Computing IT Security - Confidentiality, Integrity, Availability, Biometric Authentication, False Positive and False Negative
VerifiedAdded on 2023/06/14
|7
|1683
|77
AI Summary
This article discusses the concepts of confidentiality, integrity, and availability in computing IT security. It also covers the use of biometric authentication and the issues related to false positive and false negative.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: COMPUTING IT SECURITY
Computing IT security
Name of the student
Name of the University
Author Note:
Computing IT security
Name of the student
Name of the University
Author Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
COMPUTING IT SECURITY
Answer 1:
Confidentiality in this case involves the various information of the user, which is hidden
and should not be shared with anyone. This is the confidential information of the user. The
number of the ATM card and the CVV number of the card should not be shared with anyone as
these are the confidential information (Morse & Coulehan, 2015). If anybody gets hold of these
information then there might be stealing of the amount from the account of the user. The other
confidential information involved may be PIN number of the account holder.
The integrity policies may revolve around the hackers who try and hack the system of the
customers of the various banks for the purpose of stealing. The integrity policies also involve the
various people trying to peep in the ATMs for knowing the pin of the person using the ATM
machine (Margaria & Falletti, 2015). Many of the thieves and the cheaters call in the name of the
bank and ask for the details concerning the details of the bank account. This is also a malicious
practice and should be stopped in order to maintain the integrity policies.
The availability requirements involve the proper working of the ATM machines so that
the transaction can be properly carried out. The other requirement is the proper interface of the
machine in which the user is working and carrying out the procedure of the transaction. After the
transaction is carried out the machine should be flexible enough to generate the bills or the slip
carrying the information of the transaction that has taken place (Kisore & Koteswaraiah, 2017).
The other basic requirements may be the maintaining a proper security both physical and
technological. The systems from the banks should be protected in order to save the money of the
customers. The security should be strong enough in order to protect the systems of the
organization.
COMPUTING IT SECURITY
Answer 1:
Confidentiality in this case involves the various information of the user, which is hidden
and should not be shared with anyone. This is the confidential information of the user. The
number of the ATM card and the CVV number of the card should not be shared with anyone as
these are the confidential information (Morse & Coulehan, 2015). If anybody gets hold of these
information then there might be stealing of the amount from the account of the user. The other
confidential information involved may be PIN number of the account holder.
The integrity policies may revolve around the hackers who try and hack the system of the
customers of the various banks for the purpose of stealing. The integrity policies also involve the
various people trying to peep in the ATMs for knowing the pin of the person using the ATM
machine (Margaria & Falletti, 2015). Many of the thieves and the cheaters call in the name of the
bank and ask for the details concerning the details of the bank account. This is also a malicious
practice and should be stopped in order to maintain the integrity policies.
The availability requirements involve the proper working of the ATM machines so that
the transaction can be properly carried out. The other requirement is the proper interface of the
machine in which the user is working and carrying out the procedure of the transaction. After the
transaction is carried out the machine should be flexible enough to generate the bills or the slip
carrying the information of the transaction that has taken place (Kisore & Koteswaraiah, 2017).
The other basic requirements may be the maintaining a proper security both physical and
technological. The systems from the banks should be protected in order to save the money of the
customers. The security should be strong enough in order to protect the systems of the
organization.

2
COMPUTING IT SECURITY
Answer 2:
The thief was able to jam the card reader and break the five keys of the keypad. However,
the customer was successful in entering the PIN and extract the amount that was required but
could not take out the card as the card reader was jammed by the thief. As the five keypads have
been broken the number of option left with the thief in order to operate is 4.
Therefore, the number of options left with the thief: 4
The maximum number of PIN that the customer has to enter or the maximum number of attempts
that the thief has to make in order to successfully crack the PIN of the customer is 5!/ (5-4)!.
Thus after making 120 attempts the thief may successfully be able to crack the PIN of the
customer.
