CO4509: Computer Security Report - WidgetInc VM Security Analysis
VerifiedAdded on 2023/01/19

Computer Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document

COMPUTERS SECURITY
Table of Contents
Overview..........................................................................................................................................3
Summary of Results.........................................................................................................................3
Methodology....................................................................................................................................4
Scope............................................................................................................................................5
Information Gathering.................................................................................................................5
IP and MAC Address...................................................................................................................6
Virtual Host.................................................................................................................................7
Scanning......................................................................................................................................8
Port Scan..................................................................................................................................8
Framework.............................................................................................................................12
WEB Scan..............................................................................................................................13
SQL Injection Scan................................................................................................................14
Result and Recommendations........................................................................................................15
Bibliography..................................................................................................................................17

COMPUTERS SECURITY
Overview
The virtual machine of WidgetInc has been attacked by means of ethical hacking for the
purpose of finding out the major weaknesses that exists in the computer system and also for the
purpose of handling the various attacking environment. In order to perform the test numerous
attacks have been performed upon the host. Followed by the completion of the attack the results
have been recorded and observed so as to identify those points which are weak and are having
the possibility of getting compromising the entire virtual machine. For the purpose of
penetration, the flags have been used and this acts as the root user where the other users were
used for the purpose of exploiting those issues existing in the configuration and for finding of the
desired vulnerabilities.
The entire report is associated with demonstrating the logs related to testing the results obtained
and providing of recommendations which were used for the security compromising of the host
targeted.
Summary of Results
After successful completion of the penetration testing it was found that the virtual
machine of the victim is vulnerable to the various kind of attacks which are to be faced by the
network and this type of attacks are mainly related to the access control, authorization and
authentication. The possibility related to unauthorized access increased in the authentication
process by usage of the non-plaintext for example the DIGEST-MD5 for the different web
applications as well as for having an impact of negative nature upon the data of the users which
are present in the database of the servers (Im et al. 2016). Besides all this the services which are
seen to be available for the users would be examined in a through manner by making use of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTERS SECURITY
different aspects such as the payloads, encoders, exploits and encoders. In addition to all this, the
security weaknesses have been documented which is to be used for the purpose of execution of
the arbitrary commands by the modules for the victims targeted and for running the distCC
daemon command without checking authorization.
For the purpose of enhancing the FTP server the service known as the ProFTPD has been
used along with the features of the Apache configuration syntax which consist of various virtual,
as well as permission based FTP servers (Coffey et al. 2018). All this are used for the purpose of
testing the favorable documents and for documenting the outputs.
Another security tool known as the Kali Linux is something different which is used for
the purpose of analyzing the different kind of potential problems along with the vulnerabilities
which are faced by the host by means of the password security bypassing, tools used for cracking
and for the purpose of recovering the data which were stored previously (Ambrosini, Groux and
Bucher 2018). Besides all this packages which are kali Linux has is a mixture of various
algorithms and the cracking strategies such as the brute force the attack dictionary which are
seen to be the most productive at the time of conducting the penetration testing.
Additionally, the Web server vulnerability is also tested and this is done so as to look for
the problems and identify them present in the software or in misconfiguration of the server. The
default files along with the programs are checked for finding the outdated and for identifying the
ones which are seen to be vulnerable for the various type of attacks faced by the network.
Methodology
Number of steps are undertaken for the purpose of starting the scope of the test for any
kind of vulnerabilities and this ends by means of the reporting of the output of all the test. Inn
Paraphrase This Document

