Computer Systems Security Report: Risks, Applications, and Solutions
VerifiedAdded on 2021/01/01
|24
|6181
|477
Report
AI Summary
This report delves into the critical domain of computer systems security, examining various facets to ensure data protection and system integrity. The introduction underscores the significance of computer security in today's rapidly evolving technological landscape, emphasizing the challenges faced by organizations in managing complex operations. The literature review explores existing research on mobile security, risk assessment, and the role of cryptography. The core of the report focuses on identifying common security risks like hackers, unauthorized access, and malware, while also discussing the importance of risk analysis and mitigation strategies. It examines cryptography's application in securing data and proposes practical solutions for normal users, including app suggestions and risk charts. The report provides an overview of security threats and solutions, with a focus on smartphones and tablets. The report also addresses legal, social, and ethical considerations relevant to computer security, concluding with a summary of the key findings and recommendations. The report offers insights into the importance of computer security for individuals and organizations alike.

Computer Systems Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
ABSTRACT.....................................................................................................................................3
INTRODUCTION...........................................................................................................................4
LITERATURE REVIEW................................................................................................................5
TASK...............................................................................................................................................6
Impact on the Normal Man ........................................................................................................8
Questioners..................................................................................................................................9
Importance of Risk analysis in the primary data-.....................................................................12
Identifying the different application support to cryptography and encryption with primary
data- ..........................................................................................................................................14
Propose An App for Normal Man /Screenshot of Applications...............................................15
Create Risk chart with probability and mitigation plan with the help of primary data.............18
Legal, Social and Ethical issues:...............................................................................................23
CONCLUSION..............................................................................................................................23
REFERENCES..............................................................................................................................24
ABSTRACT.....................................................................................................................................3
INTRODUCTION...........................................................................................................................4
LITERATURE REVIEW................................................................................................................5
TASK...............................................................................................................................................6
Impact on the Normal Man ........................................................................................................8
Questioners..................................................................................................................................9
Importance of Risk analysis in the primary data-.....................................................................12
Identifying the different application support to cryptography and encryption with primary
data- ..........................................................................................................................................14
Propose An App for Normal Man /Screenshot of Applications...............................................15
Create Risk chart with probability and mitigation plan with the help of primary data.............18
Legal, Social and Ethical issues:...............................................................................................23
CONCLUSION..............................................................................................................................23
REFERENCES..............................................................................................................................24

ABSTRACT
Computer system security is a process that help for providing the safety and security in the smart
phones, tablets and other devices. Information technology is a leading field to expand the
business all over the world. It is beneficial for user to check the security options to manage the
entire processing and functionality of smartphone. Computer security is the most challenging
part of organization to handle the complication in the business operations and functions.
Computer system used the different techniques such as wireless network, smart phones, Wi-Fi
etc. cryptography techniques are beneficial for used the encryption and decryption algorithm of
providing the safety and privacy in the computer system.
Computer system security is a process that help for providing the safety and security in the smart
phones, tablets and other devices. Information technology is a leading field to expand the
business all over the world. It is beneficial for user to check the security options to manage the
entire processing and functionality of smartphone. Computer security is the most challenging
part of organization to handle the complication in the business operations and functions.
Computer system used the different techniques such as wireless network, smart phones, Wi-Fi
etc. cryptography techniques are beneficial for used the encryption and decryption algorithm of
providing the safety and privacy in the computer system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Computer system security is the part of protection and safety for hardware system to the
thefts and hackers. It is required for manage the services because it can manage the entire
functionality of the computer system. Information technology is the fastest growing field to
provide the best services to the customers in marketplace. Computer security is the most
challenging part of organization to handle the complication in the business operations and
functions. Computer system used the different techniques such as wireless network, smart
phones, Wi-Fi etc. these devices are basically used for the purpose of communication from one
node to another (Conti and et.al., 2018). At the time of sharing, the hacker can attack the
computer system and can be damage the information or data that's why, it is necessary for
organization always maintain their security aspects in proper manner. In this report, It will
discuss about the different conceptual security risk that could recognized at the time of data
processing. There are different type of risk generated in the information technology environment
therefore, it is necessary to maintain their services in proper manner.