Answer 3:
The use of the biometric authentication is made at a number of places. The concept of
bio- metric authentication involves the use of some of the part of the body of the user for gaining
the characteristics and the information about the person. However, many are reluctant to the use
of the bio- metric authentication due to various reasons.
The bio- metrics cannot be recovered in case it is destroyed or some problem occurs
(Haupt & Mozer, 2015). For instance, in case of a mail id it can be recovered with the use
of any of the secondary devices. The manipulation in the bio- metrics however cannot be
recovered or retrieved.
The passwords can be changed in case any activity occurs such as anyone comes to know
about the password or if anyone tries to get into the account unethically (Alsaadi, 2015).
COMPUTING IT SECURITY
Answer 2:
The thief was able to jam the card reader and break the five keys of the keypad. However,
the customer was successful in entering the PIN and extract the amount that was required but
could not take out the card as the card reader was jammed by the thief. As the five keypads have
been broken the number of option left with the thief in order to operate is 4.
Therefore, the number of options left with the thief: 4
The maximum number of PIN that the customer has to enter or the maximum number of attempts
that the thief has to make in order to successfully crack the PIN of the customer is 5!/ (5-4)!.
Thus after making 120 attempts the thief may successfully be able to crack the PIN of the
customer.
Answer 3:
The use of the biometric authentication is made at a number of places. The concept of
bio- metric authentication involves the use of some of the part of the body of the user for gaining
the characteristics and the information about the person. However, many are reluctant to the use
of the bio- metric authentication due to various reasons.
The bio- metrics cannot be recovered in case it is destroyed or some problem occurs
(Haupt & Mozer, 2015). For instance, in case of a mail id it can be recovered with the use
of any of the secondary devices. The manipulation in the bio- metrics however cannot be
recovered or retrieved.
The passwords can be changed in case any activity occurs such as anyone comes to know
about the password or if anyone tries to get into the account unethically (Alsaadi, 2015).

3
COMPUTING IT SECURITY
However, if someone gets the copy of the iris or the copy of the pattern of the finger of
the person then the person can access the information of the person. The person cannot
change the bio- metric information as well.
It has also be found by the various researchers couple of years ago that there were
weaknesses that were discovered in the android phones and through the phones the finger
print of the user of the phone can be obtained, which can then be used in the bio- metrics.
Answer 4:
The false positive means the situation when the situation should have resulted as negative
but has turned out as positive. The various instance of this may be the case where a particular
person is ill but the person does not have any major disease (Morton et al., 2016) Here, the result
of the illness may have due to some of a major disease. Thus, the result here should have been
negative. However, it is found that the result has turned to be a positive one as the person is just
having a minor illness and it is not due to any of the major illness. This is the situation of false
positive.
The false negative means the reverse of the false positive, which states that the result of a
situation which should have been positive has turned out to be a negative one. An instance of the
false negative can be the design of the software testing, which is designed to catch or detect a
particular virus has failed (Kowalski et al., 2017). The case should have resulted as positive but
has end up as a negative result. In this case the software testing device designed should have
been able to detect the virus that is present. The software was specially designed in order to
detect the virus. The use of the software has been made in order to detect the virus, which should
COMPUTING IT SECURITY
However, if someone gets the copy of the iris or the copy of the pattern of the finger of
the person then the person can access the information of the person. The person cannot
change the bio- metric information as well.
It has also be found by the various researchers couple of years ago that there were
weaknesses that were discovered in the android phones and through the phones the finger
print of the user of the phone can be obtained, which can then be used in the bio- metrics.
Answer 4:
The false positive means the situation when the situation should have resulted as negative
but has turned out as positive. The various instance of this may be the case where a particular
person is ill but the person does not have any major disease (Morton et al., 2016) Here, the result
of the illness may have due to some of a major disease. Thus, the result here should have been
negative. However, it is found that the result has turned to be a positive one as the person is just
having a minor illness and it is not due to any of the major illness. This is the situation of false
positive.
