Computer Systems: A Comprehensive Guide to Hardware, Software, and Maintenance
VerifiedAdded on 2024/05/31
|33
|5277
|185
AI Summary
This comprehensive guide explores the fundamental concepts of computer systems, encompassing hardware, software, and peripheral components. It delves into the role of computer systems in various environments, including homes, businesses, gaming, networking, and real-time operations. The guide further examines different types of computer systems, their specifications, and cost considerations. It provides a detailed system design specification for a client's needs, evaluating its suitability for effective communication and data management. The guide also covers the practical aspects of building and configuring a computer system, including health and safety precautions, system installation, and testing procedures. Finally, it emphasizes the importance of routine maintenance tasks, such as defragmentation, clean-up, backup, system profiling, spyware/malware removal, and hardware cleaning. The guide concludes with a discussion on hardware and software upgrades, highlighting the need for continuous improvement and adaptation to technological advancements.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

COMPUTER SYSTEM
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
INTRODUCTION......................................................................................................................1
TASK 1......................................................................................................................................2
1.1 Role of computer systems in different environment........................................................2
1.2 explain the hardware, software and peripheral components of a computer system.........4
1.3 compares different types of computer systems................................................................7
TASK 2......................................................................................................................................9
2.1 produce a system design specification to meet a client’s needs......................................9
2.2 evaluate the suitability of a system design specification...............................................12
TASK 3....................................................................................................................................14
3.1 Build and configure a computer system to meet a design specification........................14
3.2 test and document a computer system............................................................................18
TASK 4....................................................................................................................................20
4.1 perform routine maintenance tasks on a computer system............................................20
4.2 upgrade the hardware and software on a computer system...........................................25
CONCLUSION........................................................................................................................27
References................................................................................................................................28
INTRODUCTION......................................................................................................................1
TASK 1......................................................................................................................................2
1.1 Role of computer systems in different environment........................................................2
1.2 explain the hardware, software and peripheral components of a computer system.........4
1.3 compares different types of computer systems................................................................7
TASK 2......................................................................................................................................9
2.1 produce a system design specification to meet a client’s needs......................................9
2.2 evaluate the suitability of a system design specification...............................................12
TASK 3....................................................................................................................................14
3.1 Build and configure a computer system to meet a design specification........................14
3.2 test and document a computer system............................................................................18
TASK 4....................................................................................................................................20
4.1 perform routine maintenance tasks on a computer system............................................20
4.2 upgrade the hardware and software on a computer system...........................................25
CONCLUSION........................................................................................................................27
References................................................................................................................................28

LIST OF TABLES
Table 1: Types of computer systems..........................................................................................7
Table 2: Recruitment system......................................................................................................9
Table 3: System of Receptionist................................................................................................9
Table 4: Systems of Recruitment manager..............................................................................10
Table 5: System of administrator.............................................................................................10
Table 6: Secretary System........................................................................................................11
Table 7: Server system.............................................................................................................11
Table 8: Client system..............................................................................................................12
Table 9: General component....................................................................................................12
Table 1: Types of computer systems..........................................................................................7
Table 2: Recruitment system......................................................................................................9
Table 3: System of Receptionist................................................................................................9
Table 4: Systems of Recruitment manager..............................................................................10
Table 5: System of administrator.............................................................................................10
Table 6: Secretary System........................................................................................................11
Table 7: Server system.............................................................................................................11
Table 8: Client system..............................................................................................................12
Table 9: General component....................................................................................................12

LIST OF FIGURES
Figure 1: Computers in research and business...........................................................................2
Figure 2: use of computers in gamming.....................................................................................3
Figure 3: computer hardware components.................................................................................4
Figure 4: Peripheral components...............................................................................................6
Figure 5: Anti-static mat and wrist stripe.................................................................................14
Figure 6: Motherboard installation...........................................................................................15
Figure 7: Inserting processor....................................................................................................15
Figure 8: inserting cooling fan.................................................................................................16
Figure 9: Locked and unlocked RAM clips.............................................................................16
Figure 10: Power supply and other details...............................................................................17
Figure 13: Task manager..........................................................................................................18
Figure 14: PRTG tool...............................................................................................................19
Figure 15: disk defragmentation tool.......................................................................................21
Figure 16: disk Clean up tool...................................................................................................22
Figure 17: windows backup tool..............................................................................................23
Figure 18: event viewer in windows........................................................................................24
Figure 19: Windows defender..................................................................................................24
Figure 20: winrar compression tool.........................................................................................25
Figure 1: Computers in research and business...........................................................................2
Figure 2: use of computers in gamming.....................................................................................3
Figure 3: computer hardware components.................................................................................4
Figure 4: Peripheral components...............................................................................................6
Figure 5: Anti-static mat and wrist stripe.................................................................................14
Figure 6: Motherboard installation...........................................................................................15
Figure 7: Inserting processor....................................................................................................15
Figure 8: inserting cooling fan.................................................................................................16
Figure 9: Locked and unlocked RAM clips.............................................................................16
Figure 10: Power supply and other details...............................................................................17
Figure 13: Task manager..........................................................................................................18
Figure 14: PRTG tool...............................................................................................................19
Figure 15: disk defragmentation tool.......................................................................................21
Figure 16: disk Clean up tool...................................................................................................22
Figure 17: windows backup tool..............................................................................................23
Figure 18: event viewer in windows........................................................................................24
Figure 19: Windows defender..................................................................................................24
Figure 20: winrar compression tool.........................................................................................25
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INTRODUCTION
The invention of computer is considered to be a revolutionary invention for mankind and
their progressive use can be seen in almost all the industrial sectors and at all the levels of the
economy. The computers are mainly known for their speed and accuracy which may not be
guaranteed by the human mind or body. The stress and fatigue that the human body feels
because of the work is not seen in the computers and they have a capacity to work 24X7.
In the given report we have focused on the importance of computers and their accuracy and
reliability which is discussed in terms their use for real time operations in the industry and
networking and real time operations. We also consider various parts of the computers that are
like software, hardware and other peripheral components which are build-up on the basis of
such computer designs. Here we have also considered the sizes and scope of computers in the
current markets and their scope in the future. We have tried o examine the changes in costs
for these computers as well. Various increasing specifications for 2D and 3D printing features
of the computers have also been discussed herein.
At the end we have tried to conclude with some suggestions and showing the impact of the
computers which is continuously increasing in the market. The future technologies that will
be connected with the computers are also analyzed in the report.
1
The invention of computer is considered to be a revolutionary invention for mankind and
their progressive use can be seen in almost all the industrial sectors and at all the levels of the
economy. The computers are mainly known for their speed and accuracy which may not be
guaranteed by the human mind or body. The stress and fatigue that the human body feels
because of the work is not seen in the computers and they have a capacity to work 24X7.
In the given report we have focused on the importance of computers and their accuracy and
reliability which is discussed in terms their use for real time operations in the industry and
networking and real time operations. We also consider various parts of the computers that are
like software, hardware and other peripheral components which are build-up on the basis of
such computer designs. Here we have also considered the sizes and scope of computers in the
current markets and their scope in the future. We have tried o examine the changes in costs
for these computers as well. Various increasing specifications for 2D and 3D printing features
of the computers have also been discussed herein.
At the end we have tried to conclude with some suggestions and showing the impact of the
computers which is continuously increasing in the market. The future technologies that will
be connected with the computers are also analyzed in the report.
1

TASK 1
1.1 Role of computer systems in different environment
The computers in the present-day systems are designed and produced according to the needs
of the organization (Card, 2017). The increasing dependency is also increasing the
unemployment in various sectors because of the increased accuracy and speed of the
computers.
Home:
People generally use computers in order to chat with their relatives and friends and connect
with the world. The management of expenses along with the backup of information and
personal data is effectively managed with computers at home (Ricci et.al. 2015).
Business:
The performance and speed along with the accuracy is one of the most basic features of
computers which can be useful for the business purpose. With the use of efficient computer
systems and technology the cost on labor resources can be reduced further.
Figure 1: Computers in research and business
(Source: computers in business, 2017)
Gamming:
2
1.1 Role of computer systems in different environment
The computers in the present-day systems are designed and produced according to the needs
of the organization (Card, 2017). The increasing dependency is also increasing the
unemployment in various sectors because of the increased accuracy and speed of the
computers.
Home:
People generally use computers in order to chat with their relatives and friends and connect
with the world. The management of expenses along with the backup of information and
personal data is effectively managed with computers at home (Ricci et.al. 2015).
Business:
The performance and speed along with the accuracy is one of the most basic features of
computers which can be useful for the business purpose. With the use of efficient computer
systems and technology the cost on labor resources can be reduced further.
Figure 1: Computers in research and business
(Source: computers in business, 2017)
Gamming:
2

For the purpose of gaming special computers and laptops are designed which not only
provide an enhance gaming experience but also support the graphic cards which help the
gamers to have a professional exposure (Kavanagh and Johnson, 2017).
Figure 2: use of computers in gamming
(Source: computers in games, 2017)
Networking and communication:
In order to keep in touch with the day to day requirements of the world and keep connected
with the requirements of the world, which also provides better information and data
(Silberschatz et.al. 2014). The sharing and receiving of information also becomes easier with
the advent of computers.
Real-time operations:
Various serious operational enhancements is also being facilitated by the advent of new
technological advances. The computer systems also consider and help in the controlling of
various operations like launching of rockets and controlling the temperature deviations and
also to detect various hurdles in the path is there are any detected (Wyglinski et.al. 2016).
This also enhances the planning process which also determines the risks and uncertainties in
the organization.
The computers today are designed in such a manner in which they are able to forecast future
assumptions as well on the basis of the study of past data and current positions.
3
provide an enhance gaming experience but also support the graphic cards which help the
gamers to have a professional exposure (Kavanagh and Johnson, 2017).
Figure 2: use of computers in gamming
(Source: computers in games, 2017)
Networking and communication:
In order to keep in touch with the day to day requirements of the world and keep connected
with the requirements of the world, which also provides better information and data
(Silberschatz et.al. 2014). The sharing and receiving of information also becomes easier with
the advent of computers.
Real-time operations:
Various serious operational enhancements is also being facilitated by the advent of new
technological advances. The computer systems also consider and help in the controlling of
various operations like launching of rockets and controlling the temperature deviations and
also to detect various hurdles in the path is there are any detected (Wyglinski et.al. 2016).
This also enhances the planning process which also determines the risks and uncertainties in
the organization.
The computers today are designed in such a manner in which they are able to forecast future
assumptions as well on the basis of the study of past data and current positions.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.2 explain the hardware, software and peripheral components of a computer system
Main components
Central processing unit (CPU):
The main part or as it is rightly known, the brain of the computer is the part of the computer
hardware without which no computer can function properly (Nalluri et.al. 2017).
Memory:
The primary and secondary memory of the computer functions very efficiently in functioning
and storage. The Random-access memory (RAM) holds the basic intermediate data of the
computer system whereas the secondary memory can help store the larger volumes of data
(Clemm et.al. 2016).
Bus size:
In order to achieve the highest standards of performance and progress in the market,
the firm definitely needs better technology which can be achieved by using the 64 bit
architecture through which the transfer can be superfast.
Hardware requirements
Network interface card:
In order to get a faster connectivity in the firm as well as the services that are to be provided
the customers. The Ethernet cables and wireless adapters make it easier (Hau, 2015).
Figure 3: computer hardware components
4
Main components
Central processing unit (CPU):
The main part or as it is rightly known, the brain of the computer is the part of the computer
hardware without which no computer can function properly (Nalluri et.al. 2017).
Memory:
The primary and secondary memory of the computer functions very efficiently in functioning
and storage. The Random-access memory (RAM) holds the basic intermediate data of the
computer system whereas the secondary memory can help store the larger volumes of data
(Clemm et.al. 2016).
Bus size:
In order to achieve the highest standards of performance and progress in the market,
the firm definitely needs better technology which can be achieved by using the 64 bit
architecture through which the transfer can be superfast.
Hardware requirements
Network interface card:
In order to get a faster connectivity in the firm as well as the services that are to be provided
the customers. The Ethernet cables and wireless adapters make it easier (Hau, 2015).
