the relationships between hardware components and the subsystems used in a computer
system
P1 Identify the main subsystems of a computer and explain how they are organised and connected.
Here I have given a diagram of Von Neumann architecture; following are the key features of-of this
architecture.
Figure 1: von Neumann architecture
Source (Tipsandarticles, 2018.)
Memory: commuter has a memory unit which is used to hold and store the data, this also called as RAM
that means random access memory.
Types of memory in the computer: basically it is categorized in type’s primary memory and secondary
memory.
Primary memory: It is also called volatile memory because it is not able to store the data permanently,
that is known as RAM
system
P1 Identify the main subsystems of a computer and explain how they are organised and connected.
Here I have given a diagram of Von Neumann architecture; following are the key features of-of this
architecture.
Figure 1: von Neumann architecture
Source (Tipsandarticles, 2018.)
Memory: commuter has a memory unit which is used to hold and store the data, this also called as RAM
that means random access memory.
Types of memory in the computer: basically it is categorized in type’s primary memory and secondary
memory.
Primary memory: It is also called volatile memory because it is not able to store the data permanently,
that is known as RAM

Random access memory (RAM): It has an ability of both read and writes but when at the condition of a
power failure your data has been lost permanently. This may be following type DRAM, DRDRAM and
SRAM.
Secondary memory: this memory is a permanent memory and also known as an external memory of a
computer such as floppy disk and magnetic disk.
Read Only Memory (ROM): it is the permanent mammary of the computer that is available in a huge
range in modern days but it can be read-only. And there is no loss of data at the time of power failure.
There are several types of the room such as PROM, EPROM, and EEPROM.
Cache Memory: it is the fastest memory and stores a little data as compared to the main memory of
commuter.
BIOS: it means basic input and output system; it is in the form of software that stored on a memory chip
of the motherboard (Informationq, 2016).
power failure your data has been lost permanently. This may be following type DRAM, DRDRAM and
SRAM.
Secondary memory: this memory is a permanent memory and also known as an external memory of a
computer such as floppy disk and magnetic disk.
Read Only Memory (ROM): it is the permanent mammary of the computer that is available in a huge
range in modern days but it can be read-only. And there is no loss of data at the time of power failure.
There are several types of the room such as PROM, EPROM, and EEPROM.
Cache Memory: it is the fastest memory and stores a little data as compared to the main memory of
commuter.
BIOS: it means basic input and output system; it is in the form of software that stored on a memory chip
of the motherboard (Informationq, 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Control unit: this unit is the mind of the computer that manages and controls the flow of data to outside
the memory and inside the memory and also deals with programming instructions. And this contains the
registers to store the intermediate value.
Input and output:
Input: Users that enter the data for processing that is known as input and this input can be feed by
various input devices which are given below.
List of input devices: mouse, keyboard, joystick, barcode reader, and scanner.
Output: after entering the input users expect to the result after manipulating the data devices that shows
the result is known as output devices,
List of output devices: monitor, printer, speaker, plotter and projector
Arithmetic logic unit(ALU): All the arithmetic and logical calculations are performed in this part of a
computer such as addition subtraction multiplication and divide or logical calculations “greater than, less
than and equal to” all these are performing by ALU (Teach-ict, 2018)
Hardware: generally computer contains the various mechanical electrical and electronic components
these all devices are known as hardware devices such as a motherboard, mouse, flash drive floppy disk
etc.
Software: it can not touch by a human being it is a set program or instructions in a various programming
language such as Java, python and c++. These software’s such as system software, application software
etc.
The relationship between software and hardware:
Software trigger to the hardware to perform any specific work in another word it can be said that software
and hardware are the soul and heart of the computer, for example, there is software of AutoCAD that
trigger the hardware to make a design (Das, 2018).
the memory and inside the memory and also deals with programming instructions. And this contains the
registers to store the intermediate value.
Input and output:
Input: Users that enter the data for processing that is known as input and this input can be feed by
various input devices which are given below.
List of input devices: mouse, keyboard, joystick, barcode reader, and scanner.