Cryptography is the technique which used for the purpose of network security therefore,
it can decode the data from one node to another by using this technique where the hacker can not
easily damage the data in the computers. There are different approaches describe in the report
and also discuss its applications. Sometimes, threats and unwanted software impacts on the
business operations and functions that's why, it is important to manage their security aspets in the
computer system. (Ross, McEvilley and Oren, 2018). This report will discuss about the smart
phones and tablet which is suitable for the normal person in the terms of security aspects. In this
way, it can easily understand the need and requirement of technology in our day to day life.
Smartphones is a type of device that is applicable for data transmission and this device used
some terminology and technologies, issues etc. Smartphones are most preferable as compare to
tablets because smartphone provide the calling facilities and services to the customer (Thota and
et.al., 2018). Most of the organization provide their own platform to share the information to the
customer. In this way, customer can easily access the information by using computer system
that's why, it is necessary for protecting the hardware system because unnecessary threats and
virus affects the entire computer system. There are some threats generated which discuss in this
report such as malware, viruses, phishing, spam etc. These are the important threats that affecting
the entire computer system. It makes sure that devices used in the computer system must used
Computer system security is the part of protection and safety for hardware system to the
thefts and hackers. It is required for manage the services because it can manage the entire
functionality of the computer system. Information technology is the fastest growing field to
provide the best services to the customers in marketplace. Computer security is the most
challenging part of organization to handle the complication in the business operations and
functions. Computer system used the different techniques such as wireless network, smart
phones, Wi-Fi etc. these devices are basically used for the purpose of communication from one
node to another (Conti and et.al., 2018). At the time of sharing, the hacker can attack the
computer system and can be damage the information or data that's why, it is necessary for
organization always maintain their security aspects in proper manner. In this report, It will
discuss about the different conceptual security risk that could recognized at the time of data
processing. There are different type of risk generated in the information technology environment
therefore, it is necessary to maintain their services in proper manner.
Cryptography is the technique which used for the purpose of network security therefore,
it can decode the data from one node to another by using this technique where the hacker can not
easily damage the data in the computers. There are different approaches describe in the report
and also discuss its applications. Sometimes, threats and unwanted software impacts on the
business operations and functions that's why, it is important to manage their security aspets in the
computer system. (Ross, McEvilley and Oren, 2018). This report will discuss about the smart
phones and tablet which is suitable for the normal person in the terms of security aspects. In this
way, it can easily understand the need and requirement of technology in our day to day life.
Smartphones is a type of device that is applicable for data transmission and this device used
some terminology and technologies, issues etc. Smartphones are most preferable as compare to
tablets because smartphone provide the calling facilities and services to the customer (Thota and
et.al., 2018). Most of the organization provide their own platform to share the information to the
customer. In this way, customer can easily access the information by using computer system
that's why, it is necessary for protecting the hardware system because unnecessary threats and
virus affects the entire computer system. There are some threats generated which discuss in this
report such as malware, viruses, phishing, spam etc. These are the important threats that affecting
the entire computer system. It makes sure that devices used in the computer system must used
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the techniques like encryption, TCP and UDP, Decryption and IP etc (White, Fisch and Pooch,
2017). These are essential technology for protecting data or hardware system against the theft
and hackers. Encryption and decryption are the main component of computer security because
many organization used this technique to provide the safety and security in their hardware
systems(Conti and et.al., 2018). Computer security is the main part of organization that allows
securing the business operations and also protected the information and details on the specific
computer system that's why, security is the important aspects to manage and control the entire
processing of system. Security is help for removing all the threats in the system and keep protect
the hardware system. This type of security is useful for provide the integrity, availability and
confidentiality for the component in the entire system.
LITERATURE REVIEW
According to the author, A New smart phone or tablet security is the main aspects of each
and every people. They always try to secure their data and information because there are many
theft damage the functionality of smart phone and can be lost the data. First of all, person can
understand the functionality and operations of smart phones and used the different application to
protect their data in effective ways. These are the security features that applied in the smart
phones to protect their data and information effectively and efficiently (Abdo and et.al., 2018).