Figure 3: computer hardware components
4
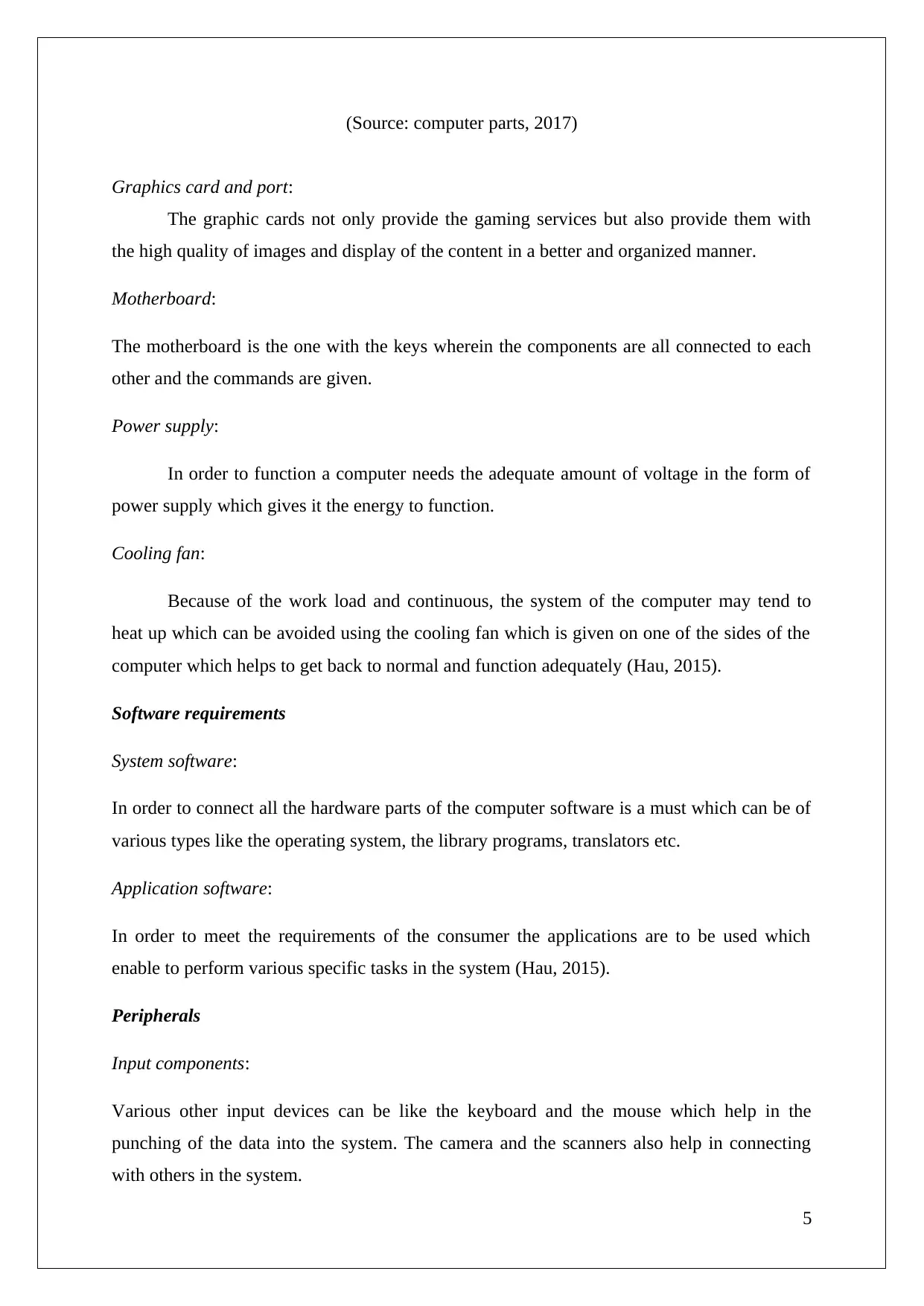
(Source: computer parts, 2017)
Graphics card and port:
The graphic cards not only provide the gaming services but also provide them with
the high quality of images and display of the content in a better and organized manner.
Motherboard:
The motherboard is the one with the keys wherein the components are all connected to each
other and the commands are given.
Power supply:
In order to function a computer needs the adequate amount of voltage in the form of
power supply which gives it the energy to function.
Cooling fan:
Because of the work load and continuous, the system of the computer may tend to
heat up which can be avoided using the cooling fan which is given on one of the sides of the
computer which helps to get back to normal and function adequately (Hau, 2015).
Software requirements
System software:
In order to connect all the hardware parts of the computer software is a must which can be of
various types like the operating system, the library programs, translators etc.
Application software:
In order to meet the requirements of the consumer the applications are to be used which
enable to perform various specific tasks in the system (Hau, 2015).
Peripherals
Input components:
Various other input devices can be like the keyboard and the mouse which help in the
punching of the data into the system. The camera and the scanners also help in connecting
with others in the system.
5
Graphics card and port:
The graphic cards not only provide the gaming services but also provide them with
the high quality of images and display of the content in a better and organized manner.
Motherboard:
The motherboard is the one with the keys wherein the components are all connected to each
other and the commands are given.
Power supply:
In order to function a computer needs the adequate amount of voltage in the form of
power supply which gives it the energy to function.
Cooling fan:
Because of the work load and continuous, the system of the computer may tend to
heat up which can be avoided using the cooling fan which is given on one of the sides of the
computer which helps to get back to normal and function adequately (Hau, 2015).
Software requirements
System software:
In order to connect all the hardware parts of the computer software is a must which can be of
various types like the operating system, the library programs, translators etc.
Application software:
In order to meet the requirements of the consumer the applications are to be used which
enable to perform various specific tasks in the system (Hau, 2015).
Peripherals
Input components:
Various other input devices can be like the keyboard and the mouse which help in the
punching of the data into the system. The camera and the scanners also help in connecting
with others in the system.
5
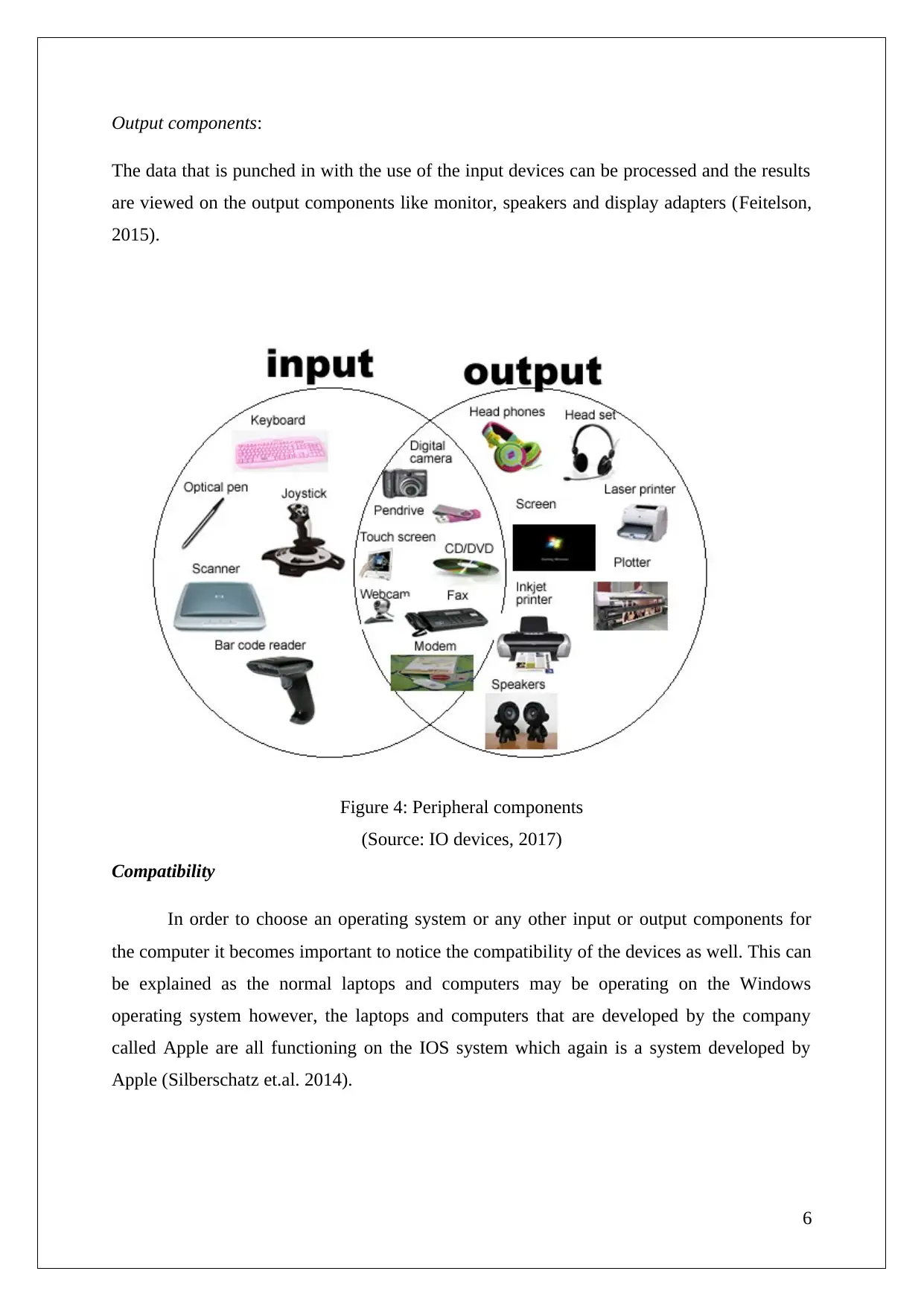
Output components:
The data that is punched in with the use of the input devices can be processed and the results
are viewed on the output components like monitor, speakers and display adapters (Feitelson,
2015).
Figure 4: Peripheral components
(Source: IO devices, 2017)
Compatibility
In order to choose an operating system or any other input or output components for
the computer it becomes important to notice the compatibility of the devices as well. This can
be explained as the normal laptops and computers may be operating on the Windows
operating system however, the laptops and computers that are developed by the company
called Apple are all functioning on the IOS system which again is a system developed by
Apple (Silberschatz et.al. 2014).
6
The data that is punched in with the use of the input devices can be processed and the results
are viewed on the output components like monitor, speakers and display adapters (Feitelson,
2015).
Figure 4: Peripheral components
(Source: IO devices, 2017)
Compatibility
In order to choose an operating system or any other input or output components for
the computer it becomes important to notice the compatibility of the devices as well. This can
be explained as the normal laptops and computers may be operating on the Windows
operating system however, the laptops and computers that are developed by the company
called Apple are all functioning on the IOS system which again is a system developed by
Apple (Silberschatz et.al. 2014).
6
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Along with this the compatibility of the software and hardware devices is also
important to be noticed and their functioning should be in a sync which helps the operational
abilities of the computer in a better manner.
Performance
The performance of a computer is also the outcome of the perfect combination and
compatibility of the devices. The storage systems also determine the performance of the
computers at certain levels which determines the high-speed performance and the accuracy of
work as well. The display is dependent on the effectiveness of the graphic cards.
Cost
The costs of computers are outnumbered by the benefits and utilities that it brings in
the organization. The effective implementation of the computer systems can also bring in
various competitive advantages with lower costs of production for the firms.
Future scope and usability
The scope and usability of these computers and the demand for better and improved
versions of software is increasing continuously in the market (Hilburn et.al. 2018). The
companies have started to realize the importance and usage of the computers and the
computers also have proved to be very effective in the functioning along with the reduction
of costs in the organization.
With the improved automation in the industry the firms are also able to target the
reduction of energy and human resource consumption as well as the power consumption
however a particular amount of charge or power is also necessary for the computers to
function in an appropriate manner (Keohane et.al. 2015). The display devices and specially
the Monitor in the hardware system is based on the functioning of the LED lights as well.
There is a wider scope for the new and better inventions of the versions of computers to
reduce the consumption of such power and improve the configuration of data and storage in
the computer as well.
1.3 compares different types of computer systems
Table 1: Types of computer systems
Features Supercomputers Mini- Mobile Mainframe Micro-
7
important to be noticed and their functioning should be in a sync which helps the operational
abilities of the computer in a better manner.
Performance
The performance of a computer is also the outcome of the perfect combination and
compatibility of the devices. The storage systems also determine the performance of the
computers at certain levels which determines the high-speed performance and the accuracy of
work as well. The display is dependent on the effectiveness of the graphic cards.
Cost
The costs of computers are outnumbered by the benefits and utilities that it brings in
the organization. The effective implementation of the computer systems can also bring in
various competitive advantages with lower costs of production for the firms.
Future scope and usability
The scope and usability of these computers and the demand for better and improved
versions of software is increasing continuously in the market (Hilburn et.al. 2018). The
companies have started to realize the importance and usage of the computers and the
computers also have proved to be very effective in the functioning along with the reduction
of costs in the organization.
With the improved automation in the industry the firms are also able to target the
reduction of energy and human resource consumption as well as the power consumption
however a particular amount of charge or power is also necessary for the computers to
function in an appropriate manner (Keohane et.al. 2015). The display devices and specially
the Monitor in the hardware system is based on the functioning of the LED lights as well.
There is a wider scope for the new and better inventions of the versions of computers to
reduce the consumption of such power and improve the configuration of data and storage in
the computer as well.