Output: after entering the input users expect to the result after manipulating the data devices that shows
the result is known as output devices,
List of output devices: monitor, printer, speaker, plotter and projector
Arithmetic logic unit(ALU): All the arithmetic and logical calculations are performed in this part of a
computer such as addition subtraction multiplication and divide or logical calculations “greater than, less
than and equal to” all these are performing by ALU (Teach-ict, 2018)
Hardware: generally computer contains the various mechanical electrical and electronic components
these all devices are known as hardware devices such as a motherboard, mouse, flash drive floppy disk
etc.
Software: it can not touch by a human being it is a set program or instructions in a various programming
language such as Java, python and c++. These software’s such as system software, application software
etc.
The relationship between software and hardware:
Software trigger to the hardware to perform any specific work in another word it can be said that software
and hardware are the soul and heart of the computer, for example, there is software of AutoCAD that
trigger the hardware to make a design (Das, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P2 Explain the purpose of the Central Processing Unit(CPU) and include details on its operation.
Purpose of the Central Processing Unit(CPU):
The main objective of the CPU is to be work on programming instructions. It is designed to execute the
particular instructions and the set of instructions carried out by the CPU to meet the purpose.
Figure 2 control processing unit
Source (Cssforum, 2018)
Purpose of the Central Processing Unit(CPU):
The main objective of the CPU is to be work on programming instructions. It is designed to execute the
particular instructions and the set of instructions carried out by the CPU to meet the purpose.
Figure 2 control processing unit
Source (Cssforum, 2018)

The function of CPU:
1. Fetching step:
This means retrieving the instructions from the memory and stores it at the instruction register.
And instruction address is to be stored at another register known as program counter register (PC)
2. Decoding step: it contains the identification of programming code that tells to the processor that which
operation is to be performed.
3. Executing step: this means performing of operations according to instruction code for an example, an
instruction that has an arithmetic operation with integer number then ALU connect to the relevant
memory address hence;
Data is to be passed through data bus from memory to ALU.
Then ALU execute the necessary operation
After result passes through data bus from the ALU
Components of CPU: there are various components in a central processing unit which are following:
Arithmetic and Logic Unit (ALU): There is an ALU in the central processing unit that contains
electronic circuitry for performing the logical and arithmetic operations with the integers.
Integer arithmetic operations are (multiplication and additions) and logical operations are OR, NOT,
AND etc. and also there is a floating point unit that used to perform the operation on floating point
numbers. And also there is a resister which is used to store the data temporary that is known as an
accumulator (Cssforum, 2018)
1. Fetching step:
This means retrieving the instructions from the memory and stores it at the instruction register.
And instruction address is to be stored at another register known as program counter register (PC)
2. Decoding step: it contains the identification of programming code that tells to the processor that which
operation is to be performed.
3. Executing step: this means performing of operations according to instruction code for an example, an
instruction that has an arithmetic operation with integer number then ALU connect to the relevant
memory address hence;
Data is to be passed through data bus from memory to ALU.
Then ALU execute the necessary operation
After result passes through data bus from the ALU
Components of CPU: there are various components in a central processing unit which are following:
Arithmetic and Logic Unit (ALU): There is an ALU in the central processing unit that contains
electronic circuitry for performing the logical and arithmetic operations with the integers.
Integer arithmetic operations are (multiplication and additions) and logical operations are OR, NOT,
AND etc. and also there is a floating point unit that used to perform the operation on floating point
numbers. And also there is a resister which is used to store the data temporary that is known as an
accumulator (Cssforum, 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Control unit: this performs the function of fetching, decoding, and executions of instructions and storing
the result. The main function of this is too control the other elements of CPU. It can communicate with
both ALU and memory unit. It has many registers such as program counter and an instruction register.
Program counter: it stores the next instruction memory address
Current instruction: this register is used to store the address of the currently executed
instruction.
Registers: These are the instant storage devices that are used to storing the data which is to be processed.
There are various registers such as programming counter, flag and stack.
Buses: these are the group of parallel wires like a pipe that is used to carry the data from CPU to external
devices and vice versa. These are available in different length such as 32, 64 bits etc. There are three main
buses which are following
Address bus: it links the memory address to CPU components to read-write operations.
Data bus: data flows through this bus between CPU and memory address when read-write
operation is carried out.
Control buses: it is used to send the control signals and acknowledge signal between the external
devices and CPU components (Gcsecomputing, 2018).
the result. The main function of this is too control the other elements of CPU. It can communicate with
both ALU and memory unit. It has many registers such as program counter and an instruction register.