As per author, Modern Technology is to be considered as the main part of business that
applicable in the tablets and new phones to provide the better services to user those who used the
smart phones. The information accessibility is easy for each and every people that store the
mobile data in the gadget collection that's why, it protects all information in proper manner.
According to author, All the service that used the specific authentication security to
protect their transaction and data. It is easier process to check and enable the security features.
Once enabled even some people easily access the password.
According to author, Computer security terminology, technologies and issues that
applicable in the smart phones. It is required for each and every hardware system to manage the
entire functionality of mobile phones. Computer security is the main component in the
smartphones and other technology because it provides the full of security and safety in the entire
functionality and operations. Sometimes, Many people install the various application that help
for providing the best quality of services related the security aspects (Liu and et.al., 2018). It can
be used the different technology applicable that only provide the security in their hardware and
2017). These are essential technology for protecting data or hardware system against the theft
and hackers. Encryption and decryption are the main component of computer security because
many organization used this technique to provide the safety and security in their hardware
systems(Conti and et.al., 2018). Computer security is the main part of organization that allows
securing the business operations and also protected the information and details on the specific
computer system that's why, security is the important aspects to manage and control the entire
processing of system. Security is help for removing all the threats in the system and keep protect
the hardware system. This type of security is useful for provide the integrity, availability and
confidentiality for the component in the entire system.
LITERATURE REVIEW
According to the author, A New smart phone or tablet security is the main aspects of each
and every people. They always try to secure their data and information because there are many
theft damage the functionality of smart phone and can be lost the data. First of all, person can
understand the functionality and operations of smart phones and used the different application to
protect their data in effective ways. These are the security features that applied in the smart
phones to protect their data and information effectively and efficiently (Abdo and et.al., 2018).
As per author, Modern Technology is to be considered as the main part of business that
applicable in the tablets and new phones to provide the better services to user those who used the
smart phones. The information accessibility is easy for each and every people that store the
mobile data in the gadget collection that's why, it protects all information in proper manner.
According to author, All the service that used the specific authentication security to
protect their transaction and data. It is easier process to check and enable the security features.
Once enabled even some people easily access the password.
According to author, Computer security terminology, technologies and issues that
applicable in the smart phones. It is required for each and every hardware system to manage the
entire functionality of mobile phones. Computer security is the main component in the
smartphones and other technology because it provides the full of security and safety in the entire
functionality and operations. Sometimes, Many people install the various application that help
for providing the best quality of services related the security aspects (Liu and et.al., 2018). It can
be used the different technology applicable that only provide the security in their hardware and

software system. This technology is running automatically remove all the unwanted software and
threats in the computer system. It is necessary for people to secure their computer system
because in most of time, the important and personal data store in the system that used for manage
in the proper manner.
TASK
Common Risk on the overall security system of computers-
There are different types of common risk generated in the computer system effectively and
efficiently.
Hackers- Hacker is basically person those who tries to crack the password of computer
system and also exploits the hardware for particular reasons. It is terminology that used in
the computer security and damage the personal information and company data. Hacker
will use the different software that access their entire processing in quickly. It is the most
common technique to lost the data anywhere.
Unauthorized access- unauthorized access is the happen when someone can use the
server to access the details of particular website. In this way, it is also accessed the
sensitive data of another person. An organization is store the details of customers in their
official database (Papernot and et.al., 2018). In this way, An authorized person easily
access the personal information of client such as transaction details, account number, card
details etc. It affects the entire processing of organization and many times, the firms face
loss and challenges issues.
Threats- It is the most common aspects of computer security that generated at any time
in the system. It mainly causes the serious damage in the hard ware that impact on the
overall operations and functions. Sometimes, threats may be affect or not because it
depends on the quality and accessibility. This is the important for people to always
protect their smartphone, tablet and PC to secure through threats. It is based on the action
and event that might happen in the computer system and it is also comprises the security
(Thota and et.al., 2018).