1.3 compares different types of computer systems
Table 1: Types of computer systems
Features Supercomputers Mini- Mobile Mainframe Micro-
7
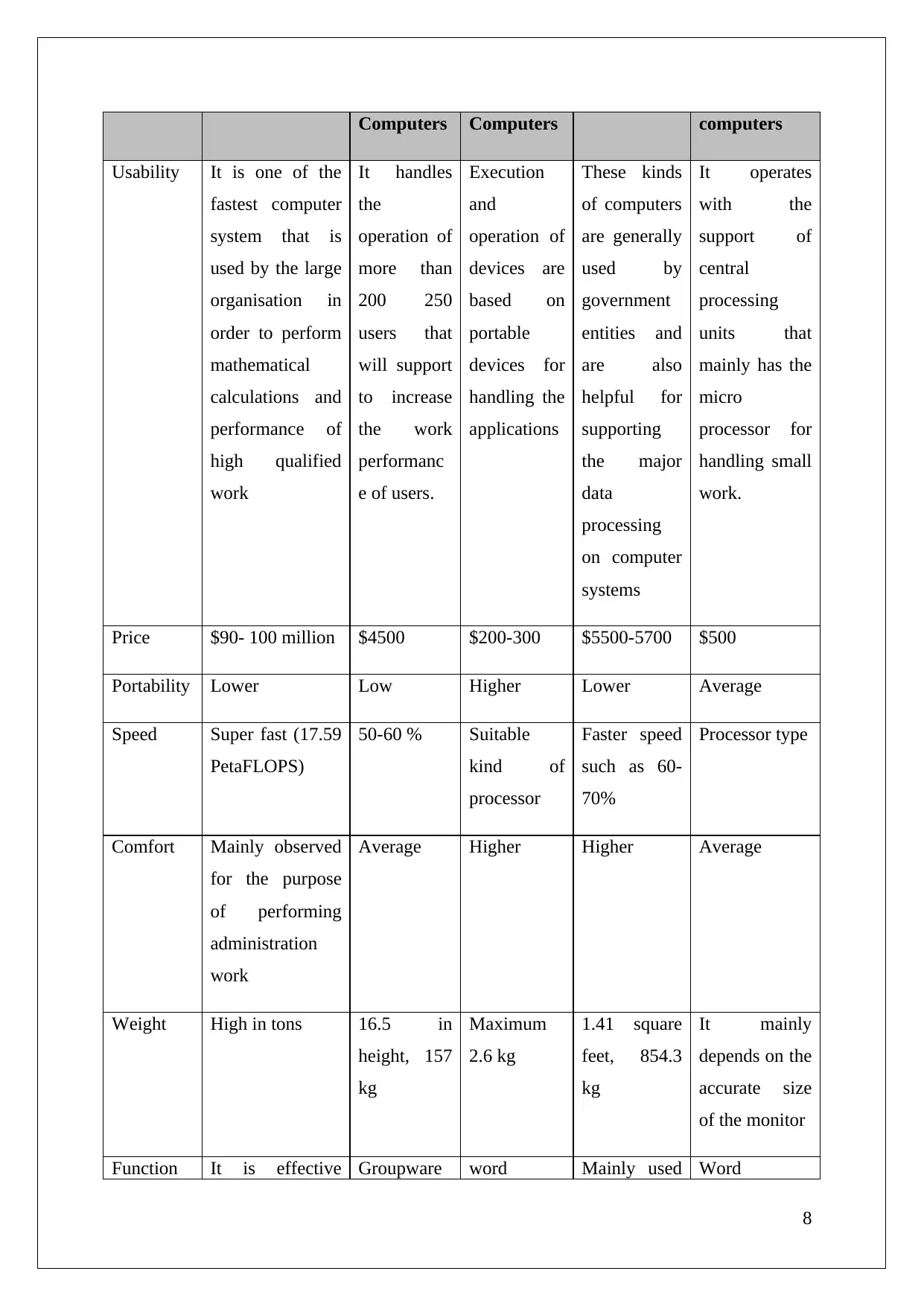
Computers Computers computers
Usability It is one of the
fastest computer
system that is
used by the large
organisation in
order to perform
mathematical
calculations and
performance of
high qualified
work
It handles
the
operation of
more than
200 250
users that
will support
to increase
the work
performanc
e of users.
Execution
and
operation of
devices are
based on
portable
devices for
handling the
applications
These kinds
of computers
are generally
used by
government
entities and
are also
helpful for
supporting
the major
data
processing
on computer
systems
It operates
with the
support of
central
processing
units that
mainly has the
micro
processor for
handling small
work.
Price $90- 100 million $4500 $200-300 $5500-5700 $500
Portability Lower Low Higher Lower Average
Speed Super fast (17.59
PetaFLOPS)
50-60 % Suitable
kind of
processor
Faster speed
such as 60-
70%
Processor type
Comfort Mainly observed
for the purpose
of performing
administration
work
Average Higher Higher Average
Weight High in tons 16.5 in
height, 157
kg
Maximum
2.6 kg
1.41 square
feet, 854.3
kg
It mainly
depends on the
accurate size
of the monitor
Function It is effective Groupware word Mainly used Word
8
Usability It is one of the
fastest computer
system that is
used by the large
organisation in
order to perform
mathematical
calculations and
performance of
high qualified
work
It handles
the
operation of
more than
200 250
users that
will support
to increase
the work
performanc
e of users.
Execution
and
operation of
devices are
based on
portable
devices for
handling the
applications
These kinds
of computers
are generally
used by
government
entities and
are also
helpful for
supporting
the major
data
processing
on computer
systems
It operates
with the
support of
central
processing
units that
mainly has the
micro
processor for
handling small
work.
Price $90- 100 million $4500 $200-300 $5500-5700 $500
Portability Lower Low Higher Lower Average
Speed Super fast (17.59
PetaFLOPS)
50-60 % Suitable
kind of
processor
Faster speed
such as 60-
70%
Processor type
Comfort Mainly observed
for the purpose
of performing
administration
work
Average Higher Higher Average
Weight High in tons 16.5 in
height, 157
kg
Maximum
2.6 kg
1.41 square
feet, 854.3
kg
It mainly
depends on the
accurate size
of the monitor
Function It is effective Groupware word Mainly used Word
8
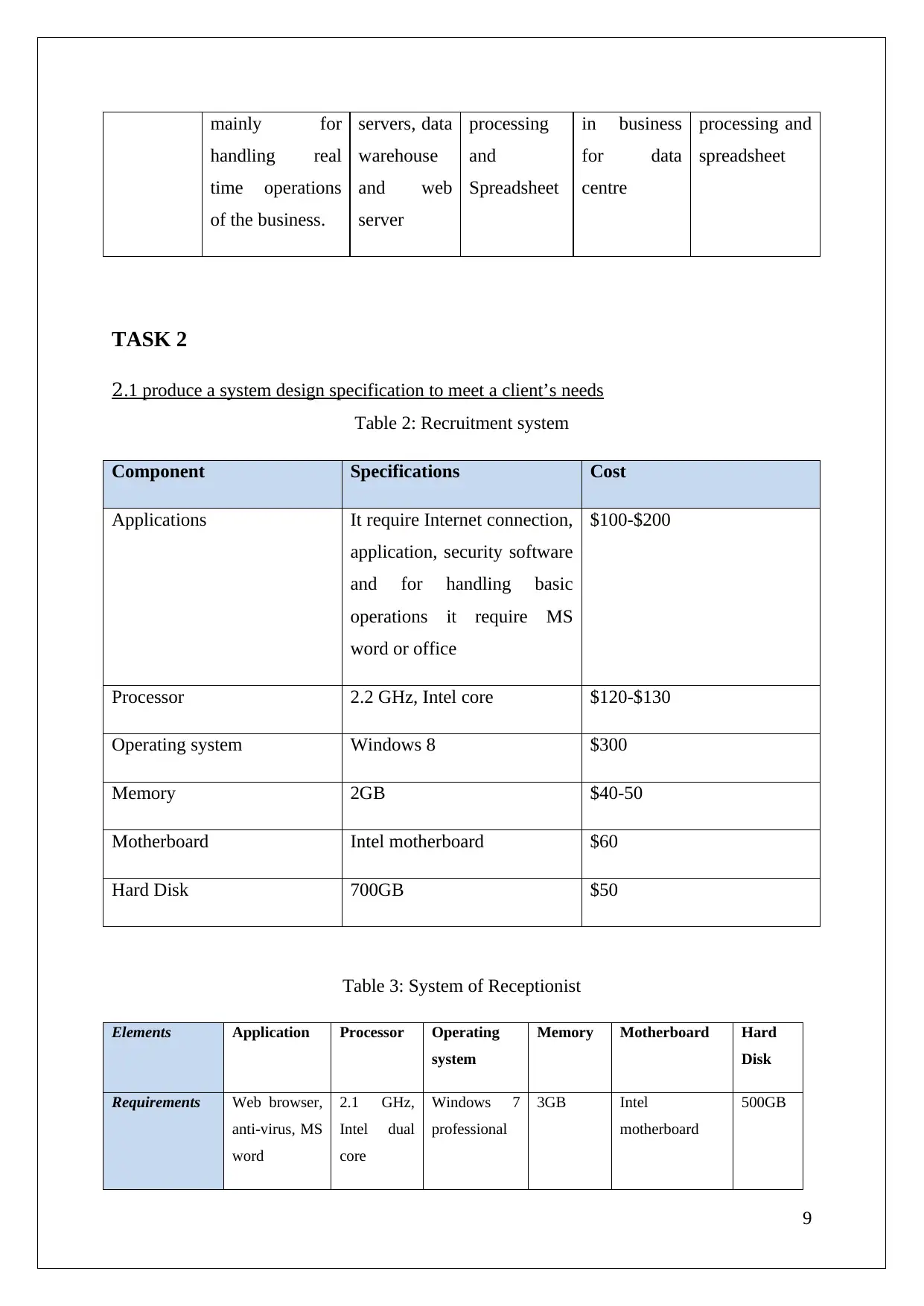
mainly for
handling real
time operations
of the business.
servers, data
warehouse
and web
server
processing
and
Spreadsheet
in business
for data
centre
processing and
spreadsheet
TASK 2
2.1 produce a system design specification to meet a client’s needs
Table 2: Recruitment system
Component Specifications Cost
Applications It require Internet connection,
application, security software
and for handling basic
operations it require MS
word or office
$100-$200
Processor 2.2 GHz, Intel core $120-$130
Operating system Windows 8 $300
Memory 2GB $40-50
Motherboard Intel motherboard $60
Hard Disk 700GB $50
Table 3: System of Receptionist
Elements Application Processor Operating
system
Memory Motherboard Hard
Disk
Requirements Web browser,
anti-virus, MS
word
2.1 GHz,
Intel dual
core
Windows 7
professional
3GB Intel
motherboard
500GB
9
handling real
time operations
of the business.