COMPUTERS SECURITY
addition to all this a test which is self-performed is also conducted all throughout the modes
which can be used by the attacker for the purpose of having a control of the execution process of
various kind of attack along with finding of different prevention methods which might be having
a harmful affect upon the entire system. It is also to be noted that the approach which is adopted
for testing the vulnerability is not limited to automation but is also associated with manual
scanning and looking out for verifications (Genge and Enăchescu 2016). Elimination of the false
positives along with the errors found in the outputs is also possible by implementing the manual
scanning and configuration verification.
Scope
The scope of the entire process of conducting the test upon the VMware image is
associated with gathering of all the information related to the security services and the security
configuration. Due to absence of any kind of information related to the virtual machine it can be
considered to be falling under the Gray box testing category and numerous tools are utilized for
the purpose of gathering all the required information related to the image (Tundis, Mazurczyk
and Mühlhäuser 2018). Additionally the changing of the network adapter in vmware to host from
the NAT is done for the purpose of IP address identification from the machine and the usage of
the kali Linux helps in having a better visibility of the IP address 192.168.202.129 which has
been targeted.
Information Gathering
Prior to getting access to the targeted victim a research would be performed for the
purpose of gathering the information which are required from the third party sources which
includes the IP address identification of the host, making of attempts for hacking upon the
machine and information related to the operating system, services operating in the different
COMPUTERS SECURITY
portsand many more. This is done for the purpose of making use of this later and for performing
of the exploitation.
IP and MAC Address
Nmap or the Network mapper is one of the free as well as open source tool would be used for the
purpose of getting the devices IP address along with Mac address that are seen to be connected to
the network and this has been depicted in the table provided below (Rodofile, Radke and Foo
2016). Besides all this the Nmapis used by the network administrator so as to identify the devices
running on the system along with helping in discovering the hosts as well which are available
along with the services that are offered, open port detection and security risk detection.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTERS SECURITY
IP Address of active host in the network Mac address of the host
192.168.202.128 00:50:56:C0:00:01
192.168.202.128 00:50:56:EE:BF:F3
192.168.202.254 00:50:56:00:10:DE
Virtual Host
Virtual hosting generally refers to the process associated with hosting of the multiple
domain names on a single server which in turn is associated with allowing one server to share all
the resources like the memory and the processor cycles and this is done without requiring any of
the services that are provided for using the same host name (Myers, Foo and Radke 2015). Here
the virtual PC has been associated with the usage of the IP address which is same as the IP
address of the website. This initially leads to reach a conclusion that there exists the possibility
of the virtual server to get compromised along with the compromise of the security of the
website. Similar type of vulnerability can also be found out in the website of WidgetInc since the
virtual server is used for hosting the site.
Paraphrase This Document

COMPUTERS SECURITY
IP Address Website Content
192.168.202.128 Widget Inc
Scanning
There exists different type of scanning which can be used for the purpose of identification of the
vulnerabilities which faced by the virtual image of the victim. The steps related to scanning have
been listed below:
Port Scan
Used tool: Masscan
Description: Masscan is one the tool which is used for the purpose of scanning the ports which
is also having the capability of performing surveys over the internet on a large scale and this