Vulnerability- It is usually based on the weakness that help to exploit by the threats in
the entire system such as attackers, This is unauthorized persona that perform in the
different action in the other devices such as computer system, Smartphones and tablets
etc. The attacker will use the one tool or technique to connect with the system weakness
threats in the computer system. It is necessary for people to secure their computer system
because in most of time, the important and personal data store in the system that used for manage
in the proper manner.
TASK
Common Risk on the overall security system of computers-
There are different types of common risk generated in the computer system effectively and
efficiently.
Hackers- Hacker is basically person those who tries to crack the password of computer
system and also exploits the hardware for particular reasons. It is terminology that used in
the computer security and damage the personal information and company data. Hacker
will use the different software that access their entire processing in quickly. It is the most
common technique to lost the data anywhere.
Unauthorized access- unauthorized access is the happen when someone can use the
server to access the details of particular website. In this way, it is also accessed the
sensitive data of another person. An organization is store the details of customers in their
official database (Papernot and et.al., 2018). In this way, An authorized person easily
access the personal information of client such as transaction details, account number, card
details etc. It affects the entire processing of organization and many times, the firms face
loss and challenges issues.
Threats- It is the most common aspects of computer security that generated at any time
in the system. It mainly causes the serious damage in the hard ware that impact on the
overall operations and functions. Sometimes, threats may be affect or not because it
depends on the quality and accessibility. This is the important for people to always
protect their smartphone, tablet and PC to secure through threats. It is based on the action
and event that might happen in the computer system and it is also comprises the security
(Thota and et.al., 2018).
Vulnerability- It is usually based on the weakness that help to exploit by the threats in
the entire system such as attackers, This is unauthorized persona that perform in the
different action in the other devices such as computer system, Smartphones and tablets
etc. The attacker will use the one tool or technique to connect with the system weakness
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

and damage their processing system (Roman, Lopez and Mambo, 2018). Security risk is
the classified on the basis of vulnerability because this concept is applicable in the system
that generate more risk on system. In this way, it directly connects with the weakness and
damage the entire process.
Attack- It is the assault on the security system where the person can be delivered the
unwanted software and text message to the accounts. In this way, the person can open the
software that impact on the computer system. This is the way to attack the hardware and
other PC, smart phones and tablet etc. It is required for every user to check in properly.
Afterwards, install the app in the smartphone because there are various types of fake
application available in the marketplace. The only reason to affect the device of hardware
to the people. In this way, the attacker access all the personal information of users in
quick manner.
Antivirus and Anti-malware- This is the software that help for providing the security
and operates the operating system of devices for preventing through the malicious
software. This is the important for user to always install the antivirus in the smart phones
because it can provide the security features and aspects to automatically control and
remove the unwanted software in the systems (Ross, McEvilley and Oren, 2018).
Social engineering- It is based on the technique where the hacker can access and use the
stolen data of another person for the purpose of psychological manipulations. It is the
based on the large number of malicious activities that happen by the human interactions.
Sometimes, the people use the psychological manipulation and trick makes mistake or
giving away the personal and sensitive information. The attack can happen into more
steps that investigate to gather all necessary information therefore, Attacker moves to
gain the trust of user and provide the stimulation action that break all the security aspects
and practices like revealing and accessing all information and granting to the critical
resources.
Virus- It is a type of malicious software that enter in the smartphone, tablets and
Computer system with the help of installation, unwanted application etc. These are
different sources that help for enter in the system. In this way, The entire system of
smartphone is slower. It also impacts on the overall efficiency and data processing. The
main purpose of malicious software to damage the smart phone operations and slow
the classified on the basis of vulnerability because this concept is applicable in the system
that generate more risk on system. In this way, it directly connects with the weakness and
damage the entire process.
Attack- It is the assault on the security system where the person can be delivered the
unwanted software and text message to the accounts. In this way, the person can open the
software that impact on the computer system. This is the way to attack the hardware and
other PC, smart phones and tablet etc. It is required for every user to check in properly.