servers, data
warehouse
and web
server
processing
and
Spreadsheet
in business
for data
centre
processing and
spreadsheet
TASK 2
2.1 produce a system design specification to meet a client’s needs
Table 2: Recruitment system
Component Specifications Cost
Applications It require Internet connection,
application, security software
and for handling basic
operations it require MS
word or office
$100-$200
Processor 2.2 GHz, Intel core $120-$130
Operating system Windows 8 $300
Memory 2GB $40-50
Motherboard Intel motherboard $60
Hard Disk 700GB $50
Table 3: System of Receptionist
Elements Application Processor Operating
system
Memory Motherboard Hard
Disk
Requirements Web browser,
anti-virus, MS
word
2.1 GHz,
Intel dual
core
Windows 7
professional
3GB Intel
motherboard
500GB
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
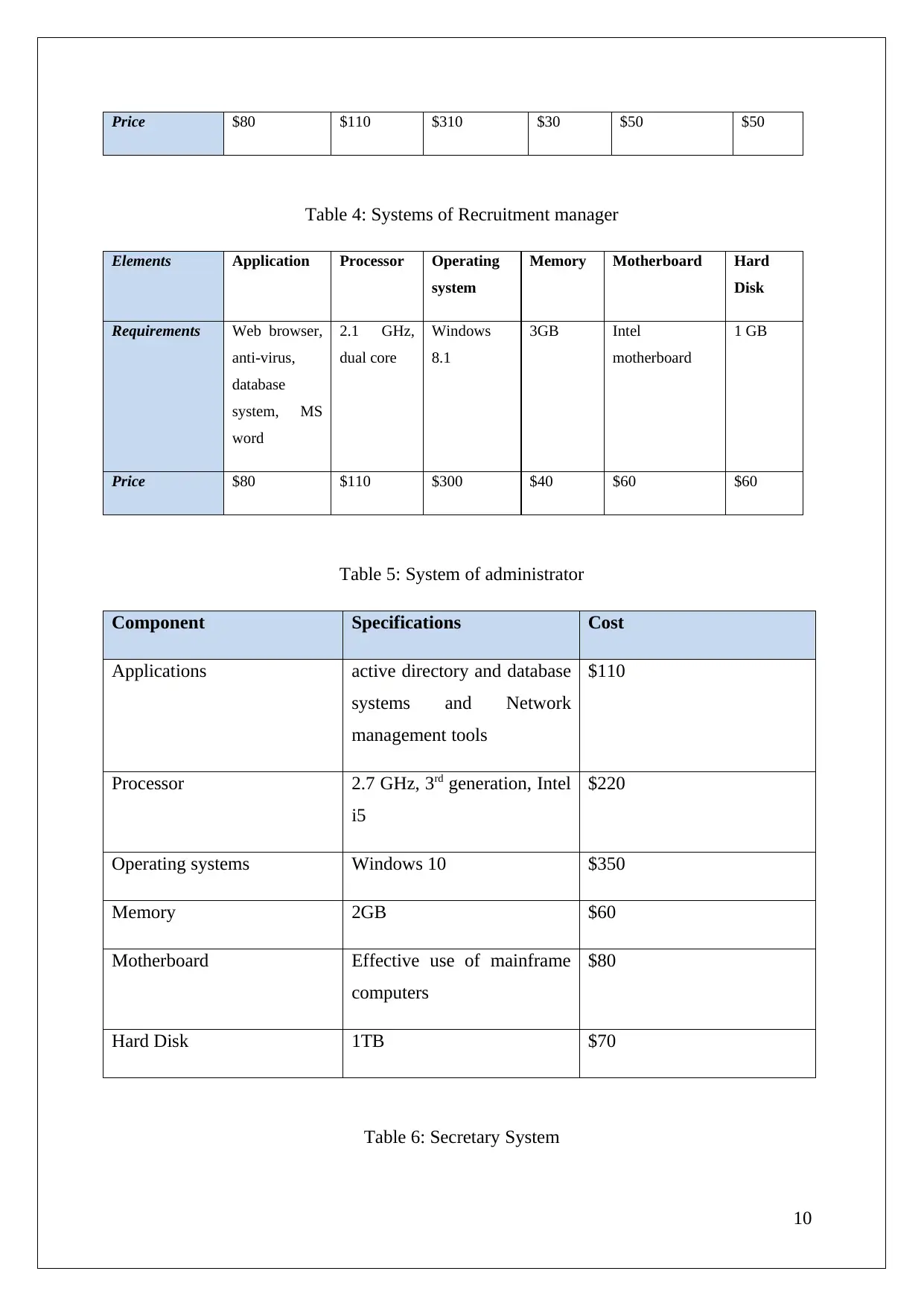
Price $80 $110 $310 $30 $50 $50
Table 4: Systems of Recruitment manager
Elements Application Processor Operating
system
Memory Motherboard Hard
Disk
Requirements Web browser,
anti-virus,
database
system, MS
word
2.1 GHz,
dual core
Windows
8.1
3GB Intel
motherboard
1 GB
Price $80 $110 $300 $40 $60 $60
Table 5: System of administrator
Component Specifications Cost
Applications active directory and database
systems and Network
management tools
$110
Processor 2.7 GHz, 3rd generation, Intel
i5
$220
Operating systems Windows 10 $350
Memory 2GB $60
Motherboard Effective use of mainframe
computers
$80
Hard Disk 1TB $70
Table 6: Secretary System
10
Table 4: Systems of Recruitment manager
Elements Application Processor Operating
system
Memory Motherboard Hard
Disk
Requirements Web browser,
anti-virus,
database
system, MS
word
2.1 GHz,
dual core
Windows
8.1
3GB Intel
motherboard
1 GB
Price $80 $110 $300 $40 $60 $60
Table 5: System of administrator
Component Specifications Cost
Applications active directory and database
systems and Network
management tools
$110
Processor 2.7 GHz, 3rd generation, Intel
i5
$220
Operating systems Windows 10 $350
Memory 2GB $60
Motherboard Effective use of mainframe
computers
$80
Hard Disk 1TB $70
Table 6: Secretary System
10
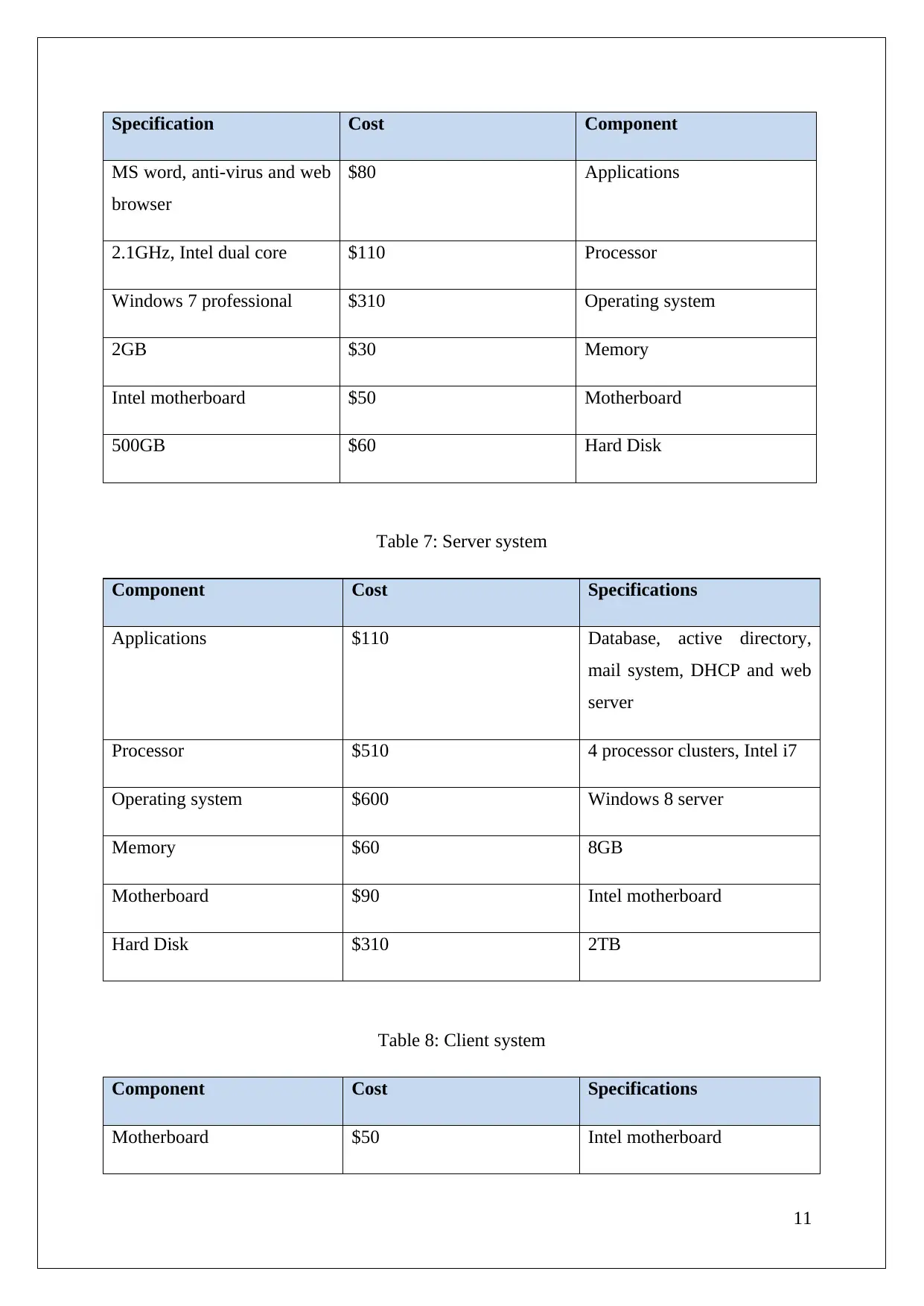
Specification Cost Component
MS word, anti-virus and web
browser
$80 Applications
2.1GHz, Intel dual core $110 Processor
Windows 7 professional $310 Operating system
2GB $30 Memory
Intel motherboard $50 Motherboard
500GB $60 Hard Disk
Table 7: Server system
Component Cost Specifications
Applications $110 Database, active directory,
mail system, DHCP and web
server
Processor $510 4 processor clusters, Intel i7
Operating system $600 Windows 8 server
Memory $60 8GB
Motherboard $90 Intel motherboard
Hard Disk $310 2TB
Table 8: Client system
Component Cost Specifications
Motherboard $50 Intel motherboard
11
MS word, anti-virus and web
browser
$80 Applications
2.1GHz, Intel dual core $110 Processor
Windows 7 professional $310 Operating system
2GB $30 Memory
Intel motherboard $50 Motherboard
500GB $60 Hard Disk
Table 7: Server system
Component Cost Specifications
Applications $110 Database, active directory,
mail system, DHCP and web
server
Processor $510 4 processor clusters, Intel i7
Operating system $600 Windows 8 server
Memory $60 8GB
Motherboard $90 Intel motherboard
Hard Disk $310 2TB
Table 8: Client system
Component Cost Specifications
Motherboard $50 Intel motherboard
11
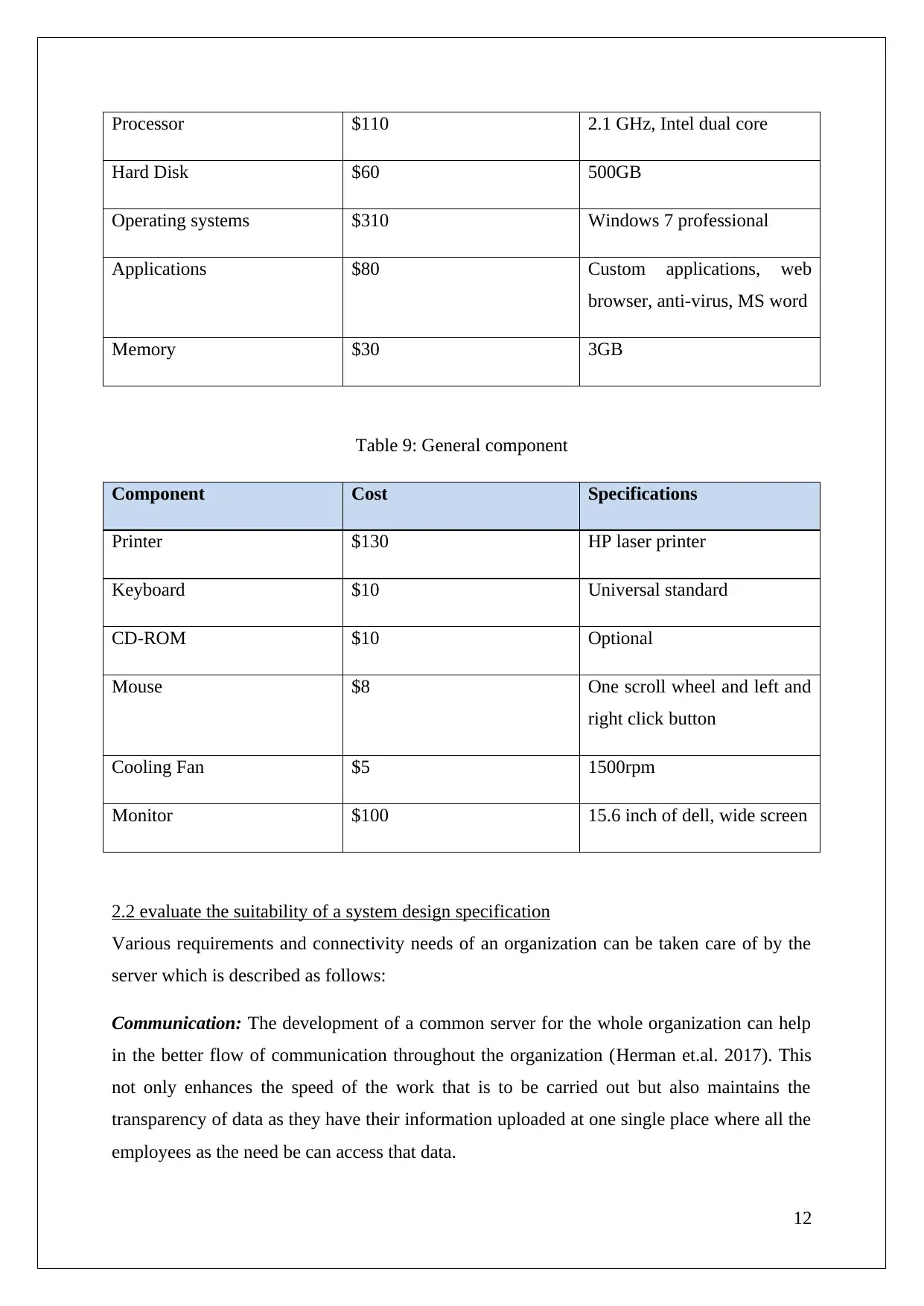
Processor $110 2.1 GHz, Intel dual core
Hard Disk $60 500GB
Operating systems $310 Windows 7 professional
Applications $80 Custom applications, web
browser, anti-virus, MS word
Memory $30 3GB
Table 9: General component
Component Cost Specifications
Printer $130 HP laser printer
Keyboard $10 Universal standard
CD-ROM $10 Optional
Mouse $8 One scroll wheel and left and
right click button
Cooling Fan $5 1500rpm
Monitor $100 15.6 inch of dell, wide screen
2.2 evaluate the suitability of a system design specification
Various requirements and connectivity needs of an organization can be taken care of by the
server which is described as follows:
Communication: The development of a common server for the whole organization can help
in the better flow of communication throughout the organization (Herman et.al. 2017). This
not only enhances the speed of the work that is to be carried out but also maintains the
transparency of data as they have their information uploaded at one single place where all the
employees as the need be can access that data.