The false negative means the reverse of the false positive, which states that the result of a
situation which should have been positive has turned out to be a negative one. An instance of the
false negative can be the design of the software testing, which is designed to catch or detect a
particular virus has failed (Kowalski et al., 2017). The case should have resulted as positive but
has end up as a negative result. In this case the software testing device designed should have
been able to detect the virus that is present. The software was specially designed in order to
detect the virus. The use of the software has been made in order to detect the virus, which should
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4
COMPUTING IT SECURITY
have been a positive result. However as the software was unable to detect the virus, the result has
turned out to be negative.
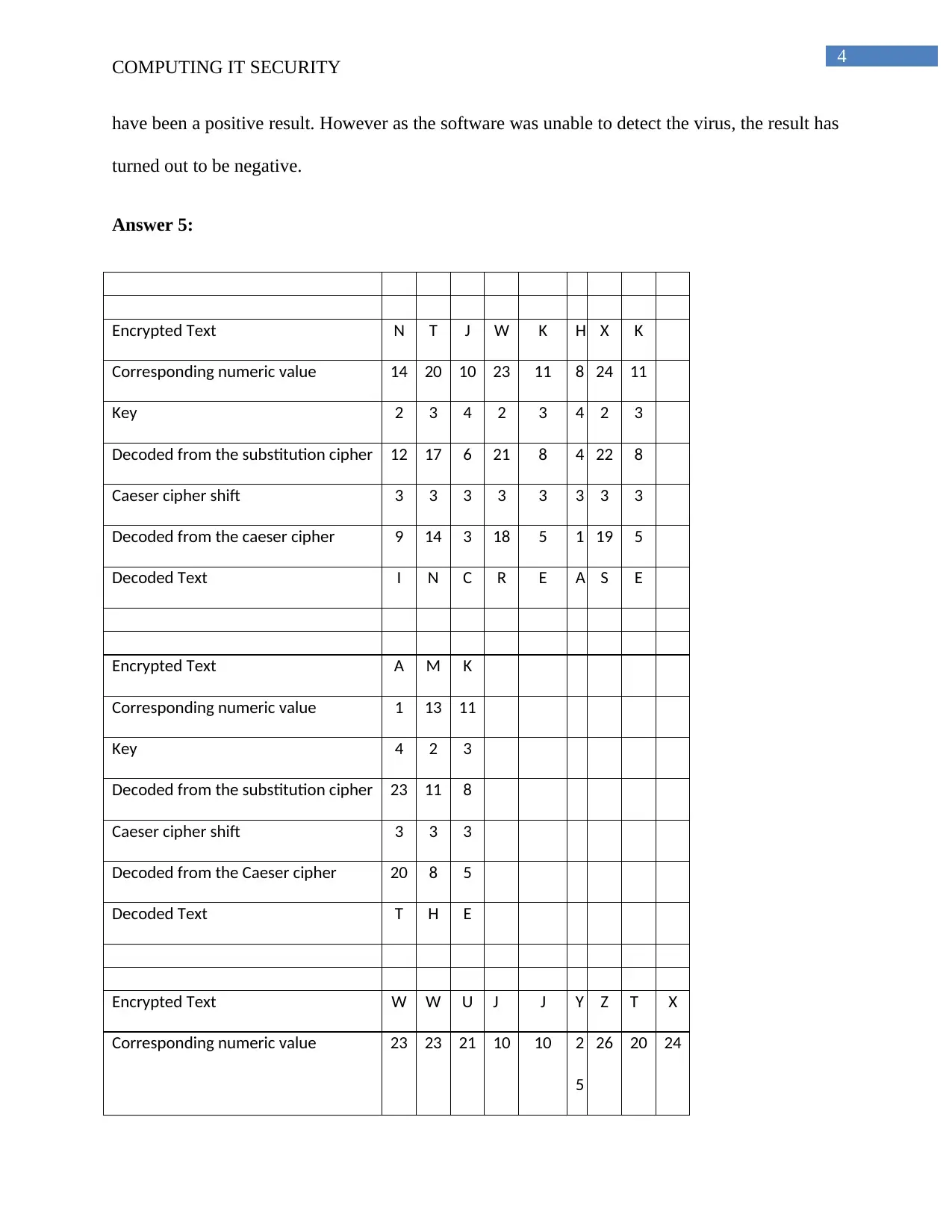
Answer 5:
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the Caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 2
5
26 20 24
COMPUTING IT SECURITY
have been a positive result. However as the software was unable to detect the virus, the result has
turned out to be negative.