Afterwards, install the app in the smartphone because there are various types of fake
application available in the marketplace. The only reason to affect the device of hardware
to the people. In this way, the attacker access all the personal information of users in
quick manner.
Antivirus and Anti-malware- This is the software that help for providing the security
and operates the operating system of devices for preventing through the malicious
software. This is the important for user to always install the antivirus in the smart phones
because it can provide the security features and aspects to automatically control and
remove the unwanted software in the systems (Ross, McEvilley and Oren, 2018).
Social engineering- It is based on the technique where the hacker can access and use the
stolen data of another person for the purpose of psychological manipulations. It is the
based on the large number of malicious activities that happen by the human interactions.
Sometimes, the people use the psychological manipulation and trick makes mistake or
giving away the personal and sensitive information. The attack can happen into more
steps that investigate to gather all necessary information therefore, Attacker moves to
gain the trust of user and provide the stimulation action that break all the security aspects
and practices like revealing and accessing all information and granting to the critical
resources.
Virus- It is a type of malicious software that enter in the smartphone, tablets and
Computer system with the help of installation, unwanted application etc. These are
different sources that help for enter in the system. In this way, The entire system of
smartphone is slower. It also impacts on the overall efficiency and data processing. The
main purpose of malicious software to damage the smart phone operations and slow
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

down. It is required for user to use the security features that help for protecting the whole
system in effective manner (Thota and et.al., 2018).
Impact on the Normal Man
Normal Man cannot operate their smart phones and computer system proper manner
because these security issues are affecting the entire processing of system. In this way, attacker
easily hack their entire data and information related the transaction and account numbers etc. In
this Normal Man can use the different methods for securing their smartphone and table by using
the security features in effective manner.
Put a strong passcode- This is the initial and easy step to protect their phone through the
viruses and threats. In new phone, there are various types of features available in the phone that
set a passcode to lock the phone. It is the security option that applicable the different options
such as fingerprint, image recognition, Number-code etc. this features is added in the phone to
protect and secure in effective manner (Alali and et.al., 2018). Many new smartphone and tablet
offers different lock pattern and without the figure print, it cannot be possible to unlock the cell
phones.
Lock your app- Many organizations always remember to the security issue so that they
launch a smart phones which offers different features. In this way, it can be individually lock
installed application with the help of passcode and scan fingerprint. This features can extra
security layer to protect their data and important content especially when you hold the phone and
other person to show something. It also useful for person to install the features and applied the
smartphones such as App-lock etc.
Use two factor authentication- Many people can ignore the security features that face
many problems and hassle at every time that's why, it is required for user to use the two factor
authentication that help for provide the security with the help of authenticate with the passcode
(Conti and et.al., 2018). It can generate the unique authenticated code for particular application
such as One time password etc. this type of security feature offered by different services such as
Facebook, twitter, Instagram, google, Amazon, Snap-chat, PayPal etc.
Install security applications- A smart phone is based on the susceptible to data theft in
the computer system. It is important to get smart phones to install the security application that
manage the entire processing of system (Lee and et.al., 2018). There are various type of security
application available in the organization such as McAfee, Trend Micro, Avast, Norton etc. This
system in effective manner (Thota and et.al., 2018).
Impact on the Normal Man
Normal Man cannot operate their smart phones and computer system proper manner
because these security issues are affecting the entire processing of system. In this way, attacker
easily hack their entire data and information related the transaction and account numbers etc. In
this Normal Man can use the different methods for securing their smartphone and table by using
the security features in effective manner.
Put a strong passcode- This is the initial and easy step to protect their phone through the
viruses and threats. In new phone, there are various types of features available in the phone that
set a passcode to lock the phone. It is the security option that applicable the different options
such as fingerprint, image recognition, Number-code etc. this features is added in the phone to
protect and secure in effective manner (Alali and et.al., 2018). Many new smartphone and tablet
offers different lock pattern and without the figure print, it cannot be possible to unlock the cell
phones.
Lock your app- Many organizations always remember to the security issue so that they
launch a smart phones which offers different features. In this way, it can be individually lock
installed application with the help of passcode and scan fingerprint. This features can extra
security layer to protect their data and important content especially when you hold the phone and
other person to show something. It also useful for person to install the features and applied the
smartphones such as App-lock etc.