COMPUTERS SECURITY
scanning might also be done on the intranet network. The tool is having a default transmit speed
of100 packet per second (Cabaj et al. 2018). However, it is also possible to modify this so as to
have a fast result after scanning which might be seen to be 25 million packet per second. This
rate of providing the results is considered to be much more than the enough so as to scan the
internet within a timespan of 3minute while finding the port.
Reason of Use: This tool is mostly used for the purpose of making sure that the ports are being
scanned at a faster rate as this is the one of the fastest port scanner available and is capable of
scanning at a speed of 10x faster than the other existing port scanners.
Host (IP) Port Status
192.168.202.128 1 Open
192.168.202.128 9 Open
192.168.202.128 13 Open
192.168.202.128 17 Open
192.168.202.128 22 Open
192.168.202.128 37 Open
192.168.202.128 80 Open
192.168.202.128 113 Open
192.168.202.128 465 Open
192.168.202.128 3306 Open
192.168.202.128 6667 Open
192.168.202.128 8080 Open
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTERS SECURITY
root@kali:~# masscan 192.168.202.128 --ports 1-65535 --rate=10000 --interface eth0 --router-
mac 00:50:56:00:10:DE
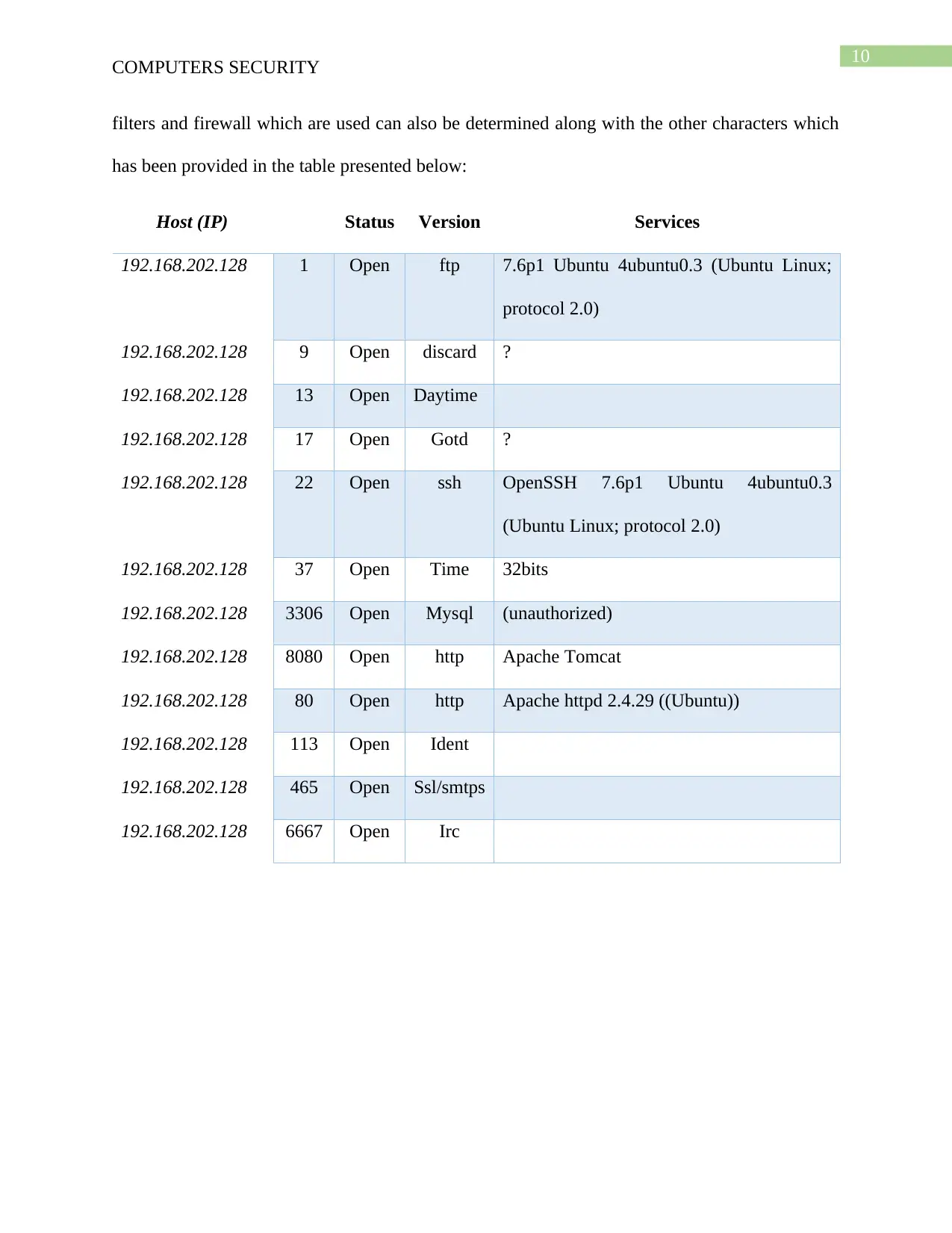
Tool Used: Nmap
Description: Nmap or the Network mapper is one of the free as well as open source tool would
be used for the purpose of getting the devices IP address along with Mac address that are seen to
be connected to the network and this has been depicted in the table provided below (Hixon and