12
Hard Disk $60 500GB
Operating systems $310 Windows 7 professional
Applications $80 Custom applications, web
browser, anti-virus, MS word
Memory $30 3GB
Table 9: General component
Component Cost Specifications
Printer $130 HP laser printer
Keyboard $10 Universal standard
CD-ROM $10 Optional
Mouse $8 One scroll wheel and left and
right click button
Cooling Fan $5 1500rpm
Monitor $100 15.6 inch of dell, wide screen
2.2 evaluate the suitability of a system design specification
Various requirements and connectivity needs of an organization can be taken care of by the
server which is described as follows:
Communication: The development of a common server for the whole organization can help
in the better flow of communication throughout the organization (Herman et.al. 2017). This
not only enhances the speed of the work that is to be carried out but also maintains the
transparency of data as they have their information uploaded at one single place where all the
employees as the need be can access that data.
12
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Data management: The database management systems are used in order to manage all the
data that the firm comes across of produces which is considered to be important for the
organization. Such data can be uploaded and made available to anyone who requires it with
the help of the servers and other database management systems (DBMS)
13
data that the firm comes across of produces which is considered to be important for the
organization. Such data can be uploaded and made available to anyone who requires it with
the help of the servers and other database management systems (DBMS)
13

TASK 3
3.1 Build and configure a computer system to meet a design specification
Consider the following steps for configuring a computer system:
Health and safety precautions
Even though the computers have proved to be one of the revolutionary inventions of mankind
there can be some measures which must be taken as well with regards to the precaution from
the disadvantages or the negative effects of the excess use of the computer. Such
disadvantages or negative effects can be described as follows:
For avoiding the static power which causes harm to the body, the static mat should be
used for the computers to prevent such harm.
In order to be safer around the use of such open wires of keyboards as well as mouse
and various other output devices or hardware devices one must use the anti-static
wrist stripes (Groover, 2016). This should be done while contacting the metal.
When you want to confirm the flow of the static power in the machine you can do so
safely with the examination of the cooling fan with the touch of a hand and this
should be done when the examiner is in touch with the ground.
Figure 5: Anti-static mat and wrist stripe
(Source: Anti-static mat and wrist stripe, 2017)
System installation
14
3.1 Build and configure a computer system to meet a design specification
Consider the following steps for configuring a computer system:
Health and safety precautions
Even though the computers have proved to be one of the revolutionary inventions of mankind
there can be some measures which must be taken as well with regards to the precaution from
the disadvantages or the negative effects of the excess use of the computer. Such
disadvantages or negative effects can be described as follows:
For avoiding the static power which causes harm to the body, the static mat should be
used for the computers to prevent such harm.
In order to be safer around the use of such open wires of keyboards as well as mouse
and various other output devices or hardware devices one must use the anti-static
wrist stripes (Groover, 2016). This should be done while contacting the metal.
When you want to confirm the flow of the static power in the machine you can do so
safely with the examination of the cooling fan with the touch of a hand and this
should be done when the examiner is in touch with the ground.
Figure 5: Anti-static mat and wrist stripe
(Source: Anti-static mat and wrist stripe, 2017)
System installation
14
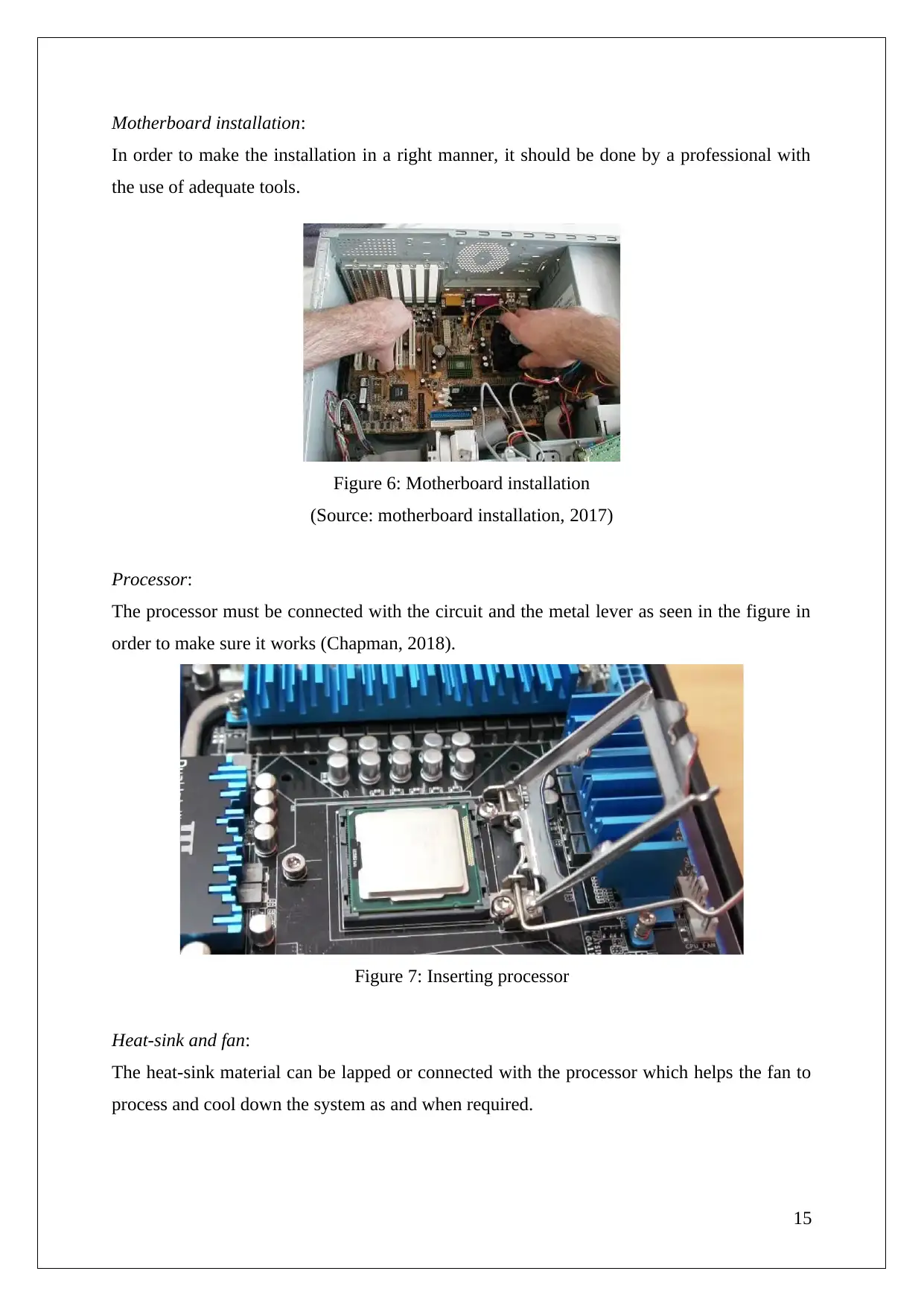
Motherboard installation:
In order to make the installation in a right manner, it should be done by a professional with
the use of adequate tools.
Figure 6: Motherboard installation
(Source: motherboard installation, 2017)
Processor:
The processor must be connected with the circuit and the metal lever as seen in the figure in
order to make sure it works (Chapman, 2018).
Figure 7: Inserting processor
Heat-sink and fan:
The heat-sink material can be lapped or connected with the processor which helps the fan to
process and cool down the system as and when required.
15
In order to make the installation in a right manner, it should be done by a professional with
the use of adequate tools.
Figure 6: Motherboard installation
(Source: motherboard installation, 2017)
Processor:
The processor must be connected with the circuit and the metal lever as seen in the figure in
order to make sure it works (Chapman, 2018).
Figure 7: Inserting processor
Heat-sink and fan:
The heat-sink material can be lapped or connected with the processor which helps the fan to
process and cool down the system as and when required.
15
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 8: inserting cooling fan
(Source: inserting cooling fan, 2017)
Memory:
While inserting the memory of the computer it is necessary to make sure the supply of power
is not on. The RAM cards must be inserted according to the cuts.
Figure 9: Locked and unlocked RAM clips
Power supply:
The power supply box is to be inserted at the end with the use of adequate tools.
Installation of other components:
Other devices like the optical drives along with the hard disk are to be installed now.
16
(Source: inserting cooling fan, 2017)
Memory:
While inserting the memory of the computer it is necessary to make sure the supply of power
is not on. The RAM cards must be inserted according to the cuts.
Figure 9: Locked and unlocked RAM clips
Power supply:
The power supply box is to be inserted at the end with the use of adequate tools.
Installation of other components:
Other devices like the optical drives along with the hard disk are to be installed now.
16
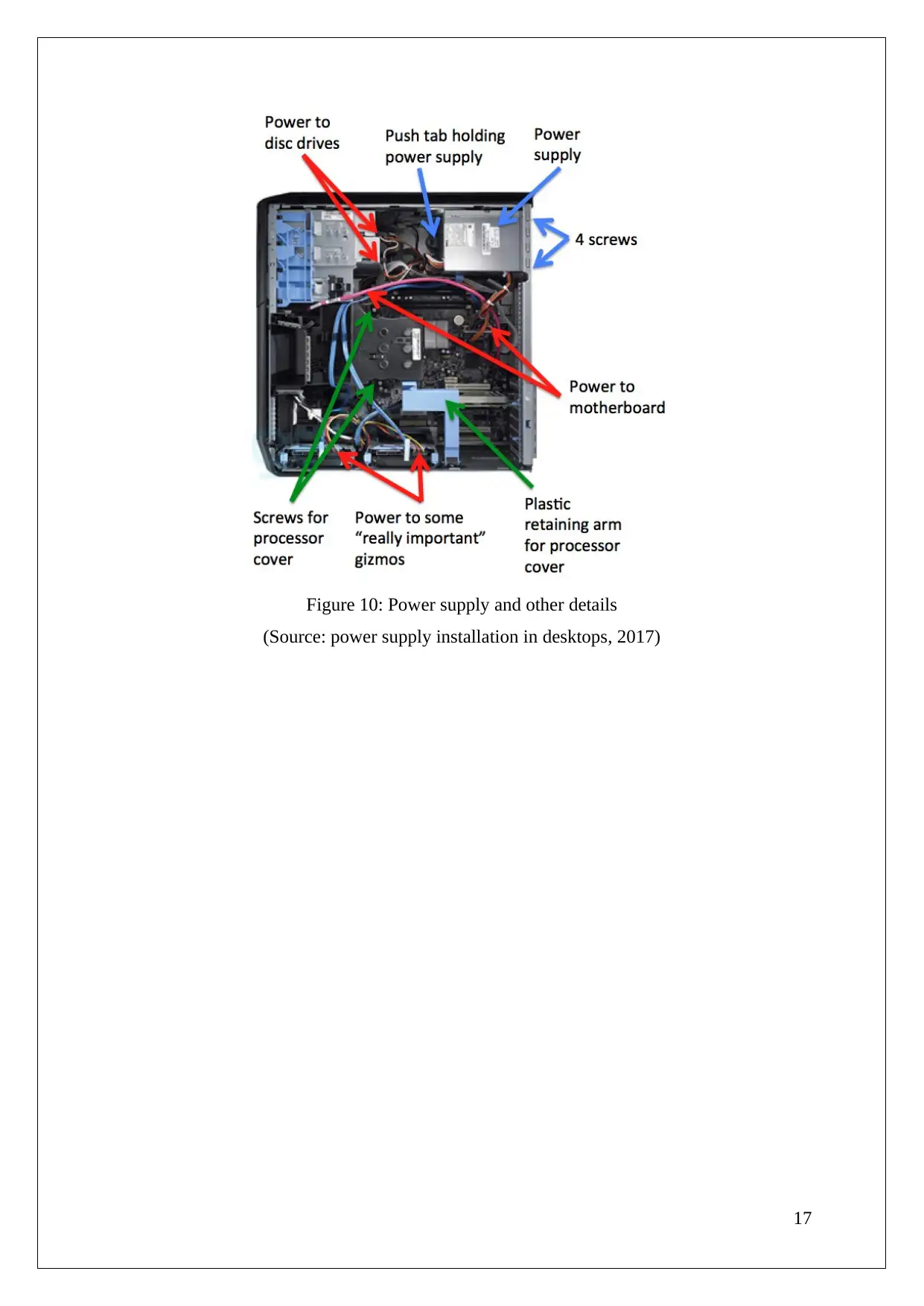
Figure 10: Power supply and other details
(Source: power supply installation in desktops, 2017)
17
(Source: power supply installation in desktops, 2017)
17
Figure 11: Task manager
3.2 test and document a computer system
In order to make sure that the tools and parts are fit according to the needs of the system and
all the parts are inserted where they are supposed to be the organization can use the Pressler
monitoring tool which ensures that the performance of the machine parts is adequate and
according to the needs (Frey and Osborne, 2017.).