Use two factor authentication- Many people can ignore the security features that face
many problems and hassle at every time that's why, it is required for user to use the two factor
authentication that help for provide the security with the help of authenticate with the passcode
(Conti and et.al., 2018). It can generate the unique authenticated code for particular application
such as One time password etc. this type of security feature offered by different services such as
Facebook, twitter, Instagram, google, Amazon, Snap-chat, PayPal etc.
Install security applications- A smart phone is based on the susceptible to data theft in
the computer system. It is important to get smart phones to install the security application that
manage the entire processing of system (Lee and et.al., 2018). There are various type of security
application available in the organization such as McAfee, Trend Micro, Avast, Norton etc. This

feature is automatically scan the smart phone and remove all unwanted threats and software in
the system.
Update phone and app regularly- This is the simplest procedure that each and every
people follows this to remove the unwanted temporary threats that affects the entire functionality
of smartphones. Google provide the notification to update and patch the phone regularly. It
always recommends to keep check all the system updates in proper manner. It is based on the
regular basis.
Questioners
Q1. Do you think people use the smart phones and computer system??
Yes
No
Not sure
Q 2. Do you think smart phone is useful device for people??
Yes
No
Not Sure
Q 3. Do you think people use the smartphone devices for Instagram and whatsapp??
yes
No
Not sure
Q 4.What is hacking??
Yes
No
Not sure
Q 5. Do you know comparison between the 4G and Wi-Fi ??