Answer 5:
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the Caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 2
5
26 20 24
5
COMPUTING IT SECURITY
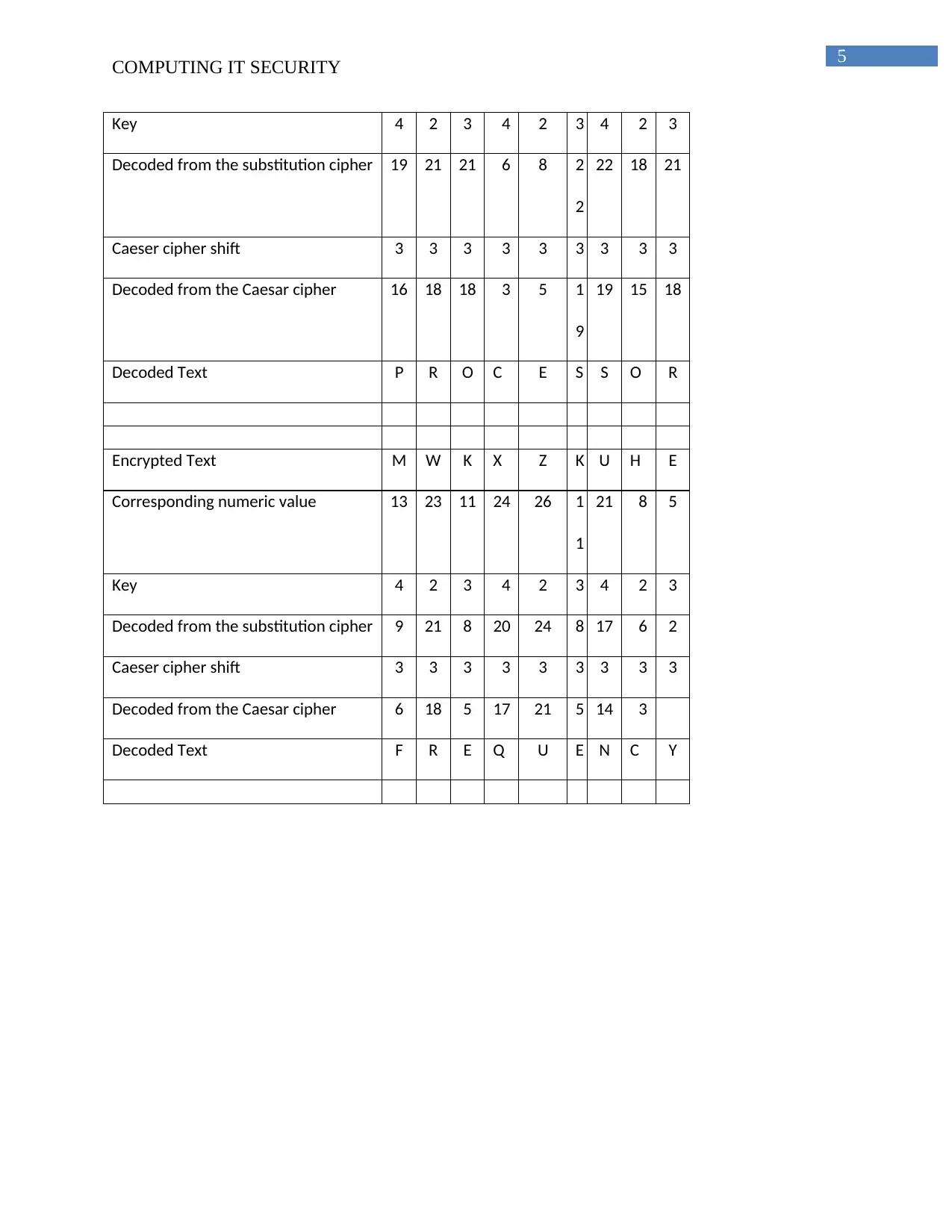
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 19 21 21 6 8 2
2
22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the Caesar cipher 16 18 18 3 5 1
9
19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 1
1
21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the Caesar cipher 6 18 5 17 21 5 14 3
Decoded Text F R E Q U E N C Y
COMPUTING IT SECURITY
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 19 21 21 6 8 2
2
22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the Caesar cipher 16 18 18 3 5 1
9
19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 1
1
21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the Caesar cipher 6 18 5 17 21 5 14 3
Decoded Text F R E Q U E N C Y

6
COMPUTING IT SECURITY
References:
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages,
Disadvantages And Future Development: A Review. International Journal Of Scientific
& Technology Research, 4(8), 285-289.