The virtual monitor introduced by Pasessler’s is also known as the PRTG tool which is used
to analyse the efficiency of the operating and virtual machine and the transmission of
information between them.
18
3.2 test and document a computer system
In order to make sure that the tools and parts are fit according to the needs of the system and
all the parts are inserted where they are supposed to be the organization can use the Pressler
monitoring tool which ensures that the performance of the machine parts is adequate and
according to the needs (Frey and Osborne, 2017.).
The virtual monitor introduced by Pasessler’s is also known as the PRTG tool which is used
to analyse the efficiency of the operating and virtual machine and the transmission of
information between them.
18
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
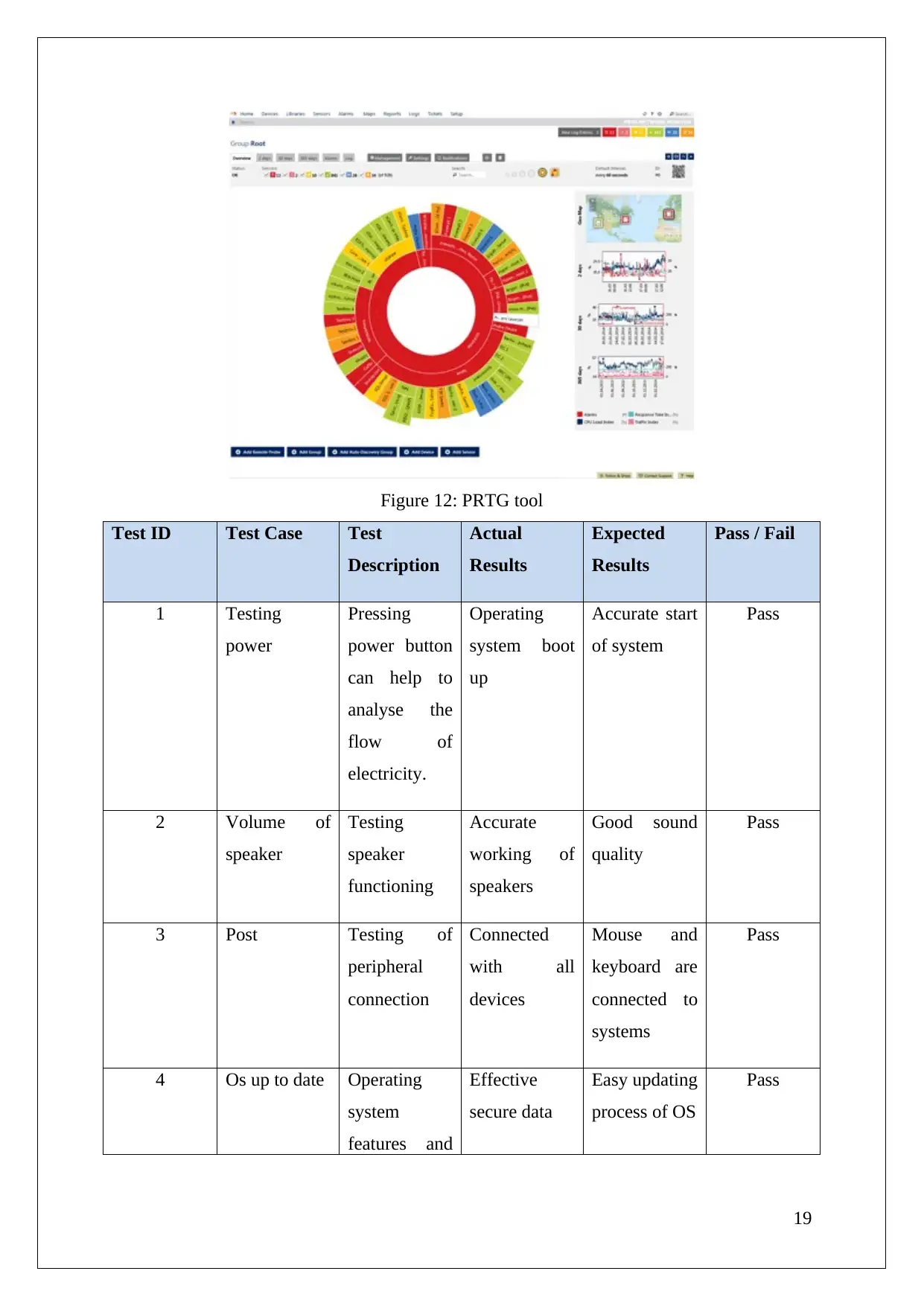
Figure 12: PRTG tool
Test ID Test Case Test
Description
Actual
Results
Expected
Results
Pass / Fail
1 Testing
power
Pressing
power button
can help to
analyse the
flow of
electricity.
Operating
system boot
up
Accurate start
of system
Pass
2 Volume of
speaker
Testing
speaker
functioning
Accurate
working of
speakers
Good sound
quality
Pass
3 Post Testing of
peripheral
connection
Connected
with all
devices
Mouse and
keyboard are
connected to
systems
Pass
4 Os up to date Operating
system
features and
Effective
secure data
Easy updating
process of OS
Pass
19
Test ID Test Case Test
Description
Actual
Results
Expected
Results
Pass / Fail
1 Testing
power
Pressing
power button
can help to
analyse the
flow of
electricity.
Operating
system boot
up
Accurate start
of system
Pass
2 Volume of
speaker
Testing
speaker
functioning
Accurate
working of
speakers
Good sound
quality
Pass
3 Post Testing of
peripheral
connection
Connected
with all
devices
Mouse and
keyboard are
connected to
systems
Pass
4 Os up to date Operating
system
features and
Effective
secure data
Easy updating
process of OS
Pass
19
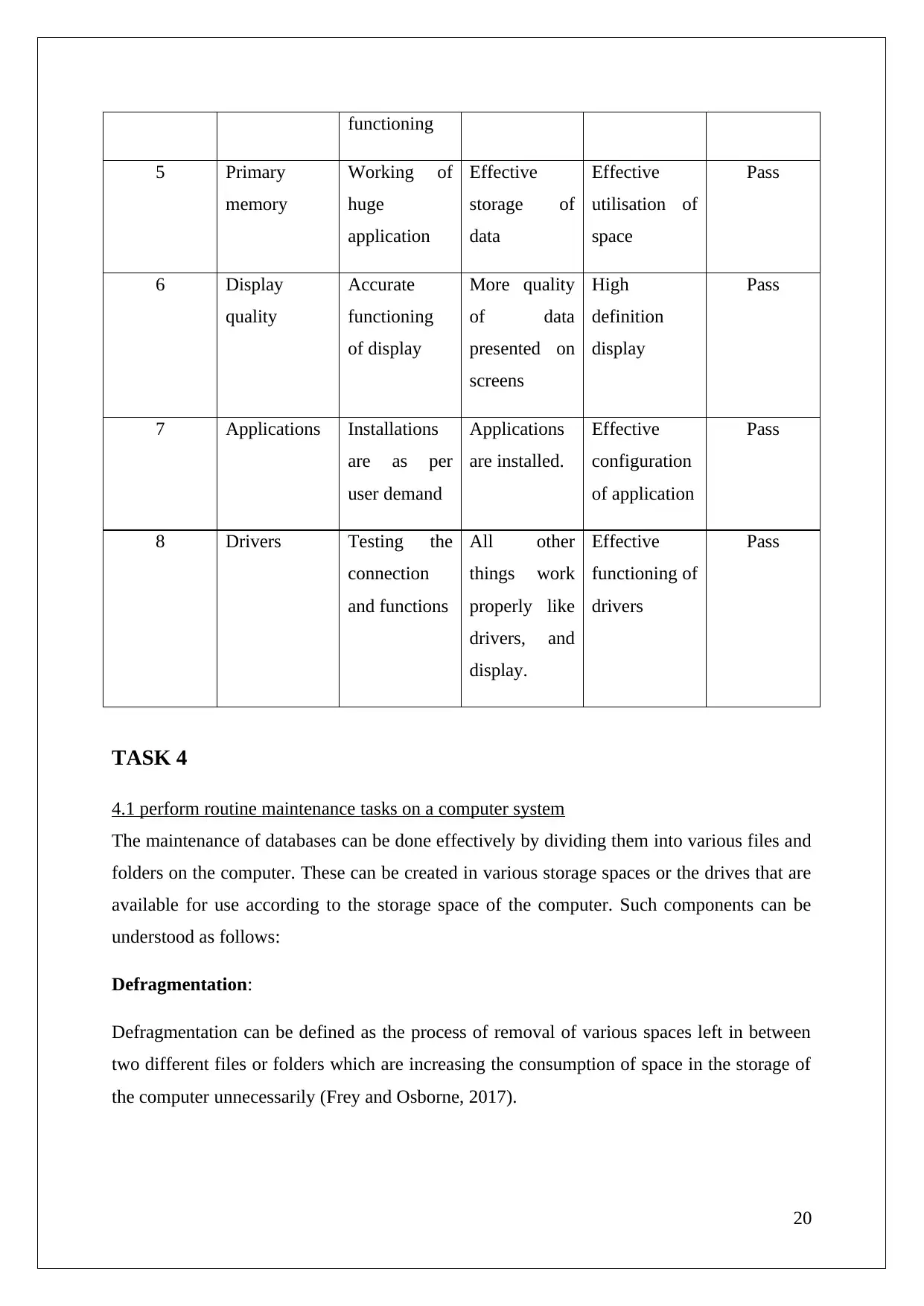
functioning
5 Primary
memory
Working of
huge
application
Effective
storage of
data
Effective
utilisation of
space
Pass
6 Display
quality
Accurate
functioning
of display
More quality
of data
presented on
screens
High
definition
display
Pass
7 Applications Installations
are as per
user demand
Applications
are installed.
Effective
configuration
of application
Pass
8 Drivers Testing the
connection
and functions
All other
things work
properly like
drivers, and
display.
Effective
functioning of
drivers
Pass
TASK 4
4.1 perform routine maintenance tasks on a computer system
The maintenance of databases can be done effectively by dividing them into various files and
folders on the computer. These can be created in various storage spaces or the drives that are
available for use according to the storage space of the computer. Such components can be
understood as follows:
Defragmentation:
Defragmentation can be defined as the process of removal of various spaces left in between
two different files or folders which are increasing the consumption of space in the storage of
the computer unnecessarily (Frey and Osborne, 2017).
20
5 Primary
memory
Working of
huge
application
Effective
storage of
data
Effective
utilisation of
space
Pass
6 Display
quality
Accurate
functioning
of display
More quality
of data
presented on
screens
High
definition
display
Pass
7 Applications Installations
are as per
user demand
Applications
are installed.
Effective
configuration
of application
Pass
8 Drivers Testing the
connection
and functions
All other
things work
properly like
drivers, and
display.
Effective
functioning of
drivers
Pass
TASK 4
4.1 perform routine maintenance tasks on a computer system
The maintenance of databases can be done effectively by dividing them into various files and
folders on the computer. These can be created in various storage spaces or the drives that are
available for use according to the storage space of the computer. Such components can be
understood as follows:
Defragmentation:
Defragmentation can be defined as the process of removal of various spaces left in between
two different files or folders which are increasing the consumption of space in the storage of
the computer unnecessarily (Frey and Osborne, 2017).