Program counter: it stores the next instruction memory address
Current instruction: this register is used to store the address of the currently executed
instruction.
Registers: These are the instant storage devices that are used to storing the data which is to be processed.
There are various registers such as programming counter, flag and stack.
Buses: these are the group of parallel wires like a pipe that is used to carry the data from CPU to external
devices and vice versa. These are available in different length such as 32, 64 bits etc. There are three main
buses which are following
Address bus: it links the memory address to CPU components to read-write operations.
Data bus: data flows through this bus between CPU and memory address when read-write
operation is carried out.
Control buses: it is used to send the control signals and acknowledge signal between the external
devices and CPU components (Gcsecomputing, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

LO2 Categorize the key features and services provided by different computer operating systems and
hardware.
P3 Describe a range of different operating systems including the purpose, use and hardware requirements
of each.
Operating system: an operating system is a software that runs on system or computer. The operating
system manages the memory of the computer and also its process. And it plays an important role in the
interaction of the user to the computer. In other words, it can be said that without operating system
computer is nothing.
Figure 3 operating system
Source (Wikipedia, 2018)
Types of the operating system: there are various operating systems in the market that are generally used
by the people, Such as Mac OS X, Microsoft Windows, Linux and Unix etc.
Microsoft Windows: it created the windows OS at the mid of 1980. After passing these years there have
been many versions introduce in the market such as windows7, windows8, and windows10, etc.
Mac OSX: It is created by Apple and it is a line of operating system its entire recent version called as
OSX, and some specific version contains El Capitan (2015), mountain lion (2012), Mavericks (2013),
Yosemite (2014) and lion (2011). These operating systems are generally less uses as compare to
windows OS because these are expensive.
Linux: it is an open source OS that means it can be modified by the user world. This is different from
windows software that can only be modified by the company.
hardware.
P3 Describe a range of different operating systems including the purpose, use and hardware requirements
of each.
Operating system: an operating system is a software that runs on system or computer. The operating
system manages the memory of the computer and also its process. And it plays an important role in the
interaction of the user to the computer. In other words, it can be said that without operating system
computer is nothing.
Figure 3 operating system
Source (Wikipedia, 2018)
Types of the operating system: there are various operating systems in the market that are generally used
by the people, Such as Mac OS X, Microsoft Windows, Linux and Unix etc.
Microsoft Windows: it created the windows OS at the mid of 1980. After passing these years there have
been many versions introduce in the market such as windows7, windows8, and windows10, etc.
Mac OSX: It is created by Apple and it is a line of operating system its entire recent version called as
OSX, and some specific version contains El Capitan (2015), mountain lion (2012), Mavericks (2013),
Yosemite (2014) and lion (2011). These operating systems are generally less uses as compare to
windows OS because these are expensive.
Linux: it is an open source OS that means it can be modified by the user world. This is different from
windows software that can only be modified by the company.

UNIX: it is also an operating system that has a GUI graphical user interface same as Microsoft windows
easy environment to use. This is a stable, multi-tasking and multi-user system for laptops and for desktops
(Gcflearn, 2018).
Android:
This is a mobile operating system that is developed by Google mainly for touch screen mobiles. The
design of this android software’s permits to the user interaction in a different way and it provide facilities
such as tapping swiping and pinching. Instead of mobile, it can be employed to the televisions
wristwatches and in cars to interface with users.
IOS:
It is a mobile operating system that is more over 10 years old. Basically, it is run on Apple smart mobile
phones, such as in iPod’s and iPhones. It is main software that allows the user to interact with Apple
mobile phones and tablets. When you visit settings of your tablet or mobile phones wherefrom you can
make changes such as brightness, Bluetooth on and off, Wi-Fi all these are done by the operating system.
(Barraclough, 2015).
Figure 4 type of operating system
Source (Whhs, 2018)
easy environment to use. This is a stable, multi-tasking and multi-user system for laptops and for desktops
(Gcflearn, 2018).
Android:
This is a mobile operating system that is developed by Google mainly for touch screen mobiles. The
design of this android software’s permits to the user interaction in a different way and it provide facilities
such as tapping swiping and pinching. Instead of mobile, it can be employed to the televisions
wristwatches and in cars to interface with users.