Hutchens 2017). Besides all this the Nmapis used by the network administrator so as to identify
the devices running on the system along with helping in discovering the hosts as well which are
available along with the services that are offered, open port detection and security risk detection.
Reason of Use: The main reason lying behind the usage of the Nmap is that the tool makes use
of the Raw IP packets for the purpose of determining the host which is available and connected
to the network and the services which the host offers. Numerous other details like the details
about the operating system which runs in the IP address which has been targeted or the types of
Paraphrase This Document
COMPUTERS SECURITY
filters and firewall which are used can also be determined along with the other characters which
has been provided in the table presented below:
Host (IP) Status Version Services
192.168.202.128 1 Open ftp 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux;
protocol 2.0)
192.168.202.128 9 Open discard ?
192.168.202.128 13 Open Daytime
192.168.202.128 17 Open Gotd ?
192.168.202.128 22 Open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3
(Ubuntu Linux; protocol 2.0)
192.168.202.128 37 Open Time 32bits
192.168.202.128 3306 Open Mysql (unauthorized)
192.168.202.128 8080 Open http Apache Tomcat
192.168.202.128 80 Open http Apache httpd 2.4.29 ((Ubuntu))
192.168.202.128 113 Open Ident
192.168.202.128 465 Open Ssl/smtps
192.168.202.128 6667 Open Irc