Haupt, G., & Mozer, T. (2015). Assessing biometric authentication: a holistic approach to
accuracy. Biometric Technology Today, 2015(3), 5-8.
Kisore, N. R., & Koteswaraiah, C. B. (2017). Improving ATM coverage area using density based
clustering algorithm and voronoi diagrams. Information Sciences, 376, 1-20.
Kowalski, T., Siddiqui, A., Loren, D., Mertz, H. R., Mallat, D., Haddad, N., ... & Okoh, E.
(2016). Management of patients with pancreatic cysts: analysis of possible false-negative
cases of malignancy. Journal of clinical gastroenterology, 50(8), 649.
Margaria, D., & Falletti, E. (2015). Proof-of-concept of the local integrity approach: Prototype
implementation and performance assessment in an urban context. In Localization and
GNSS (ICL-GNSS), 2015 International Conference on(pp. 1-6). IEEE.
Morse, J. M., & Coulehan, J. (2015). Maintaining confidentiality in qualitative publications.
Morton, T. D., Bryson, S. T., Coughlin, J. L., Rowe, J. F., Ravichandran, G., Petigura, E. A., ...
& Batalha, N. M. (2016). False positive probabilities for all Kepler objects of interest:
1284 newly validated planets and 428 likely false positives. The Astrophysical
Journal, 822(2), 86.
COMPUTING IT SECURITY
References:
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages,
Disadvantages And Future Development: A Review. International Journal Of Scientific
& Technology Research, 4(8), 285-289.
Haupt, G., & Mozer, T. (2015). Assessing biometric authentication: a holistic approach to
accuracy. Biometric Technology Today, 2015(3), 5-8.
Kisore, N. R., & Koteswaraiah, C. B. (2017). Improving ATM coverage area using density based
clustering algorithm and voronoi diagrams. Information Sciences, 376, 1-20.
Kowalski, T., Siddiqui, A., Loren, D., Mertz, H. R., Mallat, D., Haddad, N., ... & Okoh, E.
(2016). Management of patients with pancreatic cysts: analysis of possible false-negative
cases of malignancy. Journal of clinical gastroenterology, 50(8), 649.
Margaria, D., & Falletti, E. (2015). Proof-of-concept of the local integrity approach: Prototype
implementation and performance assessment in an urban context. In Localization and
GNSS (ICL-GNSS), 2015 International Conference on(pp. 1-6). IEEE.
Morse, J. M., & Coulehan, J. (2015). Maintaining confidentiality in qualitative publications.
Morton, T. D., Bryson, S. T., Coughlin, J. L., Rowe, J. F., Ravichandran, G., Petigura, E. A., ...
& Batalha, N. M. (2016). False positive probabilities for all Kepler objects of interest:
1284 newly validated planets and 428 likely false positives. The Astrophysical
Journal, 822(2), 86.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