20
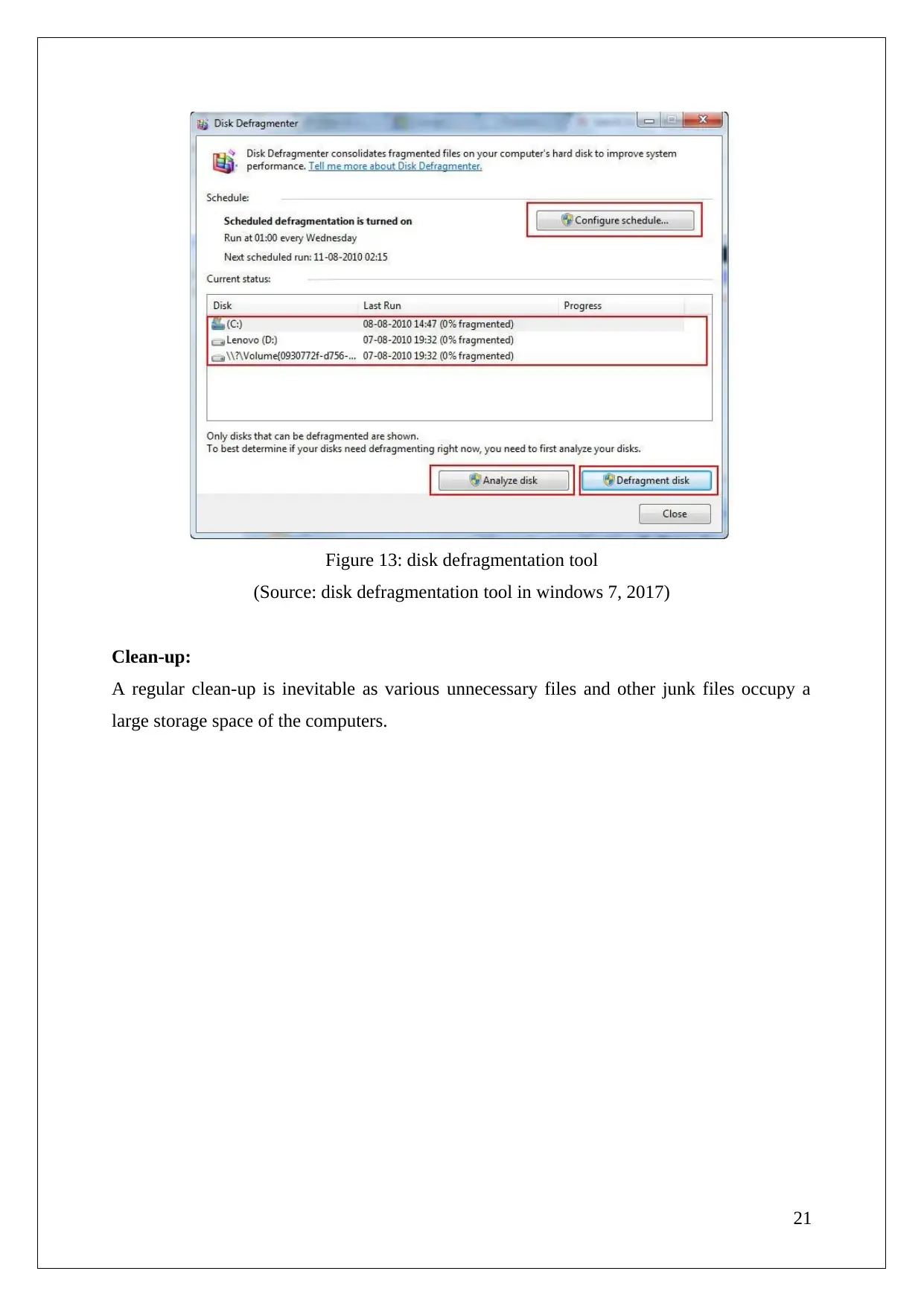
Figure 13: disk defragmentation tool
(Source: disk defragmentation tool in windows 7, 2017)
Clean-up:
A regular clean-up is inevitable as various unnecessary files and other junk files occupy a
large storage space of the computers.
21
(Source: disk defragmentation tool in windows 7, 2017)
Clean-up:
A regular clean-up is inevitable as various unnecessary files and other junk files occupy a
large storage space of the computers.
21
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
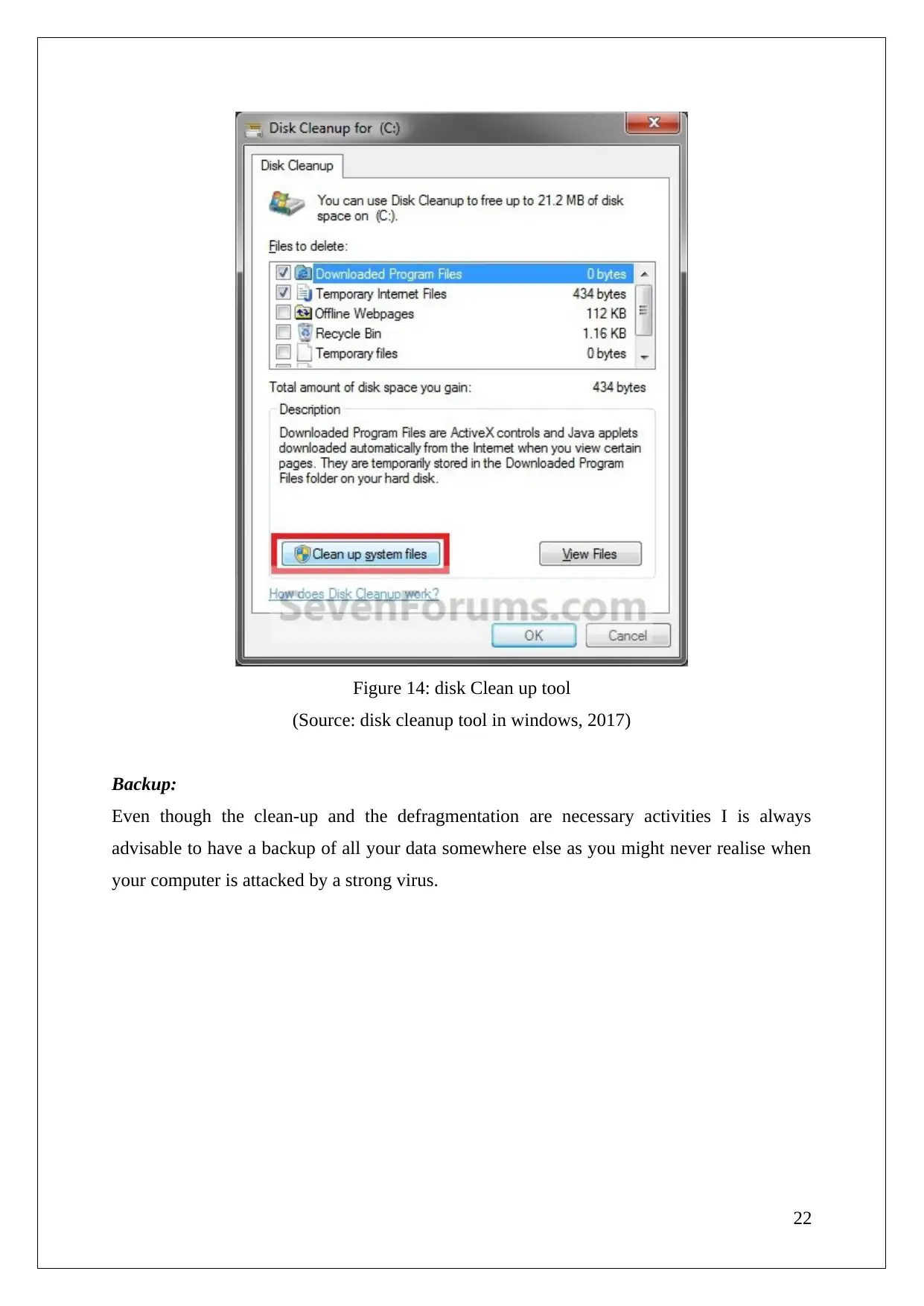
Figure 14: disk Clean up tool
(Source: disk cleanup tool in windows, 2017)
Backup:
Even though the clean-up and the defragmentation are necessary activities I is always
advisable to have a backup of all your data somewhere else as you might never realise when
your computer is attacked by a strong virus.
22
(Source: disk cleanup tool in windows, 2017)
Backup:
Even though the clean-up and the defragmentation are necessary activities I is always
advisable to have a backup of all your data somewhere else as you might never realise when
your computer is attacked by a strong virus.
22
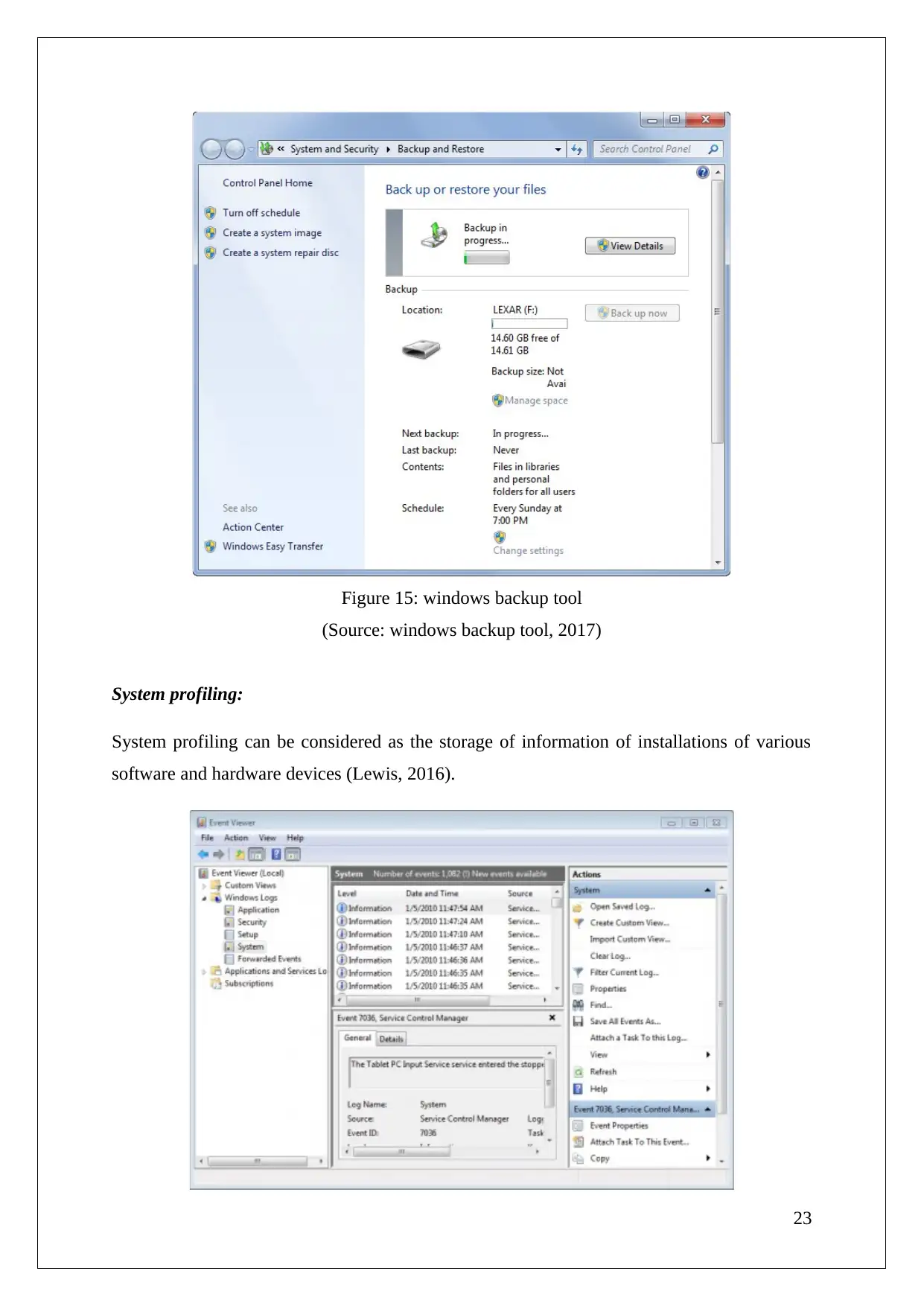
Figure 15: windows backup tool
(Source: windows backup tool, 2017)
System profiling:
System profiling can be considered as the storage of information of installations of various
software and hardware devices (Lewis, 2016).
23
(Source: windows backup tool, 2017)
System profiling:
System profiling can be considered as the storage of information of installations of various
software and hardware devices (Lewis, 2016).
23
Figure 16: event viewer in windows
(Source: event viewer in windows, 2017)
Spyware/malware removal:
In order to protect the computer from the unknown virus attacks during any given time a
regular spyware or malware from the computer.
Figure 17: Windows defender
(Source: windows defender, 2017)
Compression:
The files that are rarely used or not used but are useful to be stored must be compressed in the
system which will save the space.
24
(Source: event viewer in windows, 2017)
Spyware/malware removal:
In order to protect the computer from the unknown virus attacks during any given time a
regular spyware or malware from the computer.