COMPUTERS SECURITY
Framework
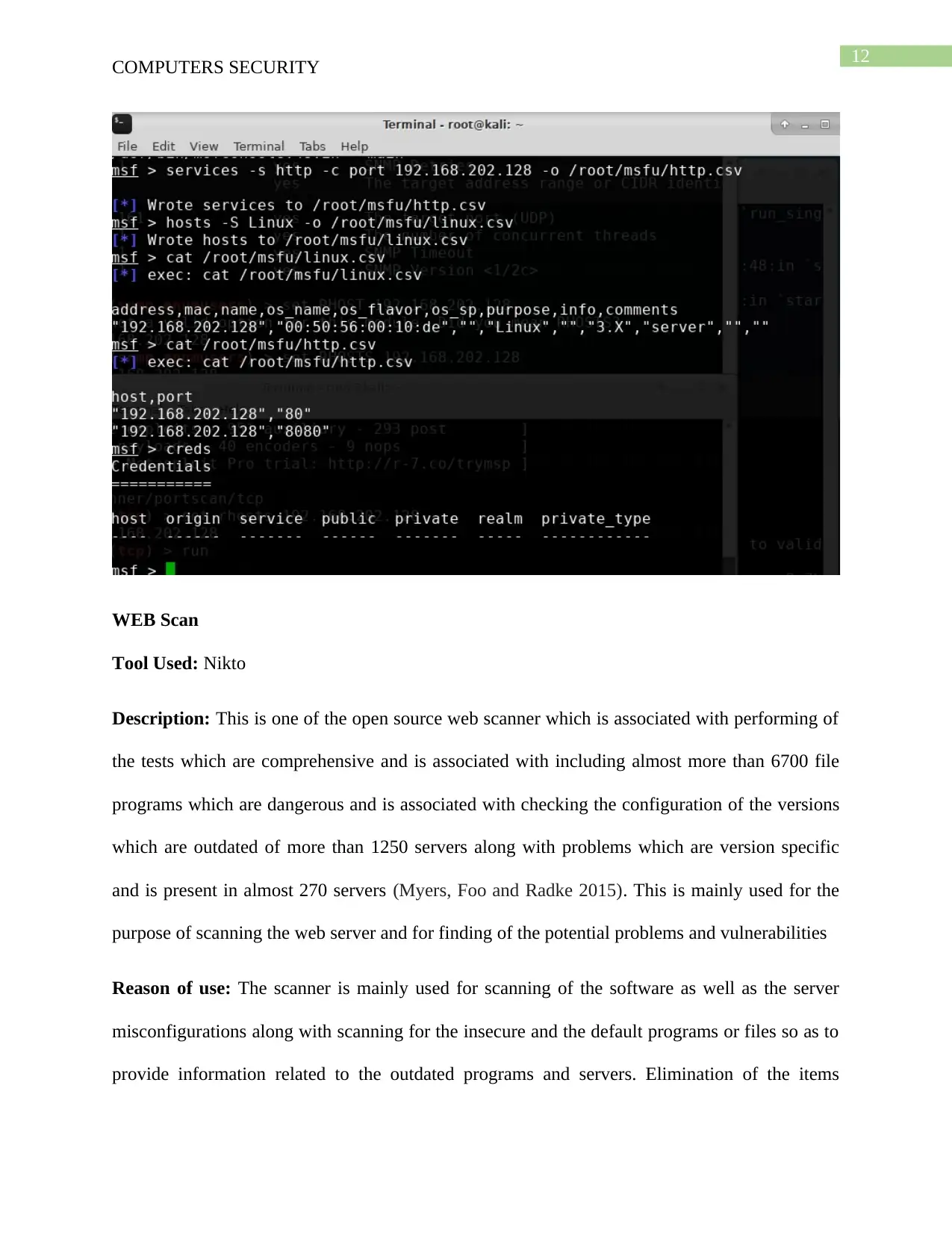
Tool Used: Metasploit
Description: This is a framework which is one of the Metsploits best-known creation and is also
considered to be the software framework which is used for the purpose of developing, executing
and testing the exploits. This can also be used for the purpose of creation of the security testing
tool and for the purpose of exploiting the modules along with being used by the penetration
testing systems (Budhrani and Sridaran 2015). This helps in the execution and development of
the exploit codes that are to be used remotely against the victim targeted.
Reason for Use: The reason for which this software is used is that it is associated with providing
the user with a choice related to exploitation of the configuration or is associated with optional
susceptibility checking for the targeted hosts and for the execution of the exploits. Besides this
there also exists a built in library functionality which is seen to be consisting of around 1662
exploits along with 951 auxiliaries, 9 nops, 40 encoders and 293 posts.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
COMPUTERS SECURITY
WEB Scan
Tool Used: Nikto
Description: This is one of the open source web scanner which is associated with performing of
the tests which are comprehensive and is associated with including almost more than 6700 file
programs which are dangerous and is associated with checking the configuration of the versions
which are outdated of more than 1250 servers along with problems which are version specific
and is present in almost 270 servers (Myers, Foo and Radke 2015). This is mainly used for the
purpose of scanning the web server and for finding of the potential problems and vulnerabilities
Reason of use: The scanner is mainly used for scanning of the software as well as the server
misconfigurations along with scanning for the insecure and the default programs or files so as to
provide information related to the outdated programs and servers. Elimination of the items
Paraphrase This Document