IOS:
It is a mobile operating system that is more over 10 years old. Basically, it is run on Apple smart mobile
phones, such as in iPod’s and iPhones. It is main software that allows the user to interact with Apple
mobile phones and tablets. When you visit settings of your tablet or mobile phones wherefrom you can
make changes such as brightness, Bluetooth on and off, Wi-Fi all these are done by the operating system.
(Barraclough, 2015).
Figure 4 type of operating system
Source (Whhs, 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
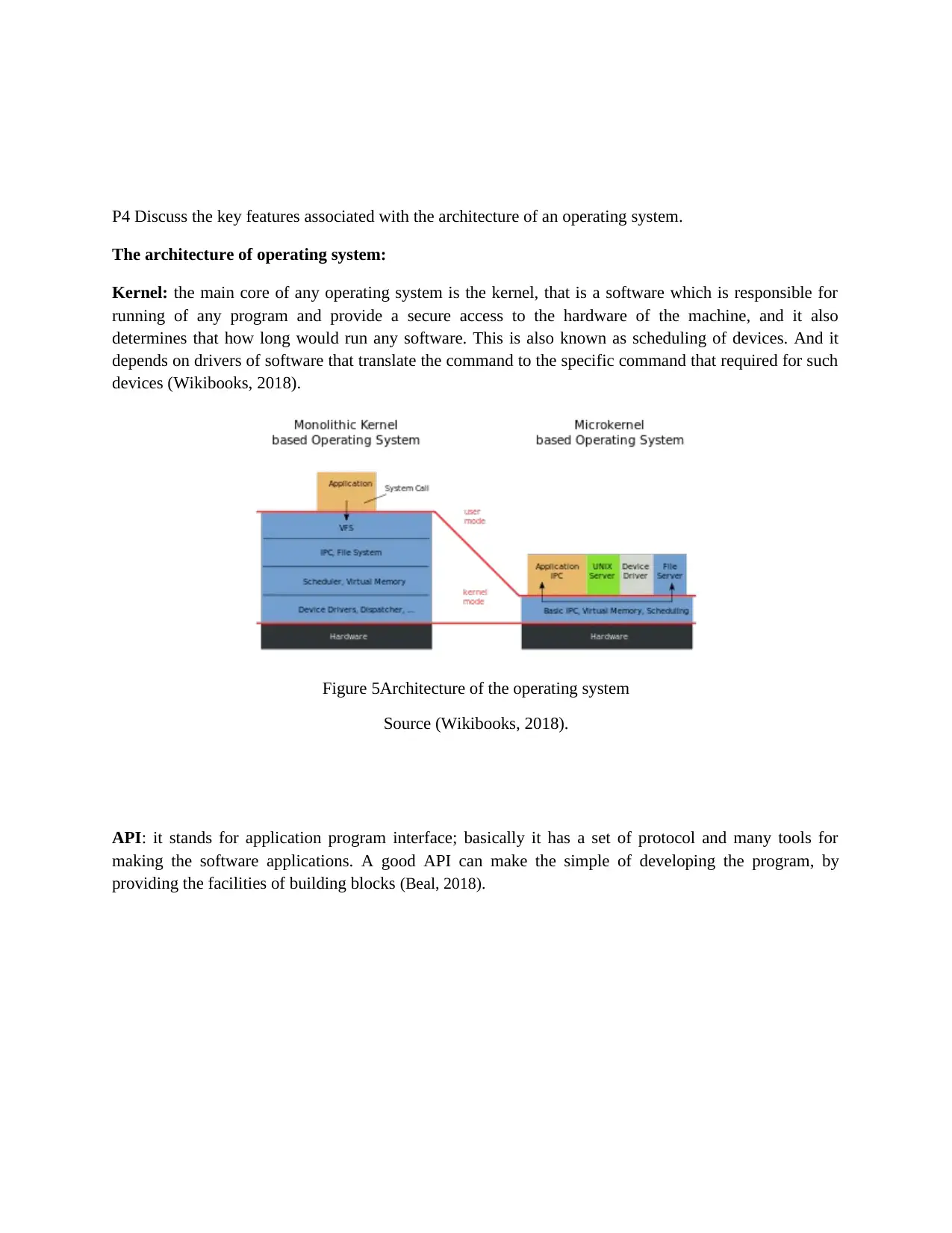
P4 Discuss the key features associated with the architecture of an operating system.