Figure 17: Windows defender
(Source: windows defender, 2017)
Compression:
The files that are rarely used or not used but are useful to be stored must be compressed in the
system which will save the space.
24
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Figure 18: winrar compression tool
(Source: winrar, 2017)
Clean hardware:
The effective cleaning and maintenance of the hardware devices like printers and monitor
along with the keyboard etc are also necessary.
Even though such cleaning is necessary it must be kept in mind that the dust that gets settled
on these devices has to be cleaned and for this purpose the use of water or soap may not be
advisable as these devices may get harmed with the use of water (Frey and Osborne, 2017.).
4.2 upgrade the hardware and software on a computer system.
Now even though the machine or the computer is fixed and is working efficiently does not
mean that the work is over here. It is also important to keep analyzing the functioning of the
computer and as and when required the hardware along with the software parts must be
replaced. This is known as upgradation.
The computer systems must be upgraded as and when required and some of the important
upgrades can be noticed as follows:
Upgrade software
Virus definition:
25
(Source: winrar, 2017)
Clean hardware:
The effective cleaning and maintenance of the hardware devices like printers and monitor
along with the keyboard etc are also necessary.
Even though such cleaning is necessary it must be kept in mind that the dust that gets settled
on these devices has to be cleaned and for this purpose the use of water or soap may not be
advisable as these devices may get harmed with the use of water (Frey and Osborne, 2017.).
4.2 upgrade the hardware and software on a computer system.
Now even though the machine or the computer is fixed and is working efficiently does not
mean that the work is over here. It is also important to keep analyzing the functioning of the
computer and as and when required the hardware along with the software parts must be
replaced. This is known as upgradation.
The computer systems must be upgraded as and when required and some of the important
upgrades can be noticed as follows:
Upgrade software
Virus definition:
25

In order to get adequate protection from the unknown components on the internet it is very
important to protect your device from the virus in the system for which the anti-virus
software is used by the firms.
Patches:
As and when the Microsoft updates come the firm must keep their systems upgraded as well.
These types of upgrades generally come as the firm launches new products or features in the
same software which is why it is updated (Siewiorek and Swarz, 2017).
Operating system upgrade:
Even though the Windows software is the oldest it is one of the best in the markets till date.
This is because of the constant upgrades in the operating system of the launched versions of
windows as well.
The current latest version of windows is windows 10 which have some of the best features
and functionality.
Hardware upgrade
Add new devices:
In order to keep up with the standards of the production the organization must keep up with
the advent of new technological devices. Since the invention of the computers, there has been
a dozen of such inventions with can help in improving the productivity of the firm. Various
such hardware devices can be like printers which have now with the advent of technology
also been able to print in three dimensions, i.e. the 3D printers, the scanners, the speakers, the
camera. Most of these features are now-a-days available on the laptop devices itself or are
connected with the computers during their production itself (Curzi et.al. 2016).
Install or configure new drivers:
The various drivers of the computer system which help in the functioning of the hard disk,
the operating system as well as the other network components can be organized and latest
technological drivers can be installed which help in better functioning.
26
important to protect your device from the virus in the system for which the anti-virus
software is used by the firms.
Patches:
As and when the Microsoft updates come the firm must keep their systems upgraded as well.
These types of upgrades generally come as the firm launches new products or features in the
same software which is why it is updated (Siewiorek and Swarz, 2017).
Operating system upgrade:
Even though the Windows software is the oldest it is one of the best in the markets till date.
This is because of the constant upgrades in the operating system of the launched versions of
windows as well.
The current latest version of windows is windows 10 which have some of the best features
and functionality.
Hardware upgrade
Add new devices:
In order to keep up with the standards of the production the organization must keep up with
the advent of new technological devices. Since the invention of the computers, there has been
a dozen of such inventions with can help in improving the productivity of the firm. Various
such hardware devices can be like printers which have now with the advent of technology
also been able to print in three dimensions, i.e. the 3D printers, the scanners, the speakers, the
camera. Most of these features are now-a-days available on the laptop devices itself or are
connected with the computers during their production itself (Curzi et.al. 2016).
Install or configure new drivers:
The various drivers of the computer system which help in the functioning of the hard disk,
the operating system as well as the other network components can be organized and latest
technological drivers can be installed which help in better functioning.
26

CONCLUSION
In the given report we have focused on the development of the computer system in the market
along with its increasing utility every day. The brief discussion on the importance and
maintenance of the parts of a computer is also done in the report. There can be different types
of computers based on their usage like the supercomputers which are used for the mining of
the bitcoins and are specially designed to solve such complex mathematical problems of the
bitcoin mining procedure. Also, it is important to keep updating the hardware of the
computers with the advent of new technology and the advancement of technology in the
economy. With the invention of computers various processes have surely been made easier
for the organizations in terms of their production.
Even after such boons of computer systems, there may be certain disadvantages as well
because of which a regular upgrade is necessary and maintenance of the computers.
27
In the given report we have focused on the development of the computer system in the market
along with its increasing utility every day. The brief discussion on the importance and
maintenance of the parts of a computer is also done in the report. There can be different types
of computers based on their usage like the supercomputers which are used for the mining of
the bitcoins and are specially designed to solve such complex mathematical problems of the
bitcoin mining procedure. Also, it is important to keep updating the hardware of the
computers with the advent of new technology and the advancement of technology in the
economy. With the invention of computers various processes have surely been made easier
for the organizations in terms of their production.
Even after such boons of computer systems, there may be certain disadvantages as well
because of which a regular upgrade is necessary and maintenance of the computers.
27
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Books and journals
Balasubramaniam, C., Kannan, R., Revashetti, S.B., Sampath, S. and Katchapalayam,
B., McAfee LLC, 2014. System, method and computer program product for
performing one or more maintenance tasks on a remotely located computer connected
to a server computer via a data network. U.S. Patent 8,706,576.
Buede, D.M. and Miller, W.D., 2016. The engineering design of systems: models and
methods. John Wiley & Sons.
Card, S.K., 2017. The psychology of human-computer interaction. CRC Press.
Chapman, W., 2018. Engineering modeling and design. Routledge.
Clemm, L.A., Chandramouli, Y., Krishnamurthy, S. and Srinivasa, S., Cisco
Technology Inc, 2016. Network embedded framework for distributed network
analytics. U.S. Patent Application 14/550,885.
Curzi, F. and Ryan, M., International Business Machines Corp, 2016. Effective
migration and upgrade of virtual machines in cloud environments. U.S. Patent
9,459,856.
Feitelson, D.G., 2015. Workload modeling for computer systems performance
evaluation. Cambridge University Press.
Frey, C.B. and Osborne, M.A., 2017. The future of employment: how susceptible are
jobs to computerisation?. Technological Forecasting and Social Change, 114, pp.254-
280.
Groover, M.P., 2016. Automation, production systems, and computer-integrated
manufacturing. Pearson Education India.
Hau, C.C. ed., 2015. Handbook of pattern recognition and computer vision. World
Scientific.
Herman, D.L. and Oftedal, M.J., DIGITALFISH Inc, 2017. Techniques and
workflows for computer graphics animation system. U.S. Patent 9,805,491.
Hilburn, J.C., Smith, J.J., Stanley, M.S. and Windell, D.T., International Business
Machines Corp, 2018. Determining suitability for disconnection from an electrical
outlet based on status of power supplies of a hardware device. U.S. Patent 9,945,893.
Kavanagh, M.J. and Johnson, R.D. eds., 2017. Human resource information systems:
Basics, applications, and future directions. Sage Publications.
28
Books and journals
Balasubramaniam, C., Kannan, R., Revashetti, S.B., Sampath, S. and Katchapalayam,
B., McAfee LLC, 2014. System, method and computer program product for
performing one or more maintenance tasks on a remotely located computer connected
to a server computer via a data network. U.S. Patent 8,706,576.
Buede, D.M. and Miller, W.D., 2016. The engineering design of systems: models and
methods. John Wiley & Sons.
Card, S.K., 2017. The psychology of human-computer interaction. CRC Press.
Chapman, W., 2018. Engineering modeling and design. Routledge.
Clemm, L.A., Chandramouli, Y., Krishnamurthy, S. and Srinivasa, S., Cisco
Technology Inc, 2016. Network embedded framework for distributed network
analytics. U.S. Patent Application 14/550,885.
Curzi, F. and Ryan, M., International Business Machines Corp, 2016. Effective
migration and upgrade of virtual machines in cloud environments. U.S. Patent
9,459,856.
Feitelson, D.G., 2015. Workload modeling for computer systems performance
evaluation. Cambridge University Press.
Frey, C.B. and Osborne, M.A., 2017. The future of employment: how susceptible are
jobs to computerisation?. Technological Forecasting and Social Change, 114, pp.254-
280.
Groover, M.P., 2016. Automation, production systems, and computer-integrated
manufacturing. Pearson Education India.
Hau, C.C. ed., 2015. Handbook of pattern recognition and computer vision. World
Scientific.
Herman, D.L. and Oftedal, M.J., DIGITALFISH Inc, 2017. Techniques and
workflows for computer graphics animation system. U.S. Patent 9,805,491.
Hilburn, J.C., Smith, J.J., Stanley, M.S. and Windell, D.T., International Business
Machines Corp, 2018. Determining suitability for disconnection from an electrical
outlet based on status of power supplies of a hardware device. U.S. Patent 9,945,893.
Kavanagh, M.J. and Johnson, R.D. eds., 2017. Human resource information systems:
Basics, applications, and future directions. Sage Publications.
28

Keohane, S.M., McBrearty, G.F., Mullen, S.P., Murillo, J.C. and Shieh, J.M.H.,
International Business Machines Corp, 2015. Techniques for presenting password
feedback to a computer system user. U.S. Patent 9,122,867.
Nalluri, H.C., Navale, A. and Ramadoss, M., Intel Corp, 2017. Hardware assist for
privilege access violation checks. U.S. Patent 9,633,230.
Paczkowski, L.W., Parsel, W.M., Persson, C.J. and Schlesener, M.C., Sprint
Communications Co LP, 2017. Trusted Security Zone Enhanced with Trusted
Hardware Drivers. U.S. Patent 9,613,208.
Ricci, R., Wong, G., Stoller, L., Webb, K., Duerig, J., Downie, K. and Hibler, M.,
2015. Apt: A platform for repeatable research in computer science. ACM SIGOPS
Operating Systems Review, 49(1), pp.100-107.
Sibert, W.O., Intertrust Technologies Corp, 2017. Secure processing unit systems and
methods. U.S. Patent 9,536,111.
Siewiorek, D. and Swarz, R., 2017. Reliable Computer Systems: Design and
Evaluatuion. Digital Press.
Silberschatz, A., Galvin, P.B. and Gagne, G., 2014. Operating system concepts
essentials. John Wiley & Sons, Inc..
Silberschatz, A., Galvin, P.B. and Gagne, G., 2014. Operating system concepts
essentials. John Wiley & Sons, Inc..
Wyglinski, A.M., Orofino, D.P., Ettus, M.N. and Rondeau, T.W., 2016.
Revolutionizing software defined radio: case studies in hardware, software, and
education. IEEE Communications Magazine, 54(1), pp.68-75.
29
International Business Machines Corp, 2015. Techniques for presenting password
feedback to a computer system user. U.S. Patent 9,122,867.
Nalluri, H.C., Navale, A. and Ramadoss, M., Intel Corp, 2017. Hardware assist for
privilege access violation checks. U.S. Patent 9,633,230.
Paczkowski, L.W., Parsel, W.M., Persson, C.J. and Schlesener, M.C., Sprint
Communications Co LP, 2017. Trusted Security Zone Enhanced with Trusted
Hardware Drivers. U.S. Patent 9,613,208.
Ricci, R., Wong, G., Stoller, L., Webb, K., Duerig, J., Downie, K. and Hibler, M.,
2015. Apt: A platform for repeatable research in computer science. ACM SIGOPS
Operating Systems Review, 49(1), pp.100-107.
Sibert, W.O., Intertrust Technologies Corp, 2017. Secure processing unit systems and
methods. U.S. Patent 9,536,111.
Siewiorek, D. and Swarz, R., 2017. Reliable Computer Systems: Design and
Evaluatuion. Digital Press.
Silberschatz, A., Galvin, P.B. and Gagne, G., 2014. Operating system concepts
essentials. John Wiley & Sons, Inc..
Silberschatz, A., Galvin, P.B. and Gagne, G., 2014. Operating system concepts
essentials. John Wiley & Sons, Inc..
Wyglinski, A.M., Orofino, D.P., Ettus, M.N. and Rondeau, T.W., 2016.
Revolutionizing software defined radio: case studies in hardware, software, and
education. IEEE Communications Magazine, 54(1), pp.68-75.
29
1 out of 33
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