COMPUTERS SECURITY
associated with returning of the false positive results are done from the output for the purpose of
increasing the simplicity.
SQL Injection Scan
The SQL Injection Scan is the scan which is generally done upon the virtual machine
which has been targeted for the purpose of checking the fact that it is possible to insert the string
so as to make the website become vulnerable to any kind of exploitation (Budhrani and Sridaran
2015). In addition to all this attempts were also made for the purpose of modifying the database
in order to add the new credentials to the user table in such manner that it become possible to
gain the root access of the system which has been targeted.

COMPUTERS SECURITY
Result and Recommendations
The results obtained have been associated with depicting the fact that the nmap port
scanner is generally utilized for information gathering related to the network as well as the
targeted host. Besides this the tool is also capable of finding out the IP address along with the
running services and the ports with the details of the versions as well. Besides this it is also
possible to search the information related to the operating system which in turn is associated with
providing support to the scans done aggressively so as to obtain the information in details related
to the web service, OS, internal files, directories disallowed, metadata and many more. For this
reasons it is recommended to close those ports which not being used any more along with the
usage of filters so as to make sure that there exist restrictions in the process of getting direct
access. The report has been associated with highlighting the different steps which has been
performed for the purpose of having an access to the virtual machine so as to perform the
exploitation.
The vulnerability identification in the organization WidgetInc virtual machine has been
associated with helping in the preparation of the plans which would be acting as a
countermeasure plan for elimination of the different type of the risks related to the unauthorized
access. It is possible to make the system secure by using the UFW so as to make sure only those
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTERS SECURITY
ports are being used which are allowed. Besides all this it is also to be made sure that mysql is
capable of of only allowing the local hosts along with resolving of the risks related to remote
modification of the database (Hixon and Hutchens 2017). The ssh brute force blocker installation
would be helping in elimination of the risks related because of the brute force or dictionary
attacks. A key based mechanism is to be used for the ssh login attempts and along with this for
managing the physical access of the data it is suggested to encrypt the hard drive of the server.
Lastly the outdated system software service also needs to be identified and patched up so as to
make sure that they do not opens loop holes which would be helping the attacker in having
access of files and information.
Paraphrase This Document

COMPUTERS SECURITY
Bibliography
Ambrosini, G., Groux, R. and Bucher, P., 2018. PWMScan: a fast tool for scanning entire
genomes with a position-specific weight matrix. Bioinformatics, 34(14), pp.2483-2484.
Budhrani, R. and Sridaran, R., 2015. Wireless Local Area Networks: Threats and Their
Discovery Using WLANs Scanning Tools. International Journal Of Advanced Networking &
Applications, pp.137-150.
Cabaj, K., Gregorczyk, M., Mazurczyk, W., Nowakowski, P. and Żórawski, P., 2018, August.
SDN-based Mitigation of Scanning Attacks for the 5G Internet of Radio Light System.
In Proceedings of the 13th International Conference on Availability, Reliability and Security (p.
49). ACM.
Coffey, K., Smith, R., Maglaras, L. and Janicke, H., 2018. Vulnerability analysis of network
scanning on SCADA systems. Security and Communication Networks, 2018.
Genge, B. and Enăchescu, C., 2016. ShoVAT: Shodan‐based vulnerability assessment tool for
Internet‐facing services. Security and communication networks, 9(15), pp.2696-2714.
Hixon, M. and Hutchens, J., 2017. Kali Linux Network Scanning Cookbook. Packt Publishing
Ltd.
Im, S.Y., Shin, S.H., Ryu, K.Y. and Roh, B.H., 2016, July. Performance evaluation of network
scanning tools with operation of firewall. In 2016 Eighth International Conference on
Ubiquitous and Future Networks (ICUFN) (pp. 876-881). IEEE.

COMPUTERS SECURITY
Myers, D., Foo, E. and Radke, K., 2015. Internet-wide scanning taxonomy and framework.
In Proceedings of Australasian Information Security Conference (ACSW-AISC), 27-30 January
2015. Australian Computer Society, Inc.
Rodofile, N.R., Radke, K. and Foo, E., 2016, February. DNP3 network scanning and
reconnaissance for critical infrastructure. In Proceedings of the Australasian Computer Science
Week Multiconference (p. 39). ACM.
Tundis, A., Mazurczyk, W. and Mühlhäuser, M., 2018, August. A review of network
vulnerabilities scanning tools: types, capabilities and functioning. In Proceedings of the 13th
International Conference on Availability, Reliability and Security (p. 65). ACM.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
© 2024 | Zucol Services PVT LTD | All rights reserved.