The architecture of operating system:
Kernel: the main core of any operating system is the kernel, that is a software which is responsible for
running of any program and provide a secure access to the hardware of the machine, and it also
determines that how long would run any software. This is also known as scheduling of devices. And it
depends on drivers of software that translate the command to the specific command that required for such
devices (Wikibooks, 2018).
Figure 5Architecture of the operating system
Source (Wikibooks, 2018).
API: it stands for application program interface; basically it has a set of protocol and many tools for
making the software applications. A good API can make the simple of developing the program, by
providing the facilities of building blocks (Beal, 2018).
The architecture of operating system:
Kernel: the main core of any operating system is the kernel, that is a software which is responsible for
running of any program and provide a secure access to the hardware of the machine, and it also
determines that how long would run any software. This is also known as scheduling of devices. And it
depends on drivers of software that translate the command to the specific command that required for such
devices (Wikibooks, 2018).
Figure 5Architecture of the operating system
Source (Wikibooks, 2018).
API: it stands for application program interface; basically it has a set of protocol and many tools for
making the software applications. A good API can make the simple of developing the program, by
providing the facilities of building blocks (Beal, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Operating system services:
User interface: it is the main part of operating system that provides to user interaction with devices such
as enter into and receives the information from the computer.
Graphical user interface: basically GUI is the widely used interface by the operating system, instead of
TUI because users can manipulate the multiple graphical objects.
TUI: it stands for text user interface, in which commands are entered in the form of text a few operating
systems used this.
Figure 6: operating system service
Source (Balasundar, 2012).
User interface: it is the main part of operating system that provides to user interaction with devices such
as enter into and receives the information from the computer.
Graphical user interface: basically GUI is the widely used interface by the operating system, instead of
TUI because users can manipulate the multiple graphical objects.
TUI: it stands for text user interface, in which commands are entered in the form of text a few operating
systems used this.
Figure 6: operating system service
Source (Balasundar, 2012).

Memory management: memory management is the controlling and managing the memory of a computer
such as assigning the blocks to the various program that are running. In hardware, it includes the elements
that store the data such as RAM chip, caches and SSDs. In the operating system, it means the allocation
of memory blocks to the particular program as users demand. It involves the various steps such as
swapping, paging, fragmentation and memory allocation.
File management: a file means a collection of data or information that is stored by the computer. The
computer can store the file in local disk for long-term storage. Example of such type of storage is DVD,
CD, magnetic disk and an optical disk. A file system generally organized in the form of directories by
which user can understand easily (Thakur, 2018).
Hardware management: a computer is made from both software and hardware, software interact to the
hardware to receive the data and after manipulating this it displays the result on the output devices every
part of hardware comes with the software which is known as a driver. A drive works as a mediator
between the software and particular hardware devices.
Most of the driver of devices is installed at the time of booting into the memory by the operating system.
And some are loaded when that particular hardware is to be connected to the computer. For example
word processor sends a signal to the printer that data is to be sent by the drivers. Similar music player
sends the music to the sounds card driver (Teach-ict, 2018).
Figure 7 Hardware management
Source (Teach-ict, 2018).
such as assigning the blocks to the various program that are running. In hardware, it includes the elements
that store the data such as RAM chip, caches and SSDs. In the operating system, it means the allocation
of memory blocks to the particular program as users demand. It involves the various steps such as
swapping, paging, fragmentation and memory allocation.
File management: a file means a collection of data or information that is stored by the computer. The
computer can store the file in local disk for long-term storage. Example of such type of storage is DVD,
CD, magnetic disk and an optical disk. A file system generally organized in the form of directories by
which user can understand easily (Thakur, 2018).
Hardware management: a computer is made from both software and hardware, software interact to the
hardware to receive the data and after manipulating this it displays the result on the output devices every
part of hardware comes with the software which is known as a driver. A drive works as a mediator
between the software and particular hardware devices.
Most of the driver of devices is installed at the time of booting into the memory by the operating system.
And some are loaded when that particular hardware is to be connected to the computer. For example
word processor sends a signal to the printer that data is to be sent by the drivers. Similar music player
sends the music to the sounds card driver (Teach-ict, 2018).
Figure 7 Hardware management
Source (Teach-ict, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 29
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