Yes
No
Not sure
Q.6 Do you Know what is anti virus protect in the smart phones??
Yes
No
the system.
Update phone and app regularly- This is the simplest procedure that each and every
people follows this to remove the unwanted temporary threats that affects the entire functionality
of smartphones. Google provide the notification to update and patch the phone regularly. It
always recommends to keep check all the system updates in proper manner. It is based on the
regular basis.
Questioners
Q1. Do you think people use the smart phones and computer system??
Yes
No
Not sure
Q 2. Do you think smart phone is useful device for people??
Yes
No
Not Sure
Q 3. Do you think people use the smartphone devices for Instagram and whatsapp??
yes
No
Not sure
Q 4.What is hacking??
Yes
No
Not sure
Q 5. Do you know comparison between the 4G and Wi-Fi ??
Yes
No
Not sure
Q.6 Do you Know what is anti virus protect in the smart phones??
Yes
No
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Not sure
Q 7. Do yo upgrade the Smart phones applications??
Yes
No
Not sure
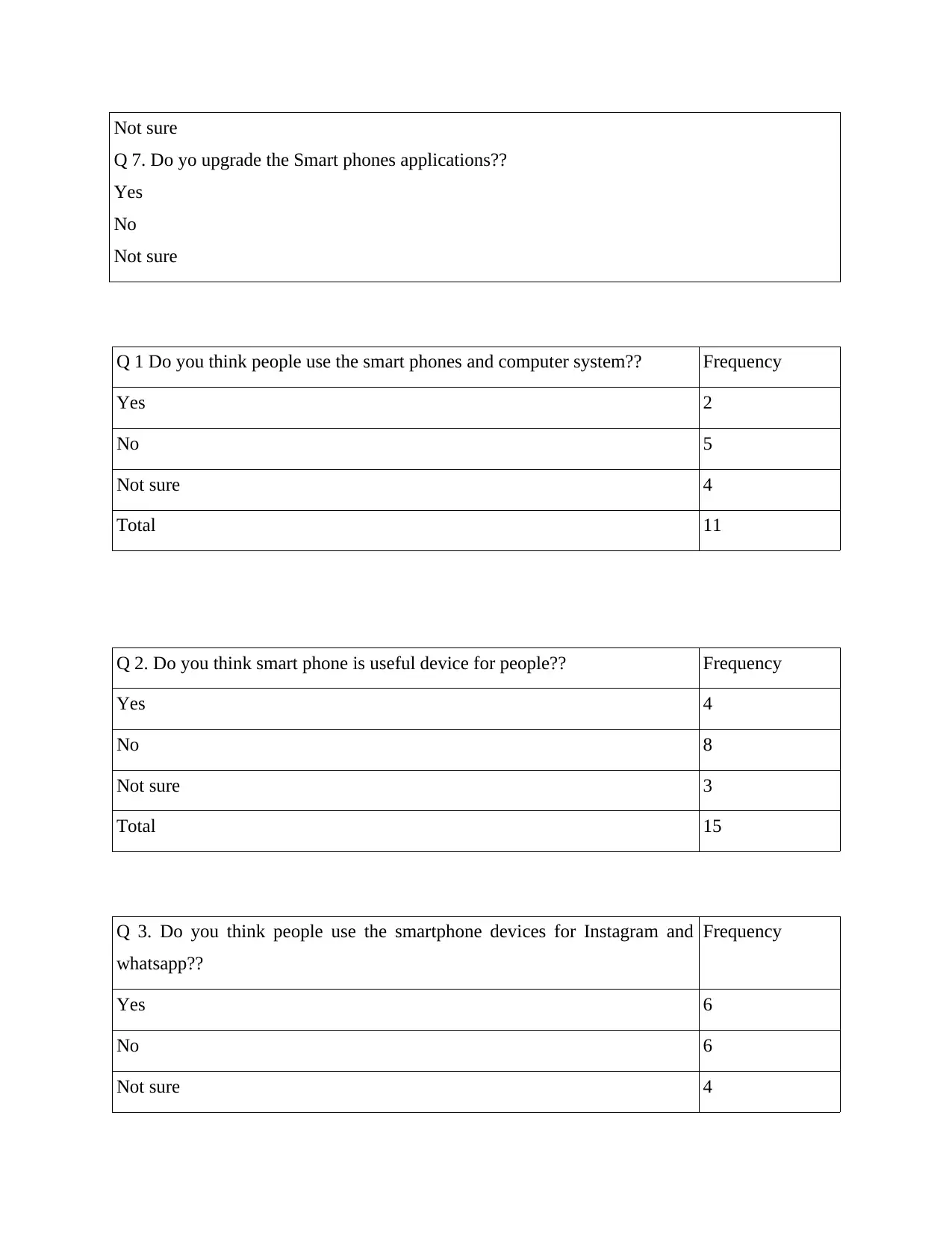
Q 1 Do you think people use the smart phones and computer system?? Frequency
Yes 2
No 5
Not sure 4
Total 11
Q 2. Do you think smart phone is useful device for people?? Frequency
Yes 4
No 8
Not sure 3
Total 15
Q 3. Do you think people use the smartphone devices for Instagram and
whatsapp??
Frequency
Yes 6
No 6
Not sure 4
Q 7. Do yo upgrade the Smart phones applications??
Yes
No
Not sure
Q 1 Do you think people use the smart phones and computer system?? Frequency
Yes 2
No 5
Not sure 4
Total 11
Q 2. Do you think smart phone is useful device for people?? Frequency
Yes 4
No 8
Not sure 3
Total 15
Q 3. Do you think people use the smartphone devices for Instagram and
whatsapp??
Frequency
Yes 6
No 6
Not sure 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Total 16
Q 4.What is hacking?? Frequency
Yes 1
No 3
Not sure 6
Total 10
Q 5. Do you know comparison between the 4G and Wi-Fi ?? Frequency
Yes 5
No 2
Not sure 2
Total 9
Q 6. Do you Know what is anti virus protect in the smart phones?? Frequency
Yes 5
No 7
Not sure 2
Total 14
Q 7. Do yo upgrade the Smart phones applications?? Frequency
Q 4.What is hacking?? Frequency
Yes 1
No 3
Not sure 6
Total 10
Q 5. Do you know comparison between the 4G and Wi-Fi ?? Frequency
Yes 5
No 2
Not sure 2
Total 9
Q 6. Do you Know what is anti virus protect in the smart phones?? Frequency
Yes 5
No 7
Not sure 2
Total 14
Q 7. Do yo upgrade the Smart phones applications?? Frequency
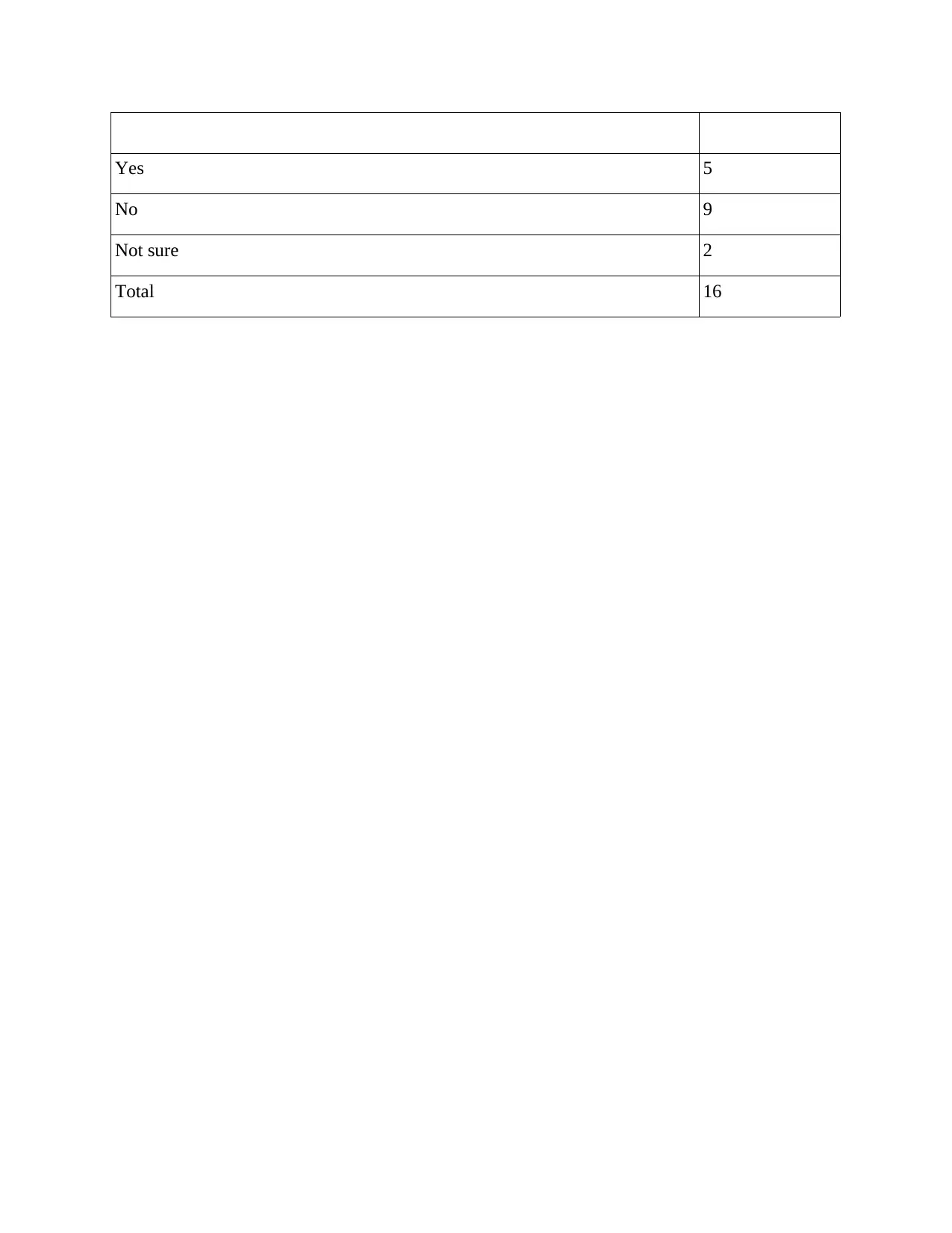
Yes 5
No 9
Not sure 2
Total 16
No 9
Not sure 2
Total 16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





